Powerpoint Templates and Google slides for Secure It
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 What Role Does SDN Play In Customer Security Software Defined Networking IT
What Role Does SDN Play In Customer Security Software Defined Networking ITThis slide represents the role of software defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Introducing What Role Does SDN Play In Customer Security Software Defined Networking IT to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Provides Several, Cybersecurity Advantages, Customer Security, using this template. Grab it now to reap its full benefits.
-
 Security Architecture In 5G Technology Working Of 5G Technology IT Ppt Topics
Security Architecture In 5G Technology Working Of 5G Technology IT Ppt TopicsThis slide represents the security architecture in 5G technology, including the system wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration. Present the topic in a bit more detail with this Security Architecture In 5G Technology Working Of 5G Technology IT Ppt Topics. Use it as a tool for discussion and navigation on Security Architecture, Technology, Security Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security In 5G Technology Architecture Working Of 5G Technology IT Ppt Ideas
Security In 5G Technology Architecture Working Of 5G Technology IT Ppt IdeasThis slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Increase audience engagement and knowledge by dispensing information using Security In 5G Technology Architecture Working Of 5G Technology IT Ppt Ideas. This template helps you present information on five stages. You can also present information on Mobile Technologys, Service, Delivery Process using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IT In Manufacturing Industry Managing Cyber Security In Manufacturing 90 Days Plan
IT In Manufacturing Industry Managing Cyber Security In Manufacturing 90 Days PlanThis slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Deliver an outstanding presentation on the topic using this IT In Manufacturing Industry Managing Cyber Security In Manufacturing 90 Days Plan. Dispense information and present a thorough explanation of Communication Methods, Training Completion, Awareness Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT In Manufacturing Industry Role Of Cyber Security In Manufacturing Automation
IT In Manufacturing Industry Role Of Cyber Security In Manufacturing AutomationThis slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Present the topic in a bit more detail with this IT In Manufacturing Industry Role Of Cyber Security In Manufacturing Automation. Use it as a tool for discussion and navigation on Threat And Risk Analysis, Network Security Evaluation, Workshops And Trainings. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managing Cyber Security In Manufacturing 30 Days Plan IT In Manufacturing Industry
Managing Cyber Security In Manufacturing 30 Days Plan IT In Manufacturing IndustryThis slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Present the topic in a bit more detail with this Managing Cyber Security In Manufacturing 30 Days Plan IT In Manufacturing Industry. Use it as a tool for discussion and navigation on Phishing Awareness, Facility Physical Security, Phishing Reporting. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managing Cyber Security In Manufacturing 60 Days Plan IT In Manufacturing Industry
Managing Cyber Security In Manufacturing 60 Days Plan IT In Manufacturing IndustryThis slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Deliver an outstanding presentation on the topic using this Managing Cyber Security In Manufacturing 60 Days Plan IT In Manufacturing Industry. Dispense information and present a thorough explanation of Data Loss Incidents, Security Operations Center, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Security Management Icon For IT Project
Cloud Security Management Icon For IT ProjectIntroducing our premium set of slides with Cloud Security Management Icon For IT Project. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cloud Security Management, Icon For It Project. So download instantly and tailor it with your information.
-
 Cloud Security Strategic Checklist For It Business
Cloud Security Strategic Checklist For It BusinessThis slide shows checklist which can be used by organizations to develop cloud security plan. It includes points such as change passwords every week, make multi factor authentication mandatory, enable anti phishing protections, etc. Presenting our well structured Cloud Security Strategic Checklist For It Business. The topics discussed in this slide are Cloud Security, Strategic Checklist, Business. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Sensor Networks IT CR WSNs In Military And Public Security Applications
Sensor Networks IT CR WSNs In Military And Public Security ApplicationsThis slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. Increase audience engagement and knowledge by dispensing information using Sensor Networks IT CR WSNs In Military And Public Security Applications. This template helps you present information on six stages. You can also present information on Targeting, Assistant Intelligence, Command And Control using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Policy Checklist For Writing An Effective It Policy
Cyber Security Policy Checklist For Writing An Effective It PolicyThis slide describes the checklist for an effective information technology policy, and it includes all the best practices that should be considered while writing an IT policy. Present the topic in a bit more detail with this Cyber Security Policy Checklist For Writing An Effective It Policy. Use it as a tool for discussion and navigation on Assessment, Essential, Weaknesses. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
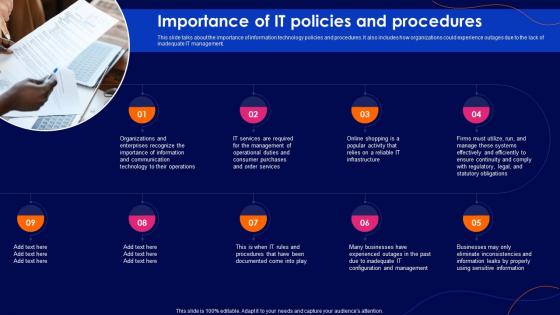 Cyber Security Policy Importance Of It Policies And Procedures
Cyber Security Policy Importance Of It Policies And ProceduresThis slide talks about the importance of information technology policies and procedures. It also includes how organizations could experience outages due to the lack of inadequate IT management. Increase audience engagement and knowledge by dispensing information using Cyber Security Policy Importance Of It Policies And Procedures. This template helps you present information on nine stages. You can also present information on Services, Operational, Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Policy It Ppt Show Graphics Template
Cyber Security Policy It Ppt Show Graphics TemplatePresent the topic in a bit more detail with this Cyber Security Policy It Ppt Show Graphics Template. Use it as a tool for discussion and navigation on Cyber Security Policy It. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
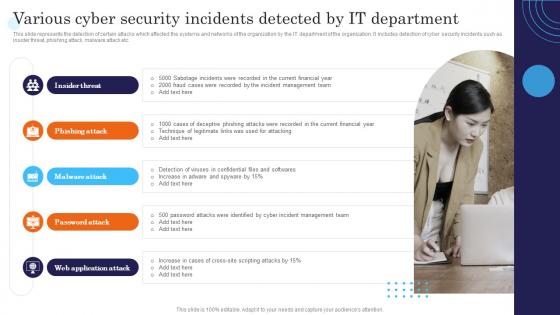 Various Cyber Security Incidents Detected By IT Department Incident Response Strategies Deployment
Various Cyber Security Incidents Detected By IT Department Incident Response Strategies DeploymentThis slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Introducing Various Cyber Security Incidents Detected By IT Department Incident Response Strategies Deployment to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Insider, Phishing, Application, using this template. Grab it now to reap its full benefits.
-
 Impact Analysis For Effective Threat Management In Securing Managing IT Threats At Workplace Overview
Impact Analysis For Effective Threat Management In Securing Managing IT Threats At Workplace OverviewThis slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Present the topic in a bit more detail with this Impact Analysis For Effective Threat Management In Securing Managing IT Threats At Workplace Overview. Use it as a tool for discussion and navigation on Analysis, Threat Management, Securing Workplace. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Selecting Secured Threat Management Software Managing IT Threats At Workplace Overview
Selecting Secured Threat Management Software Managing IT Threats At Workplace OverviewThis slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an outstanding presentation on the topic using this Selecting Secured Threat Management Software Managing IT Threats At Workplace Overview. Dispense information and present a thorough explanation of Secured, Management, Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Policy Information Security Policy For Employees Ppt Professional
IT Policy Information Security Policy For Employees Ppt ProfessionalThis slide depicts the information security policy that critical topics covered in this policy. It also covers the reasons for frequent changes in the policy. Introducing IT Policy Information Security Policy For Employees Ppt Professional to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Company Infrastructure, Policy That Changes , Key Topics Covered, using this template. Grab it now to reap its full benefits.
-
 IT Policy Overview Of Network Security Policy For Workers Ppt Diagrams
IT Policy Overview Of Network Security Policy For Workers Ppt DiagramsThis slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Introducing IT Policy Overview Of Network Security Policy For Workers Ppt Diagrams to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, Reviews Regularly, Confidentiality, Integrity, using this template. Grab it now to reap its full benefits.
-
 IT Policy Security Awareness And Training Policy Overview Ppt Diagrams
IT Policy Security Awareness And Training Policy Overview Ppt DiagramsThis slide represents the security awareness and training policy. It covers that the training program should be designed by management, and employees will sign a confidentiality agreement after getting the training. Introducing IT Policy Security Awareness And Training Policy Overview Ppt Diagrams to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Security Awareness, Training Policy, Training, using this template. Grab it now to reap its full benefits.
-
 How Amazon Secured Brand Position Amazon Business Strategy Understanding Its Core Competencies
How Amazon Secured Brand Position Amazon Business Strategy Understanding Its Core CompetenciesThis slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries. Present the topic in a bit more detail with this How Amazon Secured Brand Position Amazon Business Strategy Understanding Its Core Competencies. Use it as a tool for discussion and navigation on Product Selection, Several Features And Services, Amazons Subsidiaries . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Initiatives Playbook Dashboard To Track IT Security Incidents Prevailing Across Firm
Strategic Initiatives Playbook Dashboard To Track IT Security Incidents Prevailing Across FirmThis slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Deliver an outstanding presentation on the topic using this Strategic Initiatives Playbook Dashboard To Track IT Security Incidents Prevailing Across Firm. Dispense information and present a thorough explanation of Dashboard, Track IT Security, Incidents Prevailing Across Firm, Restrict Admin Privileges using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Initiatives Playbook IT Risk Management Framework To Manage Security Threats
Strategic Initiatives Playbook IT Risk Management Framework To Manage Security ThreatsThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Deliver an outstanding presentation on the topic using this Strategic Initiatives Playbook IT Risk Management Framework To Manage Security Threats. Dispense information and present a thorough explanation of IT Risk Management, Framework To Manage, Security Threats, Platform Upgradation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Policy Post It Notes Ppt Show Example Introduction
Cyber Security Policy Post It Notes Ppt Show Example IntroductionIntroducing Cyber Security Policy Post It Notes Ppt Show Example Introduction to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Post It Notes, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Policy What Happens In The Absence Of It Policies And Procedures
Cyber Security Policy What Happens In The Absence Of It Policies And ProceduresThis slide represents the consequences of not having IT policies and procedures. Effects include disrupted and inconsistent operational duties, communication gaps between staff and employees, etc. Introducing Cyber Security Policy What Happens In The Absence Of It Policies And Procedures to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Procedures, Information, Corporations, using this template. Grab it now to reap its full benefits.
-
 Dashboard To Track It Security Incidents Prevailing Across Firm IT Cost Optimization And Management Strategy SS
Dashboard To Track It Security Incidents Prevailing Across Firm IT Cost Optimization And Management Strategy SSThis slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Deliver an outstanding presentation on the topic using this Dashboard To Track IT Security Incidents Prevailing Across Firm IT Cost Optimization And Management Strategy SS. Dispense information and present a thorough explanation of Application Whitelisting, Patch Applications, Restrict Admin Privileges using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 How Management Enables Effective Corporate Security IT Cost Optimization And Management Strategy SS
How Management Enables Effective Corporate Security IT Cost Optimization And Management Strategy SSThis slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Introducing How Management Enables Effective Corporate Security IT Cost Optimization And Management Strategy SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Corporate, Security Governance, Management, using this template. Grab it now to reap its full benefits.
-
 Information Security And Governance Management Framework IT Cost Optimization And Management Strategy SS
Information Security And Governance Management Framework IT Cost Optimization And Management Strategy SSThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Deliver an outstanding presentation on the topic using this Information Security And Governance Management Framework IT Cost Optimization And Management Strategy SS. Dispense information and present a thorough explanation of Context, Leadership, Evaluation Direction using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Risk Management Framework To Manage Security Threats IT Cost Optimization And Management Strategy SS
IT Risk Management Framework To Manage Security Threats IT Cost Optimization And Management Strategy SSThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Present the topic in a bit more detail with this IT Risk Management Framework To Manage Security Threats IT Cost Optimization And Management Strategy SS. Use it as a tool for discussion and navigation on Implement Control Environment, Implement Security Processes, Enterprise Security Program. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Various Cyber Security Incidents Detected By It Department Development And Implementation Of Security
Various Cyber Security Incidents Detected By It Department Development And Implementation Of SecurityThis slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Increase audience engagement and knowledge by dispensing information using Various Cyber Security Incidents Detected By It Department Development And Implementation Of Security. This template helps you present information on five stages. You can also present information on Insider Threat, Phishing Attack, Malware Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN IT How Does SD WAN Improve Security Ppt Layouts Slide Portrait
SD WAN IT How Does SD WAN Improve Security Ppt Layouts Slide PortraitThis slide depicts the various security benefits of the software defined wide area network. These advantages include centralized and scalable security, zero touch and segmentation, traffic prioritization from remote locations, traffic encryption and firewalls, cloud connectivity and threat detection and response. Increase audience engagement and knowledge by dispensing information using SD WAN IT How Does SD WAN Improve Security Ppt Layouts Slide Portrait. This template helps you present information on six stages. You can also present information on Centralised And Scalable Security, Segmentation, Traffic Prioritization, Remote Locations using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN IT Secure Access Service Edge Vs SD WAN Ppt Summary Guide
SD WAN IT Secure Access Service Edge Vs SD WAN Ppt Summary GuideThis slide compares secure access service edge and software defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access. Introducing SD WAN IT Secure Access Service Edge Vs SD WAN Ppt Summary Guide to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Deployment And Architecture, Traffic And Connectivity, Security, using this template. Grab it now to reap its full benefits.
-
 Dashboard To Track IT Security Incidents Prevailing Develop Business Aligned IT Strategy
Dashboard To Track IT Security Incidents Prevailing Develop Business Aligned IT StrategyThis slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Deliver an outstanding presentation on the topic using this Dashboard To Track IT Security Incidents Prevailing Develop Business Aligned IT Strategy. Dispense information and present a thorough explanation of Application Whitelisting, Application Hardening, Patch Operating Systems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 How Management Enables Effective Corporate Security Develop Business Aligned IT Strategy
How Management Enables Effective Corporate Security Develop Business Aligned IT StrategyThis slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Deliver an outstanding presentation on the topic using this How Management Enables Effective Corporate Security Develop Business Aligned IT Strategy. Dispense information and present a thorough explanation of Senior Executives, Steering Committees, Chief Security Officer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Governance Management Develop Business Aligned IT Strategy
Information Security And Governance Management Develop Business Aligned IT StrategyThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Present the topic in a bit more detail with this Information Security And Governance Management Develop Business Aligned IT Strategy. Use it as a tool for discussion and navigation on Infrastructure Security, Response And Recovery, Security Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Risk Management Framework To Manage Security Threats Develop Business Aligned IT Strategy
IT Risk Management Framework To Manage Security Threats Develop Business Aligned IT StrategyThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Increase audience engagement and knowledge by dispensing information using IT Risk Management Framework To Manage Security Threats Develop Business Aligned IT Strategy. This template helps you present information on three stages. You can also present information on Enterprise Security Program, Control Environment, Security Processes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Attacks Response Plan Various Cyber Security Incidents Detected By It Department
Cyber Security Attacks Response Plan Various Cyber Security Incidents Detected By It DepartmentThis slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Attacks Response Plan Various Cyber Security Incidents Detected By It Department. This template helps you present information on five stages. You can also present information on Insider Threat, Phishing Attack, Malware Attack, Password Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Managing Cyber Security In Manufacturing 30 Days Plan Automation In Manufacturing IT
Managing Cyber Security In Manufacturing 30 Days Plan Automation In Manufacturing ITThis slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time and teams who are responsible and details. Present the topic in a bit more detail with this Managing Cyber Security In Manufacturing 30 Days Plan Automation In Manufacturing IT. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing Reporting, Phishing Repeat Offenders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managing Cyber Security In Manufacturing 60 Days Plan Automation In Manufacturing IT
Managing Cyber Security In Manufacturing 60 Days Plan Automation In Manufacturing ITThis slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Deliver an outstanding presentation on the topic using this Managing Cyber Security In Manufacturing 60 Days Plan Automation In Manufacturing IT. Dispense information and present a thorough explanation of Policy Violations, Data Loss Incidents, Infected Computers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Managing Cyber Security In Manufacturing 90 Days Plan Automation In Manufacturing IT
Managing Cyber Security In Manufacturing 90 Days Plan Automation In Manufacturing ITThis slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Present the topic in a bit more detail with this Managing Cyber Security In Manufacturing 90 Days Plan Automation In Manufacturing IT. Use it as a tool for discussion and navigation on Training Completion, Communication Methods, Policy Sign Off. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Role Of Cyber Security In Manufacturing Automation Automation In Manufacturing IT
Role Of Cyber Security In Manufacturing Automation Automation In Manufacturing ITThis slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Present the topic in a bit more detail with this Role Of Cyber Security In Manufacturing Automation Automation In Manufacturing IT. Use it as a tool for discussion and navigation on Unauthorized Access, Operational Disruption, Intellectual Property Theft. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Framework To Manage IT Dashboard To Track IT Security Incidents Prevailing Across Strategy SS
Strategic Framework To Manage IT Dashboard To Track IT Security Incidents Prevailing Across Strategy SSThis slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Introducing Strategic Framework To Manage IT Dashboard To Track IT Security Incidents Prevailing Across Strategy SS to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Dashboard, Track IT Security Incidents, Prevailing Across Firm, using this template. Grab it now to reap its full benefits.
-
 Strategic Framework To Manage IT How Management Enables Effective Corporate Security Strategy SS
Strategic Framework To Manage IT How Management Enables Effective Corporate Security Strategy SSThis slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Deliver an outstanding presentation on the topic using this Strategic Framework To Manage IT How Management Enables Effective Corporate Security Strategy SS. Dispense information and present a thorough explanation of Management, Effective Corporate, Security Governance, Security Resources Effectiveness using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Framework To Manage IT Information Security And Governance Management Strategy SS
Strategic Framework To Manage IT Information Security And Governance Management Strategy SSThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Present the topic in a bit more detail with this Strategic Framework To Manage IT Information Security And Governance Management Strategy SS. Use it as a tool for discussion and navigation on Information Security, Governance, Management, Framework. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Framework To Manage IT Risk Management Framework To Manage Security Threats Strategy SS
Strategic Framework To Manage IT Risk Management Framework To Manage Security Threats Strategy SSThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy. Deliver an outstanding presentation on the topic using this Strategic Framework To Manage IT Risk Management Framework To Manage Security Threats Strategy SS. Dispense information and present a thorough explanation of Implement Enterprise Security Program, Implement Control Environment, Implement Security Processes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Various Cyber Security Incidents Detected By It Department Deploying Computer Security
Various Cyber Security Incidents Detected By It Department Deploying Computer SecurityThis slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc.Introducing Various Cyber Security Incidents Detected By It Department Deploying Computer Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Current Financial, Sabotage Incidents, Technique Legitimate, using this template. Grab it now to reap its full benefits.
-
 Dashboard To Track It Security Incidents Comprehensive Plan To Ensure It And Business Alignment
Dashboard To Track It Security Incidents Comprehensive Plan To Ensure It And Business AlignmentThis slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Increase audience engagement and knowledge by dispensing information using Dashboard To Track It Security Incidents Comprehensive Plan To Ensure It And Business Alignment. This template helps you present information on eight stages. You can also present information on Dashboard, Information, Authentification using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security And Governance Comprehensive Plan To Ensure It And Business Alignment
Information Security And Governance Comprehensive Plan To Ensure It And Business AlignmentThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Deliver an outstanding presentation on the topic using this Information Security And Governance Comprehensive Plan To Ensure It And Business Alignment. Dispense information and present a thorough explanation of Governance, Management, Framework using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Is Blockchain Technology Secure Cryptographic Ledger IT
Is Blockchain Technology Secure Cryptographic Ledger ITThis slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain.Present the topic in a bit more detail with this Is Blockchain Technology Secure Cryptographic Ledger IT. Use it as a tool for discussion and navigation on Generated Math Algorithms, Weaknesses Blockchain, Networks Nevertheless. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
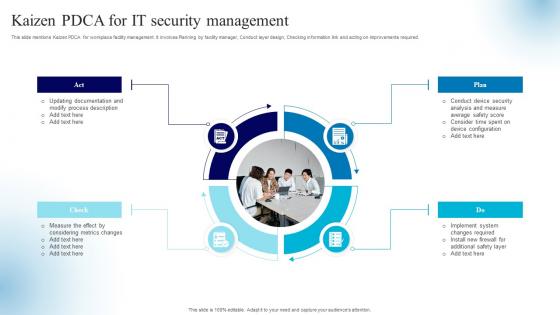 Kaizen PDCA For IT Security Management
Kaizen PDCA For IT Security ManagementThis slide mentions Kaizen PDCA for workplace facility management. It involves Planning by facility manager, Conduct layer design, Checking information link and acting on improvements required. Presenting our set of slides with name Kaizen PDCA For IT Security Management. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Considering Metrics, Changes Required, Device Security.
-
 Types Of It Security Control Framework
Types Of It Security Control FrameworkThis slide presents a framework showing multiple types of IT cyber security control to protect system integrity and information. It includes key components such as COBIT, CIS control, NIST cyber security, HITRUST CSF, NIST SP model and ISO series. Presenting our set of slides with Types Of It Security Control Framework. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Framework, Framework Options.
-
 Strategic IT Cost Optimization Role Of Management In Effective Information Security Governance
Strategic IT Cost Optimization Role Of Management In Effective Information Security GovernanceThis slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Present the topic in a bit more detail with this Strategic IT Cost Optimization Role Of Management In Effective Information Security Governance. Use it as a tool for discussion and navigation on Senior Executives, Steering Committees, Information Security Officer. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 It Infra Security Model To Eliminate Unauthorized User Access
It Infra Security Model To Eliminate Unauthorized User AccessThe following slide exhibits model for IT infrastructure security in order to determine tools that provide in depth defence. It presents information related to perimeter, endpoint, visibility, etc. Introducing It Infra Security Model To Eliminate Unauthorized User Access to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Perimeter, Application, Identify, using this template. Grab it now to reap its full benefits.
-
 Steps For It Infra Security Assessment
Steps For It Infra Security AssessmentThe following slide exhibits IT risk assessment process which aims to eliminate levels of risk at every step. It presents information related to evaluation, exposure, threat determination, etc. Introducing Steps For It Infra Security Assessment to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Evaluation, Vulnerability, Exposure, using this template. Grab it now to reap its full benefits.
-
 IT Strategy Planning Guide Dashboard To Track IT Security Incidents Prevailing Across Firm Strategy SS V
IT Strategy Planning Guide Dashboard To Track IT Security Incidents Prevailing Across Firm Strategy SS VThis slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Increase audience engagement and knowledge by dispensing information using IT Strategy Planning Guide Dashboard To Track IT Security Incidents Prevailing Across Firm Strategy SS V. This template helps you present information on eight stages. You can also present information on Dashboard, Track IT Security, Prevailing Across Firm, Application Whitelisting using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IT Strategy Planning Guide How Management Enables Effective Corporate Security Governance Strategy SS V
IT Strategy Planning Guide How Management Enables Effective Corporate Security Governance Strategy SS VThis slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Deliver an outstanding presentation on the topic using this IT Strategy Planning Guide How Management Enables Effective Corporate Security Governance Strategy SS V. Dispense information and present a thorough explanation of Demonstrate Alignment Process, Management, Corporate Security Governance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Strategy Planning Guide Information Security And Governance Management Framework Strategy SS V
IT Strategy Planning Guide Information Security And Governance Management Framework Strategy SS VThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Present the topic in a bit more detail with this IT Strategy Planning Guide Information Security And Governance Management Framework Strategy SS V. Use it as a tool for discussion and navigation on Information Security, Governance, Management Framework. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Strategy Planning Guide IT Risk Management Framework To Manage Security Threats Strategy SS V
IT Strategy Planning Guide IT Risk Management Framework To Manage Security Threats Strategy SS VThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Deliver an outstanding presentation on the topic using this IT Strategy Planning Guide IT Risk Management Framework To Manage Security Threats Strategy SS V. Dispense information and present a thorough explanation of IT Risk Management, Framework To Manage, Security Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Dashboard To Track It Security Incidents Prevailing Blueprint Develop Information It Roadmap Strategy Ss
Dashboard To Track It Security Incidents Prevailing Blueprint Develop Information It Roadmap Strategy SsThis slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Deliver an outstanding presentation on the topic using this Dashboard To Track It Security Incidents Prevailing Blueprint Develop Information It Roadmap Strategy Ss. Dispense information and present a thorough explanation of Dashboard, Information, Authentification using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Governance Management Blueprint Develop Information It Roadmap Strategy Ss
Information Security And Governance Management Blueprint Develop Information It Roadmap Strategy SsThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Present the topic in a bit more detail with this Information Security And Governance Management Blueprint Develop Information It Roadmap Strategy Ss. Use it as a tool for discussion and navigation on Evaluation And Direction, Identify Security, Infrastructure Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 It Risk Management Framework To Manage Security Blueprint Develop Information It Roadmap Strategy Ss
It Risk Management Framework To Manage Security Blueprint Develop Information It Roadmap Strategy SsThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Present the topic in a bit more detail with this It Risk Management Framework To Manage Security Blueprint Develop Information It Roadmap Strategy Ss. Use it as a tool for discussion and navigation on Management, Framework, Environment. This template is free to edit as deemed fit for your organization. Therefore download it now.





