Information Security Powerpoint Presentation Slides
Information security protects electronic devices such as computers, servers, mobile gadgets, data, electronic systems, and other networks from cyber-attacks. Check out our efficiently designed Information Security template. This information security PowerPoint presentation will be helpful to throw light on the current scenario of the organization, the requirement of information security in different sectors, and its work. In addition, computer security PPT contains the critical elements of information security, network risk identification and assessment, steps to mitigate those risks, benefits of information security, and automations role in information security. Further, this data security presentation comes with a checklist to implement information security in the organization, a 30 60 90 day plan to manage information security, and the budget to implement the same. The Information Security deck also showcases a roadmap to monitor information security and a timeline to implement information security in the organization. Lastly, this electronic information security PPT shows the effects of information security implementation on the organization and dashboard for threat tracking. Download it now.
You must be logged in to download this presentation.
 Impress your
Impress your audience
Editable
of Time
PowerPoint presentation slides
Deliver an informational PPT on various topics by using this Information Security Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds eye view of the topic. Encompassed with eighty one slides, designed using high quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
As the world moves on to a pace of life that becomes faster by the second, information becomes more and more valuable. For instance, when money and secret messages are to be passed on using codes that the internet generates, then it becomes imperative to protect and secure that information as well.
Information security, or InfoSec is the process of preventing information hazards to safeguard information. It comprises the elements of Confidentiality, Integrity, and Availability (CIA) of data.
- Confidentiality: Information security's confidentiality feature ensures that only authorized users can access data. Access controls, appropriate user authentication, and encryption are steps used to guarantee confidentiality.
- Integrity: Data must stay accurate, comprehensive, and reliable. This is known as information integrity. Digital signatures, access controls, and data validation are some of the methods used to guarantee integrity.
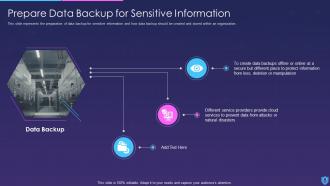
- Availability: Ensuring that information is available to authorized users when requested is referred to as availability. This entails safeguarding against interruptions such as natural catastrophes, cyberattacks, and system failures. Redundant systems, backups, disaster recovery plans, and denial-of-service (DoS) defense are some of the strategies used to guarantee availability.
Security risk is another important aspect of Information Security. To download security risk management templates, click here.
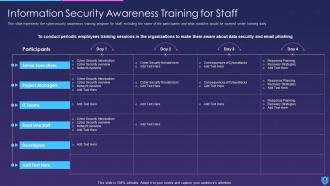
Information security also includes a range of procedures, tools, and guidelines designed to keep private data safe from prying eyes and prevent it from unauthorized and fraudulent use. This covers things like data security, endpoint security, network security, application security, and security awareness training for staff members.
You can also check here for half yearly information security transformation roadmap.
Information Security Slides
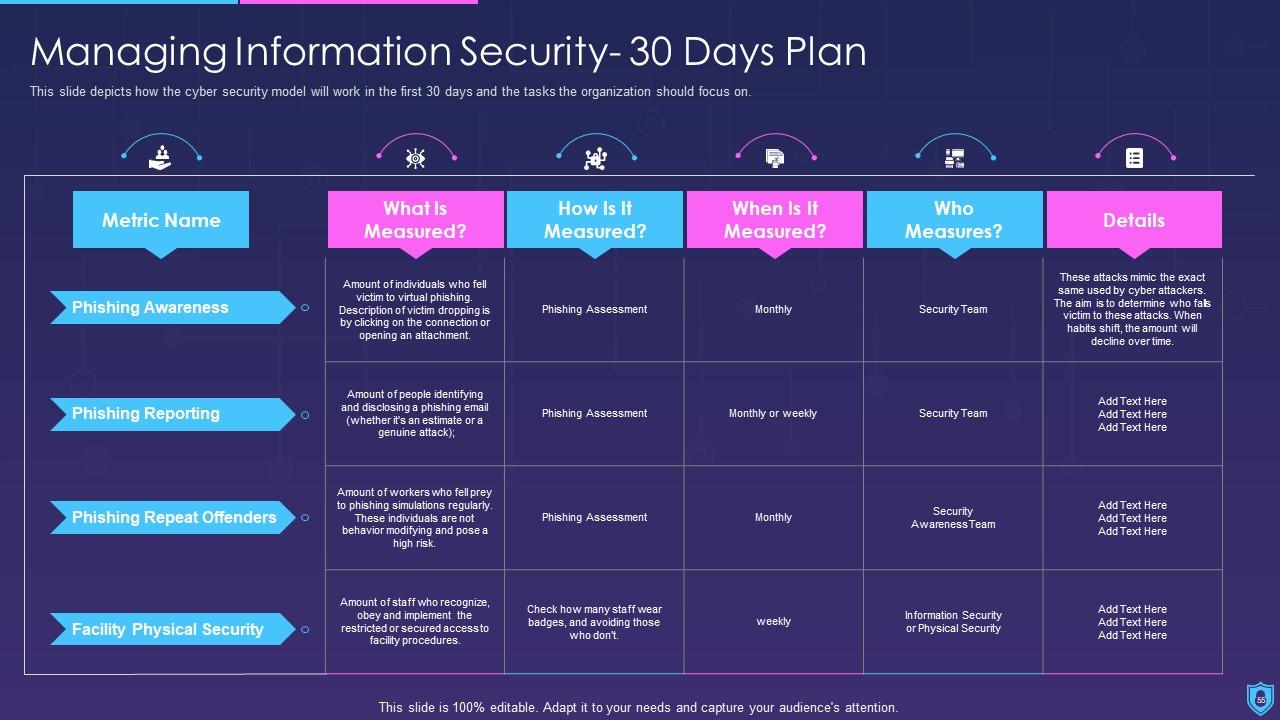
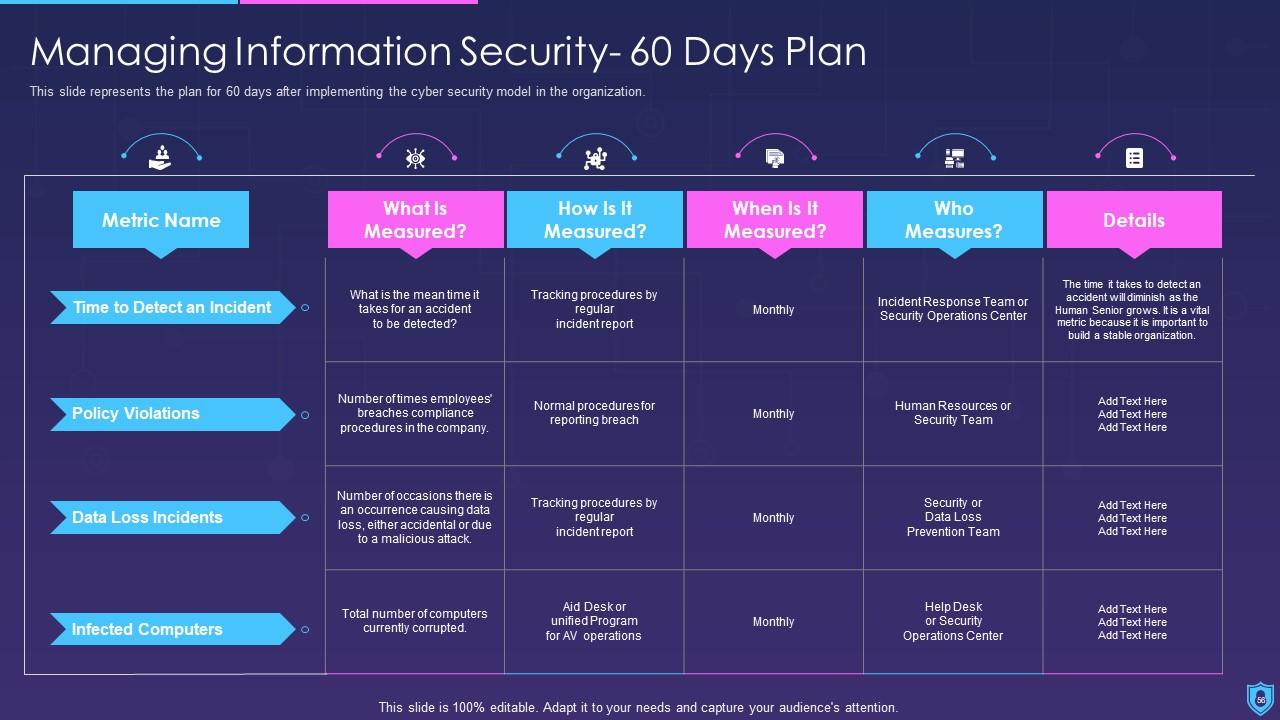
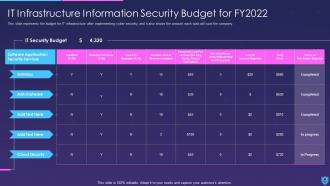
The information security presentation includes a budget for implementing information security, a 30 to 90-day strategy to manage information security, and a checklist for implementing information security in the organization.
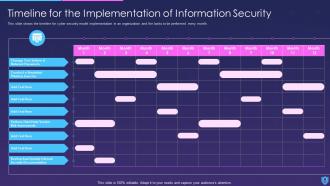
The information security deck, with 100% editable and customizable templates, also includes a schedule for implementing information security inside the company and a strategy for monitoring information security.
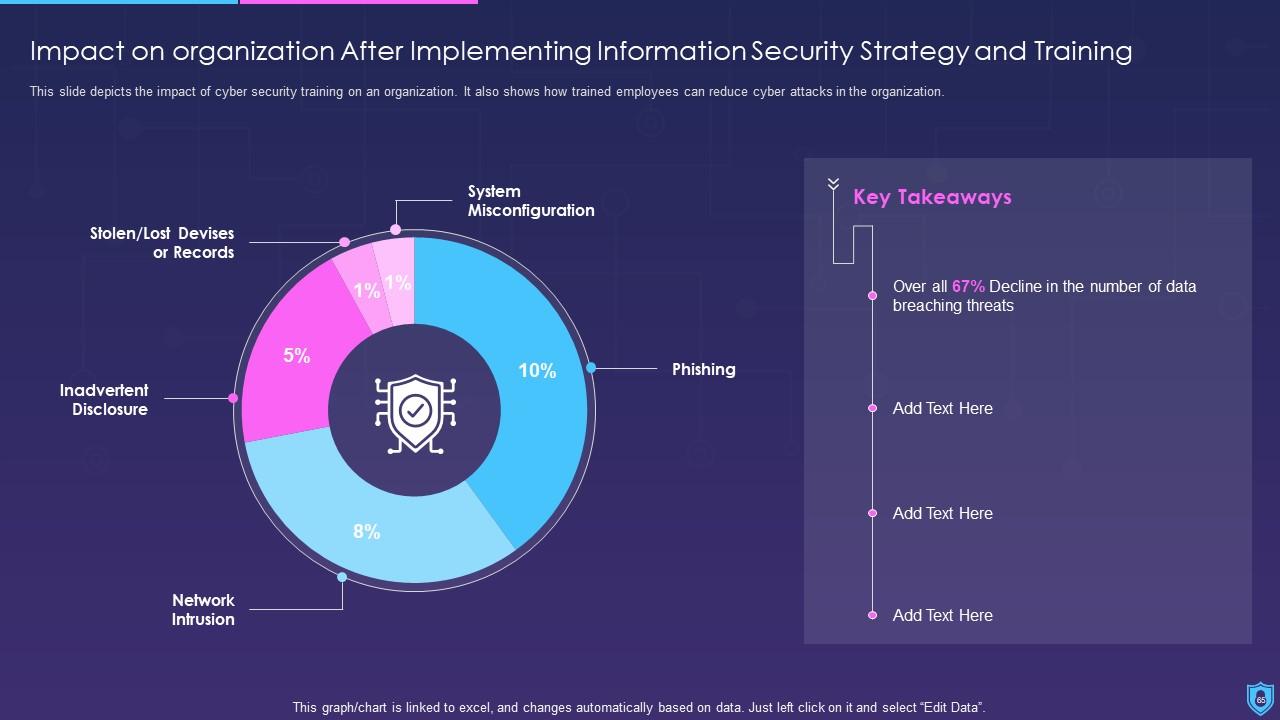
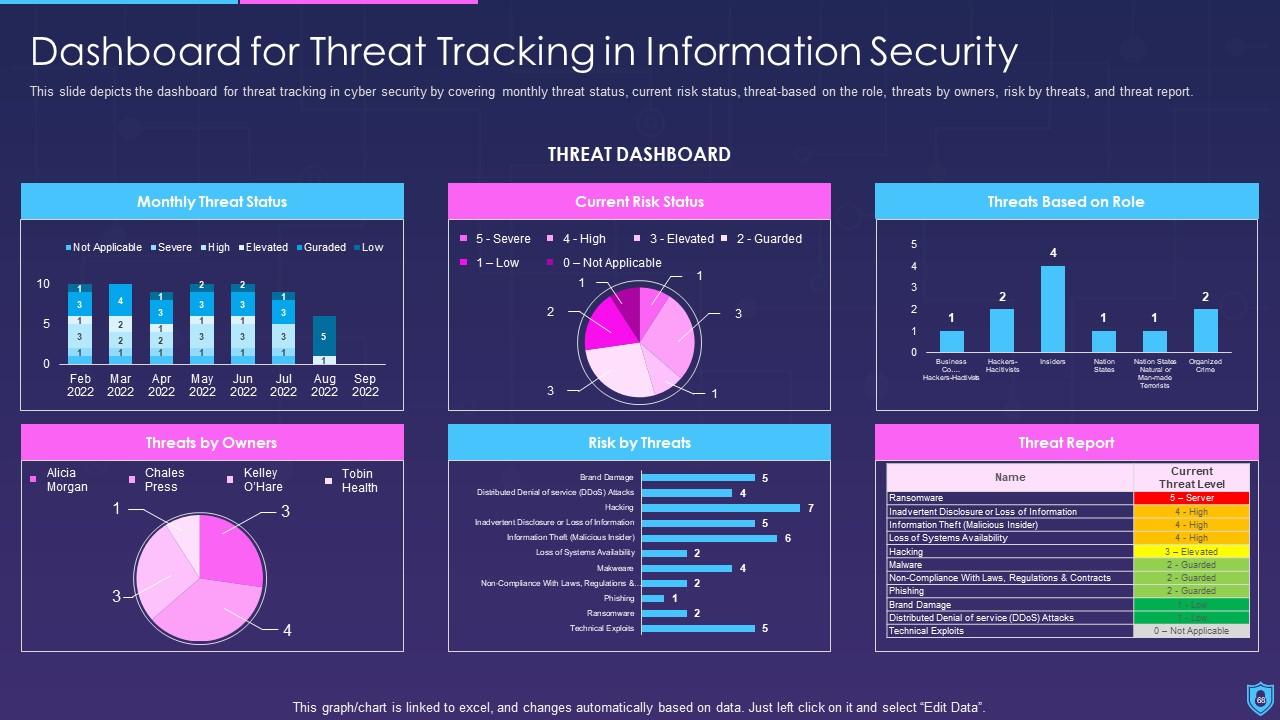
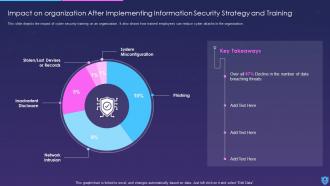
Finally, this information security PowerPoint displays the dashboard for threat tracking and the impact of information security deployment on the company.
Let’s explore!
Template 1 Information Security and its Working

Information security focuses on protecting information and information systems from multiple attacks or unauthorized assets. It includes tactics, tools, procedures, and methods designed to protect private data and guarantee its availability, confidentiality, and integrity. Information security entails both proactive steps to stop security breaches and reactive steps to identify, address, and recover from security incidents.
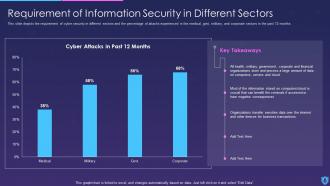
Template 2 Requirement of information security across sectors

Information security provides assistance from breaches in multiple sectors such as medical, government, military, and corporate sectors with a yearly report. It comprises detailed information on cyber attacks that took place over the past 12 months. In many industries, protecting sensitive data, maintaining privacy, adhering to regulations, reducing cyber risks, and upholding the confidence of stakeholders, and customers all depend on information security.
Template 3 Problems that Organizations Face PPT
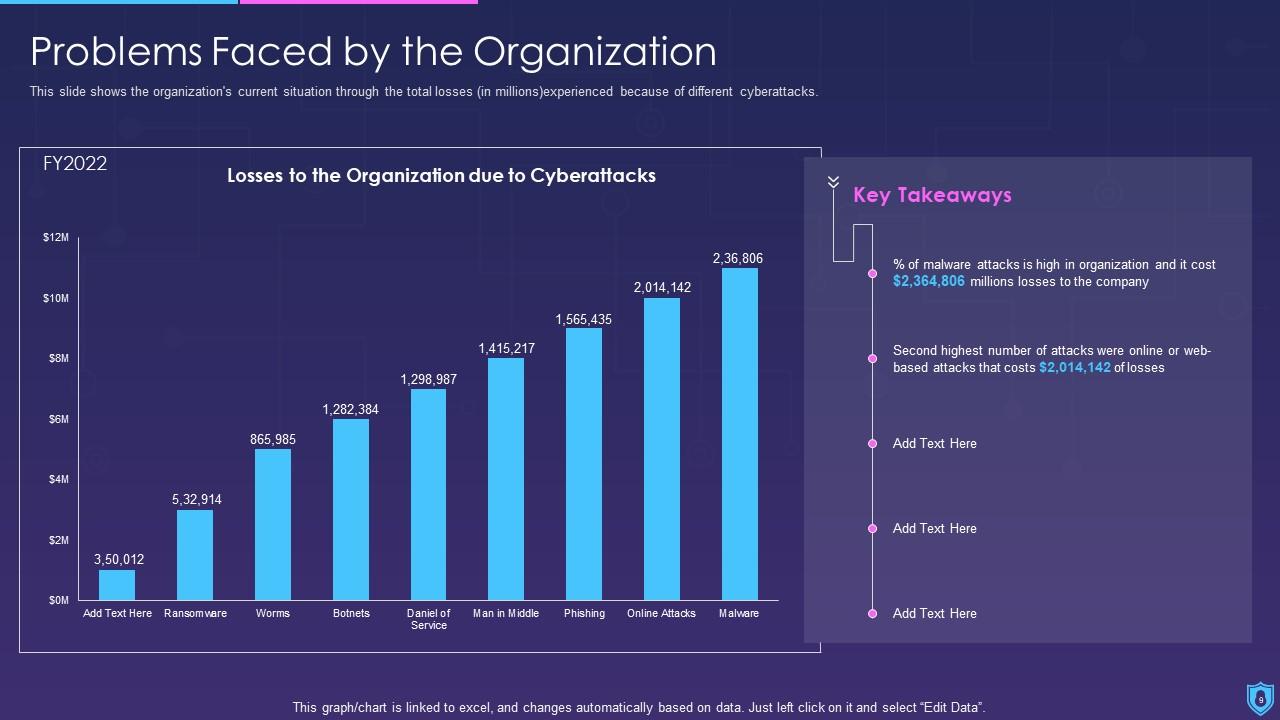
This PPT Slide depicts total current losses in millions that is expected to be hit by the help of cyberattacks. It contains information on attacks by phishing, malware, ransomware, worms, botnets, Denial of Service, man in the middle, online attacks, and some other types of attacks. It shows all the data in a graph format and the loss incurred in millions.
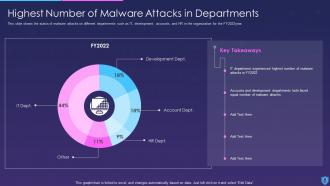
Template 4 Highest number of malware attacks in departments

This slide showcases departments that are affected by malware, such as IT, development, accounts, and HR in your very own organization and covers the data of a full year by dividing the shares of each department that got affected in the form of a pie chart. In almost all cases, the IT department is the most hit by the dangerous malware attacks.
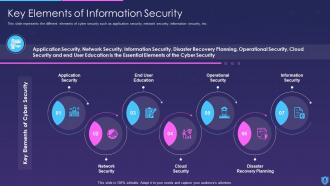
Template 5 Key Elements of Information Security
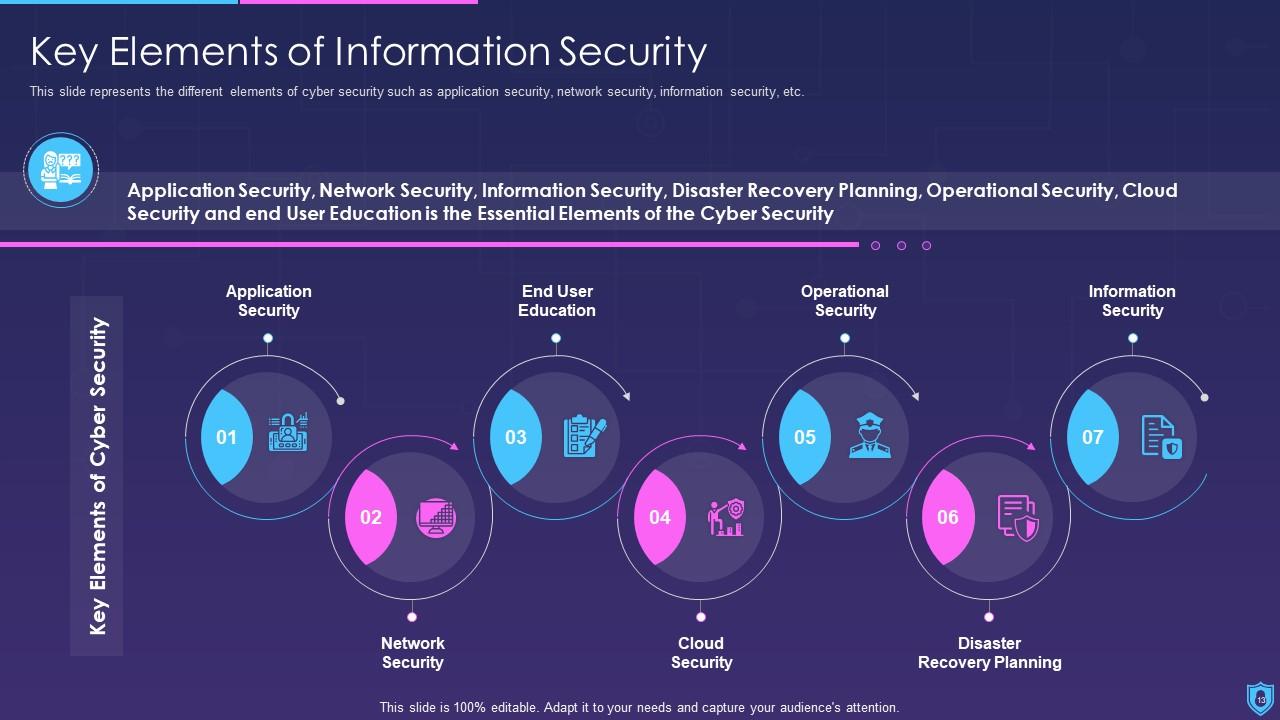
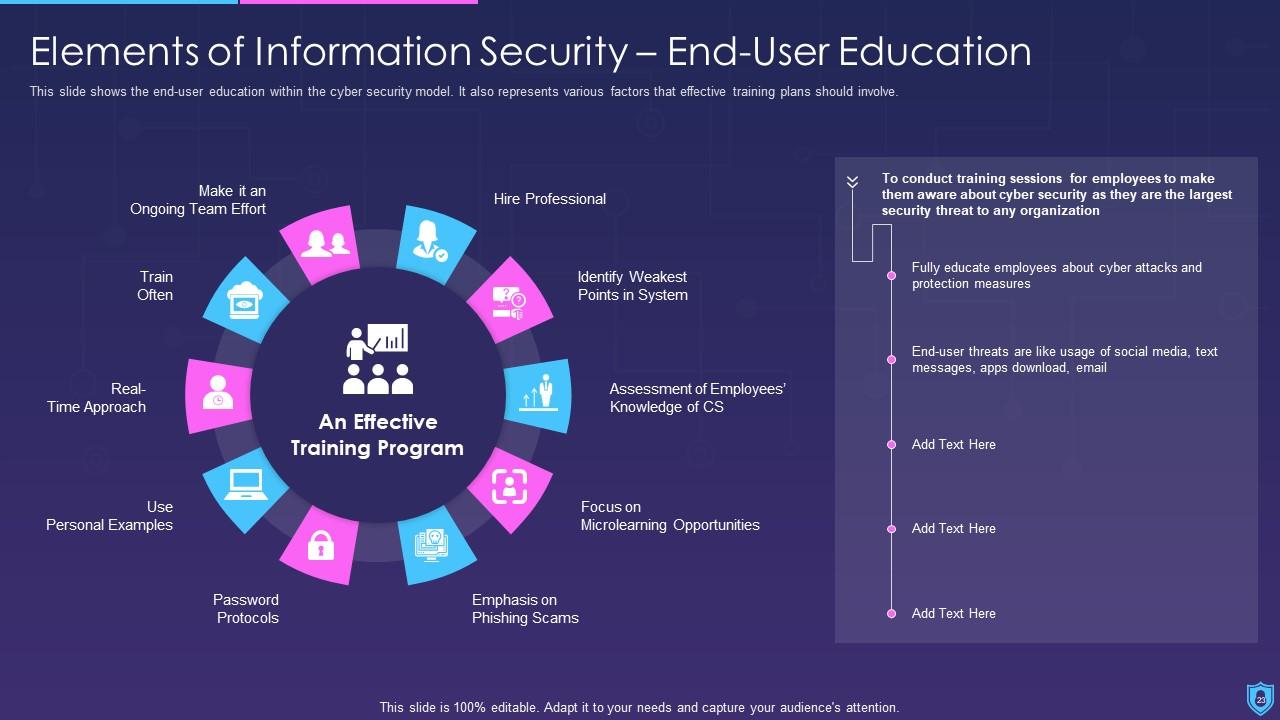
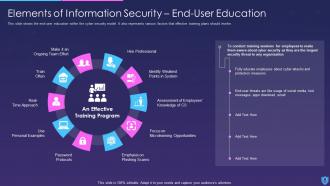
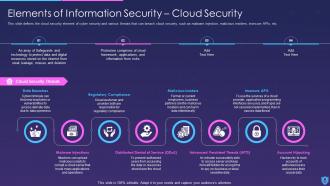
This slide depicts elements, such as application, security, end-user education, cloud, operational, disaster recovery planning, and information security to ensure information stays protected. These are considered as the main essential principles that are used for effective security on any site on the web, even if it is an independent business working on a single site, or a large multinational company that has locations.
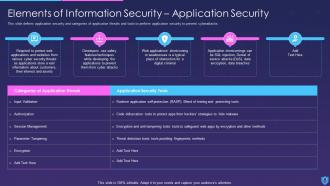
Template 6 Elements of Information Security - Application Security

This slide helps in understanding application security, and categories of application threats and also tells us about tools widely used to perform application security that helps in preventing cyber attacks. The types of application threats are - Input validation, authorization, session management, parameter tampering, and encryption. Also, the application security tools help in adding and developing testing security features within multiple applications to prevent security issues. The tools that can be used are - Runtime application self-protection or RASP, as it is a blend of both testing and protecting tools. The other tool is Code obfuscation, it is a tool to protect different apps from hackers' strategies and easily hides malware. Next is encryption and anti-tampering tools that safeguard apps by adding encryption methods. The last tool is the threat detection tool that provides additional security features by fingerprint methods.
Template 7 Elements of Information Security

This slide focuses on the methodology to prevent unauthorized access, usage, and modification of data, and also protects from damage to private user information such as - personal details, login credentials, social media details, network details, and private details. It follows the three-way principle of confidentiality, integrity, and availability.
Template 8 Main Principles of Information Security

This is an important slide that explains how to ensure that information remains confidential, consistent, and always available to designated authorized users. All details such as name, bank account, Date of birth, address, social media details remain confidential. Integrity ensures that the data is complete and accurate and protects the data from getting modified. It ensures that the data cannot be modified by unauthorized users. Data availability is also the most important principle as it checks that the data is available when it is needed to the authorized user.
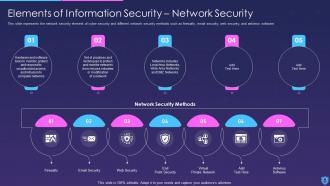
Template 9 Elements of Information security: Network Security

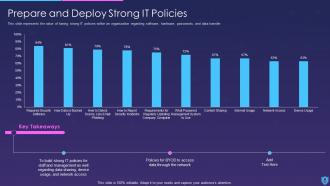
This slide explains how state-of-the-art hardware and software tools can be used to track, and protect unauthorized access to computer networks. This network security is effective for Local area networks LANs, Wide area networks WANs, and the DMZ networks. The types of network security methods discussed in the slide are - firewalls, email security, web security, endpoint security, antivirus software, and virtual private network (VPN). All these elements of network security are essential for protection against cyber security.
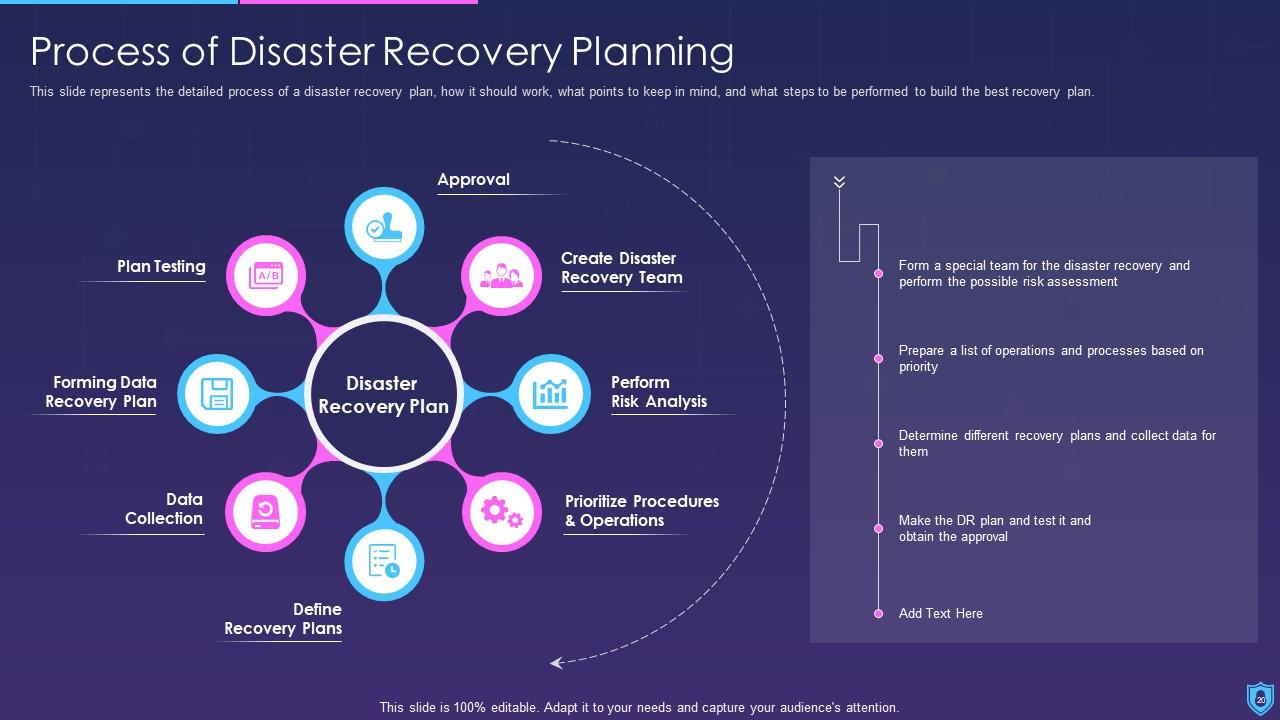
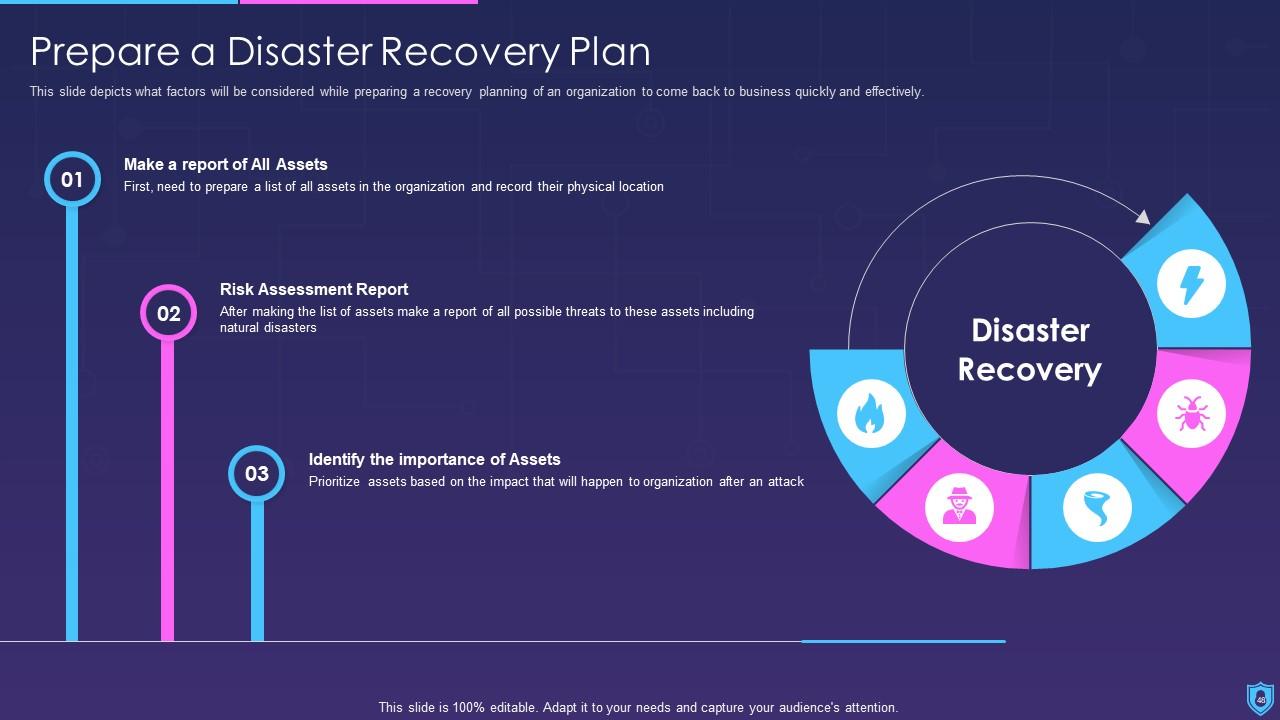
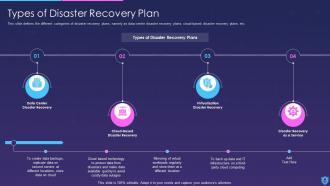
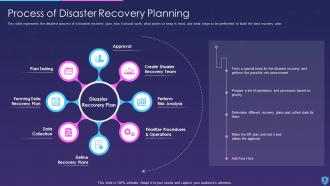
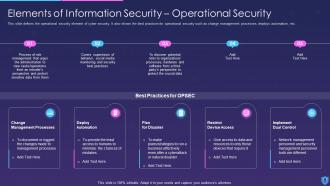
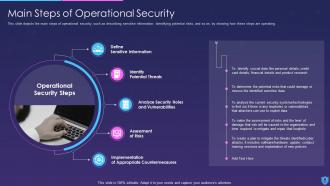
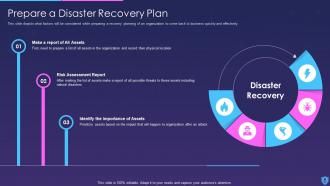
Template 10 Elements of Information Security: Disaster recovery planning

This slide lays disaster recovery planning towards cyber security and sheds light on strategies that an organization must adopt to recover from a natural disaster or a malicious attack. You can deploy fresh plans with time to keep the business in a running stage or resume quickly after a natural disaster. This slide allows you to introduce new tools that easily recover lost data and allows you to resume operations. While preparing the recovery strategies make sure to consider your financial budget, administration, resources and technology as it allows you to plan things in an effective manner.
Information security is a vast field that covers physical security, and data encryption, and ensures better network protection. Ideally, it is information assurance that protects this vital asset from threats, server failures, disasters, and from harmful malware. It protects your business from getting unauthorized access and saves all your data.
In this blog, we have covered information security and have covered aspects of it with the help of 10 slides that will assist you in protecting your servers and personal information from outside attacks.
With the growing digital age, you need to manage cyber risk. Click here for the Infosec program framework managing cyber risk in a digital age.
Information Security Powerpoint Presentation Slides with all 86 slides:
Use our Information Security Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
FAQs
Cybersecurity refers to the practice of protecting networks, devices, and data from unauthorized access, attack, theft, and damage. It helps to prevent data breaches by using various methods and techniques such as firewalls, antivirus software, encryption, multi-factor authentication, intrusion detection, and prevention systems, among others.
Cybersecurity is required in different sectors to protect the sensitive information and data stored in various devices and networks. It helps to prevent unauthorized access and attacks that can compromise the confidentiality, integrity, and availability of critical information.
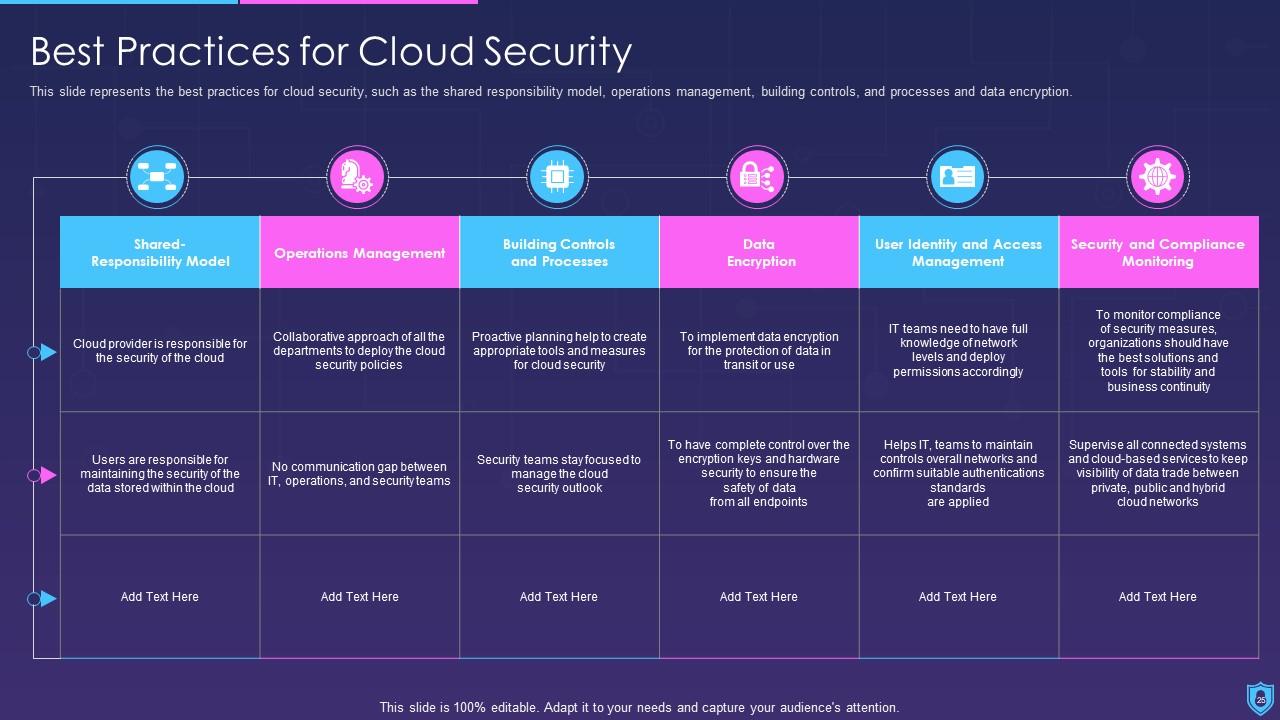
The different elements of cybersecurity include application security, network security, information security, disaster recovery planning, operational security, cloud security, and end-user education.
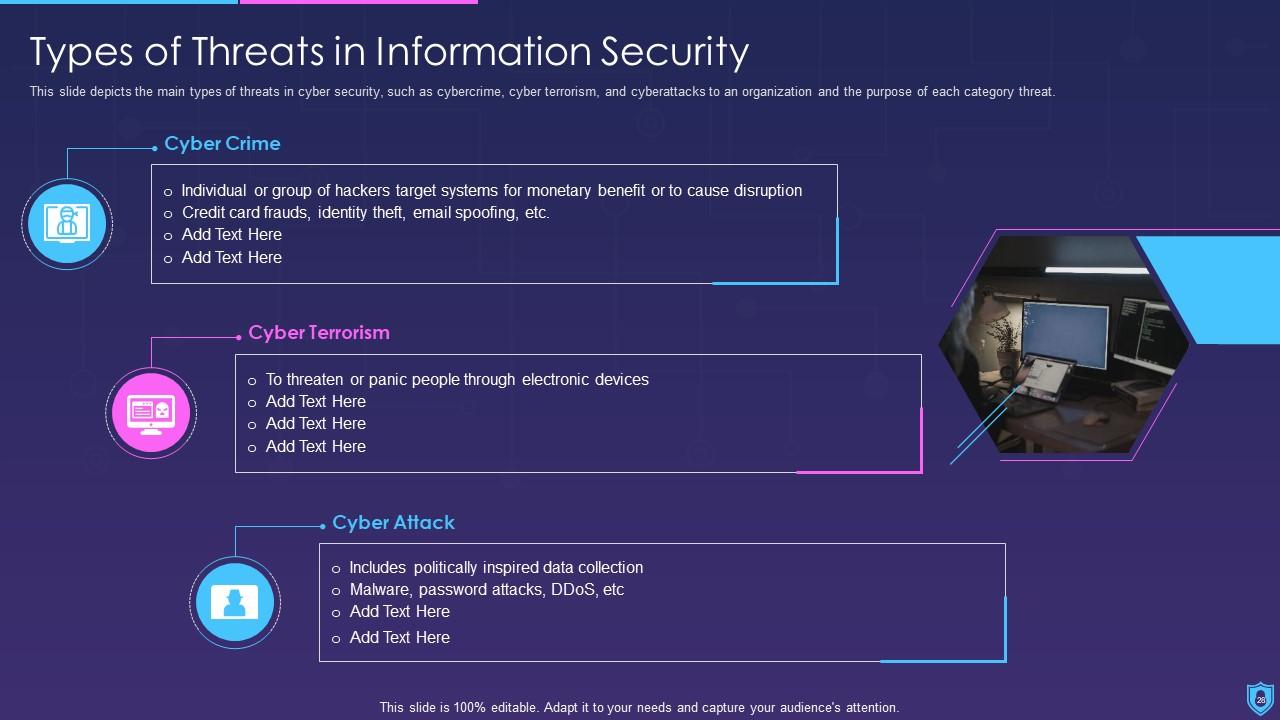
The main types of threats in data security include cybercrime, cyber terrorism, insider threats, phishing, malware, and ransomware.
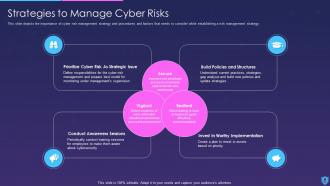
A cyber risk management strategy is important to identify, assess, and mitigate the potential risks and threats to an organization's critical data and information. It helps to develop policies and procedures to prevent and respond to cyber incidents and ensure business continuity.
-
SlideTeam makes creating presentations easy. Unlimited products, premium quality designs and affordable.
-
Very unique and reliable designs.