Powerpoint Templates and Google slides for Security Best Practices
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Devsecops Best Practices For Secure Applications Powerpoint Presentation Slides
Devsecops Best Practices For Secure Applications Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Devsecops Best Practices For Secure Applications Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the ninety six slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Hands On Blockchain Security Risk Management And Best Practices BCT CD V
Hands On Blockchain Security Risk Management And Best Practices BCT CD VDeliver an informational PPT on various topics by using this Hands On Blockchain Security Risk Management And Best Practices BCT CD V. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with seventy seven slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
-
 Email Security Best Practices And Solutions Powerpoint Presentation Slides
Email Security Best Practices And Solutions Powerpoint Presentation SlidesWhile your presentation may contain top-notch content, if it lacks visual appeal, you are not fully engaging your audience. Introducing our Email Security Best Practices And Solutions Powerpoint Presentation Slides deck, designed to engage your audience. Our complete deck boasts a seamless blend of Creativity and versatility. You can effortlessly customize elements and color schemes to align with your brand identity. Save precious time with our pre-designed template, compatible with Microsoft versions and Google Slides. Plus, it is downloadable in multiple formats like JPG, JPEG, and PNG. Elevate your presentations and outshine your competitors effortlessly with our visually stunning 100 percent editable deck.
-
 Best Practices For Workplace Security Powerpoint Presentation Slides
Best Practices For Workplace Security Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Best Practices For Workplace Security Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fifty nine slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Best Practices For Operational Security OPSEC Training Ppt
Best Practices For Operational Security OPSEC Training PptPresenting Best Practices for Operational Security OPSEC. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
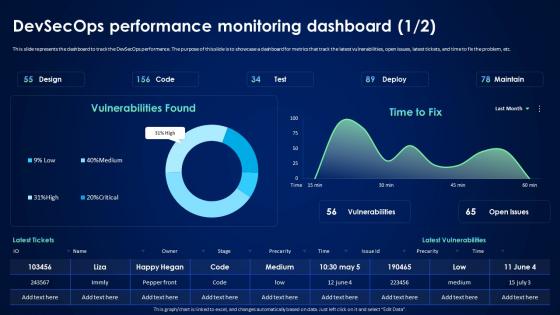 Devsecops Best Practices For Secure Devsecops Performance Monitoring Dashboard
Devsecops Best Practices For Secure Devsecops Performance Monitoring DashboardThis slide represents the dashboard to track the DevSecOps performance. The purpose of this slide is to showcase a dashboard for metrics that track the latest vulnerabilities, open issues, latest tickets, and time to fix the problem, etc. Deliver an outstanding presentation on the topic using this Devsecops Best Practices For Secure Devsecops Performance Monitoring Dashboard. Dispense information and present a thorough explanation of Devsecops Performance, Monitoring Dashboard, Track The Latest Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Best Practices For Firewall Security Management
Firewall Network Security Best Practices For Firewall Security ManagementThis slide outlines the checklist for managing firewall protection effectively. The purpose of this slide is to showcase the different best practices that businesses should keep in mind while managing a firewall, including automating firewall updates, regular firewall security audits, creating and optimizing network-based firewall policies, etc. Present the topic in a bit more detail with this Firewall Network Security Best Practices For Firewall Security Management Use it as a tool for discussion and navigation on Automate Firewall Updates, Security Audits This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure Challenges With Devsecops Implementation And Solutions
Devsecops Best Practices For Secure Challenges With Devsecops Implementation And SolutionsThis slide explain the various limitations with DevSecOps and its solution. The purpose of this slide is to discuss the solutions provided to different challenges associated with DevSecOps. These include late sage security integration, tool integration and complexity, security awareness and training, etc. Deliver an outstanding presentation on the topic using this Devsecops Best Practices For Secure Challenges With Devsecops Implementation And Solutions. Dispense information and present a thorough explanation of Security Awareness And Training, Continuous Monitoring And Compliance, Managing Security Debt using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Devsecops Best Practices For Secure Key Elements Of Successful Devsecops Implementation
Devsecops Best Practices For Secure Key Elements Of Successful Devsecops ImplementationThe slide discusses the critical elements for the successful implementation of DevSecOps. The purpose of this slide is to explain the various features that are integrated automated testing into a pipeline, automated deployment, infrastructure as code, etc. Introducing Devsecops Best Practices For Secure Key Elements Of Successful Devsecops Implementation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Infrastructure As Code, Integrate Security Testing Into Workflows, Automated Deployment, Devsecops Implementation, using this template. Grab it now to reap its full benefits.
-
 Devsecops Best Practices For Secure Key Processes Followed In Devsecops Model
Devsecops Best Practices For Secure Key Processes Followed In Devsecops ModelThis slide discusses the various processes followed in DevSecOps. The purpose of this slide is to highlight the processes, including code analysis, change management, compliance management, threat modelling and security training. Increase audience engagement and knowledge by dispensing information using Devsecops Best Practices For Secure Key Processes Followed In Devsecops Model. This template helps you present information on five stages. You can also present information on Code Analysis, Change Management, Compliance Managements, Threat Modelling using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Devsecops Best Practices For Secure Training Budget Of Devsecops Process For Customers
Devsecops Best Practices For Secure Training Budget Of Devsecops Process For CustomersThis slide showcases the breakdown cost for the DevSecOps installation and management training for the customers. The purpose of this slide is to showcase the training cost breakdown for different components such as instructor cost, training cost, etc. Present the topic in a bit more detail with this Devsecops Best Practices For Secure Training Budget Of Devsecops Process For Customers. Use it as a tool for discussion and navigation on Training Budget, Devsecops Process For Customers, Instructor Cost, Training Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure World Wide Market Size Of Devsecops Process
Devsecops Best Practices For Secure World Wide Market Size Of Devsecops ProcessThis slide depicts the global market size of DevSecOps. The purpose of this slide is to highlight the holistic evolution of the market from 2022 to 2030 in terms of the estimated market value, projected market value, and compound annual growth rate. Present the topic in a bit more detail with this Devsecops Best Practices For Secure World Wide Market Size Of Devsecops Process. Use it as a tool for discussion and navigation on Global Market Size Devsecops, Holistic Evolution, Projected Market Value, Compound Annual Growth Rate. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Content For Devsecops Best Practices For Secure Applications
Table Of Content For Devsecops Best Practices For Secure ApplicationsIntroducing Table Of Content For Devsecops Best Practices For Secure Applications to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Pipeline Security Stages, Devsecops Model Process, Continuous Process Improvement For Efficiency, Market Analysis, using this template. Grab it now to reap its full benefits.
-
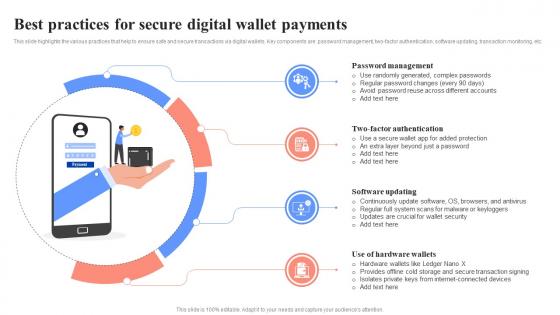 Best Practices For Secure Digital Wallet Payments Unlocking Digital Wallets All You Need Fin SS
Best Practices For Secure Digital Wallet Payments Unlocking Digital Wallets All You Need Fin SSThis slide highlights the various practices that help to ensure safe and secure transactions via digital wallets. Key components are password management, two-factor authentication, software updating, transaction monitoring, etc. Introducing Best Practices For Secure Digital Wallet Payments Unlocking Digital Wallets All You Need Fin SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Password Management, Two-Factor Authentication, Software Updating, using this template. Grab it now to reap its full benefits.
-
 A60 Email Security Best Practices And Email Security Vendor Market Share
A60 Email Security Best Practices And Email Security Vendor Market ShareThis slide represents the market of different email security service providers available in the market. The purpose of this slide is to depict the market share of each of the service providers, such as Symantec, Microsoft, Google, Mimecast, etc. Present the topic in a bit more detail with this A60 Email Security Best Practices And Email Security Vendor Market Share. Use it as a tool for discussion and navigation on Microsoft Accounts, Email Security Market. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Advanced Email Security Management Dashboard
Email Security Best Practices Advanced Email Security Management DashboardThis slide represents the dashboard to track email security incident management process. The purpose of this slide is to provide a graphical representation of email traffic, mitigation summary, unsolicited emails, advanced threat prevention, etc. Present the topic in a bit more detail with this Email Security Best Practices Advanced Email Security Management Dashboard. Use it as a tool for discussion and navigation on Email Traffic, Blocked Summary, Mitigation Summary, Advanced Threat Prevention, Data Loss Prevention, Unsolicited Emails. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Benefits Of Using Email Security Technologies
Email Security Best Practices Benefits Of Using Email Security TechnologiesThis slide outlines the advantages of email security. These include control device access, identify suspicious user behaviour, improve spam and phishing protection, maintain communication confidentiality, protection against zero-day threats, real-time threat protection, etc. Present the topic in a bit more detail with this Email Security Best Practices Benefits Of Using Email Security Technologies. Use it as a tool for discussion and navigation on Control Device Access, Identify Suspicious User Behaviour, Real-Time Threat Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Common Types Of Email Security Attacks
Email Security Best Practices Common Types Of Email Security AttacksThe purpose of this slide is to discuss the different types of email security threats in current digital era. These email security attacks are phishing, social engineering, spear phishing, ransomware, malware and spoofing. Introducing Email Security Best Practices Common Types Of Email Security Attacks to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Phishing, Social Engineering, Spear Phishing, Ransomware, using this template. Grab it now to reap its full benefits.
-
 Email Security Best Practices Estimated Cost For Email Security Training Program
Email Security Best Practices Estimated Cost For Email Security Training ProgramThis slide shows the cost breakup of email security training program for beginners. The purpose of this slide is to highlight the estimated cost of various training components, such as instructors cost, training material cost, etc. Present the topic in a bit more detail with this Email Security Best Practices Estimated Cost For Email Security Training Program. Use it as a tool for discussion and navigation on Training Cost Distribution, Instructors Cost, Training Material Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Global Email Security Market Forecast
Email Security Best Practices Global Email Security Market ForecastThis slide demonstrates the global market share of email security. The key components of this slide are email security market size, regional analysis, component segment overview of products and services, etc. Present the topic in a bit more detail with this Email Security Best Practices Global Email Security Market Forecast. Use it as a tool for discussion and navigation on Market Size, Overview, Regional Analysis, Component Segment Overview. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices To Secure GAN Generated Data Generative Adversarial Network AI SS
Best Practices To Secure GAN Generated Data Generative Adversarial Network AI SSThis slide provides information regarding best practices to enable the security of GAN-generated data through the use of encryption, application of watermarking, and deployment of access control. Introducing Best Practices To Secure GAN-Generated Data Generative Adversarial Network AI SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Usage Of Encryption, Application Of Watermarking, Deploy Access Control, using this template. Grab it now to reap its full benefits.
-
 Data security it best practices for cloud security ppt slides portfolio
Data security it best practices for cloud security ppt slides portfolioThis slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Deliver an outstanding presentation on the topic using this Data Security IT Best Practices For Cloud Security Ppt Slides Portfolio. Dispense information and present a thorough explanation of Operations Management, Building Controls And Processes, Data Encryption, Security And Compliance Monitoring using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention Best Practices To Prevent Data Security Breach
Data Breach Prevention Best Practices To Prevent Data Security BreachThis slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management. Increase audience engagement and knowledge by dispensing information using Data Breach Prevention Best Practices To Prevent Data Security Breach. This template helps you present information on five stages. You can also present information on Prioritize Cybersecurity Openings, Resolve Prioritized Threats, Review Data Access Authorizations using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices For Secure Web Gateway Implementation Network Security Using Secure Web Gateway
Best Practices For Secure Web Gateway Implementation Network Security Using Secure Web GatewayThis slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc. Deliver an outstanding presentation on the topic using this Best Practices For Secure Web Gateway Implementation Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Implementation, Assessment, Functionality using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices For Effective Endpoint Security Delivering ICT Services For Enhanced Business Strategy SS V
Best Practices For Effective Endpoint Security Delivering ICT Services For Enhanced Business Strategy SS VThis slide represents best practices for effective endpoint security. It covers educating users, finding and tracking business-owned devices, and installation maintenance of operating systems. Increase audience engagement and knowledge by dispensing information using Best Practices For Effective Endpoint Security Delivering ICT Services For Enhanced Business Strategy SS V. This template helps you present information on three stages. You can also present information on Educate Users, Find And Track Devices, Operating System using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Iot Gateway Security Best Practices Introduction To Internet Of Things IoT SS
Iot Gateway Security Best Practices Introduction To Internet Of Things IoT SSThis slide highlights ways to secure IoT gateway to eliminate data breach and leakage. Some of the best practices include edge based security, decentralised infrastructure, performance assessment, and gateway updates. Introducing Iot Gateway Security Best Practices Introduction To Internet Of Things IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Edge Based Security, Decentralised Infrastructure, using this template. Grab it now to reap its full benefits.
-
 Iot Security Best Practices To Secure Connected Introduction To Internet Of Things IoT SS
Iot Security Best Practices To Secure Connected Introduction To Internet Of Things IoT SSThis slide includes best practices to secure overall infrastructure from potential threats. These best practices include device authentication, data encryption, firmware updates, and network segmentation. Introducing Iot Security Best Practices To Secure Connected Introduction To Internet Of Things IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Device Authentication, Data Encryption, using this template. Grab it now to reap its full benefits.
-
 Implementation Of Information Best Practices For Effective Endpoint Security Strategy SS V
Implementation Of Information Best Practices For Effective Endpoint Security Strategy SS VThis slide represents best practices for effective endpoint security. It covers educating users finding and tracking business owned devices and installation maintenance of operating systems. Increase audience engagement and knowledge by dispensing information using Implementation Of Information Best Practices For Effective Endpoint Security Strategy SS V. This template helps you present information on three stages. You can also present information on Educate Users, Installation Maintenance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Storage Area Network San Best Practices For Storage Area Network Security
Storage Area Network San Best Practices For Storage Area Network SecurityThis Slide Outlines The Best Practices To Secure A Storage Area Network For An Organization. The Purpose Of This Slide Is To Showcase The Various Steps Businesses Should Take To Protect The SAN Network, Including Data Encryption, Installation Of Intrusion Detection And Prevention Systems, And So On. Present The Topic In A Bit More Detail With This Storage Area Network San Best Practices For Storage Area Network Security. Use It As A Tool For Discussion And Navigation On Protection, Techniques, Alternative Data . This Template Is Free To Edit As Deemed Fit For Your Organization. Therefore Download It Now.
-
 Best Practices For Security Awareness Communication Plan
Best Practices For Security Awareness Communication PlanThe slide showcases best practices involved in security awareness communication plan. It presents points such as develop transparent approach, link metrics, keep it simple, etc. Presenting our set of slides with Best Practices For Security Awareness Communication Plan. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security, Communication, Approach.
-
 Security Policy Best Practices In Powerpoint And Google Slides Cpb
Security Policy Best Practices In Powerpoint And Google Slides CpbPresenting Security Policy Best Practices In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Policy Best Practices. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Secure Web Application Development Best Practices
Secure Web Application Development Best PracticesThis slide represents best practices of web application development in a secure way. It includes various practices such as maintain security, being paranoid, encrypt data, use exception management, apply access control, etc Presenting our set of slides with Secure Web Application Development Best Practices. This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Maintain Security, Encrypt Data, Use Exception Management.
-
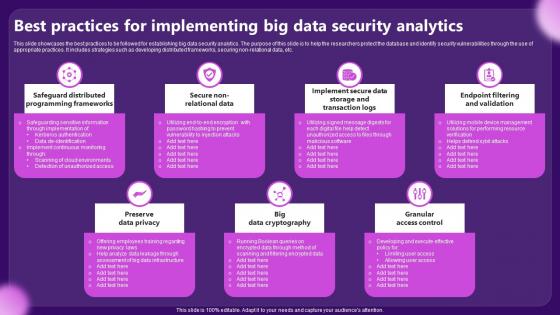 Best Practices For Implementing Big Data Security Analytics
Best Practices For Implementing Big Data Security AnalyticsThis slide showcases the best practices to be followed for establishing big data security analytics. The purpose of this slide is to help the researchers protect the database and identify security vulnerabilities through the use of appropriate practices. It includes strategies such as developing distributed frameworks, securing non relational data, etc. Presenting our set of slides with Best Practices For Implementing Big Data Security Analytics. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Preserve Data Privacy, Granular Access Control.
-
 Best Practices For Network Security Management Plan
Best Practices For Network Security Management PlanThos slide showcases the best practices to be followed for establishing a network security management plan. The purpose of this slide is to help the business develop suitable network security in order to avoid breaches and attacks. It includes conducting regular data backups, frequent employee training, etc.Introducing our premium set of slides with Best Practices For Network Security Management Plan. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Implement Formal, Information Security, Governance Framework. So download instantly and tailor it with your information.
-
 Party Vendor Management Security Best Practices In Powerpoint And Google Slides Cpb
Party Vendor Management Security Best Practices In Powerpoint And Google Slides CpbPresenting Party Vendor Management Security Best Practices In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Party Vendor Management Security Best Practices. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Comprehensive Guide To Understand Five Best Practices To Secure Bitcoin Fin SS
Comprehensive Guide To Understand Five Best Practices To Secure Bitcoin Fin SSThis slide shows details about best practices which can be adopted by Bitcoin holders to secure accounts against frauds. These tips includes hardware wallets, two factor authentication, strong passwords, etc. Introducing Comprehensive Guide To Understand Five Best Practices To Secure Bitcoin Fin SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Hardware Wallet, Two Factor Authentication, Strong Passwords, Update Software, using this template. Grab it now to reap its full benefits.
-
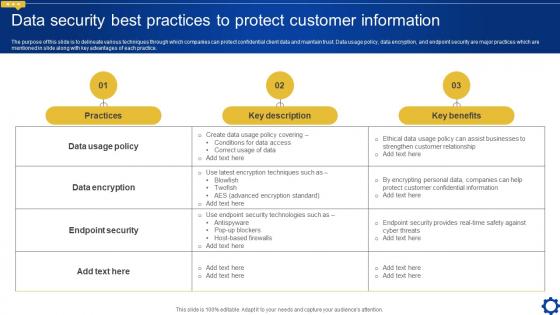 Data Security Best Practices To Protect Customer Creating Personalized Marketing Messages MKT SS V
Data Security Best Practices To Protect Customer Creating Personalized Marketing Messages MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Present the topic in a bit more detail with this Data Security Best Practices To Protect Customer Creating Personalized Marketing Messages MKT SS V. Use it as a tool for discussion and navigation on Practices, Key Description, Key Benefits. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Security Best Practices To Developing Targeted Marketing Campaign MKT SS V
Data Security Best Practices To Developing Targeted Marketing Campaign MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Increase audience engagement and knowledge by dispensing information using Data Security Best Practices To Developing Targeted Marketing Campaign MKT SS V. This template helps you present information on four stages. You can also present information on Policy, Encryption, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
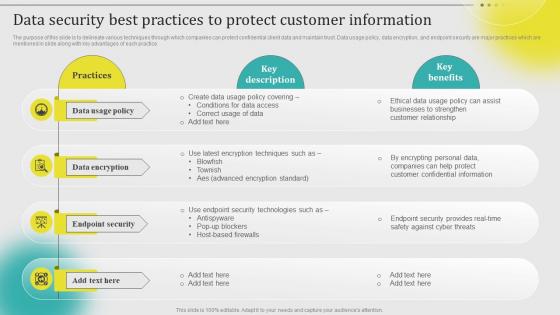 Data Security Best Practices To Protect Customer Information Leveraging Customer Data MKT SS V
Data Security Best Practices To Protect Customer Information Leveraging Customer Data MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Introducing Data Security Best Practices To Protect Customer Information Leveraging Customer Data MKT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Data Usage Policy, Data Encryption, Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Best Practices To Implement Cloud Access Security Broker
Cloud Access Security Broker CASB V2 Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a Cloud Access Security Broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Best Practices To Implement Cloud Access Security Broker. Dispense information and present a thorough explanation of Cloud Access Security Broker, Business Operations, Building Visibility, Forecasting Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices For Security Compliance Management
Best Practices For Security Compliance ManagementThis slide shows best practices for security compliance helps to improve security posture, minimize exposure to non compliance risks. It further includes practices such as develop risk assessment plan, promote team communication etc. Presenting our set of slides with Best Practices For Security Compliance Management. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Develop Risk Assessment Plan, Promote Team Communication.
-
 Best Practices For ERP Security Management
Best Practices For ERP Security ManagementThis slide showcases the best practices available to manage ERP security. Its aim is to optimise human and technological resources to secure against threats. This slide includes service level agreement, audits, monitoring, encryption, etc. Presenting our set of slides with Best Practices For ERP Security Management. This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Level Agreement, Domain Based ERP, Third Party Audits.
-
 Data Security Best Practices To Protect Complete Introduction To Database MKT SS V
Data Security Best Practices To Protect Complete Introduction To Database MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Increase audience engagement and knowledge by dispensing information using Data Security Best Practices To Protect Complete Introduction To Database MKT SS V. This template helps you present information on four stages. You can also present information on Policy, Encryption, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies Best Practices To Implement Suitable Security Protocol Into Network
Encryption Implementation Strategies Best Practices To Implement Suitable Security Protocol Into NetworkThe purpose of this slide is to outline the steps involved in implementing a security protocol into a network. These are access network requirements, plan and design, select the right protocol, prepare the network infrastructure, configure devices, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Best Practices To Implement Suitable Security Protocol Into Network. Dispense information and present a thorough explanation of Assess Network Requirements, Implement User Authentication, Suitable Security Protocol using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Security Best Practices To Protect Customer Database Marketing Strategies MKT SS V
Data Security Best Practices To Protect Customer Database Marketing Strategies MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Introducing Data Security Best Practices To Protect Customer Database Marketing Strategies MKT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Data Usage Policy, Data Encryption, using this template. Grab it now to reap its full benefits.
-
 Serverless Computing V2 Best Practices For Improving Serverless Application Security
Serverless Computing V2 Best Practices For Improving Serverless Application SecurityThe purpose of this slide is to discuss the best practices to enhance the security of serverless applications. These are safeguard critical data, add an incident response strategy, use appropriate security logging and dependence on external parties. Introducing Serverless Computing V2 Best Practices For Improving Serverless Application Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Safeguard Critical Data, Incident Response Strategy, Serverless Application Security, Appropriate Security Logging, using this template. Grab it now to reap its full benefits.
-
 Best Practices To Evaluate SASE Solutions Cloud Security Model
Best Practices To Evaluate SASE Solutions Cloud Security ModelThis slide represents the best practices to evaluate secure access service edge solutions. The purpose of this slide is to demonstrate the various considerations businesses should keep in mind while choosing and implementing a SASE solution. Present the topic in a bit more detail with this Best Practices To Evaluate SASE Solutions Cloud Security Model. Use it as a tool for discussion and navigation on Practices, Evaluate, Solutions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices To Implement Cloud Access Security Broker Cloud Security Model
Best Practices To Implement Cloud Access Security Broker Cloud Security ModelThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker Cloud Security Model. Dispense information and present a thorough explanation of Implement, Practices, Visibility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Secure And Use Comprehensive Guide To Blockchain Wallets And Applications BCT SS
Best Practices To Secure And Use Comprehensive Guide To Blockchain Wallets And Applications BCT SSThis slide covers tips to increase security of paper wallets for using it effectively. The purpose of this template is to provide recommendations such as using reputable tools or websites, encrypting private keys with strong passphrase, creating multiple copies of paper wallets, testing and verifying paper wallet, etc. Present the topic in a bit more detail with this Best Practices To Secure And Use Comprehensive Guide To Blockchain Wallets And Applications BCT SS. Use it as a tool for discussion and navigation on Passphrase, Cryptocurrency, Locations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Analytics Best Practices
Cyber Security Analytics Best PracticesThe following slide highlights firewall protection, security software, strong password enforcement, two factor authentication, and regular data backup to emphasize cybersecurity analytics best practices. It helps organizations fortify defenses and safeguard sensitive information from cyber threats. Introducing our premium set of slides with Cyber Security Analytics Best Practices. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Protection, Software, Passwords. So download instantly and tailor it with your information.
-
 Sase Security Best Practices To Evaluate Sase Solutions
Sase Security Best Practices To Evaluate Sase SolutionsThis slide represents the best practices to evaluate secure access service edge solutions. The purpose of this slide is to demonstrate the various considerations businesses should keep in mind while choosing and implementing a SASE solution. Present the topic in a bit more detail with this Sase Security Best Practices To Evaluate Sase Solutions. Use it as a tool for discussion and navigation on Evaluate, Solutions, Considerations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Best Practices To Implement Cloud Access Security Broker
Sase Security Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Sase Security Best Practices To Implement Cloud Access Security Broker. Dispense information and present a thorough explanation of Implementing, Solutions, Consumption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Evaluate Sase Solutions Secure Access Service Edge Sase
Best Practices To Evaluate Sase Solutions Secure Access Service Edge SaseThis slide represents the best practices to evaluate secure access service edge solutions. The purpose of this slide is to demonstrate the various considerations businesses should keep in mind while choosing and implementing a SASE solution. Present the topic in a bit more detail with this Best Practices To Evaluate Sase Solutions Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Solutions, Demonstrate, Considerations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices To Implement Cloud Access Security Broker Secure Access Service Edge Sase
Best Practices To Implement Cloud Access Security Broker Secure Access Service Edge SaseThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Consumption, Implementing, Solutions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Plan To Implement Best Practices For Effective Endpoint Security Strategy SS V
Strategic Plan To Implement Best Practices For Effective Endpoint Security Strategy SS VThis slide represents best practices for effective endpoint security. It covers educating users, finding and tracking business-owned devices, and installation maintenance of operating systems. Increase audience engagement and knowledge by dispensing information using Strategic Plan To Implement Best Practices For Effective Endpoint Security Strategy SS V This template helps you present information on Three stages. You can also present information on Educate Users, Find And Track Devices using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices To Make IoT Security Improving IoT Device Cybersecurity IoT SS
Best Practices To Make IoT Security Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to exhibit various strategies which can be used to make Internet of Things IoT cyber security awareness training more interactive. The strategies highlighted in slide are gamification, personalization, using high quality content, etc. Introducing Best Practices To Make IoT Security Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Variety, Personalization, Gamification, using this template. Grab it now to reap its full benefits.
-
 Execute Best Practices Of Patch Management Solutions Improving Cyber Security Risks Management
Execute Best Practices Of Patch Management Solutions Improving Cyber Security Risks ManagementThe following slide highlights some tips to execute patch management. It includes elements such as drafting policy, manage data and application, determining vendor updates, scanning vulnerabilities, ranking patches etc. Deliver an outstanding presentation on the topic using this Execute Best Practices Of Patch Management Solutions Improving Cyber Security Risks Management. Dispense information and present a thorough explanation of Draft Patch Policy, Manage Data And Application, Determine Vendor Updates using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implement Best Practices To Prevent Cyber Attacks Improving Cyber Security Risks Management
Implement Best Practices To Prevent Cyber Attacks Improving Cyber Security Risks ManagementThe following slide illustrates some best practices to execute preventive actions for cyber attacks. It includes elements such as train employees, updating systems and software, developing incident response plan, backing up data, maintaining compliance etc. Increase audience engagement and knowledge by dispensing information using Implement Best Practices To Prevent Cyber Attacks Improving Cyber Security Risks Management. This template helps you present information on six stages. You can also present information on Train Employees, Maintain Compliance, Develop Incident Response Plan using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices To Implement Cloud Access Security Broker SASE Network Security
Best Practices To Implement Cloud Access Security Broker SASE Network SecurityThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker SASE Network Security. Dispense information and present a thorough explanation of Visibility, Risk, Release using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE Network Security Best Practices To Evaluate SASE Solutions
SASE Network Security Best Practices To Evaluate SASE SolutionsThis slide represents the best practices to evaluate secure access service edge solutions. The purpose of this slide is to demonstrate the various considerations businesses should keep in mind while choosing and implementing a SASE solution. Present the topic in a bit more detail with this SASE Network Security Best Practices To Evaluate SASE Solutions. Use it as a tool for discussion and navigation on Architecture, Visibility, Tenancy. This template is free to edit as deemed fit for your organization. Therefore download it now.




