Powerpoint Templates and Google slides for Encrypt
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Encryption For Data Privacy In Digital Age IT Powerpoint Presentation Slides
Encryption For Data Privacy In Digital Age IT Powerpoint Presentation SlidesEnthrall your audience with this Encryption For Data Privacy In Digital Age IT Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising two hundred fourty one slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Encryption Implementation Strategies Powerpoint Presentation Slides
Encryption Implementation Strategies Powerpoint Presentation SlidesThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Encryption Implementation Strategies Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of one hundred eight slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Cloud Data Encryption Implementation Plan Powerpoint Presentation Slides
Cloud Data Encryption Implementation Plan Powerpoint Presentation SlidesEnthrall your audience with this Cloud Data Encryption Implementation Plan Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising sixty eight slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Encryption For Data Security Powerpoint Presentation Slides Cybersecurity CD
Encryption For Data Security Powerpoint Presentation Slides Cybersecurity CDDitch the Dull templates and opt for our engaging Encryption For Data Security Powerpoint Presentation Slides Cybersecurity CD deck to attract your audience. Our visually striking design effortlessly combines creativity with functionality, ensuring your content shines through. Compatible with Microsoft versions and Google Slides, it offers seamless integration of presentation. Save time and effort with our pre-designed PPT layout, while still having the freedom to customize fonts, colors, and everything you ask for. With the ability to download in various formats like JPG, JPEG, and PNG, sharing your slides has never been easier. From boardroom meetings to client pitches, this deck can be the secret weapon to leaving a lasting impression.
-
 Encryption Framework Upgradation Proposal Powerpoint Presentation Slides
Encryption Framework Upgradation Proposal Powerpoint Presentation SlidesIf your company needs to submit a Encryption Framework Upgradation Proposal Powerpoint Presentation Slides look no further. Our researchers have analyzed thousands of proposals on this topic for effectiveness and conversion. Just download our template add your company data and submit to your client for a positive response.
-
 Data Encryption Powerpoint Ppt Template Bundles
Data Encryption Powerpoint Ppt Template BundlesIf you require a professional template with great design, then this Data Encryption Powerpoint Ppt Template Bundles is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twenty two slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 End To End Encryption Powerpoint PPT Template Bundles
End To End Encryption Powerpoint PPT Template BundlesDeliver a lucid presentation by utilizing this End To End Encryption Powerpoint PPT Template Bundles. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as End-To-End Encryption, Chat Privacy, Whatsapp Encryption, Encryption Challenges Solutions, Business Trends Encryption, Encryption Backup Systems. All the Twenty slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
 Encryption Powerpoint PPT Template Bundles
Encryption Powerpoint PPT Template BundlesEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Encryption Powerpoint PPT Template Bundles is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With fourteen slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
 Data Encryption In Ransomware Attacks Training Ppt
Data Encryption In Ransomware Attacks Training PptPresenting Data Encryption in Ransomware Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Lack Of Encryption As An Information Security Threat Training Ppt
Lack Of Encryption As An Information Security Threat Training PptPresenting Lack of Encryption as an Information Security Threat. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Encryption As A Type Of Application Security Training Ppt
Encryption As A Type Of Application Security Training PptPresenting Encryption as a Type of Application Security. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Firewall Enterprise Protection Security Installation Encryption
Firewall Enterprise Protection Security Installation EncryptionIntroduce your topic and host expert discussion sessions with this Firewall Enterprise Protection Security Installation Encryption. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the twelve slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
-
 Blockchain icon symbol circle computers encryption security technology
Blockchain icon symbol circle computers encryption security technologyEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Blockchain Icon Symbol Circle Computers Encryption Security Technology is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With twelve slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
 Data Encryption Performance Tracking Dashboard Cloud Data Encryption
Data Encryption Performance Tracking Dashboard Cloud Data EncryptionThis slide represents the dashboard which can be utilized by organization to monitor cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, patches, highest number of critical incidents, etc. Deliver an outstanding presentation on the topic using this Data Encryption Performance Tracking Dashboard Cloud Data Encryption. Dispense information and present a thorough explanation of Progress, Critital Risks Identified using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption For Data Challenges Organization Is Facing With Encryption Cybersecurity SS
Encryption For Data Challenges Organization Is Facing With Encryption Cybersecurity SSThis slide showcases challenges organization is facing relating to encryption. Its purpose is to make businesses aware of major and potential vulnerabilities. It provides information about data discovery, compliance, etc. Present the topic in a bit more detail with this Encryption For Data Challenges Organization Is Facing With Encryption Cybersecurity SS. Use it as a tool for discussion and navigation on Problems, Data Discovery, Delayed Security Deployments. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Budget For Cloud Data Encryption Implementation Training Cloud Data Encryption
Budget For Cloud Data Encryption Implementation Training Cloud Data EncryptionThis slide shows the cost breakup of cloud data encryption implementation training. The purpose of this slide is to highlight the estimated cost of various training components, such as instructors cost, training material cost, etc. Deliver an outstanding presentation on the topic using this Budget For Cloud Data Encryption Implementation Training Cloud Data Encryption. Dispense information and present a thorough explanation of Components, Estimated Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Client Side Encryption With Kms Managed Keys Cloud Data Encryption
Client Side Encryption With Kms Managed Keys Cloud Data EncryptionThis slide demonstrates the process for client side encryption with keys managed by Key Management System. The components included are plain text data key, cipher blob data key, encryption algorithm, encrypted object data, etc. Deliver an outstanding presentation on the topic using this Client Side Encryption With Kms Managed Keys Cloud Data Encryption. Dispense information and present a thorough explanation of Encryption Process, Encryption Algorithm using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Server Side Encryption With Kms Managed Keys Cloud Data Encryption
Server Side Encryption With Kms Managed Keys Cloud Data EncryptionThis slide demonstrates the process for server side encryption with keys managed by Key Management System. The components included are plain text data key, customer managed key, encryption algorithm, encrypted object data, encrypted data key, etc. Present the topic in a bit more detail with this Server Side Encryption With Kms Managed Keys Cloud Data Encryption. Use it as a tool for discussion and navigation on Encryption Process, Customer Managed Key. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Statistics Of Cloud Data Security Attacks In Organization Cloud Data Encryption
Statistics Of Cloud Data Security Attacks In Organization Cloud Data EncryptionThis slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc. Deliver an outstanding presentation on the topic using this Statistics Of Cloud Data Security Attacks In Organization Cloud Data Encryption. Dispense information and present a thorough explanation of Data Interception, Unauthorized Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Cyber Attacks Impact On Organization In Previous Financial Year
Encryption Implementation Strategies Cyber Attacks Impact On Organization In Previous Financial YearThis slide depicts the financial loss experienced by the company in the last year due to different types of data privacy concerns. The purpose of this slide is to illustrate how increasing cyber scams have impacted the organization from april 2022 to april 2023. Present the topic in a bit more detail with this Encryption Implementation Strategies Cyber Attacks Impact On Organization In Previous Financial Year. Use it as a tool for discussion and navigation on Cyber Attacks, Financial Loss, Organization Experienced Loss, Data Privacy Concerns. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Data Encryption Performance Tracking Dashboard
Encryption Implementation Strategies Data Encryption Performance Tracking DashboardThis slide represents the dashboard which can be utilized by organization to monitor cryptographic security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, patches, highest number of critical incidents, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Data Encryption Performance Tracking Dashboard. Use it as a tool for discussion and navigation on Data Encryption Performance, Tracking Dashboard, Critical Incidents, Incident Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Overview Of Data Privacy Attacks In Different Departments
Encryption Implementation Strategies Overview Of Data Privacy Attacks In Different DepartmentsThis slide summarizes data security attacks across different organizational departments, such as human resources, IT department, finance, marketing, operations, etc. The outlined attacks are phishing scams, malware infections, data breaches, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Overview Of Data Privacy Attacks In Different Departments. Use it as a tool for discussion and navigation on Human Resources, IT Department, Finance, Marketing, Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Steps To Implement Encryption Techniques In Organization
Encryption Implementation Strategies Steps To Implement Encryption Techniques In OrganizationThis slide discusses the procedure for implementing encryption in applications. The steps mentioned in this slide are identify sensitive data, assess encryption requirements, choose encryption algorithms, implement data encryption at rest, etc. Introducing Encryption Implementation Strategies Steps To Implement Encryption Techniques In Organization to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Implement Data Encryption At Rest, Deploy Data Encryption In Transit, Assess Encryption Requirements, Choose Encryption Algorithms, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Encryption Implementation Strategies Ppt Ideas Examples
Table Of Contents For Encryption Implementation Strategies Ppt Ideas ExamplesIntroducing Table Of Contents For Encryption Implementation Strategies Ppt Ideas Examples to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Encryption Overview, States Of Data Protection, Current Situation Of Company, Encryption Implementation Strategies, using this template. Grab it now to reap its full benefits.
-
 Applications As A Service In Organizations Encryption For Data Privacy In Digital Age It
Applications As A Service In Organizations Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to outline the major uses of Encryption-as-Service method in different domains. The key applications discussed in this slide are all-time security assurance, secure sensitive information and maintaining regulatory compliance. Introducing Applications As A Service In Organizations Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Maintaining Regulatory Compliance, Secure Sensitive Information, Security Assurance, using this template. Grab it now to reap its full benefits.
-
 Comparison Symmetric And Asymmetric Encryption Encryption For Data Privacy In Digital Age It
Comparison Symmetric And Asymmetric Encryption Encryption For Data Privacy In Digital Age ItThis slide outlines the differences between symmetric and asymmetric encryption methods. The purpose of this slide is to compare the two main data encryption techniques known as symmetric key cryptography and asymmetric key cryptography. Present the topic in a bit more detail with this Comparison Symmetric And Asymmetric Encryption Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Asymmetric, Encryption, Comparison. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Encryption Performance Tracking Dashboard Encryption For Data Privacy In Digital Age It
Data Encryption Performance Tracking Dashboard Encryption For Data Privacy In Digital Age ItThis slide represents the dashboard which can be utilized by organization to monitor cryptographic security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, patches, highest number of critical incidents, etc. Deliver an outstanding presentation on the topic using this Data Encryption Performance Tracking Dashboard Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Encryption, Performance, Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Global Cloud Encryption Market Analysis Encryption For Data Privacy In Digital Age It
Global Cloud Encryption Market Analysis Encryption For Data Privacy In Digital Age ItThis slide depicts the market analysis of the global cloud cryptography usage. The purpose of this slide is to showcase the market analysis based on regions such as North America, Europe, Asia Pacific, Middle East and Arica, and South America. Present the topic in a bit more detail with this Global Cloud Encryption Market Analysis Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Regional Analysis, Segment Overview, Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Global Hardware Encryption Market Analysis Encryption For Data Privacy In Digital Age It
Global Hardware Encryption Market Analysis Encryption For Data Privacy In Digital Age ItThis slide depicts the market analysis of the global hardware encryption usage. The purpose of this slide is to showcase the market analysis based on regions and applications such as commercial, residential, industrial and government agencies. Deliver an outstanding presentation on the topic using this Global Hardware Encryption Market Analysis Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Hardware, Encryption, Analysisusing the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Global Network Encryption Market Analysis Encryption For Data Privacy In Digital Age It
Global Network Encryption Market Analysis Encryption For Data Privacy In Digital Age ItThis slide depicts the market analysis of the global network encryption usage. The purpose of this slide is to showcase the market analysis based on regions such as North America, Europe, Asia Pacific, Middle East and Arica, and South America. Present the topic in a bit more detail with this Global Network Encryption Market Analysis Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Global Network, Encryption, Market Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Global Software Encryption Market Analysis Encryption For Data Privacy In Digital Age It
Global Software Encryption Market Analysis Encryption For Data Privacy In Digital Age ItThis slide depicts the market analysis of the global software encryption usage. The purpose of this slide is to showcase the market analysis based on application segment view, such as disk encryption, database encryption, cloud encryption, etc. Deliver an outstanding presentation on the topic using this Global Software Encryption Market Analysis Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Software, Encryption, Market Analysis using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Latest Advancements In Data Encryption Technology Encryption For Data Privacy In Digital Age It
Latest Advancements In Data Encryption Technology Encryption For Data Privacy In Digital Age ItThis slide demonstrates the recent cryptographic trends in cyber security. The purpose of this slide is to represent the current advances in encryption technology. These include homomorphic encryption, honey encryption and biometric encryption. Increase audience engagement and knowledge by dispensing information using Latest Advancements In Data Encryption Technology Encryption For Data Privacy In Digital Age It. This template helps you present information on three stages. You can also present information on Homomorphic Encryption, Honey Encryption, Biometric Encryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Implement Encryption Techniques In Organization Encryption For Data Privacy In Digital Age It
Steps To Implement Encryption Techniques In Organization Encryption For Data Privacy In Digital Age ItThis slide discusses the procedure for implementing encryption in applications. The steps mentioned in this slide are identify sensitive data, assess encryption requirements, choose encryption algorithms, implement data encryption at rest, etc. Introducing Steps To Implement Encryption Techniques In Organization Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Identify Sensitive Data, Choose Encryption Algorithms, Deploy Data Encryption In Transit, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Encryption For Data Privacy In Digital Age
Table Of Contents For Encryption For Data Privacy In Digital AgeDeliver an outstanding presentation on the topic using this Table Of Contents For Encryption For Data Privacy In Digital Age. Dispense information and present a thorough explanation of Encryption Overview, Importance Of Encryption, Encryption Market And Trends using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
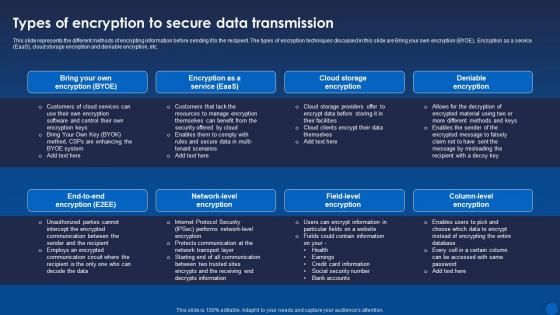 Types Of Encryption To Secure Data Transmission Encryption For Data Privacy In Digital Age It
Types Of Encryption To Secure Data Transmission Encryption For Data Privacy In Digital Age ItThis slide represents the different methods of encrypting information before sending it to the recipient. The types of encryption techniques discussed in this slide are Bring your own encryption BYOE, Encryption as a service EaaS, cloud storage encryption and deniable encryption, etc. Present the topic in a bit more detail with this Types Of Encryption To Secure Data Transmission Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Data Transmission, Encryption, Deniable Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Understanding Homomorphic Encryption Technology Encryption For Data Privacy In Digital Age It
Understanding Homomorphic Encryption Technology Encryption For Data Privacy In Digital Age ItThis slide illustrates the working process of homomorphic encryption by using algebraic principle of homomorphism. This slide also talks about the operations performed on ciphertext such as arithmetic, multiplication and Boolean. Present the topic in a bit more detail with this Understanding Homomorphic Encryption Technology Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Homomorphic, Encryption, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Understanding Working Of Quantum Encryption Technology Encryption For Data Privacy In Digital Age It
Understanding Working Of Quantum Encryption Technology Encryption For Data Privacy In Digital Age ItThis slide demonstrates the steps involved in encrypting and decrypting the keys using quantum cryptography. The steps involved are passing the photon to receiver, receive the photon, set the kay by analysing correct streams and verify the authenticity of data. Increase audience engagement and knowledge by dispensing information using Understanding Working Of Quantum Encryption Technology Encryption For Data Privacy In Digital Age It. This template helps you present information on four stages. You can also present information on Passing The Photon To Receiver, Receive The Photon, Verify Authenticity Of Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Using Elliptic Curves To Prioritize Cryptographic Strength Encryption For Data Privacy In Digital Age It
Using Elliptic Curves To Prioritize Cryptographic Strength Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to highlight the fundamental properties and concepts of elliptic curves that serve as the foundation for the Elliptic Curve Cryptography ECC algorithm. The key components include single line intersection and horizontal symmetry. Present the topic in a bit more detail with this Using Elliptic Curves To Prioritize Cryptographic Strength Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Prioritize, Cryptographic, Strength. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Of Rivest Shamir Adleman Algorithm Encryption For Data Privacy In Digital Age It
Working Of Rivest Shamir Adleman Algorithm Encryption For Data Privacy In Digital Age ItThis slide discusses the procedure of RSA asymmetric encryption algorithm. The purpose of this slide is to outline the two steps of Rivest Shamir Adleman RSA algorithm, named as key generation, and function of encryption and decryption. Deliver an outstanding presentation on the topic using this Working Of Rivest Shamir Adleman Algorithm Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Algorithm, Ciphered Data, Decrypted Plaintext Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Client Testimonials For Encryption Framework Upgradation Proposal
Client Testimonials For Encryption Framework Upgradation ProposalThis slide showcases a collection of customer testimonials received from multiple clients who have graciously shared their feedback with the organization. It highlights the names and designations of the clients. Introducing Client Testimonials For Encryption Framework Upgradation Proposal to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Client Testimonials, Encryption Framework, Customer Testimonials, using this template. Grab it now to reap its full benefits.
-
 Our Process For Upgrading Existing Encryption Framework Upgradation Proposal
Our Process For Upgrading Existing Encryption Framework Upgradation ProposalThis slide outlines the process of upgrading the existing encryption framework to automated sequential cryptography system. The key components of this process involves original data, random key generator, cloud storage, private database, encryption and decryption process, etc. Present the topic in a bit more detail with this Our Process For Upgrading Existing Encryption Framework Upgradation Proposal. Use it as a tool for discussion and navigation on Encryption Framework, Cloud Storage, Private Database, Encryption And Decryption Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Our Team For Encryption Framework Upgradation Proposal
Our Team For Encryption Framework Upgradation ProposalThis slide represents an overview of the team structure for the encryption framework upgradation proposal. It highlights the names and designations of each team member in accordance with their position within the hierarchy. Increase audience engagement and knowledge by dispensing information using Our Team For Encryption Framework Upgradation Proposal. This template helps you present information on three stages. You can also present information on Our Team, Encryption Framework, Upgradation Proposal, Expertise And Achievements using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Pricing Summary For Encryption Framework Upgradation Proposal
Pricing Summary For Encryption Framework Upgradation ProposalThis slide showcases the cost of the encryption upgradation proposal. It includes the different costs related to hardware, software, professional services, total service costs, software licenses, key management solutions, and contingency budgets. Present the topic in a bit more detail with this Pricing Summary For Encryption Framework Upgradation Proposal. Use it as a tool for discussion and navigation on Encryption Framework, Upgradation Proposal, Key Management Solutions, Contingency Budgets. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Encrypted Email Practices For Secure Messaging Cybersecurity SS
Encryption For Data Encrypted Email Practices For Secure Messaging Cybersecurity SSThis slide showcases public key cryptography deployment which can help employees increased speed and user experience of their platforms. It provides details about private key, key generation, decryption, etc. Present the topic in a bit more detail with this Encryption For Data Encrypted Email Practices For Secure Messaging Cybersecurity SS. Use it as a tool for discussion and navigation on Reduced Data Breaches, Reduced Email Compromises, Create Strong Passwords. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Endpoint Encryption Progress Monitoring Dashboard Cybersecurity SS
Encryption For Data Endpoint Encryption Progress Monitoring Dashboard Cybersecurity SSThis slide showcases endpoint encryption progress monitoring dashboard focused on tracking protection status of organizations computers. It provides details about warning period, managed, decrypted drives, etc. Present the topic in a bit more detail with this Encryption For Data Endpoint Encryption Progress Monitoring Dashboard Cybersecurity SS. Use it as a tool for discussion and navigation on Decrypting, Managed Computers, Non-Reporting Computers, Computer With Decrypted Drives. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Impact Analysis Of Comprehensive Encryption Strategies Cybersecurity SS
Encryption For Data Impact Analysis Of Comprehensive Encryption Strategies Cybersecurity SSThis slide showcases post implementation analysis of encryption strategies. Its purpose is to make businesses aware of major and potential improvements. It provides information about vulnerabilities, costs, responsiveness, etc. Present the topic in a bit more detail with this Encryption For Data Impact Analysis Of Comprehensive Encryption Strategies Cybersecurity SS. Use it as a tool for discussion and navigation on Costs, Responsiveness Speed, Vulnerabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Major Types Of Encryption For Data Security Cybersecurity SS
Encryption For Data Major Types Of Encryption For Data Security Cybersecurity SSThis slide major types of encryption technology, focused on improving data privacy and security of todays business. It provides details about symmetric, asymmetric, RSA, data encryption standard, etc. Introducing Encryption For Data Major Types Of Encryption For Data Security Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Symmetric Encryption, Asymmetric Encryption, RSA Encryption, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data SSL Protocol Deployment For Secure Communication Cybersecurity SS
Encryption For Data SSL Protocol Deployment For Secure Communication Cybersecurity SSThis slide showcases secure socket layer SSL deployment which can help employees perform secure communication within businesses. It provides details about certificate authority, webmaster, etc. Present the topic in a bit more detail with this Encryption For Data SSL Protocol Deployment For Secure Communication Cybersecurity SS. Use it as a tool for discussion and navigation on Reduced Message Forgery, Reduced Data Theft, Less Eavesdropping. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threat Analysis With Data Encryption
Cyber Threat Analysis With Data EncryptionThe purpose of this slide is to highlight how cyber threat analysis with data encryption fortifies security. It offers proactive insights into potential threats, ensuring a robust defense, and safeguarding sensitive information in the evolving landscape of cyber threats. Introducing our Cyber Threat Analysis With Data Encryption set of slides. The topics discussed in these slides are Cybersecurity Threat, Budget Constraints, Inadequate Training And Awareness. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Encryption Adoption In Different Sectors
Data Encryption Adoption In Different SectorsThe purpose of this slide is to highlight how data encryption is adopted in different sectors. It enhances cybersecurity, safeguarding sensitive information, and ensuring confidentiality in various industries. Introducing our Data Encryption Adoption In Different Sectors set of slides. The topics discussed in these slides are Government, Education, Technology, Healthcare, Finance. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
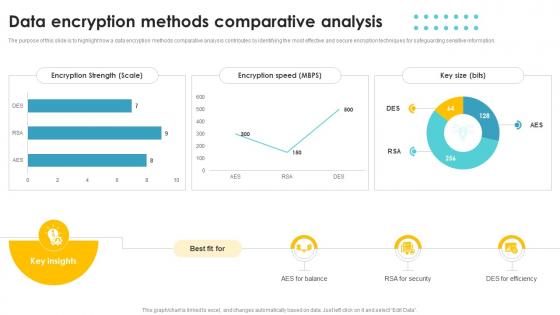 Data Encryption Methods Comparative Analysis
Data Encryption Methods Comparative AnalysisThe purpose of this slide is to highlight how a data encryption methods comparative analysis contributes by identifying the most effective and secure encryption techniques for safeguarding sensitive information. Introducing our Data Encryption Methods Comparative Analysis set of slides. The topics discussed in these slides are Encryption Strength, Encryption Speed, Key Size. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Trends In Data Encryption Adoption And Effectiveness
Trends In Data Encryption Adoption And EffectivenessThe slide aims to provide insights into trends in data encryption adoption and effectiveness, guiding organizations in optimizing cybersecurity measures against evolving threats. Introducing our Trends In Data Encryption Adoption And Effectiveness set of slides. The topics discussed in these slides are Increased Awareness Of Cybersecurity Threats, Advancements In Encryption Technologies. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Confidential Computing Market What Is Fully Homomorphic Encryption Fhe
Confidential Computing Market What Is Fully Homomorphic Encryption FheThis slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. Deliver an outstanding presentation on the topic using this Confidential Computing Market What Is Fully Homomorphic Encryption Fhe. Dispense information and present a thorough explanation of Homomorphic, Encryption, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 WIFI Off Wireless Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps Format
WIFI Off Wireless Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis is a coloured powerpoint icon of a WIFI symbol with a red cross over it, indicating the WIFI is off. Ideal for presentations or documents related to technology, networks and internet security.
-
 WIFI Off Wireless Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
WIFI Off Wireless Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint icon is perfect for presentations that need to communicate the concept of WIFI Off. It features a simple, minimalistic design that is easy to recognize and eye catching. The icon is available in both vector and raster formats for easy use.
-
 User Authentication Encryption Login Colored Icon In Powerpoint Pptx Png And Editable Eps Format
User Authentication Encryption Login Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is perfect for making your presentation stand out. It features a login symbol in bright and vivid colours that will draw the attention of your audience. It is easy to use and can be resized to fit your needs. Get creative and make your presentation memorable with this powerpoint icon.
-
 User Authentication Encryption Login Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
User Authentication Encryption Login Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMonotone Powerpoint Icon on Login is a high-quality vector icon designed to be used in presentations, websites, and other digital projects. It features a simple, minimalistic design with a monotone color palette, making it perfect for modern and professional designs.
-
 WIFI Encryption Security Device Colored Icon In Powerpoint Pptx Png And Editable Eps Format
WIFI Encryption Security Device Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis PowerPoint icon features a colourful illustration of a lock, symbolizing the security of a wireless network. It is perfect for presentations on WIFI security, data protection, and cyber safety. Use this icon to emphasize the importance of secure networks and data privacy.
-
 WIFI Encryption Security Device Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
WIFI Encryption Security Device Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is perfect for any presentation on WIFI security. It features a classic black and white design with a laptop and a router, making it ideal for any modern business presentation. It is easy to use and can be used to illustrate the importance of secure WIFI connections.
-
 File Encryption Sharing Colored Icon In Powerpoint Pptx Png And Editable Eps Format
File Encryption Sharing Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis cheerful coloured powerpoint icon is perfect for illustrating file sharing. It features a cloud with an arrow pointing up and down, representing the transfer of files between two sources.




