Powerpoint Templates and Google slides for Computer Systems
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Computer system security roadmap ppt powerpoint presentation slides visuals
Computer system security roadmap ppt powerpoint presentation slides visualsIncrease audience engagement and knowledge by dispensing information using Computer System Security Roadmap Ppt Powerpoint Presentation Slides Visuals. This template helps you present information on four stages. You can also present information on Roadmap, 2018 To 2020 using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer system security security of employees devices
Computer system security security of employees devicesThis slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Introducing Computer System Security Security Of Employees Devices to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Security Of Employees Devices, using this template. Grab it now to reap its full benefits.
-
 Computer system security set measures for secure communication
Computer system security set measures for secure communicationThis slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. Increase audience engagement and knowledge by dispensing information using Computer System Security Set Measures For Secure Communication. This template helps you present information on six stages. You can also present information on Technology, Training, Organization, Data Transfer using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer system security strategies to manage cyber risks
Computer system security strategies to manage cyber risksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Introducing Computer System Security Strategies To Manage Cyber Risks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Secure, Vigilant, Resilient, Implementation, Awareness, using this template. Grab it now to reap its full benefits.
-
 Computer system security timeline for the implementation of computer security
Computer system security timeline for the implementation of computer securityThis slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Present the topic in a bit more detail with this Computer System Security Timeline For The Implementation Of Computer Security. Use it as a tool for discussion and navigation on Security, Risk Assessments, Perform. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security timeline ppt powerpoint presentation slides visuals
Computer system security timeline ppt powerpoint presentation slides visualsIntroducing Computer System Security Timeline Ppt Powerpoint Presentation Slides Visuals to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Timeline, 2016 To 2021, using this template. Grab it now to reap its full benefits.
-
 Computer system security types of threats in computer security
Computer system security types of threats in computer securityThis slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Increase audience engagement and knowledge by dispensing information using Computer System Security Types Of Threats In Computer Security. This template helps you present information on three stages. You can also present information on Cyber Crime, Cyber Terrorism, Cyber Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer system security what is computer security and how does it work
Computer system security what is computer security and how does it workThis slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Introducing Computer System Security What Is Computer Security And How Does It Work to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Techniques, Collective, Networks, Computer Systems, using this template. Grab it now to reap its full benefits.
-
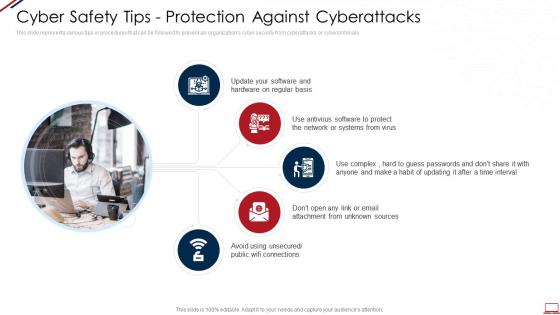 Cyber safety tips protection against cyberattacks computer system security
Cyber safety tips protection against cyberattacks computer system securityThis slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Increase audience engagement and knowledge by dispensing information using Cyber Safety Tips Protection Against Cyberattacks Computer System Security. This template helps you present information on five stages. You can also present information on Cyber Safety Tips Protection Against Cyberattacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Elements of computer security application security computer system security
Elements of computer security application security computer system securityThis slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. Introducing Elements Of Computer Security Application Security Computer System Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Developers, Weaknesses, Cyber Security, Management, Input Validation, using this template. Grab it now to reap its full benefits.
-
 Icons slide for computer system security ppt powerpoint presentation slides visuals
Icons slide for computer system security ppt powerpoint presentation slides visualsIntroducing our well researched set of slides titled Icons Slide For Computer System Security Ppt Powerpoint Presentation Slides Visuals. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Managing computer security 30 days plan computer system security
Managing computer security 30 days plan computer system securityPresent the topic in a bit more detail with this Managing Computer Security 30 Days Plan Computer System Security. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing Reporting, Phishing Repeat Offenders, Facility Physical Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prepare a disaster recovery plan computer system security ppt powerpoint tipswd
Prepare a disaster recovery plan computer system security ppt powerpoint tipswdThis slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. Introducing Prepare A Disaster Recovery Plan Computer System Security Ppt Powerpoint Tipswd to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Make A Report Of All Assets, Risk Assessment Report, Identify The Importance Of Assets, using this template. Grab it now to reap its full benefits.
-
 Table of contents for computer system security cont ppt powerpoint slides guide
Table of contents for computer system security cont ppt powerpoint slides guidePresent the topic in a bit more detail with this Table Of Contents For Computer System Security Cont Ppt Powerpoint Slides Guide. Use it as a tool for discussion and navigation on Organization, Mitigation, Implementation, Security, Planning. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Types Computer Systems In Powerpoint And Google Slides Cpb
Different Types Computer Systems In Powerpoint And Google Slides CpbPresenting Different Types Computer Systems In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Different Types Computer Systems. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Confidential Computing Market Occlum System Architecture And Features
Confidential Computing Market Occlum System Architecture And FeaturesThis slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on. Deliver an outstanding presentation on the topic using this Confidential Computing Market Occlum System Architecture And Features. Dispense information and present a thorough explanation of Architecture, Environment, Multi Process Support using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
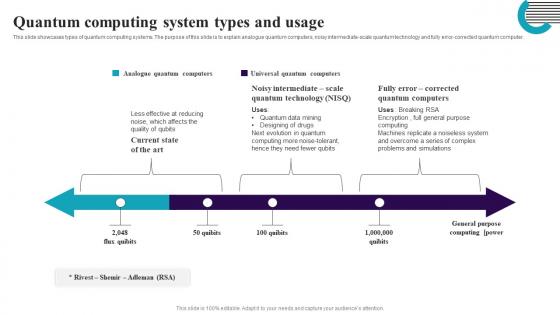 Quantum Computing System Types And Usage Quantum Computing It
Quantum Computing System Types And Usage Quantum Computing ItThis slide showcases types of quantum computing systems. The purpose of this slide is to explain analogue quantum computers, noisy intermediate-scale quantum technology and fully error-corrected quantum computer. Increase audience engagement and knowledge by dispensing information using Quantum Computing System Types And Usage Quantum Computing It. This template helps you present information on eight stages. You can also present information on Analogue Quantum Computers, Simulations, Evolution using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer Cloud Database System Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Cloud Database System Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a visual representation of a cloud database. It is designed to help you easily identify and access your cloud-based data storage. It is a great way to store and manage your data securely and efficiently.
-
 Computer Cloud Database System Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Cloud Database System Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon is a perfect visual representation of a cloud database. It is a simple, yet powerful design that conveys the concept of data storage in the cloud. It is a great choice for presentations and other projects.
-
 Processing Computer System In Powerpoint And Google Slides Cpb
Processing Computer System In Powerpoint And Google Slides CpbPresenting Processing Computer System In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Processing Computer System. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Computerized System Validation In Powerpoint And Google Slides Cpb
Computerized System Validation In Powerpoint And Google Slides CpbPresenting our Computerized System Validation In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Computerized System Validation This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Confidential Computing Hardware Occlum System Architecture And Features
Confidential Computing Hardware Occlum System Architecture And FeaturesThis slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on. Introducing Confidential Computing Hardware Occlum System Architecture And Features to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Trusted Environment, Efficient Multi Process Support, Memory Security Guarantee, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Consortium Occlum System Architecture And Features
Confidential Computing Consortium Occlum System Architecture And FeaturesThis slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on. Introducing Confidential Computing Consortium Occlum System Architecture And Features to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Trusted Environment, Powerful File Systems, Memory Security Guarantee, Efficient Multi Process Support, using this template. Grab it now to reap its full benefits.
-
 Storage Area Network San About Internet Small Computer System Interface Iscsi
Storage Area Network San About Internet Small Computer System Interface IscsiThis Slide Gives An Introduction To The Iscsitype Of Connection Protocol That Is Used In SAN. The Purpose Of This Slide Is To Provide An Overview Of Iscsi, Its Architecture, Primary Components, And Types Of Internet Small Computer System Interface Initiators, Such As Software-Based And Hardware-Based Initiators. Deliver An Outstanding Presentation On The Topic Using This Storage Area Network San About Internet Small Computer System Interface Iscsi. Dispense Information And Present A Thorough Explanation Of Resources, Information, Applications Using The Slides Given. This Template Can Be Altered And Personalized To Fit Your Needs. It Is Also Available For Immediate Download. So Grab It Now.
-
 Storage Area Network San Components Of Internet Small Computer System Interface Iscsi
Storage Area Network San Components Of Internet Small Computer System Interface IscsiThis Slide Outlines The Primary Elements Of The Internet Small Computer System Interface Iscsi. The Purpose Of This Slide Is To Showcase The Overview Of Iscsicomponents, Their Working And Cost Estimates. In Iscsi, The Data Exchange Between The Client Iscsiinitiator And The Storage Device Iscsitarget Occurs At The Block Level. Present The Topic In A Bit More Detail With This Storage Area Network San Components Of Internet Small Computer System Interface Iscsi. Use It As A Tool For Discussion And Navigation On Components, Overview, Resources. This Template Is Free To Edit As Deemed Fit For Your Organization. Therefore Download It Now.
-
 Storage Area Network San Ethernet Alternatives To Internet Small Computer System Interface Iscsi
Storage Area Network San Ethernet Alternatives To Internet Small Computer System Interface IscsiThis slide outlines the other ethernet options available to use instead of iSCSI. The purpose of this slide is to showcase the various alternatives to Internet Small Computer System Interface, including FCIP, iFCP, FCoE, and AoE. Deliver an outstanding presentation on the topic using this Storage Area Network San Ethernet Alternatives To Internet Small Computer System Interface Iscsi. Dispense information and present a thorough explanation of Alternatives, Organization, Communicate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Storage Area Network San Features And Benefits Of Internet Small Computer System Interface Iscsi
Storage Area Network San Features And Benefits Of Internet Small Computer System Interface IscsiThis Slide Represents The Characteristics And Advantages Of Internet Small Computer System Interface Iscsi. The Purpose Of This Slide Is To Showcase The Various Features And Benefits Of Iscsi. The Features Include IP Routing, Storage Array, Security, And Standard Ethernet. Deliver An Outstanding Presentation On The Topic Using This Storage Area Network San Features And Benefits Of Internet Small Computer System Interface Iscsi. Dispense Information And Present A Thorough Explanation Of Equipment, Expensive, Connection Using The Slides Given. This Template Can Be Altered And Personalized To Fit Your Needs. It Is Also Available For Immediate Download. So Grab It Now.
-
 Storage Area Network San Internet Small Computer System Interface Iscsi Architecture And Working
Storage Area Network San Internet Small Computer System Interface Iscsi Architecture And WorkingThis Slide Represents The Architecture And Working Of The Internet Small Computer System Interface Iscsi. The Purpose Of This Slide Is To Showcase The Architecture Of Iscsialong With Its Working. The Architecture Components Include The OSI Model, Iscsiinitiator, And Iscsitarget. Present The Topic In A Bit More Detail With This Storage Area Network San Internet Small Computer System Interface Iscsi Architecture And Working. Use It As A Tool For Discussion And Navigation On Architecture, Information, Virtualization. This Template Is Free To Edit As Deemed Fit For Your Organization. Therefore Download It Now.
-
 Distributed System Computer Network In Powerpoint And Google Slides Cpb
Distributed System Computer Network In Powerpoint And Google Slides CpbPresenting Distributed System Computer Network In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Distributed System Computer Network. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Grid Computing Architecture Requirements To Develop Grid Computing Systems
Grid Computing Architecture Requirements To Develop Grid Computing SystemsThis slide depicts the key requirements for developing a grid computing system. It includes one machine that will work as a server and manage all administrative functions, a network of computers running grid computing network software, and a group of computer software to perform as middleware. Increase audience engagement and knowledge by dispensing information using Grid Computing Architecture Requirements To Develop Grid Computing Systems. This template helps you present information on three stages. You can also present information on System Administrative Functions, Computing Network Program, Group Of Computer Programs, Middleware Is The Workhorse using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Text Mining System And Database Computing Icon
Text Mining System And Database Computing IconPresenting our set of slides withText Mining System And Database Computing Icon. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Text Mining System, Showcasing Data Analysis Icon.
-
 Advanced Technologies Quantum Computing System Types And Usage
Advanced Technologies Quantum Computing System Types And UsageThis slide showcases types of quantum computing systems. The purpose of this slide is to explain analogue quantum computers, noisy intermediate-scale quantum technology and fully error-corrected quantum computer. Present the topic in a bit more detail with this Advanced Technologies Quantum Computing System Types And Usage. Use it as a tool for discussion and navigation on Intermediate Scale Quantum, Quantum Computers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ack Tee 2 0 Architecture And Workflow Confidential Computing System Technology
Ack Tee 2 0 Architecture And Workflow Confidential Computing System TechnologyThis slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Present the topic in a bit more detail with this Ack Tee 2 0 Architecture And Workflow Confidential Computing System Technology. Use it as a tool for discussion and navigation on Architecture, Workflow, Confidential. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ack Tee Introduction And Version 1 0 Confidential Computing System Technology
Ack Tee Introduction And Version 1 0 Confidential Computing System TechnologyThis slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. Deliver an outstanding presentation on the topic using this Ack Tee Introduction And Version 1 0 Confidential Computing System Technology. Dispense information and present a thorough explanation of Introduction, Maintenance, Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Agenda For Confidential Computing System Technology
Agenda For Confidential Computing System TechnologyIntroducing Agenda For Confidential Computing System Technology to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Technology, Applications, Environment, using this template. Grab it now to reap its full benefits.
-
 Budget For Implementing Architecture Confidential Computing System Technology
Budget For Implementing Architecture Confidential Computing System TechnologyThis slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Deliver an outstanding presentation on the topic using this Budget For Implementing Architecture Confidential Computing System Technology. Dispense information and present a thorough explanation of Implementing, Confidential, Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Case Study Irene Energy Confidential Computing System Technology
Case Study Irene Energy Confidential Computing System TechnologyThis slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact. Present the topic in a bit more detail with this Case Study Irene Energy Confidential Computing System Technology. Use it as a tool for discussion and navigation on Manufacturers, Distributors, Solutions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Implement Architecture Confidential Computing System Technology
Checklist To Implement Architecture Confidential Computing System TechnologyThis slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person. Deliver an outstanding presentation on the topic using this Checklist To Implement Architecture Confidential Computing System Technology. Dispense information and present a thorough explanation of Confidential, Computing, Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Client Signature And Server Signature In Inclavare Confidential Computing System Technology
Client Signature And Server Signature In Inclavare Confidential Computing System TechnologyThis slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature. Present the topic in a bit more detail with this Client Signature And Server Signature In Inclavare Confidential Computing System Technology. Use it as a tool for discussion and navigation on Technology, Business, Certifications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Companies Paving The Path For Confidential Computing System Technology
Companies Paving The Path For Confidential Computing System TechnologyThis slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. Introducing Companies Paving The Path For Confidential Computing System Technology to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Containerized, Services, Execution, using this template. Grab it now to reap its full benefits.
-
 Confidential Applications In Different Sectors Confidential Computing System Technology
Confidential Applications In Different Sectors Confidential Computing System TechnologyThis slide represents the applications of confidential computing in different sectors. This slide aims to demonstrate the confidential computing applications in healthcare and research, finance, engineering and manufacturing, and automobile sectors. Deliver an outstanding presentation on the topic using this Confidential Applications In Different Sectors Confidential Computing System Technology. Dispense information and present a thorough explanation of Businesses, Information, Confidentiality using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Architecture And Realms Working Confidential Computing System Technology
Confidential Architecture And Realms Working Confidential Computing System TechnologyThis slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on. Present the topic in a bit more detail with this Confidential Architecture And Realms Working Confidential Computing System Technology. Use it as a tool for discussion and navigation on Confidential, Computing, Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Architecture Implementation Confidential Computing System Technology
Confidential Computing Architecture Implementation Confidential Computing System TechnologyThis slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Introducing Confidential Computing Architecture Implementation Confidential Computing System Technology to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Architecture, Implementation, Timeline, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Based On Azure Services Confidential Computing System Technology
Confidential Computing Based On Azure Services Confidential Computing System TechnologyThis slide represents the architecture of confidential computing based on Azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc. Present the topic in a bit more detail with this Confidential Computing Based On Azure Services Confidential Computing System Technology. Use it as a tool for discussion and navigation on Architecture, Services, Solutions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing System Technology For Table Of Contents
Confidential Computing System Technology For Table Of ContentsIntroducing Confidential Computing System Technology For Table Of Contents to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Technology, Approaches, Architecture, using this template. Grab it now to reap its full benefits.
-
 Confidential Consortium Membership Levels Confidential Computing System Technology
Confidential Consortium Membership Levels Confidential Computing System TechnologyThis slide represents the confidential computing consortium membership and participation levels. The purpose of this slide is to demonstrate the various partnership levels, annual fees, board seats, technical advisory committee seats, outreach committees, and notes. Deliver an outstanding presentation on the topic using this Confidential Consortium Membership Levels Confidential Computing System Technology. Dispense information and present a thorough explanation of Confidential, Computing, Consortium using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Consortium Overview And Benefits Confidential Computing System Technology
Confidential Consortium Overview And Benefits Confidential Computing System TechnologyThis slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium. Present the topic in a bit more detail with this Confidential Consortium Overview And Benefits Confidential Computing System Technology. Use it as a tool for discussion and navigation on Confidential, Consortium, Overview. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Executive Summary Of Key Findings Confidential Computing System Technology
Confidential Executive Summary Of Key Findings Confidential Computing System TechnologyThis slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on. Present the topic in a bit more detail with this Confidential Executive Summary Of Key Findings Confidential Computing System Technology. Use it as a tool for discussion and navigation on Implementation, Considerations, Executives. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Implementation Roadmap Confidential Computing System Technology
Confidential Implementation Roadmap Confidential Computing System TechnologyThis slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Increase audience engagement and knowledge by dispensing information using Confidential Implementation Roadmap Confidential Computing System Technology. This template helps you present information on five stages. You can also present information on Architecture, Implementation, Roadmap using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Critical Functions Of Confidential Computing Technology Confidential Computing System Technology
Critical Functions Of Confidential Computing Technology Confidential Computing System TechnologyThis slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Present the topic in a bit more detail with this Critical Functions Of Confidential Computing Technology Confidential Computing System Technology. Use it as a tool for discussion and navigation on Data Confidentially, Data Integrity, Code Integrity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial And Healthcare Industry Scenario Analysis Confidential Computing System Technology
Financial And Healthcare Industry Scenario Analysis Confidential Computing System TechnologyThis slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario. Deliver an outstanding presentation on the topic using this Financial And Healthcare Industry Scenario Analysis Confidential Computing System Technology. Dispense information and present a thorough explanation of Financial, Services, Analysis using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Future Of Confidential Computing Technology Confidential Computing System Technology
Future Of Confidential Computing Technology Confidential Computing System TechnologyThis slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Introducing Future Of Confidential Computing Technology Confidential Computing System Technology to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Confidential, Computing, Technology, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Confidential Computing System Technology
Icons Slide For Confidential Computing System TechnologyPresent the topic in a bit more detail with this Icons Slide For Confidential Computing System Technology. Use it as a tool for discussion and navigation on Icons. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 In And Threat Vectors For Confidential Computing Confidential Computing System Technology
In And Threat Vectors For Confidential Computing Confidential Computing System TechnologyThis slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Increase audience engagement and knowledge by dispensing information using In And Threat Vectors For Confidential Computing Confidential Computing System Technology. This template helps you present information on seven stages. You can also present information on Software Attacks, Protocol Attacks, Cryptographic Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Features Of Confidential Computing Platform Confidential Computing System Technology
Key Features Of Confidential Computing Platform Confidential Computing System TechnologyThis slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential Google Kubernetes Engine node. Introducing Key Features Of Confidential Computing Platform Confidential Computing System Technology to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Confidential Space, Confidential Dataproc, Confidential Gke Nodes, using this template. Grab it now to reap its full benefits.
-
 Multi Team And Cooperation In Inclavare Containers Confidential Computing System Technology
Multi Team And Cooperation In Inclavare Containers Confidential Computing System TechnologyThis slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes. Deliver an outstanding presentation on the topic using this Multi Team And Cooperation In Inclavare Containers Confidential Computing System Technology. Dispense information and present a thorough explanation of Construction, Cooperation, Containers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Multiparty Privacy Computation Architecture Design Confidential Computing System Technology
Multiparty Privacy Computation Architecture Design Confidential Computing System TechnologyThis slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on. Present the topic in a bit more detail with this Multiparty Privacy Computation Architecture Design Confidential Computing System Technology. Use it as a tool for discussion and navigation on Computation, Architecture, Technologies . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Occlum System Architecture And Features Confidential Computing System Technology
Occlum System Architecture And Features Confidential Computing System TechnologyThis slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on. Present the topic in a bit more detail with this Occlum System Architecture And Features Confidential Computing System Technology. Use it as a tool for discussion and navigation on Trusted Environment, Untrusted Environment, Memory Security Guarantee. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Computing Consortium Structure Confidential Computing System Technology
Overview Of Computing Consortium Structure Confidential Computing System TechnologyThis slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on. Present the topic in a bit more detail with this Overview Of Computing Consortium Structure Confidential Computing System Technology. Use it as a tool for discussion and navigation on Computing, Consortium, Structure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Shim Rune Workflow In Inclavare Containers Confidential Computing System Technology
Shim Rune Workflow In Inclavare Containers Confidential Computing System TechnologyThis slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on. Present the topic in a bit more detail with this Shim Rune Workflow In Inclavare Containers Confidential Computing System Technology. Use it as a tool for discussion and navigation on Component, Workflow, Inclavare Containers. This template is free to edit as deemed fit for your organization. Therefore download it now.





