Powerpoint Templates and Google slides for Security Information
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Risk Management Framework For Information Security System Management Checklist
Risk Management Framework For Information Security System Management ChecklistFollowing slide displays system management checklist. It includes system management activities and frequency of performing them. Present the topic in a bit more detail with this Risk Management Framework For Information Security System Management Checklist. Use it as a tool for discussion and navigation on System Monitoring, Data Backup, Security Patches, Virus Scanning. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Framework For Information Security Table Of Contents
Risk Management Framework For Information Security Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Risk Management Framework For Information Security Table Of Contents. This template helps you present information on one stages. You can also present information on Incident Management, Incident Management Workflow, Incidents Logging Process, Incident Prioritization Matrix, Tool We Will Use using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Risk Management Framework For Information Security Threat Identification And Vulnerability
Risk Management Framework For Information Security Threat Identification And VulnerabilityFollowing slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an outstanding presentation on the topic using this Risk Management Framework For Information Security Threat Identification And Vulnerability. Dispense information and present a thorough explanation of Communication And Network, Database, Failure To Segment Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents Risk Management Framework For Information Security
Table Of Contents Risk Management Framework For Information SecurityIntroducing Table Of Contents Risk Management Framework For Information Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Present Scenario, Training And Budget, Dashboards, Information Security System Checklists, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Risk Management Framework Budget For Information Security Management
Cybersecurity Risk Management Framework Budget For Information Security ManagementMentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost. Introducing Cybersecurity Risk Management Framework Budget For Information Security Management to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Functional Area, Training Duration, Training Cost Per Employee, Employees To Be Trained, Total Cost Of Implementation, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Risk Management Framework Defining Categories Of Information Security
Cybersecurity Risk Management Framework Defining Categories Of Information SecurityThis slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures. Introducing Cybersecurity Risk Management Framework Defining Categories Of Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Human Error, Natural Disaster, Environmental Control Failures, Deliberate Software Attacks, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Risk Management Framework Information Security Decision Framework PRISM
Cybersecurity Risk Management Framework Information Security Decision Framework PRISMPresent the topic in a bit more detail with this Cybersecurity Risk Management Framework Information Security Decision Framework PRISM. Use it as a tool for discussion and navigation on Risk Management, Risk Rating Level, Preparedness Level, Resource Allocation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
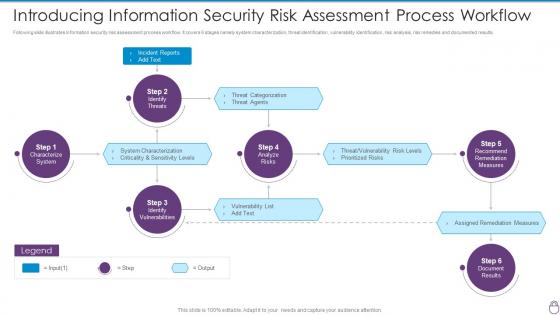 Cybersecurity Risk Management Framework Introducing Information Security Risk Assessment
Cybersecurity Risk Management Framework Introducing Information Security Risk AssessmentFollowing slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. Increase audience engagement and knowledge by dispensing information using Cybersecurity Risk Management Framework Introducing Information Security Risk Assessment. This template helps you present information on six stages. You can also present information on Incident Reports, Characterize System, Identify Vulnerabilities, Identify Threats, Analyze Risks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Risk Assessment Worksheet Cybersecurity Risk Management Framework
Information Security Risk Assessment Worksheet Cybersecurity Risk Management FrameworkMentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm. Present the topic in a bit more detail with this Information Security Risk Assessment Worksheet Cybersecurity Risk Management Framework. Use it as a tool for discussion and navigation on Threat Encountered, Vulnerability, Asset And Consequences, Risk To Firm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agenda Of Risk Based Methodology To Cyberand Information Security
Agenda Of Risk Based Methodology To Cyberand Information SecurityPresent the topic in a bit more detail with this Agenda Of Risk Based Methodology To Cyberand Information Security. Use it as a tool for discussion and navigation on Agenda. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Defining Business Priorities To Ensure Information Security Risk Based Methodology To Cyber
Defining Business Priorities To Ensure Information Security Risk Based Methodology To CyberThis slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security.Increase audience engagement and knowledge by dispensing information using Defining Business Priorities To Ensure Information Security Risk Based Methodology To Cyber This template helps you present information on three stages. You can also present information on Efficient Risk Management, Transparent Communication, Standardized Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Risk Based Methodology To Cyber and Information Security
Icons Slide For Risk Based Methodology To Cyber and Information SecurityPresenting our well crafted Icons Slide For Risk Based Methodology To Cyber and Information Security set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly
-
 Information Security Program Framework Key Components Risk Based Methodology To Cyber
Information Security Program Framework Key Components Risk Based Methodology To CyberMentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc.Introducing Information Security Program Framework Key Components Risk Based Methodology To Cyber to increase your presentation threshold. Encompassed with one stage this template is a great option to educate and entice your audience. Dispence information on Culture And Awareness, Security Risk Management, Data Security And Privacy using this template. Grab it now to reap its full benefits.
-
 Information Security Program Values To Business Risk Based Methodology To Cyber
Information Security Program Values To Business Risk Based Methodology To CyberFollowing slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management.Increase audience engagement and knowledge by dispensing information using Information Security Program Values To Business Risk Based Methodology To Cyber This template helps you present information on two stages. You can also present information on Undetectable By Current, Vulnerabilities In The Current, Threats To The Companys Environment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents For Risk Based Methodology To Cyber and Information Security
Table Of Contents For Risk Based Methodology To Cyber and Information SecurityPresent the topic in a bit more detail with this Table Of Contents For Risk Based Methodology To Cyber and Information Security Use it as a tool for discussion and navigation on Defining Business Priorities, Global Market Insights, Companies Digitization Levels This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Values To Business Introducing A Risk Based Approach To Cyber
Information Security Program Values To Business Introducing A Risk Based Approach To CyberFollowing slide displays the major program values to companys business. Values here are divided in two areas namely detection AND response and attack surface management.Deliver an outstanding presentation on the topic using this Information Security Program Values To Business Introducing A Risk Based Approach To Cyber Dispense information and present a thorough explanation of Detection And Response, Attack Surface Management, Program Will Reduce using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F28 Cybersecurity Risk Management Framework Information Security Risk Assessment
F28 Cybersecurity Risk Management Framework Information Security Risk AssessmentThis slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Present the topic in a bit more detail with this F28 Cybersecurity Risk Management Framework Information Security Risk Assessment. Use it as a tool for discussion and navigation on Valuable Information, Facilities And Equipment, Software Application, At Personnel Level. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan information security process to manage firms sensitive
Building organizational security strategy plan information security process to manage firms sensitiveThis slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Information Security Process To Manage Firms Sensitive. Use it as a tool for discussion and navigation on Information, Process, Sensitive. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity digital business management information security program values business
Cybersecurity digital business management information security program values businessFollowing slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Deliver an outstanding presentation on the topic using this Cybersecurity Digital Business Management Information Security Program Values Business. Dispense information and present a thorough explanation of Environment, Management, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Iso 27001 information security management standard ppt ideas
Iso 27001 information security management standard ppt ideasPresent the topic in a bit more detail with this ISO 27001 Information Security Management Standard Ppt Ideas. Use it as a tool for discussion and navigation on Contextual Requirements, Leadership Requirements, Planning Requirements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Iso 27001 performance indicators to measure information security controls ppt slides
Iso 27001 performance indicators to measure information security controls ppt slidesFollowing slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Deliver an outstanding presentation on the topic using this ISO 27001 Performance Indicators To Measure Information Security Controls Ppt Slides. Dispense information and present a thorough explanation of Information Security Policy, Information Security Training, Asset Inventory using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Automating threat identification security information and event management
Automating threat identification security information and event managementIncrease audience engagement and knowledge by dispensing information using Automating Threat Identification Security Information And Event Management. This template helps you present information on four stages. You can also present information on Information, Management, Compliance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Automating threat identification table of contents security information and event management
Automating threat identification table of contents security information and event managementIncrease audience engagement and knowledge by dispensing information using Automating Threat Identification Table Of Contents Security Information And Event Management. This template helps you present information on eleven stages. You can also present information on Company Overview, Management, Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security information and event management services automating threat identification
Security information and event management services automating threat identificationThis slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Increase audience engagement and knowledge by dispensing information using Security Information And Event Management Services Automating Threat Identification. This template helps you present information on eight stages. You can also present information on Data Aggregation, Data Correlation, Security Alert using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Improve it security with vulnerability information and event management logging process
Improve it security with vulnerability information and event management logging processThis slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation Introducing Improve It Security With Vulnerability Information And Event Management Logging Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Information, Management, Process, using this template. Grab it now to reap its full benefits.
-
 Agenda Of Information Security And Iso 27001
Agenda Of Information Security And Iso 27001Introducing Agenda Of Information Security And Iso 27001 to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Agenda Of Information Security And ISO 27001, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Information Security And Iso 27001
Icons Slide Information Security And Iso 27001Deliver an outstanding presentation on the topic using this Icons Slide Information Security And Iso 27001. Dispense information and present a thorough explanation of Icons using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Benefits Of Iso 27001 Certification
Information Security And Iso 27001 Benefits Of Iso 27001 CertificationThis slide displays various organizational benefits after getting ISO 27001 certification. Benefits included are information confidentiality, low operational cost, increase in the trust of valuable partners and customers and competitive advantage. Increase audience engagement and knowledge by dispensing information using Information Security And Iso 27001 Benefits Of Iso 27001 Certification. This template helps you present information on ten stages. You can also present information on Competitive, Information, Confidentiality using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security And Iso 27001 Checklist Mandatory Documents Required Iso 27001 Certification
Information Security And Iso 27001 Checklist Mandatory Documents Required Iso 27001 CertificationFollowing slide displays checklist of mandatory documents required to get ISO 27001 certification along with the status. Present the topic in a bit more detail with this Information Security And Iso 27001 Checklist Mandatory Documents Required Iso 27001 Certification. Use it as a tool for discussion and navigation on Mandatory, Documents, Required. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 Clause And Its Relationship With Isms Stages
Information Security And Iso 27001 Clause And Its Relationship With Isms StagesFollowing slide illustrates the relationship of ISO 27001 clause with ISMS stages. ISMS stages covered in the slide are design, implement, operate, monitor and improve Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 Clause And Its Relationship With Isms Stages. Dispense information and present a thorough explanation of Relationship, Leadership, Planning using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Communication Plan For Successful Implementation Of Isms
Information Security And Iso 27001 Communication Plan For Successful Implementation Of IsmsThis slide shows internal and external communication plan for successful implementation of ISMS. It includes sections namely reason for communication, initiator, recipient, frequency and medium. Present the topic in a bit more detail with this Information Security And Iso 27001 Communication Plan For Successful Implementation Of Isms. Use it as a tool for discussion and navigation on Successful, Implementation, Communication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 Current Security Management Capabilities Overview
Information Security And Iso 27001 Current Security Management Capabilities OverviewFollowing slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 Current Security Management Capabilities Overview. Dispense information and present a thorough explanation of Security, Management, Capabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Defining Risk Level And Impact Score
Information Security And Iso 27001 Defining Risk Level And Impact ScoreFollowing slide defines the incident risk level. It includes details about risk level, risk score and its description. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 Defining Risk Level And Impact Score. Dispense information and present a thorough explanation of Defining Risk Level And Impact Score using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Estimated Budget For Isms Training
Information Security And Iso 27001 Estimated Budget For Isms TrainingFollowing slide illustrates the estimate the budget for providing ISMS training. It includes information such as training title area, training duration, training cost per employee, number of employees to be trained and total training cost. Present the topic in a bit more detail with this Information Security And Iso 27001 Estimated Budget For Isms Training. Use it as a tool for discussion and navigation on Introduction, Foundation, Lead Implementer. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 Incorporation Isms Framework Into Corporate Control Processes
Information Security And Iso 27001 Incorporation Isms Framework Into Corporate Control ProcessesMentioned slide displays the incorporation of information security management system framework within the corporate control process. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 Incorporation Isms Framework Into Corporate Control Processes. Dispense information and present a thorough explanation of Framework, Corporate, Processes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Internal Isms Audit Program And Activities
Information Security And Iso 27001 Internal Isms Audit Program And ActivitiesMentioned slide portrays framework of internal ISMS audit program along with various activities. Activities covered in the slide are commissioning, initial meeting, information collection and evaluation, results and final meeting. Present the topic in a bit more detail with this Information Security And Iso 27001 Internal Isms Audit Program And Activities. Use it as a tool for discussion and navigation on Implementation, Monitoring, Improvement. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 Isms Training Program For Employees
Information Security And Iso 27001 Isms Training Program For EmployeesThis slide illustrates employee training program covering information about training title, short description, who should attend the training and duration. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 Isms Training Program For Employees. Dispense information and present a thorough explanation of Introduction, Foundation, Implementer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Iso 27001 Information Security Management Standard
Information Security And Iso 27001 Iso 27001 Information Security Management StandardPresent the topic in a bit more detail with this Information Security And Iso 27001 Iso 27001 Information Security Management Standard. Use it as a tool for discussion and navigation on Information, Security, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 It Asset Disposal Checklist
Information Security And Iso 27001 It Asset Disposal ChecklistThis slide displays IT asset disposal checklist. It includes information such as system requirement, its compliance and remarks. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 It Asset Disposal Checklist. Dispense information and present a thorough explanation of It Asset Disposal Checklist using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Mapping Of Risk Events
Information Security And Iso 27001 Mapping Of Risk EventsThis slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack. Present the topic in a bit more detail with this Information Security And Iso 27001 Mapping Of Risk Events. Use it as a tool for discussion and navigation on Mapping Of Risk Events. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 Mitigation Plan To Resolve Encountered Risk Events
Information Security And Iso 27001 Mitigation Plan To Resolve Encountered Risk EventsMentioned slide portrays mitigation plan to resolve the encountered risk events. It includes information of risk encountered, its description, threat level, mitigation plan, resources required, responsibility, resolution time and communication channel. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 Mitigation Plan To Resolve Encountered Risk Events. Dispense information and present a thorough explanation of Risk Encountered, Description, Threat Level using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Our Objectives And Goals To Grow Business
Information Security And Iso 27001 Our Objectives And Goals To Grow BusinessFollowing slide illustrates different objectives and goals of the organization to grow its business. Objectives covered are information assets security, best customer service, revenue generation and employee competency. Present the topic in a bit more detail with this Information Security And Iso 27001 Our Objectives And Goals To Grow Business. Use it as a tool for discussion and navigation on Competency, Development, Customer Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 Performance Indicators To Measure Information Security Controls
Information Security And Iso 27001 Performance Indicators To Measure Information Security ControlsFollowing slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Present the topic in a bit more detail with this Information Security And Iso 27001 Performance Indicators To Measure Information Security Controls. Use it as a tool for discussion and navigation on Performance, Indicators, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 Rasci Matrix For Assigning Responsibilities
Information Security And Iso 27001 Rasci Matrix For Assigning ResponsibilitiesMentioned slide illustrates RASCI matrix that can be used for assigning responsibilities to implement ISMS process successfully. Activities covered in the matrix are planning and analysis, designing and prototyping, coding, testing, deployment and maintenance. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 Rasci Matrix For Assigning Responsibilities. Dispense information and present a thorough explanation of RASCI Matrix For Assigning Responsibilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Risk Assessment Worksheet
Information Security And Iso 27001 Risk Assessment WorksheetFollowing slide displays information security risk assessment worksheet. It covers details about risk encountered, its description, vulnerability asset and consequences and risk to the firm. Present the topic in a bit more detail with this Information Security And Iso 27001 Risk Assessment Worksheet. Use it as a tool for discussion and navigation on Risk Assessment Worksheet. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 Security Domains That Will Be Addressed By Isms
Information Security And Iso 27001 Security Domains That Will Be Addressed By IsmsThis slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. Introducing Information Security And Iso 27001 Security Domains That Will Be Addressed By Isms to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Organization Of Information, Access Control, Cryptography, using this template. Grab it now to reap its full benefits.
-
 Information Security And Iso 27001 Statement Of Applicability
Information Security And Iso 27001 Statement Of ApplicabilityFollowing slide illustrates statement of applicability covering sections namely control reference, control, its description, status, reason for selection and associated asset. Present the topic in a bit more detail with this Information Security And Iso 27001 Statement Of Applicability. Use it as a tool for discussion and navigation on Statement Of Applicability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 Table Of Contents
Information Security And Iso 27001 Table Of ContentsDeliver an outstanding presentation on the topic using this Information Security And Iso 27001 Table Of Contents. Dispense information and present a thorough explanation of Statement Of Applicability, Successful, Implementation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Understanding The Requirement Of Interested Parties
Information Security And Iso 27001 Understanding The Requirement Of Interested Partiesdirectors and employee. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 Understanding The Requirement Of Interested Parties. Dispense information and present a thorough explanation of Organization, Assessment, Procedure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 What Will Be Our Certification Journey
Information Security And Iso 27001 What Will Be Our Certification JourneyFollowing slide portrays certification journey of the organization. Here the journey is illustrated within five stages. Increase audience engagement and knowledge by dispensing information using Information Security And Iso 27001 What Will Be Our Certification Journey. This template helps you present information on five stages. You can also present information on Recommendation, Certification, Achieved using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security And Iso 27001 Why We Need Iso 27001 Certification
Information Security And Iso 27001 Why We Need Iso 27001 CertificationMentioned slide illustrates various needs of the firm to get ISO 27001 certification. Needs covered here are low operational cost, achieve competitive advantage and comply with legal requirements. Present the topic in a bit more detail with this Information Security And Iso 27001 Why We Need Iso 27001 Certification. Use it as a tool for discussion and navigation on Achieve Competitive Advantage, Low Operational Cost, Requirements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Iso 27001 Certification Journey Information Security And Iso 27001
Iso 27001 Certification Journey Information Security And Iso 27001Deliver an outstanding presentation on the topic using this Iso 27001 Certification Journey Information Security And Iso 27001. Dispense information and present a thorough explanation of Preparation, Implementation, Improvements using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Events Reporting And Likelihood Information Security And Iso 27001
Risk Events Reporting And Likelihood Information Security And Iso 27001Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Present the topic in a bit more detail with this Risk Events Reporting And Likelihood Information Security And Iso 27001. Use it as a tool for discussion and navigation on Risk Events Reporting And Likelihood. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents For Information Security And Iso 27001 Cont
Table Of Contents For Information Security And Iso 27001 ContDeliver an outstanding presentation on the topic using this Table Of Contents For Information Security And Iso 27001 Cont. Dispense information and present a thorough explanation of Information, Requirement, Relationship using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Metrics Information Security Ppt Powerpoint Presentation Portfolio Grid Cpb
Security Metrics Information Security Ppt Powerpoint Presentation Portfolio Grid CpbPresenting our Security Metrics Information Security Ppt Powerpoint Presentation Portfolio Grid Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Security Metrics Information Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Network Security Main Principle Of Information Security
Network Security Main Principle Of Information SecurityThis slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Deliver an outstanding presentation on the topic using this Network Security Main Principle Of Information Security. Dispense information and present a thorough explanation of Main Principle Of Information Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Security Prepare Data Backup For Sensitive Information
Network Security Prepare Data Backup For Sensitive InformationThis slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Increase audience engagement and knowledge by dispensing information using Network Security Prepare Data Backup For Sensitive Information. This template helps you present information on three stages. You can also present information on Information, Protect, Manipulation, Service using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda For Information Technology Security
Agenda For Information Technology SecurityIntroducing Agenda For Information Technology Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Information, Technology, Cybersecurity, using this template. Grab it now to reap its full benefits.
-
 Elements Of Information Technology Security Application Security Information Technology Security
Elements Of Information Technology Security Application Security Information Technology SecurityThis slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. Increase audience engagement and knowledge by dispensing information using Elements Of Information Technology Security Application Security Information Technology Security. This template helps you present information on five stages. You can also present information on Session Management, Parameter Tampering, Authorization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Information Technology Security
Icons Slide For Information Technology SecurityIntroducing our well researched set of slides titled Icons Slide For Information Technology Security. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.





