Powerpoint Templates and Google slides for Data security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Tokenization For Improved Data Security Working Of Security Tokenization In Financial Assets
Tokenization For Improved Data Security Working Of Security Tokenization In Financial AssetsThis slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc. Introducing Tokenization For Improved Data Security Working Of Security Tokenization In Financial Assets to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Working Of Security Tokenization, Financial Assets, Dividend Distribution, Security Token Classification, using this template. Grab it now to reap its full benefits.
-
 Data Destruction Techniques For Securely Disposing Data Lifecycle Management To Enhance Flow
Data Destruction Techniques For Securely Disposing Data Lifecycle Management To Enhance FlowThis slide presents various data destruction techniques for securely disposing of data. It provides details about techniques such as, overwriting, degussing, physical destruction, cryptographic erasure and secure erase. Present the topic in a bit more detail with this Data Destruction Techniques For Securely Disposing Data Lifecycle Management To Enhance Flow. Use it as a tool for discussion and navigation on Physical Destruction, Cryptographic Erasure, Secure Erase, Data Destruction Technique. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Integrating Algorithms For Encrypting Data Securely Data Lifecycle Management To Enhance Flow
Integrating Algorithms For Encrypting Data Securely Data Lifecycle Management To Enhance FlowThis slide presents algorithms for encrypting data to ensure its protection and security. It includes types such as, AES advanced encryption standard and RSA rivest-shamir-adleman and ECC elliptic curve cryptography. Present the topic in a bit more detail with this Integrating Algorithms For Encrypting Data Securely Data Lifecycle Management To Enhance Flow. Use it as a tool for discussion and navigation on Encryption Algorithm, Key Characteristics, Implementation In Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Archival Stage To Ensure Secure Data Lifecycle Management To Enhance Flow
Overview Of Archival Stage To Ensure Secure Data Lifecycle Management To Enhance FlowThis stage presents an overview of the archival data stage to optimizes how necessary resources perform in the active system. It includes information about goals and benefits such as minimizing cost, enhanced backup and restore performance and decrease in data loss. Present the topic in a bit more detail with this Overview Of Archival Stage To Ensure Secure Data Lifecycle Management To Enhance Flow. Use it as a tool for discussion and navigation on Data Archive Storage Devices, Long-Term Retention And Storage Of Data, Cost-Effective Information Storage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agenda Encryption For Data Security Cybersecurity SS
Agenda Encryption For Data Security Cybersecurity SSIntroducing Agenda Encryption For Data Security Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on General Overview, Concepts And Global Significance, Key Management, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Define Security Requirements For Encryption Strategy Cybersecurity SS
Encryption For Data Define Security Requirements For Encryption Strategy Cybersecurity SSThis slide showcases encryption best practice focused on defining security requirements. It provides details about threat assessment, system vulnerabilities, business decisions, etc. Introducing Encryption For Data Define Security Requirements For Encryption Strategy Cybersecurity SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Conduct Threat Assessment, Learn Of Any Business Decisions, System Vulnerabilities, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Homomorphic Cryptography For Data Base Security Cybersecurity SS
Encryption For Data Homomorphic Cryptography For Data Base Security Cybersecurity SSThis slide showcases homomorphic cryptography deployment which can help employees increase data privacy and outsourcing security. It provides details about private key, plaintext, decryption, etc. Introducing Encryption For Data Homomorphic Cryptography For Data Base Security Cybersecurity SS to increase your presentation threshold. Encompassed with Eight stages, this template is a great option to educate and entice your audience. Dispence information on Homomorphic Encryption, Classified Plaintext, Decrypted Results, Data Owner Organization, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Organizational Chart Of Cyber Security Department Cybersecurity SS
Encryption For Data Organizational Chart Of Cyber Security Department Cybersecurity SSThis slide showcases hierarchy chart focused on building cybersecurity teams to help improve business data encryption. It provides details about DevOps, CISO, encryption specialist, engineer, etc. Present the topic in a bit more detail with this Encryption For Data Organizational Chart Of Cyber Security Department Cybersecurity SS. Use it as a tool for discussion and navigation on Organizational Chart, Cyber Security Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Password Encryption Strategy For Maximum Security Cybersecurity SS
Encryption For Data Password Encryption Strategy For Maximum Security Cybersecurity SSThis slide showcases password encryption policies which can help organizations achieve maximum data security. It provides details about salting, SHA-2, Bcrypt, passcode age, auto-lock, etc. Present the topic in a bit more detail with this Encryption For Data Password Encryption Strategy For Maximum Security Cybersecurity SS. Use it as a tool for discussion and navigation on Require Alphanumeric Value, Maximum Passcode Age, Grace Period For Device Lock. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Public Key Cryptography For Secure Access Cybersecurity SS
Encryption For Data Public Key Cryptography For Secure Access Cybersecurity SSThis slide showcases public key cryptography deployment which can help employees increased speed and user experience of their platforms. It provides details about private key, key generation, decryption, etc. Present the topic in a bit more detail with this Encryption For Data Public Key Cryptography For Secure Access Cybersecurity SS. Use it as a tool for discussion and navigation on Potential Impact, Increased Speed, Improved User Experience. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Roles And Responsibilities Of Cyber Security Department Cybersecurity SS
Encryption For Data Roles And Responsibilities Of Cyber Security Department Cybersecurity SSThis slide showcases roles and responsibilities of cybersecurity teams which can help improve business data encryption. It provides details about CTO, key management, encryption specialist and engineer, etc. Introducing Encryption For Data Roles And Responsibilities Of Cyber Security Department Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Key Management, Encryption Engineer, Chief Technology Officer, Encryption Specialist, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Security Defense Arsenal For Data Encryption Cybersecurity SS
Encryption For Data Security Defense Arsenal For Data Encryption Cybersecurity SSThis slide showcases encryption best practice focused on implementing security defense arsenal for data protection. It provides details about firewall, antimalware, authentication, encryption, etc. Introducing Encryption For Data Security Defense Arsenal For Data Encryption Cybersecurity SS to increase your presentation threshold. Encompassed with Seven stages, this template is a great option to educate and entice your audience. Dispence information on Firewall, Anti Malware, Authentication, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Encryption For Data Security Cybersecurity SS
Table Of Contents Encryption For Data Security Cybersecurity SSIntroducing Table Of Contents Encryption For Data Security Cybersecurity SS to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Team For Encryption, Encryption Costs Analysis, Pre Implementation Best Practices, using this template. Grab it now to reap its full benefits.
-
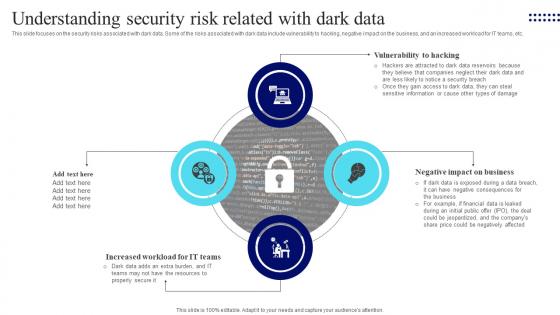 Management Of Redundant Data Understanding Security Risk Related With Dark Data
Management Of Redundant Data Understanding Security Risk Related With Dark DataThis slide focuses on the security risks associated with dark data. Some of the risks associated with dark data include vulnerability to hacking, negative impact on the business, and an increased workload for IT teams, etc. Introducing Management Of Redundant Data Understanding Security Risk Related With Dark Data to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Increased Workload For IT Teams, Negative Impact On Business, Vulnerability To Hacking, using this template. Grab it now to reap its full benefits.
-
 Assessing Data Storage Options To Ensure Securely Data Lifecycle Management To Enhance Flow
Assessing Data Storage Options To Ensure Securely Data Lifecycle Management To Enhance FlowThis slide presents the types of data storage technologies for data lifecycle management. It provides information about, relational , non-relational, object storage and cloud storage databases. Present the topic in a bit more detail with this Assessing Data Storage Options To Ensure Securely Data Lifecycle Management To Enhance Flow. Use it as a tool for discussion and navigation on Relational Databases, Object Storage, Cloud Data Storage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Physical Security Systems To Enhance Data Safety
Physical Security Systems To Enhance Data SafetyThis slide showcases physical control systems to manage and safeguard crucial data. The systems covered are cable infrastructure, fire alarm, building management, etc. Introducing our premium set of slides with Physical Security Systems To Enhance Data Safety. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cable Infrastructure, Electronic Security Systems, Building Management. So download instantly and tailor it with your information.
-
 Case Study Data Breach Incident Recovery Business Recovery Plan To Overcome Cyber Security Threat
Case Study Data Breach Incident Recovery Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about a case study related to data breach recovery. It includes key elements such as incident date, challenges faced, LinkedIn response plan, and results. Deliver an outstanding presentation on the topic using this Case Study Data Breach Incident Recovery Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Regain Customer Trust, Rebuilding Business Reputation, Linkedin Response using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Multi Factor A For Business Data Protection Business Recovery Plan To Overcome Cyber Security Threat
Multi Factor A For Business Data Protection Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information leveraging multifactor authentication to increase cyber security. It includes key points such as failed login, geographic location, time of login, operating system, IP address, etc. Deliver an outstanding presentation on the topic using this Multi Factor A For Business Data Protection Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Time Of Login Attempt, Operating System, Source Of IP Address using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Securing Food Safety In Online Leveraging Data Analytics To Forecast Deliveries
Securing Food Safety In Online Leveraging Data Analytics To Forecast DeliveriesThis slide covers utilizing data analytics tools to forecast demand involves key components such as predictive analytics, customer segmentation and sentiment analysis. Introducing Securing Food Safety In Online Leveraging Data Analytics To Forecast Deliveries to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Predictive Analytics, Customer Segmentation, Sentiment Analysis, using this template. Grab it now to reap its full benefits.
-
 Regtech Icon For Efficient Data Management And Security
Regtech Icon For Efficient Data Management And SecurityIntroducing our premium set of slides with name Regtech Icon For Efficient Data Management And Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Regtech Icon, Efficient Data, Management And Security. So download instantly and tailor it with your information.
-
 SIEM Data Cyber Security Icon
SIEM Data Cyber Security IconPresenting our set of slides with name SIEM Data Cyber Security Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on SIEM data cyber security icon.
-
 Big Data Model Of Security Sharing Based On Blockchain
Big Data Model Of Security Sharing Based On BlockchainThis slide gives an overview of the big data model of security sharing based on blockchain which include citizen, government, school, student, individual, etc. Presenting our set of slides with Big Data Model Of Security Sharing Based On Blockchain. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Collect Data, Smart Contract, Query Data.
-
 Data Transmission In Blockchain Security Icon
Data Transmission In Blockchain Security IconIntroducing our premium set of slides with Data Transmission In Blockchain Security Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Transmission, Blockchain Security, Icon. So download instantly and tailor it with your information.
-
 Cybersecurity Policy Checklist To Secure Sensitive Data
Cybersecurity Policy Checklist To Secure Sensitive DataThis slide showcases the cybersecurity policy checklist protecting sensitive data which helps an organization to secure technology and information assets and control business information. It include details such as prepare, verify, analyze, respond, etc. Introducing our Cybersecurity Policy Checklist To Secure Sensitive Data set of slides. The topics discussed in these slides are Prepare, AnalyzeThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Desktop As A Service Icon For Improving Data Security
Desktop As A Service Icon For Improving Data SecurityPresenting our set of slides with Desktop As A Service Icon For Improving Data Security This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Desktop As A Service Icon, Improving Data Security
-
 E Commerce Subscription Data Security Management Techniques
E Commerce Subscription Data Security Management TechniquesThis slide highlights the techniques to secure e-commerce subscription data to ensure data protection and management for trust building. Key strategies are encryption strategy, hand-on monitoring, and contingency planning. Introducing our premium set of slides with E Commerce Subscription Data Security Management Techniques Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Encryption Strategy, Hands-On Monitoring, Contingency Planning So download instantly and tailor it with your information.
-
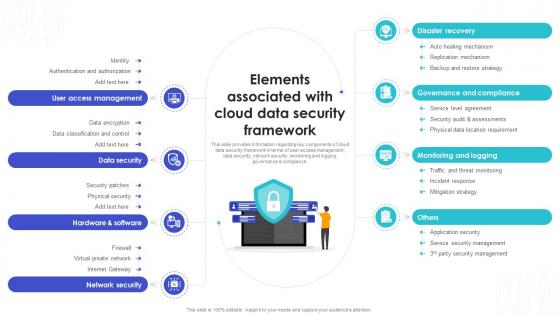 Elements Associated With Cloud Data Security Safeguarding Business With Data Loss Cybersecurity SS
Elements Associated With Cloud Data Security Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding key components of cloud data security framework in terms of user access management, data security, network security, monitoring and logging, governance and compliance.Increase audience engagement and knowledge by dispensing information using Elements Associated With Cloud Data Security Safeguarding Business With Data Loss Cybersecurity SS. This template helps you present information on eight stages. You can also present information on Disaster Recovery, User Access Management, Data Security, Network Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Training Program For Workforce Safeguarding Business With Data Loss Cybersecurity SS
Information Security Training Program For Workforce Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding training program to ensure information security at workplace by considering focus areas such as data security and encryption, network security, incident response, etc.Deliver an outstanding presentation on the topic using this Information Security Training Program For Workforce Safeguarding Business With Data Loss Cybersecurity SS. Dispense information and present a thorough explanation of Duration, Delivery Method, Assessment, Cost, Modules using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phase 4 Of Dlp Success Focus On Proactive Security Safeguarding Business With Data Loss Cybersecurity SS
Phase 4 Of Dlp Success Focus On Proactive Security Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding focusing on proactive security for successful data loss prevention execution. It will include initiatives such as infiltration, exfiltration, automated protection, etc.Increase audience engagement and knowledge by dispensing information using Phase 4 Of Dlp Success Focus On Proactive Security Safeguarding Business With Data Loss Cybersecurity SS. This template helps you present information on one stages. You can also present information on Exhibited Behavior, Objective, Customization, High Risk Events using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Server Security Data In Powerpoint And Google Slides Cpp
Server Security Data In Powerpoint And Google Slides CppPresenting our Server Security Data In Powerpoint And Google Slides Cpp PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Server Security Data This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Data Security Analysis In Powerpoint And Google Slides Cpp
Data Security Analysis In Powerpoint And Google Slides CppPresenting our Data Security Analysis In Powerpoint And Google Slides Cpp PowerPoint template design. This PowerPoint slide showcases Three stages. It is useful to share insightful information on Data Security Analysis This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Best Practices To Implement Ethics In Data Cyber Security
Best Practices To Implement Ethics In Data Cyber SecurityThis slide represents various best practices that assist companies to implement ethics to enhance their data cybersecurity. It include various best practices such as ethical code of conduct, ethical hacking and testing, third-party ethics. Introducing our Best Practices To Implement Ethics In Data Cyber Security set of slides. The topics discussed in these slides are Best Practices, Details, Impact. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Analytics Importance In Identity And Access Management Securing Systems With Identity
Data Analytics Importance In Identity And Access Management Securing Systems With IdentityThis slide showcases the importance of Identity and Access Management based data analytics. The purpose of this slide is to explain the benefits, which are anomaly detection, account monitoring, policy violation detection, and so on. Increase audience engagement and knowledge by dispensing information using Data Analytics Importance In Identity And Access Management Securing Systems With Identity This template helps you present information on Five stages. You can also present information on Anomaly Detection, Identity Certification Campaigns using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Role Of Identity And Access Management In Data Security Securing Systems With Identity
Role Of Identity And Access Management In Data Security Securing Systems With IdentityThis slide discusses the Identity and Access Management importance in data security. The purpose of this slide is to highlight the importance, including protecting business data, addressing new challenges, beyond perimeter security, combatting compromised credentials, and so on. Deliver an outstanding presentation on the topic using this Role Of Identity And Access Management In Data Security Securing Systems With Identity Dispense information and present a thorough explanation of Protecting Business Data, Combatting Compromised Credentials using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Introduction Of Cyber Threat Intelligence For Data Security
Introduction Of Cyber Threat Intelligence For Data SecurityThis slide discusses the overview of cyber threat intelligence for proactively blocking attacks and security purpose. Introducing Introduction Of Cyber Threat Intelligence For Data Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Evolving Threats Demand Intelligence, Vital For Security Architecture, Proactively Blocks Attacks, using this template. Grab it now to reap its full benefits.
-
 Data Security Operations Center Icon
Data Security Operations Center IconPresenting our set of slides with name Data Security Operations Center Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Security, Operations Center.
-
 Employee Data Security Operations Center Icon
Employee Data Security Operations Center IconIntroducing our premium set of slides with name Employee Data Security Operations Center Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Employee data, security operations center. So download instantly and tailor it with your information.
-
 Cloud Data Migration Security Risks And Solutions
Cloud Data Migration Security Risks And SolutionsThe below slide highlights the multiple security risks associated with cloud data migration along with the potential solutions to eliminate them. The various risks mentioned are unauthorized access, data breaches, weak data encryption, etc. Introducing our Cloud Data Migration Security Risks And Solutions set of slides. The topics discussed in these slides are Unauthorized Access, Data Breaches, Weak Data Encryption. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Loss Prevention Icon To Optimize Information Security
Data Loss Prevention Icon To Optimize Information SecurityIntroducing our Data Loss Prevention Icon To Optimize Information Security set of slides. The topics discussed in these slides are Information, Security, Prevention. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 NIDS Cyber Security Icon For Sensitive Data Protection
NIDS Cyber Security Icon For Sensitive Data ProtectionIntroducing our premium set of slides with NIDS Cyber Security Icon For Sensitive Data Protection. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Protection, Sensitive, Cyber Security. So download instantly and tailor it with your information.
-
 Methods To Ensure Data Security And Privacy In Biochip Technology Shaping The Future TC SS
Methods To Ensure Data Security And Privacy In Biochip Technology Shaping The Future TC SSIncrease audience engagement and knowledge by dispensing information using Methods To Ensure Data Security And Privacy In Biochip Technology Shaping The Future TC SS. This template helps you present information on three stages. You can also present information on Security Protocols, Authorized Access, Responsible Data Use using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 ERP Digital Transformation Icon For Improving Data Security
ERP Digital Transformation Icon For Improving Data SecurityIntroducing our premium set of slides with ERP Digital Transformation Icon For Improving Data Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like ERP Digital Transformation, Icon, Improving Data Security. So download instantly and tailor it with your information.
-
 Pam Framework For Optimizing Cyber Security And Data Protection
Pam Framework For Optimizing Cyber Security And Data ProtectionThis slide represents framework that assists companies to implement PAM cybersecurity to enhance their data protection and risk management. It includes various components such as use cases, defining requirements, architecture development, etc. Presenting our well structured Pam Framework For Optimizing Cyber Security And Data Protection. The topics discussed in this slide are Determine Use Cases, Define Requirements, Develop Architecture. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Applications Of Cyber Security In Banking For Data Protection
Applications Of Cyber Security In Banking For Data ProtectionThis slide represents cyber security applications in banking for data protection. This template aims to safeguard data and systems, ensure variety of cyber security tools and methodologies at access. It includes different approaches such as network security surveillance, software security, etc. Introducing our Applications Of Cyber Security In Banking For Data Protection set of slides. The topics discussed in these slides are Network Security Surveillance, Software Security, Risk Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security In Banking Icon To Protect Customer Data
Cyber Security In Banking Icon To Protect Customer DataIntroducing our premium set of slides with Cyber Security In Banking Icon To Protect Customer Data. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security In Banking, Icon To Protect, Customer Data. So download instantly and tailor it with your information.
-
 Endpoint Data Loss Prevention Tool Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Data Loss Prevention Tool Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases endpoint data loss prevention DLP tool process. It includes stages such as identification, assistance and tracking of endpoint data.Increase audience engagement and knowledge by dispensing information using Endpoint Data Loss Prevention Tool Building Next Generation Endpoint Security Cybersecurity SS. This template helps you present information three stages. You can also present information on Identify, Assist, Track, Potential Impact using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices For Data Security In Remote Healthcare Monitoring
Best Practices For Data Security In Remote Healthcare MonitoringThe slide outlines best practices to safeguard sensitive patient information on remote healthcare monitoring system. It include tips such as using data encryption, implementing strong access control and security testing. Presenting our set of slides with Best Practices For Data Security In Remote Healthcare Monitoring. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Utilize Data Encryption, Security Testing And Patching, Strong Access Controls .
-
 Email Security Best Practices Email Data Protection Overview And Features
Email Security Best Practices Email Data Protection Overview And FeaturesThe purpose of this slide is to discuss the Email Data Protection EDP solutions of email security. This slide highlights the features of Email Data Protection EDP , such as content-based email control, recipient authentication, data anonymization, etc. Present the topic in a bit more detail with this Email Security Best Practices Email Data Protection Overview And Features. Use it as a tool for discussion and navigation on Content-Based Email Control, Recipient Authentication, Two-Factor Authentication, Data Anonymization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of Encryption Algorithms For Organizational Data Security
Comparative Assessment Of Encryption Algorithms For Organizational Data SecurityThis slide provides a comparative assessment of various data encryption algorithms on different parameters. The multiple parameters used for assessment are encryption standard and use cases. Introducing our premium set of slides with Comparative Assessment Of Encryption Algorithms For Organizational Data Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Aes, Tdes, Twofish, Blowfish. So download instantly and tailor it with your information.
-
 Cloud Security Mechanism To Protect Data Gathered From IOT Devices
Cloud Security Mechanism To Protect Data Gathered From IOT DevicesThis slide showcases AWS IoT security diagram for secure data transfer. It includes user, IoT devices, Cognito ID, lambda, DynamicDB and kinesis. Presenting our well structured Cloud Security Mechanism To Protect Data Gathered From IOT Devices. The topics discussed in this slide are Security Credentials, Identity And Access, Management Policies. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 IOT Data Encryption Security Icon
IOT Data Encryption Security IconIntroducing our premium set of slides with name IOT Data Encryption Security Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like IOT, Data Encryption, Security. So download instantly and tailor it with your information.
-
 IOT Security System Tools For Data Protection
IOT Security System Tools For Data ProtectionThis slide showcases methods to secure IoT security systems. It includes digital certificates, network and application programming interface security. Presenting our set of slides with name IOT Security System Tools For Data Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Security, API Security, Digital Certificates.
-
 IOT Technology Data Security Icon
IOT Technology Data Security IconPresenting our set of slides with name IOT Technology Data Security Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on IoT Technology, Data Security.
-
 Wireless Lan Security Architecture For Data Protection
Wireless Lan Security Architecture For Data ProtectionIntroducing our Wireless Lan Security Architecture For Data Protection set of slides. The topics discussed in these slides are CRC Generation Algorithm, Radio Interface, PayloadThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Introduction Of Data Layer In Web Security Solution
Introduction Of Data Layer In Web Security SolutionThis slide discusses the overview of the sixth layer of web security, which is the data layer for enhancing security in the web. Introducing Introduction Of Data Layer In Web Security Solution to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Ensure Data Integrity, Employing Data Encryption Is Crucial, Safeguard Against Unintentional Data Loss Deletion, using this template. Grab it now to reap its full benefits.
-
 Practices To Ensure Secure Cloud Data Migration
Practices To Ensure Secure Cloud Data MigrationThis slide provides the best practices for effective monitoring of cloud data migration that helps to eliminate the potential risks associated with data deployment. Key steps are use of native solutions, compliance audit, etc. Presenting our set of slides with Practices To Ensure Secure Cloud Data Migration. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloud Security Architect, Track And Automate, Implement Compliance.
-
 Icon For Managing Big Data Governance And Security With AWS
Icon For Managing Big Data Governance And Security With AWSPresenting our set of slides with Icon For Managing Big Data Governance And Security With AWS. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon, Managing Big Data, Governance And Security, AWS.
-
 Cloud Data Management Virtualization Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Data Management Virtualization Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon represents the importance of data security in cloud virtualization. With a vibrant design, it visually conveys the significance of protecting sensitive information in a virtual environment. Use it to enhance your presentations on cloud computing and data protection.
-
 Cloud Data Management Virtualization Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Data Management Virtualization Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is the perfect addition to your presentation on Cloud virtualization data security. With a sleek design and clear imagery, it effectively represents the topic of data security in the cloud. Use it to enhance your slides and make a lasting impression on your audience.
-
 Digital Certificate Data Security Illustration
Digital Certificate Data Security IllustrationThis coloured PowerPoint icon features a lock symbol on a blue background, representing the Secure Socket Layer SSL protocol for secure online communication. Use it to enhance your presentations on internet security, encryption, and data protection. Perfect for technology and cybersecurity related presentations.





