Powerpoint Templates and Google slides for Risk And Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Types And Techniques Of Cloning Risks In Cyber Security
Types And Techniques Of Cloning Risks In Cyber SecurityThis slide covers different types of cloning and techniques that provides attackers an unauthorized access to confidential data. It covers three types of cloning such as device, software and identity cloning. Introducing our Types And Techniques Of Cloning Risks In Cyber Security set of slides. The topics discussed in these slides are Device Cloning, Software Cloning, Identity Cloning. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Determine Cyber Security Risks And Threats Creating Cyber Security Awareness
Determine Cyber Security Risks And Threats Creating Cyber Security AwarenessThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Present the topic in a bit more detail with this Determine Cyber Security Risks And Threats Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Human Errors, Factor Authentication This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Evaluate Impact And Probability Of Risk Occurrence Creating Cyber Security Awareness
Evaluate Impact And Probability Of Risk Occurrence Creating Cyber Security AwarenessThe following slide depicts the potential risk score of identified cyber risks to communicate and level threats. It includes key elements such as human and general errors, outdated security policy, selling companys confidential information, system failure etc. Deliver an outstanding presentation on the topic using this Evaluate Impact And Probability Of Risk Occurrence Creating Cyber Security Awareness Dispense information and present a thorough explanation of Data Backup Methods, Network Attached Storage, Cloud Storage Services using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Monitor And Assess Vendor Risk Management Creating Cyber Security Awareness
Monitor And Assess Vendor Risk Management Creating Cyber Security AwarenessThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Deliver an outstanding presentation on the topic using this Monitor And Assess Vendor Risk Management Creating Cyber Security Awareness Dispense information and present a thorough explanation of Select Strong Password, Conduct Password Test, Password Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Standards And Framework For IoT Risk Mitigation IoT Security And Privacy Safeguarding IoT SS
Security Standards And Framework For IoT Risk Mitigation IoT Security And Privacy Safeguarding IoT SSThis side presents IoT security standards and framework that help organisation for risk mitigation. It incudes security standards such as ISO 27000 series, NIST SP 800 53, and NIST CSF controls. Introducing Security Standards And Framework For IoT Risk Mitigation IoT Security And Privacy Safeguarding IoT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on International Organization, Information Security Issues, Management System, using this template. Grab it now to reap its full benefits.
-
 Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security Threats
Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Deliver an outstanding presentation on the topic using this Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Malware, Phishing, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats
Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Present the topic in a bit more detail with this Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Information Security And Privacy, Physical Assets And Data Security, Web Application Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Emerging Cloud Security Risks And Threats CASB Cloud Security
Emerging Cloud Security Risks And Threats CASB Cloud SecurityThis slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Present the topic in a bit more detail with this Emerging Cloud Security Risks And Threats CASB Cloud Security. Use it as a tool for discussion and navigation on System Misconfigurations, Lack Of Edge Or Perimeter Security, Risks And Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Strategies To Mitigate Cyber Security Evaluate Impact And Probability Of Risk Occurrence
Implementing Strategies To Mitigate Cyber Security Evaluate Impact And Probability Of Risk OccurrenceThe following slide depicts the potential risk score of identified cyber risks to communicate and level threats. It includes key elements such as human and general errors, outdated security policy, selling companys confidential information, system failure etc. Present the topic in a bit more detail with this Implementing Strategies To Mitigate Cyber Security Evaluate Impact And Probability Of Risk Occurrence Use it as a tool for discussion and navigation on Parameters, Impact, Probability This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mobile Security Threats And Risk Assessment
Mobile Security Threats And Risk AssessmentThis slide showcases risk and threat evaluation of mobile security and includes security breaches, phishing attacks, and mobile ransomware. Introducing our Mobile Security Threats And Risk Assessment set of slides. The topics discussed in these slides are Security Breaches, Phishing Attacks, Mobile Ransomware. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 ChatGPT For Streamlining And Improving Security Opportunities And Risks Of ChatGPT AI SS V
ChatGPT For Streamlining And Improving Security Opportunities And Risks Of ChatGPT AI SS VThis slide showcases overview of ChatGPT for streamlining and optimizing the security operations in organizations. Its key elements are cybersecurity training, enhanced communication during attack, developing policies and reporting after attack. Introducing ChatGPT For Streamlining And Improving Security Opportunities And Risks Of ChatGPT AI SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reporting After Attack, Cybersecurity Training, Developing Policies, using this template. Grab it now to reap its full benefits.
-
 ChatGPT Use Cases For Streamlining Security Opportunities And Risks Of ChatGPT AI SS V
ChatGPT Use Cases For Streamlining Security Opportunities And Risks Of ChatGPT AI SS VThis slide showcases various ChatGPT use cases for streamlining and automating the cybersecurity operations of organization. Its key elements are establish security policies, automate repetitive tasks and identification of vulnerabilities. Increase audience engagement and knowledge by dispensing information using ChatGPT Use Cases For Streamlining Security Opportunities And Risks Of ChatGPT AI SS V. This template helps you present information on three stages. You can also present information on Establish Security Policies And Sops, Automate Repetitive Tasks, Identify Vulnerabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Limitations Of Leveraging ChatGPT For Security Opportunities And Risks Of ChatGPT AI SS V
Limitations Of Leveraging ChatGPT For Security Opportunities And Risks Of ChatGPT AI SS VThis slide showcases various disadvantages of leveraging ChatGPT for security operations. Its key elements are information inaccuracy, over-reliance on automation, input misinterpretation, output bias and confidentially concerns. Introducing Limitations Of Leveraging ChatGPT For Security Opportunities And Risks Of ChatGPT AI SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality Concerns, Over-Reliance On Automation, Output Bias, using this template. Grab it now to reap its full benefits.
-
 Email Security Risks And Mitigation Plan
Email Security Risks And Mitigation PlanThis slide covers email security risks and its mitigation plan which includes risks such as phishing, evolving phishing, domain squatting and malware. Presenting our set of slides with Email Security Risks And Mitigation Plan. This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Email Security, Risks, Mitigation Plan.
-
 Website Security Risks And Penetration Testing Report
Website Security Risks And Penetration Testing ReportThis template showcases advanced penetration testing report for organization website. It covers factors such as vulnerabilities, severity and risk level. Presenting our well structured Website Security Risks And Penetration Testing Report. The topics discussed in this slide are Website Security Risks, Penetration Testing Report. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Application Security Implementation Plan Risks And Mitigation Strategies While Deploying Application Security
Application Security Implementation Plan Risks And Mitigation Strategies While Deploying Application SecurityThe purpose of this slide is to discuss the challenges faced while implementing application security such as data breaches, third-party risks, etc. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Risks And Mitigation Strategies While Deploying Application Security. Dispense information and present a thorough explanation of Vulnerabilities In Applications, Data Breaches, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Governance And Risk Management In Cloud Based Systems
Tokenization For Improved Data Security Governance And Risk Management In Cloud Based SystemsThis slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Governance And Risk Management In Cloud Based Systems. Dispense information and present a thorough explanation of Governance And Risk Management, Cloud Based Systems, During Categorization Organization Must using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security Threat
Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the cyber security attack risk assessment matrix which can be leveraged to determine the severity of cyber threats, the likelihood of occurrence, and future action plan. Present the topic in a bit more detail with this Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Assessment Matrix, Occurrence, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Associated With Identity And Access Management Process Securing Systems With Identity
Risk Associated With Identity And Access Management Process Securing Systems With IdentityThis slide outlines the potential hazards linked to the Identity and Access Management process. The purpose of this slide is to discuss the risks these include incorrectly defined roles and attributes, infrequent audits, and complex implementations. Introducing Risk Associated With Identity And Access Management Process Securing Systems With Identity to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Roles And Attributes, Infrequent Audits, Complex Implementations using this template. Grab it now to reap its full benefits.
-
 Cloud Data Migration Security Risks And Solutions
Cloud Data Migration Security Risks And SolutionsThe below slide highlights the multiple security risks associated with cloud data migration along with the potential solutions to eliminate them. The various risks mentioned are unauthorized access, data breaches, weak data encryption, etc. Introducing our Cloud Data Migration Security Risks And Solutions set of slides. The topics discussed in these slides are Unauthorized Access, Data Breaches, Weak Data Encryption. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Pam Cyber Security Risk And Adoption Scorecard
Pam Cyber Security Risk And Adoption ScorecardThis slide represents scorecard that assist companies to measure adoption of PAM cybersecurity to enhance their data protection. It includes various components such as work stream type, preferred trends, target ETS , etc. Presenting our well structured Pam Cyber Security Risk And Adoption Scorecard. The topics discussed in this slide are Adoption Scorecard, Platform, Deployment. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Factors Contributing To Rising Cyber Security Risks In Finance And Banking
Factors Contributing To Rising Cyber Security Risks In Finance And BankingThis slide represents factors affecting cyber security concerns in finance and banking. It aims to continually invest in cyber security measures, employee training, and threat intelligence to protect from evolving landscape of cyber security risks. It includes various elements such as factors, description and strategies to reduce risks. Presenting our set of slides with Factors Contributing To Rising Cyber Security Risks In Finance And Banking. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Third Party Vendors, Onboarding New Technologies, Cloud Cybercrimes.
-
 Web Security Upgradation Risks And Mitigation Strategies While Deploying Web Security
Web Security Upgradation Risks And Mitigation Strategies While Deploying Web SecurityThe purpose of this slide is to discuss the challenges faced while implementing web security such as alert overload, skill gap, etc. Present the topic in a bit more detail with this Web Security Upgradation Risks And Mitigation Strategies While Deploying Web Security. Use it as a tool for discussion and navigation on Risk, Impact, Mitigation Strategies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Concern Of Bioprinting Risks In Powerpoint And Google Slides CPP
Security Concern Of Bioprinting Risks In Powerpoint And Google Slides CPPPresenting our Security Concern Of Bioprinting Risks In Powerpoint And Google Slides CPP PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Security Concern Of Bioprinting Risks This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Ambient Intelligent Cyber Security Risk In Powerpoint And Google Slides CPP
Ambient Intelligent Cyber Security Risk In Powerpoint And Google Slides CPPPresenting Ambient Intelligent Cyber Security Risk In Powerpoint And Google Slides CPP slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Ambient Intelligent Cyber Security Risk. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Income securities risk and return level ppt background graphics
Income securities risk and return level ppt background graphicsPresenting income securities risk and return level ppt background graphics. This is a income securities risk and return level ppt background graphics. This is a four stage process. The stages in this process are risk, cash, fixed interest, property, shares.
-
 Threat and dashboard effective information security risk management process
Threat and dashboard effective information security risk management processFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Threat And Dashboard Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Security Recommendation, Security Controls, Active Remediation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information security risk management challenges and solutions
Information security risk management challenges and solutionsMentioned slide showcases various challenges and solutions of information security risk management. The challenges mentioned in the slide are continuously cyber risk measurement, risk of cyber adversaries, tracking sensitive data flows. Introducing our Information Security Risk Management Challenges And Solutions set of slides. The topics discussed in these slides are Measuring, Service, Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber threat dashboard with current risks and security service
Cyber threat dashboard with current risks and security serviceThe following slide focuses on the cyber threat dashboard which highlights current threats, current risks, regulation and policy coverage, security service and asset control issues. Presenting our well structured Cyber Threat Dashboard With Current Risks And Security Service. The topics discussed in this slide are Current Risks, Current Threats, Security Service. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Information Security Program Risk Management Kpi Dashboard With Loss Events And Actions
Information Security Program Risk Management Kpi Dashboard With Loss Events And ActionsFollowing slide illustrates a risk management KPI dashboard. KPIs covered are top ten risks, loss events, actions, key risk indicators and compliance. Deliver an outstanding presentation on the topic using this Information Security Program Risk Management Kpi Dashboard With Loss Events And Actions. Dispense information and present a thorough explanation of Management, Dashboard, Compliance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Framework For Information Security Threat And Vulnerability
Risk Management Framework For Information Security Threat And VulnerabilityFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Risk Management Framework For Information Security Threat And Vulnerability. Use it as a tool for discussion and navigation on Exposure Score, Top Vulnerable Software, Severity Distribution, Active Remediation, Configuration Score. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard For Information Security Risk Management Information Security And Iso 27001
Dashboard For Information Security Risk Management Information Security And Iso 27001This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Present the topic in a bit more detail with this Dashboard For Information Security Risk Management Information Security And Iso 27001. Use it as a tool for discussion and navigation on Dashboard, Information, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 Dashboard To Measure Total Risks Encountered And Resolved
Information Security And Iso 27001 Dashboard To Measure Total Risks Encountered And ResolvedMentioned slide portrays dashboard for measuring total risk encountered by the firm in specific period and total risks resolved. Key metrics included in the slide are issues by status, issues by priority and resolved status. Present the topic in a bit more detail with this Information Security And Iso 27001 Dashboard To Measure Total Risks Encountered And Resolved. Use it as a tool for discussion and navigation on Dashboard, Measure, Encountered. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 Percent Of Risk Events Occurred Over Last Two Years
Information Security And Iso 27001 Percent Of Risk Events Occurred Over Last Two YearsThis slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 Percent Of Risk Events Occurred Over Last Two Years. Dispense information and present a thorough explanation of Percent Of Risk Events Occurred Over Last Two Years using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Total Risk Events Encountered And Loss Amount Involved
Information Security And Iso 27001 Total Risk Events Encountered And Loss Amount InvolvedMentioned slide portrays year over year stats of number of risk events occurred within the firm. It also includes the total amount of loss caused from risk events annually. Present the topic in a bit more detail with this Information Security And Iso 27001 Total Risk Events Encountered And Loss Amount Involved. Use it as a tool for discussion and navigation on Total Risk Events Encountered And Loss Amount Involved. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
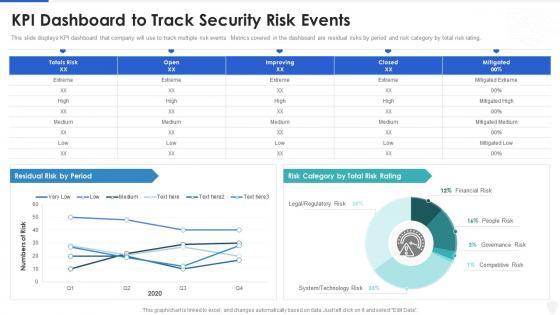 Cybersecurity and digital business risk management kpi dashboard to track security risk events
Cybersecurity and digital business risk management kpi dashboard to track security risk eventsPresent the topic in a bit more detail with this Cybersecurity And Digital Business Risk Management Kpi Dashboard To Track Security Risk Events. Use it as a tool for discussion and navigation on KPI Dashboard To Track Security Risk Events. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Assessing Cost Of Information Breach In Risk Assessment And Management Plan For Information Security
Assessing Cost Of Information Breach In Risk Assessment And Management Plan For Information SecurityPresent the topic in a bit more detail with this Assessing Cost Of Information Breach In Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Information, Sources, Engineering. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information Security
Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information SecurityThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type if cyber attacks and formulate strategies to tackle them Present the topic in a bit more detail with this Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Experienced, Organization, Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard For Data Security Risk Assessment And Management Plan For Information Security
Dashboard For Data Security Risk Assessment And Management Plan For Information SecurityThis slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status Deliver an outstanding presentation on the topic using this Dashboard For Data Security Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Dashboard, Management, Data Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Market Growth Of Information Security Industry Risk Assessment And Management Plan For Information Security
Market Growth Of Information Security Industry Risk Assessment And Management Plan For Information SecurityThis slide showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compunded annual growth rate of industry Deliver an outstanding presentation on the topic using this Market Growth Of Information Security Industry Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Growth, Information, Security Industry using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Rising Number Of Information Security Attacks Risk Assessment And Management Plan For Information Security
Rising Number Of Information Security Attacks Risk Assessment And Management Plan For Information SecurityThis slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection Present the topic in a bit more detail with this Rising Number Of Information Security Attacks Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Organizations, Information, Cybersecurity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Assessment And Management Plan For Information Security Information And Data Breach Impacting
Risk Assessment And Management Plan For Information Security Information And Data Breach ImpactingDeliver an outstanding presentation on the topic using this Risk Assessment And Management Plan For Information Security Information And Data Breach Impacting. Dispense information and present a thorough explanation of Information, Business, Financial using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Dashboard For Information Risk Assessment And Management Plan For Information Security
Risk Management Dashboard For Information Risk Assessment And Management Plan For Information SecurityThis slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities Deliver an outstanding presentation on the topic using this Risk Management Dashboard For Information Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Management, Dashboard, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents Risk Assessment And Management Plan For Information Security
Table Of Contents Risk Assessment And Management Plan For Information SecurityDeliver an outstanding presentation on the topic using this Table Of Contents Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Assessment, Organization, Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information And Data Breach Impacting Customer Loyalty Information Security Risk Management
Information And Data Breach Impacting Customer Loyalty Information Security Risk ManagementDeliver an outstanding presentation on the topic using this Information And Data Breach Impacting Customer Loyalty Information Security Risk Management. Dispense information and present a thorough explanation of Information, Data Breach Impacting, Customer Loyalty using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents Information Security Risk Management And Mitigation Plan
Table Of Contents Information Security Risk Management And Mitigation PlanDeliver an outstanding presentation on the topic using this Table Of Contents Information Security Risk Management And Mitigation Plan. Dispense information and present a thorough explanation of Organization Information, Security Capabilities, Overview using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information System Security And Risk Administration Information And Data Breach Impacting Customer Loyalty
Information System Security And Risk Administration Information And Data Breach Impacting Customer LoyaltyDeliver an outstanding presentation on the topic using this Information System Security And Risk Administration Information And Data Breach Impacting Customer Loyalty. Dispense information and present a thorough explanation of Business, Financial Data, Data Breach using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information System Security And Risk Administration Plan Risk Management Dashboard For Information Security
Information System Security And Risk Administration Plan Risk Management Dashboard For Information SecurityThis slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities. Deliver an outstanding presentation on the topic using this Information System Security And Risk Administration Plan Risk Management Dashboard For Information Security. Dispense information and present a thorough explanation of Risk Rating Breakdown, Risk Heat Map, Action Plan Breakdown using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Assessing Cost Of Information Breach In Different Information System Security And Risk Administration Plan
Assessing Cost Of Information Breach In Different Information System Security And Risk Administration PlanPresent the topic in a bit more detail with this Assessing Cost Of Information Breach In Different Information System Security And Risk Administration Plan. Use it as a tool for discussion and navigation on Past Decade, Social Engineering, Advanced Persistent Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparison Information System Security And Risk Administration Plan Ppt Styles Show
Comparison Information System Security And Risk Administration Plan Ppt Styles ShowThis graph chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Present the topic in a bit more detail with this Comparison Information System Security And Risk Administration Plan Ppt Styles Show. Use it as a tool for discussion and navigation on Mobile, Laptop, Sales. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Faced By Organization Previous Financial Year Information System Security And Risk Administration
Cyber Attacks Faced By Organization Previous Financial Year Information System Security And Risk AdministrationThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Deliver an outstanding presentation on the topic using this Cyber Attacks Faced By Organization Previous Financial Year Information System Security And Risk Administration. Dispense information and present a thorough explanation of Organization Experienced, Increasing A Rapid Rate, Financial Year using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Doughnut Chart Information System Security And Risk Administration Plan Ppt Styles Files
Doughnut Chart Information System Security And Risk Administration Plan Ppt Styles FilesPresent the topic in a bit more detail with this Doughnut Chart Information System Security And Risk Administration Plan Ppt Styles Files. Use it as a tool for discussion and navigation on Doughnut Chart, Product. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial Information System Security And Risk Administration Plan Ppt Styles Slides
Financial Information System Security And Risk Administration Plan Ppt Styles SlidesPresent the topic in a bit more detail with this Financial Information System Security And Risk Administration Plan Ppt Styles Slides. Use it as a tool for discussion and navigation on Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information System Security And Risk Administration Plandashboard For Data Security Risk Management
Information System Security And Risk Administration Plandashboard For Data Security Risk ManagementThis slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Present the topic in a bit more detail with this Information System Security And Risk Administration Plandashboard For Data Security Risk Management. Use it as a tool for discussion and navigation on Enterprise Risk, Risks By Objectives, Data Protection Findings. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Market Growth Of Information Security Industry Information System Security And Risk Administration Plan
Market Growth Of Information Security Industry Information System Security And Risk Administration PlanThis slide showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compounded annual growth rate of industry. Present the topic in a bit more detail with this Market Growth Of Information Security Industry Information System Security And Risk Administration Plan. Use it as a tool for discussion and navigation on Security Market Growth, Global Information Security, Security Industry. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Rising Number Of Information Security Attacks Information System Security And Risk Administration Plan
Rising Number Of Information Security Attacks Information System Security And Risk Administration PlanThis slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection. Deliver an outstanding presentation on the topic using thisRising Number Of Information Security Attacks Information System Security And Risk Administration Plan. Dispense information and present a thorough explanation of Financial Years, Cyber Attacks, Information Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
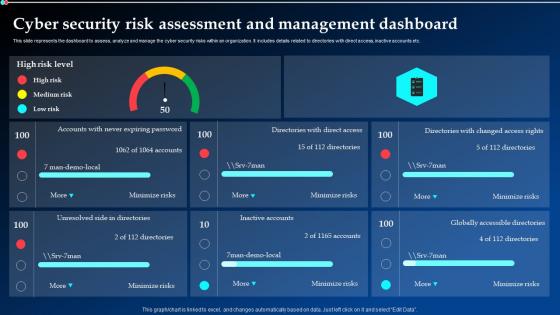 Cyber Security Risk Assessment And Management Dashboard Ppt Portrait
Cyber Security Risk Assessment And Management Dashboard Ppt PortraitThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Dashboard Ppt Portrait. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
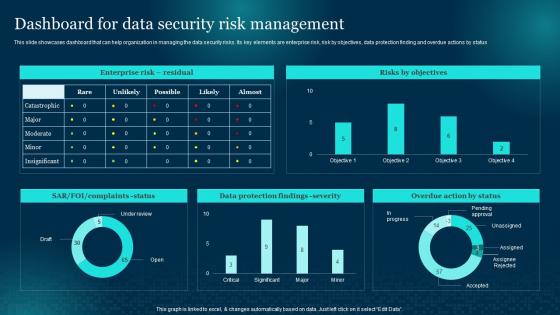 Dashboard For Data Security Risk Management Cybersecurity Risk Analysis And Management Plan
Dashboard For Data Security Risk Management Cybersecurity Risk Analysis And Management PlanThis slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status Present the topic in a bit more detail with this Dashboard For Data Security Risk Management Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Dashboard, Security, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
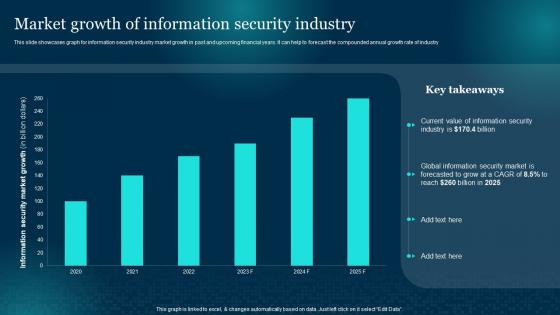 Market Growth Of Information Security Industry Cybersecurity Risk Analysis And Management Plan
Market Growth Of Information Security Industry Cybersecurity Risk Analysis And Management PlanThis slide showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compounded annual growth rate of industry Deliver an outstanding presentation on the topic using this Market Growth Of Information Security Industry Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Growth, Information, Security Industry using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
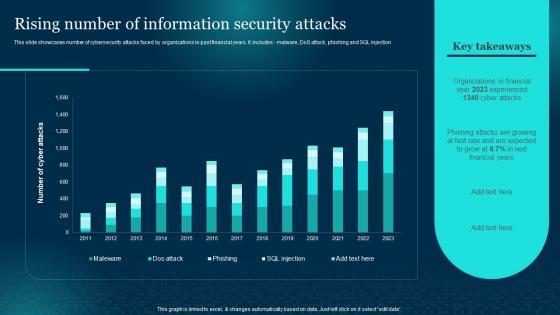 Rising Number Of Information Security Attacks Cybersecurity Risk Analysis And Management Plan
Rising Number Of Information Security Attacks Cybersecurity Risk Analysis And Management PlanThis slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection Present the topic in a bit more detail with this Rising Number Of Information Security Attacks Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Information, Security Attacks, Organizations. This template is free to edit as deemed fit for your organization. Therefore download it now.





