Powerpoint Templates and Google slides for Encrypt
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Encryption Implementation Strategies Steps Involved In Working Of Cloud Storage Encryption
Encryption Implementation Strategies Steps Involved In Working Of Cloud Storage EncryptionThis slide demonstrates the working process of cloud encryption technique to secure data stored in the cloud. The purpose of this slide is to discuss two main components of cloud cryptography, known as data-in-transit and data-at-rest. Present the topic in a bit more detail with this Encryption Implementation Strategies Steps Involved In Working Of Cloud Storage Encryption. Use it as a tool for discussion and navigation on Cloud Storage Encryption, Data In Transit, Cloud Cryptography, Cloud Encryption Technique. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
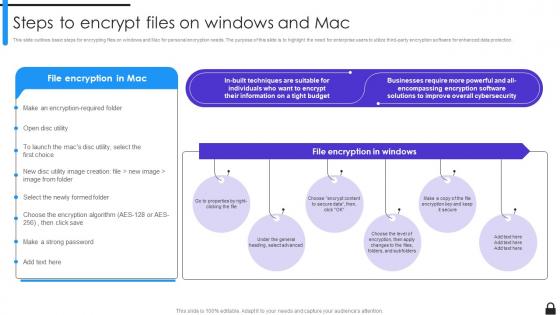 Encryption Implementation Strategies Steps To Encrypt Files On Windows And Mac
Encryption Implementation Strategies Steps To Encrypt Files On Windows And MacThis slide outlines basic steps for encrypting files on windows and Mac for personal encryption needs. The purpose of this slide is to highlight the need for enterprise users to utilize third-party encryption software for enhanced data protection. Increase audience engagement and knowledge by dispensing information using Encryption Implementation Strategies Steps To Encrypt Files On Windows And Mac. This template helps you present information on six stages. You can also present information on Encrypting Files On Windows, Mac For Personal Encryption Needs, Encryption Software, Enhanced Data Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies Steps To Implement Regulatory Compliance Plan
Encryption Implementation Strategies Steps To Implement Regulatory Compliance PlanThe purpose of this slide is to outline the critical steps involved in implementing a compliance plan to ensure data protection and privacy. These steps include auditing the environment, hiring a compliance officer, maintaining policies, providing employee training, etc. Increase audience engagement and knowledge by dispensing information using Encryption Implementation Strategies Steps To Implement Regulatory Compliance Plan. This template helps you present information on six stages. You can also present information on Maintain Policies, Regulatory Compliance Plan, Continuous Improvement, Audit Existing Environment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies Steps To Set Up Field Level Encryption
Encryption Implementation Strategies Steps To Set Up Field Level EncryptionThis slide represents the process of setting up field level encryption technology. The key steps involved in this procedure are identify sensitive fields and select encryption method, get encryption keys, make a profile for field-level encryption, etc. Introducing Encryption Implementation Strategies Steps To Set Up Field Level Encryption to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Identify Sensitive Fields, Select Encryption Method, Get Encryption Keys, Symmetric Or Asymmetric, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Symmetric Key Data Encryption Technique
Encryption Implementation Strategies Symmetric Key Data Encryption TechniqueThis slide illustrates the steps involved in transferring data using symmetric encryption. The purpose of this slide is to demonstrate how symmetric key encryption works. The critical components included are the sender, symmetric key, encrypted data, etc. Increase audience engagement and knowledge by dispensing information using Encryption Implementation Strategies Symmetric Key Data Encryption Technique. This template helps you present information on five stages. You can also present information on Encrypted Data, Symmetric Key, Data Encryption Technique, Non Understandable Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies Timeline To Implement Data Encryption In Organization
Encryption Implementation Strategies Timeline To Implement Data Encryption In OrganizationThe purpose of this slide is to represent the timeline to implement data encryption in an organization. The main phases highlighted in this slide are planning, research and evaluation, development, testing and quality assurance, deployment, etc. Introducing Encryption Implementation Strategies Timeline To Implement Data Encryption In Organization to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Development Phase, Testing And Quality Assurance Phase, Research And Evaluation Phase, Planning Phase, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Top Regulatory Compliance Frameworks For Data Protection
Encryption Implementation Strategies Top Regulatory Compliance Frameworks For Data ProtectionThe purpose of this slide is to summarize several relevant regulations. These are GDPR General Data Protection Regulation, CCPA California Consumer Privacy Act, PCI DSS Payment Card Industry Data Security Standard, NIST, and HIPAA, along with their descriptions and scopes. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Top Regulatory Compliance Frameworks For Data Protection. Dispense information and present a thorough explanation of General Data Protection Regulation, California Consumer Privacy Act, Health Insurance Portability And Accountability Act using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Training Program For Data Encryption Implementation
Encryption Implementation Strategies Training Program For Data Encryption ImplementationThis slide describes the training program for employees to implement data encryption in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Present the topic in a bit more detail with this Encryption Implementation Strategies Training Program For Data Encryption Implementation. Use it as a tool for discussion and navigation on Symmetric And Asymmetric Cryptography, Data Encryption Best Practices, Case Studies And Practical, Implementing Cryptographic Techniques. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Transport Layer Security Implementation Using Handshake
Encryption Implementation Strategies Transport Layer Security Implementation Using HandshakeThis slide discusses a cryptographic system known as transport layer security TLS. The purpose of this slide is to explain how TLS enables safe communication over computer networks using handshake protocol and record protocol. Increase audience engagement and knowledge by dispensing information using Encryption Implementation Strategies Transport Layer Security Implementation Using Handshake. This template helps you present information on two stages. You can also present information on Transport Layer Security Implementation, Handshake And Record Protocol, Computer Networks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies Understanding Information Rights Management Process
Encryption Implementation Strategies Understanding Information Rights Management ProcessThe purpose of this slide is to describe the management, restriction, and protection of content using IRM Information Rights Management. This slide also represents the DAM process, which includes create, identify, store, automate, integrate and monitor. Introducing Encryption Implementation Strategies Understanding Information Rights Management Process to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Application Of Encryption, Establishing Access Rights, Document Tracking System, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Understanding Virtual Private Network Protocols
Encryption Implementation Strategies Understanding Virtual Private Network ProtocolsThis slide discusses Virtual Private Network VPN to enable secure and private communication over public networks by creating an encrypted tunnel between users device and the VPN server. It also highlights remote access and site-to-site VPN. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Understanding Virtual Private Network Protocols. Dispense information and present a thorough explanation of Virtual Private Network Protocols, Secure And Private Communication, Support Its Configuration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Understanding Working Of Homomorphic Encryption
Encryption Implementation Strategies Understanding Working Of Homomorphic EncryptionThis slide illustrates the working of homomorphic encryption by using algebraic principle of homomorphism. This slide also talks about the operations that can be performed on ciphertext such as arithmetic, multiplication and Boolean. Present the topic in a bit more detail with this Encryption Implementation Strategies Understanding Working Of Homomorphic Encryption. Use it as a tool for discussion and navigation on Encrypted Search Results, Working Of Homomorphic, Encryption Technology, Plaintext And Ciphertext Spaces. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Understanding Working Of Quantum Encryption Technology
Encryption Implementation Strategies Understanding Working Of Quantum Encryption TechnologyThis slide demonstrates the steps involved in encrypting and decrypting the keys using quantum cryptography. The steps involved are passing the photon to receiver, receive the photon, set the kay by analysing correct streams and verify the authenticity of data. Increase audience engagement and knowledge by dispensing information using Encryption Implementation Strategies Understanding Working Of Quantum Encryption Technology. This template helps you present information on four stages. You can also present information on Passing The Photon To Receiver, Verify Authenticity Of Data, Working Of Quantum, Encryption Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies Virtual Private Networks Configuration And Implementation
Encryption Implementation Strategies Virtual Private Networks Configuration And ImplementationThe purpose of this slide is to illustrate the process of tunnel creation between users device and the VPN server, which protects user data from interception. The key components include the user device, VPN client, VPN tunnel, server, and internet. Introducing Encryption Implementation Strategies Virtual Private Networks Configuration And Implementation to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Advertisers, Government Agencies, Virtual Private Networks, Configuration And Implementation Process, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Working Of Bring Your Own Encryption Model
Encryption Implementation Strategies Working Of Bring Your Own Encryption ModelThe purpose of this slide is to explain the importance of Bring Your Own Encryption BYOE approach. It also explains the deployment of encryption software and their applications hosted on a Cloud Service Provider CSP. The key components included are client apps, ciphertext, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Working Of Bring Your Own Encryption Model. Use it as a tool for discussion and navigation on Cloud Service Provider, Own Encryption Model, Secured Ciphertext, Clients Own Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Working Of Client Slide Field Level Encryption
Encryption Implementation Strategies Working Of Client Slide Field Level EncryptionThis slide illustrates the process of client-side field level encryption CSFLE. The key components demonstrated in the working process of CSFLE are app code, plaintext, field level encryption library, key store, ciphertext, data store, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Working Of Client Slide Field Level Encryption. Dispense information and present a thorough explanation of Working Of Client Slide, Field Level Encryption, Ciphertext, Data Store using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Working Steps Of Asymmetric Key Encryption
Encryption Implementation Strategies Working Steps Of Asymmetric Key EncryptionThis slide demonstrates the steps included in the working process of asymmetric key cryptography. The purpose of this slide is to illustrate the flow diagram of public key encryption. The key components included are registration, lookup, encrypt, decode, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Working Steps Of Asymmetric Key Encryption. Use it as a tool for discussion and navigation on Working Steps Of Asymmetric, Encrypt, Public Key Encryption, Asymmetric Key Cryptography. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Technologies To Secure Data In Transit Encryption Implementation Strategies
Encryption Technologies To Secure Data In Transit Encryption Implementation StrategiesThis slide compares different data in transit protection methods, including their working and associated cost. These methods are email encryption, Managed File Transfer MFT, Data Leak Prevention DLP, Cloud Access Security Brokers CASB, etc. Deliver an outstanding presentation on the topic using this Encryption Technologies To Secure Data In Transit Encryption Implementation Strategies. Dispense information and present a thorough explanation of Managed File Transfer, Cloud Access Security Brokers, Email Encryption, Encryption Technologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Icons Slide For Encryption Implementation Strategies Ppt Ideas Designs Download
Icons Slide For Encryption Implementation Strategies Ppt Ideas Designs DownloadPresenting our well crafted Icons Slide For Encryption Implementation Strategies Ppt Ideas Designs Download set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly.
-
 Overview Of Encryption For Securing Data At Rest Encryption Implementation Strategies
Overview Of Encryption For Securing Data At Rest Encryption Implementation StrategiesThis slide represents the different possible ways of protecting data at rest. The storage methods include file servers, network shares, document management systems, external storage, databases, endpoint devices, mobile devices, cloud storage, etc. Present the topic in a bit more detail with this Overview Of Encryption For Securing Data At Rest Encryption Implementation Strategies. Use it as a tool for discussion and navigation on Database Encryption, Information Rights Management, Data Leak Prevention, Mobile Device Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Encryption For Securing Data In Transit Encryption Implementation Strategies
Overview Of Encryption For Securing Data In Transit Encryption Implementation StrategiesThis slide represents the different possible ways of protecting data in transit. The methods include email encryption, MFT Managed File Transfer, IRM Information Rights Management, CASB Cloud Access Security Brokers, and DLP Data Leak Prevention. Deliver an outstanding presentation on the topic using this Overview Of Encryption For Securing Data In Transit Encryption Implementation Strategies. Dispense information and present a thorough explanation of Information Rights Management, Data Leak Prevention, Cloud Access Security Brokers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Issues Internet Things Encryption In Powerpoint And Google Slides Cpb
Security Issues Internet Things Encryption In Powerpoint And Google Slides CpbPresenting Security Issues Internet Things Encryption In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Issues Internet Things Encryption. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS V
Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS VThis slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Present the topic in a bit more detail with this Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS V Use it as a tool for discussion and navigation on Employee Headcount, Average Employee Age, Gender Diversity Ratio This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Encryption Secure Computer Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Encryption Secure Computer Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a visual representation of secure computer. It is a modern, vibrant and eye catching icon that will help to create an impactful presentation. It is a great way to emphasize the importance of data security and safety.
-
 Data Encryption Secure Computer Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Encryption Secure Computer Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is perfect for presentations on secure computer systems. It features a black and white design depicting a computer with a padlock, symbolizing the safety of your data. Use this icon to emphasize the importance of secure computing.
-
 Confidential Computing V2 What Is Fully Homomorphic Encryption FHE
Confidential Computing V2 What Is Fully Homomorphic Encryption FHEThis slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. Introducing Confidential Computing V2 What Is Fully Homomorphic Encryption FHE to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Strict Regulatory Compliance, Enhanced Cloud Security, Homomorphic Encryption, using this template. Grab it now to reap its full benefits.
-
 About Cryptography Techniques Cloud Encryption Cloud Cryptography
About Cryptography Techniques Cloud Encryption Cloud CryptographyThis slide talks about the cloud encryption methodologies. The purpose of this slide is to outline features and benefits of encryption tools used in cloud cryptography, such as data encryption, key management, etc. It also describes popular cloud encryption tools. Present the topic in a bit more detail with this About Cryptography Techniques Cloud Encryption Cloud Cryptography. Use it as a tool for discussion and navigation on Cryptography, Techniques, Compliance . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Applications Of Standard For Advanced Encryption Aes Algorithm Cloud Cryptography
Applications Of Standard For Advanced Encryption Aes Algorithm Cloud CryptographyThis slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc. Introducing Applications Of Standard For Advanced Encryption Aes Algorithm Cloud Cryptography to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Wireless Security, General File Encryption, Encrypted Browsing, using this template. Grab it now to reap its full benefits.
-
 Best Practices For Cloud Encryption Management Cloud Cryptography
Best Practices For Cloud Encryption Management Cloud CryptographyThis slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc. Increase audience engagement and knowledge by dispensing information using Best Practices For Cloud Encryption Management Cloud Cryptography. This template helps you present information on eight stages. You can also present information on Management, Manage Encryption Keys, Service Provider using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Common Data Encryption Des Overview And Applications Cloud Cryptography
Common Data Encryption Des Overview And Applications Cloud CryptographyThis slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc. Deliver an outstanding presentation on the topic using this Common Data Encryption Des Overview And Applications Cloud Cryptography. Dispense information and present a thorough explanation of Overview, Applications, Data Transmission using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Analysis Of Symmetric And Asymmetric Encryption Cloud Cryptography
Comparative Analysis Of Symmetric And Asymmetric Encryption Cloud CryptographyThis slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Present the topic in a bit more detail with this Comparative Analysis Of Symmetric And Asymmetric Encryption Cloud Cryptography. Use it as a tool for discussion and navigation on Comparative, Analysis, Asymmetric Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Features Of Encrypted Cloud Storage Cloud Cryptography
Key Features Of Encrypted Cloud Storage Cloud CryptographyThis slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc. Introducing Key Features Of Encrypted Cloud Storage Cloud Cryptography to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Encryption, Access Control, Collaboration, using this template. Grab it now to reap its full benefits.
-
 Standard For Advanced Encryption Aes Overview And Features Cloud Cryptography
Standard For Advanced Encryption Aes Overview And Features Cloud CryptographyThis slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length. Introducing Standard For Advanced Encryption Aes Overview And Features Cloud Cryptography to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Key Expansion, Overview, Processing, using this template. Grab it now to reap its full benefits.
-
 Working Of Common Data Encryption Des Algorithm Cloud Cryptography
Working Of Common Data Encryption Des Algorithm Cloud CryptographyThis slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Deliver an outstanding presentation on the topic using this Working Of Common Data Encryption Des Algorithm Cloud Cryptography. Dispense information and present a thorough explanation of Pseudorandom, Initialization, Independent using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Working Of Standard For Advanced Encryption Aes Algorithm Cloud Cryptography
Working Of Standard For Advanced Encryption Aes Algorithm Cloud CryptographyThis slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub-bytes, shift rows, etc. Present the topic in a bit more detail with this Working Of Standard For Advanced Encryption Aes Algorithm Cloud Cryptography. Use it as a tool for discussion and navigation on Demonstrates, Encryption, Algorithm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sales force Encrypted Fields Limitations In Powerpoint And Google Slides Cpb
Sales force Encrypted Fields Limitations In Powerpoint And Google Slides CpbPresenting Sales force Encrypted Fields Limitations In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Salesforce Encrypted Fields Limitations. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Shield Encryption Salesforce Limitations In Powerpoint And Google Slides Cpb
Shield Encryption Salesforce Limitations In Powerpoint And Google Slides CpbPresenting Shield Encryption Salesforce Limitations In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Shield Encryption Salesforce Limitations. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Encryption Safety Information Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Safety Information Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is perfect for conveying safety information in a visually appealing way. It features a bright yellow background with a black image of a safety helmet, clearly indicating the importance of safety. It is sure to draw attention and help your audience understand the importance of safety in any situation.
-
 Encryption Safety Information Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Safety Information Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is perfect for highlighting safety information in presentations. It features a figure in a safety vest and hardhat, with a warning sign in the background. The icon is a great visual aid to emphasize the importance of safety in the workplace.
-
 File Encryption Download Folder Colored Icon In Powerpoint Pptx Png And Editable Eps Format
File Encryption Download Folder Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon is perfect for adding a touch of vibrancy to your presentations. It comes in a range of colours and is easy to download and use. Ideal for making your slides stand out and engaging your audience.
-
 File Encryption Download Folder Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
File Encryption Download Folder Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is perfect for presentations. It is a high quality vector image that can be scaled to any size without losing its quality. It is easy to customize and can be used in any project.
-
 Data Encryption Model For Effective Comprehensive Guide For Deployment Strategy SS V
Data Encryption Model For Effective Comprehensive Guide For Deployment Strategy SS VThis slide represents data encryption model for effective information security It includes data encoding, data decoding, backup repository etc Introducing our Data Encryption Model For Effective Comprehensive Guide For Deployment Strategy SS V set of slides The topics discussed in these slides are Specialized Software, Handling Encryption, Authorized Parties This is an immediately available PowerPoint presentation that can be conveniently customized Download it and convince your audience
-
 Encryption Digital Digital Identity Blockchain In Powerpoint And Google Slides Cpb
Encryption Digital Digital Identity Blockchain In Powerpoint And Google Slides CpbPresenting our Encryption Digital Digital Identity Blockchain In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Encryption Digital Digital, Identity Blockchain This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Encrypted Google DOCS In Powerpoint And Google Slides Cpb
Encrypted Google DOCS In Powerpoint And Google Slides CpbPresenting our Encrypted Google DOCS In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Encrypted Google DOCS This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Padlock Heart Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Padlock Heart Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful icon features a lock and key design, perfect for adding a touch of security to presentations. Ideal for business, security, or safety-related topics, it will provide a professional and eye-catching look to any project.
-
 Padlock Heart Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Padlock Heart Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is perfect for presentations on security, access control, and encryption. It features a simple, black-and-white design of a lock and key, making it an ideal visual aid for any discussion of protection and safety.
-
 Encrypt And Create Backup Of Useful Data Implementing Cyber Risk Management Process
Encrypt And Create Backup Of Useful Data Implementing Cyber Risk Management ProcessThe following slide illustrates various methods to encrypt and back-up key data to avoid information loss and improved accessibility. It includes elements such as network attached storage, cloud storage services, flat backup system, details, advantages, disadvantages, cost. Present the topic in a bit more detail with this Encrypt And Create Backup Of Useful Data Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Advantages, Disadvantages. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker And Encryption Next Generation CASB
Cloud Access Security Broker And Encryption Next Generation CASBThis slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Present the topic in a bit more detail with this Cloud Access Security Broker And Encryption Next Generation CASB Use it as a tool for discussion and navigation on Security That Tracks Data, Terminated Moment, Content Access This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Encryption Algorithms Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Security Encryption Algorithms Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a great visual aid for representing folder password protection. It is a modern and vibrant design that will add a professional touch to any presentation. The icon is easy to use and can be used to quickly and effectively communicate the importance of password security.
-
 Cyber Security Encryption Algorithms Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Security Encryption Algorithms Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Folder Password is a simple yet effective way to protect your confidential data. It is easy to use and provides a secure encryption for your files. It is an ideal solution for those who want to keep their documents safe and secure.
-
 Data Encryption Storage Lock File Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Encryption Storage Lock File Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a great visual aid for representing folder password protection. It is a modern and vibrant design that will add a professional touch to any presentation. The icon is easy to use and can be used to quickly and effectively communicate the importance of password security.
-
 Data Encryption Storage Lock File Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Encryption Storage Lock File Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Folder Password is a simple yet effective way to protect your confidential data. It is easy to use and provides a secure encryption for your files. It is an ideal solution for those who want to keep their documents safe and secure.
-
 Encryption Data Protection Devices Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Data Protection Devices Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a great visual aid for representing folder password protection. It is a modern and vibrant design that will add a professional touch to any presentation. The icon is easy to use and can be used to quickly and effectively communicate the importance of password security.
-
 Encryption Data Protection Devices Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Data Protection Devices Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Folder Password is a simple yet effective way to protect your confidential data. It is easy to use and provides a secure encryption for your files. It is an ideal solution for those who want to keep their documents safe and secure.
-
 End To End Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps Format
End To End Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a visual representation of end to end encryption, a secure method of communication that ensures data is kept safe from interception. It is an effective way to protect confidential information and is ideal for businesses and organisations.
-
 End To End Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
End To End Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMonotone PowerPoint icon on End to end encryption is a simple yet powerful graphic that conveys the message of secure data transmission. It is perfect for presentations and documents that require a visual representation of the encryption process. The icon is easy to use and customize to fit any design needs.
-
 Data Encryption Cloud Computing In Powerpoint And Google Slides Cpb
Data Encryption Cloud Computing In Powerpoint And Google Slides CpbPresenting our Data Encryption Cloud Computing In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Data Encryption Cloud Computing. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Encrypt And Create Backup Of Useful Data Cyber Risk Assessment
Encrypt And Create Backup Of Useful Data Cyber Risk AssessmentThe following slide illustrates various methods to encrypt and back-up key data to avoid information loss and improved accessibility. It includes elements such as network attached storage, cloud storage services, flat backup system, details, advantages, disadvantages, cost, Deliver an outstanding presentation on the topic using this Encrypt And Create Backup Of Useful Data Cyber Risk Assessment Dispense information and present a thorough explanation of Network Attached, Backup System, Backup Services using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 About Bring Your Own Encryption Overview And Benefits Encryption For Data Privacy In Digital Age It
About Bring Your Own Encryption Overview And Benefits Encryption For Data Privacy In Digital Age ItThis slide discusses about widely used encryption method known as Bring Your Own Encryption BYOE. The purpose of this slide is to elaborate the meaning of BYOE. This slide also outlines the benefits of Bring Your Own Keys BYOK method. Present the topic in a bit more detail with this About Bring Your Own Encryption Overview And Benefits Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Overview, Encryption, Technique. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 About Cloud Encryption Tools And Services Encryption For Data Privacy In Digital Age It
About Cloud Encryption Tools And Services Encryption For Data Privacy In Digital Age ItThis slide talks about the cloud encryption methodologies. The purpose of this slide is to outline the encryption tools used in cloud cryptography. It also describes services provided by popular cloud encryption tools such as data encryption, key management, etc. Deliver an outstanding presentation on the topic using this About Cloud Encryption Tools And Services Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Encryption, Services, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





