Powerpoint Templates and Google slides for Secured Cloud
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cloud Access Security Broker And User Authentication Next Generation CASB
Cloud Access Security Broker And User Authentication Next Generation CASBThis slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Present the topic in a bit more detail with this Cloud Access Security Broker And User Authentication Next Generation CASB Use it as a tool for discussion and navigation on Cloud Apps, Transaction Detail, User Threat Data This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker Architectural Components Next Generation CASB
Cloud Access Security Broker Architectural Components Next Generation CASBThis slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker Architectural Components Next Generation CASB Dispense information and present a thorough explanation of Secondary Enterprise Core, Platform As A Service, Connectivity Gateway using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB Introduction Next Generation CASB
Cloud Access Security Broker CASB Introduction Next Generation CASBThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Present the topic in a bit more detail with this Cloud Access Security Broker CASB Introduction Next Generation CASB Use it as a tool for discussion and navigation on Deployment Models, Out Of Band Deployment, Inline Deployment This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker Implementation Roadmap Next Generation CASB
Cloud Access Security Broker Implementation Roadmap Next Generation CASBThis slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. Introducing Cloud Access Security Broker Implementation Roadmap Next Generation CASB to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Portfolio, Cloud Application, Systems using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker Life Cycle Protection Next Generation CASB
Cloud Access Security Broker Life Cycle Protection Next Generation CASBIncrease audience engagement and knowledge by dispensing information using Cloud Access Security Broker Life Cycle Protection Next Generation CASB This template helps you present information on four stages. You can also present information on Identify Needs, Control Usage, Adaptive Access, Verify Usage using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Pillar Compliance Next Generation CASB
Cloud Access Security Broker Pillar Compliance Next Generation CASBThis slide gives an overview of the compliance pillar of cloud access security broker. The purpose of this slide is to showcase how compliance is a vital factor for an organization migrating its data and systems to the cloud. Compliance can help industries such as healthcare, retail, and financial services. Introducing Cloud Access Security Broker Pillar Compliance Next Generation CASB to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Financial Services, Risk Domains, Costly Breaches using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker Pillar Data Security Next Generation CASB
Cloud Access Security Broker Pillar Data Security Next Generation CASBThis slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Pillar Data Security Next Generation CASB This template helps you present information on five stages. You can also present information on Complex Cloud, Sensitive Material, Risk Assessments using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Pillar Overview Next Generation CASB
Cloud Access Security Broker Pillar Overview Next Generation CASBThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Introducing Cloud Access Security Broker Pillar Overview Next Generation CASB to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Compliance, Data Security, Threat Protection, Visibility using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker Pillar Threat Protection Next Generation CASB
Cloud Access Security Broker Pillar Threat Protection Next Generation CASBThis slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Pillar Threat Protection Next Generation CASB This template helps you present information on five stages. You can also present information on Services, Cloud Storage, Compromised Accounts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Pillar Visibility Next Generation CASB
Cloud Access Security Broker Pillar Visibility Next Generation CASBThis slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility. Present the topic in a bit more detail with this Cloud Access Security Broker Pillar Visibility Next Generation CASB Use it as a tool for discussion and navigation on Visibility Topography, Working Process, Overview This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker Working Process Next Generation CASB
Cloud Access Security Broker Working Process Next Generation CASBThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing Cloud Access Security Broker Working Process Next Generation CASB to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Working Process, Discovery, Classification, Remediation using this template. Grab it now to reap its full benefits.
-
 Cloud Security Standards And Control Frameworks Next Generation CASB
Cloud Security Standards And Control Frameworks Next Generation CASBThis slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA. Present the topic in a bit more detail with this Cloud Security Standards And Control Frameworks Next Generation CASB Use it as a tool for discussion and navigation on Security Standard, Accountability, Protection Regulation This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Emerging Cloud Security Risks And Threats Next Generation CASB
Emerging Cloud Security Risks And Threats Next Generation CASBThis slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Present the topic in a bit more detail with this Emerging Cloud Security Risks And Threats Next Generation CASB Use it as a tool for discussion and navigation on Virtual Private Networks, System Misconfigurations, Perimeter Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Future Of Cloud Access Security Broker CASB 2 0 Next Generation CASB
Future Of Cloud Access Security Broker CASB 2 0 Next Generation CASBThis slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc. Introducing Future Of Cloud Access Security Broker CASB 2 0 Next Generation CASB to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Endpoint Protection, Encryption, Benefits using this template. Grab it now to reap its full benefits.
-
 Leading Cloud Access Security Broker Platforms Next Generation CASB
Leading Cloud Access Security Broker Platforms Next Generation CASBThis slide outlines the Leading cloud access security broker platforms. The purpose of this slide is to highlight the leading CASB platforms, including G-suite, office 365, and Amazon Web Services, and it also represents the benefits and features of these cloud platforms. Introducing Leading Cloud Access Security Broker Platforms Next Generation CASB to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Amazon Web Services, Cloud Access, Broker Platforms using this template. Grab it now to reap its full benefits.
-
 Overview Of Cloud Access Security Broker Architecture Next Generation CASB
Overview Of Cloud Access Security Broker Architecture Next Generation CASBThis slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Present the topic in a bit more detail with this Overview Of Cloud Access Security Broker Architecture Next Generation CASB Use it as a tool for discussion and navigation on Organization, Direct To Cloud, Broker Architecture This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Popular Cloud Access Security Broker Vendors Next Generation CASB
Popular Cloud Access Security Broker Vendors Next Generation CASBThis slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. Deliver an outstanding presentation on the topic using this Popular Cloud Access Security Broker Vendors Next Generation CASB Dispense information and present a thorough explanation of Forcepoint, Cisco Systems, Microsoft, Features using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Requirements For Appropriate Cloud Security Model Next Generation CASB
Requirements For Appropriate Cloud Security Model Next Generation CASBThis slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. Increase audience engagement and knowledge by dispensing information using Requirements For Appropriate Cloud Security Model Next Generation CASB This template helps you present information on five stages. You can also present information on Continuous Compliance, Data Encryption, Strong Authentication using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Deploy Cloud Access Security Broker Next Generation CASB
Steps To Deploy Cloud Access Security Broker Next Generation CASBThis slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. Introducing Steps To Deploy Cloud Access Security Broker Next Generation CASB to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Deployment Location, Deployment Model, Release Model using this template. Grab it now to reap its full benefits.
-
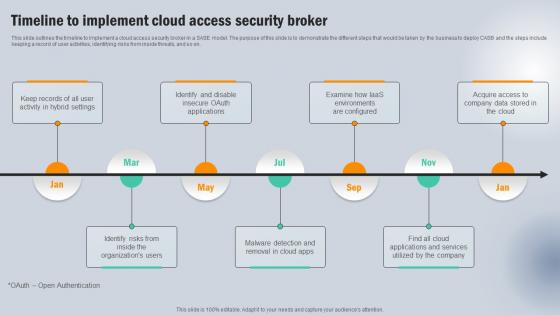 Timeline To Implement Cloud Access Security Broker Next Generation CASB
Timeline To Implement Cloud Access Security Broker Next Generation CASBThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing Timeline To Implement Cloud Access Security Broker Next Generation CASB to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Acquire Access , Company, Applications And Services using this template. Grab it now to reap its full benefits.
-
 Training Program For Cloud Access Security Broker Next Generation CASB
Training Program For Cloud Access Security Broker Next Generation CASBThis slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Present the topic in a bit more detail with this Training Program For Cloud Access Security Broker Next Generation CASB Use it as a tool for discussion and navigation on Agenda, System Requirements, Deployment Options This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Use Cases Of Cloud Access Security Broker Next Generation CASB
Use Cases Of Cloud Access Security Broker Next Generation CASBPresent the topic in a bit more detail with this Use Cases Of Cloud Access Security Broker Next Generation CASB Use it as a tool for discussion and navigation on Unsanctioned Apps, Sanctioned Apps, Cloud Threats This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Pros And Cons Of Cloud Firewall Systems
Firewall Network Security Pros And Cons Of Cloud Firewall SystemsThis slide highlights the advantages and disadvantages of cloud-based firewall systems. The purpose of this slide is to showcase the pros and cons of cloud firewalls, and the pros include deployment and scalability, access and identity management, updates, and availability. Introducing Firewall Network Security Pros And Cons Of Cloud Firewall Systems to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Pros, Cons, Speed, Embedded Malware using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Types Of Cloud Based Firewall Systems
Firewall Network Security Types Of Cloud Based Firewall SystemsThis slide describes the different types of cloud-based firewall systems. The purpose of this slide is to give an overview of different kinds of cloud-based firewall systems, such as Next Generation firewalls, Security as a Service, and Firewall as a Service. Deliver an outstanding presentation on the topic using this Firewall Network Security Types Of Cloud Based Firewall Systems Dispense information and present a thorough explanation of Next-Generation Firewalls, Saas Firewalls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Understanding Cloud Firewall Security Systems
Firewall Network Security Understanding Cloud Firewall Security SystemsThis slide gives an overview of cloud-based firewall security systems, including their importance, types, benefits, and working features. The purpose of this slide is to showcase the different aspects of cloud-based firewalls. The main types include Next Generation Firewall and SaaS firewalls. Introducing Firewall Network Security Understanding Cloud Firewall Security Systems to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Benefits, Working Functions, Types using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Working Functions Of Cloud Firewall System
Firewall Network Security Working Functions Of Cloud Firewall SystemThis slide talks about the different working functions that help cloud-based firewall systems to protect the user network and devices from malicious activities. The purpose of this slide is to showcase the various tasks of cloud firewalls, including packet filtering, stateful inspection, and proxy service. Introducing Firewall Network Security Working Functions Of Cloud Firewall System to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Stateful Inspection, Proxy Service, Packet Filtering using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Best Practices To Implement Cloud Access Security Broker
SD WAN Model Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this SD WAN Model Best Practices To Implement Cloud Access Security Broker. Dispense information and present a thorough explanation of Network And Cloud Infrastructure Monitoring, Protection Against Risks, Specific Risk Prototypes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SD WAN Model Cloud Access Security Broker Casb Overview
SD WAN Model Cloud Access Security Broker Casb OverviewThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Introducing SD WAN Model Cloud Access Security Broker Casb Overview to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Granular Cloud Usage Control, Data Loss Prevention, Cloud Access Security Broker, Risk Visibility, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Cloud Access Security Broker Implementation Models
SD WAN Model Cloud Access Security Broker Implementation ModelsThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Increase audience engagement and knowledge by dispensing information using SD WAN Model Cloud Access Security Broker Implementation Models. This template helps you present information on three stages. You can also present information on Cloud Access Security Broker, Api Scanning, Forward Proxy, Reverse Proxy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Cloud Access Security Broker Use Cases
SD WAN Model Cloud Access Security Broker Use CasesThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Present the topic in a bit more detail with this SD WAN Model Cloud Access Security Broker Use Cases. Use it as a tool for discussion and navigation on Cloud Access Security Broker, Covering Protection Against Threats, Governing Usage, Securing Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Cloud Access Security Broker Working Process
SD WAN Model Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing SD WAN Model Cloud Access Security Broker Working Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Classification And Remediation, Control And Transparency Across Data, Risks In The Cloud, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Pillars Of Cloud Access Security Broker Ppt Icon Design Ideas
SD WAN Model Pillars Of Cloud Access Security Broker Ppt Icon Design IdeasThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Increase audience engagement and knowledge by dispensing information using SD WAN Model Pillars Of Cloud Access Security Broker Ppt Icon Design Ideas. This template helps you present information on four stages. You can also present information on Cloud Access Security Broker, Compliance, Visibility, Threat Protection, Data Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
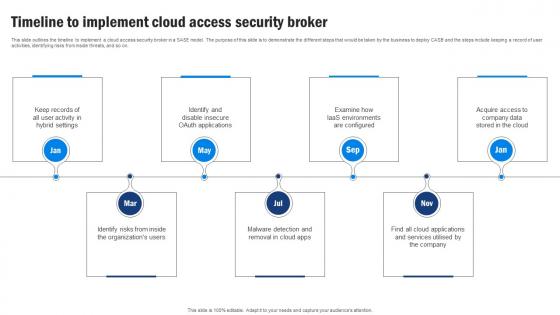 SD WAN Model Timeline To Implement Cloud Access Security Broker
SD WAN Model Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using SD WAN Model Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Cloud Access Security Broker, Environments Are Configured, Identify Risks, Malware Detection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Event Monitoring Icon
Cloud Security Event Monitoring IconIncrease audience engagement and knowledge by dispensing information using Cloud Security Event Monitoring Icon. This template helps you present information on Three stages. You can also present information on Cloud Security Event Monitoring Icon using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Software Defined Virtual Infrastructure For Cloud Management And Data Security
Software Defined Virtual Infrastructure For Cloud Management And Data SecurityThis slide represents the virtual infrastructure framework assisting companies to enhance data security and maintain business continuity. It includes various key components such as cloud management layer, physical layer, storage, etc. Presenting our well structured Software Defined Virtual Infrastructure For Cloud Management And Data Security. The topics discussed in this slide are Service Management, Business Continuity, Security Compliance. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Securing Cloud Based Solutions And IoT Elevating Small And Medium Enterprises Digital Transformation DT SS
Securing Cloud Based Solutions And IoT Elevating Small And Medium Enterprises Digital Transformation DT SSThis slide mentions various measures for securing cloud based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy. Deliver an outstanding presentation on the topic using this Securing Cloud Based Solutions And IoT Elevating Small And Medium Enterprises Digital Transformation DT SS. Dispense information and present a thorough explanation of Data Encryption, Network Security, Data Privacy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Best Practices To Implement Cloud Access Security Broker
Sase Model Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Present the topic in a bit more detail with this Sase Model Best Practices To Implement Cloud Access Security Broker. Use it as a tool for discussion and navigation on Best Practices, Description, Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Cloud Access Security Broker Casb Overview
Sase Model Cloud Access Security Broker Casb OverviewThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Increase audience engagement and knowledge by dispensing information using Sase Model Cloud Access Security Broker Casb Overview. This template helps you present information on five stages. You can also present information on Risk Visibility, Threat Prevention, Granular Cloud using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Cloud Access Security Broker Implementation Models
Sase Model Cloud Access Security Broker Implementation ModelsThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Introducing Sase Model Cloud Access Security Broker Implementation Models to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Scanning, Forward Proxy, Reverse Proxy, using this template. Grab it now to reap its full benefits.
-
 Sase Model Cloud Access Security Broker Use Cases
Sase Model Cloud Access Security Broker Use CasesThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Present the topic in a bit more detail with this Sase Model Cloud Access Security Broker Use Cases. Use it as a tool for discussion and navigation on Protection Against Threats, Govern Usage, Secure Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Cloud Access Security Broker Working Process
Sase Model Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing Sase Model Cloud Access Security Broker Working Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Discovery, Classification, Remediation, using this template. Grab it now to reap its full benefits.
-
 Sase Model Pillars Of Cloud Access Security Broker
Sase Model Pillars Of Cloud Access Security BrokerThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Increase audience engagement and knowledge by dispensing information using Sase Model Pillars Of Cloud Access Security Broker. This template helps you present information on four stages. You can also present information on Compliance, Visibility, Threat Prevention using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Timeline To Implement Cloud Access Security Broker
Sase Model Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using Sase Model Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Hybrid Settings, Environments Are Configured, Cloud App using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Emerging Trends In Cryptographic Cloud Security Encryption For Data Privacy In Digital Age It
Emerging Trends In Cryptographic Cloud Security Encryption For Data Privacy In Digital Age ItThis slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum-safe cryptography, secure multi-party computation, etc. Introducing Emerging Trends In Cryptographic Cloud Security Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Homomorphic Encryption, Quantum Safe Cryptography, Secure Multi Party Computation, using this template. Grab it now to reap its full benefits.
-
 Factors Responsible For Cloud Security Failures Encryption For Data Privacy In Digital Age It
Factors Responsible For Cloud Security Failures Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low-level encryption, reliance on cloud service providers for data protection, poor key management, etc. Introducing Factors Responsible For Cloud Security Failures Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Data Protection, Poor Key Management, Software Engineers, using this template. Grab it now to reap its full benefits.
-
 Devops Automation Checklist For Cloud Security
Devops Automation Checklist For Cloud SecurityThis slide showcases devOps automation checklist that helps to reduce manual errors and security operation automation. It includes elements such as cloud automation, access management, cloud resources, devOps pipeline, security testing and rapid detection. Introducing our Devops Automation Checklist For Cloud Securityset of slides. The topics discussed in these slides are Management Practices, Cloud Resources, Cloud Environment. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Hybrid It Cloud Server Security Architecture
Hybrid It Cloud Server Security ArchitectureFollowing slide showcases architecture of hybrid IT cloud server security, also including elements such as IAAS provider A,B,C, on premises, mergers and acquisitions, etc. Presenting our set of slides with Hybrid It Cloud Server Security Architecture. This exhibits information on fourstages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on On Premises, Mergers And Acquisitions, Security Architecture.
-
 Cloud Virtualization Icon Showcasing Data Security
Cloud Virtualization Icon Showcasing Data SecurityPresenting our set of slides with name Cloud Virtualization Icon Showcasing Data Security This exhibits information on Threestages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloud Virtualization Icon, Showcasing Data Security
-
 Key Parameters Of Cloud Technology Security Stack
Key Parameters Of Cloud Technology Security StackThis slide showcases the important elements of cloud technology security stack which helps an organization to reduce competencies and delegate activities that increases development. It include details such as identify access management, pentesting tools, cloud access security broker, etc. Introducing our premium set of slides with name Key Parameters Of Cloud Technology Security Stack Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identity Access Management, Pentesting Tools, Cloud Database . So download instantly and tailor it with your information.
-
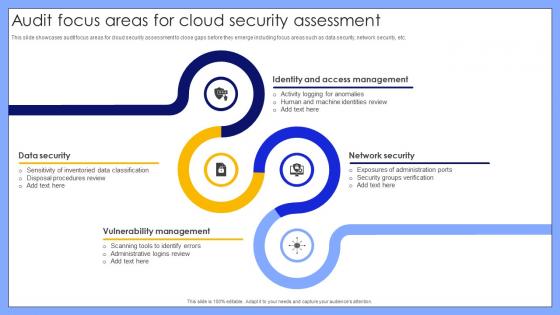 Audit Focus Areas For Cloud Security Assessment
Audit Focus Areas For Cloud Security AssessmentThis slide showcases audit focus areas for cloud security assessment to close gaps before they emerge including focus areas such as data security, network security, etc. Introducing our premium set of slides with name Audit Focus Areas For Cloud Security Assessment. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Security, Vulnerability Management, Network Security, Identity And Access Management. So download instantly and tailor it with your information.
-
 Cloud Security Audit Checklist For Businesses
Cloud Security Audit Checklist For BusinessesThis slide showcases checklist for cloud security audit to fix loopholes including checkpoints such as identifying cloud providers and services, access level management in cloud, etc. Introducing our Cloud Security Audit Checklist For Businesses set of slides. The topics discussed in these slides are Identify Cloud Providers And Services, Encrypt Data In Transit, Detecting Unusual Or Suspicious Activity. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Security Audit Techniques For Operational Efficiency
Cloud Security Audit Techniques For Operational EfficiencyThis slide showcases cloud security audit techniques to analyze data retention such as configuration review, access controls assessments, etc. Introducing our premium set of slides with name Cloud Security Audit Techniques For Operational Efficiency. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Configuration Review, Access Controls Assessment, Patch Management Review, Vendor Security Evaluation. So download instantly and tailor it with your information.
-
 Cloud Security Challenges And Solutions For Internal Audit
Cloud Security Challenges And Solutions For Internal AuditThis slide showcases solutions to overcome cloud security challenges for internal audit to ensure data protection such as lack of visibility, compliance, shared responsibility, etc. Presenting our well structured Cloud Security Challenges And Solutions For Internal Audit. The topics discussed in this slide are Lack Of Visibility, Compliance, Shared Responsibility, Identity And Access Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cloud Security Configuration Audit Icon
Cloud Security Configuration Audit IconPresenting our set of slides with name Cloud Security Configuration Audit Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloud Security, Configuration Audit Icon.
-
 Comparative Analysis Of Open Source Cloud Security Audit Tools
Comparative Analysis Of Open Source Cloud Security Audit ToolsThis slide showcases open source cloud security audit tools comparison to improve organizational position such as. Introducing our Comparative Analysis Of Open Source Cloud Security Audit Tools set of slides. The topics discussed in these slides are Comparative Analysis, Cloud Security Audit Tools, Audit Tools Comparison, Organizational Position. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Solutions To Overcome Cloud Security Audit Challenges
Solutions To Overcome Cloud Security Audit ChallengesThis slide showcases challenges and solutions of cloud security audit to standardize workloads including challenges such as effective communication, encryption strategy, etc. Presenting our set of slides with name Solutions To Overcome Cloud Security Audit Challenges. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Effective Communication, Encryption Strategy, Address Colocation, Scale And Complexity.
-
 Standards Covering Cloud Security Audit
Standards Covering Cloud Security AuditThis slide showcases standards related to cloud security audit to safeguard data and systems such as implementation, CIS foundation benchmarks, etc. Introducing our premium set of slides with name Standards Covering Cloud Security Audit. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Policies For Governance, Cloud Control Matrix, Cloud Security Audit. So download instantly and tailor it with your information.
-
 Steps To Conduct Cloud Security Audit
Steps To Conduct Cloud Security AuditThis slide showcases process to conduct cloud security audit for risk assessment such as evaluating cloud provider security, determining attack surface, etc. Presenting our well structured Steps To Conduct Cloud Security Audit. The topics discussed in this slide are Evaluate Cloud Provider Security, Determine Attack Surface, Automate Patching, Cloud Security Audit. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Features Of Virtual Private Cloud
Security Features Of Virtual Private CloudThis slide covers four essential security features of a Virtual Private Cloud VPC The purpose of this template is to educate the audience about the robust security measures available in VPCs, including examples of their real-life applications. It includes Access control lists ACLs, Security groups, Network isolation, and Data encryption. Presenting our set of slides with Security Features Of Virtual Private Cloud. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Isolation, Data Encryption, Security Groups.
-
 Virtual Private Cloud Icon Representing Data Security
Virtual Private Cloud Icon Representing Data SecurityPresenting our set of slides with Virtual Private Cloud Icon Representing Data Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Security, Representing, Cloud Icon.





