Powerpoint Templates and Google slides for It Threat
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Managing IT Threats At Workplace Overview Powerpoint Ppt Template Bundles DK MD
Managing IT Threats At Workplace Overview Powerpoint Ppt Template Bundles DK MDIf you require a professional template with great design, then this Managing IT Threats At Workplace Overview Powerpoint Ppt Template Bundles DK MD is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twenty one slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Data security it dashboard snapshot for threat tracking in data security
Data security it dashboard snapshot for threat tracking in data securityThis slide depicts the dashboard snapshot for threat tracking in data security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an outstanding presentation on the topic using this Data Security IT Dashboard For Threat Tracking In Data Security. Dispense information and present a thorough explanation of Monthly Threat Status, Current Risk Status, Threats Based On Role, Threats Owners, Risk Threats, Threat Report using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Major IOT Security Threats And Its Negative Effects
Major IOT Security Threats And Its Negative EffectsThis slide showcases major security threats that disrupt the operations. Threats covered are buffer overflow, SQL injection, worm, botnet, ransomware, password, phishing, crypto jacking, etc. Presenting our well structured Major IOT Security Threats And Its Negative Effects. The topics discussed in this slide are Negative Effective, Lack Visibility, Poor Testing. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
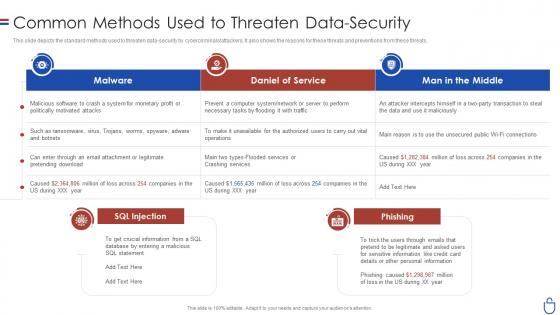 Data security it common methods used to threaten data security
Data security it common methods used to threaten data securityThis slide depicts the standard methods used to threaten data-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Present the topic in a bit more detail with this Data Security IT Common Methods Used To Threaten Data Security. Use it as a tool for discussion and navigation on Malware, Daniel Service, Man Middle, SQL Injection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
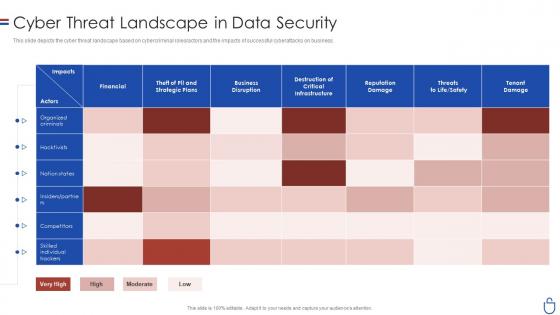 Data security it cyber threat landscape in data security
Data security it cyber threat landscape in data securityThis slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Present the topic in a bit more detail with this Data Security IT Cyber Threat Landscape In Data Security. Use it as a tool for discussion and navigation on Financial, Business Disruption, Reputation Damage, Tenant Damage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data security it latest threats in data security ppt slides background designs
Data security it latest threats in data security ppt slides background designsThis slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Increase audience engagement and knowledge by dispensing information using Data Security IT Latest Threats In Data Security Ppt Slides Background Designs. This template helps you present information on three stages. You can also present information on Dridex Malware, Romance Scams, Emotet Malware using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data security it types of threats in data security ppt slides graphic tips
Data security it types of threats in data security ppt slides graphic tipsThis slide depicts the main types of threats in data security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Increase audience engagement and knowledge by dispensing information using Data Security IT Types Of Threats In Data Security Ppt Slides Graphic Tips. This template helps you present information on three stages. You can also present information on Cyber Crime, Cyber Terrorism, Cyber Attack, Cause Disruption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IT Threat Prevention Quarterly Action Plan
IT Threat Prevention Quarterly Action PlanThis slide represents quarterly action plan for prevention from for IT threats. It further includes threats such as insider threats, viruses And worms, botnets, and ransomware. Presenting our well structured IT Threat Prevention Quarterly Action Plan. The topics discussed in this slide are Time, Priority Level, Action Taken. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Types Of Threats In IT Infrastructure Security
Types Of Threats In IT Infrastructure SecurityThis slide showcases the common threats faced in infrastructure security. Its aim is to identify threats and eliminate them. This slide includes phishing, ransomware, botnet and physical theft. Presenting our set of slides with Types Of Threats In IT Infrastructure Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Infrastructure, Personal, Exploitation.
-
 Hacking Threats In IT Industry With Mitigation Strategies
Hacking Threats In IT Industry With Mitigation StrategiesThis slide showcases potential hacking incidents in IT sector with mitigation strategies. The purpose of this slide is to help software businesses in strengthening their network security by securing digital assets. It covers mitigation strategies to overcome various hacking threats such as insider threats, phishing attacks, viruses, botnets, etc. Introducing our premium set of slides with Hacking Threats In IT Industry With Mitigation Strategies Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Insider Threats, Monitor Account Activity, Network Traffic Monitoring. So download instantly and tailor it with your information.
-
 Implementing Effective Tokenization Existing IT Security Infrastructure Threats
Implementing Effective Tokenization Existing IT Security Infrastructure ThreatsThis slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. Present the topic in a bit more detail with this Implementing Effective Tokenization Existing IT Security Infrastructure Threats. Use it as a tool for discussion and navigation on Compliance Challenges, Resource Intensiveness, Faced Security Vulnerabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Implementation Plan Existing IT Security Infrastructure Threats
Application Security Implementation Plan Existing IT Security Infrastructure ThreatsThis slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Existing IT Security Infrastructure Threats. Dispense information and present a thorough explanation of Broken Authentication, Cross Site Scripting, Denial Of Service, Infrastructure Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Major Incident Details Related To It Failure Business Recovery Plan To Overcome Cyber Security Threat
Major Incident Details Related To It Failure Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about cyber attack incidents. It includes information about incident date, impact, and incident information comprising loss of customer name, address, phone number, birth date, etc. Increase audience engagement and knowledge by dispensing information using Major Incident Details Related To It Failure Business Recovery Plan To Overcome Cyber Security Threat. This template helps you present information on three stages. You can also present information on Ransomware, Information, Cyber Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices For Minimizing Risks Of Insider Threats IT Security Awareness Training Cybersecurity SS
Best Practices For Minimizing Risks Of Insider Threats IT Security Awareness Training Cybersecurity SSThis slide represents best practices for mitigating threats that originate from within the targeted organization. It includes best practices such as perform enterprise-wide risk assessment etc. Increase audience engagement and knowledge by dispensing information using Best Practices For Minimizing Risks Of Insider Threats IT Security Awareness Training Cybersecurity SS. This template helps you present information on four stages. You can also present information on Enforce Policies And Controls, Establish Physical Security, Harden Network Perimeter Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Insider Threats Awareness Training Program IT Security Awareness Training Cybersecurity SS
Insider Threats Awareness Training Program IT Security Awareness Training Cybersecurity SSThis slide represents details related to training program for mitigating threats that arises from within the targeted organization. It includes details related to mode of training, key learnings etc. Introducing Insider Threats Awareness Training Program IT Security Awareness Training Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Insider Threats Awareness, Training Program, Key Learnings, Mitigating Threats, using this template. Grab it now to reap its full benefits.
-
 IT Security Awareness Training Defense Against Cyber Threats Cybersecurity SS
IT Security Awareness Training Defense Against Cyber Threats Cybersecurity SSThis slide represents details related to ways security awareness training helps in preventing and mitigating common threats faced by organization such as data breaches, phishing attacks etc. Deliver an outstanding presentation on the topic using this IT Security Awareness Training Defense Against Cyber Threats Cybersecurity SS. Dispense information and present a thorough explanation of Data Breaches, Phishing Attacks, Insider Threats, Social Engineering using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Objectives Of Insider Threats Awareness Training IT Security Awareness Training Cybersecurity SS
Objectives Of Insider Threats Awareness Training IT Security Awareness Training Cybersecurity SSThis slide represents objectives of providing training for mitigating treats that originates from within the targeted organization. It includes objectives such as identify and report behaviors of insider threats etc. Increase audience engagement and knowledge by dispensing information using Objectives Of Insider Threats Awareness Training IT Security Awareness Training Cybersecurity SS. This template helps you present information on four stages. You can also present information on Unintentional Insider Threats, Malicious Or Unintentional Insider, Public And National Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Introduction To Cyber Terrorism And Its Impact Strategic Guide To Implement Strategy SS
Introduction To Cyber Terrorism And Its Impact Strategic Guide To Implement Strategy SSThis slide showcases the introduction to cyber terrorism. It includes its impact such as financial losses, economic impact, data breaches, political instability and social disruption.Deliver an outstanding presentation on the topic using this Introduction To Cyber Terrorism And Its Impact Strategic Guide To Implement Strategy SS. Dispense information and present a thorough explanation of Economic Impact, Data Breaches, Social Disruption, Political Instability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Web application firewall waf it kpis dashboard for threat tracking in waf
Web application firewall waf it kpis dashboard for threat tracking in wafThis slide depicts how threat risk will be monitored and threat detection will be done in the organization through web application firewall implementation. Present the topic in a bit more detail with this Web Application Firewall Waf It Kpis Dashboard For Threat Tracking In Waf. Use it as a tool for discussion and navigation on Kpis Dashboard For Threat Tracking In WAF. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it cyber terrorism faced by companies in us ppt slides deck
Cyberterrorism it cyber terrorism faced by companies in us ppt slides deckThis slide depicts the cyber terrorism faced by the companies in the US, and the graph represents the financial losses in the last five years. Deliver an outstanding presentation on the topic using this Cyberterrorism IT Cyber Terrorism Faced By Companies In US Ppt Slides Deck. Dispense information and present a thorough explanation of Financial Loss Million, Cyber Terrorism using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyberterrorism it cyber terrorism faced by various industries ppt slides model
Cyberterrorism it cyber terrorism faced by various industries ppt slides modelThis slide describes the cyber terrorism various industries face, including health, finance, media, transportation and education. Present the topic in a bit more detail with this Cyberterrorism IT Cyber Terrorism Faced By Various Industries Ppt Slides Model. Use it as a tool for discussion and navigation on Education, Transportation, Media, Healthcare, Government. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it dashboard for threat tracking of cyber terrorism
Cyberterrorism it dashboard for threat tracking of cyber terrorismThis slide depicts the dashboard for threat tracking of cyber terrorism by covering top threats, threats by class name, etc. Deliver an outstanding presentation on the topic using this Cyberterrorism IT Dashboard For Threat Tracking Of Cyber Terrorism. Dispense information and present a thorough explanation of Threats Per Month, Top Threat, Average Threats Detection Per Day using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyberterrorism it distributed denial of service ddos as cyber terrorism too
Cyberterrorism it distributed denial of service ddos as cyber terrorism tooThis slide explains the distributed denial of services DDOS as a cyber terrorism tool and the common types of DDOS attacks. Deliver an outstanding presentation on the topic using this Cyberterrorism IT Distributed Denial Of Service DDOS As Cyber Terrorism Too. Dispense information and present a thorough explanation of Service Denial, Disrupting Services, Ceasing Sites, 2019 To 2020 using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Hacking it dashboard snapshot for threat tracking ppt slides demonstration
Hacking it dashboard snapshot for threat tracking ppt slides demonstrationThis slide depicts the dashboard snapshot for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Deliver an outstanding presentation on the topic using this Hacking It Dashboard For Threat Tracking Ppt Slides Demonstration. Dispense information and present a thorough explanation of Dashboard For Threat Tracking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implement Strong IT Guidelines In The Company Cyber Terrorism Attacks
Implement Strong IT Guidelines In The Company Cyber Terrorism AttacksThis slide depicts the strong IT guidelines which should be implemented in the company, such as security software, backups, fraud detection. Present the topic in a bit more detail with this Implement Strong IT Guidelines In The Company Cyber Terrorism Attacks. Use it as a tool for discussion and navigation on Implement Strong It Guidelines In The Company. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Infrastructure Cyber Security Budget Against Cyber Terrorism Attacks
IT Infrastructure Cyber Security Budget Against Cyber Terrorism AttacksThis slide depicts the IT infrastructure budget of incorporating cyber security, as well as the cost of each activity to the company. Present the topic in a bit more detail with this IT Infrastructure Cyber Security Budget Against Cyber Terrorism Attacks. Use it as a tool for discussion and navigation on It Infrastructure Cyber Security Budget Against Cyber Terrorism Fy19 20. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Dashboard Of It Department With Threat Frequency
Risk Management Dashboard Of It Department With Threat FrequencyThis slide shows dashboard of risk management of IT department representing net critical risks, threat and vulnerability frequency in last 60 days, open audit findings, open and vendor risks etc. Presenting our well-structured Risk Management Dashboard Of It Department With Threat Frequency. The topics discussed in this slide are Open Risks, Risk Organization Level, Net Critical Risk. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Current Potential Implications Faced By Firm As Threats Managing IT Threats At Workplace Overview
Current Potential Implications Faced By Firm As Threats Managing IT Threats At Workplace OverviewThis slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an outstanding presentation on the topic using this Current Potential Implications Faced By Firm As Threats Managing IT Threats At Workplace Overview. Dispense information and present a thorough explanation of Employees, Financial, Records using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threats Management Dashboard Managing It Threats At Workplace Overview
Cyber Threats Management Dashboard Managing It Threats At Workplace OverviewThis slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Present the topic in a bit more detail with this Cyber Threats Management Dashboard Managing It Threats At Workplace Overview. Use it as a tool for discussion and navigation on Analysis, Rating, Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Threat Management Activities Tracking Dashboard Managing IT Threats At Workplace Overview
Cybersecurity Threat Management Activities Tracking Dashboard Managing IT Threats At Workplace OverviewThis slide provides details regarding cybersecurity threat management activities tracking dashboard in terms of breach risk trends, risk issues by owner, breach likelihood, etc. Present the topic in a bit more detail with this Cybersecurity Threat Management Activities Tracking Dashboard Managing IT Threats At Workplace Overview. Use it as a tool for discussion and navigation on Cybersecurity, Management, Tracking. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial Performance Tracking Dashboard Managing It Threats At Workplace Overview
Financial Performance Tracking Dashboard Managing It Threats At Workplace OverviewThis slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Present the topic in a bit more detail with this Financial Performance Tracking Dashboard Managing It Threats At Workplace Overview. Use it as a tool for discussion and navigation on Receivables, Revenue, Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Incident Reporting Dashboard Managing IT Threats At Workplace Overview
Incident Reporting Dashboard Managing IT Threats At Workplace OverviewThe firm will track the various incidents issues faced and resolved in the firm. Present the topic in a bit more detail with this Incident Reporting Dashboard Managing IT Threats At Workplace Overview. Use it as a tool for discussion and navigation on Assignee, Resolved, Incident. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Statistics Associated To Workplace Threats Managing IT Threats At Workplace Overview
Statistics Associated To Workplace Threats Managing IT Threats At Workplace OverviewThis slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. . Present the topic in a bit more detail with this Statistics Associated To Workplace Threats Managing IT Threats At Workplace Overview. Use it as a tool for discussion and navigation on Statistics, Workplace, Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing various threats affecting it project safety key initiatives for project safety it
Addressing various threats affecting it project safety key initiatives for project safety itThis slide provides information regarding various IT threats existing at workplace disrupting IT project safety such as general and criminal IT threats. Introducing Addressing Various Threats Affecting It Project Safety Key Initiatives For Project Safety It to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Software, Email, Processing, Service, using this template. Grab it now to reap its full benefits.
-
 Determine phases of threat attack disrupting it project safety contd key initiatives for project safety it
Determine phases of threat attack disrupting it project safety contd key initiatives for project safety itThis slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. Increase audience engagement and knowledge by dispensing information using Determine Phases Of Threat Attack Disrupting It Project Safety Contd Key Initiatives For Project Safety It. This template helps you present information on four stages. You can also present information on System, Communication, Network, Implement using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine phases of threat attack disrupting it project safety key initiatives for project safety it
Determine phases of threat attack disrupting it project safety key initiatives for project safety itThis slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. Introducing Determine Phases Of Threat Attack Disrupting It Project Safety Key Initiatives For Project Safety It to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Networks, Systems, Email, Information, Target, using this template. Grab it now to reap its full benefits.
-
 Various ways to manage project safety by managing threats key initiatives for project safety it
Various ways to manage project safety by managing threats key initiatives for project safety itThis slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. Introducing Various Ways To Manage Project Safety By Managing Threats Key Initiatives For Project Safety It to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Determine, Security, Measures, Management, Advertisements, using this template. Grab it now to reap its full benefits.
-
 Addressing various threats affecting it project safety project safety management it
Addressing various threats affecting it project safety project safety management itThis slide provides information regarding various IT threats existing at workplace disrupting IT project safety such as general and criminal IT threats. Increase audience engagement and knowledge by dispensing information using Addressing Various Threats Affecting It Project Safety Project Safety Management It. This template helps you present information on two stages. You can also present information on Email, Data Processing, Security Breach, Service using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Various ways to manage project safety by managing threats project safety management it
Various ways to manage project safety by managing threats project safety management itThis slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. Introducing Various Ways To Manage Project Safety By Managing Threats Project Safety Management It to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Advertisements, Emails, Network, Risk, Management, using this template. Grab it now to reap its full benefits.
-
 Ukraine and russia cyber warfare it threat actors supporting russia and ukraine
Ukraine and russia cyber warfare it threat actors supporting russia and ukraineThis slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. Introducing Ukraine And Russia Cyber Warfare It Threat Actors Supporting Russia And Ukraine to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Ransomware, Analyzing, Servers, using this template. Grab it now to reap its full benefits.
-
 Contingency Plan For Threat Handling In Security Centre Enabling It Intelligence Framework
Contingency Plan For Threat Handling In Security Centre Enabling It Intelligence FrameworkThis slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations.Present the topic in a bit more detail with this Contingency Plan For Threat Handling In Security Centre Enabling It Intelligence Framework Use it as a tool for discussion and navigation on Local Area Network, Mainframe Systems, Distributes Systems This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 How Firm Handle Various Insider Threats At Workplace Enabling It Intelligence Framework
How Firm Handle Various Insider Threats At Workplace Enabling It Intelligence FrameworkThis slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc.Introducing How Firm Handle Various Insider Threats At Workplace Enabling It Intelligence Framework to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Employee Training, Develop Threat Hunting Team, Implement User Behavioral Analytics using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it agenda for cyber terrorism ppt slides diagrams
Cyberterrorism it agenda for cyber terrorism ppt slides diagramsIntroducing Cyberterrorism IT Agenda For Cyber Terrorism Ppt Slides Diagrams to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Terrorism, Current Situation, Globe And Tools, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it assessment matrix of cyber terrorism ppt slides picture
Cyberterrorism it assessment matrix of cyber terrorism ppt slides pictureThis slide demonstrate cyber terrorism in terms of cybercriminal actors, as well as the financial impact of successful cyber terrorists attacks. Present the topic in a bit more detail with this Cyberterrorism IT Assessment Matrix Of Cyber Terrorism Ppt Slides Picture. Use it as a tool for discussion and navigation on Organized Criminals, Financial Theft Froud, Business Destruction. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it checklist to deal with cyber terrorism threats ppt slides templates
Cyberterrorism it checklist to deal with cyber terrorism threats ppt slides templatesThis slide represents the checklist to deal with cyber terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Checklist To Deal With Cyber Terrorism Threats Ppt Slides Templates. This template helps you present information on one stages. You can also present information on Incident Response Plan, Limited Access Privileges, Evaluating Risk Third Party Vendor, Cyber Security Assessment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyberterrorism it cyber terrorism awareness programme for employees
Cyberterrorism it cyber terrorism awareness programme for employeesThis slide depicts the cyber terrorism awareness programm for employees, including the name of the participants and what modules would be covered under training. Present the topic in a bit more detail with this Cyberterrorism IT Cyber Terrorism Awareness Programme For Employees. Use it as a tool for discussion and navigation on Frontline Staff, IT Teams, Project Managers, Senior Executives. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it cyber terrorism issues faced by the company ppt slides styles
Cyberterrorism it cyber terrorism issues faced by the company ppt slides stylesThis slide represents the cyber terrorism issues faced by the company, such as increased costs, reputational damage, loss in revenue. Introducing Cyberterrorism IT Cyber Terrorism Issues Faced By The Company Ppt Slides Styles to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Increased Costs, Reputational Damage, Lost Revenue, Intellectual Property Theft, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it employee awareness training budget against cyber terrorism fy2020
Cyberterrorism it employee awareness training budget against cyber terrorism fy2020This slide demonstrates the employee awareness training budget against cyber-terrorism by a graph that includes the training date, and the degree of capacity. Present the topic in a bit more detail with this Cyberterrorism IT Employee Awareness Training Budget Against Cyber Terrorism FY2020. Use it as a tool for discussion and navigation on Provider, Training Date, Duration, Budget, Capability Level. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it managing cyber terrorism 60 days plan
Cyberterrorism it managing cyber terrorism 60 days planThis slide depicts the plan for the next 60 days after the firm has implemented the cyber security model to tackle cyber terrorism. Deliver an outstanding presentation on the topic using this Cyberterrorism IT Managing Cyber Terrorism 60 Days Plan. Dispense information and present a thorough explanation of Data Loss Incidents, Infected Computers, Policy Violations, Measures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyberterrorism it managing cyber terrorism 90 days plan
Cyberterrorism it managing cyber terrorism 90 days planThis slide demonstrates the cyber security models 90 day strategy in an enterprise, as well as training compliance and communication strategies. Present the topic in a bit more detail with this Cyberterrorism IT Managing Cyber Terrorism 90 Days Plan. Use it as a tool for discussion and navigation on Training Completion, Communication Methods, Measured. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it peroration of cyber terrorism ppt slides layout
Cyberterrorism it peroration of cyber terrorism ppt slides layoutThis slide explains the conclusion or peroration of cyber terrorism and how it is different from information warfare as it targets civilians rather than operations. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Peroration Of Cyber Terrorism Ppt Slides Layout. This template helps you present information on six stages. You can also present information on Cyber Terrorism, Information Warfare, Except IT Targets, Cyber Terrorism using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyberterrorism it phishing cyber terrorism tool ppt slides graphics
Cyberterrorism it phishing cyber terrorism tool ppt slides graphicsThis slide describes phishing in which an attacker tricks a victim to open an email, provide card credentials or any sensitive information. Introducing Cyberterrorism IT Phishing Cyber Terrorism Tool Ppt Slides Graphics to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Obtain Sensitive Information, Credit Card Details, Business, Consumer Confidence, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it phishing techniques misused for cyber assault
Cyberterrorism it phishing techniques misused for cyber assaultThis slide represents phishing techniques used for cyber assaults or cyber terrorism, such as email phishing scams and whaling. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Phishing Techniques Misused For Cyber Assault. This template helps you present information on four stages. You can also present information on Spear Phishing, Smishing And Vishing, Whaling, Email Phishing Scams using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyberterrorism it roadmap to implement cyber security to mitigate cyber terrorism
Cyberterrorism it roadmap to implement cyber security to mitigate cyber terrorismThis slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Roadmap To Implement Cyber Security To Mitigate Cyber Terrorism. This template helps you present information on four stages. You can also present information on Creating Personal Accounts, Awareness Training Employees, Keep Hardware And Software Updated using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyberterrorism it scada system misused for cyber terrorism
Cyberterrorism it scada system misused for cyber terrorismThis slide describes the SCADA system as a tool misused for cyberterrorism and any damage to the SCADA can cause a major physical damage. Introducing Cyberterrorism IT SCADA System Misused For Cyber Terrorism to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on SCADA Operator Terminal, Alarm Monitor, Radio Cellular Telemetry, Control System Adjustments, Instrumentation Inputs, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it simple advanced and complex types of cyber terrorism
Cyberterrorism it simple advanced and complex types of cyber terrorismThis slide explains the simple advanced and complex types of cyber terrorism i.e. simple structure, advanced structure, and complex coordinated around the 128 countries of the world. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Simple Advanced And Complex Types Of Cyber Terrorism. This template helps you present information on three stages. You can also present information on Simple Structured, Advanced Structured, Complex Coordinated using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyberterrorism it structure of malicious code misused for cyber terrorism
Cyberterrorism it structure of malicious code misused for cyber terrorismThis slide depicts the structure of malicious code or malware and the four steps of the structure i.e. Probe, Program, Expose and Execute. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Structure Of Malicious Code Misused For Cyber Terrorism. This template helps you present information on four stages. You can also present information on Prob, Program, Expose, Execute using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyberterrorism it table of contents for cyber terrorism ppt slides sample
Cyberterrorism it table of contents for cyber terrorism ppt slides samplePresent the topic in a bit more detail with this Cyberterrorism IT Table Of Contents For Cyber Terrorism Ppt Slides Sample. Use it as a tool for discussion and navigation on Assessment Matrix, Cyber Terrorism, Timeline, Dashboard, Threat Tracking. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it three major forms of cyber terrorism ppt slides tips
Cyberterrorism it three major forms of cyber terrorism ppt slides tipsThis slide describes the three major forms of cyber terrorism such as privacy violation, networks damage, and disruptions, and distribution denial of service attack. Introducing Cyberterrorism IT Three Major Forms Of Cyber Terrorism Ppt Slides Tips to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Privacy Violation, Networks Damage And Disruptions, Distributed Denial Service Attack, Cause Networks Damage And Their Disruptions, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it trojans as cyber terrorism tool ppt slides aids
Cyberterrorism it trojans as cyber terrorism tool ppt slides aidsThis slide depicts the Trojans as a cyber terrorism tool in which phishing is used to manipulate a user into executing the infected file. Deliver an outstanding presentation on the topic using this Cyberterrorism IT Trojans As Cyber Terrorism Tool Ppt Slides Aids. Dispense information and present a thorough explanation of Attacker Owned, Compromise Site, Downloader Trojan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.




