Powerpoint Templates and Google slides for Security Information
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Implementation Of Strong Password Policy Information Technology Security
Implementation Of Strong Password Policy Information Technology SecurityThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Implementation Of Strong Password Policy Information Technology Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Americans, Implementation, Passwords, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security 60 Days Plan
Information Technology Security 60 Days PlanThis slide represents the plan for 60 days after implementing the cyber security model in the organization. Present the topic in a bit more detail with this Information Technology Security 60 Days Plan. Use it as a tool for discussion and navigation on Managing, Information, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Assessment Matrix Of Cyber Risks
Information Technology Security Assessment Matrix Of Cyber RisksThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an outstanding presentation on the topic using this Information Technology Security Assessment Matrix Of Cyber Risks. Dispense information and present a thorough explanation of Assessment Matrix Of Cyber Risks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Awareness Training Budget For Fy2022
Information Technology Security Awareness Training Budget For Fy2022This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Present the topic in a bit more detail with this Information Technology Security Awareness Training Budget For Fy2022. Use it as a tool for discussion and navigation on Employee Awareness Training Budget For FY2022. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
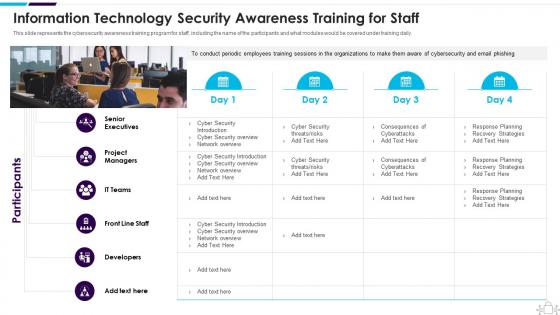 Information Technology Security Awareness Training For Staff
Information Technology Security Awareness Training For StaffThis slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver an outstanding presentation on the topic using this Information Technology Security Awareness Training For Staff. Dispense information and present a thorough explanation of Senior Executives, Project Managers, Developers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Best Practices For Cloud Security
Information Technology Security Best Practices For Cloud SecurityThis slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Present the topic in a bit more detail with this Information Technology Security Best Practices For Cloud Security. Use it as a tool for discussion and navigation on Operations, Management, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Common Methods Used Threaten Information Security
Information Technology Security Common Methods Used Threaten Information SecurityThis slide depicts the standard methods used to threaten cyber security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Introducing Information Technology Security Common Methods Used Threaten Information Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Daniel Of Service, Man In The Middle, SQL Injection , using this template. Grab it now to reap its full benefits.
-
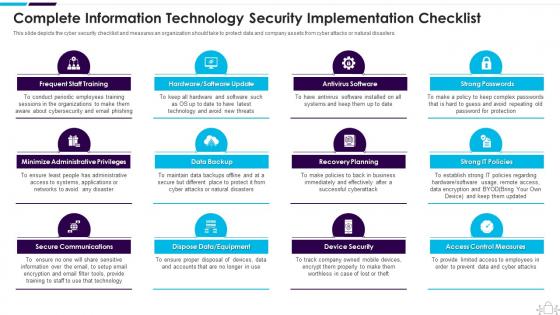 Information Technology Security Complete Information Security Implementation Checklist
Information Technology Security Complete Information Security Implementation ChecklistThis slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Introducing Information Technology Security Complete Information Security Implementation Checklist to increase your presentation threshold. Encompassed with twelve stages, this template is a great option to educate and entice your audience. Dispence information on Frequent Staff Training, Administrative Privileges, Data Backup, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Cyber Threat Landscape In Information Technology Security
Information Technology Security Cyber Threat Landscape In Information Technology SecurityThis slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver an outstanding presentation on the topic using this Information Technology Security Cyber Threat Landscape In Information Technology Security. Dispense information and present a thorough explanation of Landscape, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Data Backup For Sensitive Information
Information Technology Security Data Backup For Sensitive InformationThis slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Introducing Information Technology Security Data Backup For Sensitive Information to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Prepare Data Backup For Sensitive Information, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Define Access Control Measures For Employees
Information Technology Security Define Access Control Measures For EmployeesThis slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Increase audience engagement and knowledge by dispensing information using Information Technology Security Define Access Control Measures For Employees. This template helps you present information on four stages. You can also present information on Organization, Permissions, Responsibilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Dispose Data And Equipment Properly
Information Technology Security Dispose Data And Equipment ProperlyThis slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Introducing Information Technology Security Dispose Data And Equipment Properly to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Dispose Data And Equipment Properly, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Elements Information Technology Security Cloud Security
Information Technology Security Elements Information Technology Security Cloud SecurityThis slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Introducing Information Technology Security Elements Information Technology Security Cloud Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Elements, Information, Technology, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Employees Devices
Information Technology Security Employees DevicesThis slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Increase audience engagement and knowledge by dispensing information using Information Technology Security Employees Devices. This template helps you present information on four stages. You can also present information on Security Of Employees Devices using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security End User Education Information Technology Security
Information Technology Security End User Education Information Technology SecurityThis slide shows the end user education within the cyber security model. It also represents various factors that effective training plans should involve. Introducing Information Technology Security End User Education Information Technology Security to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Assessment, Microlearning, Opportunities, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Hardware And Software Update In Company
Information Technology Security Hardware And Software Update In CompanyThis slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Increase audience engagement and knowledge by dispensing information using Information Technology Security Hardware And Software Update In Company. This template helps you present information on three stages. You can also present information on Hardware And Software Update In Company using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security How Is Automation Used In Information Technology Security
Information Technology Security How Is Automation Used In Information Technology SecurityThis slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Introducing Information Technology Security How Is Automation Used In Information Technology Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Threat Detection, Threat Response, Human Augmentation, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Information Technology Security Elements
Information Technology Security Information Technology Security ElementsThis slide represents the different elements of cyber security such as application security, network security, information security, etc. Introducing Information Technology Security Information Technology Security Elements to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on End User Education, Operational Security, Information Security, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security It Infrastructure Information Budget For Fy2022
Information Technology Security It Infrastructure Information Budget For Fy2022This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Present the topic in a bit more detail with this Information Technology Security It Infrastructure Information Budget For Fy2022. Use it as a tool for discussion and navigation on Infrastructure, Information, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Latest Threats In Information Technology Security
Information Technology Security Latest Threats In Information Technology SecurityThis slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Deliver an outstanding presentation on the topic using this Information Technology Security Latest Threats In Information Technology Security. Dispense information and present a thorough explanation of Latest Threats In Information Technology Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Main Steps Of Operational Security
Information Technology Security Main Steps Of Operational SecurityThis slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Present the topic in a bit more detail with this Information Technology Security Main Steps Of Operational Security. Use it as a tool for discussion and navigation on Assessment Of Risks, Define Sensitive Information, Identify Potential Threats This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Managing Information Technology Security 90 Days Plan
Information Technology Security Managing Information Technology Security 90 Days PlanThis slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an outstanding presentation on the topic using this Information Technology Security Managing Information Technology Security 90 Days Plan. Dispense information and present a thorough explanation of Managing, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Minimize Administrative And Staff Privileges
Information Technology Security Minimize Administrative And Staff PrivilegesThis slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. Introducing Information Technology Security Minimize Administrative And Staff Privileges to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Minimize Administrative And Staff Privileges, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Network Security
Information Technology Security Network SecurityThis slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Increase audience engagement and knowledge by dispensing information using Information Technology Security Network Security. This template helps you present information on seven stages. You can also present information on Information, Technology, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Of Information Technology Security Disaster Recovery Planning
Information Technology Security Of Information Technology Security Disaster Recovery PlanningThis slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. Introducing Information Technology Security Of Information Technology Security Disaster Recovery Planning to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Information, Technology, Security using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Operational Security
Information Technology Security Operational SecurityThis slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Increase audience engagement and knowledge by dispensing information using Information Technology Security Operational Security. This template helps you present information on five stages. You can also present information on Change Management, Processes, Deploy Automation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Process Of Disaster Recovery Planning
Information Technology Security Process Of Disaster Recovery PlanningThis slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Introducing Information Technology Security Process Of Disaster Recovery Planning to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Process Of Disaster Recovery Planning, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Roadmap For Information Technology Security Training
Information Technology Security Roadmap For Information Technology Security TrainingThis slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Introducing Information Technology Security Roadmap For Information Technology Security Training to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Roadmap, Information, Technology, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Safety Tips Protection Against Cyberattacks
Information Technology Security Safety Tips Protection Against CyberattacksThis slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Increase audience engagement and knowledge by dispensing information using Information Technology Security Safety Tips Protection Against Cyberattacks. This template helps you present information on five stages. You can also present information on Cyber Safety Tips Protection Against Cyberattacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Set Measures For Secure Communication
Information Technology Security Set Measures For Secure CommunicationThis slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. Introducing Information Technology Security Set Measures For Secure Communication to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Organization, Measures, Communication, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Strategies To Manage Cyber Risks
Information Technology Security Strategies To Manage Cyber RisksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Increase audience engagement and knowledge by dispensing information using Information Technology Security Strategies To Manage Cyber Risks. This template helps you present information on four stages. You can also present information on Strategic, Structures, Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Table Of Contents
Information Technology Security Table Of ContentsIntroducing Information Technology Security Table Of Contents to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Information, Technology, Security, using this template. Grab it now to reap its full benefits.
-
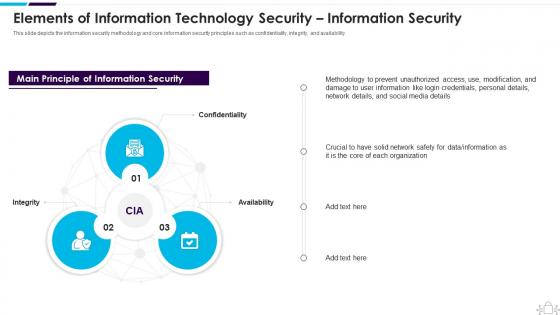 Information Technology Security Technology Security Information Security
Information Technology Security Technology Security Information SecurityThis slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. Increase audience engagement and knowledge by dispensing information using Information Technology Security Technology Security Information Security. This template helps you present information on three stages. You can also present information on Confidentiality, Availability, Integrity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Threats In Information Technology Security
Information Technology Security Threats In Information Technology SecurityThis slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Introducing Information Technology Security Threats In Information Technology Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Types Of Threats In Information Technology Security, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Types Of Disaster Recovery Plan
Information Technology Security Types Of Disaster Recovery PlanThis slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud based disaster recovery plans, etc. Increase audience engagement and knowledge by dispensing information using Information Technology Security Types Of Disaster Recovery Plan. This template helps you present information on four stages. You can also present information on Disaster, Recovery, Virtualization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security What Is Information Technology Security And How Does It Work
Information Technology Security What Is Information Technology Security And How Does It WorkThis slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Introducing Information Technology Security What Is Information Technology Security And How Does It Work to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Information, Technology, Security, using this template. Grab it now to reap its full benefits.
-
 Main Principle Of Information Security Information Technology Security
Main Principle Of Information Security Information Technology SecurityThis slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Deliver an outstanding presentation on the topic using this Main Principle Of Information Security Information Technology Security. Dispense information and present a thorough explanation of Main Principle Of Information Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Managing Information Technology Security 30 Days Plan Information Technology Security
Managing Information Technology Security 30 Days Plan Information Technology SecurityThis slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Present the topic in a bit more detail with this Managing Information Technology Security 30 Days Plan Information Technology Security. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing Reporting, Phishing Repeat Offenders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prepare A Disaster Recovery Plan Information Technology Security
Prepare A Disaster Recovery Plan Information Technology SecurityThis slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. Introducing Prepare A Disaster Recovery Plan Information Technology Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Assessment Report, Importance Of Assets, Recovery Plan, using this template. Grab it now to reap its full benefits.
-
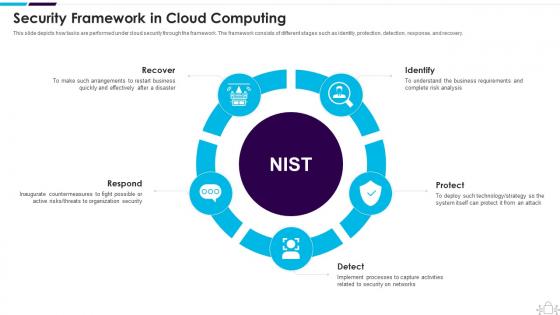 Security Framework In Cloud Computing Information Technology Security
Security Framework In Cloud Computing Information Technology SecurityThis slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. Increase audience engagement and knowledge by dispensing information using Security Framework In Cloud Computing Information Technology Security. This template helps you present information on five stages. You can also present information on Recover, Respond, Identify using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents For Information Technology Security
Table Of Contents For Information Technology SecurityIntroducing Table Of Contents For Information Technology Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Information, Technology, Security, using this template. Grab it now to reap its full benefits.
-
 Timeline For The Implementation Of Information Technology Security
Timeline For The Implementation Of Information Technology SecurityThis slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an outstanding presentation on the topic using this Timeline For The Implementation Of Information Technology Security. Dispense information and present a thorough explanation of Implementation, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 What Are The Benefits Of Information Technology Security
What Are The Benefits Of Information Technology SecurityThis slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Introducing What Are The Benefits Of Information Technology Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on What Are The Benefits Of Information Technology Security, using this template. Grab it now to reap its full benefits.
-
 Siem For Security Analysis Information And Event Management Logging Process
Siem For Security Analysis Information And Event Management Logging ProcessThis slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation Introducing Siem For Security Analysis Information And Event Management Logging Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Information, Management, Process, using this template. Grab it now to reap its full benefits.
-
 Siem For Security Analysis Security Information And Event Management Services
Siem For Security Analysis Security Information And Event Management ServicesThis slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Increase audience engagement and knowledge by dispensing information using Siem For Security Analysis Security Information And Event Management Services. This template helps you present information on eight stages. You can also present information on Data Aggregation, Data Correlation, Security Alert using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Access Control Methods Information Security Ppt Powerpoint Presentation Pictures Visual Aids Cpb
Access Control Methods Information Security Ppt Powerpoint Presentation Pictures Visual Aids CpbPresenting our Access Control Methods Information Security Ppt Powerpoint Presentation Pictures Visual Aids Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Access Control Methods Information Security. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Elements Of Network Security Information Security Ppt Slides Objects
Elements Of Network Security Information Security Ppt Slides ObjectsThis slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. Introducing Elements Of Network Security Information Security Ppt Slides Objects to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Information, Principle, Security, Confidentiality, using this template. Grab it now to reap its full benefits.
-
 Information security classification ppt powerpoint presentation inspiration picture cpb
Information security classification ppt powerpoint presentation inspiration picture cpbPresenting Information Security Classification Ppt Powerpoint Presentation Inspiration Picture Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Information Security Classification. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Addressing three essential attributes of information building organizational security strategy plan
Addressing three essential attributes of information building organizational security strategy planThis slide provides information about essential attributes of information in terms of protecting confidentiality, ensuring integrity and maintaining availability. Introducing Addressing Three Essential Attributes Of Information Building Organizational Security Strategy Plan to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Information, Confidentiality, Responsibilities, using this template. Grab it now to reap its full benefits.
-
 Addressing three essential attributes of information enhancing overall project security it
Addressing three essential attributes of information enhancing overall project security itThis slide provides information about essential attributes of information associated to IT project in terms of protecting confidentiality, ensuring integrity and maintaining availability. Introducing Addressing Three Essential Attributes Of Information Enhancing Overall Project Security It to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Information, Associated, Responsibilities, using this template. Grab it now to reap its full benefits.
-
 Big data it security of information in big data
Big data it security of information in big dataThis slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on. Introducing Big Data It Security Of Information In Big Data to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Information, Companies, Professionals, using this template. Grab it now to reap its full benefits.
-
 Role Of Chief Information Security Officer Role Of Technical Skills In Digital Transformation
Role Of Chief Information Security Officer Role Of Technical Skills In Digital TransformationThis slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc. Introducing Role Of Chief Information Security Officer Role Of Technical Skills In Digital Transformation to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Information, Security Information, External Security, using this template. Grab it now to reap its full benefits.
-
 Information Security Attacks Ppt Powerpoint Presentation Outline Inspiration Cpb
Information Security Attacks Ppt Powerpoint Presentation Outline Inspiration CpbPresenting our Information Security Attacks Ppt Powerpoint Presentation Outline Inspiration Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Information Security Attacks This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Individual Cyber Security Insurance Ppt Powerpoint Presentation Ideas Information Cpb
Individual Cyber Security Insurance Ppt Powerpoint Presentation Ideas Information CpbPresenting our Individual Cyber Security Insurance Ppt Powerpoint Presentation Ideas Information Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Individual Cyber Security Insurance This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Security Of Data And Networks In Edge Computing Distributed Information Technology
Security Of Data And Networks In Edge Computing Distributed Information TechnologyThis slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Deliver an outstanding presentation on the topic using this Security Of Data And Networks In Edge Computing Distributed Information Technology. Dispense information and present a thorough explanation of Security Of Data And Networks In Edge Computing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Icon Of Security System Interface For Securing Information
Icon Of Security System Interface For Securing InformationIntroducing our premium set of slides with Icon Of Security System Interface For Securing Information. Elucidate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon Of Security System, Interface, Securing Information. So download instantly and tailor it with your information.
-
 Q70 Risk Management Framework For Information Security Incident Management Workflow Process
Q70 Risk Management Framework For Information Security Incident Management Workflow ProcessFollowing slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Present the topic in a bit more detail with this Q70 Risk Management Framework For Information Security Incident Management Workflow Process. Use it as a tool for discussion and navigation on Incident Occurs, Team Takes Action, Auto Alerting, Fail Over Report, Organize Team, Incident Resolution. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Q71 Risk Management Framework For Information Security Information Security Decision Framework
Q71 Risk Management Framework For Information Security Information Security Decision FrameworkPresent the topic in a bit more detail with this Q71 Risk Management Framework For Information Security Information Security Decision Framework. Use it as a tool for discussion and navigation on Key Risk Areas, Vectors, Risk Factors, Prioritization Weighting, Resource Allocation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Q72 Risk Management Framework For Information Security Information Security Risk Assessment
Q72 Risk Management Framework For Information Security Information Security Risk AssessmentThis slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver an outstanding presentation on the topic using this Q72 Risk Management Framework For Information Security Information Security Risk Assessment. Dispense information and present a thorough explanation of At Personnel Level, Facilities And Equipment, Software Application using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Healthcare Information Security Risk Acceptance And Management Plan
Healthcare Information Security Risk Acceptance And Management PlanThis slide shows information security risk treatment and acceptance plan for hospitals which can benefit them in securing their data. It contains details such as possession type, risk acceptance criteria, treating the risk, techniques and approaches for risk, residual risk acceptance measures, etc. Introducing our Healthcare Information Security Risk Acceptance And Management Plan set of slides. The topics discussed in these slides are Possession Type, Risk Acceptance Criteria, Treating The Risk. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.





