Powerpoint Templates and Google slides for Security Assessments
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Process For Information Security Risk Assessment Formulating Cybersecurity Plan
Process For Information Security Risk Assessment Formulating Cybersecurity PlanThis slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Introducing Process For Information Security Risk Assessment Formulating Cybersecurity Plan to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Identifying Internal, Information Security Threats, Information Assets, using this template. Grab it now to reap its full benefits.
-
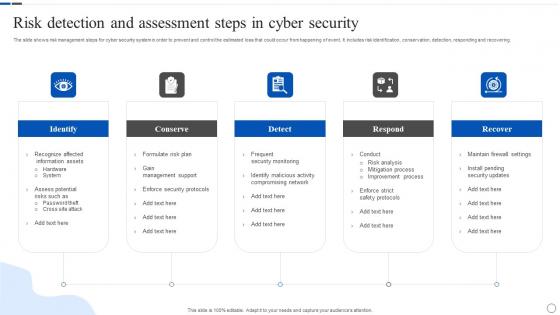 Risk Detection And Assessment Steps In Cyber Security
Risk Detection And Assessment Steps In Cyber SecurityThe slide shows risk management steps for cyber security system in order to prevent and control the estimated loss that could occur from happening of event. It includes risk identification, conservation, detection, responding and recovering. Presenting our set of slides with Risk Detection And Assessment Steps In Cyber Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Conserve, Respond, Recover.
-
 IT Security Assessment Method Framework
IT Security Assessment Method FrameworkThe following slide represents the security assessment of technological assets to assist IT team in improving the data structure. It includes key elements such as risk identification, security threat, vulnerabilities, impact analysis, risk level, controllable actions etc. Presenting our set of slides with IT Security Assessment Method Framework. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Risk Identification, Security Threat, Impact Analysis.
-
 Steps Of Security Risk Assessment Method
Steps Of Security Risk Assessment MethodThe below slide illustrates the process to evaluate security risk of IT assets to improve and minimize potential damage. It constitutes of four activities identification, assessment, mitigation and prevention. Introducing our premium set of slides with Steps Of Security Risk Assessment Method. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Prevention, Identification, Assessment, Mitigation. So download instantly and tailor it with your information.
-
 Cyber Security Environment Vulnerability Assessment In Powerpoint And Google Slides Cpb
Cyber Security Environment Vulnerability Assessment In Powerpoint And Google Slides CpbPresenting our Cyber Security Environment Vulnerability Assessment In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases eight stages. It is useful to share insightful information on Cyber Security Environment Vulnerability Assessment. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Risk Assessment Cyber Security In Powerpoint And Google Slides Cpb
Risk Assessment Cyber Security In Powerpoint And Google Slides CpbPresenting Risk Assessment Cyber Security In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Risk Assessment Cyber Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Erp Assessment Checklist To Improve It Security
Erp Assessment Checklist To Improve It SecurityThis slide signifies the enterprise resource planning evaluation to increase IT security. It covers information about automated testing tool, check system functionality and quality assurance etc. Presenting our well structured Erp Assessment Checklist To Improve It Security. The topics discussed in this slide are Business, Framework, Systems. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Erp Assessment Model To Improve Cyber Security Performance
Erp Assessment Model To Improve Cyber Security PerformanceThis slide signifies the enterprise resource planning evaluation model to increase cyber security performance. It covers infomation about implement assessment, create optimized test and detect impact. Presenting our well structured Erp Assessment Model To Improve Cyber Security Performance. The topics discussed in this slide are Data, Assessment, Application Scanner. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Importance Risk Assessment Cyber Security In Powerpoint And Google Slides Cpb
Importance Risk Assessment Cyber Security In Powerpoint And Google Slides CpbPresenting our Importance Risk Assessment Cyber Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases two stages. It is useful to share insightful information on Importance Risk Assessment Cyber Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 It Security Assessment Report Icon
It Security Assessment Report IconPresenting our set of slides with It Security Assessment Report Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security, Assessment.
-
 It Security Risk Assessment Framework
It Security Risk Assessment FrameworkThe following slide highlights the structure to identify best practices to fix risk tolerances. It constitutes of activities such as identify, protect, detect, respond and recover. Presenting our set of slides with It Security Risk Assessment Framework. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Protect, Detect .
-
 It Security Risk Assessment Grid
It Security Risk Assessment GridThe following slide depicts the analysis of IT security to prevent loss of confidentiality and integrity. The matrix constitutes of elements such as risk, likelihood, its impact and overall threat level. Introducing our premium set of slides with It Security Risk Assessment Grid. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Likelihood, Risk, Impact. So download instantly and tailor it with your information.
-
 Cyber security risk assessment matrix ppt powerpoint presentation file guidelines cpb
Cyber security risk assessment matrix ppt powerpoint presentation file guidelines cpbPresenting this set of slides with name Cyber Security Risk Assessment Matrix Ppt Powerpoint Presentation File Guidelines Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Cyber Security Risk Assessment Matrix to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Comparative Assessment Of Security Awareness Online Preventing Data Breaches Through Cyber Security
Comparative Assessment Of Security Awareness Online Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase comparison of various advance cyber security training courses. The comparison is drawn on the basis of course description, level, duration, no. of companies enrolled for this course etc. Present the topic in a bit more detail with this Comparative Assessment Of Security Awareness Online Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Course Description, Instructor, Rating. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Security Governance Tool Assessment Matrix
Data Security Governance Tool Assessment MatrixThis slide highlights a tools comparison matrix for data security governance and management. It includes key components such as threat intelligence, advanced data governance, source score, data helpdesk, price and customer satisfaction. Introducing our premium set of slides with Data Security Governance Tool Assessment Matrix. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Threat Intelligence, Advanced Data Governance. So download instantly and tailor it with your information.
-
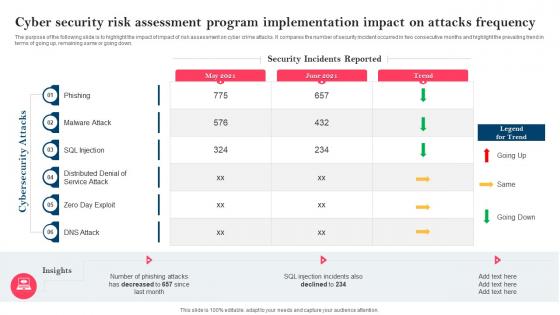 Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program Implementation
Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program ImplementationThe purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Present the topic in a bit more detail with this Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program Implementation. Use it as a tool for discussion and navigation on Cyber Security, Risk Assessment, Program Implementation, Impact On Attacks Frequency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Security Maturity Model Assessment To Improve Business Operations
Cloud Security Maturity Model Assessment To Improve Business OperationsThis slide represents cloud security maturity assessment model which helps improve cloud optimization and flexibility. It provides information regarding automation, manual scripts, managed stage and optimization. Introducing our premium set of slides with Cloud Security Maturity Model Assessment To Improve Business Operations. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Automation Optimized, Minimal Automation, Minimal Automation. So download instantly and tailor it with your information.
-
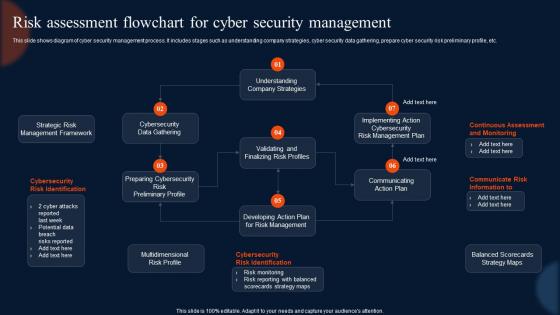 Risk Assessment Flowchart For Cyber Security Management
Risk Assessment Flowchart For Cyber Security ManagementThis slide shows diagram of cyber security management process. It includes stages such as understanding company strategies, cyber security data gathering, prepare cyber security risk preliminary profile, etc. Introducing our Risk Assessment Flowchart For Cyber Security Management set of slides. The topics discussed in these slides are Assessment, Flowchart, Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Healthcare Security Measures And Assessment Analysis
Healthcare Security Measures And Assessment AnalysisThis slide covers the details related to the measures for healthcare security and its assessment analysis. The purpose of this template is to define privacy and security of healthcare organization. It includes information related to physical, administrative and technical safeguards. Presenting our well structured Healthcare Security Measures And Assessment Analysis. The topics discussed in this slide are Security Areas, Details, Potential Security Measures. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 F1556 Comparative Assessment Of Smart Home Security Systems Iot Smart Homes Automation IOT SS
F1556 Comparative Assessment Of Smart Home Security Systems Iot Smart Homes Automation IOT SSThis slide provides an overview of the various smart home systems used to enhance safety. The comparison is done on the basis of features, compatible voice assistants, rating, installation type and price Present the topic in a bit more detail with this F1556 Comparative Assessment Of Smart Home Security Systems Iot Smart Homes Automation IOT SS. Use it as a tool for discussion and navigation on Compatible Voice Assistants, Installation Type, Comparative Assessment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1559 Comparative Assessment Of Various Security Camera Iot Smart Homes Automation IOT SS
F1559 Comparative Assessment Of Various Security Camera Iot Smart Homes Automation IOT SSThis slide provides an overview of the various security cameras for smart homes. The comparison is done on the basis of setup, storage, field of view, resolution and compatibility. Deliver an outstanding presentation on the topic using this F1559 Comparative Assessment Of Various Security Camera Iot Smart Homes Automation IOT SS. Dispense information and present a thorough explanation of Comparative, Assessment, Compatibility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Icon Showcasing Security Network Assessment
Icon Showcasing Security Network AssessmentIntroducing our premium set of slides with Icon Showcasing Security Network Assessment. Ellicudate the One stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon Showcasing Security, Network Assessment. So download instantly and tailor it with your information.
-
 Steps To Perform Vulnerability Assessment For Network Security
Steps To Perform Vulnerability Assessment For Network SecurityThis slide showcase vulnerability assessment process that help organization to identify security vulnerabilities in network system and prioritize them to plan mitigation action plan. It includes steps such as identifying, scanning, identify type of scan, configure scan etc. Introducing our premium set of slides with Steps To Perform Vulnerability Assessment For Network Security. Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Risk Identification And Analysis, Identify Type Of Scan, Configure Scan. So download instantly and tailor it with your information.
-
 Cyber Security Risk Assessment And Management Matrix Incident Response Strategies Deployment
Cyber Security Risk Assessment And Management Matrix Incident Response Strategies DeploymentThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Matrix Incident Response Strategies Deployment. Dispense information and present a thorough explanation of Vulnerability, Consequences, Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Architecture Review Of A Cloud Assess Companies Current State
Security Architecture Review Of A Cloud Assess Companies Current StateThis slide covers the current state assessment criteria as its essential to take frequent looks at your design operations to support your business evolution over time. Introducing Security Architecture Review Of A Cloud Assess Companies Current State to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Business Is Continually Changing, Current Cloud Infrastructure, Visualizing The Cloud Infrastructure, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security Incident
Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security IncidentThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security Incident. Use it as a tool for discussion and navigation on Consequences, Vulnerability, Risk. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response Plan
Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response PlanThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response Plan. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Security Audit Assessment Process
Cloud Security Audit Assessment ProcessThe slide exhibits various steps of cloud security audit for getting an excellent performance. Various steps included are understand the model, analyse, validate controls and calculate score. Introducing our premium set of slides with Cloud Security Audit Assessment Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Calculate Score, Validate Controls, Understand The Model . So download instantly and tailor it with your information.
-
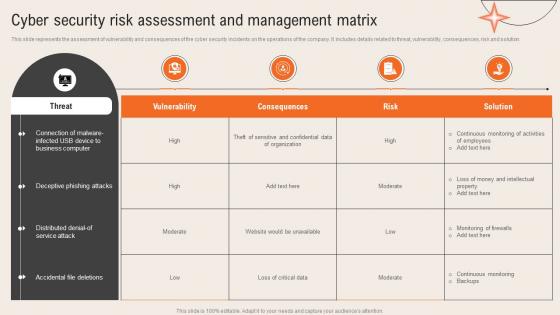 Deploying Computer Security Incident Cyber Security Risk Assessment And Management Matrix
Deploying Computer Security Incident Cyber Security Risk Assessment And Management MatrixThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution.Present the topic in a bit more detail with this Deploying Computer Security Incident Cyber Security Risk Assessment And Management Matrix. Use it as a tool for discussion and navigation on Deceptive Phishing, Business Computer, Accidental File Deletions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Digital Network Security Assessment Flowchart
Digital Network Security Assessment FlowchartThis slide showcases digital network security assessment flowchart which helps ensure reduction in information leaks. It provides information regarding network enumeration, service assessment and data collection and reporting. Presenting our well structured Digital Network Security Assessment Flowchart. The topics discussed in this slide are Assessment, Flowchart, Assessment. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Digital Safety Assessment Tools Used To Identify Security Threats
Digital Safety Assessment Tools Used To Identify Security ThreatsThis slide showcases digital safety assessment tools used to safeguard vulnerable operations systems in the organization. It provides information regarding protocol scanner, web application scanner, network scanner and attack simulation tool. Presenting our well structured Digital Safety Assessment Tools Used To Identify Security Threats. The topics discussed in this slide are Assessment, Application, Identify Vulnerable. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Software Security Testing Approaches And Vulnerability Assessment
Software Security Testing Approaches And Vulnerability AssessmentThis slide defines the software security testing approaches and risk assessment. The purpose of this template is assess and test the software vulnerability. It includes information related to the software platform, hosting infrastructure, privacy and control policies. Introducing our premium set of slides with name Software Security Testing Approaches And Vulnerability Assessment. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Software Platform, Hosting Infrastructure, Access Control Polices. So download instantly and tailor it with your information.
-
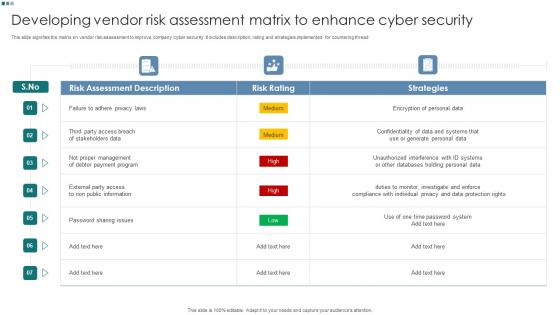 Developing Vendor Risk Assessment Matrix To Enhance Cyber Security
Developing Vendor Risk Assessment Matrix To Enhance Cyber SecurityThis slide signifies the matrix on vendor risk assessment to improve company cyber security. It includes description, rating and strategies implemented for countering thread. Introducing our Developing Vendor Risk Assessment Matrix To Enhance Cyber Security set of slides. The topics discussed in these slides are Strategies, Risk Assessment, Risk Rating. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Assessment Of Cloud Infra Security Solution
Comparative Assessment Of Cloud Infra Security SolutionThe following slide showcases comparison of different cloud infrastructure securities which provides continuous monitoring and support for improvement and better management of security. It presents information related to Microsoft defender, identity manager, etc. Present the topic in a bit more detail with this Comparative Assessment Of Cloud Infra Security Solution. Use it as a tool for discussion and navigation on Software, Services, Security Layer. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Steps For It Infra Security Assessment
Steps For It Infra Security AssessmentThe following slide exhibits IT risk assessment process which aims to eliminate levels of risk at every step. It presents information related to evaluation, exposure, threat determination, etc. Introducing Steps For It Infra Security Assessment to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Evaluation, Vulnerability, Exposure, using this template. Grab it now to reap its full benefits.
-
 Employee Safety Program Assessment And Improvement Best Practices For Workplace Security
Employee Safety Program Assessment And Improvement Best Practices For Workplace SecurityThis slide showcases the assessment and improvement of safety program which includes monitoring performance, examining program and checking improvement opportunities.Increase audience engagement and knowledge by dispensing information using Employee Safety Program Assessment And Improvement Best Practices For Workplace Security. This template helps you present information on three stages. You can also present information on Monitor Performance, Examine Program Implementation, Improvement Opportunities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Change Assessment And Evaluation Icon
Security Change Assessment And Evaluation IconPresenting our set of slides with Security Change Assessment And Evaluation Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security, Assessment, Evaluation.
-
 Cyber Security Risk Assessment Matrix
Cyber Security Risk Assessment MatrixThis slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc Introducing our premium set of slides with Cyber Security Risk Assessment Matrix Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Risk, Vulnerability, Impact So download instantly and tailor it with your information.
-
 Agenda For Cybersecurity Risk Assessment Program To Strengthen Organization Security
Agenda For Cybersecurity Risk Assessment Program To Strengthen Organization SecurityIntroducing Agenda For Cybersecurity Risk Assessment Program To Strengthen Organization Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity, Risk Assessment Program, Strengthen Organization Security, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Risk Assessment Cyber Security Risk Assessment Program Implementation Impact
Cybersecurity Risk Assessment Cyber Security Risk Assessment Program Implementation ImpactThe purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Cyber Security Risk Assessment Program Implementation Impact. Use it as a tool for discussion and navigation on Cyber Security, Risk Assessment, Program Implementation, Impact On Attacks Frequency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons Slide For Cybersecurity Risk Assessment Program To Strengthen Organization Security
Icons Slide For Cybersecurity Risk Assessment Program To Strengthen Organization SecurityPresenting our well crafted Icons Slide For Cybersecurity Risk Assessment Program To Strengthen Organization Security set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly.
-
 Table Of Contents For Cybersecurity Risk Assessment Program To Strengthen Organization Security
Table Of Contents For Cybersecurity Risk Assessment Program To Strengthen Organization SecurityIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Cybersecurity Risk Assessment Program To Strengthen Organization Security. This template helps you present information on nine stages. You can also present information on Cyber Attacks Risk Assessment, Cyber Attacks Risk Mitigation, Dashboards, Cyber Attack Identification using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 K56 Cybersecurity Risk Assessment Program To Strengthen Organization Security For Table Of Contents
K56 Cybersecurity Risk Assessment Program To Strengthen Organization Security For Table Of ContentsIntroducing K56 Cybersecurity Risk Assessment Program To Strengthen Organization Security For Table Of Contents to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity, Risk Assessment Program, Strengthen Organization Security, using this template. Grab it now to reap its full benefits.
-
 Comparative Analysis Of Cyber Security Threat Assessment Tools
Comparative Analysis Of Cyber Security Threat Assessment ToolsThis slide provides a comparative analysis of various tools to detect and assess cyber security threats in the industry to gain insights about which tool to implement. The major tools are Nessus home, GFI Languard, QualysGuard and n Circle IP 360 Presenting our well structured Comparative Analysis Of Cyber Security Threat Assessment Tools. The topics discussed in this slide are Nessus Home, Compatible Mechanisms. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Risk Assessment And Management Matrix Ppt File Visual Aids
Cyber Security Risk Assessment And Management Matrix Ppt File Visual AidsThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution.Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Matrix Ppt File Visual Aids. Use it as a tool for discussion and navigation on Deceptive Phishing Attacks, Monitoring Firewalls, Continuous Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Perceptual Mapping Assessment How Amazon Is Securing Competitive Edge Across Globe Strategy SS
Perceptual Mapping Assessment How Amazon Is Securing Competitive Edge Across Globe Strategy SSThis slide provides information regarding visual representation of Amazon positioning across the consumer mind in context to existing competitors. The attributes for consideration include product brand awareness and product varieties. Increase audience engagement and knowledge by dispensing information using Perceptual Mapping Assessment How Amazon Is Securing Competitive Edge Across Globe Strategy SS. This template helps you present information on four stages. You can also present information on Brand Awareness, Product Varieties, Optimum Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Monitor And Assess Generating Security Awareness Among Employees To Reduce
Monitor And Assess Generating Security Awareness Among Employees To ReduceThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Deliver an outstanding presentation on the topic using this Monitor And Assess Generating Security Awareness Among Employees To Reduce Dispense information and present a thorough explanation of Information Security Privacy, Physical Assets using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Communication Plan To Assess Channel Effectiveness
Cyber Security Communication Plan To Assess Channel EffectivenessThis slide provides information about various channels to effectively communicate of cyber security incidents to respected department. It includes channels such as emails, alerts, collaborative tools, intranet, digital screen and newsfeeds. Introducing our Cyber Security Communication Plan To Assess Channel Effectiveness set of slides. The topics discussed in these slides are Cyber Security Threats, Collaborative Tools, Digital Screen This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Application Portfolio Assessment On Various Strategic Plan To Secure It Infrastructure Strategy SS V
Application Portfolio Assessment On Various Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding application portfolio analysis based on the categories offered in terms of critical applications, under performing applications and data quality applications. The categories are assessed based on importance, features, usability, data quality, etc. Present the topic in a bit more detail with this Application Portfolio Assessment On Various Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Application, Portfolio, Assessment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Budget Assessment To Track Overall It Spending Strategic Plan To Secure It Infrastructure Strategy SS V
Budget Assessment To Track Overall It Spending Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding budget assessment to track overall IT spending. The budget plan include initiative, IT goal, business goal, project team, business benefits, risks, staffing estimates and cost estimates. Present the topic in a bit more detail with this Budget Assessment To Track Overall It Spending Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Business, Assessment, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managing It Technology Vendor Assessment Strategic Plan To Secure It Infrastructure Strategy SS V
Managing It Technology Vendor Assessment Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding assessment of IT technology vendors in order to select potential vendors by assessing them on different parameters such as incident management, testing, quality, etc. Present the topic in a bit more detail with this Managing It Technology Vendor Assessment Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Assessment, Technology, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Services Security Architecture Assessment
Cloud Services Security Architecture AssessmentThe slideshows an assessment model of CSP cloud service security. It includes identification of existing warrant, verification of certificates and reports, evidence review and additional information collection about third party warrant and certificates. Presenting our well structured Cloud Services Security Architecture Assessment The topics discussed in this slide are Existing And Applicable, Warrant And Certification, Comprehensive Evidence Review This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Country Health Security Risk Assessment Categories
Country Health Security Risk Assessment CategoriesThis slide highlights various risk categories in health security risk analysis of countries which helps in analyzing current health status. It provides information regarding outdated policies, infrastructural gaps, lack of vaccination , inadequate equipment etc.Introducing our premium set of slides with Country Health Security Risk Assessment Categories. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Surveillance Infrastructures, Outdated Policies, Inadequate Health. So download instantly and tailor it with your information.
-
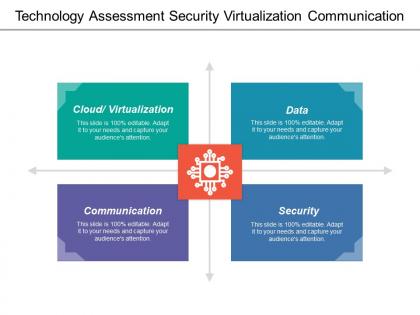 Technology assessment security virtualization communication
Technology assessment security virtualization communicationPresenting this set of slides with name - Technology Assessment Security Virtualization Communication. This is a four stage process. The stages in this process are Technology Assessment, Technology Forecasting, Technology Evaluation.
-
 Proportional potential impact assess organizational readiness food security
Proportional potential impact assess organizational readiness food securityPresenting this set of slides with name - Proportional Potential Impact Assess Organizational Readiness Food Security. This is an editable seven stages graphic that deals with topics like Proportional Potential Impact, Assess Organizational Readiness, Food Security to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
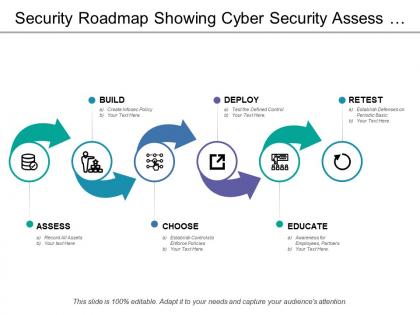 Security roadmap showing cyber security assess and educate
Security roadmap showing cyber security assess and educatePresenting this set of slides with name - Security Roadmap Showing Cyber Security Assess And Educate. This is a five stage process. The stages in this process are Security Roadmap, Security Timeline, Safer Roadmap.
-
 Optimization phase assess cost assess security build pilot
Optimization phase assess cost assess security build pilotPresenting this set of slides with name - Optimization Phase Assess Cost Assess Security Build Pilot. This is an editable seven stages graphic that deals with topics like Optimization Phase Assess Cost Assess Security Build Pilot to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Information security strategy assessment ethical hacking
Information security strategy assessment ethical hackingPresenting this set of slides with name - Information Security Strategy Assessment Ethical Hacking. This is a four stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
 Preparing investment review budgeting preliminary risk assessment security categorization
Preparing investment review budgeting preliminary risk assessment security categorizationPresenting this set of slides with name - Preparing Investment Review Budgeting Preliminary Risk Assessment Security Categorization. This is an editable seven stages graphic that deals with topics like Preparing Investment Review Budgeting, Preliminary Risk Assessment, Security Categorization to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Impact risk assessment information security risk risk matrix cpb
Impact risk assessment information security risk risk matrix cpbPresenting this set of slides with name - Impact Risk Assessment Information Security Risk Risk Matrix Cpb. This is an editable three stages graphic that deals with topics like Impact Risk Assessment, Information Security Risk, Risk Matrix to help convey your message better graphically. This product is a premium product available for immediate download,and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.





