Powerpoint Templates and Google slides for Security Processes
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Bank Frauds Prevention Process With Cyber Security Program
Bank Frauds Prevention Process With Cyber Security ProgramThe slide illustrates a banking frauds mitigation process for client to reduce and prevent issues. Its key steps are establish governance structure, define culture shift, introduce staff training, improve payment process, implement technology controls and harden human firewall. Introducing our premium set of slides with Bank Frauds Prevention Process With Cyber Security Program. Elucidate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Introduce Staff Training, Implement Technology Controls, Improve Payment Process, Harden Human Firewall. So download instantly and tailor it with your information.
-
 Process Of Secure Reverse Proxying Reverse Proxy Load Balancer Ppt Formats
Process Of Secure Reverse Proxying Reverse Proxy Load Balancer Ppt FormatsThis slide depicts secure reverse proxying and how it can be established in three ways such as secure client to the proxy, secure proxy to the content server, and the secure client to proxy and secure proxy to a content server. Introducing Process Of Secure Reverse Proxying Reverse Proxy Load Balancer Ppt Formats to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Secure Reverse, Proxy Server, Process, using this template. Grab it now to reap its full benefits.
-
 Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations
Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security OperationsThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Present the topic in a bit more detail with this Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Automation, Integrates, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Processes That Cant Be Automated Enabling Automation In Cyber Security Operations
Security Processes That Cant Be Automated Enabling Automation In Cyber Security OperationsThe following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Increase audience engagement and knowledge by dispensing information using Security Processes That Cant Be Automated Enabling Automation In Cyber Security Operations. This template helps you present information on three stages. You can also present information on Threat Modeling, Penetration Testing, Bug Bounty using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Why To Automate The It Security Process Enabling Automation In Cyber Security Operations
Why To Automate The It Security Process Enabling Automation In Cyber Security OperationsThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Increase audience engagement and knowledge by dispensing information using Why To Automate The It Security Process Enabling Automation In Cyber Security Operations. This template helps you present information on five stages. You can also present information on Better Threat Detection, Faster Containment, Improve Productivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Architecture And Security Review Data Complexity Slows Down The Business Process Multi Cloud
Cloud Architecture And Security Review Data Complexity Slows Down The Business Process Multi CloudThis slide covers the current complex multi cloud architecture with all their inherent complexity, fragility, and limitations that slow down the business process. Introducing Cloud Architecture And Security Review Data Complexity Slows Down The Business Process Multi Cloud to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Data Complexity, Slows Down The Business, Multi Cloud Architecture, using this template. Grab it now to reap its full benefits.
-
 Reverse Proxy Server Process Of Secure Reverse Proxying Ppt Powerpoint Presentation Infographic Template Ideas
Reverse Proxy Server Process Of Secure Reverse Proxying Ppt Powerpoint Presentation Infographic Template IdeasThis slide depicts secure reverse proxying and how it can be established in three ways such as secure client to the proxy, secure proxy to the content server, and the secure client to proxy and secure proxy to a content server. Introducing Reverse Proxy Server Process Of Secure Reverse Proxying Ppt Powerpoint Presentation Infographic Template Ideas to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Secure Reverse Proxying, Safe Data Transmission, Secure Sockets, using this template. Grab it now to reap its full benefits.
-
 Security Processes That Cant Be Automated Security Automation To Investigate And Remediate Cyberthreats
Security Processes That Cant Be Automated Security Automation To Investigate And Remediate CyberthreatsThe following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Introducing Security Processes That Cant Be Automated Security Automation To Investigate And Remediate Cyberthreats to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Threat Modeling, Penetration Testing, Bug Bounty , using this template. Grab it now to reap its full benefits.
-
 Why To Automate The It Security Process Security Automation To Investigate And Remediate Cyberthreats
Why To Automate The It Security Process Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Introducing Why To Automate The It Security Process Security Automation To Investigate And Remediate Cyberthreats to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Better Threat Detection, Faster Containment, Improve Productivity, using this template. Grab it now to reap its full benefits.
-
 Security Automation Integrates Tools Systems And Processes Security Automation In Information Technology
Security Automation Integrates Tools Systems And Processes Security Automation In Information TechnologyThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Increase audience engagement and knowledge by dispensing information using Security Automation Integrates Tools Systems And Processes Security Automation In Information Technology. This template helps you present information on eight stages. You can also present information on Automation, Integrates, Processes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Security Processes That Cant Be Automated Security Automation In Information Technology
Security Processes That Cant Be Automated Security Automation In Information TechnologyThe following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Increase audience engagement and knowledge by dispensing information using Security Processes That Cant Be Automated Security Automation In Information Technology. This template helps you present information on three stages. You can also present information on Threat Modeling, Penetration Testing, Bug Bounty using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Why To Automate The It Security Process Security Automation In Information Technology
Why To Automate The It Security Process Security Automation In Information TechnologyThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Increase audience engagement and knowledge by dispensing information using Why To Automate The It Security Process Security Automation In Information Technology. This template helps you present information on five stages. You can also present information on Better Threat Detection, Faster Containment, Improve Productivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Process Of Security Risk Management Plan
Process Of Security Risk Management PlanThis slide shows the process of security risk management plan which includes communication and consultation, monitoring and reviewing with establishing context such as strategic, security and entity with risk assessment steps that focuses on identification, assessment, etc. Introducing our Process Of Security Risk Management Plan set of slides. The topics discussed in these slides are Threat Assessment, Vulnerability Assessment, Security Context . This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Four Step Process Of Security Automation System
Four Step Process Of Security Automation SystemThe following slide highlights multistep process of security automation. The company can detect security breach after following steps such as investigating the steps of IT analyst, determining responsive action, eradication and closing the ticked Presenting our set of slides with name Four Step Process Of Security Automation System. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Investigating Steps, Security Analysts, Eradication.
-
 Multistep Process For Automating Cloud Security Operations
Multistep Process For Automating Cloud Security OperationsThe following slide highlights four step process of cloud security automation. The various steps are container configure management, using infrastructure as code, automating asset tagging and vulnerability scanning where security analysts should implement automation. Introducing our premium set of slides with Multistep Process For Automating Cloud Security Operations. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Container Configure Management, Infrastructure As Code, Vulnerability Scanning. So download instantly and tailor it with your information.
-
 Cyber Security Incident Response Process Flowchart
Cyber Security Incident Response Process FlowchartThis slide covers cyber security incident response process flowchart. It involves relationship between technical actions coordinator, incident manager, supporting actions coordinator and business owner. Introducing our Cyber Security Incident Response Process Flowchart set of slides. The topics discussed in these slides are Technical Actions Coordinator, Supporting Actions Coordinator, Business Owner. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Incident Management Process In Cyber Security
Incident Management Process In Cyber SecurityThis slide covers incident management process in cyber security. It involves steps such as engage team, identify incidents, assessment, investigation and documentation. Presenting our set of slides with name Incident Management Process In Cyber Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Incident Response Team, Monitoring And Evaluation, Investigation Or Resolving.
-
 Key Steps Cyber Security Incident Response Plan Process
Key Steps Cyber Security Incident Response Plan ProcessThis slide covers key steps cyber incident response plan process. It involves six stages such as preparation, detection, analysis, containment, eradication and recovery. Presenting our set of slides with name Key Steps Cyber Security Incident Response Plan Process. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Preparation, Detection, Containment, Eradication.
-
 6 Stage Process For Implementation Of Risk Management In Cyber Security Project
6 Stage Process For Implementation Of Risk Management In Cyber Security ProjectThis This slide signifies the six step process for successful implementation of risk assessment in cyber security project. It covers information about stages like identify, analyse, evaluate, prioritize, treat and monitor. Presenting our set of slides with name 6 Stage Process For Implementation Of Risk Management In Cyber Security Project. This exhibits information on six stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Analyse, Evaluate, Prioritize, Treat.
-
 Cyber Data Security Risk Management Response Process
Cyber Data Security Risk Management Response ProcessThis slide covers process to respond towards cyber data security risk. It includes steps such as preparation of incident response plan, detection of data compromises, analyse use of malicious tools, eradicate network threats, data recovery as the final step. Presenting our set of slides with name Cyber Data Security Risk Management Response Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Threats, Compromised Data, Data Compromises.
-
 Four Steps Of Cyber Security Data Breach Risk Process
Four Steps Of Cyber Security Data Breach Risk ProcessThis slide covers steps utilised to breach data. It includes stages such as probing, performing initial attack, expansion of attacks and data lifting. Introducing our premium set of slides with name Four Steps Of Cyber Security Data Breach Risk Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Initial Attack, Expanded Attack, Breach Risk Process. So download instantly and tailor it with your information.
-
 Pci Certification For Increasing Security Online Transactions How Ecommerce Financial Process Can Be Improved
Pci Certification For Increasing Security Online Transactions How Ecommerce Financial Process Can Be ImprovedThis slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Deliver an outstanding presentation on the topic using this Pci Certification For Increasing Security Online Transactions How Ecommerce Financial Process Can Be Improved. Dispense information and present a thorough explanation of Transactions, Certification, Integration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Strategic Planning Process For Cps Next Generation Computing Systems
Security Strategic Planning Process For Cps Next Generation Computing SystemsThis slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Present the topic in a bit more detail with this Security Strategic Planning Process For Cps Next Generation Computing Systems. Use it as a tool for discussion and navigation on Strategic, Planning, Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Business Process And Security Expert For Service Architecture
Business Process And Security Expert For Service ArchitectureThis slide covers business process and security exert for service architecture which includes policy generation framework, process security workbench and transformation unit. Presenting our well structured Business Process And Security Expert For Service Architecture. The topics discussed in this slide are Business Process, Security Expert, Service Architecture. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Business Security Risk Management Process
Business Security Risk Management ProcessThis slide covers business security risk management process which includes setting context, security risk assessment and implementation with monitoring. Presenting our well structured Business Security Risk Management Process. The topics discussed in this slide are Communicate Consult, Departmental Security, Risk Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Reactive And Proactive Business Security Evaluation Process
Reactive And Proactive Business Security Evaluation ProcessThis slide covers reactive and proactive business security evaluation process which includes evaluating security based on set standards. Presenting our well structured Reactive And Proactive Business Security Evaluation Process. The topics discussed in this slide are Reactive Proactive, Business Security, Evaluation Process. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Practices For Secure Online Payment Processing
Practices For Secure Online Payment ProcessingThis slide mentions practices for online payment processing to ensure secure checkout process. It includes matching IP and billing address, Encrypt data and use payment tokenization method. Introducing our premium set of slides with Practices For Secure Online Payment Processing. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Match The Ip And Billing Address, Encrypt Data, Use Payment Tokenization. So download instantly and tailor it with your information.
-
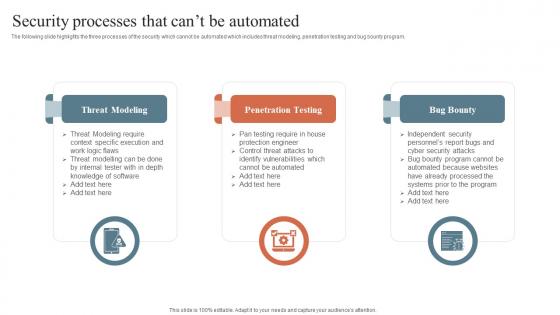 Security Processes That Cant Be Automated Security Orchestration Automation And Response Guide
Security Processes That Cant Be Automated Security Orchestration Automation And Response GuideThe following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Introducing Security Processes That Cant Be Automated Security Orchestration Automation And Response Guide to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Threat Modeling, Penetration Testing, Bug Bounty, using this template. Grab it now to reap its full benefits.
-
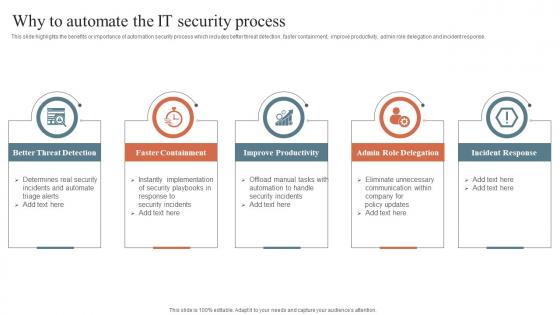 Why To Automate The It Security Process Security Orchestration Automation And Response Guide
Why To Automate The It Security Process Security Orchestration Automation And Response GuideThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Increase audience engagement and knowledge by dispensing information using Why To Automate The It Security Process Security Orchestration Automation And Response Guide. This template helps you present information on five stages. You can also present information on Better Threat Detection, Faster Containment, Improve Productivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Process For Information Security Risk Assessment Information System Security And Risk Administration Plan
Process For Information Security Risk Assessment Information System Security And Risk Administration PlanThis slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Increase audience engagement and knowledge by dispensing information using Process For Information Security Risk Assessment Information System Security And Risk Administration Plan. This template helps you present information on four stages. You can also present information on Security Threats, Information Assets, Risk Associated using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Response Process Flow Chart Ppt Powerpoint Presentation Model File Formats
Cyber Security Incident Response Process Flow Chart Ppt Powerpoint Presentation Model File FormatsThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Deliver an outstanding presentation on the topic using this Cyber Security Incident Response Process Flow Chart Ppt Powerpoint Presentation Model File Formats. Dispense information and present a thorough explanation of Instrumentation, Agency User Reporting, Cyber Threat Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Security Operation Center Process
Enterprise Security Operation Center ProcessThis slide covers enterprise security operation center process. It involves monitoring, basic investigation, mitigation, threat hunting, counter intelligence and advanced investigations. Introducing our Enterprise Security Operation Center Process set of slides. The topics discussed in these slides are Security Intelligence Platform, Help Desks, Monitoring. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Threat Prevention And Security Process
Cyber Threat Prevention And Security ProcessThis slide shows four steps to provide and assure protection against cyber threats. It includes steps secure perimeter, protect users, network segmentation, determine and control risks. Introducing our premium set of slides with name Cyber Threat Prevention And Security Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Secure Perimeter, Smart Network Segmentation, Determine And Control. So download instantly and tailor it with your information.
-
 Threat Modeling Process For Secure Data Assets
Threat Modeling Process For Secure Data AssetsThis slide shows threat modeling to protect business assets from risks. It contains two phases discovery and implementation that includes steps such as identify assets, analyze attack surface, attack vectors, analyze, prioritize and develop controls. Introducing our premium set of slides with name Threat Modeling Process For Secure Data Assets. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Hackers Path, Identified Assets, Threat Routes. So download instantly and tailor it with your information.
-
 Threat Modelling Process Of Cyber Security Program
Threat Modelling Process Of Cyber Security ProgramThis slide shows threat modelling process to identify gaps and improve efficiency of cyber security program. It contains five steps select digital asset, identify attack scenarios, evaluate existing controls, assess residual risks and construct business case. Presenting our set of slides with name Threat Modelling Process Of Cyber Security Program. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Threat Modelling, Cyber Security, Assess Residual Risk .
-
 Process For Information Security Risk Assessment Cybersecurity Risk Analysis And Management Plan
Process For Information Security Risk Assessment Cybersecurity Risk Analysis And Management PlanThis slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Introducing Process For Information Security Risk Assessment Cybersecurity Risk Analysis And Management Plan to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Process, Assessment, Information, using this template. Grab it now to reap its full benefits.
-
 Robotic Process Automation Security Steps
Robotic Process Automation Security StepsThis slide exhibits steps to ensure robotic process automation protection to prevent data leakage and fraud. It includes four steps ensure bot actions accountability, avoid fraud, protect log integrity and enable secure development. Presenting our set of slides with name Robotic Process Automation Security Steps. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Bot Actions Accountability, Avoid Fraud And Errors, Secure Log Integrity.
-
 GRC Implementation Process To Manage Security Risks
GRC Implementation Process To Manage Security RisksMentioned slide outlines 3 step process of governance, risk and compliance GRC. Information covered in this slide is related to governance, risk management and compliance which will assist organization to successfully mitigate IT and security risks. Introducing our premium set of slides with GRC Implementation Process To Manage Security Risks. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Compliance, Risk Management, Governance. So download instantly and tailor it with your information.
-
 Security Orchestration Automation Security Automation Integrates Tools Systems And Processes
Security Orchestration Automation Security Automation Integrates Tools Systems And ProcessesThis slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Deliver an outstanding presentation on the topic using this Security Orchestration Automation Security Automation Integrates Tools Systems And Processes. Dispense information and present a thorough explanation of Security Automation, Robotic Process, Security Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Process For Information Security Risk Assessment Formulating Cybersecurity Plan
Process For Information Security Risk Assessment Formulating Cybersecurity PlanThis slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Introducing Process For Information Security Risk Assessment Formulating Cybersecurity Plan to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Identifying Internal, Information Security Threats, Information Assets, using this template. Grab it now to reap its full benefits.
-
 Security Governance And Management Process Icon
Security Governance And Management Process IconPresenting our set of slides with Security Governance And Management Process Icon. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Governance, Management Process Icon.
-
 Security Strategic Planning Process For Cps Collective Intelligence Systems
Security Strategic Planning Process For Cps Collective Intelligence SystemsThis slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Increase audience engagement and knowledge by dispensing information using Security Strategic Planning Process For Cps Collective Intelligence Systems. This template helps you present information on one stages. You can also present information on Business Strategy, Environmental Trends, Gap Analysis, Prioritization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Transformation Process Flow
Cyber Security Transformation Process FlowThis slide provides a cyber security process for transformation of business operations which can be used by managers for risk mitigation by resolving security issues. The steps relate to assessment of current cyber security posture, set objectives, implement strategies, train employees etc. Introducing our premium set of slides with Cyber Security Transformation Process Flow. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Set Objectives, Implement Strategies, Train Employees. So download instantly and tailor it with your information.
-
 Nist Framework Process For Security Control Selection
Nist Framework Process For Security Control SelectionMentioned Slide Showcases The Process To Choose Security Controls Based On Nist Security Control. It Include Steps Like Security Categorization Using Fips 199, Identify Baseline Security Controls, Tailoring Baseline Security Controls And Document The Control Selection Process. Presenting Our Well Structured Nist Framework Process For Security Control Selection. The Topics Discussed In This Slide Are Framework, Process, Categorization. This Is An Instantly Available Powerpoint Presentation That Can Be Edited Conveniently. Download It Right Away And Captivate Your Audience.
-
 Digital Certificate Creation Process With Secure Communication
Digital Certificate Creation Process With Secure CommunicationThis slide showcases the steps for digital certificate creating procedure with secure communication. It includes elements such as request generation, verification, obtaining public key and sending digital certificate. Presenting our set of slides with Digital Certificate Creation Process With Secure Communication. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Certifying Authority, Digital Signature, Digital Certificate.
-
 4 Step Process To Improve Safety And Security
4 Step Process To Improve Safety And SecurityThis slide shows the four stage process to increase safety and security. It includes firewall installation, separate network for payment, passwords change and vulnerabilities test. Presenting our set of slides with 4 Step Process To Improve Safety And Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Separate Network For Payment, Passwords Change, Firewall Installation.
-
 Five Step Process Of Safety And Security
Five Step Process Of Safety And SecurityThis slide shows the five stages process of safety and security. These stages are audit, plan, execute, monitor and repeat. Introducing our premium set of slides with Five Step Process Of Safety And Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Audit, Cyber Security Training, Quarterly Plan Review. So download instantly and tailor it with your information.
-
 Cyber Security Incident Response Process
Cyber Security Incident Response ProcessThis slide covers procedure of cyber security incident response. The purpose of this process is to examine the cyber threat and try to find the ways to mitigate the risk. It includes four steps such as identification and detection, containment, eradication and recovery and post recovery.Introducing our premium set of slides with Cyber Security Incident Response Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identification Detection, Eradication Recovery, Incident Manager. So download instantly and tailor it with your information.
-
 Six Step Process For Risk Management In Cyber Security Project
Six Step Process For Risk Management In Cyber Security ProjectThis slide signifies the six step process for risk assessment in cyber security project. It covers information about stages like identify, analyse, evaluate, prioritize, treat and monitor Presenting our set of slides with name Six Step Process For Risk Management In Cyber Security Project. This exhibits information on six stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Management, Process, Computing Software.
-
 RPA Discovery Process Security Steps
RPA Discovery Process Security StepsFollowing slide exhibits steps for robotic process automation security. Purpose of this slide is to use business automation efficiently that prevents data leakage and fraud. It includes pointers such as bot actions accountability, avoid fraud, secure log integrity etc. Introducing our premium set of slides with RPA Discovery Process Security Steps. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Technical And Automations Tools, Analysis Structure, RPA Development. So download instantly and tailor it with your information.
-
 Payment Security Processing Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Payment Security Processing Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon is a visual representation of payment security. It features a padlock symbolizing safety and security, with a green background to indicate trustworthiness and reliability. Perfect for presentations on secure payment systems and processes.
-
 Payment Security Processing Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Payment Security Processing Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone powerpoint icon on Payment Security is perfect for presentations on online banking, credit card fraud prevention, and other financial security topics. It is simple yet effective, making it easy to convey your message to your audience. It is a great visual aid to help explain the importance of payment security.
-
 Supply Chain Security Risk Management Process
Supply Chain Security Risk Management ProcessThis slide showcases process that can help organization to manage supply chain security risks. Its key steps are document risks, develop framework, monitor risk and regular review. Introducing our premium set of slides with Supply Chain Security Risk Management Process Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Document Risks, Develop Framework. So download instantly and tailor it with your information.
-
 Ultimate Guide For Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS
Ultimate Guide For Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SSThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Ultimate Guide For Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS Use it as a tool for discussion and navigation on Network Security, Node Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
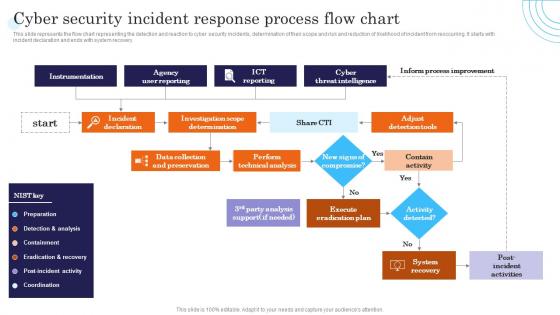 Cyber Security Incident Response Process Flow Chart Incident Response Strategies Deployment
Cyber Security Incident Response Process Flow Chart Incident Response Strategies DeploymentThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Response Process Flow Chart Incident Response Strategies Deployment. This template helps you present information on one stages. You can also present information on Instrumentation, Agency, Intelligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Response Process Flow Chart Development And Implementation Of Security
Cyber Security Incident Response Process Flow Chart Development And Implementation Of SecurityThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Deliver an outstanding presentation on the topic using this Cyber Security Incident Response Process Flow Chart Development And Implementation Of Security. Dispense information and present a thorough explanation of Data Collection And Preservation, Perform Technical Analysis, Incident Declaration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incident Response Process Flow Chart Cyber Security Attacks Response Plan
Cyber Security Incident Response Process Flow Chart Cyber Security Attacks Response PlanThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Present the topic in a bit more detail with this Cyber Security Incident Response Process Flow Chart Cyber Security Attacks Response Plan. Use it as a tool for discussion and navigation on Cyber Threat Intelligence, Agency User Reporting, Instrumentation, Cyber Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Security Audit And Testing Process
Cloud Security Audit And Testing ProcessThe slide highlights a process of cloud audit to test the security controls. Various steps involved are planning, data collection, analyse, recommendations and remediation. Presenting our set of slides with Cloud Security Audit And Testing Processs. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Planning, Analyse, Recommendations, Remediation .
-
 Cloud Security Audit Assessment Process
Cloud Security Audit Assessment ProcessThe slide exhibits various steps of cloud security audit for getting an excellent performance. Various steps included are understand the model, analyse, validate controls and calculate score. Introducing our premium set of slides with Cloud Security Audit Assessment Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Calculate Score, Validate Controls, Understand The Model . So download instantly and tailor it with your information.
-
 Cyber Security Incident Response Process Flow Chart Deploying Computer Security Incident Management
Cyber Security Incident Response Process Flow Chart Deploying Computer Security Incident ManagementThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery.Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Response Process Flow Chart Deploying Computer Security Incident Management. This template helps you present information on Two stages. You can also present information on Agency Reporting, Investigation Scope Determination, Collection Preservation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





