Powerpoint Templates and Google slides for Security Best Practices
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Email Security Best Practices Measures Of Email Account Security For Businesses
Email Security Best Practices Measures Of Email Account Security For BusinessesThe purpose of this slide is to discuss the strategies for businesses to secure the email accounts of their employees. These measures are employee training, implementing email security policies and using email encryption techniques. Introducing Email Security Best Practices Measures Of Email Account Security For Businesses to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Employee Training, Email Security Policies, Email Encryption, using this template. Grab it now to reap its full benefits.
-
 Email Security Best Practices Methods Used By Attackers To Take Over Email Accounts
Email Security Best Practices Methods Used By Attackers To Take Over Email AccountsThe purpose of this slide is to outline the different techniques used by attackers to break into email accounts. These methods are purchasing stolen credentials, brute force attacks, phishing attacks, web browser infections and spyware. Present the topic in a bit more detail with this Email Security Best Practices Methods Used By Attackers To Take Over Email Accounts. Use it as a tool for discussion and navigation on Purchasing Stolen Credentials, Attack Methods, Protective Measures, Web Browser Infections. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Overview Of Email Security Tools And Services
Email Security Best Practices Overview Of Email Security Tools And ServicesThe purpose of this slide is to discuss the tools for implementing email security, along with the services offered by each tool and their respective providers. These tools are integrated online email service, email security gateways, etc. Present the topic in a bit more detail with this Email Security Best Practices Overview Of Email Security Tools And Services. Use it as a tool for discussion and navigation on Email Security Tool, Services Offered, Providers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Popular Email Security Service Providers
Email Security Best Practices Popular Email Security Service ProvidersThis slide demonstrates the various email security tools available for enhancing security against email cyber attacks. The purpose of this slide is to outline the features of different tools, which include threat detection, anti-malware, customizability, etc. Present the topic in a bit more detail with this Email Security Best Practices Popular Email Security Service Providers. Use it as a tool for discussion and navigation on Microsoft Exchange, Proofpoint Email Protection, Mimecast Advanced Email Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Recent Trends In Email Security Technologies
Email Security Best Practices Recent Trends In Email Security TechnologiesThis slide discusses the latest trends in the field of email security advancements. The key components of this slide are machine learning and artificial intelligence, cloud-based email security, zero-trust security and advanced threat protection. Introducing Email Security Best Practices Recent Trends In Email Security Technologies to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Machine Learning And Artificial Intelligence, Cloud-Based Email Security, Zero-Trust Security, Advanced Threat Protection, using this template. Grab it now to reap its full benefits.
-
 Email Security Best Practices Roadmap For Implementing Email Security Policies
Email Security Best Practices Roadmap For Implementing Email Security PoliciesThis slide represents the roadmap to implement email security policies. These include strong password, two-factor authentication, email encryption, software updating, choose a trustworthy email provider, use a VPN Virtual Private Network , etc. Introducing Email Security Best Practices Roadmap For Implementing Email Security Policies to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Two-Factor Authentication, Email Encryption, Trustworthy Email Provider, Virtual Private Network, using this template. Grab it now to reap its full benefits.
-
 Email Security Best Practices Serious Dangers Posed By Malicious Mails
Email Security Best Practices Serious Dangers Posed By Malicious MailsThis slide represents the various threats of malicious emails and their consequences. These include gaining access to private information, infect device with malware, data theft, download more malware and put organizations at risk. Present the topic in a bit more detail with this Email Security Best Practices Serious Dangers Posed By Malicious Mails. Use it as a tool for discussion and navigation on Gain Access To Private Information, Infect Device With Malware, Data Theft. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Steps To Secure Email From Cyber Attacks
Email Security Best Practices Steps To Secure Email From Cyber AttacksThis slide outlines the steps for implementing email security policies to avoid cyber attacks. These include strong password, two-factor authentication, email encryption, software updating, choose a trustworthy email provider, etc. Present the topic in a bit more detail with this Email Security Best Practices Steps To Secure Email From Cyber Attacks. Use it as a tool for discussion and navigation on Two-Factor Authentication, Email Encryption, Virtual Private Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Timeline For Email Security Measures Implementation
Email Security Best Practices Timeline For Email Security Measures ImplementationThis slide shows the timeline for applying email security policies in organization. These include strong password, two-factor authentication, email encryption, software updating, choose a trustworthy email provider, use a VPN Virtual Private Network , etc. Introducing Email Security Best Practices Timeline For Email Security Measures Implementation to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Two-Factor Authentication, Email Encryption, Virtual Private Network, using this template. Grab it now to reap its full benefits.
-
 Email Security Best Practices Types Of Email Encryption For Secure Communication
Email Security Best Practices Types Of Email Encryption For Secure CommunicationThe purpose of this slide is to outline the different types of email encryption protocols used to secure business communication. These techniques are Pretty Good Privacy PGP , Secure Multi-purpose Internet Mail Extension S or MIME, etc. Introducing Email Security Best Practices Types Of Email Encryption For Secure Communication to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Pretty Good Privacy, Secure Multi-Purpose Internet Mail Extension, Transport Layer Security, using this template. Grab it now to reap its full benefits.
-
 Email Security Best Practices Understanding The Concept Of Email Security Process
Email Security Best Practices Understanding The Concept Of Email Security ProcessThis slide demonstrates the email account security process. The purpose of this slide is to highlight the main components of securing email communication, such as email gateway, update, action, continuously reprocess, email provider, etc. Introducing Email Security Best Practices Understanding The Concept Of Email Security Process to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Email Gateway, Email Sent For Security Check, Directs Email To Email Provider, using this template. Grab it now to reap its full benefits.
-
 Email Security Best Practices Warning Signs Of Email Account Compromise
Email Security Best Practices Warning Signs Of Email Account CompromiseThis slide represents the warning signs of email account hacking which results in need of immediate account recovery. These warning signs are inability to access account, password reset notifications, unsolicited messages, strange IP address login, etc. Present the topic in a bit more detail with this Email Security Best Practices Warning Signs Of Email Account Compromise. Use it as a tool for discussion and navigation on Account Access, Password Reset Notifications, Unsolicited Messages. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons Slide For Email Security Best Practices And Solutions
Icons Slide For Email Security Best Practices And SolutionsIntroducing our well researched set of slides titled Icons Slide For Email Security Best Practices And Solutions. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table Of Contents Email Security Best Practices And Solutions
Table Of Contents Email Security Best Practices And SolutionsIntroducing Table Of Contents Email Security Best Practices And Solutions to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Overview And Benefits, Email Security Process, Methods Used By Attackers, Dangers Posed By Malicious Mails, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Email Security Best Practices And Solutions
Table Of Contents For Email Security Best Practices And SolutionsIntroducing Table Of Contents For Email Security Best Practices And Solutions to increase your presentation threshold. Encompassed with thirteen stages, this template is a great option to educate and entice your audience. Dispence information on Market And Trends, Training And Budget, Policies And Best Practices, Execution Plan, using this template. Grab it now to reap its full benefits.
-
 IOT Network Security Best Practices
IOT Network Security Best PracticesThis slide showcases best practices followed to secure IoT networks and devices. Major practices covered are managing devices, updating passwords, and using encryption protocols. Presenting our set of slides with name IOT Network Security Best Practices. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Manage Devices, Update Passwords, Use Encryption Protocols.
-
 Best Practices To Enhance Wireless Lan Security
Best Practices To Enhance Wireless Lan SecurityThis slide represents principles that assist companies to enhance wireless LAN security against unauthorized access and data loss. It includes various principles such as guest Wi-Fi, rogue AP detection, 802.1x authentication vs PSK, etc. Presenting our well structured Best Practices To Enhance Wireless Lan Security The topics discussed in this slide are Rogue AP Detection, Port ConfigurationsThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Best Practices For Building Physical Security System
Best Practices For Building Physical Security SystemThis slide showcases the effective approaches employed for developing physical security system which helps an organization to avoid potential crimes by adding sense of heightened awareness. It include details such as create secure facility,secure business equipment,etc. Presenting our set of slides with Best Practices For Building Physical Security System. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Create Secure Facility,Secure Business Equipment,Avoid Thefts.
-
 Wireless Access Points WAP Best Practices To Secure WAP
Wireless Access Points WAP Best Practices To Secure WAPThis slide outlines the steps for Wireless Access Points security. The purpose of this slide is to highlight the best practices to secure WAP from unauthorized access, and these are enabling firewall and firmware, using VPN and guest network, disabling remote access and WPS, etc. Deliver an outstanding presentation on the topic using this Wireless Access Points WAP Best Practices To Secure WAP. Dispense information and present a thorough explanation of Enable Firewall And Firmware, Use Vpn And Guest Network, Change Default Settings using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 A247 Best Practices For Web Security Implementation
A247 Best Practices For Web Security ImplementationThe purpose of this slide is to highlight the best practices for web security such as inclusive security practices, cybersecurity adoption, etc. Introducing A247 Best Practices For Web Security Implementation to increase your presentation threshold. Encompassed with Seven stages, this template is a great option to educate and entice your audience. Dispence information on Inclusive Security Practices, Diverse Security Measures, Security Exercises, using this template. Grab it now to reap its full benefits.
-
 Supplier Engagement Best Practices To Secure Procurement
Supplier Engagement Best Practices To Secure ProcurementThis slide highlights the best techniques to encourage supplier engagement for securing procurement processes. It includes practices such as encouraging open communication, creating self-service portals, and setting clear expectations. Presenting our set of slides with Supplier Engagement Best Practices To Secure Procurement This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Encourage Open Communication, Set Clear Expectations
-
 Best Practices For Security Saas Applications On Cloud Platform
Best Practices For Security Saas Applications On Cloud PlatformThis slide represents various best practices that assist companies in securing their Software as a Service SaaS applications on cloud platforms enhancing operational efficiency. It includes best practices such as secure product engineering, use virtual private cloud, etc. Presenting our set of slides with Best Practices For Security Saas Applications On Cloud Platform. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secure Product Engineering, Applications, Organization.
-
 Best Practices Icon For Optimizing Saas Security
Best Practices Icon For Optimizing Saas SecurityPresenting our set of slides with Best Practices Icon For Optimizing Saas Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Optimizing Saas, Security.
-
 Saas Best Practices Icon To Optimize Data Migration Security
Saas Best Practices Icon To Optimize Data Migration SecurityIntroducing our Saas Best Practices Icon To Optimize Data Migration Security set of slides. The topics discussed in these slides are Optimize Data, Migration Security, Best Practices. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Best Practices For Saas Security Tools
Best Practices For Saas Security ToolsThis slide represents effective instructions for using SaaS security technologies. It aims to regularly reassess and update security measures to adapt to evolving threats and technologies. It includes various elements such as SaaS security checklist, access management, etc. Presenting our set of slides with Best Practices For Saas Security Tools. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Saas Security Checklist, Access Management, Consistent Penetration Tests.
-
 Best Practices To Ensure Mobile Application Security Mobile Device Security Cybersecurity SS
Best Practices To Ensure Mobile Application Security Mobile Device Security Cybersecurity SSThis slide showcases best practices that can help to improve mobile application security. Its key elements are data encryption, security containers and secure KPIs Increase audience engagement and knowledge by dispensing information using Best Practices To Ensure Mobile Application Security Mobile Device Security Cybersecurity SS This template helps you present information on Three stages. You can also present information on Data Encryption, Secure Apis, Security Containers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Analyzing Cloud Based Service Offerings Best Practices To Improve Data Security
Analyzing Cloud Based Service Offerings Best Practices To Improve Data SecurityThis slide showcases various tips which can be adopted by business to enhance data security of SAAs application. It provides information regarding end to end encryption, application testing, data deletion policy and VPN. Introducing Analyzing Cloud Based Service Offerings Best Practices To Improve Data Security to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on End To End Encryption, Application Testing, Data Deletion Policy, Vpn, using this template. Grab it now to reap its full benefits.
-
 Best Practices Of Effective Network Security
Best Practices Of Effective Network SecurityThis slide displays best practices for companies to deploy network security including multi factor authentication, security awareness training, and cybersecurity risk assessment. Presenting our set of slides with name Best Practices Of Effective Network Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Multi Factor Authentication, Security Awareness Training, Cybersecurity Risk Assessment.
-
 Workplace Safety Dashboard Highlighting Injury Severity Best Practices For Workplace Security
Workplace Safety Dashboard Highlighting Injury Severity Best Practices For Workplace SecurityThis slide highlights the dashboard which showcase the critical incidents, incident cost, injury consequence, type of incident and severity level of the injury.Deliver an outstanding presentation on the topic using this Workplace Safety Dashboard Highlighting Injury Severity Best Practices For Workplace Security. Dispense information and present a thorough explanation of Workplace Safety, Dashboard Highlighting, Injury Severity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Workplace Safety Dashboard To Monitor Incidents Best Practices For Workplace Security
Workplace Safety Dashboard To Monitor Incidents Best Practices For Workplace SecurityThis slide highlights the workplace safety dashboard which showcase incidents per employee, worksite incident total, incidents by total and top injuries by body part.Present the topic in a bit more detail with this Workplace Safety Dashboard To Monitor Incidents Best Practices For Workplace Security. Use it as a tool for discussion and navigation on Incidents Reported, Incidents Employee, Total Incident. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Occupation Of Fatal And Injured Employees Best Practices For Workplace Security
Occupation Of Fatal And Injured Employees Best Practices For Workplace SecurityThis slide highlights the occupation of fatal and injured employees on the organization which showcase machine operator, care worker, maintenance worker, plant operatives and emergency service worker.Deliver an outstanding presentation on the topic using this Occupation Of Fatal And Injured Employees Best Practices For Workplace Security. Dispense information and present a thorough explanation of Implementing Safety, Secure Organization, Instant Assistance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Electronic information security best practices for cloud security
Electronic information security best practices for cloud securityThis slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Increase audience engagement and knowledge by dispensing information using Electronic Information Security Best Practices For Cloud Security. This template helps you present information on six stages. You can also present information on Shared Responsibility Model, Operations Management, Building Controls And Processes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Network Security Monitoring Best Practices Ppt Powerpoint Presentation Template Cpb
Network Security Monitoring Best Practices Ppt Powerpoint Presentation Template CpbPresenting Network Security Monitoring Best Practices Ppt Powerpoint Presentation Template Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Network Security Monitoring Best Practices. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Information Security Best Practices For Cloud Security
Information Security Best Practices For Cloud SecurityThis slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Present the topic in a bit more detail with this Information Security Best Practices For Cloud Security. Use it as a tool for discussion and navigation on Best Practices For Cloud Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Best Practices For Cloud Security
Network Security Best Practices For Cloud SecurityThis slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Deliver an outstanding presentation on the topic using this Network Security Best Practices For Cloud Security. Dispense information and present a thorough explanation of Best Practices For Cloud Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Best Practices For Cloud Security
Information Technology Security Best Practices For Cloud SecurityThis slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Present the topic in a bit more detail with this Information Technology Security Best Practices For Cloud Security. Use it as a tool for discussion and navigation on Operations, Management, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Incident Response Playbook Best Work From Home Data Security Practices
Incident Response Playbook Best Work From Home Data Security PracticesPurpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc. Increase audience engagement and knowledge by dispensing information using Incident Response Playbook Best Work From Home Data Security Practices. This template helps you present information on six stages. You can also present information on System Update, Avoid Using External Device, Communication using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Best Practices Cloud Information Security
Cloud Security Best Practices Cloud Information SecurityThis slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues.Present the topic in a bit more detail with this Cloud Security Best Practices Cloud Information Security Use it as a tool for discussion and navigation on Control Identity, Administrative Rights, Access Systems This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Security Best Practices Cloud Computing Security Ppt Brochure
Cloud Security Best Practices Cloud Computing Security Ppt BrochureThis slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver an outstanding presentation on the topic using this Cloud Security Best Practices Cloud Computing Security Ppt Brochure. Dispense information and present a thorough explanation of Cloud Utilization And Risk, Cloud Protection Issues, Data Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Security Best Practices Cloud Data Protection
Cloud Security Best Practices Cloud Data ProtectionThis slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver an outstanding presentation on the topic using this Cloud Security Best Practices Cloud Data Protection. Dispense information and present a thorough explanation of Cloud Protection Issues, Cloud Service, Infrastructure As A Service using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Safety Practices For Saas Security
Best Safety Practices For Saas SecurityThe following slide illustrates some best practices to ensure and maintain SaaS security. It includes activities such as creating security review checklist, training employees, hiring security service providers, establishing secure infrastructure, protecting data by monitoring etc. Presenting our set of slides with name Best Safety Practices For Saas Security. This exhibits information on five stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Train Employees, Protect Data Monitoring, Establish Secure Infrastructure.
-
 Saas Security Best Practices Icon
Saas Security Best Practices IconIntroducing our premium set of slides with Saas Security Best Practices Icon. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Saas, Security Best, Practices Icon. So download instantly and tailor it with your information.
-
 Best Practices To Manage Cyber Security Of Organization
Best Practices To Manage Cyber Security Of OrganizationThis slide shows various practices which can be used to by organizations to manage information technology security. These practices are monitor, risk plan, security protocols and use technology. Introducing our premium set of slides with Best Practices To Manage Cyber Security Of Organization. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Success Rate, Security Protocols, Use Technology. So download instantly and tailor it with your information.
-
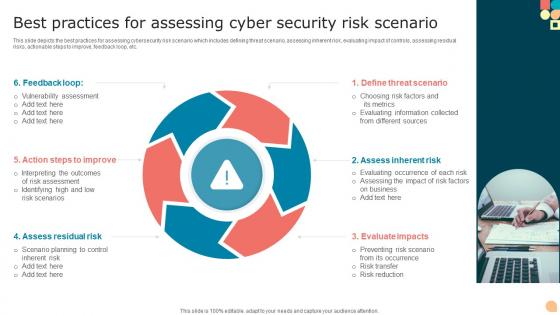 Best Practices For Assessing Cyber Security Risk Scenario
Best Practices For Assessing Cyber Security Risk ScenarioThis slide depicts the best practices for assessing cybersecurity risk scenario which includes defining threat scenario, assessing inherent risk, evaluating impact of controls, assessing residual risks, actionable steps to improve, feedback loop, etc. Introducing our premium set of slides with Best Practices For Assessing Cyber Security Risk Scenario. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Feedback Loop, Define Threat Scenario, Assess Inherent Risk. So download instantly and tailor it with your information.
-
 Best Work From Home Data Security Practices Security Incident Response Playbook
Best Work From Home Data Security Practices Security Incident Response PlaybookPurpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc. Introducing Best Work From Home Data Security Practices Security Incident Response Playbook to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on System Update, Communication, External Devices, using this template. Grab it now to reap its full benefits.
-
 Best Practices To Secure Internet Of Things Gateway
Best Practices To Secure Internet Of Things GatewayThe following slide showcases best practices to secure IOT gateway that are device establishment, establishing strong identity and provide identity to ecosystem. Introducing our premium set of slides with Best Practices To Secure Internet Of Things Gateway. Elucidate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Gateway Device Establishment, Establish Strong, Gateway To Provide Identity. So download instantly and tailor it with your information.
-
 Enterprise Security Operation Center Best Practices
Enterprise Security Operation Center Best PracticesThis slide covers enterprise security operation center best practices. It involves practices such as setting up right time, align strategy with business goals, leverage best tools and continuously monitor network. Presenting our well structured Enterprise Security Operation Center Best Practices. The topics discussed in this slide are Leverage Best Tools, Continuously Monitor Network, Business Goals. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Strategy Best Practices To Defend Against Threats
Cyber Security Strategy Best Practices To Defend Against ThreatsThis slide represents cyber security strategy best practices to defend against threats such a development of insider threat program, training employees, maintaining compliance etc. Presenting our set of slides with name Cyber Security Strategy Best Practices To Defend Against Threats. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Training Employees, Initiating Phishing Stimulations, Maintaining Compliance.
-
 Best It And Data Security Practices
Best It And Data Security PracticesThe following slide highlights the best practices to protect the business from security threats. It includes activities such as installing and upgrading protective software, adopting strong password policy, applying multi layer authentication etc. Presenting our set of slides with Best It And Data Security Practices. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Make Regular Backups, Strong Password Policy, Protective Software.
-
 Best Work From Home Data Security Practices Cybersecurity Incident And Vulnerability
Best Work From Home Data Security Practices Cybersecurity Incident And VulnerabilityPurpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc. Introducing Best Work From Home Data Security Practices Cybersecurity Incident And Vulnerability to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Configure WIFI Encryption, Avoid Using External Devices, System Update, using this template. Grab it now to reap its full benefits.
-
 Information Security Governance Best Practices
Information Security Governance Best PracticesThis slide presents various best practices for information security governance to effectively manage and mitigate IT risks. It includes key practices such as reflect business objectives, develop and enforce security program, embrace organizations culture, etc. Presenting our set of slides with Information Security Governance Best Practices. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Develop, Enforce Security Program.
-
 Best Work From Home Data Security Practices Upgrading Cybersecurity With Incident Response Playbook
Best Work From Home Data Security Practices Upgrading Cybersecurity With Incident Response PlaybookPurpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc. Introducing Best Work From Home Data Security Practices Upgrading Cybersecurity With Incident Response Playbook to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Communication, Attachments, Department, using this template. Grab it now to reap its full benefits.
-
 Best Practices For Optimising IoT Healthcare Security Effective IoT Device Management IOT SS
Best Practices For Optimising IoT Healthcare Security Effective IoT Device Management IOT SSThis slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc.Introducing Best Practices For Optimising IoT Healthcare Security Effective IoT Device Management IOT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Exchanged Platforms, Administer Private, Patients Communicate, using this template. Grab it now to reap its full benefits.
-
 Best Practices For Healthcare Iot Security Implementing Iot Devices For Care Management IOT SS
Best Practices For Healthcare Iot Security Implementing Iot Devices For Care Management IOT SSFollowing slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc. Present the topic in a bit more detail with this Best Practices For Healthcare Iot Security Implementing Iot Devices For Care Management IOT SS. Use it as a tool for discussion and navigation on Attack Surface Visibility, Segregated Internal Networking, Zero Trust Approach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Serverless Computing Best Practices For Improving Serverless Application Security
Serverless Computing Best Practices For Improving Serverless Application SecurityThe purpose of this slide is to discuss the best practices to enhance the security of serverless applications. These are safeguard critical data, add an incident response strategy, use appropriate security logging and dependence on external parties. Increase audience engagement and knowledge by dispensing information using Serverless Computing Best Practices For Improving Serverless Application Security. This template helps you present information on four stages. You can also present information on Safeguard Critical Data, Appropriate Security Logging, Dependence On External Parties, Serverless Application Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Online Security Best Practices In Powerpoint And Google Slides Cpb
Online Security Best Practices In Powerpoint And Google Slides CpbPresenting Online Security Best Practices In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Online Security Best Practices. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Comprehensive Guide For Successful Best Practices For Website Security Management
Comprehensive Guide For Successful Best Practices For Website Security ManagementFollowing slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc. Increase audience engagement and knowledge by dispensing information using Comprehensive Guide For Successful Best Practices For Website Security Management. This template helps you present information on four stages. You can also present information on Implement Anti Malware Programs, Run Regular Backups, Use Secure Plugins using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Supply Chain Security Best Practices
Supply Chain Security Best PracticesThe following slide highlights best practices for supply chain security to evaluate risks, protect important business data etc. It includes components such as vulnerability mitigation, security strategy assessment, digitization and data identification. Presenting our set of slides with Supply Chain Security Best Practices This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Risk Reduction, Manage Vulnerabilities.
-
 Three Network Security Management Best Practices In Powerpoint And Google Slides Cpb
Three Network Security Management Best Practices In Powerpoint And Google Slides CpbPresenting our Three Network Security Management Best Practices In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Three Network Security Management Best Practices. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Best Practices To Design Secure Blockchain Crypto Wallet
Best Practices To Design Secure Blockchain Crypto WalletThis slides depicts key tactics to develop efficient crypto wallet. It includes various practices such as understanding users, implementing security measures, following standards and regulations, testing and iteration. Presenting our set of slides with Best Practices To Design Secure Blockchain Crypto Wallet. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Understand Users, Implement Security Measures.





