Powerpoint Templates and Google slides for Breach
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Data Breach Prevention Best Practices To Prevent Data Security Breach
Data Breach Prevention Best Practices To Prevent Data Security BreachThis slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management. Increase audience engagement and knowledge by dispensing information using Data Breach Prevention Best Practices To Prevent Data Security Breach. This template helps you present information on five stages. You can also present information on Prioritize Cybersecurity Openings, Resolve Prioritized Threats, Review Data Access Authorizations using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Breach Prevention Comparison Between Data Breaches And Data Leaks
Data Breach Prevention Comparison Between Data Breaches And Data LeaksThe purpose of this slide is to compare the data breach and data leak based on different aspects. The factors used to differentiate data breaches and data leaks are definition, intent, potential impact, cause, and prevention. Present the topic in a bit more detail with this Data Breach Prevention Comparison Between Data Breaches And Data Leaks. Use it as a tool for discussion and navigation on Financial Losses, Reputational Damage, Legal Matters, Cyberattacks, Insider Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Prevention Comparison Between Different Data Loss Prevention Tools
Data Breach Prevention Comparison Between Different Data Loss Prevention ToolsThis slide represents the services offered by various data loss prevention solutions available in the market. The benefits include endpoint protection, incident management, insider threat management, next-generation Data Loss Prevention, etc. Deliver an outstanding presentation on the topic using this Data Breach Prevention Comparison Between Different Data Loss Prevention Tools. Dispense information and present a thorough explanation of Data Loss Prevention Solutions, Endpoint Protection, Incident Management, Insider Threat Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention Data Breach Prevention Services Provided By Security Tools
Data Breach Prevention Data Breach Prevention Services Provided By Security ToolsThis slide represents the multiple layers of protection provided by security solution providers against data breaches. These include database firewalls, data masking and encryption, Data Loss Prevention DLP, user behavior analytics, alert prioritization, etc. Present the topic in a bit more detail with this Data Breach Prevention Data Breach Prevention Services Provided By Security Tools. Use it as a tool for discussion and navigation on Data Breach Prevention, Services Provided By Security Tools, Obfuscates Sensitive Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Prevention Data Breach Response Plan Notify Appropriate Parties
Data Breach Prevention Data Breach Response Plan Notify Appropriate PartiesThis slide represents steps, actions, timeline, and responsible party for sending notifications to affected parties after a data breach. The measures include determining legal requirements, notifying law enforcement, notifying affected businesses, notifying individuals, etc. Deliver an outstanding presentation on the topic using this Data Breach Prevention Data Breach Response Plan Notify Appropriate Parties. Dispense information and present a thorough explanation of Determine Legal Requirements, Notify Law Enforcement, Notify Affected Businesses, Notify Individuals using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention Immediate And Long Term Impact Of Data Security Breach
Data Breach Prevention Immediate And Long Term Impact Of Data Security BreachThis slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc. Present the topic in a bit more detail with this Data Breach Prevention Immediate And Long Term Impact Of Data Security Breach. Use it as a tool for discussion and navigation on Customer Breach Notifications, Damaged Brand Reputation, Public Relations Costs, Operational Disruption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Prevention Implementation Budget For Organization Data Breach Prevention
Data Breach Prevention Implementation Budget For Organization Data Breach PreventionThis slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security. Deliver an outstanding presentation on the topic using this Data Breach Prevention Implementation Budget For Organization Data Breach Prevention. Dispense information and present a thorough explanation of Data Breach Prevention, Cost Categories, Security Software And Tools, Security Consultants, Data Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention Information Included In Data Breach Notification
Data Breach Prevention Information Included In Data Breach NotificationThis slide outlines the key points to be included in data breach notification. These are descriptions of the compromise, information stolen, actions taken to handle the situation, actions to protect individuals, relevant points of contacts in the organization, etc. Present the topic in a bit more detail with this Data Breach Prevention Information Included In Data Breach Notification. Use it as a tool for discussion and navigation on Data Breach Notification, Information Stolen, Handle The Situation, Actions To Protect Individuals. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Prevention Major Consequences Of Data Breach Cyber Attack
Data Breach Prevention Major Consequences Of Data Breach Cyber AttackThis slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss. Introducing Data Breach Prevention Major Consequences Of Data Breach Cyber Attack to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Intellectual Property Loss, Financial Loss, Reputational Damage, Legal Consequences, using this template. Grab it now to reap its full benefits.
-
 Data Breach Prevention Phases Of Data Breach Attack Cycle
Data Breach Prevention Phases Of Data Breach Attack CycleThis slide represents the flow diagram of the data breach attack cycle. The major components of this slide are research, stage attack, exfiltrate, social engineering, attacker, weak infrastructure, database, server, accessed data, HTTP, FTP, email, etc. Deliver an outstanding presentation on the topic using this Data Breach Prevention Phases Of Data Breach Attack Cycle. Dispense information and present a thorough explanation of Infrastructure Weakness, Accessed Data, Social Engineering, Attacker Transfers Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention Roadmap To Implement Data Breach Prevention Strategies
Data Breach Prevention Roadmap To Implement Data Breach Prevention StrategiesThis slide represents the roadmap to prevent data breach attacks in organizations. The key steps include conduct a comprehensive risk assessment, implement data encryption, enforce access controls, employee training, develop an incident response plan, etc. Introducing Data Breach Prevention Roadmap To Implement Data Breach Prevention Strategies to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Roadmap To Prevent, Data Breach Attacks, Comprehensive Risk Assessment, Implement Data Encryption, Enforce Access Controls, using this template. Grab it now to reap its full benefits.
-
 Data Breach Prevention Security Software To Protect Business From Data Breach
Data Breach Prevention Security Software To Protect Business From Data BreachThe purpose of this slide is to highlight the available security tools to stay safe from data breaches. The popular security software are access control solutions, Security Information And Event Management SIEM tools, and antivirus software. Increase audience engagement and knowledge by dispensing information using Data Breach Prevention Security Software To Protect Business From Data Breach. This template helps you present information on three stages. You can also present information on Security Information And Event Management, Amends Permissions As Needed, Security Software To Protect Business using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Breach Prevention Steps For Developing A Data Breach Response Plan
Data Breach Prevention Steps For Developing A Data Breach Response PlanThis slide demonstrates the working of the data breach response plan. The steps involved in developing a response plan are preplanning exercises, define response teams and members, create a contact list, create a communication plan and perform incident response. Introducing Data Breach Prevention Steps For Developing A Data Breach Response Plan to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Preplanning Exercises, Perform Incident Response, Communications Plan, using this template. Grab it now to reap its full benefits.
-
 Data Breach Prevention Strategies For Employees Data Breach Prevention And Mitigation
Data Breach Prevention Strategies For Employees Data Breach Prevention And MitigationThis slide highlights the data breach mitigation measures for workers. These strategies include maintain a record of banking receipts, do not believe everything, be mindful of sharing anything on social media, secure all devices, protect individual accounts, etc. Deliver an outstanding presentation on the topic using this Data Breach Prevention Strategies For Employees Data Breach Prevention And Mitigation. Dispense information and present a thorough explanation of Data Breach Mitigation Measures, Banking Receipts, Social Media, Secure All Devices, Protect Individual Accounts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention Strategies For Enterprises Data Breach Prevention And Mitigation
Data Breach Prevention Strategies For Enterprises Data Breach Prevention And MitigationThe purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Present the topic in a bit more detail with this Data Breach Prevention Strategies For Enterprises Data Breach Prevention And Mitigation. Use it as a tool for discussion and navigation on Network Security, Data Loss Prevention, Regularly Perform Patching Activities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Prevention Strategies For Users Data Breach Prevention And Mitigation
Data Breach Prevention Strategies For Users Data Breach Prevention And MitigationThis slide represents the strategies to protect users from data breaches. These include use unique passwords, two-factor authentication, only submit sensitive data on HTTPS websites, software and hardware updates, encrypt hard drives, etc. Deliver an outstanding presentation on the topic using this Data Breach Prevention Strategies For Users Data Breach Prevention And Mitigation. Dispense information and present a thorough explanation of Unusual Email Attachments, Maintain Software And Hardware, Several Online Services using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention Timeline To Implement Data Breach Response Plan
Data Breach Prevention Timeline To Implement Data Breach Response PlanThis slide shows the timeline for implementing data breach response plan. The key steps include access the impact of data breach, secure operations, review network segmentation, notify affected parties. Increase audience engagement and knowledge by dispensing information using Data Breach Prevention Timeline To Implement Data Breach Response Plan. This template helps you present information on five stages. You can also present information on Secure Operations, Consult With Legal Counsel, Communicate Transparently using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
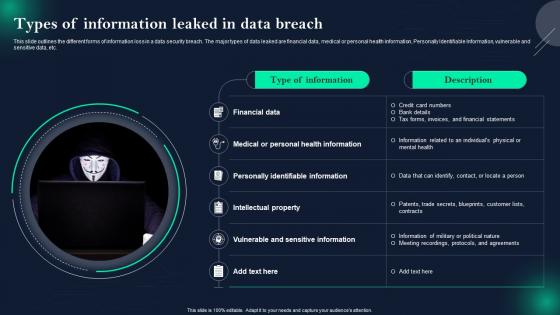 Data Breach Prevention Types Of Information Leaked In Data Breach
Data Breach Prevention Types Of Information Leaked In Data BreachThis slide outlines the different forms of information loss in a data security breach. The major types of data leaked are financial data, medical or personal health information, Personally Identifiable Information, vulnerable and sensitive data, etc. Introducing Data Breach Prevention Types Of Information Leaked In Data Breach to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Financial Data, Intellectual Property, Vulnerable And Sensitive Information, Personally Identifiable Information, using this template. Grab it now to reap its full benefits.
-
 Data Breach Prevention Vulnerabilities Targeted In Data Breach Attacks
Data Breach Prevention Vulnerabilities Targeted In Data Breach AttacksThe purpose of this slide is to discuss the most vulnerable target points of data breach attacks. The significant vulnerabilities include weak credentials, stolen information, compromised assets, payment card fraud, third-party access, mobile devices, etc. Increase audience engagement and knowledge by dispensing information using Data Breach Prevention Vulnerabilities Targeted In Data Breach Attacks. This template helps you present information on five stages. You can also present information on Payment Card Fraud, Mobile Devices, Weak Credentials, Compromised Assets, Data Breach Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Breach Prevention Working Steps Of Data Breach Attack Cycle
Data Breach Prevention Working Steps Of Data Breach Attack CycleThis slide explains the phases of the data breach attack cycle to gain unauthorized access to sensitive information. The steps involved are reconnaissance, intrusion and presence, lateral migration, using data for personal benefits, demanding a ransom, etc. Introducing Data Breach Prevention Working Steps Of Data Breach Attack Cycle to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reconnaissance, Intrusion And Presence, Lateral Migration, Exfiltration , using this template. Grab it now to reap its full benefits.
-
 Data Breach Response Plan Secure Operations Data Breach Prevention And Mitigation
Data Breach Response Plan Secure Operations Data Breach Prevention And MitigationThis slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. Present the topic in a bit more detail with this Data Breach Response Plan Secure Operations Data Breach Prevention And Mitigation. Use it as a tool for discussion and navigation on Assemble Expert Team, Consult With Legal Counsel, Secure Physical Areas. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons Slide For Data Breach Prevention And Mitigation Strategies For Businesses
Icons Slide For Data Breach Prevention And Mitigation Strategies For BusinessesPresenting our well crafted Icons Slide For Data Breach Prevention And Mitigation Strategies For Businesses set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly.
-
 Table Of Contents For Data Breach Prevention And Mitigation Strategies For Businesses
Table Of Contents For Data Breach Prevention And Mitigation Strategies For BusinessesIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Data Breach Prevention And Mitigation Strategies For Businesses. This template helps you present information on ten stages. You can also present information on Data Breach Prevention Tools, Data Breach Response Plan, Prevention And Mitigation, Training And Budget using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icon For Investigation Of Data Breach With Digital Forensic
Icon For Investigation Of Data Breach With Digital ForensicIntroducing our Icon For Investigation Of Data Breach With Digital Forensic set of slides. The topics discussed in these slides are Investigation Data, Breach With Digital Forensic. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
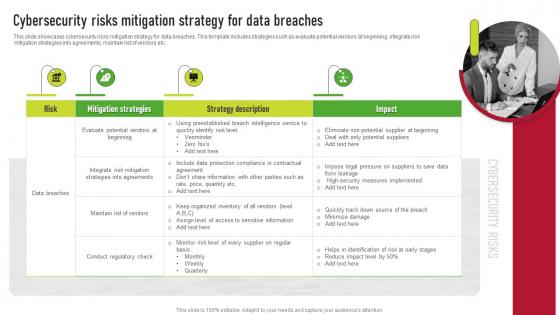 Cybersecurity Risks Mitigation Strategy For Data Breaches Supplier Risk Management
Cybersecurity Risks Mitigation Strategy For Data Breaches Supplier Risk ManagementThis slide showcases cybersecurity risks mitigation strategy for data breaches. This template includes strategies such as evaluate potential vendors at beginning, integrate risk mitigation strategies into agreements, maintain list of vendors etc. Introducing Cybersecurity Risks Mitigation Strategy For Data Breaches Supplier Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Mitigation Strategies, Strategy Description, Risk, using this template. Grab it now to reap its full benefits.
-
 Casepoint Data Breach In Powerpoint And Google Slides Cpb
Casepoint Data Breach In Powerpoint And Google Slides CpbPresenting Casepoint Data Breach In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Casepoint Data Breach. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 K81 Data Breach Prevention And Mitigation Strategies For Businesses For Table Of Contents
K81 Data Breach Prevention And Mitigation Strategies For Businesses For Table Of ContentsIntroducing K81 Data Breach Prevention And Mitigation Strategies For Businesses For Table Of Contents to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Data Breach Prevention, Mitigation Strategies For Businesses, Data Loss Prevention Tools, using this template. Grab it now to reap its full benefits.
-
 Key Components Of Data Security Breach Management Plan
Key Components Of Data Security Breach Management PlanThis slide showcases the critical components of a business security breach management plan. This slide aims to help the business effectively manage a data security breach to prevent financial loss, market share loss, or reputational damage.Introducing our premium set of slides with Key Components Of Data Security Breach Management Plan. Ellicudate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Prevent Identity, Credit Report Monitoring, Review Security Measures. So download instantly and tailor it with your information.
-
 Prevent Cyber Security Breaches In Powerpoint And Google Slides Cpb
Prevent Cyber Security Breaches In Powerpoint And Google Slides CpbPresenting Prevent Cyber Security Breaches In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Prevent Cyber Security Breaches. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Healthcare Cybersecurity Action Plan For Data Breach
Healthcare Cybersecurity Action Plan For Data BreachThis slide presents healthcare cybersecurity action plan for preventing or containing data breach, helpful in managing emergent situations. It includes steps such as to contain, evaluate, notify and review that help to handle unwanted circumstances along with guidelines for healthcare department. Introducing our Healthcare Cybersecurity Action Plan For Data Breach set of slides. The topics discussed in these slides are Contain, Evaluate, Notify. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Healthcare Cybersecurity Plan Icon For Data Breach
Healthcare Cybersecurity Plan Icon For Data BreachIntroducing our premium set of slides with Healthcare Cybersecurity Plan Icon For Data Breach. Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Healthcare Cybersecurity Plan, Icon For Data Breach. So download instantly and tailor it with your information.
-
 Potential Cyberattack Sources To Breach Mobile Devices E Wallets As Emerging Payment Method Fin SS V
Potential Cyberattack Sources To Breach Mobile Devices E Wallets As Emerging Payment Method Fin SS VThis slide shows diagram which can be used to understand the potential sources of cyberattacks used by hackers to get through users mobile devices. It is further categorized in four parts which are via browser, system, phone or SMS or applications. Increase audience engagement and knowledge by dispensing information using Potential Cyberattack Sources To Breach Mobile Devices E Wallets As Emerging Payment Method Fin SS V. This template helps you present information on four stages. You can also present information on Potential,Cyberattack,Sources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategies To Investigate Data Theft And Breaches
Strategies To Investigate Data Theft And BreachesThis slide covers the five techniques used to investigate data theft. The purpose of this template is to provide a high level overview of these techniques and the resources required to conduct them. It includes Stochastic forensics, digital artifact analysis, lag analysis, network traffic analysis, and endpoint analysis. Introducing our Strategies To Investigate Data Theft And Breaches set of slides. The topics discussed in these slides are Analysis, Digital, Endpoint. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Credit Karma Data Breach In Powerpoint And Google Slides Cpb
Credit Karma Data Breach In Powerpoint And Google Slides CpbPresenting Credit Karma Data Breach In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Credit Karma Data Breach. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Agenda Improving IoT Device Cybersecurity To Prevent Data Breaches IoT SS
Agenda Improving IoT Device Cybersecurity To Prevent Data Breaches IoT SSIntroducing Agenda Improving IoT Device Cybersecurity To Prevent Data Breaches IoT SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Provide, Business, Common, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Improving IoT Device Cybersecurity To Prevent Data Breaches IoT SS
Icons Slide Improving IoT Device Cybersecurity To Prevent Data Breaches IoT SSIntroducing our well researched set of slides titled Icons Slide Improving IoT Device Cybersecurity To Prevent Data Breaches IoT SS. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Improving IoT Device Cybersecurity To Prevent Data Breaches Table Of Contents IoT SS
Improving IoT Device Cybersecurity To Prevent Data Breaches Table Of Contents IoT SSIntroducing Improving IoT Device Cybersecurity To Prevent Data Breaches Table Of Contents IoT SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on General, Strategies, Security, using this template. Grab it now to reap its full benefits.
-
 Obligations Under GDPR Project Plan In Case Of Data Breach
Obligations Under GDPR Project Plan In Case Of Data BreachThe purpose of this slide is to showcase actions that take place in case of security breach in GDPR. It includes various stages such as data control, data security, right to erasure, risk mitigation and due diligence and breach notification. Introducing our premium set of slides with Obligations Under GDPR Project Plan In Case Of Data Breach. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Control, Security, Notification. So download instantly and tailor it with your information.
-
 Data Breaches Cyber Security In Powerpoint And Google Slides Cpb
Data Breaches Cyber Security In Powerpoint And Google Slides CpbPresenting our Data Breaches Cyber Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Data Breaches Cyber Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Security Breach Access Control In Powerpoint And Google Slides Cpb
Security Breach Access Control In Powerpoint And Google Slides CpbPresenting our Security Breach Access Control In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Security Breach Access Control This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 NEO Banks For Digital Funds Potential Cyberattack Sources To Breach Mobile Devices Fin SS V
NEO Banks For Digital Funds Potential Cyberattack Sources To Breach Mobile Devices Fin SS VThis slide shows diagram which can be used to understand the potential sources of cyberattacks used by hackers to get through users mobile devices. It is further categorized in four parts which are via browser, system, phone or SMS or applications. Increase audience engagement and knowledge by dispensing information using NEO Banks For Digital Funds Potential Cyberattack Sources To Breach Mobile Devices Fin SS V. This template helps you present information on four stages. You can also present information on Improper SSL Validation, Config Manipulation, Dynamic Runtime Injection, Unintended Permissions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Breach Investigations Report In Powerpoint And Google Slides Cpb
Data Breach Investigations Report In Powerpoint And Google Slides CpbPresenting our Data Breach Investigations Report In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Data Breach Investigations Report This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Best Practices To Ensure Efficient Data Breach Management
Best Practices To Ensure Efficient Data Breach ManagementThis slide depicts the key strategies to be utilized in order to effectively manage data breaches. The purpose of this template is to help the business efficiently identify and control data breach impact in order to reduce losses. It includes practices such as preparation, data access security, etc. Presenting our set of slides with Best Practices To Ensure Efficient Data Breach Management. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify Employees With Access, Ensure All Employees, Conduct Mock Data Breaches.
-
 Best Practices To Implement Data Breach Management Plan
Best Practices To Implement Data Breach Management PlanThis slide showcases the key practices to execute data breach management plan. The purpose of this template is to help the business utilize suitable practices in order to improve its performance. It includes practices such as securing network operations, secure network operations, etc. Introducing our premium set of slides with Best Practices To Implement Data Breach Management Plan. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Secure Network Operations, Secure Network Operations, Notify Appropriate Stakeholders. So download instantly and tailor it with your information.
-
 Challenges To Effective Data Breach Management
Challenges To Effective Data Breach ManagementThis slide showcases the difficulties faced during effective data breach management. The purpose of this slide is to help the business overcome these challenges through the use of resolution strategies given below. It includes challenges such as lack of immediate detection, inadequate incident response plan, etc. Introducing our Challenges To Effective Data Breach Management set of slides. The topics discussed in these slides are Lack Of Immediate Detection, Inadequate Incident Response Plan, Insufficient Employee Training. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Checklist To Implement Data Breach Security Response Plan
Checklist To Implement Data Breach Security Response PlanThis slide depicts the checklist to execute response plans during data security breaches. The purpose of this checklist is to help the business ensure all suitable actions are implemented in order to prevent data leaks. It includes elements such as activity status, person responsible, etc. Presenting our well structured Checklist To Implement Data Breach Security Response Plan. The topics discussed in this slide are Isolate Affected Systems, Notify Appropriate Stakeholders, Identify The Nature. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Critical Elements Of Data Breach Management And Response Plan
Critical Elements Of Data Breach Management And Response PlanThis slide highlights the critical components of company data breach management and response plan. The purpose of this slide is to help the business ensure all elements are successfully implemented in order to manage and contain damage. Presenting our set of slides with Critical Elements Of Data Breach Management And Response Plan. This exhibits information on nine stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Incident Response Team Formulation, Identify Occurrence Of Incident, Notify Relevant Authorities .
-
 Data Breach And Cybersecurity Management Framework
Data Breach And Cybersecurity Management FrameworkThis slide showcases the data breach and cybersecurity management framework. The purpose of this slide is to help ensure the company implements suitable programs in order to identify, manage and contain data breach impact. Introducing our Data Breach And Cybersecurity Management Framework set of slides. The topics discussed in these slides are Personal Cybersecurity, Environmental Security, Execution Of Risk Management . This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Breach Management And Recovery Icon
Data Breach Management And Recovery IconIntroducing our premium set of slides with Data Breach Management And Recovery Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Breach, Management, Recovery Icon. So download instantly and tailor it with your information.
-
 Data Breach Management Process Framework
Data Breach Management Process FrameworkThis slide depicts the data breach management procedure architecture. The purpose of this slide is to help the business utilize the following framework in order to effectively manage its data breach and initiate recovery plans. It includes elements such as evaluation of risk profile, management of security incident, etc. Introducing our Data Breach Management Process Framework set of slides. The topics discussed in these slides are Data Breach Management, Evaluation Of Risk Profile, Evaluation Of Resolution Strategies. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Breach Management Software Comparative Analysis
Data Breach Management Software Comparative AnalysisThis slide depicts the data breach management software comparison. The purpose of this slide is to help the business make a well informed purchase decision through the use of following comparative analysis. It includes comparison on the basis of industries, ratings, etc. Presenting our well structured Data Breach Management Software Comparative Analysis. The topics discussed in this slide are Hospital And Healthcare, Non Profit Organization, Utilizes Privacy Framework. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Data Flow Map For Effective Management Of Enterprise Data Breach
Data Flow Map For Effective Management Of Enterprise Data BreachThis slide depicts the information flow map to manage companys data breach incident. The purpose of this slide is to help the business ensure information is efficiently conveyed through the use of following map. Presenting our set of slides with Data Flow Map For Effective Management Of Enterprise Data Breach. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Determine Business Impact, Notification Of Cybersecurity, Incident Recognition Through.
-
 Enterprise Data Breach Management Process
Enterprise Data Breach Management ProcessThis slide depicts the organizations data breach management procedure. The purpose of this template is to help the business ensure all steps are suitably implemented in order to minimize damage. It includes steps such as identification of breach, notification of senior authority, etc. Introducing our premium set of slides with Enterprise Data Breach Management Process. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Notify Relevant Authorities, Identify Company Preference, Determine Potential Data Breach. So download instantly and tailor it with your information.
-
 Icon For Data Breach Identification And Management
Icon For Data Breach Identification And ManagementPresenting our set of slides with Icon For Data Breach Identification And Management. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon, Data Breach, Identification And Management.
-
 Icon For Effective Data Breach Management
Icon For Effective Data Breach ManagementIntroducing our premium set of slides with Icon For Effective Data Breach Management. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon For Effective, Data Breach, Management. So download instantly and tailor it with your information.
-
 Key Statistics Related To Ineffective Data Breach Management
Key Statistics Related To Ineffective Data Breach ManagementThis slide depicts the key statistics associated with ineffective data breach management. The purpose of this slide is to help the business ensure it implements suitable practices in order to improve its data protection and security. Presenting our set of slides with Key Statistics Related To Ineffective Data Breach Management. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Company Networks And Data, Data Security Breach Occur, Data Breach And Cyberattacks.
-
 Phases Of Data Breach Management Plan
Phases Of Data Breach Management PlanThis slide depicts the multi phase data breach management plan. The purpose of this slide is to help the business ensure data breach is immediately identified and resolved. It includes phases such as confirming breach, understanding breach, determination data sensitivity, etc. Introducing our premium set of slides with Phases Of Data Breach Management Plan. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Determine Severity Of Data, Deploy Suitable Management, Identify Potential Vectors . So download instantly and tailor it with your information.
-
 Stages To Implement Data Breach Management Plan
Stages To Implement Data Breach Management PlanThis slide showcases the multiple stages of executing data breach management plan. The purpose of this slide is to help the business ensure data breach is successfully identified and contained through the use of stages such as preparation, prevention, tracking, etc. Presenting our set of slides with Stages To Implement Data Breach Management Plan. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Determine Cybersecurity Benchmarks, Develop Suitable Recovery Plans, Monitor And Record Data.
-
 Workflow During Data Breach Management
Workflow During Data Breach ManagementThis slide highlights the workflow observed during data breach management. The purpose of this slide is to help the business ensure in implementing of suitable processes in order to manage and contain data breach damage. It includes identification and containment of theft, regulatory assessment, etc. Introducing our premium set of slides with Workflow During Data Breach Management. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Communicate To Stakeholders, Regulatory Assessment, Investigate The Breach. So download instantly and tailor it with your information.
-
 Everything About Mobile Banking Potential Cyberattack Sources To Breach Mobile Devices Fin SS V
Everything About Mobile Banking Potential Cyberattack Sources To Breach Mobile Devices Fin SS VThis slide shows diagram which can be used to understand the potential sources of cyberattacks used by hackers to get through users mobile devices. It is further categorized in four parts which are via browser, system, phone or SMS or applications. Increase audience engagement and knowledge by dispensing information using Everything About Mobile Banking Potential Cyberattack Sources To Breach Mobile Devices Fin SS V. This template helps you present information on four stages. You can also present information on Sensitive Data Storage, Unintended Permissions, Escalated Privileges, Config Manipulation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





