Powerpoint Templates and Google slides for Model Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Technical Security Control Model With Isk Management Guide For Information Technology Systems
Technical Security Control Model With Isk Management Guide For Information Technology SystemsThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver an outstanding presentation on the topic using this Technical Security Control Model With Isk Management Guide For Information Technology Systems. Dispense information and present a thorough explanation of Technical Security, Control Model, Supporting Technical, Control Function using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Model For Information Technology Security Risk Management
Model For Information Technology Security Risk ManagementThis slide shows the model that depicts IT security risk management which focuses on identification, protection, detection, response and recovery planning with security asset management, governance, data security, detection processes, risk analysis and planning, etc. Introducing Model For Information Technology Security Risk Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Identifying, Protecting, Detecting, using this template. Grab it now to reap its full benefits.
-
 Addressing Mobile Device Management Model Enterprise Mobile Security For On Device
Addressing Mobile Device Management Model Enterprise Mobile Security For On DeviceThis slide provides information regarding various mobile device management models such as BYOD, COPE, COBO, COSU that can be selected by vendor based on requirement.Increase audience engagement and knowledge by dispensing information using Addressing Mobile Device Management Model Enterprise Mobile Security For On Device. This template helps you present information on four stages. You can also present information on Professional Purpose, Owned Personally, Permitted Tasks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
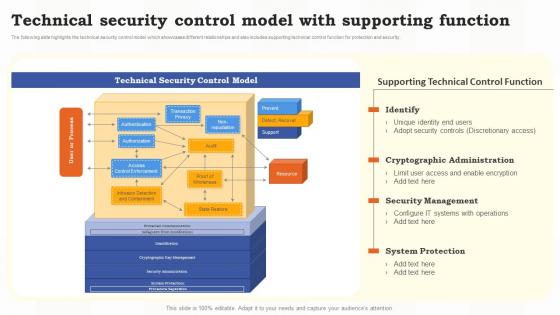 Technical Security Control Model With Supporting Function Risk Assessment Of It Systems
Technical Security Control Model With Supporting Function Risk Assessment Of It SystemsThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver an outstanding presentation on the topic using this Technical Security Control Model With Supporting Function Risk Assessment Of It Systems. Dispense information and present a thorough explanation of Technical, Security Management, System Protection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Types Of Web Application Firewall Security Models Ppt Styles Graphics Design
Types Of Web Application Firewall Security Models Ppt Styles Graphics DesignThis slide represents the various types of WAF security models, including the whitelist or negative security model, blacklist or positive security model, and hybrid security model. Deliver an outstanding presentation on the topic using this Types Of Web Application Firewall Security Models Ppt Styles Graphics Design. Dispense information and present a thorough explanation of Web Application, Firewall Security Models using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Service Delivery Models Anything As A Service Ppt File Background Designs
Security Service Delivery Models Anything As A Service Ppt File Background DesignsThis slide shows the security service delivery models, including on premise security, managed security, and security as a service and method of provided services. Deliver an outstanding presentation on the topic using this Security Service Delivery Models Anything As A Service Ppt File Background Designs. Dispense information and present a thorough explanation of Security Service, Allocation Of Dedicated, Resources Long Term, Relationship using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incident Response Lifecycle Model
Cyber Security Incident Response Lifecycle ModelThis slide covers cyber security incident response lifecycle model. It involves stages such as prepare, identify, eradicate, contain and recover. Introducing our Cyber Security Incident Response Lifecycle Model set of slides. The topics discussed in these slides are Identify, Contain, Eradicate, Digital Forensics. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Naas And Secure Access Service Edge Sase Naas Service Models Ppt Powerpoint Presentation Pictures Themes
Naas And Secure Access Service Edge Sase Naas Service Models Ppt Powerpoint Presentation Pictures ThemesThis slide talks about the relationship between network as a service and secure access service edge.The SAFE provides DNS filtering, secure web gateway, anti malware, file sandboxing, cloud delivered firewall, app visibility and control, and so on.Introducing Naas And Secure Access Service Edge Sase Naas Service Models Ppt Powerpoint Presentation Pictures Themes to increase your presentation threshold.Encompassed with two stages, this template is a great option to educate and entice your audience.Dispence information on Performance Optimization, Secure Direct, Loss Prevention, using this template.Grab it now to reap its full benefits.
-
 Business Data Security Management Model
Business Data Security Management ModelThis slide covers business data security management model which includes Defining, executing and measuring security controls. Introducing our Business Data Security Management Model set of slides. The topics discussed in these slides are Business Data, Security, Management Model. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Technology Replacement Model For Business Network Security
Technology Replacement Model For Business Network SecurityThis slide covers technology replacement model for business network security which includes smart infrastructure, interoperable solutions, organizational capability for risk mitigation, secure network with standalone products. Introducing our premium set of slides with name Technology Replacement Model For Business Network Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Interoperable Solutions, Secured Business, Standalone Products. So download instantly and tailor it with your information.
-
 Addressing Mobile Device Management Model For Enterprise Unified Endpoint Security
Addressing Mobile Device Management Model For Enterprise Unified Endpoint SecurityThis slide provides information regarding various mobile device management models such as BYOD, COPE, COBO, COSU that can be selected by vendor based on requirement. Increase audience engagement and knowledge by dispensing information using Addressing Mobile Device Management Model For Enterprise Unified Endpoint Security. This template helps you present information on four stages. You can also present information on Equipment Personal, Devices Professional, Employees Personal using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Model In Powerpoint And Google Slides Cpb
Secure Model In Powerpoint And Google Slides CpbPresenting our Secure Model In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Secure Model This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Agenda For Information System Security And Risk Administration Plan Ppt Styles Model
Agenda For Information System Security And Risk Administration Plan Ppt Styles ModelIntroducing Agenda For Information System Security And Risk Administration Plan Ppt Styles Model to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Information System Security, Current Information Security, Information Security Risks, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Handling Checklist Ppt Powerpoint Presentation Model Introduction
Cyber Security Incident Handling Checklist Ppt Powerpoint Presentation Model IntroductionThis slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post incident activity. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Handling Checklist Ppt Powerpoint Presentation Model Introduction. This template helps you present information on one stage. You can also present information on Detection And Analysis, Containment, Eradication And Recovery using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Response Process Flow Chart Ppt Powerpoint Presentation Model File Formats
Cyber Security Incident Response Process Flow Chart Ppt Powerpoint Presentation Model File FormatsThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Deliver an outstanding presentation on the topic using this Cyber Security Incident Response Process Flow Chart Ppt Powerpoint Presentation Model File Formats. Dispense information and present a thorough explanation of Instrumentation, Agency User Reporting, Cyber Threat Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Security Operation Model To Build Secure Organization
Enterprise Security Operation Model To Build Secure OrganizationThis slide covers enterprise security operation model to build secure organization. It involves regulatory requirements, customer expectations, industry forums and internal business demands. Introducing our premium set of slides with Enterprise Security Operation Model To Build Secure Organization. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Regulatory Requirements, Customer Expectations, Industry Norms. So download instantly and tailor it with your information.
-
 Threat Modeling Process For Secure Data Assets
Threat Modeling Process For Secure Data AssetsThis slide shows threat modeling to protect business assets from risks. It contains two phases discovery and implementation that includes steps such as identify assets, analyze attack surface, attack vectors, analyze, prioritize and develop controls. Introducing our premium set of slides with name Threat Modeling Process For Secure Data Assets. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Hackers Path, Identified Assets, Threat Routes. So download instantly and tailor it with your information.
-
 Threat Modelling Process Of Cyber Security Program
Threat Modelling Process Of Cyber Security ProgramThis slide shows threat modelling process to identify gaps and improve efficiency of cyber security program. It contains five steps select digital asset, identify attack scenarios, evaluate existing controls, assess residual risks and construct business case. Presenting our set of slides with name Threat Modelling Process Of Cyber Security Program. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Threat Modelling, Cyber Security, Assess Residual Risk .
-
 6 Level Cyber Security Strategy Maturity Model
6 Level Cyber Security Strategy Maturity ModelThis slide represent 6 level cyber security strategy maturity model illustrating levels such as initial, developing, defined, managed, optimization and unified. Presenting our well structured 6 Level Cyber Security Strategy Maturity Model. The topics discussed in this slide are Cyber Security, Strategy, Maturity Model. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 OT Cyber Security Strategy Maturity Model
OT Cyber Security Strategy Maturity ModelThis slide represents OT cyber security strategy maturity model illustrating networking, human resource, processes, security management technology, security technology etc. Introducing our OT Cyber Security Strategy Maturity Model set of slides. The topics discussed in these slides are Security, Defense, Contain, Monitor. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Erp Assessment Model To Improve Cyber Security Performance
Erp Assessment Model To Improve Cyber Security PerformanceThis slide signifies the enterprise resource planning evaluation model to increase cyber security performance. It covers infomation about implement assessment, create optimized test and detect impact. Presenting our well structured Erp Assessment Model To Improve Cyber Security Performance. The topics discussed in this slide are Data, Assessment, Application Scanner. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Business Cyber Security Governance Model
Business Cyber Security Governance ModelThis slide showcases a framework for cyber security risk governance and management model to align business and IT objectives. It includes key components such as analysis, design, specification, implementation, testing, production, operations, etc. Presenting our set of slides with Business Cyber Security Governance Model. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Organization, Resources, Cybersecurity Governance.
-
 Cloud Security Governance Risk And Compliance Model
Cloud Security Governance Risk And Compliance ModelThe following slide presents a GRC model to manage and control cloud cyber security operations and reduce the impact of risk events. It includes key components such as governance, risk and compliance. Introducing our Cloud Security Governance Risk And Compliance Model set of slides. The topics discussed in these slides are Governance, Compliance, Update And Publish Policies. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information Security Governance Strategic Model
Information Security Governance Strategic ModelThe following slide showcases a framework presenting strategy development and implementation phase in information security governance. It includes key components such as organizational structure, value delivery, strategic alignment, resource optimization, performance measurement, etc. Presenting our set of slides with Information Security Governance Strategic Model. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Organizational Structure, Strategic Alignment, Compliance.
-
 Infrastructure As Code Workflow Security Model
Infrastructure As Code Workflow Security ModelThe following slide depicts the workflow model of infrastructure as code IaC to ensure high level security feature. It includes elements such as building infrastructure, analysis engine, console, viewing scan output, reviewing reports, drafting policies etc. Introducing our Infrastructure As Code Workflow Security Model set of slides. The topics discussed in these slides are Build Infrastructure, Code Repository, Scam Results. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Automation Model For Infrastructure As Code
Security Automation Model For Infrastructure As CodeThe following slide showcases the infrastructure as code IoC automated security framework to minimize cost and human error. It includes key elements such as development, peer review, QA, pre production, version control, bug test, security assessment etc. Introducing our Security Automation Model For Infrastructure As Code set of slides. The topics discussed in these slides are Development, Peer Review, Version Control, Production. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Data Security Architectural Solution Model
Cloud Data Security Architectural Solution ModelThis slide shows architecture solution which can be used by organizations in cloud data security. It includes web application firewall, risk detection, data detection, etc. Introducing our Cloud Data Security Architectural Solution Model set of slides. The topics discussed in these slides are Cloud Environment Security, Data Security Product, Cloud Product Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Security Shared Responsibility Business Model
Cloud Security Shared Responsibility Business ModelThis slide shows matrix which can be used by organization to develop cloud security responsibility. It includes customers data, platform, application, access management, etc. Introducing our Cloud Security Shared Responsibility Business Model set of slides. The topics discussed in these slides are Customer, Cloud Platform Provider, Software. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Five Levels Cloud Security Maturity Model
Five Levels Cloud Security Maturity ModelThis slide shows maturity model which can be used by IT managers in cloud security. These five levels are no automation, simple automation, manually executed scripts, guardrails and automation everywhere. Presenting our set of slides with Five Levels Cloud Security Maturity Model. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on No Automation, Simple Automation, Manually Executed Scripts.
-
 Introduction To Grid Computing Security Model Ppt Powerpoint Presentation Slides Design
Introduction To Grid Computing Security Model Ppt Powerpoint Presentation Slides DesignThis slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti virus management, policy management, user management, key management, and so on. Present the topic in a bit more detail with this Introduction To Grid Computing Security Model Ppt Powerpoint Presentation Slides Design. Use it as a tool for discussion and navigation on Grid Security Model, Policy Expression And Exchange, Binding Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Security Maturity Model Assessment To Improve Business Operations
Cloud Security Maturity Model Assessment To Improve Business OperationsThis slide represents cloud security maturity assessment model which helps improve cloud optimization and flexibility. It provides information regarding automation, manual scripts, managed stage and optimization. Introducing our premium set of slides with Cloud Security Maturity Model Assessment To Improve Business Operations. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Automation Optimized, Minimal Automation, Minimal Automation. So download instantly and tailor it with your information.
-
 Business Governance Model For Cryptographically Secured Services
Business Governance Model For Cryptographically Secured ServicesThis slide signifies the organisation governance model for cryptographically secured services. It includes steps like generic value network, analysis, canvas analysis and plan. Presenting our well structured Business Governance Model For Cryptographically Secured Services. The topics discussed in this slide are Cloud Services, Value Network, Business Model Canvas. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Model For Protection And Security Of Healthcare Data
Model For Protection And Security Of Healthcare DataThis slide depicts the flowchart used for explaining the process of protecting the healthcare data. The purpose of this template is to define a model used for maintaining privacy and confidentiality of health data. It includes information related to security, trust, confidentiality and privacy. Introducing our Model For Protection And Security Of Healthcare Data set of slides. The topics discussed in these slides are Security, Trust, Confidentiality, Privacy. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Supply Chain Security Management Model
Supply Chain Security Management ModelThe following slide highlights framework for supply chain security management to eliminate risks of external suppliers, vendors, logistics etc. It includes components such as managing facility, managing cargo, managing human resources, managing information and managing company. Introducing our premium set of slides with Supply Chain Security Management Model. Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Managing Cargo, Managing Information. So download instantly and tailor it with your information.
-
 Secure Payment Gateway Integration Model
Secure Payment Gateway Integration ModelThis slide represents the model showing the integration of ecommerce payment gateway which helps users to accept credit cards and do transaction checks. It includes details related to merchant, merchant bank, online consumer and client bank.Present the topic in a bit more detail with this Secure Payment Gateway Integration Model. Use it as a tool for discussion and navigation on Connection Transaction, Transaction Confirmation, Updates Related. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Three Lines Of Defense Model For Cyber Security
Three Lines Of Defense Model For Cyber SecurityThis slide represents the cyber security and governance lines of defense model. It includes functions of the three lines of defense such as policies, procedures and standards documentation, penetration testing, review policies and procedures, conduct cyber risk assessments etc. Presenting our set of slides with Three Lines Of Defense Model For Cyber Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Processes, Data Classification, Risk Assessments.
-
 It Infra Security Model To Eliminate Unauthorized User Access
It Infra Security Model To Eliminate Unauthorized User AccessThe following slide exhibits model for IT infrastructure security in order to determine tools that provide in depth defence. It presents information related to perimeter, endpoint, visibility, etc. Introducing It Infra Security Model To Eliminate Unauthorized User Access to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Perimeter, Application, Identify, using this template. Grab it now to reap its full benefits.
-
 SDN Security IT Models Of Software Defined Networking SDN
SDN Security IT Models Of Software Defined Networking SDNThis slide depicts the software defined networking models, covering open SDN, SDN by APIs, SDN overlay model and hybrid SDN. Every SDN implementation has three components that include the controller, the standard to interact with hardware devices, and switches. Introducing SDN Security IT Models Of Software Defined Networking SDN to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Software, Models, Networking, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Risk Governance Operating Model
Cyber Security Risk Governance Operating ModelThe slide showcases an operating model of cyber security risk governance to address business threats. It includes key elements like governance, risk management and compliance. Introducing our Cyber Security Risk Governance Operating Model set of slides. The topics discussed in these slides are Governance, Risk, Compliance. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Risk Governance Operating Model
Security Risk Governance Operating ModelThe following slide highlights a risk governance operating model to manage impacts of risk on IT assets. It includes key activities like risks identification, protection, detection, reaction, awareness and compliance and assurance. Presenting our set of slides with Security Risk Governance Operating Model. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information onProtection, Detection, Reaction.
-
 Phone Security Management Models For Workplace
Phone Security Management Models For WorkplaceThis slide shows phone security models for automating security framework of mobile at workplace with description, features and available market products etc. It include models such as MDM, EDM and UEM. Introducing our Phone Security Management Models For Workplace set of slides. The topics discussed in these slides are Management Type, Market Products . This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Scan Principle For Phone Security Model
Scan Principle For Phone Security ModelThis slide shows SCAN framework for securing phone against possible threats to prevent loss of business data. It include components such as system, configuration, application and network, etc. Presenting our set of slides with Scan Principle For Phone Security Model. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on System, Configuration, Network.
-
 Data Encryption Model For Effective Information Security Strategy SS
Data Encryption Model For Effective Information Security Strategy SSThis slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc.Present the topic in a bit more detail with this Data Encryption Model For Effective Information Security Strategy SS. Use it as a tool for discussion and navigation on Backup Repository, Encrypted Data, Proper Decryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Access Security Control Models Implementation Of ICT Strategic Plan Strategy SS
Key Access Security Control Models Implementation Of ICT Strategic Plan Strategy SSThis slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role based access control and attributes based access control.Deliver an outstanding presentation on the topic using this Key Access Security Control Models Implementation Of ICT Strategic Plan Strategy SS. Dispense information and present a thorough explanation of Discretionary Access, Mandatory Access, Access Granted using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Security Model To Effective Implementation Of ICT Strategic Plan Strategy SS
Network Security Model To Effective Implementation Of ICT Strategic Plan Strategy SSThis slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc.Present the topic in a bit more detail with this Network Security Model To Effective Implementation Of ICT Strategic Plan Strategy SS. Use it as a tool for discussion and navigation on Message Transformation, Secure Message, Security Breaches. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE IT Cloud Access Security Broker Implementation Models Ppt Powerpoint Template
SASE IT Cloud Access Security Broker Implementation Models Ppt Powerpoint TemplateThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Introducing SASE IT Cloud Access Security Broker Implementation Models Ppt Powerpoint Template to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on API Scanning, Forward Proxy, Reverse Proxy, using this template. Grab it now to reap its full benefits.
-
 Roles And Responsibilities Of Soc As A Service Security Model Ppt Graphics
Roles And Responsibilities Of Soc As A Service Security Model Ppt GraphicsThis slide illustrates the roles and responsibilities of the SOC as a Service security model. The purpose of this slide is to highlight the various roles and responsibilities in a SOC as a Service environment. The main roles include SOC manager, security analyst, security architecture, compliance auditor, and SOC coordinator. Introducing Roles And Responsibilities Of Soc As A Service Security Model Ppt Graphics to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Soc Manager, Security Architect, using this template. Grab it now to reap its full benefits.
-
 SecOps Security Operations Model And Incidents Management Ppt Diagrams
SecOps Security Operations Model And Incidents Management Ppt DiagramsThis slide represents the security operations model, covering the incidents managed by the security operations center. The model includes three teams such as hunters, investigators, and triage. The incidents include multi stage incidents, known campaign tracking, and high volume incidents. Deliver an outstanding presentation on the topic using this SecOps Security Operations Model And Incidents Management Ppt Diagrams. Dispense information and present a thorough explanation of Threat Intelligence, External Intelligence Sources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Security Models In Powerpoint And Google Slides Cpb
Cloud Security Models In Powerpoint And Google Slides CpbPresenting Cloud Security Models In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cloud Security Models. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Introduction To Grid Computing Security Model Grid Computing Services
Introduction To Grid Computing Security Model Grid Computing ServicesThis slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti virus management, policy management, user management, key management, and so on. Deliver an outstanding presentation on the topic using this Introduction To Grid Computing Security Model Grid Computing Services. Dispense information and present a thorough explanation of Authentication, Delegation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Icons Slide For Cloud Access Security Broker CASB Ppt Model Guidelines
Icons Slide For Cloud Access Security Broker CASB Ppt Model GuidelinesPresenting our well crafted Icons Slide For Cloud Access Security Broker CASB Ppt Model Guidelines set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly
-
 Overview Of CASB Deployment Models Cloud Access Security Broker CASB
Overview Of CASB Deployment Models Cloud Access Security Broker CASBThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out of band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Introducing Overview Of CASB Deployment Models Cloud Access Security Broker CASB. to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Deployment Models, Api Scanning, Forward Proxy, using this template. Grab it now to reap its full benefits.
-
 Requirements For Appropriate Cloud Security Model Ppt Infographic
Requirements For Appropriate Cloud Security Model Ppt InfographicThis slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. Increase audience engagement and knowledge by dispensing information using Requirements For Appropriate Cloud Security Model Ppt Infographic. This template helps you present information on five stages. You can also present information on Visibility And Threat Detection, Continuous Compliance, Data Encryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 ZTNA Features Of Zero Trust Network Access Security Model
ZTNA Features Of Zero Trust Network Access Security ModelThis slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Deliver an outstanding presentation on the topic using this ZTNA Features Of Zero Trust Network Access Security Model. Dispense information and present a thorough explanation of Security Controls, Location, Network Visibility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 ZTNA Traditional Security Models Vs Zero Trust Network Access
ZTNA Traditional Security Models Vs Zero Trust Network AccessThis slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Deliver an outstanding presentation on the topic using this ZTNA Traditional Security Models Vs Zero Trust Network Access. Dispense information and present a thorough explanation of Traditional Security Model, Static Security, Changing Environment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB API Scanning CASB Deployment Model
Cloud Access Security Broker CASB API Scanning CASB Deployment ModelThis slide outlines the overview of the API scanning model of CASB deployment. The purpose of this slide is to showcase its features and introduce APIs and how this deployment works. It also represents the architecture of the API scanning model and its components include mobile and corporate devices and APIs. Present the topic in a bit more detail with this Cloud Access Security Broker CASB API Scanning CASB Deployment Model. Use it as a tool for discussion and navigation on Features, Apis, Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB Proxy Based CASB Deployment Model
Cloud Access Security Broker CASB Proxy Based CASB Deployment ModelThis slide outlines the overview of proxy based CASB deployment. The purpose of this slide is to highlight the proxy based implementation of the CASB model and it also includes the fundamental modes of proxy deployment, including forward proxy and reverse proxy. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB Proxy Based CASB Deployment Model. Dispense information and present a thorough explanation of Standard Modes, Operation Of Several, Origin Server using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB Reverse Proxy CASB Deployment Model
Cloud Access Security Broker CASB Reverse Proxy CASB Deployment ModelThis slide outlines the overview of the reverse proxy cloud access security model broker. The purpose of this slide is to showcase overview of working and various types of reverse proxy CASB. The main types include regular reverse proxies and load balancers. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB Reverse Proxy CASB Deployment Model. Dispense information and present a thorough explanation of Overview, Internet, Reverse Proxy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Pillar Data Security Ppt Portfolio Model
Cloud Access Security Broker Pillar Data Security Ppt Portfolio ModelThis slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. Introducing Cloud Access Security Broker Pillar Data Security Ppt Portfolio Model. to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Technologies, Sophisticated, Functions, using this template. Grab it now to reap its full benefits.
-
 Strategic Model To Manage Overall It Spending Strategic Plan To Secure It Infrastructure Strategy SS V
Strategic Model To Manage Overall It Spending Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding the strategic cost prioritization model deployed by IT department in order to assess scores on various parameters such as IT control, strategic value, cost and benefit, impact on customer, and investment required, etc. Deliver an outstanding presentation on the topic using this Strategic Model To Manage Overall It Spending Strategic Plan To Secure It Infrastructure Strategy SS V. Dispense information and present a thorough explanation of Strategic, Department, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





