Powerpoint Templates and Google slides for Model Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Traditional Security Models Vs Zero Trust Network Access Identity Defined Networking
Traditional Security Models Vs Zero Trust Network Access Identity Defined NetworkingThis slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Deliver an outstanding presentation on the topic using this Traditional Security Models Vs Zero Trust Network Access Identity Defined Networking Dispense information and present a thorough explanation of Traditional Security Model, Foundation, Dependence, Visibility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Business Model Secure Email Solution Investor Funding Elevator Pitch Deck By Paubox
Business Model Secure Email Solution Investor Funding Elevator Pitch Deck By PauboxThis slide covers the business model canvas for email security software firm. It includes information about key partners, key activities, value proposition, key resources, distribution channels, customer relationships, customer segments, cost structure, revenue streams. Deliver an outstanding presentation on the topic using this Business Model Secure Email Solution Investor Funding Elevator Pitch Deck By Paubox. Dispense information and present a thorough explanation of Key Partners, Key Activities, Key Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Features Of Zero Trust Network Access Security Model Ppt File Files
Features Of Zero Trust Network Access Security Model Ppt File FilesThis slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Present the topic in a bit more detail with this Features Of Zero Trust Network Access Security Model Ppt File Files. Use it as a tool for discussion and navigation on Safeguards Private Apps, Features, Description. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Components Of Crypto Ledger Security Model
Key Components Of Crypto Ledger Security ModelThis template aims to cover core elements of crypto ledger security model for asset protection. It covers elements such as offline storage, security, trusted display, etc. Deliver an outstanding presentation on the topic using this Key Components Of Crypto Ledger Security Model. Dispense information and present a thorough explanation of Offline Storage, Security, Trusted Display using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Business Model Smart Farming Technology Pitch Deck For Food Security
Business Model Smart Farming Technology Pitch Deck For Food SecurityFollowing slide showcases business and operational model of company. It includes elements such as key partners, resources, channels, value preposition, customer relationships, segments etc. Deliver an outstanding presentation on the topic using this Business Model Smart Farming Technology Pitch Deck For Food Security Dispense information and present a thorough explanation of Value Propositions, Customer Relationship, Customer Segments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 30 60 90 Days Plan To Deploy CASB Model CASB Cloud Security
30 60 90 Days Plan To Deploy CASB Model CASB Cloud SecurityThis slide represents the 30-60-90 days plan to implement the cloud access security broker model in an organization. The purpose of this slide is to showcase the various steps to be taken to deploy CASB at the interval every 30 days. Introducing 30 60 90 Days Plan To Deploy CASB Model CASB Cloud Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on 30 60 90 Days Plan, Cloud Access Security Broker, Connect To Current Security Architecture, Security Operations Center Functions, using this template. Grab it now to reap its full benefits.
-
 Api Scanning CASB Deployment Model CASB Cloud Security
Api Scanning CASB Deployment Model CASB Cloud SecurityThis slide outlines the overview of the API scanning model of CASB deployment. The purpose of this slide is to showcase its features and introduce APIs and how this deployment works. It also represents the architecture of the API scanning model and its components include mobile and corporate devices and APIs. Deliver an outstanding presentation on the topic using this Api Scanning CASB Deployment Model CASB Cloud Security. Dispense information and present a thorough explanation of Deployment Works, Mobile And Corporate Devices, Submitting Queries Or Commands using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Future Use Of Emerging Technologies In CASB Model CASB Cloud Security
Future Use Of Emerging Technologies In CASB Model CASB Cloud SecurityThis slide gives an overview of the technologies that can be used in the cloud access security broker model in the future. The purpose of this slide is to showcase the various emerging technologies that can help CASB to grow in the future. The technologies include AI, ML, CSPM, data privacy and protection, etc. Deliver an outstanding presentation on the topic using this Future Use Of Emerging Technologies In CASB Model CASB Cloud Security. Dispense information and present a thorough explanation of Cloud Native Security Solutions, Cloud Security Posture Management, Data Privacy And Protection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview Of CASB Deployment Models CASB Cloud Security
Overview Of CASB Deployment Models CASB Cloud SecurityThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Introducing Overview Of CASB Deployment Models CASB Cloud Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Out Of Band Deployment, Inline Deployment, Terms Of Development And Operations, using this template. Grab it now to reap its full benefits.
-
 Proxy Based CASB Deployment Model CASB Cloud Security
Proxy Based CASB Deployment Model CASB Cloud SecurityThis slide outlines the overview of proxy-based CASB deployment. The purpose of this slide is to highlight the proxy-based implementation of the CASB model and it also includes the fundamental modes of proxy deployment, including forward proxy and reverse proxy. Increase audience engagement and knowledge by dispensing information using Proxy Based CASB Deployment Model CASB Cloud Security. This template helps you present information on two stages. You can also present information on Forward Proxy Mode, Reverse Proxy Mode, Login Attempts, Access Efforts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Requirements For Appropriate Cloud Security Model CASB Cloud Security
Requirements For Appropriate Cloud Security Model CASB Cloud SecurityThis slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. Introducing Requirements For Appropriate Cloud Security Model CASB Cloud Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Strong Authentication, Integrated Security, Data Encryption, Continuous Compliance, Visibility And Threat Detection, using this template. Grab it now to reap its full benefits.
-
 Reverse Proxy CASB Deployment Model CASB Cloud Security
Reverse Proxy CASB Deployment Model CASB Cloud SecurityThis slide outlines the overview of the reverse proxy cloud access security model broker. The purpose of this slide is to showcase overview of working and various types of reverse proxy CASB. The main types include regular reverse proxies and load balancers. Increase audience engagement and knowledge by dispensing information using Reverse Proxy CASB Deployment Model CASB Cloud Security. This template helps you present information on five stages. You can also present information on Reverse Proxy Cloud, Access Security Model Broker, Proxies And Load Balancers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Big Data Attack Detection Model In Cyber Security
Big Data Attack Detection Model In Cyber SecurityThis slide visualises the detection models used in defending cyber security in big data. Its aim is to detect any malicious attack. This slide includes training data, data preparation, testing, attack detection model, etc. Introducing our Big Data Attack Detection Model In Cyber Security set of slides. The topics discussed in these slides are Network, Activity, Application. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Infrastructure Security Model System
Cloud Infrastructure Security Model SystemThis slide represents the cloud infrastructure security model system. Its objective is to reach the market goals and by using business models for customers. This slide includes saas, paas, iaas. Introducing our premium set of slides with Cloud Infrastructure Security Model System. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Software, Platform, Infrastructure. So download instantly and tailor it with your information.
-
 M72 Traditional Security Models Vs Zero Trust Network Access Zero Trust Architecture ZTA
M72 Traditional Security Models Vs Zero Trust Network Access Zero Trust Architecture ZTAThis slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Deliver an outstanding presentation on the topic using this M72 Traditional Security Models Vs Zero Trust Network Access Zero Trust Architecture ZTA. Dispense information and present a thorough explanation of Factors, Traditional Security Model, ZTNA using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Testing Tools Reference Model Ppt File Infographics
Application Security Testing Tools Reference Model Ppt File InfographicsThis slide showcases the application security testing tools reference model along with the workflow. Deliver an outstanding presentation on the topic using this Application Security Testing Tools Reference Model Ppt File Infographics. Dispense information and present a thorough explanation of Software Composition Analysis, Static Application Security Testing, Dynamic Application Security Testing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Roadmap To Implement DevSecOps Pipeline Security Working Of DevSecOps Model
Strategic Roadmap To Implement DevSecOps Pipeline Security Working Of DevSecOps ModelThis slide discusses the pipeline security of DevSecOps. The purpose of this slide is to explain pipeline security and its importance in DevSecOps, which includes maximizing security personnel efficiency, automating non-intellectual tasks, improving the tracking of task statuses, and so on. Deliver an outstanding presentation on the topic using this Strategic Roadmap To Implement DevSecOps Pipeline Security Working Of DevSecOps Model. Dispense information and present a thorough explanation of Boost Workflow Efficiency, Performance Metrics, Pipeline Security Working using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Shared Security Model For Internet Of Things Internet Of Things IoT Security Cybersecurity SS
Shared Security Model For Internet Of Things Internet Of Things IoT Security Cybersecurity SSDeliver an outstanding presentation on the topic using this Shared Security Model For Internet Of Things Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of Device Management, Account Management, Configuration, Virtualization Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Web Based Software Security Stakeholder Engagement Model
Web Based Software Security Stakeholder Engagement ModelThis slide showcases SaaS security to meet business needs and ensure data management. This includes four major elements such as vendor management, cloud security, business engagement, and comminate proactively. Introducing our premium set of slides with Web Based Software Security Stakeholder Engagement Model. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Vendor Management, Cloud Security, Business Engagement. So download instantly and tAIlor it with your information.
-
 IP Security Model For Integrating Data
IP Security Model For Integrating DataThis slide showcase process of IP security. This includes data source, applications, devices, clients, activities, sensors, digital assets, integration of data, streaming data, data warehousing, storage pf object, etc. Introducing our IP Security Model For Integrating Data set of slides. The topics discussed in these slides are Data Warehouse Autonomous, Streaming Data, Services Of Big Data, Integration Of Data. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Creation Of Secure Networks Using MBSE Integrated Modelling And Engineering
Creation Of Secure Networks Using MBSE Integrated Modelling And EngineeringThe purpose of this slide is to explain how MBSE principles can be applied to create secure networks and align with the criteria and models of information security management systems. This slide also highlights the steps involved, such as plan, do, check, and act. Present the topic in a bit more detail with this Creation Of Secure Networks Using MBSE Integrated Modelling And Engineering. Use it as a tool for discussion and navigation on Series Of Steps, Overview, Check. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Industrial Endpoint Cyber Security Maturity Model
Industrial Endpoint Cyber Security Maturity ModelThis slide lays out maturity framework for ensuring industrial endpoint cyber security. The purpose of this slide is to assist businesses in efficient management of security processes, policies and administrative tasks. It covers elements such as protection levels, defense mechanism, strategic solutions for management of vulnerabilities issues and security threats. Introducing our Industrial Endpoint Cyber Security Maturity Model set of slides. The topics discussed in these slides are Specialists, Cyber Security Assets, Cyber Security Professionals This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Securing Food Safety In Online Current Business Model Canvas Of Restaurant
Securing Food Safety In Online Current Business Model Canvas Of RestaurantThis slide covers restaurant business model canvas includes partners associated, activities involved, value propositions and revenue streams of business. Present the topic in a bit more detail with this Securing Food Safety In Online Current Business Model Canvas Of Restaurant. Use it as a tool for discussion and navigation on Key Partners, Key Activities, Value Propositions, Customer Relationships. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Big Data Model Of Security Sharing Based On Blockchain
Big Data Model Of Security Sharing Based On BlockchainThis slide gives an overview of the big data model of security sharing based on blockchain which include citizen, government, school, student, individual, etc. Presenting our set of slides with Big Data Model Of Security Sharing Based On Blockchain. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Collect Data, Smart Contract, Query Data.
-
 Maturity Model To Monitor OT Cyber Security Adoption
Maturity Model To Monitor OT Cyber Security AdoptionThis slide represents maturity model that assist companies to monitor and track cyber security adoption for enhancing OT protection. It includes various phases such as secure, defend, contain, monitor and manage phase. Presenting our well structured Maturity Model To Monitor OT Cyber Security Adoption The topics discussed in this slide are Secure, Defend, Contain, MonitorThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Models Of Cyber Security In Industry 4 0
Models Of Cyber Security In Industry 4 0This slide showcases the cyber security in industry 4.0. Its objective is to protection of internet connected systems. This slide includes security, anomaly detection, computing technology, computer crime and professional topic. Introducing our premium set of slides with Models Of Cyber Security In Industry 4 0. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Computing Technology, Computer Crime, Professional Topic. So download instantly and tailor it with your information.
-
 Tactical Maturity Model Of Security Operations Center
Tactical Maturity Model Of Security Operations CenterThe below slide represents the maturity model levels of security operations center that helps to identify and mitigate potential risk more effectively. The different levels include mean time to detect, respond, answer, and good. Introducing our Tactical Maturity Model Of Security Operations Center set of slides. The topics discussed in these slides are Prepare, Detect, Response, Investigate. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Organization Security Maturity Model For Effective Communication
Organization Security Maturity Model For Effective CommunicationThis slide represents a maturity model matrix for organization security that helps to foster effective communication of security measures to board. Key components are fundamentals, awareness level, technology, ownership, etc. Presenting our well structured Organization Security Maturity Model For Effective Communication. The topics discussed in this slide are Organizing Fundamental, Awareness Level, Technology. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Define Security Token Project Business Model Ultimate Guide Smart BCT SS V
Define Security Token Project Business Model Ultimate Guide Smart BCT SS VThe following slide depicts sample security token project business model to enhance liquidity and accessibility for fund raising. It includes elements such as overview tokenization, revenue streams, fund utilization, etc. Deliver an outstanding presentation on the topic using this Define Security Token Project Business Model Ultimate Guide Smart BCT SS V. Dispense information and present a thorough explanation of Key Elements, Project Name, Tokenization Model using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 User Based Security Training Model Strategic Guide To Implement Strategy SS
User Based Security Training Model Strategic Guide To Implement Strategy SSIntroducing User Based Security Training Model Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Compromised System, Compromised Network, Critical Assets, Exfiltrate Sensitive Data, using this template. Grab it now to reap its full benefits.
-
 Data Encryption Working Model For Security
Data Encryption Working Model For SecurityThe purpose of this slide is to elucidate how data encryption working model for security offers insight into safeguarding sensitive data through encryption mechanisms. It helps thwart unauthorized access or breaches. Introducing our Data Encryption Working Model For Security set of slides. The topics discussed in these slides are Sender, Plaintext, Ciphertext. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Model of governance and security of big data diagram ppt presentations
Model of governance and security of big data diagram ppt presentationsPresenting model of governance and security of big data diagram ppt presentations. This is a model of governance and security of big data diagram ppt presentations. This is a three stage process. The stages in this process are confidentiality, integrity, availability, security model.
-
 Web app security model powerpoint slide deck
Web app security model powerpoint slide deckPresenting web app security model powerpoint slide deck. This is a web app security model powerpoint slide deck. This is a five stage process. The stages in this process are web browser, veracode discovery, external code, uncover and retire, inventory.
-
 Security Hacker Costs Of Repairing Damages Ppt Powerpoint Presentation Model Ideas
Security Hacker Costs Of Repairing Damages Ppt Powerpoint Presentation Model IdeasThis slide depicts the increased additional costs caused by cyber attacks to the organization, such as DDOS attacks, hacking of the website, email domain, and ransom money. Present the topic in a bit more detail with this Security Hacker Costs Of Repairing Damages Ppt Powerpoint Presentation Model Ideas. Use it as a tool for discussion and navigation on Social Network Accounts, Network Equipment, Servers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Architecture And Security Review Cloud Capability Model For Strategy Architecture And Governance
Cloud Architecture And Security Review Cloud Capability Model For Strategy Architecture And GovernanceThis slide covers the cloud capability model including strategy, architecture, governance, identity and security with data centre, platform, infrastructure and software as services. Increase audience engagement and knowledge by dispensing information using Cloud Architecture And Security Review Cloud Capability Model For Strategy Architecture And Governance. This template helps you present information on four stages. You can also present information on Traditional Data Center, Orchestration And Integration, Service Request Brokering using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Architecture And Security Review Model For Workload Placement For On And Off Premises
Cloud Architecture And Security Review Model For Workload Placement For On And Off PremisesThis slide covers the workload placement such as Workloads shown on the left are marked as off premises which are more suitable for a public cloud where as those on the right are for on premises appropriate for a private cloud and those in the middle are for a hybrid cloud. Deliver an outstanding presentation on the topic using this Cloud Architecture And Security Review Model For Workload Placement For On And Off Premises. Dispense information and present a thorough explanation of Model For Workload, Placement, On And Off Premises using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security processing technologies ppt powerpoint presentation model graphics download cpb
Security processing technologies ppt powerpoint presentation model graphics download cpbPresenting this set of slides with name - Security Processing Technologies Ppt Powerpoint Presentation Model Graphics Download Cpb. This is an editable three stages graphic that deals with topics like Security Processing Technologies to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Ways secure web server ppt powerpoint presentation model outfit cpb
Ways secure web server ppt powerpoint presentation model outfit cpbPresenting our Ways Secure Web Server Ppt Powerpoint Presentation Model Outfit Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Ways Secure Web Server This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Online meeting app security features ppt powerpoint presentation model infographics cpb
Online meeting app security features ppt powerpoint presentation model infographics cpbPresenting our Online Meeting App Security Features Ppt Powerpoint Presentation Model Infographics Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Online Meeting App Security Features This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Secure website hackers ppt powerpoint presentation model infographic template cpb
Secure website hackers ppt powerpoint presentation model infographic template cpbPresenting Secure Website Hackers Ppt Powerpoint Presentation Model Infographic Template Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Secure Website Hackers. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Secure network connection ppt powerpoint presentation model grid cpb
Secure network connection ppt powerpoint presentation model grid cpbPresenting Secure Network Connection Ppt Powerpoint Presentation Model Grid Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Secure Network Connection. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Online payment security ppt powerpoint presentation model slide download cpb
Online payment security ppt powerpoint presentation model slide download cpbPresenting Online Payment Security Ppt Powerpoint Presentation Model Slide Download Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase seven stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Online Payment Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Security information and event management benchmarking maturity model
Security information and event management benchmarking maturity modelThis slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Introducing Security Information And Event Management Benchmarking Maturity Model to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Improve, Visibility, Identify, using this template. Grab it now to reap its full benefits.
-
 Security information and event management cloud siem model
Security information and event management cloud siem modelThis slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver an outstanding presentation on the topic using this Security Information And Event Management Cloud SIEM Model. Dispense information and present a thorough explanation of Visualization, Alerting, Analytics using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security information and event management fully managed service model
Security information and event management fully managed service modelPresent the topic in a bit more detail with this Security Information And Event Management Fully Managed Service Model. Use it as a tool for discussion and navigation on Visualization, Correlation, Aggregation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information and event management hybrid managed siem model
Security information and event management hybrid managed siem modelPresent the topic in a bit more detail with this Security Information And Event Management Hybrid Managed SIEM Model. Use it as a tool for discussion and navigation on Hybrid Managed SIEM Model. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure video sharing platform investor determine profitable business model of online video hosting platform
Secure video sharing platform investor determine profitable business model of online video hosting platformThis slide caters details about profitable business model for video hosting platform by addressing its key partners, value propositions, revenue streams, etc. Deliver an outstanding presentation on the topic using this Secure Video Sharing Platform Investor Determine Profitable Business Model Of Online Video Hosting Platform. Dispense information and present a thorough explanation of Profitable, Business, Revenue using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Website security testing tools online ppt powerpoint presentation model diagrams cpb
Website security testing tools online ppt powerpoint presentation model diagrams cpbPresenting Website Security Testing Tools Online Ppt Powerpoint Presentation Model Diagrams Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Website Security Testing Tools Online. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Job security factors ppt powerpoint presentation model graphics download cpb
Job security factors ppt powerpoint presentation model graphics download cpbPresenting our Job Security Factors Ppt Powerpoint Presentation Model Graphics Download Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Job Security Factors. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Tax percentage social security income ppt powerpoint presentation model designs cpb
Tax percentage social security income ppt powerpoint presentation model designs cpbPresenting Tax Percentage Social Security Income Ppt Powerpoint Presentation Model Designs Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Tax Percentage Social Security Income. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Availability database security ppt powerpoint presentation model vector cpb
Availability database security ppt powerpoint presentation model vector cpbPresenting Availability Database Security Ppt Powerpoint Presentation Model Vector Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Availability Database Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Web application firewall waf it types of web application firewall security models
Web application firewall waf it types of web application firewall security modelsThis slide represents the various types of WAF security models, including the whitelist or negative security model, blacklist or positive security model, and hybrid security model. Present the topic in a bit more detail with this Web Application Firewall Waf It Types Of Web Application Firewall Security Models. Use it as a tool for discussion and navigation on Organizations, Application, Firewall. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
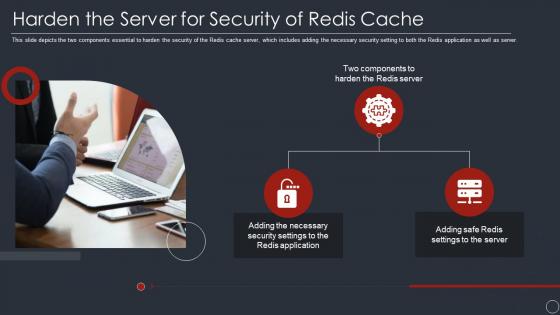 Harden the server for security of redis cache ppt powerpoint presentation model guide
Harden the server for security of redis cache ppt powerpoint presentation model guideThis slide depicts the two components essential to harden the security of the Redis cache server, which includes adding the necessary security setting to both the Redis application as well as server. Introducing Harden The Server For Security Of Redis Cache Ppt Powerpoint Presentation Model Guide to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Two Components To Harden The Redis Server, Adding The Necessary Security Settings To The Redis Application, Adding Safe Redis Settings To The Server, using this template. Grab it now to reap its full benefits.
-
 Cyber threat security maturity model with protection levels
Cyber threat security maturity model with protection levelsThe following slide illustrates the model of cyber threat security which includes secure, defend, contain, monitor and manage levels. Presenting our well structured Cyber Threat Security Maturity Model With Protection Levels. The topics discussed in this slide are Security Management Technology, Threat Management Platform, Threat Intelligence. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Types Security Controls Ppt Powerpoint Presentation Model Samples Cpb
Types Security Controls Ppt Powerpoint Presentation Model Samples CpbPresenting our Types Security Controls Ppt Powerpoint Presentation Model Samples Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Types Security Controls. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Strategic Model For Information Security Program
Strategic Model For Information Security ProgramThis slide focuses on strategic model for information security program which includes governance and management such as security risk analysis, audit and assessment, supplier management, backup and recovery, etc. Presenting our well-structured Strategic Model For Information Security Program. The topics discussed in this slide are Evaluation And Direction, Leadership, Human Resource Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Types Fixed Income Securities Ppt Powerpoint Presentation Model Slides Cpb
Types Fixed Income Securities Ppt Powerpoint Presentation Model Slides CpbPresenting Types Fixed Income Securities Ppt Powerpoint Presentation Model Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Types Fixed Income Securities. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cyber Security Fraud Detection Ppt Powerpoint Presentation Layouts Model Cpb
Cyber Security Fraud Detection Ppt Powerpoint Presentation Layouts Model CpbPresenting our Cyber Security Fraud Detection Ppt Powerpoint Presentation Layouts Model Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Cyber Security Fraud Detection. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Secure meeting platforms ppt powerpoint presentation model structure cpb
Secure meeting platforms ppt powerpoint presentation model structure cpbPresenting our Secure Meeting Platforms Ppt Powerpoint Presentation Model Structure Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Secure Meeting Platforms. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Secure offshore outsourcing ppt powerpoint presentation model introduction cpb
Secure offshore outsourcing ppt powerpoint presentation model introduction cpbPresenting Secure Offshore Outsourcing Ppt Powerpoint Presentation Model Introduction Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Secure Offshore Outsourcing. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.





