Powerpoint Templates and Google slides for Risk And Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
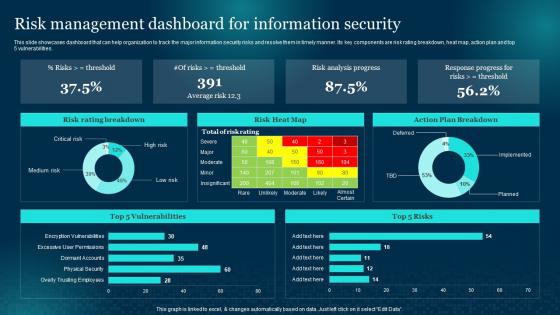 Risk Management Dashboard For Information Security Cybersecurity Risk Analysis And Management Plan
Risk Management Dashboard For Information Security Cybersecurity Risk Analysis And Management PlanThis slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities. Deliver an outstanding presentation on the topic using this Risk Management Dashboard For Information Security Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Management, Dashboard, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Assessment And Management Dashboard Incident Response Strategies Deployment
Cyber Security Risk Assessment And Management Dashboard Incident Response Strategies DeploymentThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Dashboard Incident Response Strategies Deployment. Use it as a tool for discussion and navigation on Accounts, Globally, Unresolved. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Risk Assessment And Management Dashboard Development And Implementation Of Security
Cyber Security Risk Assessment And Management Dashboard Development And Implementation Of SecurityThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Dashboard Development And Implementation Of Security. Dispense information and present a thorough explanation of Medium Risk, Unresolved Side, Inactive Accounts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
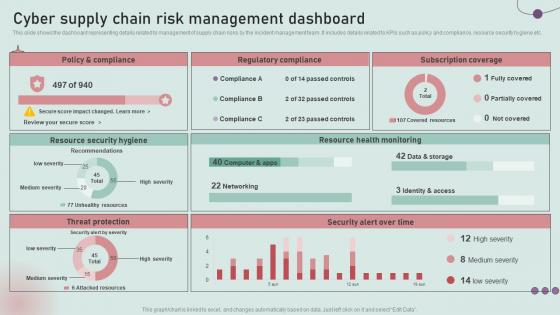 Cyber Supply Chain Risk Management Dashboard Development And Implementation Of Security Incident
Cyber Supply Chain Risk Management Dashboard Development And Implementation Of Security IncidentThis slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Deliver an outstanding presentation on the topic using this Cyber Supply Chain Risk Management Dashboard Development And Implementation Of Security Incident. Dispense information and present a thorough explanation of Regulatory Compliance, Subscription Coverage, Resource Health using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
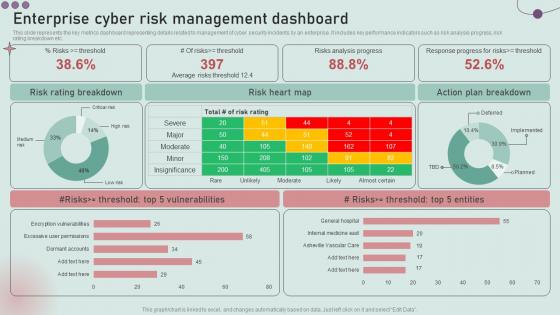 Enterprise Cyber Risk Management Dashboard Development And Implementation Of Security Incident
Enterprise Cyber Risk Management Dashboard Development And Implementation Of Security IncidentThis slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Present the topic in a bit more detail with this Enterprise Cyber Risk Management Dashboard Development And Implementation Of Security Incident. Use it as a tool for discussion and navigation on Risk Rating Breakdown, Risk Heart Map, Action Plan Breakdown. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management Dashboard
Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management DashboardThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management Dashboard. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Assessment And Management Dashboard Deploying Computer Security Incident
Cyber Security Risk Assessment And Management Dashboard Deploying Computer Security IncidentThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc.Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Dashboard Deploying Computer Security Incident. Use it as a tool for discussion and navigation on Expiring Password, Accessible Directories, Directories Direct Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Kpi for security risks total revenue policy deployment and adoption ppt slide
Kpi for security risks total revenue policy deployment and adoption ppt slidePresenting kpi for security risks total revenue policy deployment and adoption ppt slide. This presentation slide shows three Key Performance Indicators or KPIs in a Dashboard style design. The first KPI that can be shown is Number of Information Security Related Risks. The second KPI is Information Security Costs as a Proportion of Total Revenue or it Budget and the third is Information Security Policy Deployment and Adoption. These KPI Powerpoint graphics are all data driven,and the shape automatically adjusts according to your data. Just right click on the KPI graphic,enter the right value and the shape will adjust automatically. Make a visual impact with our KPI slides.
-
 Risk Management Kpi Dashboard Showing Overall Security Risk And Regulatory
Risk Management Kpi Dashboard Showing Overall Security Risk And RegulatoryPresenting this set of slides with name - Risk Management Kpi Dashboard Showing Overall Security Risk And Regulatory Compliance. This is a four stage process. The stages in this process are Risk Management, Risk Assessment, Project Risk.
-
 Risk reporting and likelihood effective information security risk management process
Risk reporting and likelihood effective information security risk management processMentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an outstanding presentation on the topic using this Risk Reporting And Likelihood Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Attack Scenario, Risk Encountered, Equipment Failure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Roles and responsibilities effective information security risk management process
Roles and responsibilities effective information security risk management processFollowing slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development.Increase audience engagement and knowledge by dispensing information using Roles And Responsibilities Effective Information Security Risk Management Process. This template helps you present information on one stage. You can also present information on Information Management Manager, Risk Management Officer, Development And Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Effective information security risk reporting and likelihood ppt slides layout
Effective information security risk reporting and likelihood ppt slides layoutMentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an outstanding presentation on the topic using this Effective Information Security Risk Reporting And Likelihood Ppt Slides Layout. Dispense information and present a thorough explanation of Risk Encountered, Frequency, Attack Scenario, Affected Asset using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Icon showcasing data availability security against risks and threats
Icon showcasing data availability security against risks and threatsPresenting our set of slides with Icon Showcasing Data Availability Security Against Risks And Threats. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon Showcasing Data Availability Security Against Risks And Threats.
-
 5 practices of information and cyber security risk management
5 practices of information and cyber security risk managementMentioned slide delineates best practices for information security risk management. Knowledge of IT environment and assets, developing risk management strategy, embedding risk management into organization culture, continuous risk assessment and security protocols are the practices covered in this slide. Presenting our set of slides with 5 Practices Of Information And Cyber Security Risk Management. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Management, Organization, Risk.
-
 Cyber and information security risk management framework
Cyber and information security risk management frameworkMentioned slide exhibits information security risk management framework which can be used to enhance cybersecurity of organization. The various components covered in this framework are service design, transition and operationalization, penetration testing etc. Introducing our Cyber And Information Security Risk Management Framework set of slides. The topics discussed in these slides are Development, Service Transition, Service Operationalization. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Icon for information and cyber security risk management
Icon for information and cyber security risk managementIntroducing our premium set of slides with Icon For Information And Cyber Security Risk Management. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon For Information And Cyber Security Risk Management. So download instantly and tailor it with your information.
-
 Icon for information security and risk management team
Icon for information security and risk management teamIntroducing our premium set of slides with Icon For Information Security And Risk Management Team. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon For Information Security And Risk Management Team. So download instantly and tailor it with your information.
-
 Information and cyber security risk management maturity levels
Information and cyber security risk management maturity levelsMentioned slide showcase maturity stages of information security risk management, which will assist company to develop comprehensive cybersecurity strategy. The maturity stages could be Partial informed repetitive and adaptive. Introducing our premium set of slides with Information And Cyber Security Risk Management Maturity Levels. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Partial, Informed, Repetitive. So download instantly and tailor it with your information.
-
 Information and cyber security risk management plan
Information and cyber security risk management planMentioned slide showcase information security risk management plan. The template provides information about various risks such as DDoS, crypto jacking, malware and password theft and with other details like degree of risk involved, impact, strategies to be deployed. Introducing our Information And Cyber Security Risk Management Plan set of slides. The topics discussed in these slides are Degree Of Risk, Strategies, Devices. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information security risk assessment and management tools
Information security risk assessment and management toolsMentioned slide highlights several information security risk management tools which can be used by organization. The multiple tools are automated questionnaires, security ratings and vulnerability assessment report. Introducing our premium set of slides with Information Security Risk Assessment And Management Tools. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Ratings, Automated Questionnaires, Vulnerability Assessment Report. So download instantly and tailor it with your information.
-
 How financial risk can be controlled managing critical threat vulnerabilities and security threats
How financial risk can be controlled managing critical threat vulnerabilities and security threatsThis slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Increase audience engagement and knowledge by dispensing information using How Financial Risk Can Be Controlled Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on three stages. You can also present information on Liquidity Risk, Exchange Risk, Credit Exchange Risk using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber threat security planning process with risk tolerance and threats
Cyber threat security planning process with risk tolerance and threatsThis following slide illustrates the cyber security threat program planning which include steps like identify key personnel, risk tolerance strategy and developing frequency. Presenting our set of slides with Cyber Threat Security Planning Process With Risk Tolerance And Threats. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Built Risk Tolerance, Identify And Document, Establish Governance.
-
 Risk Based Methodology To Cyber And Information Security Table Of Contents
Risk Based Methodology To Cyber And Information Security Table Of ContentsDeliver an outstanding presentation on the topic using this Risk Based Methodology To Cyber And Information Security Table Of Contents Dispense information and present a thorough explanation of Threat Matrix, Identified Assets, Impact Assessment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Encountered Risks Summary And Their Impact Assessment
Information Security Program Encountered Risks Summary And Their Impact AssessmentMentioned slide provides information about the risks encountered by the company till date and their impact on existing business operations. Deliver an outstanding presentation on the topic using this Information Security Program Encountered Risks Summary And Their Impact Assessment. Dispense information and present a thorough explanation of Assessment, Encountered, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Scorecard To Check Cybersecurity And Digital Risk Preparedness
Information Security Program Scorecard To Check Cybersecurity And Digital Risk PreparednessFollowing slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Present the topic in a bit more detail with this Information Security Program Scorecard To Check Cybersecurity And Digital Risk Preparedness. Use it as a tool for discussion and navigation on Preparedness, Cybersecurity, Scorecard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Framework For Information Security Online And Onsite Training Schedule
Risk Management Framework For Information Security Online And Onsite Training ScheduleThis slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration. Present the topic in a bit more detail with this Risk Management Framework For Information Security Online And Onsite Training Schedule. Use it as a tool for discussion and navigation on Employee, Training Mode, Intermediate, Online And Onsite. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Framework For Information Security Risk Reporting And Likelihood
Risk Management Framework For Information Security Risk Reporting And LikelihoodMentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Present the topic in a bit more detail with this Risk Management Framework For Information Security Risk Reporting And Likelihood. Use it as a tool for discussion and navigation on Risk Encountered, Frequency, Attack Scenario, Affected Asset. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Framework For Information Security Roles And Responsibilities For Managing
Risk Management Framework For Information Security Roles And Responsibilities For ManagingFollowing slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development. Increase audience engagement and knowledge by dispensing information using Risk Management Framework For Information Security Roles And Responsibilities For Managing. This template helps you present information on two stages. You can also present information on Chief Information Officer, Information Management Manager, IT Manger, Risk Management Officer using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Risk Management Framework For Information Security Threat Identification And Vulnerability
Risk Management Framework For Information Security Threat Identification And VulnerabilityFollowing slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an outstanding presentation on the topic using this Risk Management Framework For Information Security Threat Identification And Vulnerability. Dispense information and present a thorough explanation of Communication And Network, Database, Failure To Segment Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Icons Slide For Risk Based Methodology To Cyber and Information Security
Icons Slide For Risk Based Methodology To Cyber and Information SecurityPresenting our well crafted Icons Slide For Risk Based Methodology To Cyber and Information Security set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly
-
 Table Of Contents For Risk Based Methodology To Cyber and Information Security
Table Of Contents For Risk Based Methodology To Cyber and Information SecurityPresent the topic in a bit more detail with this Table Of Contents For Risk Based Methodology To Cyber and Information Security Use it as a tool for discussion and navigation on Defining Business Priorities, Global Market Insights, Companies Digitization Levels This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat Drivers And Emerging Introducing A Risk Based Approach To Cyber Security
Threat Drivers And Emerging Introducing A Risk Based Approach To Cyber SecurityMentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security.Increase audience engagement and knowledge by dispensing information using Threat Drivers And Emerging Introducing A Risk Based Approach To Cyber Security This template helps you present information on one stage. You can also present information on Internet Of Things, Artificial Intelligence, Human Machine Interface using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Case study 4 improving patient security and reducing risk ppt microsoft
Case study 4 improving patient security and reducing risk ppt microsoftThe slide provides the case study of a healthcare company that faced the issue of growing risks of patient security and violence in the hospital. The slide provides the solutions offered by the technology company related to risk protection and security effectiveness. Deliver an outstanding presentation on the topic using this Case Study 4 Improving Patient Security And Reducing Risk Ppt Microsoft. Dispense information and present a thorough explanation of Power Management, Space Management, Building Management, Security Management, Risk Protection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
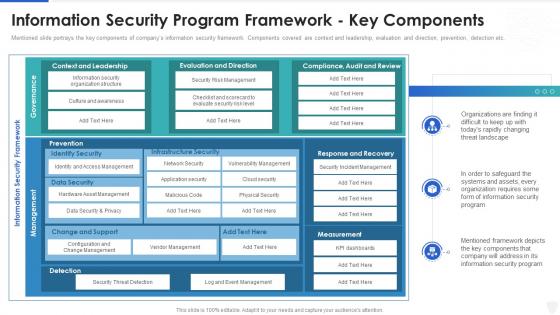 Cybersecurity and digital business risk management security program framework
Cybersecurity and digital business risk management security program frameworkMentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver an outstanding presentation on the topic using this Cybersecurity And Digital Business Risk Management Security Program Framework. Dispense information and present a thorough explanation of Framework, Information, Organizations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing internal and external sources data cyber security risk management
Addressing internal and external sources data cyber security risk managementThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Deliver an outstanding presentation on the topic using this Addressing Internal And External Sources Data Cyber Security Risk Management. Dispense information and present a thorough explanation of Internal Sources, External Sources, Targeted Intelligence, Malware Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing several financial scenarios and signs cyber security risk management
Addressing several financial scenarios and signs cyber security risk managementThis slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Introducing Addressing Several Financial Scenarios And Signs Cyber Security Risk Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Liquidity, Profitability, Financial Performance, Employees, using this template. Grab it now to reap its full benefits.
-
 Cyber security risk management roles and responsibilities ensure work environment
Cyber security risk management roles and responsibilities ensure work environmentThis slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Roles And Responsibilities Ensure Work Enviro. This template helps you present information on four stages. You can also present information on Employee Responsibilities, Unit Supervisor, Manager Responsibilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security risk management various types of workplace violence and threats
Cyber security risk management various types of workplace violence and threatsThis slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. Introducing Cyber Security Risk Management Various Types Of Workplace Violence And Threats to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Threats Or Threatening Behavior, Physical Assault, Property Damage, using this template. Grab it now to reap its full benefits.
-
 Information Security And Iso 27001 Defining Risk Level And Impact Score
Information Security And Iso 27001 Defining Risk Level And Impact ScoreFollowing slide defines the incident risk level. It includes details about risk level, risk score and its description. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 Defining Risk Level And Impact Score. Dispense information and present a thorough explanation of Defining Risk Level And Impact Score using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Mapping Of Risk Events
Information Security And Iso 27001 Mapping Of Risk EventsThis slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack. Present the topic in a bit more detail with this Information Security And Iso 27001 Mapping Of Risk Events. Use it as a tool for discussion and navigation on Mapping Of Risk Events. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 Risk Assessment Worksheet
Information Security And Iso 27001 Risk Assessment WorksheetFollowing slide displays information security risk assessment worksheet. It covers details about risk encountered, its description, vulnerability asset and consequences and risk to the firm. Present the topic in a bit more detail with this Information Security And Iso 27001 Risk Assessment Worksheet. Use it as a tool for discussion and navigation on Risk Assessment Worksheet. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Events Reporting And Likelihood Information Security And Iso 27001
Risk Events Reporting And Likelihood Information Security And Iso 27001Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Present the topic in a bit more detail with this Risk Events Reporting And Likelihood Information Security And Iso 27001. Use it as a tool for discussion and navigation on Risk Events Reporting And Likelihood. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan risk assessment matrix with severity and likelihood
Building organizational security strategy plan risk assessment matrix with severity and likelihoodThe risk assessment matrix is an effective tool that helps in evaluating risk by considering the probability of risk to happen against the severity linked with potential risk available. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Risk Assessment Matrix With Severity And Likelihood. Use it as a tool for discussion and navigation on Assessment, Evaluating, Potential. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
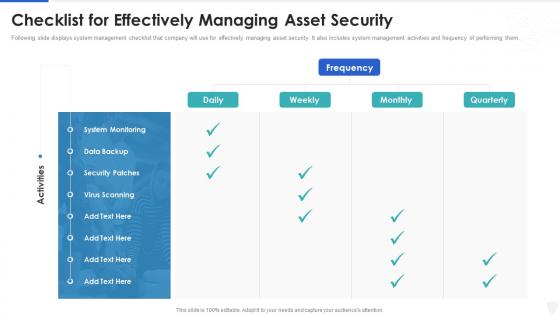 Cybersecurity and digital business risk management checklist for effectively managing asset security
Cybersecurity and digital business risk management checklist for effectively managing asset securityFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Present the topic in a bit more detail with this Cybersecurity And Digital Business Risk Management Checklist For Effectively Managing Asset Security. Use it as a tool for discussion and navigation on System Monitoring, Data Backup, Security Patches . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
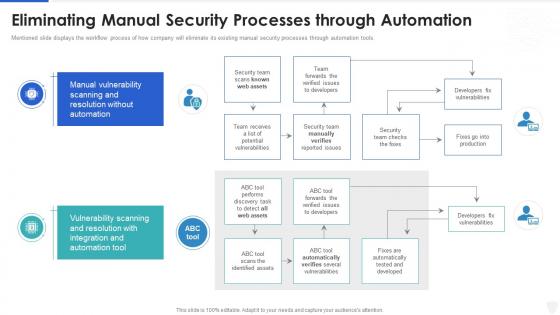 Cybersecurity and digital business risk management eliminating manual security processes
Cybersecurity and digital business risk management eliminating manual security processesMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Present the topic in a bit more detail with this Cybersecurity And Digital Business Risk Management Eliminating Manual Security Processes. Use it as a tool for discussion and navigation on Processes, Resolution, Automation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity and digital business risk management key security controls to be addressed
Cybersecurity and digital business risk management key security controls to be addressedPurpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Increase audience engagement and knowledge by dispensing information using Cybersecurity And Digital Business Risk Management Key Security Controls To Be Addressed. This template helps you present information on three stages. You can also present information on Framework, Authentification, Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
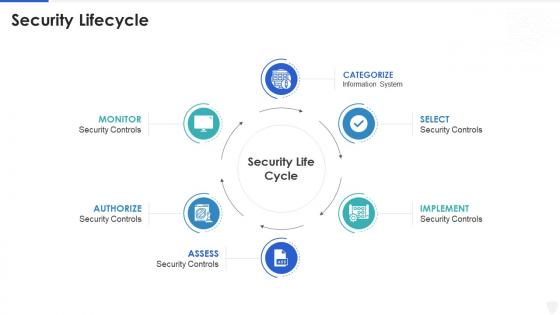 Cybersecurity and digital business risk management security lifecycle
Cybersecurity and digital business risk management security lifecycleIntroducing Cybersecurity And Digital Business Risk Management Security Lifecycle to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Security Lifecycle, using this template. Grab it now to reap its full benefits.
-
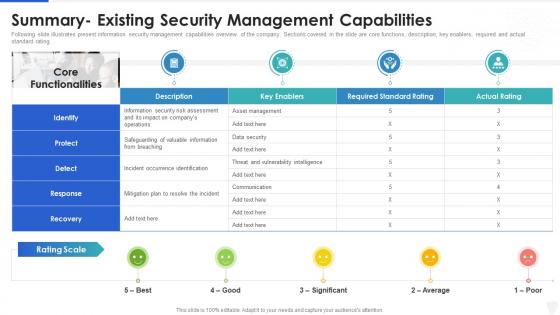 Cybersecurity and digital business risk management summary- existing security management
Cybersecurity and digital business risk management summary- existing security managementFollowing slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an outstanding presentation on the topic using this Cybersecurity And Digital Business Risk Management Summary- Existing Security Management. Dispense information and present a thorough explanation of Management, Information, Communication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Healthcare Information Security Risk Acceptance And Management Plan
Healthcare Information Security Risk Acceptance And Management PlanThis slide shows information security risk treatment and acceptance plan for hospitals which can benefit them in securing their data. It contains details such as possession type, risk acceptance criteria, treating the risk, techniques and approaches for risk, residual risk acceptance measures, etc. Introducing our Healthcare Information Security Risk Acceptance And Management Plan set of slides. The topics discussed in these slides are Possession Type, Risk Acceptance Criteria, Treating The Risk. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Determining Roles And Responsibilities For Risk Handling Android Device Security Management
Determining Roles And Responsibilities For Risk Handling Android Device Security ManagementThis slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Key people involved in risk handling are chief risk officer, chief information security officer, senior management and executives and line managers. Introducing Determining Roles And Responsibilities For Risk Handling Android Device Security Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Line Management, Senior Management, Chief Information Security Officer, using this template. Grab it now to reap its full benefits.
-
 Phase 1 Understand Cloud Utilization And Risk Cloud Information Security
Phase 1 Understand Cloud Utilization And Risk Cloud Information SecurityThis slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of.Introducing Phase 1 Understand Cloud Utilization And Risk Cloud Information Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Authentication Process, Cloud Access, Eliminate Malware using this template. Grab it now to reap its full benefits.
-
 Cloud Computing Security Phase1 Understand Cloud Utilization And Risk
Cloud Computing Security Phase1 Understand Cloud Utilization And RiskThis slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of. Present the topic in a bit more detail with this Cloud Computing Security Phase1 Understand Cloud Utilization And Risk. Use it as a tool for discussion and navigation on Recognize Critical Data, User Activities, Risk Assessment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F415 Risk Assessment And Management Plan For Information Security Analyzing Impact Security Threats
F415 Risk Assessment And Management Plan For Information Security Analyzing Impact Security ThreatsDeliver an outstanding presentation on the topic using this F415 Risk Assessment And Management Plan For Information Security Analyzing Impact Security Threats. Dispense information and present a thorough explanation of Analyzing, Organization, Financial using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Agenda For Risk Assessment And Management Plan For Information Security
Agenda For Risk Assessment And Management Plan For Information SecurityIntroducing Agenda For Risk Assessment And Management Plan For Information Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Assessment, Management, Information, using this template. Grab it now to reap its full benefits.
-
 Allocating Budget For Information Security Risk Assessment And Management Plan For Information Security
Allocating Budget For Information Security Risk Assessment And Management Plan For Information SecurityThis slide showcase budget to be allocated for conducting training for information security risk management. It showcases budget for area like cybersecurity awareness, threat detection and risk management Present the topic in a bit more detail with this Allocating Budget For Information Security Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Information, Management, Programme. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Analyzing The Impact On Assets Due To Risk Assessment And Management Plan For Information Security
Analyzing The Impact On Assets Due To Risk Assessment And Management Plan For Information SecurityThis slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets Deliver an outstanding presentation on the topic using this Analyzing The Impact On Assets Due To Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Revenue, Information, Importance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Asset Identification For Information Risk Assessment And Management Plan For Information Security
Asset Identification For Information Risk Assessment And Management Plan For Information SecurityThis slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack Deliver an outstanding presentation on the topic using this Asset Identification For Information Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Sales Records, Customers Database, Products Database using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Assigning Criticality Rating To Information Risk Assessment And Management Plan For Information Security
Assigning Criticality Rating To Information Risk Assessment And Management Plan For Information SecurityThis slide showcases criticality rating that can be allocated to assets for identifying critical assets. Its key elements are asset, failure cost, failure impact and criticality rating Present the topic in a bit more detail with this Assigning Criticality Rating To Information Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Customer Database, Product Database, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Budget For Information Security Risk Assessment And Management Plan For Information Security
Budget For Information Security Risk Assessment And Management Plan For Information SecurityThis slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup Deliver an outstanding presentation on the topic using this Budget For Information Security Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Training Of Employees, Software Implementation, Risk Monitoring using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist For Information Security Risk Assessment And Management Plan For Information Security
Checklist For Information Security Risk Assessment And Management Plan For Information SecurityThis slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status Deliver an outstanding presentation on the topic using this Checklist For Information Security Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Information, Management, Consequences using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





