Powerpoint Templates and Google slides for Secure It
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Zero Trust Policy And Why You Should Embrace It Cloud Information Security
Zero Trust Policy And Why You Should Embrace It Cloud Information SecurityThis slide represents the zero trust policy and why organizations should embrace it, and how user access control is managed under the zero trust policy.Deliver an outstanding presentation on the topic using this Zero Trust Policy And Why You Should Embrace It Cloud Information Security Dispense information and present a thorough explanation of Zones Separate, Give Access, Best Example using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Evaluating It System Security Using Swot Analysis Building A Security Awareness Program
Evaluating It System Security Using Swot Analysis Building A Security Awareness ProgramThe purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Increase audience engagement and knowledge by dispensing information using Evaluating It System Security Using Swot Analysis Building A Security Awareness Program. This template helps you present information on four stages. You can also present information on Strengths, Weakness, Opportunities, Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Most Effective It Security Tools For Protection Against Insider Threat
Most Effective It Security Tools For Protection Against Insider ThreatThis slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM Introducing our premium set of slides with Most Effective It Security Tools For Protection Against Insider Threat. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Loss Prevention, User Entity Behavior, Identity Access Management. So download instantly and tailor it with your information.
-
 Smart Enterprise Digitalization IT OT Convergence Security Objectives Challenges Catalysts
Smart Enterprise Digitalization IT OT Convergence Security Objectives Challenges CatalystsThis slide covers objectives challenges catalysts and benefits of the Security in IT or OT convergence and Reduce systems cyberattack surface. Increase audience engagement and knowledge by dispensing information using Smart Enterprise Digitalization IT OT Convergence Security Objectives Challenges Catalysts. This template helps you present information on four stages. You can also present information on Objectives, Catalysts, Resources, Challenges, Benefits using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Computing Security Difference Between Cloud Security Solutions And Traditional IT Solutions
Cloud Computing Security Difference Between Cloud Security Solutions And Traditional IT SolutionsThis slide represents the difference between cloud security solutions and traditional IT solutions based on information centers, cost, scalability, and expenses. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security Difference Between Cloud Security Solutions And Traditional IT Solutions. This template helps you present information on two stages. You can also present information on Cloud Security, Traditional It Security, Low Efficiency using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Security Labor Items In Powerpoint And Google Slides Cpb
Social Security Labor Items In Powerpoint And Google Slides CpbPresenting Social Security Labor Items In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Social Security Labor Items. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Big Data And Its Types Security Of Information In Big Data Ppt PowerPoint Presentation gallery
Big Data And Its Types Security Of Information In Big Data Ppt PowerPoint Presentation galleryThis slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on. Increase audience engagement and knowledge by dispensing information using Big Data And Its Types Security Of Information In Big Data Ppt PowerPoint Presentation gallery. This template helps you present information on two stages. You can also present information on Challenges, Solution, Data Collections using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Post It Notes Security Services Business Profile Ppt Sample
Post It Notes Security Services Business Profile Ppt SampleIncrease audience engagement and knowledge by dispensing information using Post It Notes Security Services Business Profile Ppt Sample. This template helps you present information on three stages. You can also present information on Post It Notes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 CIOS Handbook For IT Role Of Management In Effective Information Security Governance
CIOS Handbook For IT Role Of Management In Effective Information Security GovernanceThis slide provides information regarding role of management in effective information security governance in strategic alignment, risk management, integration, value delivery, etc. Present the topic in a bit more detail with this CIOS Handbook For IT Role Of Management In Effective Information Security Governance. Use it as a tool for discussion and navigation on Strategic Alignment, Risk Management, Security Governance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Approaches To Manage IT Service
Application Security Approaches To Manage IT ServiceThis slide exhibits the various application security approaches which can be implemented by organization to manage their IT services. The key approaches are design review, code review and application security audit. Introducing our Application Security Approaches To Manage IT Service set of slides. The topics discussed in these slides are Approaches, Design Review, Code Review, Key Activities. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Icon For Managed IT Security Service
Icon For Managed IT Security ServicePresenting our set of slides with Icon For Managed IT Security Service. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon For Managed, IT Security Service.
-
 It Security Audit With Risk Level Procedure To Perform Digital Marketing Audit
It Security Audit With Risk Level Procedure To Perform Digital Marketing AuditThis slide highlights the security audit which showcase the risks related to accounts and user computers and also states the data which are at high risk. Present the topic in a bit more detail with this It Security Audit With Risk Level Procedure To Perform Digital Marketing Audit. Use it as a tool for discussion and navigation on Inactive User Accounts, Inactive Computer Accounts, Empty Security Groups. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F472 Role Of Management In Effective Information Security It Cost Optimization Priorities By Cios
F472 Role Of Management In Effective Information Security It Cost Optimization Priorities By CiosThis slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an outstanding presentation on the topic using this F472 Role Of Management In Effective Information Security It Cost Optimization Priorities By Cioss. Dispense information and present a thorough explanation of Information, Security, Governance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
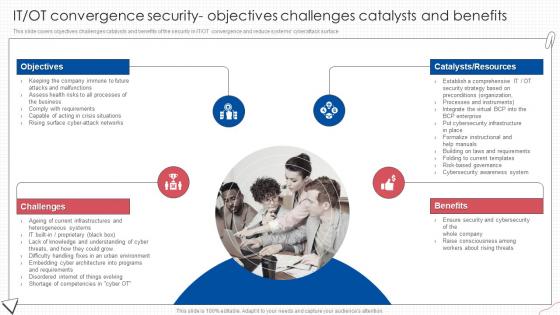 IT OT Convergence Security Objectives Digital Transformation Of Operational Industries
IT OT Convergence Security Objectives Digital Transformation Of Operational IndustriesThis slide covers objectives challenges catalysts and benefits of the security in IT OT convergence and reduce systems cyberattack surface.Introducing IT OT Convergence Security Objectives Digital Transformation Of Operational Industries to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Benefits, Consciousness Among, using this template. Grab it now to reap its full benefits.
-
 Major Saas Security Challenges For It Department
Major Saas Security Challenges For It DepartmentThe following slide highlights some SaaS security challenges faced by IT team to plan mitigation actions. It mainly includes file security, insider threat, privilege access etc. Introducing our premium set of slides with Major Saas Security Challenges For It Department. Elucidate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Department, Neglecting Employees, Permissions. So download instantly and tailor it with your information.
-
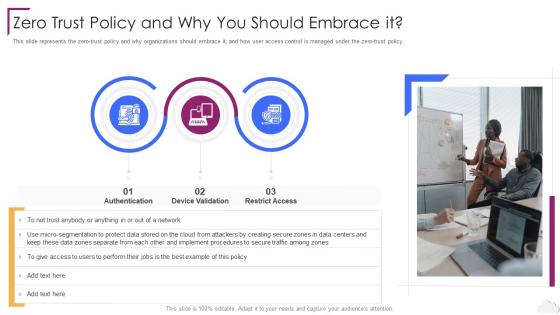 Cloud Computing Security Zero Trust Policy And Why You Should Embrace It
Cloud Computing Security Zero Trust Policy And Why You Should Embrace ItThis slide represents the zero trust policy and why organizations should embrace it, and how user access control is managed under the zero trust policy. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security Zero Trust Policy And Why You Should Embrace It. This template helps you present information on three stages. You can also present information on Authentication, Device Validation, Restrict Access using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Business IT Security Framework With Safety Programs
Business IT Security Framework With Safety ProgramsThis slide outlines the strategic security framework created by an organization to overcome potential external or internal threats along with security programs. Risks include hacking and accidental data disclosure with certain protective programs like anti-spyware software and cloud security. Introducing our premium set of slides with Business IT Security Framework With Safety Programs. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Organization Strategy, Assess Potential Threats, Identify Current Safeguard. So download instantly and tailor it with your information.
-
 Certified Information Systems Security Professional Top 15 IT Certifications In Demand For 2022
Certified Information Systems Security Professional Top 15 IT Certifications In Demand For 2022This slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications. Increase audience engagement and knowledge by dispensing information using Certified Information Systems Security Professional Top 15 IT Certifications In Demand For 2022. This template helps you present information on four stages. You can also present information on Become Certified, Certification, Information Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IT Security Audit With Risk Level Complete Guide To Conduct Digital Marketing Audit
IT Security Audit With Risk Level Complete Guide To Conduct Digital Marketing AuditThis slide highlights the security audit which showcase the risks related to accounts and user computers and also states the data which are at high risk. Present the topic in a bit more detail with this IT Security Audit With Risk Level Complete Guide To Conduct Digital Marketing Audit. Use it as a tool for discussion and navigation on Risks, Current Value, Risk Level. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Q308 IT Professionals Certification Collection Certified Information Systems Security Professional
Q308 IT Professionals Certification Collection Certified Information Systems Security ProfessionalThis slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications. Introducing Q308 IT Professionals Certification Collection Certified Information Systems Security Professional to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on CISS Certification, Network Security, Administrative Activities, using this template. Grab it now to reap its full benefits.
-
 Solutions To Overcome Various IT Security Challenges
Solutions To Overcome Various IT Security ChallengesThis slide shows solutions to various challenges faced by organizations to provide information technology security. These challenges are data breaches, lack of expertise, insider threats and unsecured APIs. Introducing our premium set of slides with Solutions To Overcome Various IT Security Challenges. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Breaches, Lack Of Expertise, Insider Threats. So download instantly and tailor it with your information.
-
 Various Impact Of Cybercrime On IT Security
Various Impact Of Cybercrime On IT SecurityThis slide shows the adverse impact of cybercrime on information technology companies. These impacts are increased costs, operational disruption, revenue loss and stolen intellectual property. Introducing our premium set of slides with Various Impact Of Cybercrime On IT Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Increase Costs, Operational Disruption, Revenue Loss, Stolen Intellectual Property. So download instantly and tailor it with your information.
-
 IT Security Risk Mitigation Strategies Icon
IT Security Risk Mitigation Strategies IconPresenting our well-structured IT Security Risk Mitigation Strategies Icon. The topics discussed in this slide are IT Security, Risk Mitigation Strategies, Icon. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 IT Security Threat Mitigation Strategies
IT Security Threat Mitigation StrategiesThe slide covers strategies to prevent IT security threats for reducing overall impact of risks or attacks on business. It includes four strategies such as risk assessment, network access control, incident response plan and regular network traffic monitoring Introducing our premium set of slides with IT Security Threat Mitigation Strategies. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Risk Assessment, Network Access Controls, Incident Response Plan, Regular Network Traffic Monitoring. So download instantly and tailor it with your information.
-
 IT Risk Management Strategies Detection And Prevention Of Management Security Controls
IT Risk Management Strategies Detection And Prevention Of Management Security ControlsThe following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Introducing IT Risk Management Strategies Detection And Prevention Of Management Security Controls to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Preventive Management, Security Controls, Detection Management, using this template. Grab it now to reap its full benefits.
-
 IT Risk Management Strategies Financial Burden To Company From It Security Breaches
IT Risk Management Strategies Financial Burden To Company From It Security BreachesThis slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Present the topic in a bit more detail with this IT Risk Management Strategies Financial Burden To Company From It Security Breaches. Use it as a tool for discussion and navigation on Professional Services, Lost Business Opportunities, Total Damage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Risk Management Strategies IT Security Residual Risk Matrix With Response Actions
IT Risk Management Strategies IT Security Residual Risk Matrix With Response ActionsThis slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Deliver an outstanding presentation on the topic using this IT Risk Management Strategies IT Security Residual Risk Matrix With Response Actions. Dispense information and present a thorough explanation of Control Topic, Evaluation Question, Response Action, Threat using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation Plan
IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation PlanThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Increase audience engagement and knowledge by dispensing information using IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation Plan. This template helps you present information on one stages. You can also present information on Threat, Risk, Risk Priority, Risk Reduction Timeline using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IT Risk Management Strategies Security Criteria And Control Measures For IT System Vulnerabilities
IT Risk Management Strategies Security Criteria And Control Measures For IT System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Introducing IT Risk Management Strategies Security Criteria And Control Measures For It System Vulnerabilities to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Security, Operational Security, Technical Security, using this template. Grab it now to reap its full benefits.
-
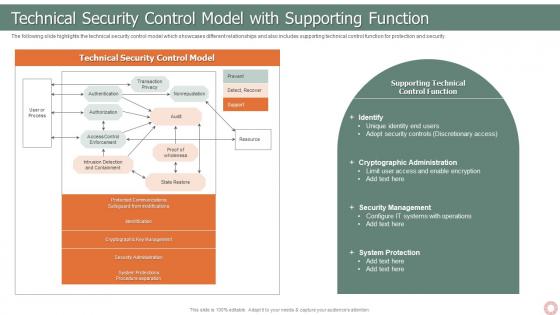 IT Risk Management Strategies Technical Security Control Model With Supporting Function
IT Risk Management Strategies Technical Security Control Model With Supporting FunctionThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Introducing IT Risk Management Strategies Technical Security Control Model With Supporting Function to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Technical Security, Control Model, Transaction Privacy, State Restore, using this template. Grab it now to reap its full benefits.
-
 Enterprise Risk Management Financial Burden To Company From IT Security Breaches
Enterprise Risk Management Financial Burden To Company From IT Security BreachesThis slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Deliver an outstanding presentation on the topic using this Enterprise Risk Management Financial Burden To Company From IT Security Breaches. Dispense information and present a thorough explanation of Professional Services, Lost Business Opportunities, Total Damage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Risk Management IT Security Residual Risk Matrix With Response Actions
Enterprise Risk Management IT Security Residual Risk Matrix With Response ActionsThis slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Present the topic in a bit more detail with this Enterprise Risk Management IT Security Residual Risk Matrix With Response Actions. Use it as a tool for discussion and navigation on Control Topic, Evaluation Question, Response Action, Threat. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise Risk Management Security Criteria And Control Measures For IT System Vulnerabilities
Enterprise Risk Management Security Criteria And Control Measures For IT System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Introducing Enterprise Risk Management Security Criteria And Control Measures For IT System Vulnerabilities to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Security, Operational Security, Technical Security, using this template. Grab it now to reap its full benefits.
-
 IT Security Residual Risk Matrix With Risk Management Guide For Information Technology Systems
IT Security Residual Risk Matrix With Risk Management Guide For Information Technology SystemsThis slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Deliver an outstanding presentation on the topic using this IT Security Residual Risk Matrix With Risk Management Guide For Information Technology Systems. Dispense information and present a thorough explanation of Database Access, Evaluation Question, Response Action using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Criteria And Control Measures For IT System Vulnerabilities
Security Criteria And Control Measures For IT System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Introducing Security Criteria And Control Measures For IT System Vulnerabilities to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Security, Operational Security, Technical Security, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Elements IT Application Security Element Of Cyber Security Ppt Background
Cyber Security Elements IT Application Security Element Of Cyber Security Ppt BackgroundThis slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. The application threat categories include input validation, authorization, session management, parameter tampering, and encryption. Present the topic in a bit more detail with this Cyber Security Elements IT Application Security Element Of Cyber Security Ppt Background. Use it as a tool for discussion and navigation on Session Management, Application Security, Application Threat Categories. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Elements IT Career Opportunities In Cybersecurity Profession Ppt Mockup
Cyber Security Elements IT Career Opportunities In Cybersecurity Profession Ppt MockupThis slide depicts the career opportunities in cybersecurity, including various job roles such as chief information security officer, chief security office, security engineers, architects, analysts and penetration testers. Introducing Cyber Security Elements IT Career Opportunities In Cybersecurity Profession Ppt Mockup to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Deploys Security, Security Engineers, Security Architects, Security Analysts, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Elements IT Cloud Security Element Of Cyber Security Ppt Slides
Cyber Security Elements IT Cloud Security Element Of Cyber Security Ppt SlidesThis slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. It also caters to best practices and the security framework of the cloud. Present the topic in a bit more detail with this Cyber Security Elements IT Cloud Security Element Of Cyber Security Ppt Slides. Use it as a tool for discussion and navigation on Security Framework, Protect, Identify, Respond. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Elements IT Disaster Recovery Planning Element Of Cyber Security Ppt Microsoft
Cyber Security Elements IT Disaster Recovery Planning Element Of Cyber Security Ppt MicrosoftThis slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. It also contains the types of disaster recovery plans and planning process. Deliver an outstanding presentation on the topic using this Cyber Security Elements IT Disaster Recovery Planning Element Of Cyber Security Ppt Microsoft. Dispense information and present a thorough explanation of Disaster Recovery, Planning Element, Cyber Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Elements IT End User Security Element Of Cyber Security Ppt Sample
Cyber Security Elements IT End User Security Element Of Cyber Security Ppt SampleThis slide shows the end user education within the cyber security model. It also represents various factors that effective training plans should involve, such as hiring professionals, identifying weakest points in systems, assessing employees knowledge of cyber security and so on. Introducing Cyber Security Elements IT End User Security Element Of Cyber Security Ppt Sample to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Security Element, Cyber Security, Microlearning Opportunities, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Elements IT Information Security Element Of Cyber Security Ppt Microsoft
Cyber Security Elements IT Information Security Element Of Cyber Security Ppt MicrosoftThis slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. These are also known as cyber security objectives. Increase audience engagement and knowledge by dispensing information using Cyber Security Elements IT Information Security Element Of Cyber Security Ppt Microsoft. This template helps you present information on three stages. You can also present information on Confidentiality, Availability, Integrity, Information Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Elements IT Network Security Element Of Cyber Security Ppt Background
Cyber Security Elements IT Network Security Element Of Cyber Security Ppt BackgroundThis slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, end point security, virtual private security and antivirus software. Introducing Cyber Security Elements IT Network Security Element Of Cyber Security Ppt Background to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Email Security, Virtual Private Network, Antivirus Software, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Elements IT Operational Security Element Of Cyber Security Ppt Introduction
Cyber Security Elements IT Operational Security Element Of Cyber Security Ppt IntroductionThis slide defines the operational security element of cyber security. It also shows the best practices for operational security, such as changing management processes, deploying automation, planning for disasters, restricting device access, and implementing dual control. Increase audience engagement and knowledge by dispensing information using Cyber Security Elements IT Operational Security Element Of Cyber Security Ppt Introduction. This template helps you present information on five stages. You can also present information on Deploy Automation, Restrict Device Access, Change Management Processes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Elements IT Principles Of Cyber Security Ppt Demonstration
Cyber Security Elements IT Principles Of Cyber Security Ppt DemonstrationThis slide depicts cyber security principles, including work factor, compromising recording, the economy of mechanism, fail safe defaults, complete mediation, open design, separation of privilege, least privilege, least common mechanism, and so on. Introducing Cyber Security Elements IT Principles Of Cyber Security Ppt Demonstration to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Separation Of Privilege, Open Design, Economy Of Mechanism, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Elements IT Tools Used For Cyber Security Goals Ppt Brochure
Cyber Security Elements IT Tools Used For Cyber Security Goals Ppt BrochureThis slide outlines the tools used to achieve cyber security goals such as confidentiality, integrity, and availability. The tools for confidentiality include encryption, access control, authentication, authentication, authorization, and physical security. Increase audience engagement and knowledge by dispensing information using Cyber Security Elements IT Tools Used For Cyber Security Goals Ppt Brochure. This template helps you present information on one stage. You can also present information on Tools For Confidentiality, Tools For Integrity, Tools For Availability using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Elements IT Types Of Cyber Attackers Ppt Professional
Cyber Security Elements IT Types Of Cyber Attackers Ppt ProfessionalThis slide represents the types of cyber attackers, including cyber criminals, hacktivists, state sponsored attackers, and insider threats. Insider threats can be occurred from within the organization and can be malicious, accidental or negligent. Introducing Cyber Security Elements IT Types Of Cyber Attackers Ppt Professional to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Criminals, Insider Threats, Hacktivists, using this template. Grab it now to reap its full benefits.
-
 Comparison Analysis Of Traditional Vs Cloud It Security
Comparison Analysis Of Traditional Vs Cloud It SecurityThis slide showcases the difference between the cloud computer security and standard computer security that enable manager to choose the best strategy. It shows the variation of data centers, initial cost investment, price, time to market and so on Introducing our premium set of slides with Comparison Analysis Of Traditional Vs Cloud It Security. Elucidate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cloud Security, Traditional IT Security. So download instantly and tailor it with your information.
-
 Role Of Security In Open Ran Standards Open Ran It Ppt Show Background Images
Role Of Security In Open Ran Standards Open Ran It Ppt Show Background ImagesThis slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. Deliver an outstanding presentation on the topic using this Role Of Security In Open Ran Standards Open Ran It Ppt Show Background Images. Dispense information and present a thorough explanation of Assessment, Methodology, Requirements using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Evaluating It System Security Using Swot Analysis Developing Cyber Security Awareness Training Program
Evaluating It System Security Using Swot Analysis Developing Cyber Security Awareness Training ProgramThe purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Introducing Evaluating It System Security Using Swot Analysis Developing Cyber Security Awareness Training Program to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strengths, Weaknesses, Opportunities, Threats, using this template. Grab it now to reap its full benefits.
-
 Amrs In Autonomous Security Robots Asrs Autonomous Mobile Robots It
Amrs In Autonomous Security Robots Asrs Autonomous Mobile Robots ItThis slide describes the application of autonomous security robots to help security personnel. AMRs are also beneficial for cutting the high personnel costs and a thorough inspection of the incidents if anything suspicious is found. Introducing Amrs In Autonomous Security Robots Asrs Autonomous Mobile Robots It to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Autonomous, Inspection, Analysis, using this template. Grab it now to reap its full benefits.
-
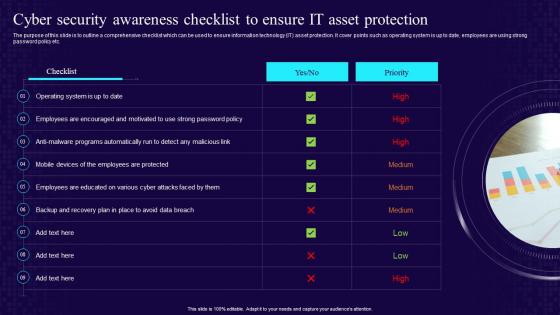 Developing Cyber Security Awareness Cyber Security Awareness Checklist To Ensure It Asset Protection
Developing Cyber Security Awareness Cyber Security Awareness Checklist To Ensure It Asset ProtectionThe purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Introducing Developing Cyber Security Awareness Cyber Security Awareness Checklist To Ensure It Asset Protection to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Security, Awareness Checklist, IT Asset Protection, using this template. Grab it now to reap its full benefits.
-
 Response Workflow For It Security Incident Management
Response Workflow For It Security Incident ManagementPresenting our well structured Response Workflow For It Security Incident Management. The topics discussed in this slide are Investigation, Contain And Restore, Data Protection . This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Secure Sockets Layer SSL Proxy Server And Its Architecture Reverse Proxy Load Balancer Ppt Themes
Secure Sockets Layer SSL Proxy Server And Its Architecture Reverse Proxy Load Balancer Ppt ThemesThis slide represents the SSL proxy server, how this proxy decrypts the information between client and server, and how it hides its existence from client and server. Deliver an outstanding presentation on the topic using this Secure Sockets Layer SSL Proxy Server And Its Architecture Reverse Proxy Load Balancer Ppt Themes. Dispense information and present a thorough explanation of Conjunction, Engine Position, Architecture, Secure Sockets Layer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Network It Security Automation Enabling Automation In Cyber Security Operations
Enterprise Network It Security Automation Enabling Automation In Cyber Security OperationsThis slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Deliver an outstanding presentation on the topic using this Enterprise Network It Security Automation Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Orchestrating Network Security, Troubleshooting, Integrating Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Why To Automate The It Security Process Enabling Automation In Cyber Security Operations
Why To Automate The It Security Process Enabling Automation In Cyber Security OperationsThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Increase audience engagement and knowledge by dispensing information using Why To Automate The It Security Process Enabling Automation In Cyber Security Operations. This template helps you present information on five stages. You can also present information on Better Threat Detection, Faster Containment, Improve Productivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 F638 Certified Information Systems Security Professional Cissp Details It Certifications To Expand Your Skillset
F638 Certified Information Systems Security Professional Cissp Details It Certifications To Expand Your SkillsetThis slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications Deliver an outstanding presentation on the topic using this F638 Certified Information Systems Security Professional Cissp Details It Certifications To Expand Your Skillset. Dispense information and present a thorough explanation of Certification, Security Professional, Information Systems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F639 Certified Information Systems Security Professional Cissp Details It Certifications To Expand Your Skillset
F639 Certified Information Systems Security Professional Cissp Details It Certifications To Expand Your SkillsetThis slide covers information about CISSP Examination such as weight of each domain in exams, prep courses details, qualification details etc. Present the topic in a bit more detail with this F639 Certified Information Systems Security Professional Cissp Details It Certifications To Expand Your Skillset. Use it as a tool for discussion and navigation on Examination, Information, Professional. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Architecture And Security Multi Cloud It Environments After Implementing Solutions
Cloud Architecture And Security Multi Cloud It Environments After Implementing SolutionsThis slide covers the running all the workloads on a variety of clouds including public cloud, third party public clouds, hosted private clouds, and colocation servers while managing them. Increase audience engagement and knowledge by dispensing information using Cloud Architecture And Security Multi Cloud It Environments After Implementing Solutions. This template helps you present information on seven stages. You can also present information on Colocation, Hosted Private Cloud, Migration Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 About Us It Consulting Firm Introduction Cloud Architecture And Security Review
About Us It Consulting Firm Introduction Cloud Architecture And Security ReviewThis slide covers the introduction for IT consultancy firm including a brief about company and the major clients they have captured. Present the topic in a bit more detail with this About Us It Consulting Firm Introduction Cloud Architecture And Security Review. Use it as a tool for discussion and navigation on Meeting And Surpassing, Reviewing And Evaluating, Return On Investment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Awareness Checklist To Ensure IT Asset Protection Conducting Security Awareness
Cyber Security Awareness Checklist To Ensure IT Asset Protection Conducting Security AwarenessThe purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Present the topic in a bit more detail with this Cyber Security Awareness Checklist To Ensure IT Asset Protection Conducting Security Awareness. Use it as a tool for discussion and navigation on Checklist, Operating System, Employees Encouraged. This template is free to edit as deemed fit for your organization. Therefore download it now.





