Powerpoint Templates and Google slides for Information Technology Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Information Technology Security Powerpoint Presentation Slides
Information Technology Security Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts,this Information Technology Security Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the eighty one slides are editable and modifiable,so feel free to adjust them to your business setting. The font,color,and other components also come in an editable format making this PPT design the best choice for your next presentation. So,download now.
-
 Enterprise Risk Management And Information Technology Security Complete Deck
Enterprise Risk Management And Information Technology Security Complete DeckDeliver an informational PPT on various topics by using this Enterprise Risk Management And Information Technology Security Complete Deck. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with fifty two slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
-
 Security Automation In Information Technology Powerpoint Presentation Slides
Security Automation In Information Technology Powerpoint Presentation SlidesThis complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of fourty two slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.
-
 Risk Management Maturity Model Information Security Data Technology Culture
Risk Management Maturity Model Information Security Data Technology CultureDeliver a credible and compelling presentation by deploying this Risk Management Maturity Model Information Security Data Technology Culture. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The twenty eight slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Risk Management Maturity Model Information Security Data Technology Culture PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Information Technology Security Powerpoint PPT Template Bundles
Information Technology Security Powerpoint PPT Template BundlesIntroduce your topic and host expert discussion sessions with this Information Technology Security Powerpoint PPT Template Bundles. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the twelve slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
-
 Information Technology Expenditure Summary Dashboard Creating Cyber Security Awareness
Information Technology Expenditure Summary Dashboard Creating Cyber Security AwarenessThe following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. Deliver an outstanding presentation on the topic using this Information Technology Expenditure Summary Dashboard Creating Cyber Security Awareness Dispense information and present a thorough explanation of Inadequate Security Guidelines, Inappropriate Privacy Policies, Insufficient Security Failure By Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats
Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. Deliver an outstanding presentation on the topic using this Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Cyber Security Budget Spent, It Costs And Revenue, Issue Status Summary using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Assessment Dashboard
Information Technology Security Assessment DashboardThis slide represents dashboard for information technology security assessment which includes elements such as intrusion attempts, mean resolve time, mean detect time, etc. Introducing our Information Technology Security Assessment Dashboard set of slides. The topics discussed in these slides are Intrusion Attempts, IT Security Rating, Phishing Test Success Rate. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information Technology Network Security Computing Illustration
Information Technology Network Security Computing IllustrationThis colourful PowerPoint icon is perfect for presentations on Information Technology topics. It features a laptop with a blue and green screen, a yellow and red processor, and a purple and orange hard drive. It is a great visual aid to help you explain complex IT concepts.
-
 Comparative Analysis Of Top Information Security Plan Tools
Comparative Analysis Of Top Information Security Plan ToolsThis slide mentions top 5 software comparison chart for information security plan to identify threat easily and manage risk. It involves comparison on basis of business size, features, free trial, price and ratings. Introducing our Comparative Analysis Of Top Information Security Plan Tools set of slides. The topics discussed in these slides are Rating, Business Size, Features This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use
Encryption Implementation Strategies Data Protection Technologies To Secure Information In UseThis slide compares different data in use protection methods, and their working and associated cost. These methods are IDM Identity and Access Management, RBAC Role Based Access and conditional access, IRM Information Rights Management, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use. Use it as a tool for discussion and navigation on Identity Management Tools, Digital Rights Protection, Data Protection Technologies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Technological Trends Used For Enhancing Information Security Management
Technological Trends Used For Enhancing Information Security ManagementThis slide represents various technologies that help organizations enhance information security management and reduce data loss incidents. It includes strategies such as user behavior analytics, cloud access security brokers, etc. Presenting our well structured Technological Trends Used For Enhancing Information Security Management. The topics discussed in this slide are Security Testing Devops, User Behavior Analytics, Cloud Access Security Brokers. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Core Principles To Secure Information Technology
Core Principles To Secure Information TechnologyThis slide showcases the core fundamental principles of information technology. Its aim is to secure system and improve transparent decision making. This slide includes collaborating secure system, transparent decision making, etc. Introducing our premium set of slides with Core Principles To Secure Information Technology. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Transparent Decision Making, Secure System, Collaboration. So download instantly and tailor it with your information.
-
 Impact Of Emerging Technologies On Information Security
Impact Of Emerging Technologies On Information SecurityThis slide highlights influence of technology on information security. The purpose of this slide is to assist IT teams in assessing and measuring various factors for driving success of security initiatives. It includes elements such as zero trust architecture, IoT security, etc.Introducing our Impact Of Emerging Technologies On Information Security set of slides. The topics discussed in these slides are Artificial Intelligence, Zero Trust Architecture, Iot Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparison Analysis Of Data Masking Tools For Information Security
Comparison Analysis Of Data Masking Tools For Information SecurityThis slide represents comparison analysis of data masking tools that assist companies to enhance their sensitive information security. It includes various tools such as K2View data masking, DATPROF data masking tool, Oracle data masking and subsetting, etc. Presenting our well structured Comparison Analysis Of Data Masking Tools For Information Security. The topics discussed in this slide are Virtualization, Synthetic Data Generation, Tokenization. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Organizational Information Technology Security Budget Analysis
Organizational Information Technology Security Budget AnalysisThis slide provides the budget analysis for development of organizational security by installation of new services. The various cost estimation parameters are new license required, subscription cost, purchase status, etc. Introducing our Organizational Information Technology Security Budget Analysis set of slides. The topics discussed in these slides are Revenue, Security Goal, IT Security Budget. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Information Technology List
Cyber Security Information Technology ListThis slide showcases list of cyber security data technology. The purpose of this template is to help businesses in maintaining confidentiality of information systems for building trust of customers in digital age. It includes elements such as firewalls, antivirus, etc. Presenting our set of slides with name Cyber Security Information Technology List. This exhibits information on Eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Firewalls, Intrusion Detection And Prevention Systems, Antivirus, Access Control Systems.
-
 Information Technology Network Security Icon
Information Technology Network Security IconIntroducing our premium set of slides with name Information Technology Network Security Icon. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Technology, Network Security. So download instantly and tailor it with your information.
-
 Strategic Information Technology Security Plan
Strategic Information Technology Security PlanThis slide represents strategic plan for information technology security which includes security types such as network security, internet security, endpoint security, etc. Introducing our premium set of slides with name Strategic Information Technology Security Plan. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Purpose, Person Responsible, Actions Required, Status. So download instantly and tailor it with your information.
-
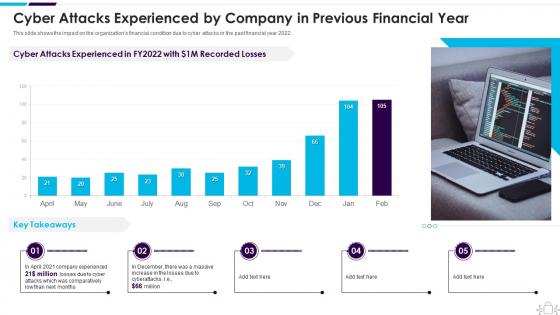 Cyber Attacks Experienced By Company In Previous Information Technology Security
Cyber Attacks Experienced By Company In Previous Information Technology SecurityThis slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2022. Present the topic in a bit more detail with this Cyber Attacks Experienced By Company In Previous Information Technology Security. Use it as a tool for discussion and navigation on Experienced, Previous, Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Compliance Dashboard Snapshot For Information Technology Security
Information Technology Security Compliance Dashboard Snapshot For Information Technology SecurityThis slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Present the topic in a bit more detail with this Information Technology Security Compliance Dashboard Snapshot For Information Technology Security. Use it as a tool for discussion and navigation on Dashboard, Information, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Dashboard Snapshot Threat Tracking Information Technology Security
Information Technology Security Dashboard Snapshot Threat Tracking Information Technology SecurityThis slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Present the topic in a bit more detail with this Information Technology Security Dashboard Threat Tracking Information Technology Security. Use it as a tool for discussion and navigation on Dashboard, Information, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Detail Impact Information Technology Reduce Organization
Information Technology Security Detail Impact Information Technology Reduce OrganizationThis slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Present the topic in a bit more detail with this Information Technology Security Detail Impact Information Technology Reduce Organization. Use it as a tool for discussion and navigation on Information, Technology, Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Highest Number Of Malware Attacks In Departments
Information Technology Security Highest Number Of Malware Attacks In DepartmentsThis slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2022 year. Present the topic in a bit more detail with this Information Technology Security Highest Number Of Malware Attacks In Departments. Use it as a tool for discussion and navigation on Department, Experienced, Malware. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Impact Organization After Implementing Strategy Training
Information Technology Security Impact Organization After Implementing Strategy TrainingThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Present the topic in a bit more detail with this Information Technology Security Impact Organization After Implementing Strategy Training. Use it as a tool for discussion and navigation on Organization, Implementing, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Prepare And Deploy Strong It Policies
Information Technology Security Prepare And Deploy Strong It PoliciesThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an outstanding presentation on the topic using this Information Technology Security Prepare And Deploy Strong It Policies. Dispense information and present a thorough explanation of Prepare And Deploy Strong IT Policies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Problems Faced By The Organization
Information Technology Security Problems Faced By The OrganizationThis slide shows the organizations current situation through the total losses in millions experienced because of different cyberattacks. Present the topic in a bit more detail with this Information Technology Security Problems Faced By The Organization. Use it as a tool for discussion and navigation on Problems Faced By The Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Requirement Of Information Technology Security In Different Sectors
Information Technology Security Requirement Of Information Technology Security In Different SectorsThis slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an outstanding presentation on the topic using this Information Technology Security Requirement Of Information Technology Security In Different Sectors. Dispense information and present a thorough explanation of Requirement, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Update And Installation Of Antivirus Software
Information Technology Security Update And Installation Of Antivirus SoftwareThis slide depicts the benefits of using antivirus software in the organization, different antivirus software available in the market, and their usage by a graph. Deliver an outstanding presentation on the topic using this Information Technology Security Update And Installation Of Antivirus Software. Dispense information and present a thorough explanation of Update And Installation Of Antivirus Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Dashboard With Incident And Threat Management
Information Technology Security Dashboard With Incident And Threat ManagementThis slide shows the dashboard of cyber security with incidents and threat management. It includes overall progress, risk identified , number of critical incidents, initiative , incident and threat management etc. Introducing our Information Technology Security Dashboard With Incident And Threat Management set of slides. The topics discussed in these slides are Threat Management, Incident Management, Critical Risks Identified. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Quarterly Comparison Of Information Technology Security Threats
Quarterly Comparison Of Information Technology Security ThreatsThis slide shows the four types of security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Introducing our Quarterly Comparison Of Information Technology Security Threats set of slides. The topics discussed in these slides are Quarterly Comparison, Information Technology, Security Threats. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 F652 Security Automation In Information Technology Security Automation Dashboard Highlighting Phishing
F652 Security Automation In Information Technology Security Automation Dashboard Highlighting PhishingThis slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Present the topic in a bit more detail with this F652 Security Automation In Information Technology Security Automation Dashboard Highlighting Phishing. Use it as a tool for discussion and navigation on Automation, Dashboard, Phishing Alerts. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation Dashboard Highlighting Resolved Events Security Automation In Information Technology
Security Automation Dashboard Highlighting Resolved Events Security Automation In Information TechnologyThis slide highlights the security automation dashboard which includes resolved events, mean dwell time, time and dollar saved, workload, events by status and top actions. Deliver an outstanding presentation on the topic using this Security Automation Dashboard Highlighting Resolved Events Security Automation In Information Technology. Dispense information and present a thorough explanation of Automation, Dashboard, Workload using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Automation In Information Technology Time To Fix Security Threat With Manual Testing
Security Automation In Information Technology Time To Fix Security Threat With Manual TestingThis slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Deliver an outstanding presentation on the topic using this Security Automation In Information Technology Time To Fix Security Threat With Manual Testing. Dispense information and present a thorough explanation of Security, Threat, Manual Testing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Automation In Information Technology Current State Of Security Automation With Projected Development
Security Automation In Information Technology Current State Of Security Automation With Projected DevelopmentThis slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. Deliver an outstanding presentation on the topic using this Security Automation In Information Technology Current State Of Security Automation With Projected Development. Dispense information and present a thorough explanation of Projected Development, Security Automation, Organizations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Generating Security Awareness Among Employees To Reduce
Information Technology Generating Security Awareness Among Employees To ReduceThe following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. Present the topic in a bit more detail with this Information Technology Generating Security Awareness Among Employees To Reduce Use it as a tool for discussion and navigation on Cyber Security, Budget Spent This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Electronic information security of employees devices
Electronic information security of employees devicesThis slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Introducing Electronic Information Security Of Employees Devices to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Peripheral Devices, Supervision And Prevent, Project, Data, using this template. Grab it now to reap its full benefits.
-
 Information security risk assessment and management tools
Information security risk assessment and management toolsMentioned slide highlights several information security risk management tools which can be used by organization. The multiple tools are automated questionnaires, security ratings and vulnerability assessment report. Introducing our premium set of slides with Information Security Risk Assessment And Management Tools. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Ratings, Automated Questionnaires, Vulnerability Assessment Report. So download instantly and tailor it with your information.
-
 Agenda For Information Technology Security
Agenda For Information Technology SecurityIntroducing Agenda For Information Technology Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Information, Technology, Cybersecurity, using this template. Grab it now to reap its full benefits.
-
 Elements Of Information Technology Security Application Security Information Technology Security
Elements Of Information Technology Security Application Security Information Technology SecurityThis slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. Increase audience engagement and knowledge by dispensing information using Elements Of Information Technology Security Application Security Information Technology Security. This template helps you present information on five stages. You can also present information on Session Management, Parameter Tampering, Authorization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Information Technology Security
Icons Slide For Information Technology SecurityIntroducing our well researched set of slides titled Icons Slide For Information Technology Security. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Implementation Of Strong Password Policy Information Technology Security
Implementation Of Strong Password Policy Information Technology SecurityThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Implementation Of Strong Password Policy Information Technology Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Americans, Implementation, Passwords, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security 60 Days Plan
Information Technology Security 60 Days PlanThis slide represents the plan for 60 days after implementing the cyber security model in the organization. Present the topic in a bit more detail with this Information Technology Security 60 Days Plan. Use it as a tool for discussion and navigation on Managing, Information, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Assessment Matrix Of Cyber Risks
Information Technology Security Assessment Matrix Of Cyber RisksThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an outstanding presentation on the topic using this Information Technology Security Assessment Matrix Of Cyber Risks. Dispense information and present a thorough explanation of Assessment Matrix Of Cyber Risks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Awareness Training Budget For Fy2022
Information Technology Security Awareness Training Budget For Fy2022This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Present the topic in a bit more detail with this Information Technology Security Awareness Training Budget For Fy2022. Use it as a tool for discussion and navigation on Employee Awareness Training Budget For FY2022. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
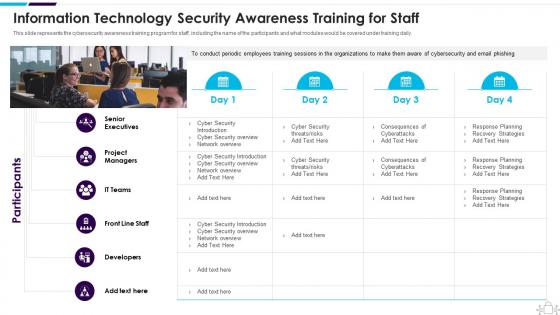 Information Technology Security Awareness Training For Staff
Information Technology Security Awareness Training For StaffThis slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver an outstanding presentation on the topic using this Information Technology Security Awareness Training For Staff. Dispense information and present a thorough explanation of Senior Executives, Project Managers, Developers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Best Practices For Cloud Security
Information Technology Security Best Practices For Cloud SecurityThis slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Present the topic in a bit more detail with this Information Technology Security Best Practices For Cloud Security. Use it as a tool for discussion and navigation on Operations, Management, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Common Methods Used Threaten Information Security
Information Technology Security Common Methods Used Threaten Information SecurityThis slide depicts the standard methods used to threaten cyber security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Introducing Information Technology Security Common Methods Used Threaten Information Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Daniel Of Service, Man In The Middle, SQL Injection , using this template. Grab it now to reap its full benefits.
-
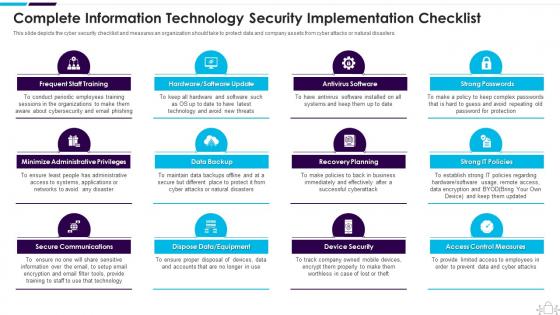 Information Technology Security Complete Information Security Implementation Checklist
Information Technology Security Complete Information Security Implementation ChecklistThis slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Introducing Information Technology Security Complete Information Security Implementation Checklist to increase your presentation threshold. Encompassed with twelve stages, this template is a great option to educate and entice your audience. Dispence information on Frequent Staff Training, Administrative Privileges, Data Backup, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Cyber Threat Landscape In Information Technology Security
Information Technology Security Cyber Threat Landscape In Information Technology SecurityThis slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver an outstanding presentation on the topic using this Information Technology Security Cyber Threat Landscape In Information Technology Security. Dispense information and present a thorough explanation of Landscape, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Data Backup For Sensitive Information
Information Technology Security Data Backup For Sensitive InformationThis slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Introducing Information Technology Security Data Backup For Sensitive Information to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Prepare Data Backup For Sensitive Information, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Define Access Control Measures For Employees
Information Technology Security Define Access Control Measures For EmployeesThis slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Increase audience engagement and knowledge by dispensing information using Information Technology Security Define Access Control Measures For Employees. This template helps you present information on four stages. You can also present information on Organization, Permissions, Responsibilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Dispose Data And Equipment Properly
Information Technology Security Dispose Data And Equipment ProperlyThis slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Introducing Information Technology Security Dispose Data And Equipment Properly to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Dispose Data And Equipment Properly, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Elements Information Technology Security Cloud Security
Information Technology Security Elements Information Technology Security Cloud SecurityThis slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Introducing Information Technology Security Elements Information Technology Security Cloud Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Elements, Information, Technology, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Employees Devices
Information Technology Security Employees DevicesThis slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Increase audience engagement and knowledge by dispensing information using Information Technology Security Employees Devices. This template helps you present information on four stages. You can also present information on Security Of Employees Devices using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security End User Education Information Technology Security
Information Technology Security End User Education Information Technology SecurityThis slide shows the end user education within the cyber security model. It also represents various factors that effective training plans should involve. Introducing Information Technology Security End User Education Information Technology Security to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Assessment, Microlearning, Opportunities, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Hardware And Software Update In Company
Information Technology Security Hardware And Software Update In CompanyThis slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Increase audience engagement and knowledge by dispensing information using Information Technology Security Hardware And Software Update In Company. This template helps you present information on three stages. You can also present information on Hardware And Software Update In Company using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security How Is Automation Used In Information Technology Security
Information Technology Security How Is Automation Used In Information Technology SecurityThis slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Introducing Information Technology Security How Is Automation Used In Information Technology Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Threat Detection, Threat Response, Human Augmentation, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Information Technology Security Elements
Information Technology Security Information Technology Security ElementsThis slide represents the different elements of cyber security such as application security, network security, information security, etc. Introducing Information Technology Security Information Technology Security Elements to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on End User Education, Operational Security, Information Security, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security It Infrastructure Information Budget For Fy2022
Information Technology Security It Infrastructure Information Budget For Fy2022This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Present the topic in a bit more detail with this Information Technology Security It Infrastructure Information Budget For Fy2022. Use it as a tool for discussion and navigation on Infrastructure, Information, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.




