Powerpoint Templates and Google slides for Security Protection
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Firewall Protection Secure Computer Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Firewall Protection Secure Computer Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is perfect for presentations on secure computer systems. It features a black and white design depicting a computer with a padlock, symbolizing the safety of your data. Use this icon to emphasize the importance of secure computing.
-
 Security Measures For Protecting Wireless Networks
Security Measures For Protecting Wireless NetworksThis slide highlights security methods for wireless network protection. The purpose of this slide is to establish security tactics for protecting data transmission and functioning seamlessly in interconnected world. It includes elements such as encryption, firewall, etc. Introducing our premium set of slides with Security Measures For Protecting Wireless Networks. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Intrusion Detection, Regular Firmware Updates. So download instantly and tailor it with your information.
-
 Treasury Inflation Protected Securities In Powerpoint And Google Slides Cpb
Treasury Inflation Protected Securities In Powerpoint And Google Slides CpbPresenting our Treasury Inflation Protected Securities In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Treasury Inflation Protected Securities. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
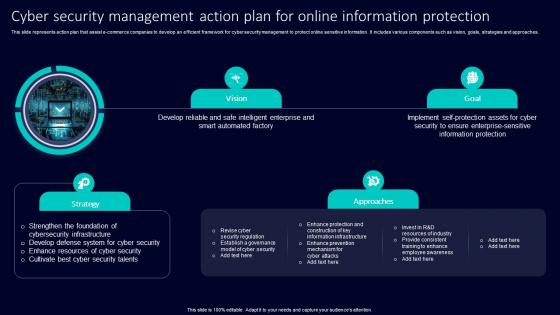 Cyber Security Management Action Plan For Online Information Protection
Cyber Security Management Action Plan For Online Information ProtectionThis slide represents action plan that assist e commerce companies to develop an efficient framework for cyber security management to protect online sensitive information. It includes various components such as vision, goals, strategies and approaches. Presenting our set of slides with Cyber Security Management Action Plan For Online Information Protection. This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Strengthen Foundation Cybersecurity Infrastructure, Develop Defense System Cyber Security, Enhance Resources Cyber Security.
-
 Information Security Management Framework For Organization Data Protection
Information Security Management Framework For Organization Data ProtectionThis slide represents framework that assists organizations in developing information security management to enhance data protection. This model sets information security at tactical level, strategic level, and operational level. Introducing our Information Security Management Framework For Organization Data Protection set of slides. The topics discussed in these slides are Information Security Plan, Consciousness Management, Risk Analysis. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information Security Management Icon For Data Protection
Information Security Management Icon For Data ProtectionPresenting our set of slides with Information Security Management Icon For Data Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Information Security Management Icon, Data Protection.
-
 Managing Information Security Threats To Enhance Data Protection
Managing Information Security Threats To Enhance Data ProtectionThis slide represents strategies that help businesses mitigate threats of information security management and reduce data loss incidents. It includes various threats such as social media attacks, social engineering, lack of encryption, etc. Presenting our well structured Managing Information Security Threats To Enhance Data Protection. The topics discussed in this slide are Social Media Attacks, Social Engineering, Malware On Endpoints. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Key Approaches To Protect From Honeypot Scams Hands On Blockchain Security Risk BCT SS V
Key Approaches To Protect From Honeypot Scams Hands On Blockchain Security Risk BCT SS VThe following slide illustrates some methods to protect blockchain network users from honeypot scams and implement defensive actions. It includes elements such as no dead coins, audits, check social media, scrutinize website, etc. Increase audience engagement and knowledge by dispensing information using Key Approaches To Protect From Honeypot Scams Hands On Blockchain Security Risk BCT SS V. This template helps you present information on four stages. You can also present information on Audits, Check Social Media, Scrutinize Website using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Methods To Avoid Sybil Attack For Protecting Tokens Hands On Blockchain Security Risk BCT SS V
Methods To Avoid Sybil Attack For Protecting Tokens Hands On Blockchain Security Risk BCT SS VThe following slide illustrates various ways to minimize and prevent sybil attacks and ensure safe blockchain transactions. It includes elements such as identity validation, hierarchical, defense system, cost of new nodes, social trust graphs, etc. Increase audience engagement and knowledge by dispensing information using Methods To Avoid Sybil Attack For Protecting Tokens Hands On Blockchain Security Risk BCT SS V. This template helps you present information on five stages. You can also present information on Identity Validation, Defense System, Cost Of New Node using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Audit Protection Icon
Cyber Security Audit Protection IconIntroducing our premium set of slides with Cyber Security Audit Protection Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security, Audit Protection Icon. So download instantly and tailor it with your information.
-
 Short Term Inflation Protected Securities Index Fund In Powerpoint And Google Slides Cpb
Short Term Inflation Protected Securities Index Fund In Powerpoint And Google Slides CpbPresenting our Short Term Inflation Protected Securities Index Fund In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Short Term Inflation, Protected Securities, Index Fund This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Inflation Protected Securities In Powerpoint And Google Slides Cpb
Inflation Protected Securities In Powerpoint And Google Slides CpbPresenting our Inflation Protected Securities In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Inflation Protected Securities This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Lock Protect Guard Key Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Lock Protect Guard Key Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful icon features a lock and key design, perfect for adding a touch of security to presentations. Ideal for business, security, or safety-related topics, it will provide a professional and eye-catching look to any project.
-
 Lock Protect Guard Key Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Lock Protect Guard Key Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is perfect for presentations on security, access control, and encryption. It features a simple, black-and-white design of a lock and key, making it an ideal visual aid for any discussion of protection and safety.
-
 Infrastructure As Code Iac Approaches Iac Security For Protecting Cloud Infrastructure
Infrastructure As Code Iac Approaches Iac Security For Protecting Cloud InfrastructureThis slide showcases the security of Infrastructure as Code for protecting cloud Infrastructure. The purpose of this slide is to highlight the importance of IaC security such as consistency and predictability, early detection and prevention, reduced human error, etc. Increase audience engagement and knowledge by dispensing information using Infrastructure As Code Iac Approaches Iac Security For Protecting Cloud Infrastructure. This template helps you present information on two stages. You can also present information on Consistency And Predictability, Scalability And Efficiency, Cloud Security, Configuring Cloud Resources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Treasury Inflation Protected Securities Yields In Powerpoint And Google Slides Cpb
Treasury Inflation Protected Securities Yields In Powerpoint And Google Slides CpbPresenting our Treasury Inflation Protected Securities Yields In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Treasury Inflation Protected Securities Yields. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Security Measures To Protect Wireless Communication
Security Measures To Protect Wireless CommunicationThis slide shows wireless communication security measures for data protection which helps to ensure privacy and integrity of information over wireless networks. It further includes security measures such as wired equivalent privacy, Wi-Fi protected access etc. Presenting our well structured Security Measures To Protect Wireless Communication The topics discussed in this slide are Wired Equivalent, Protected Access, Wireless Networks This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Data Security Strategies To Protect Retail Customer Digital Transformation Of Retail DT SS
Data Security Strategies To Protect Retail Customer Digital Transformation Of Retail DT SSThis slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness. Increase audience engagement and knowledge by dispensing information using Data Security Strategies To Protect Retail Customer Digital Transformation Of Retail DT SS This template helps you present information on six stages. You can also present information on Customer Data Protection, Online Transactions, Management Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementing Byod Policy To Enhance Develop Security Policies For Data Protection
Implementing Byod Policy To Enhance Develop Security Policies For Data ProtectionThis slide shows major data protection policies for handling sensitive data of corporate. It include policies such as device security, network and data handling, etc. Introducing Implementing Byod Policy To Enhance Develop Security Policies For Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, Data Handling, Device Security, Data Protection, using this template. Grab it now to reap its full benefits.
-
 Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod Policy
Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod PolicyThis slide shows essential considerations for protecting crucial data of company in organization. It include security areas such as device security, network security and software updates, etc. Increase audience engagement and knowledge by dispensing information using Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod Policy. This template helps you present information on five stages. You can also present information on Device Security, Mobile Device Management, Network Security, Malware Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Life Cycle Protection Next Generation CASB
Cloud Access Security Broker Life Cycle Protection Next Generation CASBIncrease audience engagement and knowledge by dispensing information using Cloud Access Security Broker Life Cycle Protection Next Generation CASB This template helps you present information on four stages. You can also present information on Identify Needs, Control Usage, Adaptive Access, Verify Usage using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Pillar Threat Protection Next Generation CASB
Cloud Access Security Broker Pillar Threat Protection Next Generation CASBThis slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Pillar Threat Protection Next Generation CASB This template helps you present information on five stages. You can also present information on Services, Cloud Storage, Compromised Accounts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Policy Management Overview In Firewall Protection
Firewall Network Security Policy Management Overview In Firewall ProtectionThis slide provides an overview of policy management in a firewall protection system. The purpose of this slide is to showcase the multiple guidelines for policy management and various advantages such as reducing mistakes, eliminating conflicts, and the possibility of harmful attacks. Present the topic in a bit more detail with this Firewall Network Security Policy Management Overview In Firewall Protection Use it as a tool for discussion and navigation on SOCKS, IBM Db2, Proxy Server This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Primary Types Of Software Firewall Protection
Firewall Network Security Primary Types Of Software Firewall ProtectionThis slide represents the main types of software firewalls. The purpose of this slide is to showcase the three primary kinds of software firewall protection, including virtual firewall, container firewall and managed service firewall or Firewall as a Service. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Primary Types Of Software Firewall Protection This template helps you present information on Three stages. You can also present information on Advantages, Disadvantages using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Security Measures To Improve Firewall Protection
Firewall Network Security Security Measures To Improve Firewall ProtectionThis slide represents the different security steps to enhance firewall protection in a network. The purpose of this slide is to showcase the various security measures to improve firewall protection, such as updating the firewall, using antivirus protection, restricting accessible ports and hosts, segmenting the network, etc. Introducing Firewall Network Security Security Measures To Improve Firewall Protection to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Screened Host Firewalls, Packet Filtering Router using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Technologies Used In Firewall Network Protection
Firewall Network Security Technologies Used In Firewall Network ProtectionThis slide gives an overview of the technologies used in firewall mechanisms. The purpose of this slide is to showcase the different technologies and techniques used in firewalls to protect a network, such as real-time monitoring, proxy servers, virtual private network, network address translation, and so on. Introducing Firewall Network Security Technologies Used In Firewall Network Protection to increase your presentation threshold. Encompassed with Eight stages, this template is a great option to educate and entice your audience. Dispence information on Packet Filters, Proxy Servers, Virtual Private Network using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Understanding Proxy Firewall Protection System
Firewall Network Security Understanding Proxy Firewall Protection SystemThis slide outlines the overview of the proxy firewall system. The purpose of this slide is to introduce the proxy firewall, including its functions, limitations, and benefits, such as security, logging capabilities, threat assessment, control, and granularity. Deliver an outstanding presentation on the topic using this Firewall Network Security Understanding Proxy Firewall Protection System Dispense information and present a thorough explanation of Internet, Proxy Firewall, Internet Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Benefits Of Next Generation Firewall Protection System
Firewall Network Security Benefits Of Next Generation Firewall Protection SystemThis slide highlights the advantages of Next Generation Firewalls for network protection. The purpose of this slide is to showcase the different benefits of next-generation firewall, such as robust threat prevention, flexible deployment, app, and identity-based checking and control, etc. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Benefits Of Next Generation Firewall Protection System This template helps you present information on Four stages. You can also present information on Firewall Network Security Benefits Of Next Generation Firewall Protection System using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Importance Of Using Firewall Network Protection
Firewall Network Security Importance Of Using Firewall Network ProtectionThis slide outlines the benefits of using firewall protection in an organizational network. This slide aims to showcase some essential features of a firewall, including monitoring network traffic, promoting privacy, preventing hacks, and eliminating virus and malware attacks. Deliver an outstanding presentation on the topic using this Firewall Network Security Importance Of Using Firewall Network Protection Dispense information and present a thorough explanation of Enhance Security, IP Addresses, Malicious Content using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Key Benefits Of Firewall Protection System
Firewall Network Security Key Benefits Of Firewall Protection SystemThis slide talks about the main advantages of a firewall security system. The purpose of this slide is to highlight the key benefits of a firewall for businesses, such as spyware protection, the significant barrier against viruses, protection against hacking, privacy promotion, and network traffic monitoring. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Key Benefits Of Firewall Protection System This template helps you present information on Five stages. You can also present information on Intelligent Protection, Traffic Filtering, Communication Protocol Administration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Key Components Of Firewall Protection System
Firewall Network Security Key Components Of Firewall Protection SystemThis slide talks about the primary elements of a firewall security system. The purpose of this slide is to showcase the different components of a firewall, such as network policy, advanced authentication, packet filtering, and application gateway. Present the topic in a bit more detail with this Firewall Network Security Key Components Of Firewall Protection System Use it as a tool for discussion and navigation on Misconfiguration, Software Vulnerabilities, Missing Firewall Policy This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Security Strategies To Protect Retail Customer Comprehensive Retail Transformation DT SS
Data Security Strategies To Protect Retail Customer Comprehensive Retail Transformation DT SSThis slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness. Present the topic in a bit more detail with this Data Security Strategies To Protect Retail Customer Comprehensive Retail Transformation DT SS. Use it as a tool for discussion and navigation on Online Transactions, Customer Data Protection, POS Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Folder Security File Protection Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Folder Security File Protection Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a great visual aid for representing folder password protection. It is a modern and vibrant design that will add a professional touch to any presentation. The icon is easy to use and can be used to quickly and effectively communicate the importance of password security.
-
 Folder Security File Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Folder Security File Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Folder Password is a simple yet effective way to protect your confidential data. It is easy to use and provides a secure encryption for your files. It is an ideal solution for those who want to keep their documents safe and secure.
-
 Folder Security Password Protection Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Folder Security Password Protection Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a great visual aid for representing folder password protection. It is a modern and vibrant design that will add a professional touch to any presentation. The icon is easy to use and can be used to quickly and effectively communicate the importance of password security.
-
 Folder Security Password Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Folder Security Password Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Folder Password is a simple yet effective way to protect your confidential data. It is easy to use and provides a secure encryption for your files. It is an ideal solution for those who want to keep their documents safe and secure.
-
 Essential Guide To Database Marketing Data Security Best Practices To Protect Customer Information MKT SS V
Essential Guide To Database Marketing Data Security Best Practices To Protect Customer Information MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Deliver an outstanding presentation on the topic using this Essential Guide To Database Marketing Data Security Best Practices To Protect Customer Information MKT SS V Dispense information and present a thorough explanation of Data Usage Policy, Data Encryption, Endpoint Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Approaches To Protect Securing Blockchain Transactions A Beginners Guide BCT SS V
Key Approaches To Protect Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide illustrates some methods to protect blockchain network users from honeypot scams and implement defensive actions. It includes elements such as no dead coins, audits, check social media, scrutinize website, etc. Introducing Key Approaches To Protect Securing Blockchain Transactions A Beginners Guide BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on No Dead Coins, Audits, Check Social Media, using this template. Grab it now to reap its full benefits.
-
 Data Security Best Practices To Protect Database Marketing Practices To Increase MKT SS V
Data Security Best Practices To Protect Database Marketing Practices To Increase MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Increase audience engagement and knowledge by dispensing information using Data Security Best Practices To Protect Database Marketing Practices To Increase MKT SS V. This template helps you present information on four stages. You can also present information on Policy, Encryption, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloning In Cyber Security For Data Protection
Cloning In Cyber Security For Data ProtectionThis slide shows benefits of cloning for cyber protection. It aims to prevent cloning security risks to mitigate unauthorized access to technical assets. It covers four cyber security measures such as data protection, integrity, loss prevention and transfers. Presenting our set of slides with name Cloning In Cyber Security For Data Protection. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Protection, Data Integrity, Data Transfers.
-
 Cyber Security Icon Protecting Card Cloning Fraud
Cyber Security Icon Protecting Card Cloning FraudIntroducing our premium set of slides with name Cyber Security Icon Protecting Card Cloning Fraud. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security, Icon Protecting, Card Cloning Fraud. So download instantly and tailor it with your information.
-
 Secure Protection Service Business In Powerpoint And Google Slides Cpb
Secure Protection Service Business In Powerpoint And Google Slides CpbPresenting our Secure Protection Service Business In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Secure Protection Service Business This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Data Security Best Practices To Protect Using Customer Data To Improve MKT SS V
Data Security Best Practices To Protect Using Customer Data To Improve MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Deliver an outstanding presentation on the topic using this Data Security Best Practices To Protect Using Customer Data To Improve MKT SS V. Dispense information and present a thorough explanation of Policy, Data, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Protection Workplace Skills For Security Analysts
Cyber Protection Workplace Skills For Security AnalystsThe following slide highlights technical expertise and proficiency levels to demonstrate cybersecurity workplace skills for security analytics. It helps organizations evaluate and develop cybersecurity workforce effectively Presenting our well structured Cyber Protection Workplace Skills For Security Analysts. The topics discussed in this slide are Beginner, Intermediate, Advance. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Types Of Wireless Internet Security For Data Protection
Types Of Wireless Internet Security For Data ProtectionThe following slide highlights key points such as WEP, WPA, WPA2, and WPA3 protocols to show types of wireless internet security for privacy protection. It helps in understanding and comparing different safety procedures for effective data protection. Introducing our premium set of slides with Types Of Wireless Internet Security For Data Protection. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Protection, Wireless Internet. So download instantly and tailor it with your information.
-
 Csirt Cyber Security Icon For Protecting Data
Csirt Cyber Security Icon For Protecting DataIntroducing our premium set of slides with Csirt Cyber Security Icon For Protecting Data. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Csirt Cyber Security, Protecting Data. So download instantly and tailor it with your information.
-
 Data Protection Server Security Technology Icon
Data Protection Server Security Technology IconPresenting our set of slides with Data Protection Server Security Technology Icon. This exhibits information on threestages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Protection, Server Security Technology.
-
 Enhance Server Security Through Data Protection Storage Icon
Enhance Server Security Through Data Protection Storage IconPresenting our set of slides with Enhance Server Security Through Data Protection Storage Icon. This exhibits information on fourstages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Server Security, Data Protection Storage.
-
 File Network Protection Icon Through Server Security
File Network Protection Icon Through Server SecurityIntroducing our premium set of slides with File Network Protection Icon Through Server Security. Ellicudate the threestages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like File Network Protection, Server Security. So download instantly and tailor it with your information.
-
 Triage Cyber Security For System Protection Icon
Triage Cyber Security For System Protection IconPresenting our set of slides with name Triage Cyber Security For System Protection Icon This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Triage Cyber Security, System Protection Icon
-
 Facility Security Icon For Asset Protection
Facility Security Icon For Asset ProtectionIntroducing our premium set of slides with name Facility Security Icon For Asset Protection. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Facility Security, Icon For Asset Protection. So download instantly and tailor it with your information.
-
 Data Security Best Practices To Protect Customer Information Database Marketing Techniques MKT SS V
Data Security Best Practices To Protect Customer Information Database Marketing Techniques MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Deliver an outstanding presentation on the topic using this Data Security Best Practices To Protect Customer Information Database Marketing Techniques MKT SS V. Dispense information and present a thorough explanation of Data Usage Policy, Data Encryption, Endpoint Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Security Icon Protecting From Cyber Threats
Firewall Security Icon Protecting From Cyber ThreatsIntroducing our Firewall Security Icon Protecting From Cyber Threats set of slides. The topics discussed in these slides are Firewall Security, Protecting. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Containerization Technology Security Best Practices To Protect Containerized Environments
Containerization Technology Security Best Practices To Protect Containerized EnvironmentsThis slide outlines the best practices for securing containerized environments. The purpose of this slide is to define the security best practices for organizations to protect containerized environments, and these are securing images, securing registries, securing deployments, and so on. Deliver an outstanding presentation on the topic using this Containerization Technology Security Best Practices To Protect Containerized Environments. Dispense information and present a thorough explanation of Securing Registries, Securing Deployment, Securing Container Runtime, Securing Kubernetes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 CASB As A Streamline Endpoint Protection Solution CASB Cloud Security
CASB As A Streamline Endpoint Protection Solution CASB Cloud SecurityThis slide outlines how cloud access security broker 2.0 streamlines endpoint protection. The purpose of this slide is to showcase how CASB 2.0 improves endpoint security for streamlined deployment. It also includes the features of CASB 2.0 and endpoint security integration. Deliver an outstanding presentation on the topic using this CASB As A Streamline Endpoint Protection Solution CASB Cloud Security. Dispense information and present a thorough explanation of Streamline Endpoint Protection Solution, Endpoint Security Integration, Streamlined Deployment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Life Cycle Protection CASB Cloud Security
Cloud Access Security Broker Life Cycle Protection CASB Cloud SecurityThe steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. Introducing Cloud Access Security Broker Life Cycle Protection CASB Cloud Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Assess Risk And Compliance, Discover New Requirements, Prioritize Risk Contain, Mitigate Risk, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker Pillar Threat Protection CASB Cloud Security
Cloud Access Security Broker Pillar Threat Protection CASB Cloud SecurityThis slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Introducing Cloud Access Security Broker Pillar Threat Protection CASB Cloud Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker Pillar, Threat Protection Pillar, Machine Learning Algorithms, using this template. Grab it now to reap its full benefits.
-
 Advantages Of Utilizing Advanced Threat Protection In Cyber Security
Advantages Of Utilizing Advanced Threat Protection In Cyber SecurityThe following slide highlights the possible benefits of implementing advanced threat protection against sophisticated cyber threats and attacks. Presenting our set of slides with Advantages Of Utilizing Advanced Threat Protection In Cyber Security. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security, Analytics, Protection.
-
 IoT Cyber Security Technologies For Advanced Threat Protection
IoT Cyber Security Technologies For Advanced Threat ProtectionThe purpose of this slide is to showcase various types of Internet of Things IoT security technologies that assists in safeguarding cyber threats. Introducing our premium set of slides with IoT Cyber Security Technologies For Advanced Threat Protection. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Architecture, Security, Computing. So download instantly and tailor it with your information.
-
 Cyber Security Checklist To Protect Saas Applications
Cyber Security Checklist To Protect Saas ApplicationsThis slide represents cybersecurity checklist for SaaS applications to protect data. It aims to assist organizations in identifying potential vulnerabilities as well as examining security standards. It includes various elements such as backing up creation and testing, using real-time security service, etc. Introducing our Cyber Security Checklist To Protect Saas Applications set of slides. The topics discussed in these slides are Determines Data Isolation, Safeguards Against Data Theft This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.





