Powerpoint Templates and Google slides for Breach
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Contingency Plan To Mitigate Customer Data Breach
Contingency Plan To Mitigate Customer Data BreachThis slide represents contingency plan to mitigate customer data breach including elements such as event, trigger points, event response, etc. Presenting our set of slides with Contingency Plan To Mitigate Customer Data Breach This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Supervisor, Trigger Points, Contingency Plan
-
 Web application firewall waf it implementation decreased risk data breach in web apps
Web application firewall waf it implementation decreased risk data breach in web appsThis slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Deliver an outstanding presentation on the topic using this Web Application Firewall Waf It Implementation Decreased Risk Data Breach In Web Apps. Dispense information and present a thorough explanation of Implementation, Misconfiguration, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Detail Impact Information Security Can Reduce Risk Data Breach Organization
Information Security Detail Impact Information Security Can Reduce Risk Data Breach OrganizationThis slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver an outstanding presentation on the topic using this Information Security Detail Impact Information Security Can Reduce Risk Data Breach Organization. Dispense information and present a thorough explanation of Organization, Information, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Assessing Cost Of Information Breach In Risk Assessment And Management Plan For Information Security
Assessing Cost Of Information Breach In Risk Assessment And Management Plan For Information SecurityPresent the topic in a bit more detail with this Assessing Cost Of Information Breach In Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Information, Sources, Engineering. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Assessment And Management Plan For Information Security Information And Data Breach Impacting
Risk Assessment And Management Plan For Information Security Information And Data Breach ImpactingDeliver an outstanding presentation on the topic using this Risk Assessment And Management Plan For Information Security Information And Data Breach Impacting. Dispense information and present a thorough explanation of Information, Business, Financial using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Assessing Cost Of Information Breach In Different Countries Information Security Risk Management
Assessing Cost Of Information Breach In Different Countries Information Security Risk ManagementDeliver an outstanding presentation on the topic using this Assessing Cost Of Information Breach In Different Countries Information Security Risk Management. Dispense information and present a thorough explanation of Assessing, Information Breach, Different Countries using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information And Data Breach Impacting Customer Loyalty Information Security Risk Management
Information And Data Breach Impacting Customer Loyalty Information Security Risk ManagementDeliver an outstanding presentation on the topic using this Information And Data Breach Impacting Customer Loyalty Information Security Risk Management. Dispense information and present a thorough explanation of Information, Data Breach Impacting, Customer Loyalty using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Firewall WAF Implementation Decreased the Risk of Data Breach in Web Apps
Application Firewall WAF Implementation Decreased the Risk of Data Breach in Web AppsThis slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Present the topic in a bit more detail with this Application Firewall WAF Implementation Decreased the Risk of Data Breach in Web Apps. Use it as a tool for discussion and navigation on SQL Injection, Ddos Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Average Costing On Risk Management For Data Breach Incident
Average Costing On Risk Management For Data Breach IncidentThis slide covers total cost incurred on response of data breach incident. It includes four categories such as incident detection and escalation, notifications, post breach response, lost business cost ,etc. Presenting our well structured Average Costing On Risk Management For Data Breach Incident. The topics discussed in this slide are Average Costing On Risk, Management, Data Breach Incident. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Breakdown Of Malicious Data Breach Risk Root Cause By Threat
Breakdown Of Malicious Data Breach Risk Root Cause By ThreatThis slide depicts division of data breach with root cause. It includes risk categories such as compromised credentials, cloud misconfiguration, third party software vulnerability, phishing, security compromise, social engineering, business email compromise, etc. Introducing our Breakdown Of Malicious Data Breach Risk Root Cause By Threat set of slides. The topics discussed in these slides are Social Engineering, Business Email Compromise, Malicious Insider. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Breach Risks Stats On Social Media Platforms And Incident Sources
Data Breach Risks Stats On Social Media Platforms And Incident SourcesThis slide covers trends on social media data breach incidents reported. It also includes various sources of data theft such as malicious outsider, accidental loss, malicious insider, hacker, etc. Introducing our Data Breach Risks Stats On Social Media Platforms And Incident Sources set of slides. The topics discussed in these slides are Data Breach Risks, Stats On Social Media, Platforms And Incident Sources. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Theft And Breach Risk Monitoring Dashboard
Data Theft And Breach Risk Monitoring DashboardThis slide covers dashboard to monitor top data breaches and loss of confidential data in organization. It includes KPIs such percentage of data risks detected, number of data risks, data risk analysis, response progress for data risks, data risk ratings. Presenting our well structured Data Theft And Breach Risk Monitoring Dashboard. The topics discussed in this slide are Data Theft And Breach, Risk Monitoring, Dashboard. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Information System Security And Risk Administration Information And Data Breach Impacting Customer Loyalty
Information System Security And Risk Administration Information And Data Breach Impacting Customer LoyaltyDeliver an outstanding presentation on the topic using this Information System Security And Risk Administration Information And Data Breach Impacting Customer Loyalty. Dispense information and present a thorough explanation of Business, Financial Data, Data Breach using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Assessing Cost Of Information Breach In Different Information System Security And Risk Administration Plan
Assessing Cost Of Information Breach In Different Information System Security And Risk Administration PlanPresent the topic in a bit more detail with this Assessing Cost Of Information Breach In Different Information System Security And Risk Administration Plan. Use it as a tool for discussion and navigation on Past Decade, Social Engineering, Advanced Persistent Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt Diagrams
Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt DiagramsThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Deliver an outstanding presentation on the topic using this Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt Diagrams. Dispense information and present a thorough explanation of Data Breaches, Consequences, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
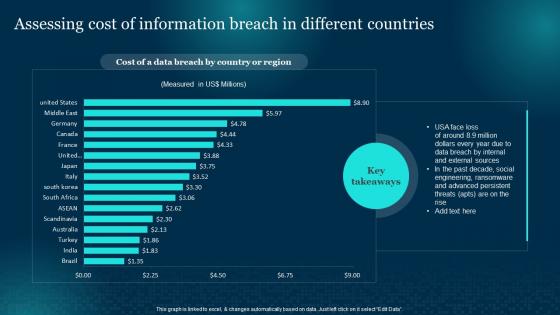 Assessing Cost Of Information Breach In Cybersecurity Risk Analysis And Management Plan
Assessing Cost Of Information Breach In Cybersecurity Risk Analysis And Management PlanPresent the topic in a bit more detail with this Assessing Cost Of Information Breach In Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Information, Ransomware, Sources. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
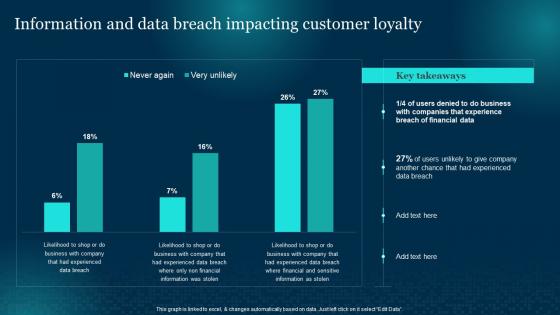 Cybersecurity Risk Analysis And Management Plan Information And Data Breach Impacting
Cybersecurity Risk Analysis And Management Plan Information And Data Breach ImpactingPresent the topic in a bit more detail with this Cybersecurity Risk Analysis And Management Plan Information And Data Breach Impacting. Use it as a tool for discussion and navigation on Information, Customer Loyalty, Financial Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Assessing Cost Of Information Breach In Different Countries Formulating Cybersecurity Plan
Assessing Cost Of Information Breach In Different Countries Formulating Cybersecurity PlanPresent the topic in a bit more detail with this Assessing Cost Of Information Breach In Different Countries Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Assessing, Information Breach, Different Countries. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information And Data Breach Impacting Customer Loyalty Formulating Cybersecurity Plan
Information And Data Breach Impacting Customer Loyalty Formulating Cybersecurity PlanPresent the topic in a bit more detail with this Information And Data Breach Impacting Customer Loyalty Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Information, Data Breach Impacting, Customer Loyalty. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Conducting Cyber Security Gap Analysis Of Organization Preventing Data Breaches Through Cyber Security
Conducting Cyber Security Gap Analysis Of Organization Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Deliver an outstanding presentation on the topic using this Conducting Cyber Security Gap Analysis Of Organization Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Current State, Email, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determining The Actors Behind Most Significant Cyber Attack Preventing Data Breaches Through Cyber Security
Determining The Actors Behind Most Significant Cyber Attack Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present the topic in a bit more detail with this Determining The Actors Behind Most Significant Cyber Attack Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Online Criminals, Foreign Government Officials, Malicious Insiders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Statistics Showing The Impact Of Security Awarenesspreventing Data Breaches Through Cyber Security
Key Statistics Showing The Impact Of Security Awarenesspreventing Data Breaches Through Cyber SecurityPresent the topic in a bit more detail with this Key Statistics Showing The Impact Of Security Awarenesspreventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Employees, Security, Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Kpi Dashboard To Monitor Cyber Security Performance Preventing Data Breaches Through Cyber Security
Kpi Dashboard To Monitor Cyber Security Performance Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. Deliver an outstanding presentation on the topic using this Kpi Dashboard To Monitor Cyber Security Performance Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Control Review Status, Management, Cyber Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber Security
Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Present the topic in a bit more detail with this Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Risk By Threats, Threat Report, Current Risk Status. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Measuring The Impact Of Security Awareness Training Preventing Data Breaches Through Cyber Security
Measuring The Impact Of Security Awareness Training Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. Present the topic in a bit more detail with this Measuring The Impact Of Security Awareness Training Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Security Awareness, Social Engineering. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Most Common Cyber Attack Faced By Our Employees Preventing Data Breaches Through Cyber Security
Most Common Cyber Attack Faced By Our Employees Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. Introducing Most Common Cyber Attack Faced By Our Employees Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Ransomware, Password Attack, Cryptojacking, using this template. Grab it now to reap its full benefits.
-
 Operational Outlook Of Security Awareness Training Software Preventing Data Breaches Through Cyber Security
Operational Outlook Of Security Awareness Training Software Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Present the topic in a bit more detail with this Operational Outlook Of Security Awareness Training Software Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Finished Training, Awareness Factors, Training Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Practices To Improve Security Awareness Level Amongst The Preventing Data Breaches Through Cyber Security
Practices To Improve Security Awareness Level Amongst The Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Increase audience engagement and knowledge by dispensing information using Practices To Improve Security Awareness Level Amongst The Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Get Management Involved, Develop Robust Policies, Set Guidelines using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Awareness Training Program Challenges Preventing Data Breaches Through Cyber Security
Security Awareness Training Program Challenges Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Increase audience engagement and knowledge by dispensing information using Security Awareness Training Program Challenges Preventing Data Breaches Through Cyber Security. This template helps you present information on five stages. You can also present information on Outdated Content, Employees Lose Interest, Burden On Administrators using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber Security
Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Limit Public Information, Verify The Source, No Sharing Of Password. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents For Preventing Data Breaches Through Cyber Security Awareness
Table Of Contents For Preventing Data Breaches Through Cyber Security AwarenessDeliver an outstanding presentation on the topic using this Table Of Contents For Preventing Data Breaches Through Cyber Security Awareness. Dispense information and present a thorough explanation of Cyber Security Awareness, Online Courses, Automation Tools using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 How To Overcome The Security Awareness Training Program Preventing Data Breaches Through Cyber Security
How To Overcome The Security Awareness Training Program Preventing Data Breaches Through Cyber SecurityThe purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program. Deliver an outstanding presentation on the topic using this How To Overcome The Security Awareness Training Program Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Outdated Content, Burden On Administrators, Low Employee Participation Rate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Safety And Security Breaches In Organization
Safety And Security Breaches In OrganizationThis slide shows the percentage of safety and security breaches took place in the company during each quarter. Introducing our Safety And Security Breaches In Organization set of slides. The topics discussed in these slides are Computer Data, Key Insights, Total Breaches. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Consequences Of Data Breaches Faced By Organization Incident Response Strategies Deployment
Consequences Of Data Breaches Faced By Organization Incident Response Strategies DeploymentThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Present the topic in a bit more detail with this Consequences Of Data Breaches Faced By Organization Incident Response Strategies Deployment. Use it as a tool for discussion and navigation on Data, Consequences, Portable. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Consequences Of Data Breaches Faced By Organization Development And Implementation Of Security
Consequences Of Data Breaches Faced By Organization Development And Implementation Of SecurityThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Deliver an outstanding presentation on the topic using this Consequences Of Data Breaches Faced By Organization Development And Implementation Of Security. Dispense information and present a thorough explanation of Payment Card Fraud, Physical Loss, Insider Leak using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Consequences Of Data Breaches Faced By Organization
Cyber Security Attacks Response Plan Consequences Of Data Breaches Faced By OrganizationThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Consequences Of Data Breaches Faced By Organization. Use it as a tool for discussion and navigation on Consequences, Data Breaches, Unintended Disclosure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
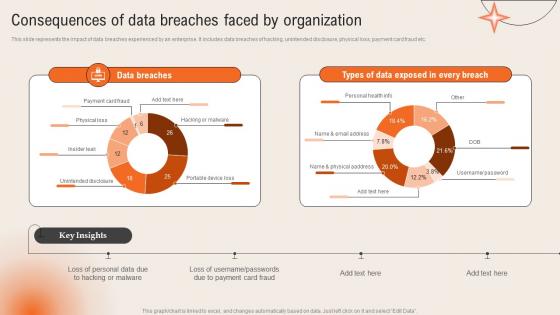 Consequences Of Data Breaches Faced By Organization Deploying Computer Security Incident Management
Consequences Of Data Breaches Faced By Organization Deploying Computer Security Incident ManagementThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc.Present the topic in a bit more detail with this Consequences Of Data Breaches Faced By Organization Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Unintended Disclosure, Portable Device, Hacking Malware. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Top Vulnerable Industries To Cyber Security Threats And Data Breaches
Top Vulnerable Industries To Cyber Security Threats And Data BreachesThis slide provides useful insights about most vulnerable industries to cyber security attacks and data breaches. The major industries are government, banking, communications, healthcare, e commerce, shipping and logistics and cryptocurrency Introducing our Top Vulnerable Industries To Cyber Security Threats And Data Breaches set of slides. The topics discussed in these slides are Government, Department. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 SecOps Effective Implementation Impact On Security Breaches Ppt Elements
SecOps Effective Implementation Impact On Security Breaches Ppt ElementsThis slide outlines the successful implementation impact of SecOps on organizational security breaches. The purpose of this slide is to highlight the number of reduced security breaches inside a company after implementing SecOps. Security breaches include phishing, network intrusion, and so on. Present the topic in a bit more detail with this SecOps Effective Implementation Impact On Security Breaches Ppt Elements. Use it as a tool for discussion and navigation on Security Breaches, Implementing Secops System. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Trend Generating Security Awareness Among Employees To Reduce
Data Breach Trend Generating Security Awareness Among Employees To ReduceThe following slide depicts the data breach trends to minimize information leakage and patch affected system. It includes elements such as breach risk trend, breach by risk category, current and future goal analysis etc. Deliver an outstanding presentation on the topic using this Data Breach Trend Generating Security Awareness Among Employees To Reduce Dispense information and present a thorough explanation of Data Breach Trend, Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Healthcare Cybersecurity Breach Downtime Report
Healthcare Cybersecurity Breach Downtime ReportThis slide presents pie chart to indicate cybersecurity breach downtime report in healthcare organisations helpful in gaining insights on effectiveness of threats that pose challenge for smooth operations. It includes amount of downtime due to cyberattacks and insights on actual damage done by these breaches. Presenting our well structured Healthcare Cybersecurity Breach Downtime Report The topics discussed in this slide are Amount Of Downtime, Due To Cyberattack. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Kpi for number of major control breaches percentage of key controls ppt slide
Kpi for number of major control breaches percentage of key controls ppt slidePresenting kpi for number of major control breaches percentage of key controls ppt slide. This presentation slide shows two Key Performance Indicators or KPIs in a Dashboard style design. The first KPI that can be shown is Number of Major Internal Control Breaches. The second KPI is percentage of Key Controls. These KPI Powerpoint graphics are all data driven,and the shape automatically adjusts according to your data. Just right click on the KPI graphic,enter the right value and the shape will adjust automatically. Make a visual impact with our KPI slides.
-
 Services breach ppt powerpoint presentation model format ideas cpb
Services breach ppt powerpoint presentation model format ideas cpbPresenting our Services Breach Ppt Powerpoint Presentation Model Format Ideas Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Services Breach This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Different types security breaches ppt powerpoint presentation portfolio file formats cpb
Different types security breaches ppt powerpoint presentation portfolio file formats cpbPresenting Different Types Security Breaches Ppt PowerPoint Presentation Portfolio File Formats Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Different Types Security Breaches. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Steps for developing data breach response plan
Steps for developing data breach response planThis slide covers the steps for developing data breach response plan which focuses on breach identification, internal notification and engagement of legal compliance which helps the organization proper management of security response plan. Introducing our premium set of slides with Steps For Developing Data Breach Response Plan. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identification, Occurrence, Determine, Compliance. So download instantly and tailor it with your information.
-
 Action plan in case of breaches managing cyber risk in a digital age
Action plan in case of breaches managing cyber risk in a digital ageMentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time. Present the topic in a bit more detail with this Action Plan In Case Of Breaches Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Action Plan In Case Of Breaches. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Communication plan for cyber breaches managing cyber risk in a digital age
Communication plan for cyber breaches managing cyber risk in a digital ageMentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Deliver an outstanding presentation on the topic using this Communication Plan For Cyber Breaches Managing Cyber Risk In A Digital Age. Dispense information and present a thorough explanation of Communication Plan For Cyber Breaches using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Evervault investor funding elevator we can end the data breach epidemic ppt icon
Evervault investor funding elevator we can end the data breach epidemic ppt iconThis slide depicts the major issues which organizations are facing such as breaches of customers, cost of breaches, protection of data, etc. Introducing Evervault Investor Funding Elevator We Can End The Data Breach Epidemic Ppt Icon to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on We Can End The Data Breach Epidemic, using this template. Grab it now to reap its full benefits.
-
 Information Security Program Cybersecurity Action Plan In Case Of Breaches
Information Security Program Cybersecurity Action Plan In Case Of BreachesMentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Action Plan In Case Of Breaches. Dispense information and present a thorough explanation of Action Plan In Case Of Breaches using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Cybersecurity Communication Plan For Cyber Breaches
Information Security Program Cybersecurity Communication Plan For Cyber BreachesMentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Communication Plan For Cyber Breaches. Dispense information and present a thorough explanation of Communication Plan For Cyber Breaches using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Action Plan In Case Of Breaches Risk Based Methodology To Cyber
Action Plan In Case Of Breaches Risk Based Methodology To CyberMentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time.Present the topic in a bit more detail with this Action Plan In Case Of Breaches Risk Based Methodology To Cyber Use it as a tool for discussion and navigation on Security Breach, Confidential Information, Resources Required This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Action Plan In Case Of Breaches Introducing A Risk Based Approach To Cyber Security
Action Plan In Case Of Breaches Introducing A Risk Based Approach To Cyber SecurityMentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time.Present the topic in a bit more detail with this Action Plan In Case Of Breaches Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Expected Resolution Time, Responsible Person, Communication Mode This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Communication Plan For Cyber Breaches Introducing A Risk Based Approach To Cyber Security
Communication Plan For Cyber Breaches Introducing A Risk Based Approach To Cyber SecurityMentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible.Present the topic in a bit more detail with this Communication Plan For Cyber Breaches Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Evaluate Sprint Status, Quality Standards, Project Coordinator This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Stage Five Security Breach Readiness AI Playbook Accelerate Digital Transformation
Stage Five Security Breach Readiness AI Playbook Accelerate Digital TransformationPurpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions.Present the topic in a bit more detail with this Stage Five Security Breach Readiness AI Playbook Accelerate Digital Transformation . Use it as a tool for discussion and navigation on Stage Five Security Breach Readiness Checklist . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ai Transformation Playbook Stage Five Security Breach Readiness Checklist
Ai Transformation Playbook Stage Five Security Breach Readiness ChecklistPurpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions.Present the topic in a bit more detail with this Ai Transformation Playbook Stage Five Security Breach Readiness Checklist Use it as a tool for discussion and navigation on Proper Risk Management, Each Organizational, Governance Procedures This template is free to edit as deemed fit for your organization. Therefore download it now.
-
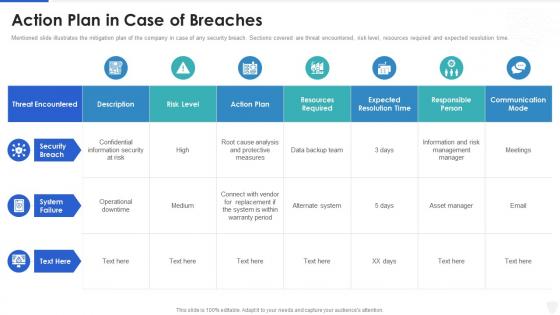 Cybersecurity and digital business risk management action plan in case of breaches
Cybersecurity and digital business risk management action plan in case of breachesMentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time. Present the topic in a bit more detail with this Cybersecurity And Digital Business Risk Management Action Plan In Case Of Breaches. Use it as a tool for discussion and navigation on Measures, Replacement, Resources. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity and digital business risk management communication plan for cyber breaches
Cybersecurity and digital business risk management communication plan for cyber breachesMentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Deliver an outstanding presentation on the topic using this Cybersecurity And Digital Business Risk Management Communication Plan For Cyber Breaches. Dispense information and present a thorough explanation of Communication, Product, Development using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 AIOps Playbook Stage Five Security Breach Readiness Checklist Ppt Topics
AIOps Playbook Stage Five Security Breach Readiness Checklist Ppt TopicsPurpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions. Introducing AIOps Playbook Stage Five Security Breach Readiness Checklist Ppt Topics to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Stage Five Security Breach Readiness Checklist, using this template. Grab it now to reap its full benefits.
-
 Stage Five Security Breach Readiness Checklist Artificial Intelligence Playbook For Business
Stage Five Security Breach Readiness Checklist Artificial Intelligence Playbook For BusinessPurpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions. Introducing Stage Five Security Breach Readiness Checklist Artificial Intelligence Playbook For Business to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Organizational Procedure, IT Operations, Operational Team, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Contract Breaches With Clients Cloud Information Security
Cloud Security Threats Contract Breaches With Clients Cloud Information SecurityThis slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data.Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Contract Breaches With Clients Cloud Information Security This template helps you present information on four stages. You can also present information on Organizations Cybercriminals, Customers OR Clients, Contact Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





