Powerpoint Templates and Google slides for Security Assessments
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Select Tools To Reduce Cyber Security Failure Cyber Risk Assessment
Select Tools To Reduce Cyber Security Failure Cyber Risk AssessmentThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Introducing Select Tools To Reduce Cyber Security Failure Cyber Risk Assessment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Suspicious Activities, Select Tools, Cyber Security Failure using this template. Grab it now to reap its full benefits.
-
 Chatgpt Security Operations Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V
Chatgpt Security Operations Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS VThis slide showcases various ChatGPT use cases for streamlining and automating the cybersecurity operations of organization. Its key elements are establish security policies, automate repetitive tasks and identification of vulnerabilities Increase audience engagement and knowledge by dispensing information using Chatgpt Security Operations Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V. This template helps you present information on three stages. You can also present information on Streamlining, Operations, Identify Vulnerabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview And Security Operations Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V
Overview And Security Operations Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS VThis slide showcases overview of streamlining security operations which can help organization to prevent cyber attacks in organization. It also highlight various benefits of streamlining security operations such as timely incident response, vulnerability assessment, reduction in cyber attacks etc. Deliver an outstanding presentation on the topic using this Overview And Security Operations Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V. Dispense information and present a thorough explanation of Overview, Streamlining, Operations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Conduct Third Party Risk Assessment Creating Cyber Security Awareness
Conduct Third Party Risk Assessment Creating Cyber Security AwarenessThe following slide illustrates checklist to evaluate third party risk assessment to eliminate unnecessary threats. It includes elements such as cyber security policies, patch management process, physical security guidelines, information safety etc. Deliver an outstanding presentation on the topic using this Conduct Third Party Risk Assessment Creating Cyber Security Awareness Dispense information and present a thorough explanation of Response, Status, Notes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Monitor And Assess Vendor Risk Management Creating Cyber Security Awareness
Monitor And Assess Vendor Risk Management Creating Cyber Security AwarenessThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Deliver an outstanding presentation on the topic using this Monitor And Assess Vendor Risk Management Creating Cyber Security Awareness Dispense information and present a thorough explanation of Select Strong Password, Conduct Password Test, Password Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Digital Facility Security Assessment Checklist
Digital Facility Security Assessment ChecklistThe purpose of this slide is to systematically evaluate and enhance security measures of digital facility by identifying potential vulnerabilities and implementing necessary safeguards. Introducing our Digital Facility Security Assessment Checklist set of slides. The topics discussed in these slides are Access Control Systems, Check Fencing Condition, Monitor Entry Point Systems, Intrusion Detection. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
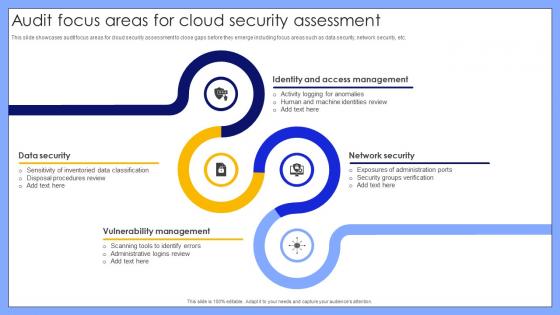 Audit Focus Areas For Cloud Security Assessment
Audit Focus Areas For Cloud Security AssessmentThis slide showcases audit focus areas for cloud security assessment to close gaps before they emerge including focus areas such as data security, network security, etc. Introducing our premium set of slides with name Audit Focus Areas For Cloud Security Assessment. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Security, Vulnerability Management, Network Security, Identity And Access Management. So download instantly and tailor it with your information.
-
 Comparative Assessment Of EDR Security Solutions Tools
Comparative Assessment Of EDR Security Solutions ToolsThis slide represents EDR software tools and includes tools, solution scope, delivery model, features, pricing, and rating. Presenting our well structured Comparative Assessment Of EDR Security Solutions Tools. The topics discussed in this slide are Symantec Endpoint Protection, Crowd Strike Falcon Insight, Threat Intelligence, Detect Hidden Packages. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security Threats
Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates checklist to evaluate third party risk assessment to eliminate unnecessary threats. It includes elements such as cyber security policies, patch management process, physical security guidelines, information safety etc. Deliver an outstanding presentation on the topic using this Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Parameters, Response, Status using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats
Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Present the topic in a bit more detail with this Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Information Security And Privacy, Physical Assets And Data Security, Web Application Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
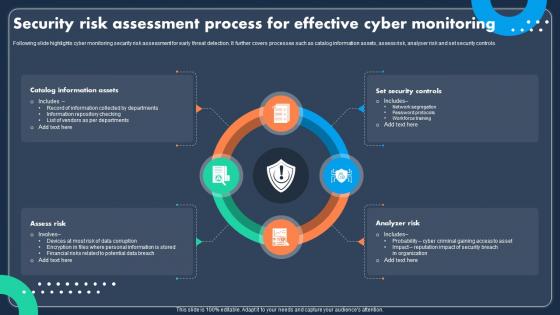 Security Risk Assessment Process For Effective Cyber Monitoring
Security Risk Assessment Process For Effective Cyber MonitoringFollowing slide highlights cyber monitoring security risk assessment for early threat detection. It further covers processes such as catalog information assets, assess risk, analyser risk and set security controls. Introducing our premium set of slides with Security Risk Assessment Process For Effective Cyber Monitoring Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Assets, Security Controls, Analyzer Risk. So download instantly and tailor it with your information.
-
 Comparative Assessment For Data Security Management Tools
Comparative Assessment For Data Security Management ToolsThis slide represents the comparative analysis assisting businesses to choose correct tools to enhance data security management. It includes various tools such as oracle data safe, satori data security platform, etc. Introducing our Comparative Assessment For Data Security Management Tools set of slides. The topics discussed in these slides are Oracle Data Safe, Data Security Platform, Manager For Databases. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Mobile Application Security Risk Assessment
Mobile Application Security Risk AssessmentThis slide demonstrates mobile application security to assess risks and includes improper platform usage, insecure data storage, and insecure communication. Presenting our set of slides with name Mobile Application Security Risk Assessment. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Improper Platform Usage, Insecure Data Storage, Insecure Communication.
-
 Mobile Security Threats And Risk Assessment
Mobile Security Threats And Risk AssessmentThis slide showcases risk and threat evaluation of mobile security and includes security breaches, phishing attacks, and mobile ransomware. Introducing our Mobile Security Threats And Risk Assessment set of slides. The topics discussed in these slides are Security Breaches, Phishing Attacks, Mobile Ransomware. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 BNPL Software Solutions Comparative Assessment Enhancing Transaction Security With E Payment
BNPL Software Solutions Comparative Assessment Enhancing Transaction Security With E PaymentMentioned slide showcases comparative analysis of various BSNL Buy Now Pay Later application which can be leveraged by businesses to attract more customers. It includes key attributes such as number of installation, features, interest rate, late payment fees and present customer users. Present the topic in a bit more detail with this BNPL Software Solutions Comparative Assessment Enhancing Transaction Security With E Payment Use it as a tool for discussion and navigation on Paypal, Afterpay, Affirm This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of ACH Payment Processors Enhancing Transaction Security With E Payment
Comparative Assessment Of ACH Payment Processors Enhancing Transaction Security With E PaymentMentioned slide illustrates comparative analysis of various ACH Automated Clearing House payment processors which can be leveraged by businesses to making bank transfer. It includes key attributes such as ACH processors, best attribute, features, rating, price, and company size. Deliver an outstanding presentation on the topic using this Comparative Assessment Of ACH Payment Processors Enhancing Transaction Security With E Payment Dispense information and present a thorough explanation of ACH Payment Processors, Best Attribute, Features using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Cashless And Contactless Payment Enhancing Transaction Security With E Payment
Comparative Assessment Of Cashless And Contactless Payment Enhancing Transaction Security With E PaymentMentioned slide showcases comparative analysis between cashless and contactless payment system which can be implemented by businesses to improve cashflow management. It includes key attributes such as meaning, closed and open loop system, Present the topic in a bit more detail with this Comparative Assessment Of Cashless And Contactless Payment Enhancing Transaction Security With E Payment Use it as a tool for discussion and navigation on Attributes, Cashless Payment, Contactless Payment This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of Debit And Credit Card Enhancing Transaction Security With E Payment
Comparative Assessment Of Debit And Credit Card Enhancing Transaction Security With E PaymentMentioned slide shows comparative analysis of debit and credit card payment options which can be used by businesses for making daily payments. It includes key attributes such as funds availability, spending limit, charges, interest charges reward points, repayment, etc. Deliver an outstanding presentation on the topic using this Comparative Assessment Of Debit And Credit Card Enhancing Transaction Security With E Payment Dispense information and present a thorough explanation of Attributes, Credit Card, Debit Card using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Multiple Mobile Wallet Applications Enhancing Transaction Security With E Payment
Comparative Assessment Of Multiple Mobile Wallet Applications Enhancing Transaction Security With E PaymentFollowing slide shows comparative analysis of multiple types of mobile wallet which can be leverages by business to go contactless. It includes key components such as features, transaction level, payment fees, transaction time, security and type of wallet. Present the topic in a bit more detail with this Comparative Assessment Of Multiple Mobile Wallet Applications Enhancing Transaction Security With E Payment Use it as a tool for discussion and navigation on Features, Transaction Level, Payment Fees This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of QR Code Generating Professionals Enhancing Transaction Security With E Payment
Comparative Assessment Of QR Code Generating Professionals Enhancing Transaction Security With E PaymentFollowing slide showcases comparative analysis of multiple code generators whose services can be leveraged by businesses to design customized QR code. It includes key attributes such as Deliver an outstanding presentation on the topic using this Comparative Assessment Of QR Code Generating Professionals Enhancing Transaction Security With E Payment Dispense information and present a thorough explanation of Attributes, QR Code Generator Pro, Flow Code using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Various Payment Cryptocurrencies Enhancing Transaction Security With E Payment
Comparative Assessment Of Various Payment Cryptocurrencies Enhancing Transaction Security With E PaymentMentioned slide demonstrates comparative analysis of various crypto coins which can be used by businesses in cashless payment. It includes key points such as launch year, trading value, transaction rate, transaction fees, privacy, block time, and trading history. Present the topic in a bit more detail with this Comparative Assessment Of Various Payment Cryptocurrencies Enhancing Transaction Security With E Payment Use it as a tool for discussion and navigation on Launch Year, Ticker Symbol, Current Trading Value This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Assessment Of Mobile Wallet Application Enhancing Transaction Security With E Payment
Impact Assessment Of Mobile Wallet Application Enhancing Transaction Security With E PaymentMentioned slide provides information about mobile wallet payment implementation impact on business activities. It includes impacts such as easy customer data analytics, offer reward and loyalty points, smooth workflow, and improved security. Increase audience engagement and knowledge by dispensing information using Impact Assessment Of Mobile Wallet Application Enhancing Transaction Security With E Payment This template helps you present information on four stages. You can also present information on Easy Customer Data Analytics, Smooth Workflow, Improved Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Multiple Gift Cards Comparative Assessment Enhancing Transaction Security With E Payment
Multiple Gift Cards Comparative Assessment Enhancing Transaction Security With E PaymentMentioned slide provides information about various kinds of gift cards that can be offered by businesses to increase brand awareness among customers. It includes key points such as description, activation fees, flexibility, type of card, and card reload option. Deliver an outstanding presentation on the topic using this Multiple Gift Cards Comparative Assessment Enhancing Transaction Security With E Payment Dispense information and present a thorough explanation of Categories, Single Store, Store Family using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Proactively Assess The Impact Of Potential Security Internet Of Things IoT Security Cybersecurity SS
Proactively Assess The Impact Of Potential Security Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of impact assessment on internet of things IoT device security events, referable for businesses in developing mitigation process. It provides details about threat model, security layers, etc. Introducing Proactively Assess The Impact Of Potential Security Internet Of Things IoT Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Comprehensive Security, Assessment And Security Layers, Credential Provisioning, using this template. Grab it now to reap its full benefits.
-
 Comparative Assessment Of Cyber Security Tools In Automotive Industry
Comparative Assessment Of Cyber Security Tools In Automotive IndustryThis slide highlights comparison of digital security tools in automobile sector. The purpose of this slide is to aid businesses in utilizing reliable software for managing automotive cybersecurity. It includes elements such as intrusion detection, secure boot, etc. Introducing our Comparative Assessment Of Cyber Security Tools In Automotive Industry set of slides. The topics discussed in these slides are Intrusion Detection, Access Control, Network Monitoring This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Assessing Data Storage Options To Ensure Securely Data Lifecycle Management To Enhance Flow
Assessing Data Storage Options To Ensure Securely Data Lifecycle Management To Enhance FlowThis slide presents the types of data storage technologies for data lifecycle management. It provides information about, relational , non-relational, object storage and cloud storage databases. Present the topic in a bit more detail with this Assessing Data Storage Options To Ensure Securely Data Lifecycle Management To Enhance Flow. Use it as a tool for discussion and navigation on Relational Databases, Object Storage, Cloud Data Storage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Physical Security Audit And Assessment Checklist
Physical Security Audit And Assessment ChecklistThis slide showcases security audit checklist to ensure safe working environment for the employees. The checklist includes questions regarding camera installations, fire alarms, lighting, etc. Introducing our Physical Security Audit And Assessment Checklist set of slides. The topics discussed in these slides are Procedures And Tests, Good Condition, Business. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security Threat
Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the cyber security attack risk assessment matrix which can be leveraged to determine the severity of cyber threats, the likelihood of occurrence, and future action plan. Present the topic in a bit more detail with this Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Assessment Matrix, Occurrence, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Securing Food Safety In Online Analyzing Current Scenario To Assess Restaurant
Securing Food Safety In Online Analyzing Current Scenario To Assess RestaurantThis slide covers current scenario and KPIs affected such as customer satisfaction rate, order accuracy, average delivery time, order cancellation rate and average table occupancy. Present the topic in a bit more detail with this Securing Food Safety In Online Analyzing Current Scenario To Assess Restaurant. Use it as a tool for discussion and navigation on Customer Satisfaction, Order Accuracy, Average Delivery Time, Order Cancellation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of Threat Intelligence Teams In Security Operation Center
Comparative Assessment Of Threat Intelligence Teams In Security Operation CenterThe below slide highlights the threat intelligence types that offer a foundation for establishment of security operation center. The parameters for evaluation are description, use case, and benefit. Introducing our premium set of slides with name Comparative Assessment Of Threat Intelligence Teams In Security Operation Center. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Tactical, Strategic, Operational. So download instantly and tailor it with your information.
-
 Security Operations Center Threat Level Assessment
Security Operations Center Threat Level AssessmentThe below slide provides various risks associated with security operations that helps to analyze the severity level and resolutions status. The different threats are APT, phishing, malware, ransomware, etc. Introducing our Security Operations Center Threat Level Assessment set of slides. The topics discussed in these slides are Ransomware, Malware, Phishing. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Assessment Of Fraud Prevention Initiatives Implementing E Commerce Security Measures
Comparative Assessment Of Fraud Prevention Initiatives Implementing E Commerce Security MeasuresThis slide showcases comparative assessment of fraud prevention strategies by company, referable for businesses facing similar situation. It include companies, position, recent fraud incidents and ongoing efforts. Deliver an outstanding presentation on the topic using this Comparative Assessment Of Fraud Prevention Initiatives Implementing E Commerce Security Measures. Dispense information and present a thorough explanation of Position, Action Plan, Recent Ecommerce Fraud Incidents using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Audits Report For Vulnerability Assessment Implementing E Commerce Security Measures
Security Audits Report For Vulnerability Assessment Implementing E Commerce Security MeasuresThe slide showcases security audit report to asses open vulnerabilities. It include vulnerability category, number of occurrences, and vulnerability level such as critical, high, medium and low. Present the topic in a bit more detail with this Security Audits Report For Vulnerability Assessment Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Weak Authentication, Unauthorized Access, Security Misconfiguration, Payment Gateway Vulnerability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of IT Security Awareness Training Tools Cybersecurity SS
Comparative Assessment Of IT Security Awareness Training Tools Cybersecurity SSThis slide represents comparison between IT security awareness training tools based on features such as audio mixing, text animation, time mapping, titles and captions etc. Deliver an outstanding presentation on the topic using this Comparative Assessment Of IT Security Awareness Training Tools Cybersecurity SS. Dispense information and present a thorough explanation of Time Mapping, Text Animation, Tram Reviews, Security Awareness Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS
Comparative Assessment Of Endpoint Security Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases comparative analysis for endpoint security tools. It provides details about endpoint firewall, compatibility, data loss prevention, regulatory compliance, etc.Present the topic in a bit more detail with this Comparative Assessment Of Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Regulatory Compliance, Data Loss Prevention, Endpoint Firewall. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of Encryption Algorithms For Organizational Data Security
Comparative Assessment Of Encryption Algorithms For Organizational Data SecurityThis slide provides a comparative assessment of various data encryption algorithms on different parameters. The multiple parameters used for assessment are encryption standard and use cases. Introducing our premium set of slides with Comparative Assessment Of Encryption Algorithms For Organizational Data Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Aes, Tdes, Twofish, Blowfish. So download instantly and tailor it with your information.
-
 Organization Security Risk Assessment Matrix
Organization Security Risk Assessment MatrixThis slide provide a risk assessment matrix for organizations to assess the threat vulnerability. The various outcomes mentioned are insignificant, minor, moderate, major, and severe. Introducing our Organization Security Risk Assessment Matrix set of slides. The topics discussed in these slides are Insignificant, Minor, Moderate. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Assessment Of Wireless Lan Security Protocols
Comparative Assessment Of Wireless Lan Security ProtocolsThis slide represents comparative assessment of various WLAN security protocols that assist companies in selecting relevant protocol suitable for specific use cases. It includes various protocols such as WEP, WPA, WPA2, and WPA3 Presenting our well structured Comparative Assessment Of Wireless Lan Security Protocols The topics discussed in this slide are Year Release, Cryptographic Technique, Session Key SizeThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Process Phases For Application Security Assessment
Process Phases For Application Security AssessmentThis slide highlights the steps of application security assessment which include determining threats, identifying sensitive data, mapping application attacks, etc. Introducing our premium set of slides with Process Phases For Application Security Assessment Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Application Security, Statistical Representation So download instantly and tailor it with your information.
-
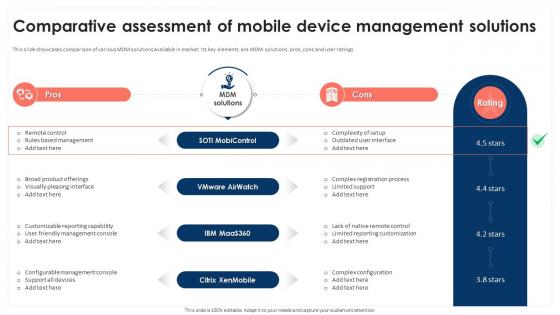 Comparative Assessment Of Mobile Device Management Solutions Mobile Device Security Cybersecurity SS
Comparative Assessment Of Mobile Device Management Solutions Mobile Device Security Cybersecurity SSThis slide showcases comparison of various MDM solutions available in market. Its key elements are MDM solutions, pros, cons and user ratings Increase audience engagement and knowledge by dispensing information using Comparative Assessment Of Mobile Device Management Solutions Mobile Device Security Cybersecurity SS This template helps you present information on Two stages. You can also present information on SOTI Mobicontrol, Vmware Airwatch, Citrix Xenmobile using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security risk assessment methodology analysis ppt powerpoint image
Security risk assessment methodology analysis ppt powerpoint imagePresenting security risk assessment methodology analysis ppt powerpoint image. This is a security risk assessment methodology analysis ppt powerpoint image. This is a six stage process. The stages in this process are define scope, agree start date, configuration review, vulnerability scanning, penetration testing, configuration review.
-
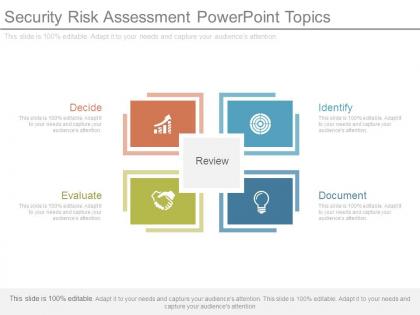 Security risk assessment powerpoint topics
Security risk assessment powerpoint topicsPresenting security risk assessment powerpoint topics. This is a security risk assessment powerpoint topics. This is a four stage process. The stages in this process are identify, document, evaluate, decide, review.
-
 Information security assessment ppt background designs
Information security assessment ppt background designsPresenting information security assessment ppt background designs. This is a information security assessment ppt background designs. This is a four stage process. The stages in this process are assess, control, monitor, respond, assets, technology, people, processes.
-
 Security assessment layout powerpoint slides templates
Security assessment layout powerpoint slides templatesPresenting security assessment layout powerpoint slides templates. This is a security assessment layout powerpoint slides templates. This is a four stage process. The stages in this process are vulnerability scanning, penetration testing, configuration review, code review.
-
 Risk Assessment Dashboard For Securing Supply Chain System
Risk Assessment Dashboard For Securing Supply Chain SystemThis slide demonstrates risk assessment matrix for improving the efficiency of industrial supply chain system. It includes supplier risks, service type and service health etc. Presenting our well structured Risk Assessment Dashboard For Securing Supply Chain System. The topics discussed in this slide are Service Health, Service Type, Supplier Risk. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Technology assessment scorecard with device security ppt slides deck
Technology assessment scorecard with device security ppt slides deckThis graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an outstanding presentation on the topic using this Technology Assessment Scorecard With Device Security Ppt Slides Deck. Dispense information and present a thorough explanation of Compromised, Not Encrypted, Mention Security Feature, Last Seen Overview, Ownership using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Technology assessment scorecard with security incidents ppt slides graphics
Technology assessment scorecard with security incidents ppt slides graphicsThis graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Present the topic in a bit more detail with this Technology Assessment Scorecard With Security Incidents Ppt Slides Graphics. Use it as a tool for discussion and navigation on Criminal Activity, Investigation, Denial Service, Data Breach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Center Dashboard Snapshot With Security And User Assessment
Data Center Dashboard Snapshot With Security And User AssessmentIntroducing our Data Center Dashboard Snapshot With Security And User Assessment set of slides. The topics discussed in these slides are Security Assessment, User Assessment, Data Discovery. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Assessing Cost Of Information Breach In Risk Assessment And Management Plan For Information Security
Assessing Cost Of Information Breach In Risk Assessment And Management Plan For Information SecurityPresent the topic in a bit more detail with this Assessing Cost Of Information Breach In Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Information, Sources, Engineering. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information Security
Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information SecurityThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type if cyber attacks and formulate strategies to tackle them Present the topic in a bit more detail with this Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Experienced, Organization, Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard For Data Security Risk Assessment And Management Plan For Information Security
Dashboard For Data Security Risk Assessment And Management Plan For Information SecurityThis slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status Deliver an outstanding presentation on the topic using this Dashboard For Data Security Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Dashboard, Management, Data Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Market Growth Of Information Security Industry Risk Assessment And Management Plan For Information Security
Market Growth Of Information Security Industry Risk Assessment And Management Plan For Information SecurityThis slide showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compunded annual growth rate of industry Deliver an outstanding presentation on the topic using this Market Growth Of Information Security Industry Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Growth, Information, Security Industry using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Rising Number Of Information Security Attacks Risk Assessment And Management Plan For Information Security
Rising Number Of Information Security Attacks Risk Assessment And Management Plan For Information SecurityThis slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection Present the topic in a bit more detail with this Rising Number Of Information Security Attacks Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Organizations, Information, Cybersecurity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Assessment And Management Plan For Information Security Information And Data Breach Impacting
Risk Assessment And Management Plan For Information Security Information And Data Breach ImpactingDeliver an outstanding presentation on the topic using this Risk Assessment And Management Plan For Information Security Information And Data Breach Impacting. Dispense information and present a thorough explanation of Information, Business, Financial using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Dashboard For Information Risk Assessment And Management Plan For Information Security
Risk Management Dashboard For Information Risk Assessment And Management Plan For Information SecurityThis slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities Deliver an outstanding presentation on the topic using this Risk Management Dashboard For Information Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Management, Dashboard, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents Risk Assessment And Management Plan For Information Security
Table Of Contents Risk Assessment And Management Plan For Information SecurityDeliver an outstanding presentation on the topic using this Table Of Contents Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Assessment, Organization, Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Assessing Cost Of Information Breach In Different Countries Information Security Risk Management
Assessing Cost Of Information Breach In Different Countries Information Security Risk ManagementDeliver an outstanding presentation on the topic using this Assessing Cost Of Information Breach In Different Countries Information Security Risk Management. Dispense information and present a thorough explanation of Assessing, Information Breach, Different Countries using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Assessing Cost Of Information Breach In Different Information System Security And Risk Administration Plan
Assessing Cost Of Information Breach In Different Information System Security And Risk Administration PlanPresent the topic in a bit more detail with this Assessing Cost Of Information Breach In Different Information System Security And Risk Administration Plan. Use it as a tool for discussion and navigation on Past Decade, Social Engineering, Advanced Persistent Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
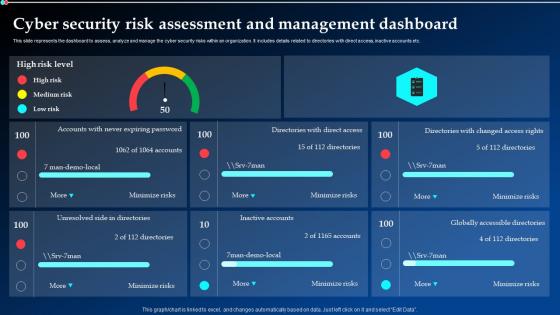 Cyber Security Risk Assessment And Management Dashboard Ppt Portrait
Cyber Security Risk Assessment And Management Dashboard Ppt PortraitThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Dashboard Ppt Portrait. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Security Vulnerabilities Assessment Approach
Network Security Vulnerabilities Assessment ApproachThis slide illustrates network security vulnerabilities assessment results that help the organization to secure network security loop holes to mitigate vulnerabilities. It key components are unpatched security, patched security and total number of vulnerabilities. Introducing our Network Security Vulnerabilities Assessment Approach set of slides. The topics discussed in these slides are Sion And Configuration. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.





