Powerpoint Templates and Google slides for Security Protection
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Inflation protected securities ppt powerpoint presentation styles professional cpb
Inflation protected securities ppt powerpoint presentation styles professional cpbPresenting our Inflation Protected Securities Ppt Powerpoint Presentation Styles Professional Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Inflation Protected Securities This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Endpoint protection vs endpoint security ppt powerpoint presentation clipart cpb
Endpoint protection vs endpoint security ppt powerpoint presentation clipart cpbPresenting Endpoint Protection Vs Endpoint Security Ppt Powerpoint Presentation Clipart Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Endpoint Protection Vs Endpoint Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
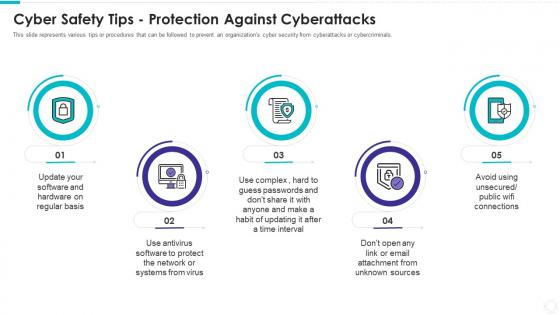 Electronic information security cyber safety tips protection against cyberattacks
Electronic information security cyber safety tips protection against cyberattacksThis slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Introducing Electronic Information Security Cyber Safety Tips Protection Against Cyberattacks to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Regular Basis, Protect Network, Systems Virustime Interval, Email Attachment Unknown Sources, using this template. Grab it now to reap its full benefits.
-
 Types network security protection ppt powerpoint presentation summary vector cpb
Types network security protection ppt powerpoint presentation summary vector cpbPresenting Types Network Security Protection Ppt Powerpoint Presentation Summary Vector Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Types Network Security Protection. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Payroll system security data protection ppt powerpoint presentation infographic template cpb
Payroll system security data protection ppt powerpoint presentation infographic template cpbPresenting our Payroll System Security Data Protection Ppt Powerpoint Presentation Infographic Template Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Payroll System Security Data Protection. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cyber security risk management framework for threat protection
Cyber security risk management framework for threat protectionThis slide highlights the cyber security risk management framework which include third party risk management, IT risk assessment and security center operations. Presenting our set of slides with Cyber Security Risk Management Framework For Threat Protection. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Governance, Security Assessment, Independent Audit.
-
 Cyber threat approaches for security protection
Cyber threat approaches for security protectionThe following slide highlights the cyber threat approaches which include traditional and artificial intelligence based approaches to counter threats. Presenting our well structured Cyber Threat Approaches For Security Protection. The topics discussed in this slide are Cybersecurity Threat, Social Engineering, Traditional Approach. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber threat security company users and protection
Cyber threat security company users and protectionThe following slide highlights the cyber threat security companies with its users retailers, BFSI, large scale enterprises, protection and pricing. Introducing our Cyber Threat Security Company Users And Protection set of slides. The topics discussed in these slides are Pricing, Company, Users. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber threat security maturity model with protection levels
Cyber threat security maturity model with protection levelsThe following slide illustrates the model of cyber threat security which includes secure, defend, contain, monitor and manage levels. Presenting our well structured Cyber Threat Security Maturity Model With Protection Levels. The topics discussed in this slide are Security Management Technology, Threat Management Platform, Threat Intelligence. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber threat strategies for security protection
Cyber threat strategies for security protectionThis slide highlights the cyber threat strategies that include risk assessment, phishing program, software protocols and end point protection. Presenting our set of slides with Cyber Threat Strategies For Security Protection. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Phishing Program, Software Protocols, End Point Protection.
-
 Icon Of Computer Security Program For Protection
Icon Of Computer Security Program For ProtectionIntroducing our premium set of slides with Icon Of Computer Security Program For Protection. Elucidate the one stage and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon Of Computer Security Program For Protection. So download instantly and tailor it with your information.
-
 Security Program Icon For Protecting Client Data
Security Program Icon For Protecting Client DataPresenting our set of slides with name Security Program Icon For Protecting Client Data. This exhibits information on one stage of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Program Icon For Protecting Client Data.
-
 Information Security Safety Tips Protection Against Cyberattacks
Information Security Safety Tips Protection Against CyberattacksThis slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Introducing Information Security Safety Tips Protection Against Cyberattacks to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Safety Tips Protection Against Cyberattacks, using this template. Grab it now to reap its full benefits.
-
 Network Security Network Safety Tips Protection Against
Network Security Network Safety Tips Protection AgainstThis slide represents various tips or procedures that can be followed to prevent an organizations network security from cyberattacks or networkcriminals. Increase audience engagement and knowledge by dispensing information using Network Security Network Safety Tips Protection Against. This template helps you present information on five stages. You can also present information on Network Safety Tips Protection Against Networkattacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Safety Tips Protection Against Cyberattacks
Information Technology Security Safety Tips Protection Against CyberattacksThis slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Increase audience engagement and knowledge by dispensing information using Information Technology Security Safety Tips Protection Against Cyberattacks. This template helps you present information on five stages. You can also present information on Cyber Safety Tips Protection Against Cyberattacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Building organizational security strategy plan elevating brand protection strategy
Building organizational security strategy plan elevating brand protection strategyThis slide provides information about enhancing brand protection strategy by implementing anti counterfeiting measures in terms of overt security features, covert security features and serialization. Deliver an outstanding presentation on the topic using this Building Organizational Security Strategy Plan Elevating Brand Protection Strategy. Dispense information and present a thorough explanation of Protection, Strategy, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Management Security And Protection Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Management Security And Protection Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Management security and protection colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Management Security And Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Management Security And Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Management security and protection monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Security Hacker Techniques To Keep Our Website Protected Ppt Icons
Security Hacker Techniques To Keep Our Website Protected Ppt IconsThis slide represents the techniques to protect our website from hacking and cyber attacks, including enhanced access controls, increased network security, installation of security software, etc. Increase audience engagement and knowledge by dispensing information using Security Hacker Techniques To Keep Our Website Protected Ppt Icons. This template helps you present information on eight stages. You can also present information on Hide Administrator Pages, Install Security Software, Update Everything using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phase 3 Respond To Cloud Protection Issues Cloud Information Security
Phase 3 Respond To Cloud Protection Issues Cloud Information SecurityThis slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services.Introducing Phase 3 Respond To Cloud Protection Issues Cloud Information Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Premises Conditions, Micro Segmentation, Contaminated Host using this template. Grab it now to reap its full benefits.
-
 Most Effective It Security Tools For Protection Against Insider Threat
Most Effective It Security Tools For Protection Against Insider ThreatThis slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM Introducing our premium set of slides with Most Effective It Security Tools For Protection Against Insider Threat. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Loss Prevention, User Entity Behavior, Identity Access Management. So download instantly and tailor it with your information.
-
 Cloud Computing Security Phase 3 Respond To Cloud Protection Issues
Cloud Computing Security Phase 3 Respond To Cloud Protection IssuesThis slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services. Deliver an outstanding presentation on the topic using this Cloud Computing Security Phase 3 Respond To Cloud Protection Issues. Dispense information and present a thorough explanation of Authentication Process, Cloud Service, Cloud Access Standards using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Global Cyber Security And Protection Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Global Cyber Security And Protection Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Global cyber security and protection colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Global Cyber Security And Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Global Cyber Security And Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Global cyber security and protection monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Cloud Security Protection Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Security Protection Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Cloud security protection colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Cloud Security Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Security Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Cloud security protection monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Cloud Security Threat Protection Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Security Threat Protection Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Cloud security threat protection colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Cloud Security Threat Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Security Threat Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Cloud security threat protection monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Architecture Of Cloud Security Cloud Data Protection
Architecture Of Cloud Security Cloud Data ProtectionThis slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an outstanding presentation on the topic using this Architecture Of Cloud Security Cloud Data Protection. Dispense information and present a thorough explanation of Infrastructure Security, Monitoring, Processing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Implement Cloud Security In Business Cloud Data Protection
Checklist To Implement Cloud Security In Business Cloud Data ProtectionThis slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Introducing Checklist To Implement Cloud Security In Business Cloud Data Protection to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispense information on Logging And Monitoring, Networking, Data Encryption, using this template. Grab it now to reap its full benefits.
-
 Cloud Data Protection Architecture Of Cloud Security
Cloud Data Protection Architecture Of Cloud SecurityThis slide defines the architecture of the cloud security system and how data is kept, managed, and secured based on customer and service providers responsibilities. Increase audience engagement and knowledge by dispensing information using Cloud Data Protection Architecture Of Cloud Security. This template helps you present information on two stages. You can also present information on Customer Data, Customer Responsibility, Cloud Service using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Data Protection Essential Pillars Of Cloud Security
Cloud Data Protection Essential Pillars Of Cloud SecurityThis slide shows the four essential pillars of cloud security, namely visibility and consistency, process based security, network security, and identity security. Introducing Cloud Data Protection Essential Pillars Of Cloud Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Process Based Security, Network Security, Identity Security, using this template. Grab it now to reap its full benefits.
-
 Cloud Data Protection How To Manage Security In Cloud
Cloud Data Protection How To Manage Security In CloudThis slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery. Increase audience engagement and knowledge by dispensing information using Cloud Data Protection How To Manage Security In Cloud. This template helps you present information on four stages. You can also present information on Access Controls, Data Recovery, Data Masking using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Data Protection Key Challenges In Cloud Security
Cloud Data Protection Key Challenges In Cloud SecurityThis slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs. Introducing Cloud Data Protection Key Challenges In Cloud Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Compliance Violations, Access Control, Organizations, using this template. Grab it now to reap its full benefits.
-
 Cloud Data Protection Phase 2 Secure Your Cloud
Cloud Data Protection Phase 2 Secure Your CloudThis slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Deliver an outstanding presentation on the topic using this Cloud Data Protection Phase 2 Secure Your Cloud. Dispense information and present a thorough explanation of Implement Information Security, Data Encryption, Segmented Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Data Protection Precautions Need To Take In Cloud Security
Cloud Data Protection Precautions Need To Take In Cloud SecurityThis slide depicts the cloud security precautions that one organization should take while signing up for a cloud service. Introducing Cloud Data Protection Precautions Need To Take In Cloud Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Cloud Vendors, Cloud Computing, Devoted Equipment, using this template. Grab it now to reap its full benefits.
-
 Cloud Data Protection Tools Used In Cloud Security
Cloud Data Protection Tools Used In Cloud SecurityThis slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. Increase audience engagement and knowledge by dispensing information using Cloud Data Protection Tools Used In Cloud Security. This template helps you present information on one stage. You can also present information on Cloud Solutions, Security, Networks using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Data Protection What Are The Downsides Of A Cloud Security
Cloud Data Protection What Are The Downsides Of A Cloud SecurityThis slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches. Introducing Cloud Data Protection What Are The Downsides Of A Cloud Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Data Security, Organizations, Data Breaches, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Best Practices Cloud Data Protection
Cloud Security Best Practices Cloud Data ProtectionThis slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver an outstanding presentation on the topic using this Cloud Security Best Practices Cloud Data Protection. Dispense information and present a thorough explanation of Cloud Protection Issues, Cloud Service, Infrastructure As A Service using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Security Checklist Access Control Cloud Data Protection
Cloud Security Checklist Access Control Cloud Data ProtectionThis slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. Introducing Cloud Security Checklist Access Control Cloud Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispense information on Cloud Services, Information, Data Servers, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Backup And Data Recovery Cloud Data Protection
Cloud Security Checklist Backup And Data Recovery Cloud Data ProtectionThis slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them. Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Backup And Data Recovery Cloud Data Protection. This template helps you present information on five stages. You can also present information on Data Servers, Location, Effective Data Plan using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Security Checklist Data Encryption Cloud Data Protection
Cloud Security Checklist Data Encryption Cloud Data ProtectionThis slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. Introducing Cloud Security Checklist Data Encryption Cloud Data Protection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Data Servers, Network, Cloud, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Logging And Monitoring Cloud Data Protection
Cloud Security Checklist Logging And Monitoring Cloud Data ProtectionThis slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Logging And Monitoring Cloud Data Protection. This template helps you present information on five stages. You can also present information on Organization, Network, Security using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Security Checklist Networking Cloud Data Protection
Cloud Security Checklist Networking Cloud Data ProtectionThis slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks. Introducing Cloud Security Checklist Networking Cloud Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispense information on Ensure Security, Network, Critical Data, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Policies And Procedures Cloud Data Protection
Cloud Security Checklist Policies And Procedures Cloud Data ProtectionThis slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization. Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Policies And Procedures Cloud Data Protection. This template helps you present information on five stages. You can also present information on Organization, On Boarding Employees, Cloud Security using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Security Checklist Security Patches And Updates Cloud Data Protection
Cloud Security Checklist Security Patches And Updates Cloud Data ProtectionThis slide depicts the importance of security patches and timely updates of security technologies. It also shows how it is crucial to scan systems, servers, and frameworks regularly. Introducing Cloud Security Checklist Security Patches And Updates Cloud Data Protection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Technologies, Organization, Servers, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Risks Or Threats Cloud Data Protection
Cloud Security Risks Or Threats Cloud Data ProtectionThis slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on. Increase audience engagement and knowledge by dispensing information using Cloud Security Risks Or Threats Cloud Data Protection. This template helps you present information on eight stages. You can also present information on Revenue Losses, Compliance Violations, Loss Of Data using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Security Threats Compliance Violations Cloud Data Protection
Cloud Security Threats Compliance Violations Cloud Data ProtectionThis slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non-compliance state. Introducing Cloud Security Threats Compliance Violations Cloud Data Protection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Authentication Procedures, Business, Organizations, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Contract Breaches With Clients Cloud Data Protection
Cloud Security Threats Contract Breaches With Clients Cloud Data ProtectionThis slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Contract Breaches With Clients Cloud Data Protection. This template helps you present information on four stages. You can also present information on Business Partners, Organization, Cloud using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Security Threats End User Control Cloud Data Protection
Cloud Security Threats End User Control Cloud Data ProtectionThis slide represents the end-user threat in cloud security and how an organization needs to control user access and be aware of potential threats. Introducing Cloud Security Threats End User Control Cloud Data Protection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Business Data, Customers, Centralized Data, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Loss Of Data Cloud Data Protection
Cloud Security Threats Loss Of Data Cloud Data ProtectionThis slide represents the data loss threat of cloud security it is essential to secure organization data and create backups. Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Loss Of Data Cloud Data Protection. This template helps you present information on four stages. You can also present information on Storage Locations, Organization, Strategies using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Security Threats Malware Attacks Cloud Data Protection
Cloud Security Threats Malware Attacks Cloud Data ProtectionThis slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. Introducing Cloud Security Threats Malware Attacks Cloud Data Protection to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispense information on Frameworks, Targets, Technology, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Revenue Losses Cloud Data Protection
Cloud Security Threats Revenue Losses Cloud Data ProtectionThis slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan. Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Revenue Losses Cloud Data Protection. This template helps you present information on five stages. You can also present information on Organizations Could, Revenue, Customers using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Security Threats Shared Vulnerabilities Cloud Data Protection
Cloud Security Threats Shared Vulnerabilities Cloud Data ProtectionThis slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data. Introducing Cloud Security Threats Shared Vulnerabilities Cloud Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispense information on Secure Cloud Data, Organizations, Data Security, using this template. Grab it now to reap its full benefits.
-
 Difference Between Cloud Security Solutions And Traditional Cloud Data Protection
Difference Between Cloud Security Solutions And Traditional Cloud Data ProtectionThis slide represents the difference between cloud security solutions and traditional IT solutions based on information centers, cost, scalability, and expenses. Deliver an outstanding presentation on the topic using this Difference Between Cloud Security Solutions And Traditional Cloud Data Protection. Dispense information and present a thorough explanation of Opportunity, Low Efficiency, Cloud Security, Expense using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Cloud Security Solutions Cloud Data Protection
Enterprise Cloud Security Solutions Cloud Data ProtectionThis slide describes the enterprise cloud security solutions, including multi-factor authentication, managing accounts and service proactively, being careful about shadow IT, and analyzing the cost-benefits of hybrid cloud. Present the topic in a bit more detail with this Enterprise Cloud Security Solutions Cloud Data Protection. Use it as a tool for discussion and navigation on Business Operation, Organizations, Analyze Cost Benefits . This template is free to edit as deemed fit for your organization. Therefore download it now
-
 How Does Cloud Security Work Cloud Data Protection
How Does Cloud Security Work Cloud Data ProtectionThis slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. Introducing How Does Cloud Security Work Cloud Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispense information on Data Security, Access Management, Business Continuity Planning, Cloud Security, using this template. Grab it now to reap its full benefits.
-
 How Does Cloud Security Work Data Retention And Business Cloud Data Protection
How Does Cloud Security Work Data Retention And Business Cloud Data ProtectionThis slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Data Retention And Business Cloud Data Protection. This template helps you present information on four stages. You can also present information on Impact Analysis, Business Continuity, Plan Development, Recovery Strategies using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 How Does Cloud Security Work Data Security Cloud Data Protection
How Does Cloud Security Work Data Security Cloud Data ProtectionThis slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. Introducing How Does Cloud Security Work Data Security Cloud Data Protection to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispense information on Wireless Security, Internet Security, Application Security, Network Security, Information Security, using this template. Grab it now to reap its full benefits.
-
 How Does Cloud Security Work Governance Cloud Data Protection
How Does Cloud Security Work Governance Cloud Data ProtectionThis slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Governance Cloud Data Protection. This template helps you present information on five stages. You can also present information on Knowledge, Quality, Security, Accessibility, Data Governance using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations





