Powerpoint Templates and Google slides for Information And Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Matrix For Threat Solution And Risk Assessment And Management Plan For Information Security
Matrix For Threat Solution And Risk Assessment And Management Plan For Information SecurityThis slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack Present the topic in a bit more detail with this Matrix For Threat Solution And Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Protocols, Management, Transactions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mitigation Strategies To Tackle Information Risk Assessment And Management Plan For Information Security
Mitigation Strategies To Tackle Information Risk Assessment And Management Plan For Information SecurityThis slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help orgnaization to minimize the financial loss and maintain reputation of business Introducing Mitigation Strategies To Tackle Information Risk Assessment And Management Plan For Information Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Mitigation, Strategies, Information, using this template. Grab it now to reap its full benefits.
-
 Probability Assessment Matrix For Risk Assessment And Management Plan For Information Security
Probability Assessment Matrix For Risk Assessment And Management Plan For Information SecurityThis slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information Present the topic in a bit more detail with this Probability Assessment Matrix For Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Probability, Assessment, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Process For Information Security Risk Assessment And Management Plan For Information Security
Process For Information Security Risk Assessment And Management Plan For Information SecurityThis slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets Introducing Process For Information Security Risk Assessment And Management Plan For Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Process, Information, Assessment, using this template. Grab it now to reap its full benefits.
-
 Reporting Structure For Information Security Risk Assessment And Management Plan For Information Security
Reporting Structure For Information Security Risk Assessment And Management Plan For Information SecurityThis slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact Deliver an outstanding presentation on the topic using this Reporting Structure For Information Security Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Structure, Information, Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Assessment And Management Plan For Information Security Analyzing The Impact Of Security Threats
Risk Assessment And Management Plan For Information Security Analyzing The Impact Of Security ThreatsDeliver an outstanding presentation on the topic using this Risk Assessment And Management Plan For Information Security Analyzing The Impact Of Security Threats. Dispense information and present a thorough explanation of Analyzing, Organization, Financial using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Assessment And Management Plan For Information Security Current Information And Data Security
Risk Assessment And Management Plan For Information Security Current Information And Data SecurityThis slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating Present the topic in a bit more detail with this Risk Assessment And Management Plan For Information Security Current Information And Data Security. Use it as a tool for discussion and navigation on Information, Capabilities, Risk Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
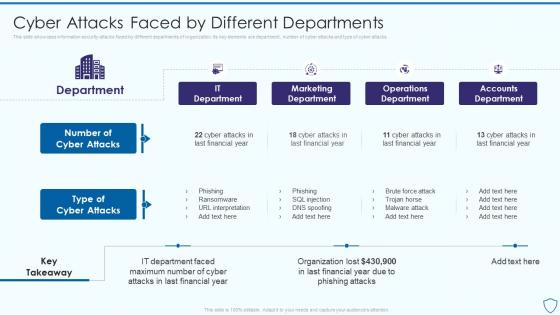 Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By Different
Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By DifferentThis slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks Deliver an outstanding presentation on the topic using this Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By Different. Dispense information and present a thorough explanation of Marketing Department, Operations Department, Accounts Department using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Assessment And Management Plan For Information Security Identifying Employees For Information
Risk Assessment And Management Plan For Information Security Identifying Employees For InformationThis slide showcases plan that can help organization to conduct training for employees for information security risk management. It will enable employees to monitor risks and resolve them in timely manner Present the topic in a bit more detail with this Risk Assessment And Management Plan For Information Security Identifying Employees For Information. Use it as a tool for discussion and navigation on Information, Programme, Identifying. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Assessment And Management Plan For Information Security Table Of Contents
Risk Assessment And Management Plan For Information Security Table Of ContentsIntroducing Risk Assessment And Management Plan For Information Security Table Of Contents to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Departments, Organization, Information, using this template. Grab it now to reap its full benefits.
-
 Risk Assessment Matrix With Vulnerability Risk Assessment And Management Plan For Information Security
Risk Assessment Matrix With Vulnerability Risk Assessment And Management Plan For Information SecurityThis slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level Present the topic in a bit more detail with this Risk Assessment Matrix With Vulnerability Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Assessment, Vulnerability, Associated. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Roles And Responsibilities Of Risk Management Risk Assessment And Management Plan For Information Security
Roles And Responsibilities Of Risk Management Risk Assessment And Management Plan For Information SecurityThis slide showcases responsibilities of major employees involved in information security risk management team. Key roles are information security manager, risk management officer and chief information officer Present the topic in a bit more detail with this Roles And Responsibilities Of Risk Management Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Responsibilities, Management, Information . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Selecting Suitable Software For Information Risk Assessment And Management Plan For Information Security
Selecting Suitable Software For Information Risk Assessment And Management Plan For Information SecurityThis slide showcases software that can help organization to monitor and manage the risk. It provides information about Cyber Risk Quantification, vvulnerability management, Ccentralized rrepository for aassets etc Deliver an outstanding presentation on the topic using this Selecting Suitable Software For Information Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Software, Information, Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps For Information Security Risk Management Risk Assessment And Management Plan For Information Security
Steps For Information Security Risk Management Risk Assessment And Management Plan For Information SecurityThis slide showcase steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond Present the topic in a bit more detail with this Steps For Information Security Risk Management Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Communication, Mitigation, Response Planning. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Timeline For Information Security Risk Assessment And Management Plan For Information Security
Timeline For Information Security Risk Assessment And Management Plan For Information SecurityThis slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress Deliver an outstanding presentation on the topic using this Timeline For Information Security Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Information, Management, Email Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Vulnerability Rating For Risk Identification Risk Assessment And Management Plan For Information Security
Vulnerability Rating For Risk Identification Risk Assessment And Management Plan For Information SecurityThis slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description Present the topic in a bit more detail with this Vulnerability Rating For Risk Identification Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Identification, Information, Vulnerability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Challenges And Solutions In Information Risk Assessment And Management Plan For Information Security
Challenges And Solutions In Information Risk Assessment And Management Plan For Information SecurityThis slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them Present the topic in a bit more detail with this Challenges And Solutions In Information Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Fighting Frauds, Internal Vulnerabilities, Employee Awareness. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Attacks Faced By Risk Assessment And Management Plan For Information Security
Information Security Attacks Faced By Risk Assessment And Management Plan For Information SecurityThis slide showcases most common information attacks faced by organization. It includes malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack Deliver an outstanding presentation on the topic using this Information Security Attacks Faced By Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Malware, Phishing, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Safety And Security Icon
Information Technology Safety And Security IconPresenting our set of slides with Information Technology Safety And Security Icon. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Information Technology, Safety And Security.
-
 Information And Cyber Security Policy Development
Information And Cyber Security Policy DevelopmentThe following slide highlights the information and cyber security policy development by depicting purpose, audience, information security, access control, data segregation, data support, security awareness and responsibilities. Introducing our premium set of slides with name Information And Cyber Security Policy Development. Ellicudate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Awareness, Responsibilities, Information Security, Data Segregation. So download instantly and tailor it with your information.
-
 Information Security Risk Indicators Examples In Powerpoint And Google Slides Cpb
Information Security Risk Indicators Examples In Powerpoint And Google Slides CpbPresenting our Information Security Risk Indicators Examples In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Information Security Risk Indicators Examples This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Key Risk Indicators Examples Information Security In Powerpoint And Google Slides Cpb
Key Risk Indicators Examples Information Security In Powerpoint And Google Slides CpbPresenting our Key Risk Indicators Examples Information Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Key Risk Indicators Examples Information Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Agenda Enterprise Risk Management And Information Technology Security
Agenda Enterprise Risk Management And Information Technology SecurityIntroducing Agenda Enterprise Risk Management And Information Technology Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Organization, IT Networks, IT Risk Management, using this template. Grab it now to reap its full benefits.
-
 Enterprise Risk Management And Information Technology Security Table Of Contents
Enterprise Risk Management And Information Technology Security Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Enterprise Risk Management And Information Technology Security Table Of Contents. This template helps you present information on one stages. You can also present information on Security Criteria, Control Measures, IT System Vulnerabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Enterprise Risk Management And Information Technology Security
Icons Slide For Enterprise Risk Management And Information Technology SecurityIntroducing our well researched set of slides titled Icons Slide For Enterprise Risk Management And Information Technology Security. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table Of Contents For Enterprise Risk Management And Information Technology Security
Table Of Contents For Enterprise Risk Management And Information Technology SecurityIntroducing Table Of Contents For Enterprise Risk Management And Information Technology Security to increase your presentation threshold. Encompassed with eleven stages, this template is a great option to educate and entice your audience. Dispence information on IT Risks, Threat Evaluation, IT Risk Management, Cost Estimation, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security And Risk Management With Capabilities
Information Technology Security And Risk Management With CapabilitiesThis slide focuses on the information technology security and risk management which covers capabilities such as enterprise security strategy, compliance, vulnerability management, security architecture, data leakage protection, identify management, etc. Deliver an outstanding presentation on the topic using this Information Technology Security And Risk Management With Capabilities. Dispense information and present a thorough explanation of Security Policy Compliance, Compliance, Enterprise Security Strategy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Agenda For Information Security Risk Management And Mitigation Plan Ppt Tips
Agenda For Information Security Risk Management And Mitigation Plan Ppt TipsIntroducing Agenda For Information Security Risk Management And Mitigation Plan Ppt Tips to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispense information on Organization, Information Security, Risk Management, using this template. Grab it now to reap its full benefits.
-
 Challenges And Solutions In Information Security Risk Management
Challenges And Solutions In Information Security Risk ManagementThis slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them. Introducing Challenges And Solutions In Information Security Risk Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispense information on Fighting Frauds, Internal Vulnerabilities, Employee Awareness, using this template. Grab it now to reap its full benefits.
-
 Current Information And Data Security Capabilities Of Firm Information Security Risk Management
Current Information And Data Security Capabilities Of Firm Information Security Risk ManagementThis slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. Introducing Current Information And Data Security Capabilities Of Firm Information Security Risk Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispense information on Risk Management Functions, Required Standard Rating, Actual Standard Rating, using this template. Grab it now to reap its full benefits.
-
 G9 Table Of Contents For Information Security Risk Management And Mitigation Plan
G9 Table Of Contents For Information Security Risk Management And Mitigation PlanIntroducing G9 Table Of Contents For Information Security Risk Management And Mitigation Plan to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispense information on Information Security Risk, Management Plan, Process, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Information Security Risk Management And Mitigation Plan
Icons Slide Information Security Risk Management And Mitigation PlanPresenting our well crafted Icons Slide Information Security Risk Management And Mitigation Plan set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly
-
 Identifying Information Security Threats And Impact Information Security Risk Management
Identifying Information Security Threats And Impact Information Security Risk ManagementThis slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. Increase audience engagement and knowledge by dispensing information using Identifying Information Security Threats And Impact Information Security Risk Management. This template helps you present information on one stage. You can also present information on Errors And Omissions, Employee Sabotage, Physical Infrastructure Loss using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
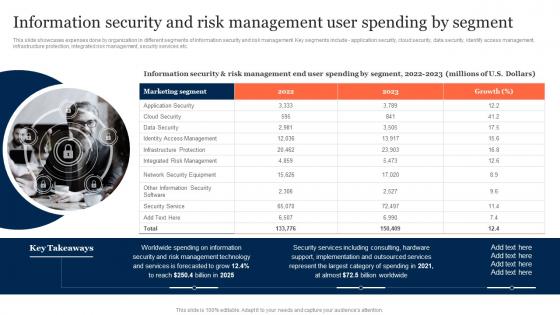 Information Security And Risk Management User Information Security Risk Management
Information Security And Risk Management User Information Security Risk ManagementThis slide showcases expenses done by organization in different segments of information security and risk management. Key segments include - application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. Introducing Information Security And Risk Management User Information Security Risk Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispense information on Marketing Segment, Identity Access Management, Information Security, using this template. Grab it now to reap its full benefits.
-
 Matrix For Threat Solution And Risk Management Information Security Risk Management
Matrix For Threat Solution And Risk Management Information Security Risk ManagementThis slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack. Introducing Matrix For Threat Solution And Risk Management Information Security Risk Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispense information on Monitor Database Activity, Validate Database Protocols, Capture Detailed Transactions, using this template. Grab it now to reap its full benefits.
-
 Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Management
Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk ManagementThis slide showcases assessment matrix to identify risk associate with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level. Deliver an outstanding presentation on the topic using this Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Management. Dispense information and present a thorough explanation of Risk Assessment Matrix, Vulnerability Level, Threat Level using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Roles And Responsibilities Of Risk Management Team Information Security Risk Management
Roles And Responsibilities Of Risk Management Team Information Security Risk ManagementThis slide showcases responsibilities of major employees involved in information security risk management team. Key roles are information security manager, risk management officer and chief information officer. Introducing Roles And Responsibilities Of Risk Management Team Information Security Risk Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispense information on Information Security Manager, Risk Management Officer, Chief Information Officer, using this template. Grab it now to reap its full benefits.
-
 Threat Identification And Vulnerability Assessment Information Security Risk Management
Threat Identification And Vulnerability Assessment Information Security Risk ManagementThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Present the topic in a bit more detail with this Threat Identification And Vulnerability Assessment Information Security Risk Management. Use it as a tool for discussion and navigation on Threat Identification, Vulnerability Assessment, Risk Identification. This template is free to edit as deemed fit for your organization. Therefore download it now
-
 Information Security Program Manager Roles And Responsibilities
Information Security Program Manager Roles And ResponsibilitiesThis slide covers information security program manager roles and responsibilities. It involves information owner, security administrator and IT management. Introducing our premium set of slides with Information Security Program Manager Roles And Responsibilities. Elucidate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Owner, Security Administrator, IT Management. So download instantly and tailor it with your information.
-
 Information Technology Security And Privacy Roadmap
Information Technology Security And Privacy RoadmapThe following slide showcases IT security and privacy roadmap to protect digital information from severe threats. It includes elements such as assess, build, select, deploy, train and test. Introducing our premium set of slides with name Information Technology Security And Privacy Roadmap. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Categorize Assets, Security Tool, Software Required. So download instantly and tailor it with your information.
-
 Information Security Staffing In Powerpoint And Google Slides Cpb
Information Security Staffing In Powerpoint And Google Slides CpbPresenting our Information Security Staffing In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Information Security Staffing This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
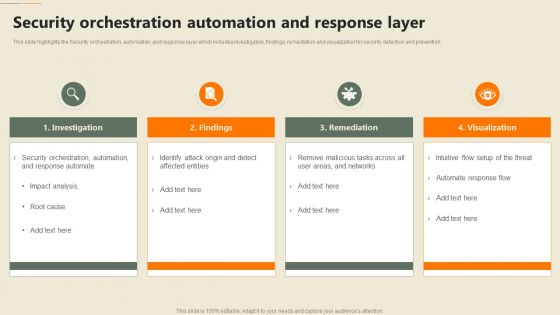 Security Automation In Information Technology Security Orchestration Automation And Response Layer
Security Automation In Information Technology Security Orchestration Automation And Response LayerThis slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention Increase audience engagement and knowledge by dispensing information using Security Automation In Information Technology Security Orchestration Automation And Response Layer. This template helps you present information on four stages. You can also present information on Investigation, Remediation, Visualization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Impacts Of Ineffective Information Technology Security Automation To Investigate And Remediate Cyberthreats
Impacts Of Ineffective Information Technology Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Increase audience engagement and knowledge by dispensing information using Impacts Of Ineffective Information Technology Security Automation To Investigate And Remediate Cyberthreats. This template helps you present information on five stages. You can also present information on Ineffective, Information, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Different Security Automation Tools With Pros And Cons Security Automation In Information Technology
Different Security Automation Tools With Pros And Cons Security Automation In Information TechnologyThis slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM Deliver an outstanding presentation on the topic using this Different Security Automation Tools With Pros And Cons Security Automation In Information Technology. Dispense information and present a thorough explanation of Automation, Security Orchestration, Process Automation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
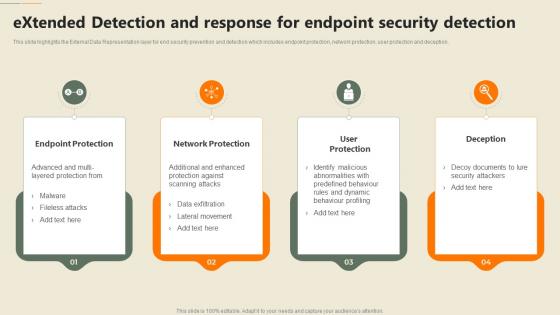 Extended Detection And Response For Endpoint Security Detection Security Automation In Information Technology
Extended Detection And Response For Endpoint Security Detection Security Automation In Information TechnologyThis slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Increase audience engagement and knowledge by dispensing information using Extended Detection And Response For Endpoint Security Detection Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Endpoint Protection, Network Protection, Deception using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
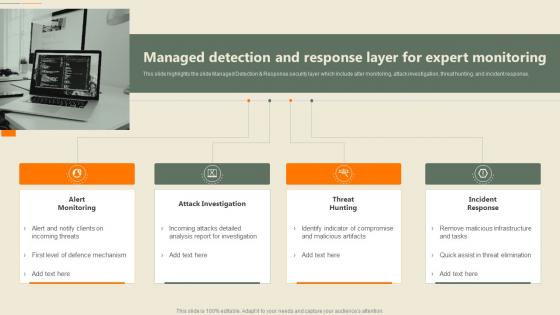 Managed Detection And Response Layer For Expert Monitoring Security Automation In Information Technology
Managed Detection And Response Layer For Expert Monitoring Security Automation In Information TechnologyThis slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response Increase audience engagement and knowledge by dispensing information using Managed Detection And Response Layer For Expert Monitoring Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Attack Investigation, Incident Response, Threat Hunting using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
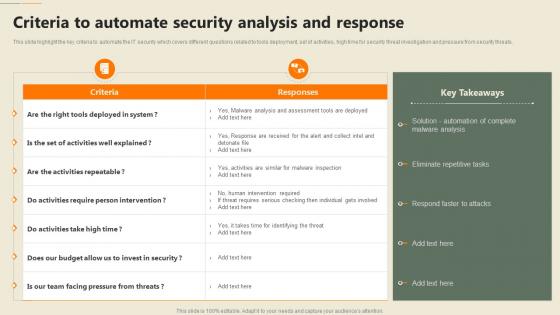 Security Automation In Information Technology Criteria To Automate Security Analysis And Response
Security Automation In Information Technology Criteria To Automate Security Analysis And ResponseThis slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats. Present the topic in a bit more detail with this Security Automation In Information Technology Criteria To Automate Security Analysis And Response. Use it as a tool for discussion and navigation on Analysis, Eliminate Repetitive Tasks, Respond Faster To Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation Integrates Tools Systems And Processes Security Automation In Information Technology
Security Automation Integrates Tools Systems And Processes Security Automation In Information TechnologyThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Increase audience engagement and knowledge by dispensing information using Security Automation Integrates Tools Systems And Processes Security Automation In Information Technology. This template helps you present information on eight stages. You can also present information on Automation, Integrates, Processes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Data Protection And Information Security Policy And Procedure Staff Induction Training Guide
Data Protection And Information Security Policy And Procedure Staff Induction Training GuideThis slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Present the topic in a bit more detail with this Data Protection And Information Security Policy And Procedure Staff Induction Training Guide. Use it as a tool for discussion and navigation on Applicable, Enforcement, Organization Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Management Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Information Security Management Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Information security management colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Information Security Management Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Information Security Management Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Information security management monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Information Security Protocol Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Information Security Protocol Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Information security protocol colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Information Security Protocol Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Information Security Protocol Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Information security protocol monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Information Security Services Pricing In Powerpoint And Google Slides Cpb
Information Security Services Pricing In Powerpoint And Google Slides CpbPresenting Information Security Services Pricing In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Information Security Services Pricing. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Unsure Information Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Unsure Information Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Unsure information security colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Unsure Information Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Unsure Information Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Unsure information security monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Information Systems Security Officer Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Information Systems Security Officer Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Information systems security officer colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Information Systems Security Officer Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Information Systems Security Officer Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Information systems security officer monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Data Protection And Information Security Policy And Procedure Corporate Induction Program For New Staff
Data Protection And Information Security Policy And Procedure Corporate Induction Program For New StaffThis slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Introducing Data Protection And Information Security Policy And Procedure Corporate Induction Program For New Staff to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Protection, Information, Procedure, using this template. Grab it now to reap its full benefits.
-
 Security Awareness And Training Policy Overview Information Technology Policy
Security Awareness And Training Policy Overview Information Technology PolicyThis slide represents the security awareness and training policy. It covers that the training program should be designed by management, and employees will sign a confidentiality agreement after getting the training. Increase audience engagement and knowledge by dispensing information using Security Awareness And Training Policy Overview Information Technology Policy. This template helps you present information on six stages. You can also present information on Corporate Data, Security, Employees using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





