Powerpoint Templates and Google slides for Data security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Data Protection Network Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Protection Network Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your incident response capabilities with our vibrant PowerPoint icon, representing the power of EDR solutions. With its eye-catching color and design, this icon is the perfect addition to your presentation on facilitating incident response trends. Grab your audiences attention and showcase the importance of EDR in handling security incidents.
-
 Data Protection Network Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Protection Network Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your incident response strategy with our Monotone PowerPoint icon. This sleek and modern design represents the power of EDR solutions in facilitating efficient and effective response to security incidents. Perfect for presentations on cybersecurity and risk management, this icon will elevate your content and captivate your audience.
-
 Security Measures In Data Center Migration Project Plan Icon
Security Measures In Data Center Migration Project Plan IconIntroducing our premium set of slides with Security Measures In Data Center Migration Project Plan Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Measures, Data Center Migration, Project Plan Icon. So download instantly and tailor it with your information.
-
 IT Modernization Strategy Icon For Data Security
IT Modernization Strategy Icon For Data SecurityIntroducing our premium set of slides with IT Modernization Strategy Icon For Data Security Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Modernization Strategy, Data Security So download instantly and tailor it with your information.
-
 Saas Best Practices Icon To Optimize Data Migration Security
Saas Best Practices Icon To Optimize Data Migration SecurityIntroducing our Saas Best Practices Icon To Optimize Data Migration Security set of slides. The topics discussed in these slides are Optimize Data, Migration Security, Best Practices. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Agenda For Mobile Device Security For Data Protection Cybersecurity SS
Agenda For Mobile Device Security For Data Protection Cybersecurity SSIntroducing Agenda For Mobile Device Security For Data Protection Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Agenda using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Mobile Device Security For Data Protection Cybersecurity SS
Icons Slide For Mobile Device Security For Data Protection Cybersecurity SSIntroducing our well researched set of slides titled Icons Slide For Mobile Device Security For Data Protection Cybersecurity SS It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Mobile Device Encryption Plan For Data Security Mobile Device Security Cybersecurity SS
Mobile Device Encryption Plan For Data Security Mobile Device Security Cybersecurity SSThis slide showcases data encryption plan that can help to enhance mobile security. Its key elements are target devices, employees, encryption technique used, software used, authentication method etc. Introducing Mobile Device Encryption Plan For Data Security Mobile Device Security Cybersecurity SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Encrypted Communication, Secure Remote Access, Data Privacy using this template. Grab it now to reap its full benefits.
-
 Mobile Device Encryption Policy To Safeguard Data Mobile Device Security Cybersecurity SS
Mobile Device Encryption Policy To Safeguard Data Mobile Device Security Cybersecurity SSThis slide showcases mobile encryption policy that can help in data privacy. Its key components are purpose of policy, scope and encryption policy Increase audience engagement and knowledge by dispensing information using Mobile Device Encryption Policy To Safeguard Data Mobile Device Security Cybersecurity SS This template helps you present information on Three stages. You can also present information on Geographical Region, Detected Globally, Mobile Cyber Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Mobile Device Security For Data Protection Table Of Contents Cybersecurity SS
Mobile Device Security For Data Protection Table Of Contents Cybersecurity SSIntroducing Mobile Device Security For Data Protection Table Of Contents Cybersecurity SS to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Target Devices, Target Employees, Encryption Technique Used using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Mobile Device Security For Data Protection Cybersecurity SS
Table Of Contents For Mobile Device Security For Data Protection Cybersecurity SSIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Mobile Device Security For Data Protection Cybersecurity SS This template helps you present information on Five stages. You can also present information on Financial Companies, Million Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Analyzing Cloud Based Service Offerings Best Practices To Improve Data Security
Analyzing Cloud Based Service Offerings Best Practices To Improve Data SecurityThis slide showcases various tips which can be adopted by business to enhance data security of SAAs application. It provides information regarding end to end encryption, application testing, data deletion policy and VPN. Introducing Analyzing Cloud Based Service Offerings Best Practices To Improve Data Security to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on End To End Encryption, Application Testing, Data Deletion Policy, Vpn, using this template. Grab it now to reap its full benefits.
-
 Incorporating Secure Multi Party Computation To Boost Data Implementing Digital Transformation And Ai DT SS
Incorporating Secure Multi Party Computation To Boost Data Implementing Digital Transformation And Ai DT SSThis slide provides glimpse about utilizing secure multi party computation SMPC approach that can help businesses in boosting data confidentiality. It includes stages such as input sharing, secure computation, output reconstruction, etc. Increase audience engagement and knowledge by dispensing information using Incorporating Secure Multi Party Computation To Boost Data Implementing Digital Transformation And Ai DT SS. This template helps you present information on three stages. You can also present information on Increase Security Against Attacks, Boost Data Confidentiality, Input Sharing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Methods Of Cloud Data Network Security
Methods Of Cloud Data Network SecurityThis slide focuses on cloud data network security techniques including methods, strategic actions, and illustrations. Introducing our Methods Of Cloud Data Network Security set of slides. The topics discussed in these slides are Strategic Actions, Illustrations, Methods. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Protecting Sensitive Data From Network Security Threats
Protecting Sensitive Data From Network Security ThreatsThis slide highlights network security threats to protect from unauthorized access including trojan viruses, malware, and computer worms. Introducing our premium set of slides with name Protecting Sensitive Data From Network Security Threats. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Trojan Virus, Malware, Computer Worms. So download instantly and tailor it with your information.
-
 Data Security Incident Investigation Icon
Data Security Incident Investigation IconIntroducing our Data Security Incident Investigation Icon set of slides. The topics discussed in these slides are Data Security Incident, Investigation Icon. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Asymmetric Data Encryption For Secure Communication
Asymmetric Data Encryption For Secure CommunicationThe purpose of this slide is to elucidate how asymmetric data encryption enhances secure communication through the use of key pairs. It ensures robust protection against unauthorized access and interception. Introducing our Asymmetric Data Encryption For Secure Communication set of slides. The topics discussed in these slides are Device, Securing, Communication Channels, Cloud Server. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Encryption Essentials For Robust Data Security
Cloud Encryption Essentials For Robust Data SecurityThe purpose of this slide is to highlight how cloud encryption essentials bolster robust data security. It safeguard sensitive information stored in cloud environments through cryptographic techniques. Presenting our set of slides with name Cloud Encryption Essentials For Robust Data Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Insider Threat Defense, Secure Data Transfers, Organizational Integrity.
-
 Data Encryption Algorithms For Security Solutions
Data Encryption Algorithms For Security SolutionsThe purpose of this slide is to demonstrate how data encryption algorithms for security solutions enhance protection. It encode data to prevent unauthorized access or manipulation. Introducing our Data Encryption Algorithms For Security Solutions set of slides. The topics discussed in these slides are Advanced Encryption Standard, Rivest Shamir Adleman, Elliptic Curve Cryptography. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Encryption Icon For Secure Messaging
Data Encryption Icon For Secure MessagingPresenting our set of slides with name Data Encryption Icon For Secure Messaging. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Encryption Icon, Secure Messaging.
-
 Data Encryption Working Model For Security
Data Encryption Working Model For SecurityThe purpose of this slide is to elucidate how data encryption working model for security offers insight into safeguarding sensitive data through encryption mechanisms. It helps thwart unauthorized access or breaches. Introducing our Data Encryption Working Model For Security set of slides. The topics discussed in these slides are Sender, Plaintext, Ciphertext. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Strategies To Implement Encryption Trends In Data Security
Strategies To Implement Encryption Trends In Data SecurityThe purpose of this slide is to guide and inform on effective strategies for implementing encryption trends in data security. It provides actionable insights to enhance data protection and address evolving cyber threats. Introducing our Strategies To Implement Encryption Trends In Data Security set of slides. The topics discussed in these slides are Biometric Authentication, Multi-Factor Authentication, Cloud Encryption, Blockchain Encryption. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Computer Security Data Protection Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Security Data Protection Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your presentations on cyber risk management with our vibrant Computer Security PowerPoint icon. This eye-catching icon features a lock symbol in bold colors, representing the importance of safeguarding your data and systems. Perfect for showcasing the importance of cyber security in todays digital age.
-
 Computer Security Data Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Security Data Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon represents the importance of computer security in cyber risk management. It is a visual representation of the need for safeguarding sensitive information and protecting against potential cyber threats. Use this icon to enhance presentations on cyber security and emphasize the significance of risk management in the digital world.
-
 Data Security And Privacy Survey Overview Report Survey SS
Data Security And Privacy Survey Overview Report Survey SSFollowing slides demonstrates data security evaluation summary report which can be used by business to reduce data hacking. It includes elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Presenting our well structured Data Security And Privacy Survey Overview Report Survey SS. The topics discussed in this slide are Data Security Tools, Budget Allocated, Software Solutions. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security software data services example of ppt
Security software data services example of pptThis PowerPoint design can be used for expressing your business strategies and Security Software Data Services related ideas in an attractive manner. The colors shown in star figure can be altered in any PowerPoint software. The text shown in the slide can also be according to your analytics. Downloading this slide will give you access to its full version. The stages in this process are web acceleration, security software, shopping carts, data services.
-
 Framework for big data control and security presentation outline
Framework for big data control and security presentation outlinePresenting framework for big data control and security presentation outline. This is a framework for big data control and security presentation outline. This is a four stage process. The stages in this process are define, data discovery, data classification, dissect, data intelligence, data analytics.
-
 Model of governance and security of big data diagram ppt presentations
Model of governance and security of big data diagram ppt presentationsPresenting model of governance and security of big data diagram ppt presentations. This is a model of governance and security of big data diagram ppt presentations. This is a three stage process. The stages in this process are confidentiality, integrity, availability, security model.
-
 Information Security Detail Impact Information Security Can Reduce Risk Data Breach Organization
Information Security Detail Impact Information Security Can Reduce Risk Data Breach OrganizationThis slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver an outstanding presentation on the topic using this Information Security Detail Impact Information Security Can Reduce Risk Data Breach Organization. Dispense information and present a thorough explanation of Organization, Information, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Center Dashboard Snapshot With Security And User Assessment
Data Center Dashboard Snapshot With Security And User AssessmentIntroducing our Data Center Dashboard Snapshot With Security And User Assessment set of slides. The topics discussed in these slides are Security Assessment, User Assessment, Data Discovery. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Sales CRM Cloud Implementation Securing Our Data With CRM Ppt Slides Image
Sales CRM Cloud Implementation Securing Our Data With CRM Ppt Slides ImageThis slide illustrates the issues that trigger poor relationship with customers which includes no real time support, no innovative product launched, bad after sale service and lack of engagement. Present the topic in a bit more detail with this Sales CRM Cloud Implementation Poor Relationship With Customers Ppt Slides Picture. Use it as a tool for discussion and navigation on Weak Relationship Building, Poor Customer Service, Product Launched. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Securing Our Data With Crm Crm Software Implementation Ppt Slides Demonstration
Securing Our Data With Crm Crm Software Implementation Ppt Slides DemonstrationThis slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security. Deliver an outstanding presentation on the topic using this Securing Our Data With Crm Crm Software Implementation Ppt Slides Demonstration. Dispense information and present a thorough explanation of Data Storage And Failover, Communication Protection, Data Backup using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Dashboard For Data Security Risk Assessment And Management Plan For Information Security
Dashboard For Data Security Risk Assessment And Management Plan For Information SecurityThis slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status Deliver an outstanding presentation on the topic using this Dashboard For Data Security Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Dashboard, Management, Data Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Assessment And Management Plan For Information Security Information And Data Breach Impacting
Risk Assessment And Management Plan For Information Security Information And Data Breach ImpactingDeliver an outstanding presentation on the topic using this Risk Assessment And Management Plan For Information Security Information And Data Breach Impacting. Dispense information and present a thorough explanation of Information, Business, Financial using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Data Analysis With Reported Incident KPI
Cyber Security Data Analysis With Reported Incident KPIThis slide displays the chart which includes the year wise distribution of information breaches incidents involving personal information and other security information with a five year annual average. Introducing our Cyber Security Data Analysis With Reported Incident KPI set of slides. The topics discussed in these slides are Cyber Security Data Analysis, Reported Incident KPI. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
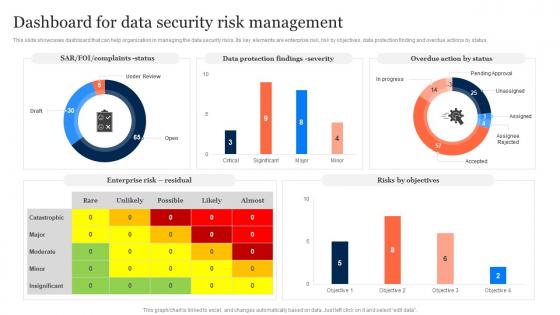 Dashboard For Data Security Risk Management Information Security Risk Management
Dashboard For Data Security Risk Management Information Security Risk ManagementThis slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Present the topic in a bit more detail with this Dashboard For Data Security Risk Management Information Security Risk Management. Use it as a tool for discussion and navigation on Dashboard, Data Security, Risk Management. This template is free to edit as deemed fit for your organization. Therefore download it now
-
 Information And Data Breach Impacting Customer Loyalty Information Security Risk Management
Information And Data Breach Impacting Customer Loyalty Information Security Risk ManagementDeliver an outstanding presentation on the topic using this Information And Data Breach Impacting Customer Loyalty Information Security Risk Management. Dispense information and present a thorough explanation of Information, Data Breach Impacting, Customer Loyalty using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Online Data Security Limitation Analysis For Digital Organizations
Online Data Security Limitation Analysis For Digital OrganizationsThis slide depicts the challenges faced while storing digital data. The purpose of this template is to analyze the security limitations faced in the technology industries. It also includes elements such as cyberattack, loss of devices, etc. Introducing our Online Data Security Limitation Analysis For Digital Organizations set of slides. The topics discussed in these slides are Data Limitations, Impact, Technology Industry. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information System Security And Risk Administration Information And Data Breach Impacting Customer Loyalty
Information System Security And Risk Administration Information And Data Breach Impacting Customer LoyaltyDeliver an outstanding presentation on the topic using this Information System Security And Risk Administration Information And Data Breach Impacting Customer Loyalty. Dispense information and present a thorough explanation of Business, Financial Data, Data Breach using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information System Security And Risk Administration Plandashboard For Data Security Risk Management
Information System Security And Risk Administration Plandashboard For Data Security Risk ManagementThis slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Present the topic in a bit more detail with this Information System Security And Risk Administration Plandashboard For Data Security Risk Management. Use it as a tool for discussion and navigation on Enterprise Risk, Risks By Objectives, Data Protection Findings. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt Diagrams
Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt DiagramsThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Deliver an outstanding presentation on the topic using this Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt Diagrams. Dispense information and present a thorough explanation of Data Breaches, Consequences, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
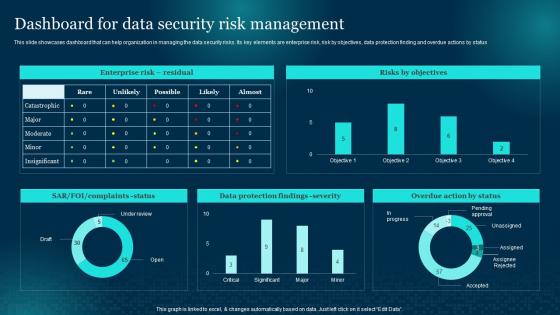 Dashboard For Data Security Risk Management Cybersecurity Risk Analysis And Management Plan
Dashboard For Data Security Risk Management Cybersecurity Risk Analysis And Management PlanThis slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status Present the topic in a bit more detail with this Dashboard For Data Security Risk Management Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Dashboard, Security, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard For Data Security Risk Management Formulating Cybersecurity Plan
Dashboard For Data Security Risk Management Formulating Cybersecurity PlanThis slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Present the topic in a bit more detail with this Dashboard For Data Security Risk Management Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Data Protection, Dashboard, Data Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Conducting Cyber Security Gap Analysis Of Organization Preventing Data Breaches Through Cyber Security
Conducting Cyber Security Gap Analysis Of Organization Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Deliver an outstanding presentation on the topic using this Conducting Cyber Security Gap Analysis Of Organization Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Current State, Email, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determining The Actors Behind Most Significant Cyber Attack Preventing Data Breaches Through Cyber Security
Determining The Actors Behind Most Significant Cyber Attack Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present the topic in a bit more detail with this Determining The Actors Behind Most Significant Cyber Attack Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Online Criminals, Foreign Government Officials, Malicious Insiders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Statistics Showing The Impact Of Security Awarenesspreventing Data Breaches Through Cyber Security
Key Statistics Showing The Impact Of Security Awarenesspreventing Data Breaches Through Cyber SecurityPresent the topic in a bit more detail with this Key Statistics Showing The Impact Of Security Awarenesspreventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Employees, Security, Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Kpi Dashboard To Monitor Cyber Security Performance Preventing Data Breaches Through Cyber Security
Kpi Dashboard To Monitor Cyber Security Performance Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. Deliver an outstanding presentation on the topic using this Kpi Dashboard To Monitor Cyber Security Performance Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Control Review Status, Management, Cyber Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber Security
Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Present the topic in a bit more detail with this Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Risk By Threats, Threat Report, Current Risk Status. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Measuring The Impact Of Security Awareness Training Preventing Data Breaches Through Cyber Security
Measuring The Impact Of Security Awareness Training Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. Present the topic in a bit more detail with this Measuring The Impact Of Security Awareness Training Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Security Awareness, Social Engineering. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Most Common Cyber Attack Faced By Our Employees Preventing Data Breaches Through Cyber Security
Most Common Cyber Attack Faced By Our Employees Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. Introducing Most Common Cyber Attack Faced By Our Employees Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Ransomware, Password Attack, Cryptojacking, using this template. Grab it now to reap its full benefits.
-
 Operational Outlook Of Security Awareness Training Software Preventing Data Breaches Through Cyber Security
Operational Outlook Of Security Awareness Training Software Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Present the topic in a bit more detail with this Operational Outlook Of Security Awareness Training Software Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Finished Training, Awareness Factors, Training Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Practices To Improve Security Awareness Level Amongst The Preventing Data Breaches Through Cyber Security
Practices To Improve Security Awareness Level Amongst The Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Increase audience engagement and knowledge by dispensing information using Practices To Improve Security Awareness Level Amongst The Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Get Management Involved, Develop Robust Policies, Set Guidelines using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Awareness Training Program Challenges Preventing Data Breaches Through Cyber Security
Security Awareness Training Program Challenges Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Increase audience engagement and knowledge by dispensing information using Security Awareness Training Program Challenges Preventing Data Breaches Through Cyber Security. This template helps you present information on five stages. You can also present information on Outdated Content, Employees Lose Interest, Burden On Administrators using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber Security
Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Limit Public Information, Verify The Source, No Sharing Of Password. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents For Preventing Data Breaches Through Cyber Security Awareness
Table Of Contents For Preventing Data Breaches Through Cyber Security AwarenessDeliver an outstanding presentation on the topic using this Table Of Contents For Preventing Data Breaches Through Cyber Security Awareness. Dispense information and present a thorough explanation of Cyber Security Awareness, Online Courses, Automation Tools using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 How To Overcome The Security Awareness Training Program Preventing Data Breaches Through Cyber Security
How To Overcome The Security Awareness Training Program Preventing Data Breaches Through Cyber SecurityThe purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program. Deliver an outstanding presentation on the topic using this How To Overcome The Security Awareness Training Program Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Outdated Content, Burden On Administrators, Low Employee Participation Rate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Consequences Of Data Breaches Faced By Organization Development And Implementation Of Security
Consequences Of Data Breaches Faced By Organization Development And Implementation Of SecurityThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Deliver an outstanding presentation on the topic using this Consequences Of Data Breaches Faced By Organization Development And Implementation Of Security. Dispense information and present a thorough explanation of Payment Card Fraud, Physical Loss, Insider Leak using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Consequences Of Data Breaches Faced By Organization
Cyber Security Attacks Response Plan Consequences Of Data Breaches Faced By OrganizationThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Consequences Of Data Breaches Faced By Organization. Use it as a tool for discussion and navigation on Consequences, Data Breaches, Unintended Disclosure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
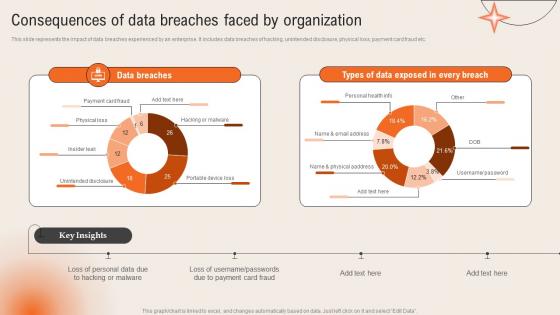 Consequences Of Data Breaches Faced By Organization Deploying Computer Security Incident Management
Consequences Of Data Breaches Faced By Organization Deploying Computer Security Incident ManagementThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc.Present the topic in a bit more detail with this Consequences Of Data Breaches Faced By Organization Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Unintended Disclosure, Portable Device, Hacking Malware. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Process To Manage Firms Sensitive Data Defense Plan To Protect Firm Assets
Information Security Process To Manage Firms Sensitive Data Defense Plan To Protect Firm AssetsThis slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Present the topic in a bit more detail with this Information Security Process To Manage Firms Sensitive Data Defense Plan To Protect Firm Assets. Use it as a tool for discussion and navigation on Privileged Password Management, Network Administrator. This template is free to edit as deemed fit for your organization. Therefore download it now.





