Powerpoint Templates and Google slides for Computer Systems
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Technical Stack For Confidential Computing Solutions Confidential Computing System Technology
Technical Stack For Confidential Computing Solutions Confidential Computing System TechnologyThis slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks. Present the topic in a bit more detail with this Technical Stack For Confidential Computing Solutions Confidential Computing System Technology. Use it as a tool for discussion and navigation on Application Software Vendors, Infrastructure Providers, Hardware Vendors. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Technologies Used To Protect Data In Use Confidential Computing System Technology
Technologies Used To Protect Data In Use Confidential Computing System TechnologyThis slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Deliver an outstanding presentation on the topic using this Technologies Used To Protect Data In Use Confidential Computing System Technology. Dispense information and present a thorough explanation of Technologies, Security Comparison, Scalability Comparison using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 What Is Environment Tee In Confidential Computing Confidential Computing System Technology
What Is Environment Tee In Confidential Computing Confidential Computing System TechnologyThis slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Present the topic in a bit more detail with this What Is Environment Tee In Confidential Computing Confidential Computing System Technology. Use it as a tool for discussion and navigation on Confidentiality, Data Integrity, Code Integrity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Of Confidential Computing Technology Confidential Computing System Technology
Working Of Confidential Computing Technology Confidential Computing System TechnologyThis slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Present the topic in a bit more detail with this Working Of Confidential Computing Technology Confidential Computing System Technology. Use it as a tool for discussion and navigation on Confidential, Computing, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing System Technology Components Of Inclavare Containers Architecture
Confidential Computing System Technology Components Of Inclavare Containers ArchitectureThis slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API. Increase audience engagement and knowledge by dispensing information using Confidential Computing System Technology Components Of Inclavare Containers Architecture. This template helps you present information on eight stages. You can also present information on Language Runtime, Containers Architecture, Components using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing System Technology Functional Comparison Of Different Tee Environments
Confidential Computing System Technology Functional Comparison Of Different Tee EnvironmentsThis slide talks about the functional comparison between different TEE environments available in the market. The purpose of this slide is to demonstrate the comparison and challenges with TEE environments. The main TEE environment provider includes Intel SGX, AMD SEV-ES, and IBM SE. Present the topic in a bit more detail with this Confidential Computing System Technology Functional Comparison Of Different Tee Environments. Use it as a tool for discussion and navigation on Environments, Functional, Comparison. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing System Technology Hi Tech And Manufacturing Industry Scenario Case Analysis
Confidential Computing System Technology Hi Tech And Manufacturing Industry Scenario Case AnalysisThis slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case. Deliver an outstanding presentation on the topic using this Confidential Computing System Technology Hi Tech And Manufacturing Industry Scenario Case Analysis. Dispense information and present a thorough explanation of Analysis, Manufacturing, Infrastructure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing System Technology Inclavare Confidential Containers Architecture In Tee
Confidential Computing System Technology Inclavare Confidential Containers Architecture In TeeThis slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. Deliver an outstanding presentation on the topic using this Confidential Computing System Technology Inclavare Confidential Containers Architecture In Tee. Dispense information and present a thorough explanation of Collaboration, Technology, Compatibility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing System Technology Intel Sgx With A Smaller Trusted Computing Base Tcb
Confidential Computing System Technology Intel Sgx With A Smaller Trusted Computing Base TcbThis slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Present the topic in a bit more detail with this Confidential Computing System Technology Intel Sgx With A Smaller Trusted Computing Base Tcb. Use it as a tool for discussion and navigation on Deployment, Environment, Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing System Technology Introduction To Confidential Computing Technology
Confidential Computing System Technology Introduction To Confidential Computing TechnologyThis slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Deliver an outstanding presentation on the topic using this Confidential Computing System Technology Introduction To Confidential Computing Technology. Dispense information and present a thorough explanation of Introduction, Confidential, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing System Technology Need For Confidential Computing In Cloud Environment
Confidential Computing System Technology Need For Confidential Computing In Cloud EnvironmentThis slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems. Deliver an outstanding presentation on the topic using this Confidential Computing System Technology Need For Confidential Computing In Cloud Environment. Dispense information and present a thorough explanation of Confidential, Environment, Solutions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing System Technology Operational And Technical Assurance Of Data Privacy
Confidential Computing System Technology Operational And Technical Assurance Of Data PrivacyThis slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data. Deliver an outstanding presentation on the topic using this Confidential Computing System Technology Operational And Technical Assurance Of Data Privacy. Dispense information and present a thorough explanation of Operational, Deployment, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing System Technology Overview Of Confidential Computing Technologies
Confidential Computing System Technology Overview Of Confidential Computing TechnologiesThis slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Increase audience engagement and knowledge by dispensing information using Confidential Computing System Technology Overview Of Confidential Computing Technologies. This template helps you present information on six stages. You can also present information on Homomorphic Encryption, Trusted Execution Environment, Secure Multi Party Computation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing System Technology Primary Approaches To Obtain Confidential Computing
Confidential Computing System Technology Primary Approaches To Obtain Confidential ComputingThis slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Present the topic in a bit more detail with this Confidential Computing System Technology Primary Approaches To Obtain Confidential Computing. Use it as a tool for discussion and navigation on Approaches, Administrator, Virtualization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing System Technology Process Of Using Intel Sgx Based Trusted Applications
Confidential Computing System Technology Process Of Using Intel Sgx Based Trusted ApplicationsThis slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Deliver an outstanding presentation on the topic using this Confidential Computing System Technology Process Of Using Intel Sgx Based Trusted Applications. Dispense information and present a thorough explanation of Applications, Install The Environment, Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing System Technology Public And Retail And Cpg Sector Scenario Case Analysis
Confidential Computing System Technology Public And Retail And Cpg Sector Scenario Case AnalysisThis slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors. Present the topic in a bit more detail with this Confidential Computing System Technology Public And Retail And Cpg Sector Scenario Case Analysis. Use it as a tool for discussion and navigation on Analysis, Confidential, Computing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing System Technology Role Of Hardware In Confidential Computing Technology
Confidential Computing System Technology Role Of Hardware In Confidential Computing TechnologyThis slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware. Introducing Confidential Computing System Technology Role Of Hardware In Confidential Computing Technology to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Operators, Cloud Environment, Peripheral Vendors, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing System Technology Trust Boundary Across Azure Confidential Computing Services
Confidential Computing System Technology Trust Boundary Across Azure Confidential Computing ServicesThis slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Present the topic in a bit more detail with this Confidential Computing System Technology Trust Boundary Across Azure Confidential Computing Services. Use it as a tool for discussion and navigation on Confidential, Computing, Services. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing System Technology Trusted Execution Environment Tee Hardware Platform
Confidential Computing System Technology Trusted Execution Environment Tee Hardware PlatformThis slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD. Deliver an outstanding presentation on the topic using this Confidential Computing System Technology Trusted Execution Environment Tee Hardware Platform. Dispense information and present a thorough explanation of Environment, Information, Application using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing System Technology What Is Fully Homomorphic Encryption Fhe
Confidential Computing System Technology What Is Fully Homomorphic Encryption FheThis slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. Deliver an outstanding presentation on the topic using this Confidential Computing System Technology What Is Fully Homomorphic Encryption Fhe. Dispense information and present a thorough explanation of Improved Privacy, Strict Regulatory Compliance, Enhanced Cloud Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Computerized Scheduling System In Powerpoint And Google Slides Cpb
Computerized Scheduling System In Powerpoint And Google Slides CpbPresenting Computerized Scheduling System In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase seven stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Computerized Scheduling System. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Confidential Computing System Technology Computing Use Cases And Ecosystem
Confidential Computing System Technology Computing Use Cases And EcosystemThis slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Present the topic in a bit more detail with this Confidential Computing System Technology Computing Use Cases And Ecosystem. Use it as a tool for discussion and navigation on Key Management Systems, Secure Cloud Migration, Database Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing System Technology Market Segments Overview
Confidential Computing System Technology Market Segments OverviewThis slide represents the overview of market segments of confidential computing. The purpose of this slide is to showcase confidential computing market segments such as hardware, software and services. It also caters to the components of each segment along with its description. Present the topic in a bit more detail with this Confidential Computing System Technology Market Segments Overview. Use it as a tool for discussion and navigation on Confidential, Computing, Overview. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing System Technology Platform For Healthcare Industry
Confidential Computing System Technology Platform For Healthcare IndustryThis slide depicts the confidential computing platform for the healthcare industry, including its components such as blob storage, Azure Kubernetes Service cluster, web API, Redis cache, AKS cluster interference model, and azure attestation. Present the topic in a bit more detail with this Confidential Computing System Technology Platform For Healthcare Industry. Use it as a tool for discussion and navigation on Confidential, Healthcare Industry, Components. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing System Technology Total Privacy Assurance
Confidential Computing System Technology Total Privacy AssuranceThis slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Deliver an outstanding presentation on the topic using this Confidential Computing System Technology Total Privacy Assurance. Dispense information and present a thorough explanation of Information, Business, Assurance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Computer System Design In Powerpoint And Google Slides Cpb
Computer System Design In Powerpoint And Google Slides CpbPresenting Computer System Design In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Computer System Design. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
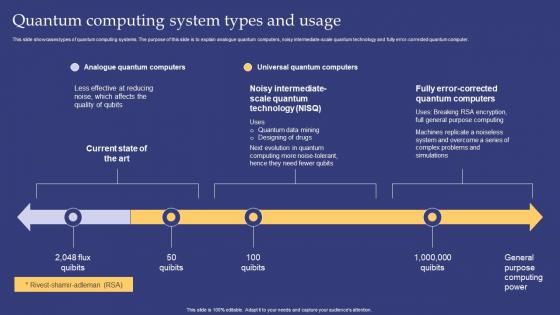 Emerging Technologies Quantum Computing System Types And Usage
Emerging Technologies Quantum Computing System Types And UsageThis slide showcases types of quantum computing systems. The purpose of this slide is to explain analogue quantum computers, noisy intermediate scale quantum technology and fully error corrected quantum computer. Present the topic in a bit more detail with this Emerging Technologies Quantum Computing System Types And Usage. Use it as a tool for discussion and navigation on Analogue Quantum Computers, Universal Quantum Computers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing System Technology Benefits Of Confidential Computing For Businesses
Confidential Computing System Technology Benefits Of Confidential Computing For BusinessesThis slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on. Present the topic in a bit more detail with this Confidential Computing System Technology Benefits Of Confidential Computing For Businesses. Use it as a tool for discussion and navigation on Stakeholders, Intellectual, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing System Technology Business Scenarios Of Confidential Computing Platform
Confidential Computing System Technology Business Scenarios Of Confidential Computing PlatformThis slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. Increase audience engagement and knowledge by dispensing information using Confidential Computing System Technology Business Scenarios Of Confidential Computing Platform. This template helps you present information on seven stages. You can also present information on Key Management, Edge Computing, Business Scenarios using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Trending Technologies Quantum Computing System Types And Usage
Trending Technologies Quantum Computing System Types And UsageThis slide showcases types of quantum computing systems. The purpose of this slide is to explain analogue quantum computers, noisy intermediate-scale quantum technology and fully error-corrected quantum computer. Present the topic in a bit more detail with this Trending Technologies Quantum Computing System Types And Usage. Use it as a tool for discussion and navigation on Quantum Computing System, Types And Usage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Limitations Of Serverless Computing V2 Technology Systems
Limitations Of Serverless Computing V2 Technology SystemsThis slide represents the drawbacks of serverless computing systems. The purpose of this slide is to outline the various disadvantages of serverless computing systems. These include lock-in of vendors, inefficient for long-running applications, etc. Increase audience engagement and knowledge by dispensing information using Limitations Of Serverless Computing V2 Technology Systems. This template helps you present information on four stages. You can also present information on Serverless Computing Technology Systems, Long Running Applications, Serverless Computing Systems using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing V2 Occlum System Architecture And Features
Confidential Computing V2 Occlum System Architecture And FeaturesThis slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on. Deliver an outstanding presentation on the topic using this Confidential Computing V2 Occlum System Architecture And Features. Dispense information and present a thorough explanation of Efficient Multi Process Support, Memory Security Guarantee, Deployment Environment, Occlum System Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Arrange Parts Systems Computer In Powerpoint And Google Slides Cpb
Arrange Parts Systems Computer In Powerpoint And Google Slides CpbPresenting Arrange Parts Systems Computer In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Arrange Parts Systems Computer. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Quantum Computing System Types And Usage Modern Technologies
Quantum Computing System Types And Usage Modern TechnologiesThis slide showcases types of quantum computing systems. The purpose of this slide is to explain analogue quantum computers,noisy intermediate scale quantum technology and fully error corrected quantum computer.Present the topic in a bit more detail with this Quantum Computing System Types And Usage Modern Technologies. Use it as a tool for discussion and navigation on Planning,Developing,Integrating. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 AXG Accelerated Computing Systems And Graphics Intel Company Profile CP SS
AXG Accelerated Computing Systems And Graphics Intel Company Profile CP SSThis slide showcases a brief introduction of AXG Accelerated computing systems and graphics segment. It shows AXG segment revenue contribution and products and competition. Introducing AXG Accelerated Computing Systems And Graphics Intel Company Profile CP SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Accelerating Comp, Immersive Computing, Computing Applications, using this template. Grab it now to reap its full benefits.
-
 Architectural Operating System Model Of Computers
Architectural Operating System Model Of ComputersThis slide represents operating systems purpose for managing computational activities and providing environment for development of programs. It includes aspects such as low level software, interface, computer memory, execute programs, resources, etc. Presenting our well structured Architectural Operating System Model Of Computers. The topics discussed in this slide are Platform Software, User Software, Operating System, Data Transfer. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Digital Transformation System Icon With Global Computing Ideas Background Images
Digital Transformation System Icon With Global Computing Ideas Background ImagesPresenting our set of slides with name Digital Transformation System Icon With Global Computing Ideas Background Images. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Digital Transformation, System Icon, Global Computing .
-
 Operating System Based Virtualization For Serverless Computing
Operating System Based Virtualization For Serverless ComputingThis slide exhibits operating system based virtualization for allowing direct access to created virtual machines to user. It includes elements such as guest operating system and application software, virtual machine management and hardware. Presenting our well structured Operating System Based Virtualization For Serverless Computing The topics discussed in this slide are Virtual Machine Management, Hardware This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cloud Computing Warehouse Execution System Icon
Cloud Computing Warehouse Execution System IconIntroducing our Cloud Computing Warehouse Execution System Icon set of slides. The topics discussed in these slides are Cloud Computing, Warehouse Execution, System Icon. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Current Trending Technologies Quantum Computing System Types And Usage
Current Trending Technologies Quantum Computing System Types And UsageThis slide showcases types of quantum computing systems. The purpose of this slide is to explain analogue quantum computers, noisy intermediate-scale quantum technology and fully error-corrected quantum computer. Deliver an outstanding presentation on the topic using this Current Trending Technologies Quantum Computing System Types And Usage. Dispense information and present a thorough explanation of Analogue Quantum Computers, Universal Quantum Computers, Quantum Computing Systems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 New Technologies Quantum Computing System Types And Usage
New Technologies Quantum Computing System Types And UsageThis slide showcases types of quantum computing systems. The purpose of this slide is to explain analogue quantum computers, noisy intermediate-scale quantum technology and fully error-corrected quantum computer. Present the topic in a bit more detail with this New Technologies Quantum Computing System Types And Usage. Use it as a tool for discussion and navigation on Analogue Quantum Computers, Universal Quantum Computers, Quantum Computers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Memory System Computer Architecture In Powerpoint And Google Slides Cpb
Memory System Computer Architecture In Powerpoint And Google Slides CpbPresenting Memory System Computer Architecture In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase seven stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Memory System Computer Architecture. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Server Security And Computer Networking System Icon
Server Security And Computer Networking System IconPresenting our set of slides with Server Security And Computer Networking System Icon. This exhibits information on threestages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Server Security, Computer Networking System.
-
 Computer Maintenance Report To Assess System Performance
Computer Maintenance Report To Assess System PerformanceFollowing slide showcases maintenance report of computer systems, also including critical tasks, frequency, status, date of completion. Introducing our Computer Maintenance Report To Assess System Performance set of slides. The topics discussed in these slides are Frequency, Date Completed This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Considerations For Cloud Computing Systems Audit
Considerations For Cloud Computing Systems AuditThis slide showcases key considerations for cloud computing systems audit to determine potential vulnerabilities such as security by design, logging and monitoring, etc. Presenting our set of slides with name Considerations For Cloud Computing Systems Audit. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Key Considerations, Cloud Computing Systems Audit, Potential Vulnerabilities, Logging And Monitoring.
-
 Adopting Green Computing For Attaining Green Hardware System To Reduce
Adopting Green Computing For Attaining Green Hardware System To ReduceThis slide covers integrating energy efficient green hardware system to reduce energy consumption. It involves hardware systems such as energy efficient processors, advanced power management and green data centers. Introducing Adopting Green Computing For Attaining Green Hardware System To Reduce to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Reduced Energy Consumption, Improved Performance, Extended Hardware Lifespan, Lower Operating Costs, using this template. Grab it now to reap its full benefits.
-
 Key Components Of Computer Network System
Key Components Of Computer Network SystemThis slide highlights major elements of computer network mechanisms which help system to receive and send data over network. It includes components such as IP addresses, nodes, routers, ports, and cable. Presenting our set of slides with Key Components Of Computer Network System. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Create, And Store Data Over Network, Transfer Information, Connect Physical Devices.
-
 Open System Interconnection Model Layers In Computer Network
Open System Interconnection Model Layers In Computer NetworkThis slide highlights multiple layers of open system interconnection model of computer networks to provide a standardized framework that facilitates interoperability and communication between diverse network technologies. Introducing our premium set of slides with Open System Interconnection Model Layers In Computer Network. Ellicudate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Network, Data Frames, Computer Network. So download instantly and tailor it with your information.
-
 Icon For Ubiquitous Computing In Business It Systems
Icon For Ubiquitous Computing In Business It SystemsIntroducing our premium set of slides with Icon For Ubiquitous Computing In Business It Systems. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon, Ubiquitous Computing, Business IT Systems. So download instantly and tailor it with your information.
-
 Key Features Of Ubiquitous Computing In It Systems
Key Features Of Ubiquitous Computing In It SystemsThis slide highlights the key characteristics of ubiquitous computing. The purpose of this slide is to help the business enhance its IT systems through the installation of ubiquitous computing. It includes characteristics such as cost effectiveness, real time connectivity, etc. Presenting our set of slides with Key Features Of Ubiquitous Computing In It Systems. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cost Effectiveness, Improved Surveillance, Wireless Technology Integration.
-
 Computer Maintenance Record To Assess System
Computer Maintenance Record To Assess SystemThis slide showcases showcases maintenance report of computer systems, also including critical tasks, frequency, status, date of completion. Presenting our well structured Computer Maintenance Record To Assess System. The topics discussed in this slide are Inspection Of Noise And Vibration, Replacement Of Belts, Computer Maintenance. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Computer Function Operating System In Powerpoint And Google Slides Cpp
Computer Function Operating System In Powerpoint And Google Slides CppPresenting Computer Function Operating System In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Computer Function Operating System. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Computer Vision Applications In Intelligent Transportation Systems Driving Smart TC SS
Computer Vision Applications In Intelligent Transportation Systems Driving Smart TC SSThis slide showcases the impact of integrating computer vision to optimize the applications of intelligent transportation system. It includes traffic monitoring and management, vehicle counting and classification, and predictive maintenance. Present the topic in a bit more detail with this Computer Vision Applications In Intelligent Transportation Systems Driving Smart TC SS. Use it as a tool for discussion and navigation on Traffic Monitoring And Management, Vehicle Counting And Classification, Predictive Maintenance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer System Virus Icon For Prevention In DOS Cyberattack
Computer System Virus Icon For Prevention In DOS CyberattackIntroducing our premium set of slides with name Computer System Virus Icon For Prevention In DOS Cyberattack. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Computer System, Virus Icon, Prevention DOS Cyberattack. So download instantly and tailor it with your information.
-
 Embedded Vs General Purpose Computing Systems Mastering Embedded Systems Technology
Embedded Vs General Purpose Computing Systems Mastering Embedded Systems TechnologyThis slide compares an embedded system and a general-purpose computing system. The purpose of this slide is to highlight the key differences between embedded and general-purpose computing systems based on primary function, hardware, software, real-time operation, power consumption and so on. Present the topic in a bit more detail with this Embedded Vs General Purpose Computing Systems Mastering Embedded Systems Technology. Use it as a tool for discussion and navigation on Customized And Often Lightweight, Form Factor, Resource Constraints, Primary Function. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Main Types Of Memory Hierarchy In Computer System Memory Hierarchy
Main Types Of Memory Hierarchy In Computer System Memory HierarchyThis slide highlights the two types of memory hierarchy in operating system which includes internal and external memory hierarchy. Increase audience engagement and knowledge by dispensing information using Main Types Of Memory Hierarchy In Computer System Memory Hierarchy This template helps you present information on two stages. You can also present information on Accessed By Processes, Stores Data, Holds Megabytes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Major Components Of High Performance Computing System
Major Components Of High Performance Computing SystemThe purpose of this slide is to highlight the main components of high-performance computing such as computing, network, storage, etc. Introducing Major Components Of High Performance Computing System to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Compute, Network, Storage, using this template. Grab it now to reap its full benefits.
-
 Comparitive Assessment For Billing Computer Software Systems
Comparitive Assessment For Billing Computer Software SystemsFollowing slide highlights aiding enterprise performance with billing computer software for enhanced automation solution. It further covers tools, cost, remarks and features such as automated data collection, customized reporting, etc. Introducing our Comparitive Assessment For Billing Computer Software Systems set of slides. The topics discussed in these slides are Tools, Features, CostThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Key Features For Computer System To Imporve Crm
Key Features For Computer System To Imporve CrmFollowing slide highlights computer system CRM software features for correct business decisions. It further covers features such as real time data, automation, customization, reports and CRM analytics. Presenting our set of slides with Key Features For Computer System To Imporve Crm This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Customization, Automation, Real Time Data
-
 Pharmacy Management System Computer Software
Pharmacy Management System Computer SoftwareFollowing slide highlights computer software management system of pharmacy for customization. It further covers tools, deployment, integration number, mobile apps, use cases, customization capabilities, etc. Presenting our set of slides with Pharmacy Management System Computer Software This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Deployment, Integrations Number, Mobile App





