Powerpoint Templates and Google slides for Prevents Attacks
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Prevention of Cyber Attacks Training Ppt
Prevention of Cyber Attacks Training PptPresenting Training Deck on Prevention of Cyber Attacks. This deck comprises of 88 slides. Each slide is well crafted and designed by our PowerPoint experts. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed business presentation, add your content, and present it with confidence.
-
 Implementing Security Awareness Training To Prevent Cyber Attacks Powerpoint Presentation Slides
Implementing Security Awareness Training To Prevent Cyber Attacks Powerpoint Presentation SlidesEnthrall your audience with this Implementing Security Awareness Training To Prevent Cyber Attacks Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising senenty five slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Social Engineering Attacks Prevention For Businesses Powerpoint Presentation Slides
Social Engineering Attacks Prevention For Businesses Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Social Engineering Attacks Prevention For Businesses Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fifty eight slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Security Plan To Prevent Cyber Attacks Powerpoint Presentation Slides
Security Plan To Prevent Cyber Attacks Powerpoint Presentation SlidesDeliver an informational PPT on various topics by using this Security Plan To Prevent Cyber Attacks Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with forty slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
-
 Email Based Phishing Attacks Prevention IT Powerpoint Ppt Template Bundles
Email Based Phishing Attacks Prevention IT Powerpoint Ppt Template BundlesDeliver a credible and compelling presentation by deploying this Email Based Phishing Attacks Prevention IT Powerpoint Ppt Template Bundles. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The twenty seven slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Email Based Phishing Attacks Prevention It Powerpoint Ppt Template Bundles PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
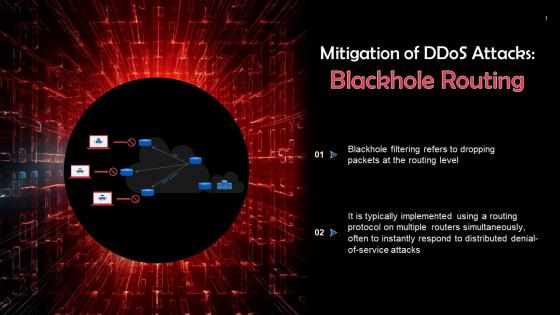 Blackhole Routing To Prevent Password Attacks Training Ppt
Blackhole Routing To Prevent Password Attacks Training PptPresenting Blackhole Routing to Prevent Password Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Rate Limiting To Prevent DDoS Attacks Training Ppt
Rate Limiting To Prevent DDoS Attacks Training PptPresenting Rate Limiting to Prevent DDoS Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Anycast Network Diffusion To Prevent DDoS Attacks Training Ppt
Anycast Network Diffusion To Prevent DDoS Attacks Training PptPresenting Anycast Network Diffusion to Prevent DDoS Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Web Application Firewalls Wafs To Prevent Password Attacks Training Ppt
Web Application Firewalls Wafs To Prevent Password Attacks Training PptPresenting Web Application Firewalls WAFs to Prevent Password Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
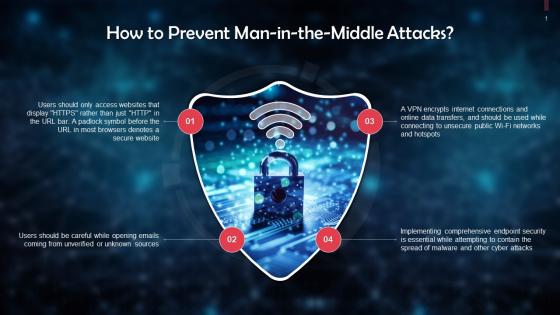 Prevention Of Man In The Middle Attacks Training Ppt
Prevention Of Man In The Middle Attacks Training PptPresenting Prevention of Man in the Middle Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
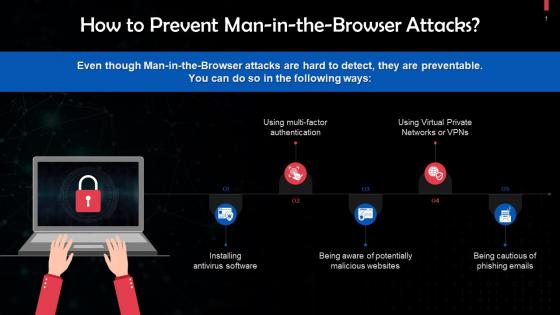 Preventing Man In The Browser Attacks Training Ppt
Preventing Man In The Browser Attacks Training PptPresenting Preventing Man-in-the-Browser Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Ways To Prevent A Cryptojacking Attack Training Ppt
Ways To Prevent A Cryptojacking Attack Training PptPresenting Ways to Prevent a Cryptojacking Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Tips To Prevent Phishing Attacks Training Ppt
Tips To Prevent Phishing Attacks Training PptPresenting Tips to Prevent Phishing Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Tips To Prevent Password Attacks Training Ppt
Tips To Prevent Password Attacks Training PptPresenting Tips to Prevent Password Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Setting Strong Passwords To Prevent Password Attacks Training Ppt
Setting Strong Passwords To Prevent Password Attacks Training PptPresenting Setting Strong Passwords to Prevent Password Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Password Training In Organizations To Prevent Password Attacks Training Ppt
Password Training In Organizations To Prevent Password Attacks Training PptPresenting Password Training in Organizations to Prevent Password Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Multi Factor Authentication To Prevent Password Attacks Training Ppt
Multi Factor Authentication To Prevent Password Attacks Training PptPresenting Multi Factor Authentication to Prevent Password Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Using A Password Manager To Prevent Password Attacks Training Ppt
Using A Password Manager To Prevent Password Attacks Training PptPresenting Using a Password Manager to Prevent Password Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Passive Attacks And How To Prevent Them Training Ppt
Passive Attacks And How To Prevent Them Training PptPresenting Passive Attacks and How to Prevent them. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Prevention Of 51 Percent Attack On Blockchain Technology Training Ppt
Prevention Of 51 Percent Attack On Blockchain Technology Training PptPresenting Prevention of 51 percent Attack on Blockchain Technology. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Strategies To Prevent Routing Attacks In Blockchain Technology Training Ppt
Strategies To Prevent Routing Attacks In Blockchain Technology Training PptPresenting Strategies to Prevent Routing Attacks in Blockchain Technology. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Preventive Measures To Protect Blockchain From User Wallet Attacks Training Ppt
Preventive Measures To Protect Blockchain From User Wallet Attacks Training PptPresenting Preventive Measures to Protect Blockchain from User Wallet Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Download this professionally designed business presentation, add your content, and present it with confidence.
-
 Prevention From Sybil Attack On Blockchain Network Training Ppt
Prevention From Sybil Attack On Blockchain Network Training PptPresenting Prevention from Sybil Attack on Blockchain Network. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Download this professionally designed business presentation, add your content, and present it with confidence.
-
 Data Breach Prevention Potential Causes For Data Breach Attacks
Data Breach Prevention Potential Causes For Data Breach AttacksThis slide highlights the reasons behind the success of data breach attacks. These include unintentional data leakage, data in motion, malware, ransomware, phishing, keystroke recording, password guessing, SQL Structured Query Language injections, etc. Increase audience engagement and knowledge by dispensing information using Data Breach Prevention Potential Causes For Data Breach Attacks. This template helps you present information on eight stages. You can also present information on Unintentional Data Leakage, Keystrokes Recording, Password Guessing, Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Attacks Faced By Organization Security Plan To Prevent Cyber
Cyber Attacks Faced By Organization Security Plan To Prevent CyberThis slide provides information regarding the number of cyber attacks faced by the organization and its impact on IT operations and system downtime. It also provides details of percentage rise in such attacks since last month. Present the topic in a bit more detail with this Cyber Attacks Faced By Organization Security Plan To Prevent Cyber. Use it as a tool for discussion and navigation on Cyber Attacks, IT Operations, System Downtime. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Plan To Prevent Cyber Dashboard For Tracking Cyber Attack Risk Levels
Security Plan To Prevent Cyber Dashboard For Tracking Cyber Attack Risk LevelsThe slide represents the dashboard for tracking cyber attack risk levels. It includes information regarding the multiple threat agents, attack methods, preventive controls along with details of risk score and infected systems. Present the topic in a bit more detail with this Security Plan To Prevent Cyber Dashboard For Tracking Cyber Attack Risk Levels. Use it as a tool for discussion and navigation on Infrastructure Controls, Preventive Controls, Detective Controls. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Plan To Prevent Cyber Dashboard To Monitor Cyber Attack Incidents
Security Plan To Prevent Cyber Dashboard To Monitor Cyber Attack IncidentsThis slide indicates the dashboard to monitor cyber attacks on IT assets of the firm. It includes information regarding the total cyber attack incidents both month and day wise along with the details of threat class, overall risk factor and top vulnerabilities. Deliver an outstanding presentation on the topic using this Security Plan To Prevent Cyber Dashboard To Monitor Cyber Attack Incidents. Dispense information and present a thorough explanation of Dashboard To Monitor, Cyber Attacks, IT Assets Of The Firm, Risk Factor And Top Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Plan To Prevent Cyber Summary Of Key Cyber Attacks Occurred
Security Plan To Prevent Cyber Summary Of Key Cyber Attacks OccurredThis slide shows the summary of key of cybers attacks occurred in organization such as phishing, malware attack, denial of service, SQL injections, identity thefts. It also contains details of the cyber attacker origin such as inadvertent actors, malicious insiders. Present the topic in a bit more detail with this Security Plan To Prevent Cyber Summary Of Key Cyber Attacks Occurred. Use it as a tool for discussion and navigation on Cybers Attacks, Phishing, Malware Attack, Denial Of Service, SQL Injections, Malicious Insiders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Password Attack Prevention Strategies Improving IoT Device Cybersecurity IoT SS
IoT Password Attack Prevention Strategies Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to highlight Internet of Things IoT password attack prevention measures. The techniques outlined in slide are limit public information, verifying the source, and no sharing of password. Deliver an outstanding presentation on the topic using this IoT Password Attack Prevention Strategies Improving IoT Device Cybersecurity IoT SS. Dispense information and present a thorough explanation of Information, Verify, Password using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ransomware In Digital Age Best Practices To Prevent Ransomware Attacks
Ransomware In Digital Age Best Practices To Prevent Ransomware AttacksThis slide highlights the best practices to prevent ransomware attacks by performing certain security checks such as backup your data, keep all system and software updated . it also referring that how make your system secure. Present the topic in a bit more detail with this Ransomware In Digital Age Best Practices To Prevent Ransomware Attacks. Use it as a tool for discussion and navigation on Backup Your Data, Install Antivirus Software And Firewalls, Prevent Ransomware Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attacks Prevention Budget For Social Engineering Awareness Training
Social Engineering Attacks Prevention Budget For Social Engineering Awareness TrainingThis slide shows the cost breakup of social engineering awareness training program. The purpose of this slide is to highlight the estimated cost of various training components, such as instructors cost, training material cost, etc. Deliver an outstanding presentation on the topic using this Social Engineering Attacks Prevention Budget For Social Engineering Awareness Training. Dispense information and present a thorough explanation of Social Engineering Awareness, Training Program, Training Components, Training Material Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Attacks Prevention Classification Of Social Engineering Attack Targets
Social Engineering Attacks Prevention Classification Of Social Engineering Attack TargetsThis slide outlines the various targets of social engineering scams. The major components include people with lack of knowledge, new employees, famous people, middle and senior management, bank system, vehicle systems, IT firms, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Attacks Prevention Classification Of Social Engineering Attack Targets. This template helps you present information on four stages. You can also present information on Targets Of Social Engineering Attacks, Organizations And Companies, Social Engineering Attack Targets using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Attacks Prevention Social Engineering Attacks Experienced By Major Business
Social Engineering Attacks Prevention Social Engineering Attacks Experienced By Major BusinessThis slide depicts the statistics of social engineering scams in top IT players. The purpose of this slide is to outline the number of social engineering attacks happened in popular business firms, such as Microsoft, Facebook, WhatsApp, PayPal, Google, etc. Present the topic in a bit more detail with this Social Engineering Attacks Prevention Social Engineering Attacks Experienced By Major Business. Use it as a tool for discussion and navigation on Social Engineering Attacks Experienced, Social Engineering Scams, Major Business Players. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attacks Prevention Targeted Industries Of Social Engineering Attacks
Social Engineering Attacks Prevention Targeted Industries Of Social Engineering AttacksThis slide represents the statistics of most targeted industries of social engineering scams. The purpose of this slide is to outline the various sectors which are more prone to such attacks. These industries are retail, manufacturing, food and beverage, tech, etc. Present the topic in a bit more detail with this Social Engineering Attacks Prevention Targeted Industries Of Social Engineering Attacks. Use it as a tool for discussion and navigation on Targeted Industries, Social Engineering Attacks, Manufacturing, Food And Beverage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attacks Reported In Previous Financial Year Social Engineering Attacks Prevention
Social Engineering Attacks Reported In Previous Financial Year Social Engineering Attacks PreventionThis slide represents the statistics of different types of social engineering scams. The purpose of this slide is to outline the various social engineering attacks reported in last year, such as hacking attempts, malware, phishing, insider theft, watering hole, etc. Present the topic in a bit more detail with this Social Engineering Attacks Reported In Previous Financial Year Social Engineering Attacks Prevention. Use it as a tool for discussion and navigation on Social Engineering Attacks, Phishing, Insider Theft, Watering Hole. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attacks Tracking Dashboard Social Engineering Attacks Prevention
Social Engineering Attacks Tracking Dashboard Social Engineering Attacks PreventionDeliver an outstanding presentation on the topic using this Social Engineering Attacks Tracking Dashboard Social Engineering Attacks Prevention. Dispense information and present a thorough explanation of Social Engineering Attacks, Tracking Dashboard, Organization Health Risk, Improvement Curve using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention And Mitigation Checklist For Responding To A Data Breach Attack
Data Breach Prevention And Mitigation Checklist For Responding To A Data Breach AttackThis slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc. Present the topic in a bit more detail with this Data Breach Prevention And Mitigation Checklist For Responding To A Data Breach Attack. Use it as a tool for discussion and navigation on Data Breach Response Plan, Fundamental Approaches, Systems Or Networks, Perform A Formal Risk Assessment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Prevention And Mitigation Common Data Breach Attack Vectors
Data Breach Prevention And Mitigation Common Data Breach Attack VectorsThis slide represents several data breach attack vectors. The main components are stolen or compromised credentials, social engineering attacks, ransomware, system vulnerabilities, human error and IT failures, physical or site security errors, etc. Deliver an outstanding presentation on the topic using this Data Breach Prevention And Mitigation Common Data Breach Attack Vectors. Dispense information and present a thorough explanation of Brute Force Attacks, Purchasing Stolen Credentials, Phishing Scams, Fraudulent Emails, Deceptive Websites using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention And Mitigation Data Breach Attacks Experienced By Major Business
Data Breach Prevention And Mitigation Data Breach Attacks Experienced By Major BusinessThis slide highlights the top data breach victims based on different industrial sectors. These industries include email service providers, social media websites, online auction websites, retail services, government agencies, file-sharing and hosting services, etc. Present the topic in a bit more detail with this Data Breach Prevention And Mitigation Data Breach Attacks Experienced By Major Business. Use it as a tool for discussion and navigation on Heartland Payment Systems, Email Service Provider, Social Media Website, Online Auction Website. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Prevention And Mitigation Different Modes Of Data Breach Attack
Data Breach Prevention And Mitigation Different Modes Of Data Breach AttackThis slide discusses the unintentional and intentional methods of data breach attacks. The examples outlined in this slide are accessing unsecured websites, downloading compromised software, losing work devices in a public place, etc. Deliver an outstanding presentation on the topic using this Data Breach Prevention And Mitigation Different Modes Of Data Breach Attack. Dispense information and present a thorough explanation of Unintentional And Intentional Methods, Data Breach Attacks, Unsecured Websites, Downloading Compromised Software, Losing Work Devices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention Major Consequences Of Data Breach Cyber Attack
Data Breach Prevention Major Consequences Of Data Breach Cyber AttackThis slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss. Introducing Data Breach Prevention Major Consequences Of Data Breach Cyber Attack to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Intellectual Property Loss, Financial Loss, Reputational Damage, Legal Consequences, using this template. Grab it now to reap its full benefits.
-
 Data Breach Prevention Phases Of Data Breach Attack Cycle
Data Breach Prevention Phases Of Data Breach Attack CycleThis slide represents the flow diagram of the data breach attack cycle. The major components of this slide are research, stage attack, exfiltrate, social engineering, attacker, weak infrastructure, database, server, accessed data, HTTP, FTP, email, etc. Deliver an outstanding presentation on the topic using this Data Breach Prevention Phases Of Data Breach Attack Cycle. Dispense information and present a thorough explanation of Infrastructure Weakness, Accessed Data, Social Engineering, Attacker Transfers Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention Vulnerabilities Targeted In Data Breach Attacks
Data Breach Prevention Vulnerabilities Targeted In Data Breach AttacksThe purpose of this slide is to discuss the most vulnerable target points of data breach attacks. The significant vulnerabilities include weak credentials, stolen information, compromised assets, payment card fraud, third-party access, mobile devices, etc. Increase audience engagement and knowledge by dispensing information using Data Breach Prevention Vulnerabilities Targeted In Data Breach Attacks. This template helps you present information on five stages. You can also present information on Payment Card Fraud, Mobile Devices, Weak Credentials, Compromised Assets, Data Breach Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Breach Prevention Working Steps Of Data Breach Attack Cycle
Data Breach Prevention Working Steps Of Data Breach Attack CycleThis slide explains the phases of the data breach attack cycle to gain unauthorized access to sensitive information. The steps involved are reconnaissance, intrusion and presence, lateral migration, using data for personal benefits, demanding a ransom, etc. Introducing Data Breach Prevention Working Steps Of Data Breach Attack Cycle to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reconnaissance, Intrusion And Presence, Lateral Migration, Exfiltration , using this template. Grab it now to reap its full benefits.
-
 Agenda For Security Plan To Prevent Cyber Attacks Ppt Icon Design Inspiration
Agenda For Security Plan To Prevent Cyber Attacks Ppt Icon Design InspirationIntroducing Agenda For Security Plan To Prevent Cyber Attacks Ppt Icon Design Inspiration to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Risk Assessment, Attacks Frequency, Assessment Program For Organization, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Security Plan To Prevent Cyber Attacks Ppt Icon Elements
Icons Slide Security Plan To Prevent Cyber Attacks Ppt Icon ElementsPresenting our well crafted Icons Slide Security Plan To Prevent Cyber Attacks Ppt Icon Elements set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly.
-
 Security Plan To Prevent Cyber Key Approaches To Minimize Cyber Attacks Risks
Security Plan To Prevent Cyber Key Approaches To Minimize Cyber Attacks RisksThis slide indicates the key approaches to minimize the risk associated with cyber attacks. The approaches discussed are update and upgrade outdated software, control accounts access, introduce signed software execution policies, regularly track network intrusions and use multifactor authentication. Increase audience engagement and knowledge by dispensing information using Security Plan To Prevent Cyber Key Approaches To Minimize Cyber Attacks Risks. This template helps you present information on five stages. You can also present information on Use Multifactor Authentication, Regularly Track Network Intrusions, Control Accounts Access using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Plan To Prevent Cyber Major Cyber Attacks Faced By Organization
Security Plan To Prevent Cyber Major Cyber Attacks Faced By OrganizationThis purpose of this slide is to showcase the major cyber attacks faced by business organization. The key attacks listed are phishing, malware attack, denial of service attacks, SQL injections, and ransomware. It also provides details regarding the major IT assets impacted and primary objective of each of the attacks. Introducing Security Plan To Prevent Cyber Major Cyber Attacks Faced By Organization to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Network And Application Infrastructure, Database Servers, Cause Operational Disruption, using this template. Grab it now to reap its full benefits.
-
 Security Plan To Prevent Cyber Mapping Of Multiple Cyber Attacks Using Risk Heat Map
Security Plan To Prevent Cyber Mapping Of Multiple Cyber Attacks Using Risk Heat MapThis slide shows the mapping of cyber attacks based on the likelihood of risk occurrence and its impact. It also contains details of attacks segmentation and the control actions that must be taken such as track, monitor and mitigate against such cyber attacks. Deliver an outstanding presentation on the topic using this Security Plan To Prevent Cyber Mapping Of Multiple Cyber Attacks Using Risk Heat Map. Dispense information and present a thorough explanation of Cyber Attacks, Risk Occurrence, Attacks Segmentation, Monitor And Mitigate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Plan To Prevent Cyber Risk Register To Measure Cyber Attacks Vulnerabilities
Security Plan To Prevent Cyber Risk Register To Measure Cyber Attacks VulnerabilitiesThis slide indicates the risk register to measure the cyber attack risk vulnerabilities faced by an organization. It includes information regarding the multiple risks in terms of vulnerability exploited, impact level, likelihood of occurrence and control recommended. Present the topic in a bit more detail with this Security Plan To Prevent Cyber Risk Register To Measure Cyber Attacks Vulnerabilities. Use it as a tool for discussion and navigation on Financial Transactions, Credentials Compromised, Cloud Network, Compromised. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Plan To Prevent Cyber Strategic Plan To Mitigate Cyber Attacks
Security Plan To Prevent Cyber Strategic Plan To Mitigate Cyber AttacksThe slide indicates the risk mitigation plan for the multiple cyber attacks. It also includes details of cost involved and implementation time required for each mitigation approach. Increase audience engagement and knowledge by dispensing information using Security Plan To Prevent Cyber Strategic Plan To Mitigate Cyber Attacks. This template helps you present information on four stages. You can also present information on Cybersecurity Attacks, Recommended Mitigation Strategy, Strategy Implementation Time Required using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents For Security Plan To Prevent Cyber Attacks
Table Of Contents For Security Plan To Prevent Cyber AttacksIntroducing Table Of Contents For Security Plan To Prevent Cyber Attacks to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Risk Assessment Program, Cyber Attacks Identification, Cyber Attacks Faced By Organization, Cyber Attacks Risk Assessment, using this template. Grab it now to reap its full benefits.
-
 Cyber Attack Prevention Plan In Powerpoint And Google Slides Cpb
Cyber Attack Prevention Plan In Powerpoint And Google Slides CpbPresenting Cyber Attack Prevention Plan In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Attack Prevention Plan. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 K103 Identification And Prevention Of Spear Phishing Attacks And Strategies To Mitigate Them V2
K103 Identification And Prevention Of Spear Phishing Attacks And Strategies To Mitigate Them V2This slide talks about the various methods of identifying spear phishing cyber attacks. The purpose of this slide is to help users prevent spear phishing scams. The key signs include unusual request, shared drive links and documents with password protection. Introducing K103 Identification And Prevention Of Spear Phishing Attacks And Strategies To Mitigate Them V2 to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing Cyber Attacks, Prevent Spear Phishing Scams, Password Protection, Identification And Prevention, using this template. Grab it now to reap its full benefits.
-
 K104 Preventive Measures To Avoid Evil Twin Scams Phishing Attacks And Strategies To Mitigate Them V2
K104 Preventive Measures To Avoid Evil Twin Scams Phishing Attacks And Strategies To Mitigate Them V2This slide outlines the various preventive measures to avoid evil twin attacks. The key steps include use your own hotspot, avoid unsecured wi-fis, disable auto-connect, avoid logging into private accounts on public Wi-Fi, use VPN, visit HTTPS websites, etc. Increase audience engagement and knowledge by dispensing information using K104 Preventive Measures To Avoid Evil Twin Scams Phishing Attacks And Strategies To Mitigate Them V2. This template helps you present information on six stages. You can also present information on Avoid Evil Twin Scams, Personal Information, Preventive Measures, Hackers Accessing Your Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 K105 Preventive Measures To Avoid Watering Hole Phishing Attacks And Strategies To Mitigate Them V2
K105 Preventive Measures To Avoid Watering Hole Phishing Attacks And Strategies To Mitigate Them V2This slide outlines the various preventive measures to avoid watering hole phishing attacks. The purpose of this slide is to help in protecting users from watering hole scams. The key steps include vulnerability scanning, security patches, input validation, etc. Introducing K105 Preventive Measures To Avoid Watering Hole Phishing Attacks And Strategies To Mitigate Them V2 to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability Scanning, Security Patches, Bug Bounty Programs, Input Validation, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Clone Phishing Attacks Preventive Measures
Phishing Attacks And Strategies To Mitigate Them V2 Clone Phishing Attacks Preventive MeasuresThis slide talks about the various steps that can be taken to prevent clone phishing attacks. These include review senders address, preview links before opening them, use a password manager, investigate spoofed replies, double check URL addresses, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Clone Phishing Attacks Preventive Measures. This template helps you present information on eight stages. You can also present information on Investigate Spoofed Replies, Clone Phishing Attacks Preventive, Resemble Authentic Email Addresses using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Identification And Prevention Of Angler Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Identification And Prevention Of Angler PhishingThis slide talks about the various methods of identifying angler phishing cyber attacks. The purpose of this slide is to help users identify angler phishing scams. These include notifications, abnormal direct messages, links to the different websites, etc. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Identification And Prevention Of Angler Phishing. Use it as a tool for discussion and navigation on Identification And Prevention, Angler Phishing Scams, Abnormal Direct Messages, Credentials In Direct Messages. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Preventive Measures For Man In The Middle Cyber
Phishing Attacks And Strategies To Mitigate Them V2 Preventive Measures For Man In The Middle CyberThis slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Preventive Measures For Man In The Middle Cyber to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Secure Connections, Avoid Phishing Emails, Endpoint Security, Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Prevention Email Signing And Code
Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Prevention Email Signing And CodeThis slide talks about the techniques which can help in protecting organizations from phishing and vishing attacks. The purpose of this slide is to explain two important methods of preventing cyber scams. These techniques are email signing and code signing. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Prevention Email Signing And Code. Dispense information and present a thorough explanation of Vishing Attacks Prevention, Email Signing And Code Signing, Preventing Cyber Scams using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.




