Powerpoint Templates and Google slides for Secure System
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Home Security Surveillance System In Powerpoint And Google Slides Cpb
Home Security Surveillance System In Powerpoint And Google Slides CpbPresenting our Home Security Surveillance System In Powerpoint And Google Slides Cpb. PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Home Security Surveillance System. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Security System Used In Smart IoT Remote Asset Monitoring And Management IoT SS
Security System Used In Smart IoT Remote Asset Monitoring And Management IoT SSThis slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities. Increase audience engagement and knowledge by dispensing information using Security System Used In Smart IoT Remote Asset Monitoring And Management IoT SS. This template helps you present information on three stages. You can also present information on Components, Features, Detection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Food Security System In Powerpoint And Google Slides Cpb
Food Security System In Powerpoint And Google Slides CpbPresenting Food Security System In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Five RMD Holding. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Integrating Security Principle With Dynamic System Development Method
Integrating Security Principle With Dynamic System Development MethodThis slide showcases incorporation of software security principles in DSDM model which helps in improving degree of project agility. It provides information regarding execution, functional model iteration, security design and security functional modulation. Introducing our Integrating Security Principle With Dynamic System Development Method set of slides. The topics discussed in these slides are Business Study, Integrating Security, Dynamic System Development. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Camera System Business In Powerpoint And Google Slides Cpb
Security Camera System Business In Powerpoint And Google Slides CpbPresenting Security Camera System Business In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Camera System Business. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Ensuring Security Compliance For Banking Systems With Patch Management Process
Ensuring Security Compliance For Banking Systems With Patch Management ProcessFollowing slide showcases process of patch management to ensure security of banking systems. The purpose of this slide is to outline a series of steps to align with industry regulations while maintaining the security and stability of financial operations. It includes steps such as regulatory framework, etc.Presenting our set of slides with Ensuring Security Compliance For Banking Systems With Patch Management Process. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Vulnerability Management, Compliance Validation, Documentation Improvement
-
 Security Patch Management Process For Healthcare IT Systems
Security Patch Management Process For Healthcare IT SystemsFollowing slide showcases the healthcare industry security patch management process. The purpose of this slide is to help healthcare organizations in ensuring that their IT systems are patched safely and effectively. It includes steps such as define, identify and prioritize, etc.Presenting our set of slides with Security Patch Management Process For Healthcare IT Systems. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Roles Responsibilities, Ensure Introduced, Deployment Depends.
-
 Information Security Management System Workflow
Information Security Management System WorkflowThis slide represents the workflow that helps businesses to implement effective information security management system in organization. This workflow includes major phases , tasks and users responsible for each activity. Introducing our premium set of slides with Information Security Management System Workflow. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Develop ISMS, Document Policy Freme Work, Designate Internal Auditor. So download instantly and tailor it with your information.
-
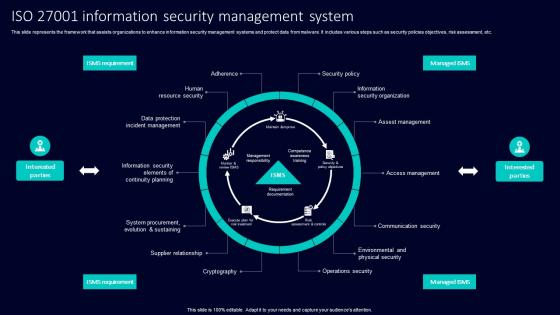 Iso 27001 Information Security Management System
Iso 27001 Information Security Management SystemThis slide represents the framework that assists organizations to enhance information security management systems and protect data from malware. It includes various steps such as security policies objectives, risk assessment, etc. Presenting our set of slides with Iso 27001 Information Security Management System. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Adherence, Security Policy, Assest Management.
-
 Roadmap To Implement Information Security Management System In Organization
Roadmap To Implement Information Security Management System In OrganizationThis slide represents roadmap that helps organizations implement system for information security management systems to protect sensitive data. It includes steps such as defining scope and objectives, identifying assets, recognizing risk, etc. Introducing our premium set of slides with Roadmap To Implement Information Security Management System In Organization. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Recognize Risk, Make Improvement, Identify Mitigation Measures. So download instantly and tailor it with your information.
-
 Discovery Identifying Potential Vulnerabilities In System Hands On Blockchain Security Risk BCT SS V
Discovery Identifying Potential Vulnerabilities In System Hands On Blockchain Security Risk BCT SS VThe following slide showcases key phases of penetration testing to identify potential flaws and malware. It includes elements of discovery phase such as architecture, compliance readiness, readiness analysis, etc. Introducing Discovery Identifying Potential Vulnerabilities In System Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Architecture Of Blockchain, Compliance Readiness, Readiness Analysis, using this template. Grab it now to reap its full benefits.
-
 Network Security Management System Icon
Network Security Management System IconPresenting our set of slides with Network Security Management System Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Security Management, System Icon.
-
 Parameters To Secure Network Security Management System
Parameters To Secure Network Security Management SystemThis slide showcases the safe security management system parameters which helps an organization to protect critical data and prevents unauthorized access to applications. It include details such as control removable media, smartly surf webpages, etc. Presenting our set of slides with Parameters To Secure Network Security Management System. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Control Removable Media, Smartly Surf Webpages, Ensure Time Backups.
-
 MAGAL Security Systems Stock In Powerpoint And Google Slides Cpb
MAGAL Security Systems Stock In Powerpoint And Google Slides CpbPresenting MAGAL Security Systems Stock In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like MAGAL Security Systems Stock. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Implement Security Systems Icon Using Operating System
Implement Security Systems Icon Using Operating SystemIntroducing our premium set of slides with Implement Security Systems Icon Using Operating System. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Implement Security, Systems Icon, Using Operating System. So download instantly and tailor it with your information.
-
 Elements Of Systems Applications And Products Cyber Security
Elements Of Systems Applications And Products Cyber SecurityThis slide depicts the components of SAP cybersecurity. The purpose of this template is to help understand the areas of business networks that can be safeguarded with the help of SAP cybersecurity elements. It includes data base security, infrastructure security, etc. Presenting our set of slides with Elements Of Systems Applications And Products Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Database Security, Operating System Security, Network Security, Infrastructure Security.
-
 Use Cases Of System Application And Product Cyber Security
Use Cases Of System Application And Product Cyber SecurityThis template depicts the applications of SAP cyber security. The purpose of this slide is to help the business leverage SAP cybersecurity to improve its internal network safety. It includes use cases such as ensuring data integrity, identification of unauthorized access, etc. Presenting our well structured Use Cases Of System Application And Product Cyber Security. The topics discussed in this slide are Prevent Exploitation And Fraud, Ensuring Data Integrity, Continuous Results. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Firewall Network Security Overview Of Next Generation Firewall NGFW Systems
Firewall Network Security Overview Of Next Generation Firewall NGFW SystemsThis slide gives an overview of the Next Generation Firewall security system, including its architecture and features. The purpose of this slide is to introduce the Next Generation Firewall protection mechanism, covering its benefits such as robust threat prevention, flexible deployment, and so on. Deliver an outstanding presentation on the topic using this Firewall Network Security Overview Of Next Generation Firewall NGFW Systems Dispense information and present a thorough explanation of Architecture, Internet, Dynamic Packet Filtering using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Pros And Cons Of Cloud Firewall Systems
Firewall Network Security Pros And Cons Of Cloud Firewall SystemsThis slide highlights the advantages and disadvantages of cloud-based firewall systems. The purpose of this slide is to showcase the pros and cons of cloud firewalls, and the pros include deployment and scalability, access and identity management, updates, and availability. Introducing Firewall Network Security Pros And Cons Of Cloud Firewall Systems to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Pros, Cons, Speed, Embedded Malware using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Types Of Cloud Based Firewall Systems
Firewall Network Security Types Of Cloud Based Firewall SystemsThis slide describes the different types of cloud-based firewall systems. The purpose of this slide is to give an overview of different kinds of cloud-based firewall systems, such as Next Generation firewalls, Security as a Service, and Firewall as a Service. Deliver an outstanding presentation on the topic using this Firewall Network Security Types Of Cloud Based Firewall Systems Dispense information and present a thorough explanation of Next-Generation Firewalls, Saas Firewalls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Understanding Cloud Firewall Security Systems
Firewall Network Security Understanding Cloud Firewall Security SystemsThis slide gives an overview of cloud-based firewall security systems, including their importance, types, benefits, and working features. The purpose of this slide is to showcase the different aspects of cloud-based firewalls. The main types include Next Generation Firewall and SaaS firewalls. Introducing Firewall Network Security Understanding Cloud Firewall Security Systems to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Benefits, Working Functions, Types using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Understanding Proxy Firewall Protection System
Firewall Network Security Understanding Proxy Firewall Protection SystemThis slide outlines the overview of the proxy firewall system. The purpose of this slide is to introduce the proxy firewall, including its functions, limitations, and benefits, such as security, logging capabilities, threat assessment, control, and granularity. Deliver an outstanding presentation on the topic using this Firewall Network Security Understanding Proxy Firewall Protection System Dispense information and present a thorough explanation of Internet, Proxy Firewall, Internet Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Unified Threat Management UTM Firewall System Overview
Firewall Network Security Unified Threat Management UTM Firewall System OverviewThis slide provides an introduction to the Unified Threat Management firewall system. The purpose of this slide is to showcase the features, benefits, and inspection methods of Unified Threat Management firewall systems, such as flow-based and proxy-based inspection. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Understanding Critical Risks Of Firewall Absence This template helps you present information on Three stages. You can also present information on Content Filtering, Faster Security, Flexibility And Adaptability using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Working Functions Of Cloud Firewall System
Firewall Network Security Working Functions Of Cloud Firewall SystemThis slide talks about the different working functions that help cloud-based firewall systems to protect the user network and devices from malicious activities. The purpose of this slide is to showcase the various tasks of cloud firewalls, including packet filtering, stateful inspection, and proxy service. Introducing Firewall Network Security Working Functions Of Cloud Firewall System to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Stateful Inspection, Proxy Service, Packet Filtering using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Working Of Next Generation Firewall Systems
Firewall Network Security Working Of Next Generation Firewall SystemsThis slide gives architectures of traditional firewalls and Next Generation Firewall systems, including their working. The purpose of this slide is to showcase how Next Generation Firewall works in comparison with conventional firewall systems. Introducing Firewall Network Security Working Of Next Generation Firewall Systems to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Malicious Traffic, Reaches A Network, Security Posture using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Working Process Of Proxy Firewall System
Firewall Network Security Working Process Of Proxy Firewall SystemThis slide represents a proxy firewall systems working process and user query flow. The purpose of this slide is to showcase how a proxy firewall works to safeguard network data from unethical activities. The components include a proxy server, proxy client, internet, and real server. Present the topic in a bit more detail with this Firewall Network Security Working Process Of Proxy Firewall System Use it as a tool for discussion and navigation on Working, Technologies Used, Firewall Architecture This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Architecture Of Web Application Firewall System
Firewall Network Security Architecture Of Web Application Firewall SystemThis slide represents the framework of the web application firewall. The purpose of this slide is to showcase the WAF architecture and its various parts such as core infrastructure, visibility, compliance, active threat monitoring, availability and support, and policy management. Present the topic in a bit more detail with this Firewall Network Security Architecture Of Web Application Firewall System Use it as a tool for discussion and navigation on Policy Management, Malicious Attacks This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Benefits And Limitations Of Proxy Firewall Systems
Firewall Network Security Benefits And Limitations Of Proxy Firewall SystemsThis slide outlines the advantages and disadvantages of proxy firewall systems. The purpose of this slide is to highlight the various pros and cons of proxy firewalls, and the pros include security, logging capabilities, control, and granularity. Deliver an outstanding presentation on the topic using this Firewall Network Security Benefits And Limitations Of Proxy Firewall Systems Dispense information and present a thorough explanation of Logging Capabilities, Single Point Of Failure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Benefits Of Next Generation Firewall Protection System
Firewall Network Security Benefits Of Next Generation Firewall Protection SystemThis slide highlights the advantages of Next Generation Firewalls for network protection. The purpose of this slide is to showcase the different benefits of next-generation firewall, such as robust threat prevention, flexible deployment, app, and identity-based checking and control, etc. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Benefits Of Next Generation Firewall Protection System This template helps you present information on Four stages. You can also present information on Firewall Network Security Benefits Of Next Generation Firewall Protection System using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Criteria To Compare Firewall Management Systems
Firewall Network Security Criteria To Compare Firewall Management SystemsThis slide describes some key features to look for in a firewall management system. The purpose of this slide is to showcase some of the criteria to compare a firewall management system, including ease of use, efficiency, built-in integrations, and scalability. Introducing Firewall Network Security Criteria To Compare Firewall Management Systems to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Ease Of Use, Efficiency, Scalability using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Deployment Methods Of Firewall Security System
Firewall Network Security Deployment Methods Of Firewall Security SystemThis slide represents the key applications of firewall security systems. The purpose of this slide is to showcase the different deployment options of firewall security systems, such as software-based applications, hardware-based applications, and cloud-based applications. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Deployment Methods Of Firewall Security System This template helps you present information on Three stages. You can also present information on Software Based Applications, Hardware Based Applications, Cloud Based Applications using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Features Of Distributed Firewall Management System
Firewall Network Security Features Of Distributed Firewall Management SystemThis slide represents the key characteristics of distributed firewall management system. The purpose of this slide is to showcase the different features of distributed firewalls, such as central management systems, security policy distribution, enhanced access control, and host-end execution. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Features Of Distributed Firewall Management System This template helps you present information on Four stages. You can also present information on Access Control, Concurrency Processing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Importance And Benefits Of Distributed Firewall Management System
Firewall Network Security Importance And Benefits Of Distributed Firewall Management SystemThis slide outlines the importance of distributed firewall management system. It also includes the various advantages of distributed firewalls, including security from insider threats, intrusion detection, service exposure, and port scanning. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Importance And Benefits Of Distributed Firewall Management System This template helps you present information on Three stages. You can also present information on Network Address Translation, Virtual Private Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
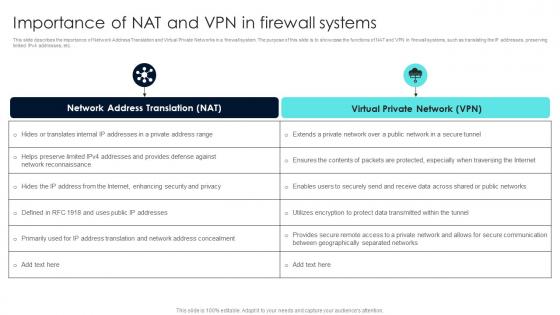 Firewall Network Security Importance Of NAT And VPN In Firewall Systems
Firewall Network Security Importance Of NAT And VPN In Firewall SystemsThis slide describes the importance of Network Address Translation and Virtual Private Networks in a firewall system. The purpose of this slide is to showcase the functions of NAT and VPN in firewall systems, such as translating the IP addresses, preserving limited IPv4 addresses, etc. Present the topic in a bit more detail with this Firewall Network Security Importance Of NAT And VPN In Firewall Systems Use it as a tool for discussion and navigation on Consistent Security, Statistical Anomaly Detection, Stateful Protocol Analysis Detection This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Intrusion Prevention Systems Ipss Overview And Methods
Firewall Network Security Intrusion Prevention Systems Ipss Overview And MethodsThis slide talks about the Intrusion Prevention System and its various methods for analyzing traffic. The purpose of this slide is to give an overview of Intrusion Prevention Systems and their methods, such as signature-based detection, statistical anomaly detection, and stateful protocol analysis detection. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Intrusion Prevention Systems Ipss Overview And Methods This template helps you present information on Three stages. You can also present information on Spyware Protection, Against Viruses, Prevents Hacking using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Key Benefits Of Firewall Protection System
Firewall Network Security Key Benefits Of Firewall Protection SystemThis slide talks about the main advantages of a firewall security system. The purpose of this slide is to highlight the key benefits of a firewall for businesses, such as spyware protection, the significant barrier against viruses, protection against hacking, privacy promotion, and network traffic monitoring. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Key Benefits Of Firewall Protection System This template helps you present information on Five stages. You can also present information on Intelligent Protection, Traffic Filtering, Communication Protocol Administration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Key Components Of Firewall Management System
Firewall Network Security Key Components Of Firewall Management SystemThis slide talks about the important elements of the firewall management system. The purpose of this slide is to showcase the vital components of a firewall management system, such as a graphical interface, policy control, threat management, device management, third-party integrations, and scalability. Introducing Firewall Network Security Key Components Of Firewall Management System to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Secure Access Service, Artificial Intelligence using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Key Components Of Firewall Protection System
Firewall Network Security Key Components Of Firewall Protection SystemThis slide talks about the primary elements of a firewall security system. The purpose of this slide is to showcase the different components of a firewall, such as network policy, advanced authentication, packet filtering, and application gateway. Present the topic in a bit more detail with this Firewall Network Security Key Components Of Firewall Protection System Use it as a tool for discussion and navigation on Misconfiguration, Software Vulnerabilities, Missing Firewall Policy This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Key Steps To Configure A Firewall System
Firewall Network Security Key Steps To Configure A Firewall SystemThis slide outlines the critical steps for firewall system configuration. The purpose of this slide is to showcase the different steps businesses can take while configuring a firewall system, such as protecting the firewall, creating firewall zones in addition to an IP address structure, setup access control lists, and so on. Deliver an outstanding presentation on the topic using this Firewall Network Security Key Steps To Configure A Firewall System Dispense information and present a thorough explanation of Complexity, False Sense Of Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ethical Hacking And Network Security Domain Name System Dns Spoofing
Ethical Hacking And Network Security Domain Name System Dns SpoofingThis slide represents the domain name system spoofing, including its methods such as man in the middle and DNS server compromise and how it is done through altered DNS records. Deliver an outstanding presentation on the topic using this Ethical Hacking And Network Security Domain Name System Dns Spoofing. Dispense information and present a thorough explanation of Domain Name System Spoofing, Server Compromise, Confidential Data, Technique For Gathering Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Elevating Living Spaces With Smart Devices For Security And System Maintenance
Elevating Living Spaces With Smart Devices For Security And System MaintenanceThis slide discusses the devices used in smart home technology. The purpose of this slide is to show smart home devices and their usage. These devices include a security system for monitoring and a smart controller for maintenance. Introducing Elevating Living Spaces With Smart Devices For Security And System Maintenance to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Security System, System And Maintenance, Remote Home Monitoring, Ring Alarm Security System, using this template. Grab it now to reap its full benefits.
-
 Committee National Security Systems In Powerpoint And Google Slides Cpb
Committee National Security Systems In Powerpoint And Google Slides CpbPresenting Committee National Security Systems In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Committee National Security Systems. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Identify Threat And Vulnerabilities Within Information System Creating Cyber Security Awareness
Identify Threat And Vulnerabilities Within Information System Creating Cyber Security AwarenessThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Deliver an outstanding presentation on the topic using this Identify Threat And Vulnerabilities Within Information System Creating Cyber Security Awareness Dispense information and present a thorough explanation of Unclear Storage Mechanism, Monitor User Behaviour, No Appropriate Structure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices For Securing IoT System IoT Security And Privacy Safeguarding IoT SS
Best Practices For Securing IoT System IoT Security And Privacy Safeguarding IoT SSThis slide exhibits IoT security best practices that help in addressing potential security weaknesses. It includes best practices such as network segmentation, IoT incident response plan, intrusion detection system, and patching and remediation. Increase audience engagement and knowledge by dispensing information using Best Practices For Securing IoT System IoT Security And Privacy Safeguarding IoT SS. This template helps you present information on four stages. You can also present information on Network Segmentation, Intrusion Detection System, Patching Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices To Provision Devices And Systems IoT Security And Privacy Safeguarding IoT SS
Best Practices To Provision Devices And Systems IoT Security And Privacy Safeguarding IoT SSThis slide outlines best practices of device and system provisioning that aim to effectively integrate devices into the IoT ecosystem. It includes allocate unique identifies, set up access control, and backup and recovery. Introducing Best Practices To Provision Devices And Systems IoT Security And Privacy Safeguarding IoT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Unique Identifies, Systematic Backup Process, Reduce Downtime, using this template. Grab it now to reap its full benefits.
-
 Data Processing And Storage System Security Measures IoT Security And Privacy Safeguarding IoT SS
Data Processing And Storage System Security Measures IoT Security And Privacy Safeguarding IoT SSThis slide includes security measures to address security and data privacy concerns of IoT architecture processing layer. It includes three elements such as cloud storage, data center, and web services. Deliver an outstanding presentation on the topic using this Data Processing And Storage System Security Measures IoT Security And Privacy Safeguarding IoT SS. Dispense information and present a thorough explanation of Data Tampering, Strong Authentications, Regular Hardware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps To Implement Network Segmentation In IoT System IoT Security And Privacy Safeguarding IoT SS
Steps To Implement Network Segmentation In IoT System IoT Security And Privacy Safeguarding IoT SSThis slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor. Deliver an outstanding presentation on the topic using this Steps To Implement Network Segmentation In IoT System IoT Security And Privacy Safeguarding IoT SS. Dispense information and present a thorough explanation of Assets Organisations, Between Segments, Monitor Segments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Types Of Intrusion Detection System IoT Security And Privacy Safeguarding IoT SS
Types Of Intrusion Detection System IoT Security And Privacy Safeguarding IoT SSThis slide exhibits two types of intrusion detection systems that may be deployed to provide layered security and enhance business operations. It includes two types of intrusion detection system such as network intrusion detection system and host intrusion detection system. Present the topic in a bit more detail with this Types Of Intrusion Detection System IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Network Intrusion, Best Suitable, Operating System. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Digital Systems Engineering Creation Of Secure Networks Using Mbse Principles
Digital Systems Engineering Creation Of Secure Networks Using Mbse PrinciplesThe purpose of this slide is to explain how MBSE principles can be applied to create secure networks and align with the criteria and models of information security management systems. This slide also highlights the steps involved, such as plan, do, check, and act. Present the topic in a bit more detail with this Digital Systems Engineering Creation Of Secure Networks Using Mbse Principles. Use it as a tool for discussion and navigation on Techniques, Information, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 National Security Entry Exit Registration System In Powerpoint And Google Slides Cpb
National Security Entry Exit Registration System In Powerpoint And Google Slides CpbPresenting our National Security Entry Exit Registration System In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on National Security Entry Exit Registration System This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Integrating ChatGPT With Other Systems Security How ChatGPT Actually Work ChatGPT SS V
Integrating ChatGPT With Other Systems Security How ChatGPT Actually Work ChatGPT SS VThis slide provides information regarding the integration of ChatGPT with other systems for managing security and compliance in terms of fraud detection, handling cybersecurity, risk assessment and compliance monitoring. Increase audience engagement and knowledge by dispensing information using Integrating ChatGPT With Other Systems Security How ChatGPT Actually Work ChatGPT SS V. This template helps you present information on four stages. You can also present information on Fraud Detection, Compliance Tracking, Risk Analysis using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Potential Threats Of Traditional Firewall Systems In Modern Network Security Firewall Virtualization
Potential Threats Of Traditional Firewall Systems In Modern Network Security Firewall VirtualizationThis slide highlights the various limitations of traditional firewall systems. The purpose of this slide is to outline the different issues of traditional firewalls. These include unable to prevent transfer of infected files, do not protect already compromised systems, etc. Deliver an outstanding presentation on the topic using this Potential Threats Of Traditional Firewall Systems In Modern Network Security Firewall Virtualization. Dispense information and present a thorough explanation of Harmful Websites, Non Technical Security, Security Rules using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Efficient Sales Processes With CRM Add Roles And Enable Security In CRM System CRP DK SS
Efficient Sales Processes With CRM Add Roles And Enable Security In CRM System CRP DK SSThis slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management. Present the topic in a bit more detail with this Efficient Sales Processes With CRM Add Roles And Enable Security In CRM System CRP DK SS. Use it as a tool for discussion and navigation on Enable Security, Lead Generation, Emails For Contact Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Role Of Intrusion Prevention Systems In Wireless Internet Security
Role Of Intrusion Prevention Systems In Wireless Internet SecurityThe outlined slide covers essential aspects, including encryption, authentication, access control, device security, and intrusion detection prevention. It provides a comprehensive view of wireless internet security measures, crucial for thwarting data theft. Introducing our premium set of slides with Role Of Intrusion Prevention Systems In Wireless Internet Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Compliance Requirements, Increased Network Visibility, Cost Effective Security. So download instantly and tailor it with your information.
-
 Organizational Csirt Cyber Security System
Organizational Csirt Cyber Security SystemThis slide showcases framework of CSIRT cyber security. The main purpose of this template is conflicting management and collective learning. This includes technology, CSIRT processes, CSIRT level situation, etc. Introducing our Organizational Csirt Cyber Security System set of slides. The topics discussed in these slides are Event Management, Conflict Management, Collective Learning. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Multi Layered Server Security System Flowchart
Multi Layered Server Security System FlowchartFollowing slide highlights flowchart of multi layered server security, also including elements such as host authentication, server network access, physical access, data masking, etc. Introducing our Multi Layered Server Security System Flowchart set of slides. The topics discussed in these slides are Physical Access, Host Access, Data Masking. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Server Security And Computer Networking System Icon
Server Security And Computer Networking System IconPresenting our set of slides with Server Security And Computer Networking System Icon. This exhibits information on threestages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Server Security, Computer Networking System.
-
 Triage Cyber Security For System Protection Icon
Triage Cyber Security For System Protection IconPresenting our set of slides with name Triage Cyber Security For System Protection Icon This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Triage Cyber Security, System Protection Icon
-
 Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber Security
Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber SecurityThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Deliver an outstanding presentation on the topic using this Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber Security Dispense information and present a thorough explanation of Vulnerability, Threat, Threat Source using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Securing Voting Systems With Blockchain Decoding The Future Of Blockchain Technology BCT SS
Securing Voting Systems With Blockchain Decoding The Future Of Blockchain Technology BCT SSThis slide highlights how blockchain technology helps governments in ensuring secured voting mechanisms to reduce frauds. It includes protection against fraud, decentralized and trust, real time monitoring, eradication of double voting and elimination of intermediaries. Introducing Securing Voting Systems With Blockchain Decoding The Future Of Blockchain Technology BCT SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Decentralization And Trust, Protection Against Fraud, Real-Time Monitoring And Auditing, using this template. Grab it now to reap its full benefits.





