Powerpoint Templates and Google slides for Security Processes
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Reverse Proxy It Process Of Secure Reverse Proxying
Reverse Proxy It Process Of Secure Reverse ProxyingThis slide depicts secure reverse proxying and how it can be established in three ways such as secure client to the proxy, secure proxy to the content server, and the secure client to proxy and secure proxy to a content server. Increase audience engagement and knowledge by dispensing information using Reverse Proxy It Process Of Secure Reverse Proxying. This template helps you present information on five stages. You can also present information on Process Of Secure Reverse Proxying using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Program Cybersecurity Flow Diagram Of Incident Response Process
Information Security Program Cybersecurity Flow Diagram Of Incident Response ProcessMentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Flow Diagram Of Incident Response Process. Dispense information and present a thorough explanation of Flow Diagram Of Incident Response Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Cybersecurity Introducing New Incidents Logging Process
Information Security Program Cybersecurity Introducing New Incidents Logging ProcessThis slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. Present the topic in a bit more detail with this Information Security Program Cybersecurity Introducing New Incidents Logging Process. Use it as a tool for discussion and navigation on Introducing New Incidents Logging Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
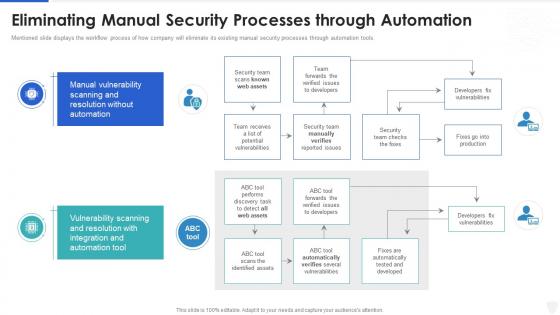
 Information Security Program Eliminating Manual Security Processes Through Automation
Information Security Program Eliminating Manual Security Processes Through AutomationMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver an outstanding presentation on the topic using this Information Security Program Eliminating Manual Security Processes Through Automation. Dispense information and present a thorough explanation of Processes, Automation, Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Embedding Risk Based Approach Product Development Process
Information Security Program Embedding Risk Based Approach Product Development ProcessPurpose of this slide is to highlight the risk based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models. Present the topic in a bit more detail with this Information Security Program Embedding Risk Based Approach Product Development Process. Use it as a tool for discussion and navigation on Product, Development, Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Gap Identification Current Approach Process Flaws And Cost
Information Security Program Gap Identification Current Approach Process Flaws And CostPurpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Present the topic in a bit more detail with this Information Security Program Gap Identification Current Approach Process Flaws And Cost. Use it as a tool for discussion and navigation on Identification, Current Approach, Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Eliminating Manual Security Processes Through Automation Risk Based Methodology To Cyber
Eliminating Manual Security Processes Through Automation Risk Based Methodology To CyberMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools.Present the topic in a bit more detail with this Eliminating Manual Security Processes Through Automation Risk Based Methodology To Cyber Use it as a tool for discussion and navigation on Manual Vulnerability, Scanning And Resolution, Vulnerability Scanning This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Flow Diagram Of Incident Response Process Introducing A Risk Based Approach To Cyber Security
Flow Diagram Of Incident Response Process Introducing A Risk Based Approach To Cyber SecurityMentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down.Present the topic in a bit more detail with this Flow Diagram Of Incident Response Process Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Remediate Eradicate, Contain Mitigate, Consider The Potential This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Introducing New Incidents Logging Process Introducing A Risk Based Approach To Cyber Security
Introducing New Incidents Logging Process Introducing A Risk Based Approach To Cyber SecurityThis slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details.Present the topic in a bit more detail with this Introducing New Incidents Logging Process Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Category Selection, Assigned To Responsible, Provide An Interaction This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan information security process to manage firms sensitive
Building organizational security strategy plan information security process to manage firms sensitiveThis slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Information Security Process To Manage Firms Sensitive. Use it as a tool for discussion and navigation on Information, Process, Sensitive. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan security process to manage firms
Building organizational security strategy plan security process to manage firmsThis slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an outstanding presentation on the topic using this Building Organizational Security Strategy Plan Security Process To Manage Firms. Dispense information and present a thorough explanation of Information, Process, Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Improve it security with vulnerability information and event management logging process
Improve it security with vulnerability information and event management logging processThis slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation Introducing Improve It Security With Vulnerability Information And Event Management Logging Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Information, Management, Process, using this template. Grab it now to reap its full benefits.
-
 Information Security And Iso 27001 Incorporation Isms Framework Into Corporate Control Processes
Information Security And Iso 27001 Incorporation Isms Framework Into Corporate Control ProcessesMentioned slide displays the incorporation of information security management system framework within the corporate control process. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 Incorporation Isms Framework Into Corporate Control Processes. Dispense information and present a thorough explanation of Framework, Corporate, Processes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Credit Card Processing Security Ppt Powerpoint Presentation Portfolio Brochure Cpb
Credit Card Processing Security Ppt Powerpoint Presentation Portfolio Brochure CpbPresenting our Credit Card Processing Security Ppt Powerpoint Presentation Portfolio Brochure Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Credit Card Processing Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Secure Loan Processing Ppt Powerpoint Presentation Show Skills Cpb
Secure Loan Processing Ppt Powerpoint Presentation Show Skills CpbPresenting Secure Loan Processing Ppt Powerpoint Presentation Show Skills Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Secure Loan Processing. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Network Security Process Of Disaster Recovery Planning
Network Security Process Of Disaster Recovery PlanningThis slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Introducing Network Security Process Of Disaster Recovery Planning to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Operations, Processes, Assessment, Perform, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Process Of Disaster Recovery Planning
Information Technology Security Process Of Disaster Recovery PlanningThis slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Introducing Information Technology Security Process Of Disaster Recovery Planning to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Process Of Disaster Recovery Planning, using this template. Grab it now to reap its full benefits.
-
 Siem For Security Analysis Information And Event Management Logging Process
Siem For Security Analysis Information And Event Management Logging ProcessThis slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation Introducing Siem For Security Analysis Information And Event Management Logging Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Information, Management, Process, using this template. Grab it now to reap its full benefits.
-
 Computer Security Technical Assessment Process
Computer Security Technical Assessment ProcessThis slide signifies the technical assessment process on company security. It steps include identify, analyse, prioritize and monitoring. Introducing our premium set of slides with Computer Security Technical Assessment Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify, Analyse, Prioritize, Monitoring. So download instantly and tailor it with your information.
-
 Cyber Security Technical Assessment Process
Cyber Security Technical Assessment ProcessThis slide signifies the technical assessment process of cyber security. It include stages like identify, planning, execution, monitor and closure. Presenting our set of slides with Cyber Security Technical Assessment Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Execution, Closure, Planning, Monitor.
-
 Secure Online Credit Card Processing Ppt Powerpoint Presentation File Backgrounds Cpb
Secure Online Credit Card Processing Ppt Powerpoint Presentation File Backgrounds CpbPresenting Secure Online Credit Card Processing Ppt Powerpoint Presentation File Backgrounds Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Secure Online Credit Card Processing. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Building organizational security strategy plan streamlining employee verification process to ensure
Building organizational security strategy plan streamlining employee verification process to ensureThis slide provides information about streamlining employee verification process at workplace to ensure people security by performing pre and post employee verification. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Streamlining Employee Verification Process To Ensure. Use it as a tool for discussion and navigation on Streamlining, Verification, Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 4 steps of rpa security for process automation improvement
4 steps of rpa security for process automation improvementPresenting our set of slides with 4 Steps Of RPA Security For Process Automation Improvement. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Ensure Accountability, Protect Log Integrity, Enable Secure RPA Development.
-
 Cybersecurity and digital business risk management eliminating manual security processes
Cybersecurity and digital business risk management eliminating manual security processesMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Present the topic in a bit more detail with this Cybersecurity And Digital Business Risk Management Eliminating Manual Security Processes. Use it as a tool for discussion and navigation on Processes, Resolution, Automation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure Online Payment Processing Ppt Powerpoint Presentation Ideas Background Cpb
Secure Online Payment Processing Ppt Powerpoint Presentation Ideas Background CpbPresenting our Secure Online Payment Processing Ppt Powerpoint Presentation Ideas Background Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Secure Online Payment Processing. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Q70 Risk Management Framework For Information Security Incident Management Workflow Process
Q70 Risk Management Framework For Information Security Incident Management Workflow ProcessFollowing slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Present the topic in a bit more detail with this Q70 Risk Management Framework For Information Security Incident Management Workflow Process. Use it as a tool for discussion and navigation on Incident Occurs, Team Takes Action, Auto Alerting, Fail Over Report, Organize Team, Incident Resolution. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Multistep Process Of Security Risk Acceptance
Multistep Process Of Security Risk AcceptanceThis slide shows multistep process of security risk acceptance which contains identifying risk, summarizing risk and risk acceptance and action. This can assist businesses in understanding the cause and effect of risks. Introducing our premium set of slides with Multistep Process Of Security Risk Acceptance. Elucidate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identifying Risk, Summarizing Risk, Risk Acceptance Action. So download instantly and tailor it with your information.
-
 Automatic Technology Steps To Ensure Robotic Process Automation Security
Automatic Technology Steps To Ensure Robotic Process Automation SecurityThis slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development. Introducing Automatic Technology Steps To Ensure Robotic Process Automation Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Guarantee Accountability, Protect Log Respectability, RPA Development, using this template. Grab it now to reap its full benefits.
-
 Pillars Of Cloud Security Process Based Security Cloud Information Security
Pillars Of Cloud Security Process Based Security Cloud Information SecurityThis slide represents the process based security pillar of cloud security. It also shows how it works and what precautions does it take.Increase audience engagement and knowledge by dispensing information using Pillars Of Cloud Security Process Based Security Cloud Information Security This template helps you present information on four stages. You can also present information on Platform Customers, Different Locations, Adaptable Structure using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enterprise Security Operations Processing Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Enterprise Security Operations Processing Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Enterprise security operations processing colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Enterprise Security Operations Processing Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Enterprise Security Operations Processing Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Enterprise security operations processing monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Steps To Ensure Robotic Process Automation Security Robotic Process Automation Types
Steps To Ensure Robotic Process Automation Security Robotic Process Automation TypesThis slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development. Increase audience engagement and knowledge by dispensing information using Steps To Ensure Robotic Process Automation Security Robotic Process Automation Types. This template helps you present information on four stages. You can also present information on Process, Automation, Accountability using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Pillars Of Cloud Security Process Based Security Cloud Computing Security
Pillars Of Cloud Security Process Based Security Cloud Computing SecurityThis slide represents the process based security pillar of cloud security. It also shows how it works and what precautions does it take. Increase audience engagement and knowledge by dispensing information using Pillars Of Cloud Security Process Based Security Cloud Computing Security. This template helps you present information on four stages. You can also present information on End User Systems, Application Lifecycle, Operational Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Roadmap With Process And Tasks
Cyber Security Roadmap With Process And TasksThis slide represent roadmap for various cyber security task and process like response planning ,risk assessment progress in an organization with timeline. It includes hours per week ,owner and start date introducing our Cyber Security Roadmap With Process And Tasks set of slides. The topics discussed in these slides are Roadmap, Process, Assessment. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 PCI Certification For Increasing Security Of Online Transactions Improving Financial Management Process
PCI Certification For Increasing Security Of Online Transactions Improving Financial Management ProcessThis slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Increase audience engagement and knowledge by dispensing information using PCI Certification For Increasing Security Of Online Transactions Improving Financial Management Process. This template helps you present information on three stages. You can also present information on Before PCI Integration, PCI Integration, After Integration Impact using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Advantages And Working Of Secure SDLC Software Development Process
Advantages And Working Of Secure SDLC Software Development ProcessThis slide represents the advantages and working of secure software development life cycle, including its various phases, such as concept, planning, design and development, testing, release, sustain, and disposal. Introducing Advantages And Working Of Secure SDLC Software Development Process to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Security Planning, Existing Development, Design And Development, using this template. Grab it now to reap its full benefits.
-
 Overview And Importance Of Secure SDLC Software Development Process
Overview And Importance Of Secure SDLC Software Development ProcessThis slide depicts the overview and importance of a secure software development life cycle, including how it helps to reduce total software development time and cost. Increase audience engagement and knowledge by dispensing information using Overview And Importance Of Secure SDLC Software Development Process. This template helps you present information on two stages. You can also present information on Importance Of SDL, Overview Of SDL using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Managed Security Service Threat Detection Process
Managed Security Service Threat Detection ProcessThe following slide highlights multistep process of managed security service to mitigate IT risks. It covers step such as operational readiness review, use cases, email notification, security analysis and event resolution. Introducing our premium set of slides with Managed Security Service Threat Detection Process. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Event Resolution, Operational Readiness Review, Email Notification, Security Analysis. So download instantly and tailor it with your information.
-
 Current Security Management Capabilities Overview Iso 27001certification Process
Current Security Management Capabilities Overview Iso 27001certification ProcessFollowing slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an outstanding presentation on the topic using this Current Security Management Capabilities Overview Iso 27001certification Process. Dispense information and present a thorough explanation of Management, Capabilities, Overview using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Iso 27001 Information Security Management Standard Iso 27001certification Process
Iso 27001 Information Security Management Standard Iso 27001certification ProcessDeliver an outstanding presentation on the topic using this Iso 27001 Information Security Management Standard Iso 27001certification Process. Dispense information and present a thorough explanation of Contextual Requirements, Leadership Requirements, Planning Requirements using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Performance Indicators To Measure Information Security Controls Iso 27001certification Process
Performance Indicators To Measure Information Security Controls Iso 27001certification ProcessFollowing slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Deliver an outstanding presentation on the topic using this Performance Indicators To Measure Information Security Controls Iso 27001certification Process. Dispense information and present a thorough explanation of Performance, Measure, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Domains That Will Be Addressed By Isms Iso 27001certification Process
Security Domains That Will Be Addressed By Isms Iso 27001certification ProcessThis slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. Introducing Security Domains That Will Be Addressed By Isms Iso 27001certification Process to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Security Policy, Human Resources Security, Access Control, using this template. Grab it now to reap its full benefits.
-
 Process For Information Security Risk Assessment And Management Plan For Information Security
Process For Information Security Risk Assessment And Management Plan For Information SecurityThis slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets Introducing Process For Information Security Risk Assessment And Management Plan For Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Process, Information, Assessment, using this template. Grab it now to reap its full benefits.
-
 Crm Implementation Process Implementation Steps Enable Data Security
Crm Implementation Process Implementation Steps Enable Data SecurityThis slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Present the topic in a bit more detail with this Crm Implementation Process Implementation Steps Enable Data Security. Use it as a tool for discussion and navigation on Implementation, Authentication, Restrictions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Pillars Of Cloud Security Process Based Security Cloud Data Protection
Pillars Of Cloud Security Process Based Security Cloud Data ProtectionThis slide represents the process-based security pillar of cloud security. It also shows how it works and what precautions does it take. Increase audience engagement and knowledge by dispensing information using Pillars Of Cloud Security Process Based Security Cloud Data Protection. This template helps you present information on four stages. You can also present information on Operational Security, Management, Operations using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Key Steps Of Saas Security Process
Key Steps Of Saas Security ProcessThe following slide depicts the SaaS security process to acknowledge the gap and have proactive approach. It mainly constitutes of three phases discover, monitor and protect. Presenting our set of slides with name Key Steps Of Saas Security Process. This exhibits information on three stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Ascertain Threats And Attacks, Encrypt Sensitive Data, Review Log Activities.
-
 Four Information Technology Security Processes
Four Information Technology Security ProcessesThis slide shows the four step by step processes used in information technology security. It includes penetration testing, VPN configuration, network security audit checklist and privileged password management. Presenting our set of slides with Four Information Technology Security Processes. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Penetration Testing, VPNConfiguration, Network Security Audit.
-
 Security Strategic Planning Process For CPS Cyber Physical Systems In Powerpoint And Google Slides
Security Strategic Planning Process For CPS Cyber Physical Systems In Powerpoint And Google SlidesThis slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Deliver an outstanding presentation on the topic using this Security Strategic Planning Process For CPS Cyber Physical Systems In Powerpoint And Google Slides. Dispense information and present a thorough explanation of Gap Analysis, Prioritization, Environmental Trends using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Process For Cloud Services
Cyber Security Process For Cloud ServicesThe following slide highlights the cyber security process for cloud computing, cloud storage and cloud analytics storage. It depict identification, network security, data safety, application safety, monitoring and policy control to govern, protect and control the cloud services. Introducing our premium set of slides with name Cyber Security Process For Cloud Services. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Security, Policy Control, Monitoring. So download instantly and tailor it with your information.
-
 Process Of Cyber Security Asset Management
Process Of Cyber Security Asset ManagementThe following slide highlights the process of cyber security asset management depicting four steps which include asset inventory, synchronization, security gaps and response to save assets and mitigate the risk in minimum time. Introducing our premium set of slides with name Process Of Cyber Security Asset Management. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Asset Inventory, Synchronization, Response, Security Gaps. So download instantly and tailor it with your information.
-
 Three Layers Of Cyber Security Management Process
Three Layers Of Cyber Security Management ProcessThe following slide highlights the three layers of cyber security management process which are dependent on people, process and technology, it helps company to manage cyber risks such as phishing attacks, data loss and exposed vulnerabilities. Presenting our set of slides with name Three Layers Of Cyber Security Management Process. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on People, Process, Technology.
-
 Business Cyber Security Risk Assessment Process
Business Cyber Security Risk Assessment ProcessThe slide shows cyber threat detection and protection measures in order to eliminate the potential risks to the business. The steps include identifying, detecting, responding, protecting, and recovering. Presenting our set of slides with Business Cyber Security Risk Assessment Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Detect, Respond, Protect.
-
 Security Strategic Planning Process For Cps Intelligent System
Security Strategic Planning Process For Cps Intelligent SystemThis slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Deliver an outstanding presentation on the topic using this Security Strategic Planning Process For Cps Intelligent System. Dispense information and present a thorough explanation of Strategic, Planning, Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Communication Process Framework
Cyber Security Risk Communication Process FrameworkThis slide showcases a model of risk communication process for cyber security. It includes identify issues, set goals, and objectives, community and constraints, stakeholder assessment, communication and engagement tools, implement strategy and evaluate and follow up. Introducing our premium set of slides with Cyber Security Risk Communication Process Framework. Ellicudate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify Issue, Implement Strategy, Identify Messages. So download instantly and tailor it with your information.
-
 Problem Management Process For Enhancing Cyber Security
Problem Management Process For Enhancing Cyber SecurityThis slide signifies increasing cyber security and IT through problem management process. It includes stages like detection, define, investigate, identify resolutions, implement and follow up Introducing our premium set of slides with Problem Management Process For Enhancing Cyber Security. Elucidate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Problem Detection, Define, Investigate, Identify Resolutions, Implement. So download instantly and tailor it with your information.
-
 Process For Information Security Risk Assessment Information Security Risk Management
Process For Information Security Risk Assessment Information Security Risk ManagementThis slide showcases process that can help organization to perform information security risk assessment. It can help to identify security threats and allocate vulnerability rating to information assets. Introducing Process For Information Security Risk Assessment Information Security Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Information Security Threats, Allocating Vulnerability, Risk Assessment, using this template. Grab it now to reap its full benefits.
-
 Business Security Management Four Stage Process
Business Security Management Four Stage ProcessThe purpose of this slide is to outline the risk management procedures in a business organization and to provide desired solutions. This includes four steps- monitor, identify, evaluate and treat. Presenting our set of slides with name Business Security Management Four Stage Process. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Evaluate, Treat, Monitor.
-
 Canva Security Processes And Systems Canva Company Profile Ppt Summary Graphics Tutorials
Canva Security Processes And Systems Canva Company Profile Ppt Summary Graphics TutorialsThis slide highlights the Canva security systems encryption, data security, attack, monitoring, staged releases, secure development, account safety and in app permissions. Introducing Canva Security Processes And Systems Canva Company Profile Ppt Summary Graphics Tutorials to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Secure Development, Monitoring, Data Security, using this template. Grab it now to reap its full benefits.
-
 Process Flow Diagram Depicting Ransomware Incidents Occurrence Security Incident Response Playbook
Process Flow Diagram Depicting Ransomware Incidents Occurrence Security Incident Response PlaybookMentioned slide depicts the incident workflow diagram of a ransomware event. It starts with the threat actors entry and ends with the threat actor demanding ransom. Deliver an outstanding presentation on the topic using this Process Flow Diagram Depicting Ransomware Incidents Occurrence Security Incident Response Playbook. Dispense information and present a thorough explanation of Process, Ransomware, Occurrence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Incident Response Playbook Addressing The Cyber Incident Logging Process
Security Incident Response Playbook Addressing The Cyber Incident Logging ProcessThis slide displays logging process for a cyber incident logging. It covers information about process ID, procedure, its description and owner details. Deliver an outstanding presentation on the topic using this Security Incident Response Playbook Addressing The Cyber Incident Logging Process. Dispense information and present a thorough explanation of Process, Information, Procedure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





