Powerpoint Templates and Google slides for Information And Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Security information and event management hybrid managed siem model
Security information and event management hybrid managed siem modelPresent the topic in a bit more detail with this Security Information And Event Management Hybrid Managed SIEM Model. Use it as a tool for discussion and navigation on Hybrid Managed SIEM Model. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information and event management key features of siem software
Security information and event management key features of siem softwareThis slide provides the details about our companys SIEM key features such as automated reports, log collection and classification, high scalability, security automation, etc. Introducing Security Information And Event Management Key Features Of SIEM Software to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Comprehensive, Collection, Compliance, using this template. Grab it now to reap its full benefits.
-
 Security information and event management log management metrics
Security information and event management log management metricsIncrease audience engagement and knowledge by dispensing information using Security Information And Event Management Log Management Metrics. This template helps you present information on eight stages. You can also present information on Configurations, Virtualization, Application using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security information and event management need for siem software in your company
Security information and event management need for siem software in your companyThis slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management Introducing Security Information And Event Management Need For SIEM Software In Your Company to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Digital, Security, Generating, using this template. Grab it now to reap its full benefits.
-
 Security information and event management next evolution of siem software
Security information and event management next evolution of siem softwareThis slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Increase audience engagement and knowledge by dispensing information using Security Information And Event Management Next Evolution Of SIEM Software. This template helps you present information on six stages. You can also present information on Traffic Analysis, Behavior Analytics, Threat Intelligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security information and event management our organization flow
Security information and event management our organization flowThis slide covers the companys log flow and understand how the data is gathered, security alerts are notified to the clients. Introducing Security Information And Event Management Our Organization Flow to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Our Organization SIEM Log Flow, using this template. Grab it now to reap its full benefits.
-
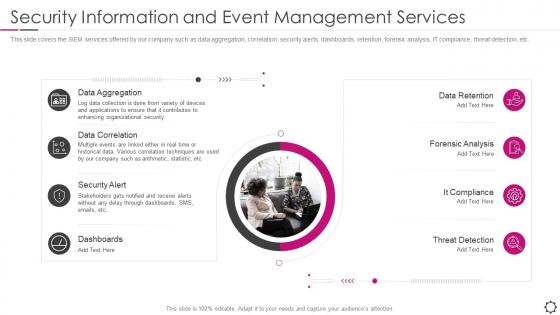 Security information and event management security management services
Security information and event management security management servicesThis slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Introducing Security Information And Event Management Security Management Services to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Aggregation, Data Correlation, Security Alert, using this template. Grab it now to reap its full benefits.
-
 Security information and event management siem logging sources
Security information and event management siem logging sourcesThis slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. Increase audience engagement and knowledge by dispensing information using Security Information And Event Management SIEM Logging Sources. This template helps you present information on four stages. You can also present information on Security Devices, Network Devices, Servers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
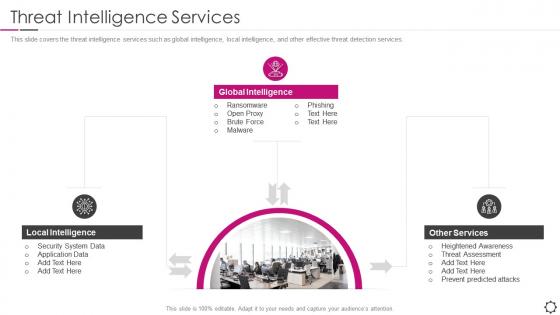 Security information and event management threat intelligence services
Security information and event management threat intelligence servicesThis slide covers the threat intelligence services such as global intelligence, local intelligence, and other effective threat detection services. Introducing Security Information And Event Management Threat Intelligence Services to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Global Intelligence, Local Intelligence, Services, using this template. Grab it now to reap its full benefits.
-
 Security information and event management traditional siem deployment
Security information and event management traditional siem deploymentThis slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Present the topic in a bit more detail with this Security Information And Event Management Traditional SIEM Deployment. Use it as a tool for discussion and navigation on Visualization, Collection, Aggregation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information and event management various siem cost
Security information and event management various siem costThis slide covers the different costs plan offered by our company such as basic, intermediate, advanced, learning model costs. Deliver an outstanding presentation on the topic using this Security Information And Event Management Various SIEM Cost. Dispense information and present a thorough explanation of Correlation, Response, Intermediate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
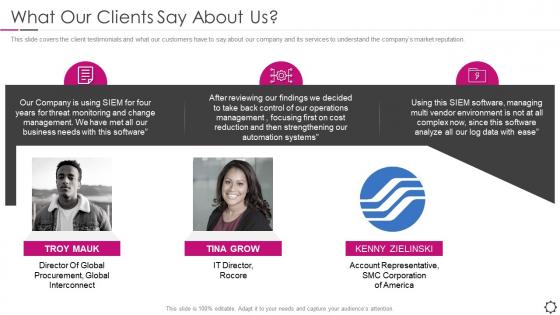 Security information and event management what about us
Security information and event management what about usThis slide covers the client testimonials and what our customers have to say about our company and its services to understand the companys market reputation.Introducing Security Information And Event Management What About Us to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on What Our Clients Say About Us, using this template. Grab it now to reap its full benefits.
-
 Security information and event management security intelligence services
Security information and event management security intelligence servicesThis slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Introducing Security Information And Event Management Security Intelligence Services to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Response, Management, Cyber, Analytics, using this template. Grab it now to reap its full benefits.
-
 Security information and event management sim vs sem vs siem
Security information and event management sim vs sem vs siemIncrease audience engagement and knowledge by dispensing information using Security Information And Event Management SIM Vs SEM Vs SIEM. This template helps you present information on three stages. You can also present information on Information, Management, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Siem competitive advantage security information and event management
Siem competitive advantage security information and event managementThis slide covers the SIEM competitive landscape based on various categories such as digital experience management, health check, application performance monitoring, event management, etc. Present the topic in a bit more detail with this SIEM Competitive Advantage Security Information And Event Management. Use it as a tool for discussion and navigation on Experience, Management, Performance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information and event management siem software challenges
Security information and event management siem software challengesThis slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. Deliver an outstanding presentation on the topic using this Security Information And Event Management SIEM Software Challenges. Dispense information and present a thorough explanation of Configurations, Respond, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Siem competitive value security information and event management
Siem competitive value security information and event managementThis slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Present the topic in a bit more detail with this SIEM Competitive Value Security Information And Event Management. Use it as a tool for discussion and navigation on SIEM Competitive Advantage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information process security information and event management
Security information process security information and event managementThis slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation Introducing Security Information Process Security Information And Event Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Connecting, Assessing, Streaming, Protocol, using this template. Grab it now to reap its full benefits.
-
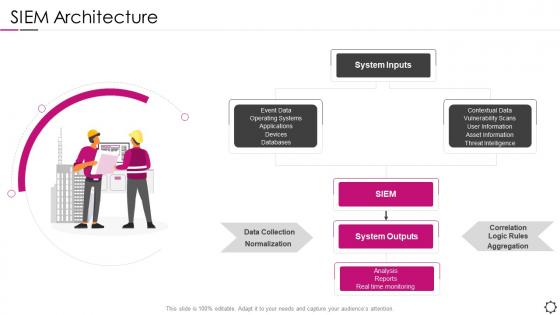 Siem architecture security information and event management
Siem architecture security information and event managementPresent the topic in a bit more detail with this SIEM Architecture Security Information And Event Management. Use it as a tool for discussion and navigation on Operating, Systems, Vulnerability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk reporting and likelihood effective information security risk management process
Risk reporting and likelihood effective information security risk management processMentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an outstanding presentation on the topic using this Risk Reporting And Likelihood Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Attack Scenario, Risk Encountered, Equipment Failure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Roles and responsibilities effective information security risk management process
Roles and responsibilities effective information security risk management processFollowing slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development.Increase audience engagement and knowledge by dispensing information using Roles And Responsibilities Effective Information Security Risk Management Process. This template helps you present information on one stage. You can also present information on Information Management Manager, Risk Management Officer, Development And Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Effective information security risk reporting and likelihood ppt slides layout
Effective information security risk reporting and likelihood ppt slides layoutMentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an outstanding presentation on the topic using this Effective Information Security Risk Reporting And Likelihood Ppt Slides Layout. Dispense information and present a thorough explanation of Risk Encountered, Frequency, Attack Scenario, Affected Asset using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 5 practices of information and cyber security risk management
5 practices of information and cyber security risk managementMentioned slide delineates best practices for information security risk management. Knowledge of IT environment and assets, developing risk management strategy, embedding risk management into organization culture, continuous risk assessment and security protocols are the practices covered in this slide. Presenting our set of slides with 5 Practices Of Information And Cyber Security Risk Management. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Management, Organization, Risk.
-
 Cyber and information security risk management framework
Cyber and information security risk management frameworkMentioned slide exhibits information security risk management framework which can be used to enhance cybersecurity of organization. The various components covered in this framework are service design, transition and operationalization, penetration testing etc. Introducing our Cyber And Information Security Risk Management Framework set of slides. The topics discussed in these slides are Development, Service Transition, Service Operationalization. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Icon for information and cyber security risk management
Icon for information and cyber security risk managementIntroducing our premium set of slides with Icon For Information And Cyber Security Risk Management. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon For Information And Cyber Security Risk Management. So download instantly and tailor it with your information.
-
 Icon for information security and risk management team
Icon for information security and risk management teamIntroducing our premium set of slides with Icon For Information Security And Risk Management Team. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon For Information Security And Risk Management Team. So download instantly and tailor it with your information.
-
 Information and cyber security risk management maturity levels
Information and cyber security risk management maturity levelsMentioned slide showcase maturity stages of information security risk management, which will assist company to develop comprehensive cybersecurity strategy. The maturity stages could be Partial informed repetitive and adaptive. Introducing our premium set of slides with Information And Cyber Security Risk Management Maturity Levels. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Partial, Informed, Repetitive. So download instantly and tailor it with your information.
-
 Information and cyber security risk management plan
Information and cyber security risk management planMentioned slide showcase information security risk management plan. The template provides information about various risks such as DDoS, crypto jacking, malware and password theft and with other details like degree of risk involved, impact, strategies to be deployed. Introducing our Information And Cyber Security Risk Management Plan set of slides. The topics discussed in these slides are Degree Of Risk, Strategies, Devices. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information security risk assessment and management tools
Information security risk assessment and management toolsMentioned slide highlights several information security risk management tools which can be used by organization. The multiple tools are automated questionnaires, security ratings and vulnerability assessment report. Introducing our premium set of slides with Information Security Risk Assessment And Management Tools. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Ratings, Automated Questionnaires, Vulnerability Assessment Report. So download instantly and tailor it with your information.
-
 Risk Based Methodology To Cyber And Information Security Table Of Contents
Risk Based Methodology To Cyber And Information Security Table Of ContentsDeliver an outstanding presentation on the topic using this Risk Based Methodology To Cyber And Information Security Table Of Contents Dispense information and present a thorough explanation of Threat Matrix, Identified Assets, Impact Assessment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information and event management logging process real time analysis of security alerts
Information and event management logging process real time analysis of security alertsThis slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation Present the topic in a bit more detail with this Information And Event Management Logging Process Real Time Analysis Of Security Alerts. Use it as a tool for discussion and navigation on Information, Management, Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Real time analysis of security alerts security information and event management services
Real time analysis of security alerts security information and event management servicesThis slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Increase audience engagement and knowledge by dispensing information using Real Time Analysis Of Security Alerts Security Information And Event Management Services. This template helps you present information on eight stages. You can also present information on Data Aggregation, Data Correlation, Security Alert using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Dispose Data And Equipment Properly
Information Security Dispose Data And Equipment ProperlyThis slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Increase audience engagement and knowledge by dispensing information using Information Security Dispose Data And Equipment Properly. This template helps you present information on three stages. You can also present information on Dispose Data And Equipment Properly using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Hardware And Software Update In Company
Information Security Hardware And Software Update In CompanyThis slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Introducing Information Security Hardware And Software Update In Company to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Introduce, Hardware, Software using this template. Grab it now to reap its full benefits.
-
 Information Security Minimize Administrative And Staff Privileges
Information Security Minimize Administrative And Staff PrivilegesThis slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. Increase audience engagement and knowledge by dispensing information using Information Security Minimize Administrative And Staff Privileges. This template helps you present information on three stages. You can also present information on Minimize Administrative And Staff Privileges using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security What Is Information Security And How Does It Work
Information Security What Is Information Security And How Does It WorkThis slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Increase audience engagement and knowledge by dispensing information using Information Security What Is Information Security And How Does It Work. This template helps you present information on five stages. You can also present information on Techniques, Procedures, Approach using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Program Encountered Risks Summary And Their Impact Assessment
Information Security Program Encountered Risks Summary And Their Impact AssessmentMentioned slide provides information about the risks encountered by the company till date and their impact on existing business operations. Deliver an outstanding presentation on the topic using this Information Security Program Encountered Risks Summary And Their Impact Assessment. Dispense information and present a thorough explanation of Assessment, Encountered, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Gap Identification Current Approach Process Flaws And Cost
Information Security Program Gap Identification Current Approach Process Flaws And CostPurpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Present the topic in a bit more detail with this Information Security Program Gap Identification Current Approach Process Flaws And Cost. Use it as a tool for discussion and navigation on Identification, Current Approach, Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Scorecard To Check Cybersecurity And Digital Risk Preparedness
Information Security Program Scorecard To Check Cybersecurity And Digital Risk PreparednessFollowing slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Present the topic in a bit more detail with this Information Security Program Scorecard To Check Cybersecurity And Digital Risk Preparedness. Use it as a tool for discussion and navigation on Preparedness, Cybersecurity, Scorecard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Framework For Information Security Online And Onsite Training Schedule
Risk Management Framework For Information Security Online And Onsite Training ScheduleThis slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration. Present the topic in a bit more detail with this Risk Management Framework For Information Security Online And Onsite Training Schedule. Use it as a tool for discussion and navigation on Employee, Training Mode, Intermediate, Online And Onsite. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Framework For Information Security Risk Reporting And Likelihood
Risk Management Framework For Information Security Risk Reporting And LikelihoodMentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Present the topic in a bit more detail with this Risk Management Framework For Information Security Risk Reporting And Likelihood. Use it as a tool for discussion and navigation on Risk Encountered, Frequency, Attack Scenario, Affected Asset. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Framework For Information Security Roles And Responsibilities For Managing
Risk Management Framework For Information Security Roles And Responsibilities For ManagingFollowing slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development. Increase audience engagement and knowledge by dispensing information using Risk Management Framework For Information Security Roles And Responsibilities For Managing. This template helps you present information on two stages. You can also present information on Chief Information Officer, Information Management Manager, IT Manger, Risk Management Officer using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Risk Management Framework For Information Security Threat Identification And Vulnerability
Risk Management Framework For Information Security Threat Identification And VulnerabilityFollowing slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an outstanding presentation on the topic using this Risk Management Framework For Information Security Threat Identification And Vulnerability. Dispense information and present a thorough explanation of Communication And Network, Database, Failure To Segment Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Icons Slide For Risk Based Methodology To Cyber and Information Security
Icons Slide For Risk Based Methodology To Cyber and Information SecurityPresenting our well crafted Icons Slide For Risk Based Methodology To Cyber and Information Security set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly
-
 Table Of Contents For Risk Based Methodology To Cyber and Information Security
Table Of Contents For Risk Based Methodology To Cyber and Information SecurityPresent the topic in a bit more detail with this Table Of Contents For Risk Based Methodology To Cyber and Information Security Use it as a tool for discussion and navigation on Defining Business Priorities, Global Market Insights, Companies Digitization Levels This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Automating threat identification security information and event management
Automating threat identification security information and event managementIncrease audience engagement and knowledge by dispensing information using Automating Threat Identification Security Information And Event Management. This template helps you present information on four stages. You can also present information on Information, Management, Compliance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Automating threat identification table of contents security information and event management
Automating threat identification table of contents security information and event managementIncrease audience engagement and knowledge by dispensing information using Automating Threat Identification Table Of Contents Security Information And Event Management. This template helps you present information on eleven stages. You can also present information on Company Overview, Management, Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security information and event management services automating threat identification
Security information and event management services automating threat identificationThis slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Increase audience engagement and knowledge by dispensing information using Security Information And Event Management Services Automating Threat Identification. This template helps you present information on eight stages. You can also present information on Data Aggregation, Data Correlation, Security Alert using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Improve it security with vulnerability information and event management logging process
Improve it security with vulnerability information and event management logging processThis slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation Introducing Improve It Security With Vulnerability Information And Event Management Logging Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Information, Management, Process, using this template. Grab it now to reap its full benefits.
-
 Agenda Of Information Security And Iso 27001
Agenda Of Information Security And Iso 27001Introducing Agenda Of Information Security And Iso 27001 to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Agenda Of Information Security And ISO 27001, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Information Security And Iso 27001
Icons Slide Information Security And Iso 27001Deliver an outstanding presentation on the topic using this Icons Slide Information Security And Iso 27001. Dispense information and present a thorough explanation of Icons using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Benefits Of Iso 27001 Certification
Information Security And Iso 27001 Benefits Of Iso 27001 CertificationThis slide displays various organizational benefits after getting ISO 27001 certification. Benefits included are information confidentiality, low operational cost, increase in the trust of valuable partners and customers and competitive advantage. Increase audience engagement and knowledge by dispensing information using Information Security And Iso 27001 Benefits Of Iso 27001 Certification. This template helps you present information on ten stages. You can also present information on Competitive, Information, Confidentiality using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security And Iso 27001 Checklist Mandatory Documents Required Iso 27001 Certification
Information Security And Iso 27001 Checklist Mandatory Documents Required Iso 27001 CertificationFollowing slide displays checklist of mandatory documents required to get ISO 27001 certification along with the status. Present the topic in a bit more detail with this Information Security And Iso 27001 Checklist Mandatory Documents Required Iso 27001 Certification. Use it as a tool for discussion and navigation on Mandatory, Documents, Required. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 Clause And Its Relationship With Isms Stages
Information Security And Iso 27001 Clause And Its Relationship With Isms StagesFollowing slide illustrates the relationship of ISO 27001 clause with ISMS stages. ISMS stages covered in the slide are design, implement, operate, monitor and improve Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 Clause And Its Relationship With Isms Stages. Dispense information and present a thorough explanation of Relationship, Leadership, Planning using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Communication Plan For Successful Implementation Of Isms
Information Security And Iso 27001 Communication Plan For Successful Implementation Of IsmsThis slide shows internal and external communication plan for successful implementation of ISMS. It includes sections namely reason for communication, initiator, recipient, frequency and medium. Present the topic in a bit more detail with this Information Security And Iso 27001 Communication Plan For Successful Implementation Of Isms. Use it as a tool for discussion and navigation on Successful, Implementation, Communication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 Current Security Management Capabilities Overview
Information Security And Iso 27001 Current Security Management Capabilities OverviewFollowing slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 Current Security Management Capabilities Overview. Dispense information and present a thorough explanation of Security, Management, Capabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Defining Risk Level And Impact Score
Information Security And Iso 27001 Defining Risk Level And Impact ScoreFollowing slide defines the incident risk level. It includes details about risk level, risk score and its description. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 Defining Risk Level And Impact Score. Dispense information and present a thorough explanation of Defining Risk Level And Impact Score using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Estimated Budget For Isms Training
Information Security And Iso 27001 Estimated Budget For Isms TrainingFollowing slide illustrates the estimate the budget for providing ISMS training. It includes information such as training title area, training duration, training cost per employee, number of employees to be trained and total training cost. Present the topic in a bit more detail with this Information Security And Iso 27001 Estimated Budget For Isms Training. Use it as a tool for discussion and navigation on Introduction, Foundation, Lead Implementer. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 Incorporation Isms Framework Into Corporate Control Processes
Information Security And Iso 27001 Incorporation Isms Framework Into Corporate Control ProcessesMentioned slide displays the incorporation of information security management system framework within the corporate control process. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 Incorporation Isms Framework Into Corporate Control Processes. Dispense information and present a thorough explanation of Framework, Corporate, Processes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Internal Isms Audit Program And Activities
Information Security And Iso 27001 Internal Isms Audit Program And ActivitiesMentioned slide portrays framework of internal ISMS audit program along with various activities. Activities covered in the slide are commissioning, initial meeting, information collection and evaluation, results and final meeting. Present the topic in a bit more detail with this Information Security And Iso 27001 Internal Isms Audit Program And Activities. Use it as a tool for discussion and navigation on Implementation, Monitoring, Improvement. This template is free to edit as deemed fit for your organization. Therefore download it now.





