Powerpoint Templates and Google slides for Secure System
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Historical Evolution Of Identity And Access Management Securing Systems With Identity
Historical Evolution Of Identity And Access Management Securing Systems With IdentityThis slide discusses the Identity and Access Management historical evolution. The purpose of this slide is to explain the historical background of IAM, including the historical roots of IAM, early IAM solutions, the role of tools, challenges with the directory, and so on. Introducing Historical Evolution Of Identity And Access Management Securing Systems With Identity to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Historical Roots Of Iam, Early Iam Solutions, Role Of Tools using this template. Grab it now to reap its full benefits.
-
 IAM Authentication And Authorization Workflow Process Securing Systems With Identity
IAM Authentication And Authorization Workflow Process Securing Systems With IdentityThis slide showcases the workflow of IAM authentication and authorization. The purpose of this slide is to explain the process, starting with user authentication and authorization, that often uses a single sign-on solution that incorporates multi-factor authentication and assigns access rights to resources. Increase audience engagement and knowledge by dispensing information using IAM Authentication And Authorization Workflow Process Securing Systems With Identity This template helps you present information on Two stages. You can also present information on Authentication, Authorization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Securing Systems With Identity And Access Management
Icons Slide For Securing Systems With Identity And Access ManagementIntroducing our well researched set of slides titled Icons Slide For Securing Systems With Identity And Access Management It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Identity And Access Management Challenges And Solutions Securing Systems With Identity
Identity And Access Management Challenges And Solutions Securing Systems With IdentityThis slide highlights the challenges associated with IAM. The purpose of this slide is to discuss the solutions provided to different challenges related to IAM. These include distributed workforce, distributed application, productive provisioning, BYOD, etc. Present the topic in a bit more detail with this Identity And Access Management Challenges And Solutions Securing Systems With Identity Use it as a tool for discussion and navigation on Challenges, Description, Solutions This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity And Access Management Introduction And Functions Securing Systems With Identity
Identity And Access Management Introduction And Functions Securing Systems With IdentityThis slide gives an overview of the Identity and Access Management process. The purpose of this slide is to explain the IAM and its functions in ensuring authentication, reporting, authorization, workflow, access management, and so on. Introducing Identity And Access Management Introduction And Functions Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Company Data And Resources, Streamline Workflows using this template. Grab it now to reap its full benefits.
-
 Identity And Access Management Process In Workplace Securing Systems With Identity
Identity And Access Management Process In Workplace Securing Systems With IdentityThis slide discusses the Identity and Access Management process in the workplace. The purpose of this slide is to highlight the various usages of IAM in the workplace these include increasing the number of applications, managing identity data, and complex access scenarios. Increase audience engagement and knowledge by dispensing information using Identity And Access Management Process In Workplace Securing Systems With Identity This template helps you present information on Three stages. You can also present information on Increasing Number Of Applications, Managing Identity Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Identity And Access Management Technologies And Tools Securing Systems With Identity
Identity And Access Management Technologies And Tools Securing Systems With IdentityThis slide discusses the tools and technologies used in the Identity and Access Management process. The purpose of this slide is to highlight the various tools, which are security assertion markup language, open ID connect, and a system for cross-domain identity management. Present the topic in a bit more detail with this Identity And Access Management Technologies And Tools Securing Systems With Identity Use it as a tool for discussion and navigation on Saml, Oidc, Scim This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity And Access Management Training Schedule For Staff Securing Systems With Identity
Identity And Access Management Training Schedule For Staff Securing Systems With IdentityThis slide represents the training schedule for staff in the Identity and Access Management. The purpose of this slide is to manage and monitor IAM training procedures. It includes the time slots for training, the total days of training, and the modules to be covered in the training. Deliver an outstanding presentation on the topic using this Identity And Access Management Training Schedule For Staff Securing Systems With Identity Dispense information and present a thorough explanation of Policies And Procedures, Infrastructure And Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identity And Access Management Working Functions Securing Systems With Identity
Identity And Access Management Working Functions Securing Systems With IdentityThis slide discusses the working process of Identity and Access Management . The purpose of this slide is to explain the workflow of the IAM this includes identity management that validates login attempts and access management that manages the entitys access. Introducing Identity And Access Management Working Functions Securing Systems With Identity to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Identity Management, Access Management using this template. Grab it now to reap its full benefits.
-
 Impact Of Identity And Access Management On Business Securing Systems With Identity
Impact Of Identity And Access Management On Business Securing Systems With IdentityThis slide represents the Identity and Access Management impact on organization. The purpose of this slide is to highlight the impact associated with IAM for business which are enhances security, regularity compliance and so on. Deliver an outstanding presentation on the topic using this Impact Of Identity And Access Management On Business Securing Systems With Identity Dispense information and present a thorough explanation of Enhanced Security, Cost Savings using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Parameters Of IAM Implementation Process Securing Systems With Identity
Key Parameters Of IAM Implementation Process Securing Systems With IdentityThis slide highlights the key function of the Identity and Access Management implementation process. The purpose of this slide is to explain the various parameters of IAM implementation these include identity lifecycle management, access control, authentication, and so on. Introducing Key Parameters Of IAM Implementation Process Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Authentication, Authorization, Identity Governance using this template. Grab it now to reap its full benefits.
-
 Major Focus Areas Of Identity And Access Management Securing Systems With Identity
Major Focus Areas Of Identity And Access Management Securing Systems With IdentityThis slide discusses the Identity and Access Management focus area. The purpose of this slide is to explain the focus area of IAM these include access management, privilege management, and identity governance. Increase audience engagement and knowledge by dispensing information using Major Focus Areas Of Identity And Access Management Securing Systems With Identity This template helps you present information on Three stages. You can also present information on Access Management, Privilege Management, Identity Governance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Need For The Identity And Access Management Securing Systems With Identity
Need For The Identity And Access Management Securing Systems With IdentityThis slide discusses the requirement for Identity and Access Management process. The purpose of this slide is to highlight the needs these include secure user access, strong authentication, IAM solutions, IAM tasks, an evolving IT environment, etc. Present the topic in a bit more detail with this Need For The Identity And Access Management Securing Systems With Identity Use it as a tool for discussion and navigation on Secure User Access, Strong Authentication This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Associated With Identity And Access Management Process Securing Systems With Identity
Risk Associated With Identity And Access Management Process Securing Systems With IdentityThis slide outlines the potential hazards linked to the Identity and Access Management process. The purpose of this slide is to discuss the risks these include incorrectly defined roles and attributes, infrequent audits, and complex implementations. Introducing Risk Associated With Identity And Access Management Process Securing Systems With Identity to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Roles And Attributes, Infrequent Audits, Complex Implementations using this template. Grab it now to reap its full benefits.
-
 Roadmap For Identity And Access Management Implementation Securing Systems With Identity
Roadmap For Identity And Access Management Implementation Securing Systems With IdentityThis slide highlights the project roadmap to implement the Identity and Access Management process. The purpose of this slide is to showcase the different phases of the IAM implementation plan, such as implementing emerging IAM technologies, BYOI adoption, etc. Increase audience engagement and knowledge by dispensing information using Roadmap For Identity And Access Management Implementation Securing Systems With Identity This template helps you present information on Four stages. You can also present information on Iam Technologies, Byoi Adoption, Testing And Security Assurance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Role Of Identity And Access Management In Data Security Securing Systems With Identity
Role Of Identity And Access Management In Data Security Securing Systems With IdentityThis slide discusses the Identity and Access Management importance in data security. The purpose of this slide is to highlight the importance, including protecting business data, addressing new challenges, beyond perimeter security, combatting compromised credentials, and so on. Deliver an outstanding presentation on the topic using this Role Of Identity And Access Management In Data Security Securing Systems With Identity Dispense information and present a thorough explanation of Protecting Business Data, Combatting Compromised Credentials using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Securing Systems With Identity And Access Management Table Of Content
Securing Systems With Identity And Access Management Table Of ContentIntroducing Securing Systems With Identity And Access Management Table Of Content to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Introduction And Functions, Biometric Authentication using this template. Grab it now to reap its full benefits.
-
 Steps To Implement Digital Authentication With IAM Securing Systems With Identity
Steps To Implement Digital Authentication With IAM Securing Systems With IdentityThis slide discusses the IAM implementing digital authentication. The purpose of this slide is to highlight the various types of digital authentication done by IAM, which are unique passwords, pre-shared keys, Behavioral authentication, and biometrics. Increase audience engagement and knowledge by dispensing information using Steps To Implement Digital Authentication With IAM Securing Systems With Identity This template helps you present information on Five stages. You can also present information on Unique Passwords, Biometrics using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Implement Identity And Access Management In Enterprises Securing Systems With Identity
Steps To Implement Identity And Access Management In Enterprises Securing Systems With IdentityThis slide discusses the Identity and Access Management implementing process in enterprises. The purpose of this slide is to highlight the implementation process, including usage assessment, environment understanding, key IAM considerations, and so on. Introducing Steps To Implement Identity And Access Management In Enterprises Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Usage Assessment, Environment Understanding using this template. Grab it now to reap its full benefits.
-
 Steps To Implement Identity And Access Management Securing Systems With Identity
Steps To Implement Identity And Access Management Securing Systems With IdentityThis slide discusses the Identity and Access Management implementing program. The purpose of this slide is to highlight the implementation process of IAM, including scope identification, evaluating the right IAM approach, finding the best solution, and so on. Increase audience engagement and knowledge by dispensing information using Steps To Implement Identity And Access Management Securing Systems With Identity This template helps you present information on Six stages. You can also present information on Scope Identification, Define A Strategy, Assess Cost Factors using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Streamlining Identity Management Process Within IAM Securing Systems With Identity
Streamlining Identity Management Process Within IAM Securing Systems With IdentityThis slide discusses the identity management of the Identity and Access Management process. The purpose of this slide is to explain identity management that relies on a combination of process, organizational structure, and enabling technologies. Introducing Streamlining Identity Management Process Within IAM Securing Systems With Identity to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Organization Structure, Processes, Technology using this template. Grab it now to reap its full benefits.
-
 Table Of Content For Securing Systems With Identity And Access Management
Table Of Content For Securing Systems With Identity And Access ManagementIncrease audience engagement and knowledge by dispensing information using Table Of Content For Securing Systems With Identity And Access Management This template helps you present information on One stages. You can also present information on Iam Overview, Training And Budget using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Timeline To Implement Identity And Access Management Plan Securing Systems With Identity
Timeline To Implement Identity And Access Management Plan Securing Systems With IdentityThis slide shows the timeline for implementing the Identity and Access Management plan. The key steps include defining the project objective, identifying key stakeholders, determining compliance, integrating IAM with the existing system, etc. Introducing Timeline To Implement Identity And Access Management Plan Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Applications And Data, Public Cloud Platforms using this template. Grab it now to reap its full benefits.
-
 Traditional Vs Modern IAM Security Landscape Securing Systems With Identity
Traditional Vs Modern IAM Security Landscape Securing Systems With IdentityThis slide compares traditional vs. modern Identity and Access Management security landscape. The purpose of this slide is to highlight the difference between conventional and contemporary Identity and Access Management systems. Increase audience engagement and knowledge by dispensing information using Traditional Vs Modern IAM Security Landscape Securing Systems With Identity This template helps you present information on Two stages. You can also present information on Authorization, Central User Repository, User Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Understanding Of Identity And Access Management Securing Systems With Identity
Understanding Of Identity And Access Management Securing Systems With IdentityThis slide discusses the concepts of the Identity and Access Management process. The purpose of this slide is to explain the key components of IAM, including authentication, authorization, user management, and central user repository. Introducing Understanding Of Identity And Access Management Securing Systems With Identity to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Access Management, Identity Mgmt using this template. Grab it now to reap its full benefits.
-
 Uniting Identity And Access Management Processes Securing Systems With Identity
Uniting Identity And Access Management Processes Securing Systems With IdentityThis slide discusses the Identity and Access Management uniting process. The purpose of this slide is to explain the Identity and Access Management unit, which involves users, access management, resources, identity management, and ID sources. Increase audience engagement and knowledge by dispensing information using Uniting Identity And Access Management Processes Securing Systems With Identity This template helps you present information on Four stages. You can also present information on Key Takeaways, Iam Market Size using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Use Cases Of Identity And Access Management Securing Systems With Identity
Use Cases Of Identity And Access Management Securing Systems With IdentityThis slide highlights the Identity and Access Management process use cases. The purpose of this slide is to discuss the cases these include IAM for zero trust at better.com and IAM for streamlined onboarding at hearst. Introducing Use Cases Of Identity And Access Management Securing Systems With Identity to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Loss Prevention, Compromising Security using this template. Grab it now to reap its full benefits.
-
 Various Types Of Biometric Authentication With IAM Securing Systems With Identity
Various Types Of Biometric Authentication With IAM Securing Systems With IdentityIncrease audience engagement and knowledge by dispensing information using Various Types Of Biometric Authentication With IAM Securing Systems With Identity This template helps you present information on One stages. You can also present information on Iris Recognition, Dna Matching, Privacy Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices For Secure Embedded Systems Mastering Embedded Systems Technology
Best Practices For Secure Embedded Systems Mastering Embedded Systems TechnologyThis slide showcases the best methods for developing secure embedded systems. The purpose of this slide is to showcase the best practices for building secure embedded systems, and these are securing boot, securing enclaves with Trusted Execution Environments TEE, implementing FOTA, etc. Present the topic in a bit more detail with this Best Practices For Secure Embedded Systems Mastering Embedded Systems Technology. Use it as a tool for discussion and navigation on Operating Systems In Market, Consumer Electronics, Industrial, Agriculture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Challenges In Maintaining Security Of Embedded Systems Mastering Embedded Systems Technology
Challenges In Maintaining Security Of Embedded Systems Mastering Embedded Systems TechnologyThis slide showcases the various security challenges and mitigation methods for embedded systems. The purpose of this slide is to represent the challenges in maintaining the security of embedded systems, such as irregular security updates, attack replication, dependability, and so on. Deliver an outstanding presentation on the topic using this Challenges In Maintaining Security Of Embedded Systems Mastering Embedded Systems Technology. Dispense information and present a thorough explanation of Irregular Security Updates, Dependability, Industrial Protocols, Remote Deployment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Develop Secure Embedded Systems Mastering Embedded Systems Technology
Checklist To Develop Secure Embedded Systems Mastering Embedded Systems TechnologyThis slide outlines the checklist for building secure embedded systems. The purpose of this slide is to showcase the various tasks that need to be performed to develop secure embedded systems, required actions, responsible person, and status. Present the topic in a bit more detail with this Checklist To Develop Secure Embedded Systems Mastering Embedded Systems Technology. Use it as a tool for discussion and navigation on Operating System Selection, Processor And Peripherals, Prototype Development, System Architecture Design. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Address Verification System To Reduce Payment Fraud Implementing E Commerce Security Measures
Address Verification System To Reduce Payment Fraud Implementing E Commerce Security MeasuresThe slide illustrates address verification process to prevent payment fraud along with its key impacts. The process include buyer, billing address, comparing address, and return code. Introducing Address Verification System To Reduce Payment Fraud Implementing E Commerce Security Measures to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Billing Address, Cardholder Records, Potential Impact, using this template. Grab it now to reap its full benefits.
-
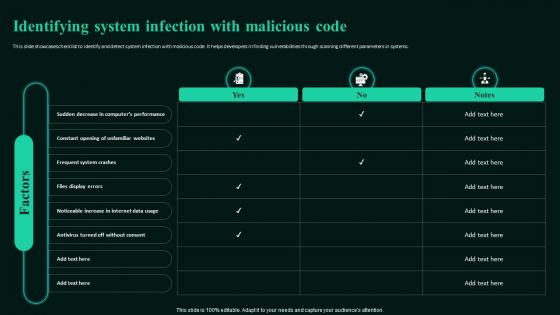 Identifying System Infection With Malicious Building Next Generation Endpoint Security Cybersecurity SS
Identifying System Infection With Malicious Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases checklist to identify and detect system infection with malicious code. It helps developers in finding vulnerabilities through scanning different parameters in systems.Deliver an outstanding presentation on the topic using this Identifying System Infection With Malicious Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Frequent System Crashes, Files Display Errors, Unfamiliar Websites using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IOT Security System Tools For Data Protection
IOT Security System Tools For Data ProtectionThis slide showcases methods to secure IoT security systems. It includes digital certificates, network and application programming interface security. Presenting our set of slides with name IOT Security System Tools For Data Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Security, API Security, Digital Certificates.
-
 Security Icon To Protect Wireless Lan System
Security Icon To Protect Wireless Lan SystemIntroducing our premium set of slides with Security Icon To Protect Wireless Lan System Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Icon To Protect, Wireless LAN System So download instantly and tailor it with your information.
-
 Wireless Lan Security Policy Management System Framework
Wireless Lan Security Policy Management System FrameworkThis slide represents framework that assists organizations that relies on wireless network to enhance LAN security compliance and incident response. It includes various components such as global policy server, WLAN policy zone, access point, etc. Presenting our well structured Wireless Lan Security Policy Management System Framework The topics discussed in this slide are Local Role Server, Mobile Hast, Mobile Host, Global Policy ServerThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Best Practices For Building Physical Security System
Best Practices For Building Physical Security SystemThis slide showcases the effective approaches employed for developing physical security system which helps an organization to avoid potential crimes by adding sense of heightened awareness. It include details such as create secure facility,secure business equipment,etc. Presenting our set of slides with Best Practices For Building Physical Security System. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Create Secure Facility,Secure Business Equipment,Avoid Thefts.
-
 Comparative Analysis Of Building Security System Software
Comparative Analysis Of Building Security System SoftwareThis slide showcases the comparison between tools employed for developing effective security system which helps an organization to carefully select the best tool that reduce operational costs. It include details such as price month,ratings,integrations,scalability,etc. Introducing our Comparative Analysis Of Building Security System Software set of slides. The topics discussed in these slides are Basis Comparison,Rating,Integrations. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Essential Types Of Building Security System
Essential Types Of Building Security SystemThis slide showcases the major types of building security system which helps an organization to develop effective,secure and safer environment and identify potential criminals. It include details such as alarm,cctv,intercom and access control systems. Presenting our set of slides with Essential Types Of Building Security System. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Alarm Systems,CCTV Systems,Intercom Systems.
-
 How To Build Organizational Network Security System
How To Build Organizational Network Security SystemThis slide showcases the effective guidelines for creating organizational network security system which helps them to ensure continuity of operations and protect sensitive enterprise data. It include details such as run regular audit networks,develop firewalls,etc. Introducing our premium set of slides with How To Build Organizational Network Security System. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Provide Information,Develop Firewalls,Employ Multi Factor Authentication. So download instantly and tailor it with your information.
-
 Key Components Required For Building Security System
Key Components Required For Building Security SystemThis slide showcases the key elements required for developing effective security system which helps an organization to tackle issues in most efficient manner by providing quick response time. It include details such as surveillance,deterrence and response. Presenting our set of slides with Key Components Required For Building Security System. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Surveillance,Deterrence,Environmental Designs.
-
 Steps To Build Physical Security System Installation
Steps To Build Physical Security System InstallationThis slide showcases the effective guidelines for developing physical security system installation which helps an organization to protect and manage daily AND routine business activities. It include details such as planning,designing and implementing. Introducing our premium set of slides with Steps To Build Physical Security System Installation. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Planning,Designing,Implementing. So download instantly and tailor it with your information.
-
 Monitor Security Configuration Management System
Monitor Security Configuration Management SystemThis slide depicts the security configuration management flow. Its aim is to manage the configuration system efficiently. This slide includes publisher, automatic checks, configuration guide, rule implementation, administrator monitoring, etc. Presenting our well structured Monitor Security Configuration Management System. The topics discussed in this slide are Administrator, System Testing, Legend, Implement Rules. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Steps In Security Configuration Management System
Steps In Security Configuration Management SystemThis slide depicts the security configuration management steps. Its aim Is to discover assets, solve problem, initiate baseline and make changes in it. This slide includes discovery of asset, baseline device, solve problem and make changes. Introducing our premium set of slides with name Steps In Security Configuration Management System. Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Discover Asset, Initiate Baseline, Make Changes, Solve Problem. So download instantly and tailor it with your information.
-
 A211 ChatGPT Next Generation AI Integrating ChatGPT With Other Systems Security ChatGPT SS V
A211 ChatGPT Next Generation AI Integrating ChatGPT With Other Systems Security ChatGPT SS VThis slide provides information regarding the integration of ChatGPT with other systems for managing security and compliance in terms of fraud detection, handling cybersecurity, risk assessment and compliance monitoring. Present the topic in a bit more detail with this A211 ChatGPT Next Generation AI Integrating ChatGPT With Other Systems Security ChatGPT SS V. Use it as a tool for discussion and navigation on Fraud Detection, Compliance Tracking, Cybersecurity, Risk Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Suspicious Activities And Prevent Threats, Protect Organizations Networks, Filter Out Malicious Activities, Security Devices Or Controls, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing our well researched set of slides titled Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table Of Contents For Implementing Intrusion Prevention System For Effective Network Security
Table Of Contents For Implementing Intrusion Prevention System For Effective Network SecurityIntroducing Table Of Contents For Implementing Intrusion Prevention System For Effective Network Security to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Issues Experienced Due Inefficient Network Security, Impact On Organizational Operations, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Budget Plan, Impact Assessment, Dashboards, Case Study Analysis, using this template. Grab it now to reap its full benefits.
-
 Types Of Effective Web Filtering To Secure System
Types Of Effective Web Filtering To Secure SystemThis slide showcases various types of web filtering firewall system. Its objective is to understand the importance of firewall system to maintain secure environment. This slide includes packet, inspection, proxy, application and next generation firewall. Presenting our set of slides with name Types Of Effective Web Filtering To Secure System. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Packet Filtering, Stateful Inspection, Proxy, Application Level .
-
 Ppts information security system diagram powerpoint topics
Ppts information security system diagram powerpoint topicsPresenting ppts information security system diagram powerpoint topics. This is a information security system diagram powerpoint topics. This is a one stage process. The stages in this process are information, network security, access control, security management, physical security, business continuity and dr planning, operations security, application system security.
-
 Security and auditing systems powerpoint slides
Security and auditing systems powerpoint slidesPresenting security and auditing systems powerpoint slides. This is a security and auditing systems powerpoint slides. This is a five stage process. The stages in this process are risk assessment and periodization, risk register and management plan, measuring and monitoring, feedback evaluation and improvement, requirements identification and updates, policies objectives targets goals, quality management.
-
 Security examination trading system diagram layout ppt gallery
Security examination trading system diagram layout ppt galleryPresenting security examination trading system diagram layout ppt gallery. This is a security examination trading system diagram layout ppt gallery. This is a six stage process. The stages in this process are executions, commercial bank, customer service assistance, bank office, custodian.
-
 Operating system app security template powerpoint presentation templates
Operating system app security template powerpoint presentation templatesPresenting operating system app security template powerpoint presentation templates. Presenting operating system app security template powerpoint presentation templates. This is a operating system app security template powerpoint presentation templates. This is a four stage process. The stages in this process are web server, endpoint security, content security, database.
-
 Security administration system template ppt samples
Security administration system template ppt samplesPresenting security administration system template ppt samples. This is a security administration system template ppt samples. This is four stage process. The stages in this process are safety promotion, safety policy, safety manager, hr coordinator.
-
 Certified information systems security professional cissp examination details
Certified information systems security professional cissp examination detailsThis slide covers information about CISSP Examination such as weight of each domain in exams, prep courses details, qualification details etc. Deliver an outstanding presentation on the topic using this Certified Information Systems Security Professional CISSP Examination Details. Dispense information and present a thorough explanation of Asset Security, Security Operations, Communications And Network Security, Security Engineering, Security Assessment And Testing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Certified information systems security professional cissp salary and job details
Certified information systems security professional cissp salary and job detailsThis slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Deliver an outstanding presentation on the topic using this Certified Information Systems Security Professional CISSP Salary And Job Details. Dispense information and present a thorough explanation of Information Security Analyst, Information Security Manager, Chief Information Security Officer, Security Architect, Security Engineer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Assessment Dashboard For Securing Supply Chain System
Risk Assessment Dashboard For Securing Supply Chain SystemThis slide demonstrates risk assessment matrix for improving the efficiency of industrial supply chain system. It includes supplier risks, service type and service health etc. Presenting our well structured Risk Assessment Dashboard For Securing Supply Chain System. The topics discussed in this slide are Service Health, Service Type, Supplier Risk. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Paid Subscribers By Channel Home Security Systems Company Profile
Paid Subscribers By Channel Home Security Systems Company ProfileThis slide highlights the security company paid subscribers count by channel in bar graph format. It includes data of dealer or retailer and direct channel from 2018 to 2022. Deliver an outstanding presentation on the topic using this Paid Subscribers By Channel Home Security Systems Company Profile . Dispense information and present a thorough explanation of Paid Subscribers By Channel using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Revenue And Profit Of Security Company Home Security Systems Company Profile
Revenue And Profit Of Security Company Home Security Systems Company ProfileThis slide highlights the revenue and profit of security company in bar graph format which includes data from last 5 years from financial year 2018 to 2022. Present the topic in a bit more detail with this Revenue And Profit Of Security Company Home Security Systems Company Profile . Use it as a tool for discussion and navigation on Revenue And Profit Of Security Company. This template is free to edit as deemed fit for your organization. Therefore download it now.





