Powerpoint Templates and Google slides for Secure Deployment
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Types Of Forward Proxy Server Deployment CASB Cloud Security
Types Of Forward Proxy Server Deployment CASB Cloud SecurityThis slide describes the two main categories of forward proxy server implementation. The purpose of this slide is to show how residential and data center proxies work, including their features. The components of a residential proxy include a proxy user, central proxy server, residential IP and internet. Present the topic in a bit more detail with this Types Of Forward Proxy Server Deployment CASB Cloud Security. Use it as a tool for discussion and navigation on Forward Proxy Server Deployment, Residential Proxy, Central Proxy Server. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Progress Tracking Checklist For Mobile Security Deployment
Progress Tracking Checklist For Mobile Security DeploymentThis slide is a checklist to track progress on mobile security deployment which includes remote lock, proactive data wipe, auto configuration of devices, etc. Presenting our well structured Progress Tracking Checklist For Mobile Security Deployment. The topics discussed in this slide are Progress Tracking Checklist, Mobile Security Deployment, Configuration Of Devices. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Concerns And Solution For Application Security Deployment
Concerns And Solution For Application Security DeploymentThis slide outlines the problems and relevant solutions of application security deployment to ensure smooth functioning. Present the topic in a bit more detail with this Concerns And Solution For Application Security Deployment. Use it as a tool for discussion and navigation on Implement Strict Input Validation, Employ Bot Detection Mechanisms, Application Security Deployment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Create Continuous Update And Deployment Mechanisms Internet Of Things IoT Security Cybersecurity SS
Create Continuous Update And Deployment Mechanisms Internet Of Things IoT Security Cybersecurity SSThis slide showcases comparative analysis for internet of things IoT security tools. It provides details about secure cryptographic key provisioning, identity, access and relationship management, IoT device provisioning, etc. Introducing Create Continuous Update And Deployment Mechanisms Internet Of Things IoT Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Secure Deployment, Cryptographic Protocols, Automated Security Update Deployment, Monitoring And Response Mechanisms, using this template. Grab it now to reap its full benefits.
-
 Deploy Security Auditing And Monitoring Mechanisms Internet Of Things IoT Security Cybersecurity SS
Deploy Security Auditing And Monitoring Mechanisms Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of auditing and monitoring for internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about response plan, etc. Increase audience engagement and knowledge by dispensing information using Deploy Security Auditing And Monitoring Mechanisms Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on three stages. You can also present information on Auditing And Reporting, Incident Response Planning, Record Of Security Actions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan RACI Matrix To Deploy Application Security
Application Security Implementation Plan RACI Matrix To Deploy Application SecurityThis slide showcases a RACI matrix for application security, outlining the appropriate roles and steps to be taken during application security implementation. Present the topic in a bit more detail with this Application Security Implementation Plan RACI Matrix To Deploy Application Security. Use it as a tool for discussion and navigation on Secure Development Practices, Risk Assessment, Data Encryption, Application Security . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Implementation Plan Risks And Mitigation Strategies While Deploying Application Security
Application Security Implementation Plan Risks And Mitigation Strategies While Deploying Application SecurityThe purpose of this slide is to discuss the challenges faced while implementing application security such as data breaches, third-party risks, etc. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Risks And Mitigation Strategies While Deploying Application Security. Dispense information and present a thorough explanation of Vulnerabilities In Applications, Data Breaches, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Steps For Deploying Application Security Testing
Application Security Implementation Plan Steps For Deploying Application Security TestingThis slide showcases the steps for deploying effective application security testing which include establishing test case, including security exam, etc. Introducing Application Security Implementation Plan Steps For Deploying Application Security Testing to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Execute Security Exam, Examine Outcomes, Include Security Exam, Stablish Working Test Case, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Steps For Effective Encryption Method Deployment
Application Security Implementation Plan Steps For Effective Encryption Method DeploymentThis slide highlights the steps for deploying effective encryption which include selecting appropriate algorithm, choosing correct key size, etc. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Steps For Effective Encryption Method Deployment. This template helps you present information on six stages. You can also present information on Select Appropriate Algorithm, Select Appropriate Program, Maintain Key Security, Encryption Method Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan Steps To Deploy Efficient Access Control
Application Security Implementation Plan Steps To Deploy Efficient Access ControlThis slide discusses the process phases of implementing access control which include taking inventory of systems, examining staffs, etc. Introducing Application Security Implementation Plan Steps To Deploy Efficient Access Control to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Establish Roles, Resist Sporadic Adjustments, Examine The Staff, Take Inventory Of Systems, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Team Structure For Application Security Deployment
Application Security Implementation Plan Team Structure For Application Security DeploymentThis slide represents the team structure for the application security in the IT infrastructure which includes manager, team lead, application security team, etc. Present the topic in a bit more detail with this Application Security Implementation Plan Team Structure For Application Security Deployment. Use it as a tool for discussion and navigation on Application Security Team, Database Management Team, Security Analyst, Malware Analyst. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Implementation Plan Timeline For Deploying Efficient Application Security
Application Security Implementation Plan Timeline For Deploying Efficient Application SecurityThis slide outlines the different steps performed while deploying application security, including planning phase, requirement gathering, etc. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Timeline For Deploying Efficient Application Security. This template helps you present information on six stages. You can also present information on Education And Training, Patch Management, Incident Response Planning, Establish Security Policies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan Authorization Deployment Steps For Application Security
Application Security Implementation Plan Authorization Deployment Steps For Application SecurityThis slide discusses the process phases for implementing effective authorization which include assessment, planning, defining access control policies, etc. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Authorization Deployment Steps For Application Security. This template helps you present information on seven stages. You can also present information on Technology Selection, Assessment And Planning, Training And Awareness using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Benefits Of Deploying Ai In Network Security
Benefits Of Deploying Ai In Network SecurityThis slide shows the major benefits of using artificial intelligence for security purposes. The major benefits are faster threat detection, improved accuracy, improved scalability and cost-saving Presenting our set of slides with Benefits Of Deploying Ai In Network Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Faster Threat Detection, Improved Accuracy, Scalability And Cost Saving .
-
 Deploying Ai Network Security In Defence Sector
Deploying Ai Network Security In Defence SectorThis slide shows how artificial intelligence is deployed in the defense sector to build strong network security. The major reasons for deploying AI are to analyse network threats, malware detection, insider threat detection and mitigation Introducing our premium set of slides with Deploying Ai Network Security In Defence Sector. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Threat Analysis, Malware Detection, Insider Threat Detection And Mitigation. So download instantly and tailor it with your information.
-
 Application Security Deployment Best Practices
Application Security Deployment Best PracticesThis slide discusses the best approaches for application security deployment which include assess threats, shift security left, control rights, etc. Presenting our set of slides with Application Security Deployment Best Practices This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Monitor App Security Results, Manage Access Levels
-
 Checklist For Effective Application Security Deployment
Checklist For Effective Application Security DeploymentThis slide showcases the actions performed while deploying application security, person responsible, status and comments for the same. Presenting our well structured Checklist For Effective Application Security Deployment The topics discussed in this slide are Person Responsible, StatusThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Key Benefits Of Application Security Deployment
Key Benefits Of Application Security DeploymentThis slide outlines the various advantages of deploying application security such as risk reduction, preserved brand reputation, trust enhancement, etc. Presenting our set of slides with Key Benefits Of Application Security Deployment This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Preserves Brand Reputation, Prevents Sensitive Data Leaks
-
 Web Security Upgradation Impact Of Web Security Deployment On Business
Web Security Upgradation Impact Of Web Security Deployment On BusinessThis slide showcases the after web security impact on industries which include security, reduced cyber threats in web, etc. Introducing Web Security Upgradation Impact Of Web Security Deployment On Business to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Decrease In Cyber Threats, Legal Consultations, Internet Safety Standards, using this template. Grab it now to reap its full benefits.
-
 Web Security Upgradation Raci Matrix To Deploy Web Security
Web Security Upgradation Raci Matrix To Deploy Web SecurityThis slide showcases a RACI matrix for web security, outlining the appropriate roles and steps to be taken during web security implementation. Present the topic in a bit more detail with this Web Security Upgradation Raci Matrix To Deploy Web Security. Use it as a tool for discussion and navigation on Risk Assessment, Authentication, Secure Development Practices, Data Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Web Security Upgradation Risks And Mitigation Strategies While Deploying Web Security
Web Security Upgradation Risks And Mitigation Strategies While Deploying Web SecurityThe purpose of this slide is to discuss the challenges faced while implementing web security such as alert overload, skill gap, etc. Present the topic in a bit more detail with this Web Security Upgradation Risks And Mitigation Strategies While Deploying Web Security. Use it as a tool for discussion and navigation on Risk, Impact, Mitigation Strategies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Web Security Upgradation Timeline For Web Security Deployment In Business
Web Security Upgradation Timeline For Web Security Deployment In BusinessThis slide outlines the timeline for implementing web security in an organization which include assessment, planning, etc. Introducing Web Security Upgradation Timeline For Web Security Deployment In Business to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Assessment And Planning, Infrastructure Security, Secure Development Practices, using this template. Grab it now to reap its full benefits.
-
 Chatbot Security Deployment Best Practices
Chatbot Security Deployment Best PracticesThis slide shows details regarding various best practices that can be adopted by organizations or businesses while deploying chatbots on their websites. These best practices are data segregation, input sanitization, content moderation, etc. Presenting our set of slides with Chatbot Security Deployment Best Practices. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Train Chatbot, Segregate Sensitive, Data From Models.
-
 Timeline For Web Security Deployment In Business
Timeline For Web Security Deployment In BusinessThis slide outlines the different steps performed while deploying web security, including assessment, planning, and so on. Introducing Timeline For Web Security Deployment In Business to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Assessment And Planning, Infrastructure Security, Secure Development Practices, using this template. Grab it now to reap its full benefits.
-
 Main Tools For Deploying Application Security
Main Tools For Deploying Application SecurityThis slide discusses the tools used for implementing application security such as Static Application Security Testing, Dynamic Application Security Testing, etc. Presenting our well structured Main Tools For Deploying Application Security The topics discussed in this slide are Security Scanning Tools, Runtime Protection ToolsThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
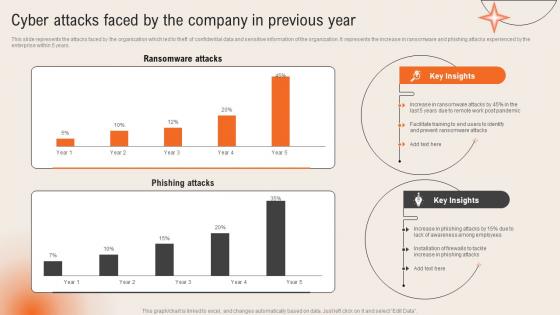 Cyber Attacks Faced By The Company In Previous Year Deploying Computer Security Incident Management
Cyber Attacks Faced By The Company In Previous Year Deploying Computer Security Incident ManagementThis slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years.Present the topic in a bit more detail with this Cyber Attacks Faced By The Company In Previous Year Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Ransomware Attacks, Phishing Attacks, Awareness Among Employees. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Prepare And Deploy Strong It Policies
Information Security Prepare And Deploy Strong It PoliciesThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Present the topic in a bit more detail with this Information Security Prepare And Deploy Strong It Policies. Use it as a tool for discussion and navigation on Prepare And Deploy Strong IT Policies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Prepare And Deploy Strong It Policies
Network Security Prepare And Deploy Strong It PoliciesThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an outstanding presentation on the topic using this Network Security Prepare And Deploy Strong It Policies. Dispense information and present a thorough explanation of Prepare And Deploy Strong It Policies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Prepare And Deploy Strong It Policies
Information Technology Security Prepare And Deploy Strong It PoliciesThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an outstanding presentation on the topic using this Information Technology Security Prepare And Deploy Strong It Policies. Dispense information and present a thorough explanation of Prepare And Deploy Strong IT Policies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ensuring Checklist For Mobile Security Deployment Contd Android Device Security Management
Ensuring Checklist For Mobile Security Deployment Contd Android Device Security ManagementThis slide provides information regarding mobile device security deployment checklist in terms of ensuring secure connections to corporate networks, prevent network based intrusion, centralized policies control and corporate directories. Introducing Ensuring Checklist For Mobile Security Deployment Contd Android Device Security Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Parameters, Ensuring Checklist, Mobile Security Deployment, using this template. Grab it now to reap its full benefits.
-
 Ensuring Checklist For Mobile Security Deployment Management And Monitoring
Ensuring Checklist For Mobile Security Deployment Management And MonitoringThis slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Introducing Ensuring Checklist For Mobile Security Deployment Management And Monitoring to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Ensuring Checklist, Mobile Security Deployment, using this template. Grab it now to reap its full benefits.
-
 Ensuring Checklist For Mobile Security Deployment Enterprise Mobile Security For On Device
Ensuring Checklist For Mobile Security Deployment Enterprise Mobile Security For On DeviceThis slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Deliver an outstanding presentation on the topic using this Ensuring Checklist For Mobile Security Deployment Enterprise Mobile Security For On Device. Dispense information and present a thorough explanation of Enforcing Effective, Automatic Configuration, Effective Handling using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ensuring Checklist For Mobile Security Deployment Unified Endpoint Security
Ensuring Checklist For Mobile Security Deployment Unified Endpoint SecurityThis slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Introducing Ensuring Checklist For Mobile Security Deployment Unified Endpoint Security to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Password Protection, Automatic Configuration, Patches Management, using this template. Grab it now to reap its full benefits.
-
 Managing Mobile Device Solutions For Workforce Ensuring Checklist For Mobile Security Deployment
Managing Mobile Device Solutions For Workforce Ensuring Checklist For Mobile Security DeploymentThis slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Present the topic in a bit more detail with this Managing Mobile Device Solutions For Workforce Ensuring Checklist For Mobile Security Deployment. Use it as a tool for discussion and navigation on Device Security, Protection Against, Malicious Codes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managing Mobile Devices For Optimizing Ensuring Checklist For Mobile Security Deployment
Managing Mobile Devices For Optimizing Ensuring Checklist For Mobile Security DeploymentThis slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Present the topic in a bit more detail with this Managing Mobile Devices For Optimizing Ensuring Checklist For Mobile Security Deployment. Use it as a tool for discussion and navigation on Parameters, Protection, Malicious Codes, Mobile Security Deployment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Response KPI Dashboard Incident Response Strategies Deployment
Cyber Security Incident Response KPI Dashboard Incident Response Strategies DeploymentThis slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Deliver an outstanding presentation on the topic using this Cyber Security Incident Response KPI Dashboard Incident Response Strategies Deployment. Dispense information and present a thorough explanation of Monitoring, Operational, Score using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Assessment And Management Dashboard Incident Response Strategies Deployment
Cyber Security Risk Assessment And Management Dashboard Incident Response Strategies DeploymentThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Dashboard Incident Response Strategies Deployment. Use it as a tool for discussion and navigation on Accounts, Globally, Unresolved. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Systems Monitoring Report Incident Response Strategies Deployment
Cyber Security Systems Monitoring Report Incident Response Strategies DeploymentThis slide represents the report to effectively monitor the networks and systems of the organization. It includes kpis such as total intrusion attempts, mean detect team, mean resolve time etc. Present the topic in a bit more detail with this Cyber Security Systems Monitoring Report Incident Response Strategies Deployment. Use it as a tool for discussion and navigation on Success, Resolve, Intrusion. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategies To Analyze Cyber Security Incidents Response Strategies Deployment
Strategies To Analyze Cyber Security Incidents Response Strategies DeploymentThis slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Introducing Strategies To Analyze Cyber Security Incidents Response Strategies Deployment to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Details, Strategies, Correlation, using this template. Grab it now to reap its full benefits.
-
 Budget Allocation For Cyber Incident Management Training Deploying Computer Security
Budget Allocation For Cyber Incident Management Training Deploying Computer SecurityThis slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc.Present the topic in a bit more detail with this Budget Allocation For Cyber Incident Management Training Deploying Computer Security. Use it as a tool for discussion and navigation on Training Budget, Supply Chain, Operational. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
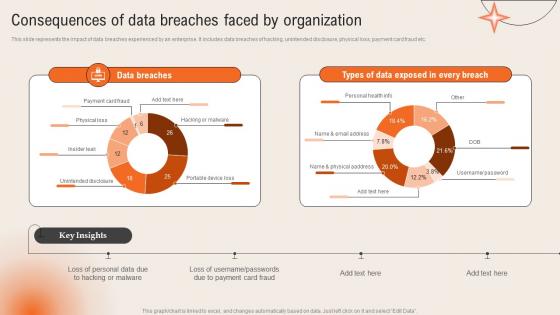 Consequences Of Data Breaches Faced By Organization Deploying Computer Security Incident Management
Consequences Of Data Breaches Faced By Organization Deploying Computer Security Incident ManagementThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc.Present the topic in a bit more detail with this Consequences Of Data Breaches Faced By Organization Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Unintended Disclosure, Portable Device, Hacking Malware. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
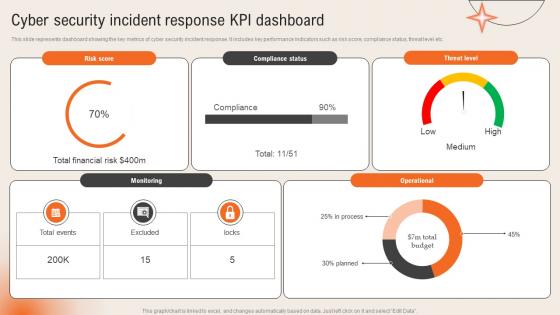 Cyber Security Incident Response Kpi Dashboard Deploying Computer Security Incident Management
Cyber Security Incident Response Kpi Dashboard Deploying Computer Security Incident ManagementThis slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc.Present the topic in a bit more detail with this Cyber Security Incident Response Kpi Dashboard Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Compliance Status, Threat Level, Operational. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Risk Assessment And Management Dashboard Deploying Computer Security Incident
Cyber Security Risk Assessment And Management Dashboard Deploying Computer Security IncidentThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc.Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Dashboard Deploying Computer Security Incident. Use it as a tool for discussion and navigation on Expiring Password, Accessible Directories, Directories Direct Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
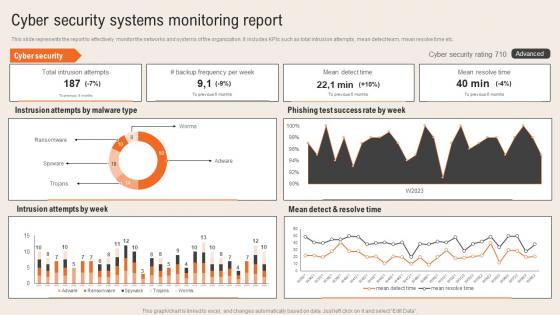 Cyber Security Systems Monitoring Report Deploying Computer Security Incident Management
Cyber Security Systems Monitoring Report Deploying Computer Security Incident ManagementThis slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc.Present the topic in a bit more detail with this Cyber Security Systems Monitoring Report Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Intrusion Attempts, Ransomware, Phishing Test Success. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Supply Chain Risk Management Dashboard Deploying Computer Security Incident Management
Cyber Supply Chain Risk Management Dashboard Deploying Computer Security Incident ManagementThis slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc.Present the topic in a bit more detail with this Cyber Supply Chain Risk Management Dashboard Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Resource Security Hygiene, Subscription Coverage, Resource Health Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
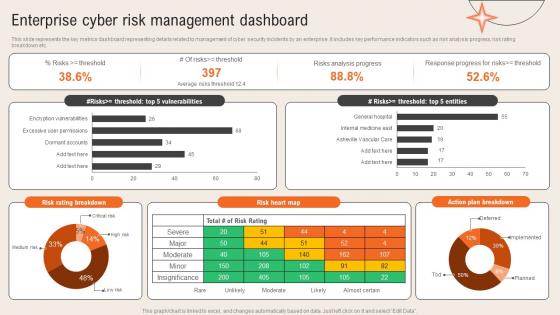 Enterprise Cyber Risk Management Dashboard Deploying Computer Security Incident Management
Enterprise Cyber Risk Management Dashboard Deploying Computer Security Incident ManagementThis slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc.Present the topic in a bit more detail with this Enterprise Cyber Risk Management Dashboard Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Risks Analysis Progress, Response Progress, Action Plan Breakdown. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Kpi for security risks total revenue policy deployment and adoption ppt slide
Kpi for security risks total revenue policy deployment and adoption ppt slidePresenting kpi for security risks total revenue policy deployment and adoption ppt slide. This presentation slide shows three Key Performance Indicators or KPIs in a Dashboard style design. The first KPI that can be shown is Number of Information Security Related Risks. The second KPI is Information Security Costs as a Proportion of Total Revenue or it Budget and the third is Information Security Policy Deployment and Adoption. These KPI Powerpoint graphics are all data driven,and the shape automatically adjusts according to your data. Just right click on the KPI graphic,enter the right value and the shape will adjust automatically. Make a visual impact with our KPI slides.
-
 Security information and event management traditional siem deployment
Security information and event management traditional siem deploymentThis slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Present the topic in a bit more detail with this Security Information And Event Management Traditional SIEM Deployment. Use it as a tool for discussion and navigation on Visualization, Collection, Aggregation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Web application firewall waf it security use cases of web application firewall deployment
Web application firewall waf it security use cases of web application firewall deploymentThis slide represents the security use cases of web application firewall and how it would stop cyberattacks such as DDoS attacks, malicious bot abuse, and customer data breaches. Introducing Web Application Firewall Waf It Security Use Cases Of Web Application Firewall Deployment to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Application, Performance, Deployment, using this template. Grab it now to reap its full benefits.
-
 Real time analysis of security alerts traditional siem deployment model
Real time analysis of security alerts traditional siem deployment modelThis slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver an outstanding presentation on the topic using this Real Time Analysis Of Security Alerts Traditional Siem Deployment Model. Dispense information and present a thorough explanation of Vulnerability, Management, Processes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Improve it security with vulnerability management traditional siem deployment model
Improve it security with vulnerability management traditional siem deployment modelThis slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver an outstanding presentation on the topic using this Improve It Security With Vulnerability Management Traditional Siem Deployment Model. Dispense information and present a thorough explanation of Vulnerability, Management, Processes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Siem For Security Analysis Traditional Siem Deployment Model
Siem For Security Analysis Traditional Siem Deployment ModelThis slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Present the topic in a bit more detail with this Siem For Security Analysis Traditional Siem Deployment Model. Use it as a tool for discussion and navigation on Vulnerability, Management, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective Mobile Device Management Ensuring Checklist For Mobile Security Deployment
Effective Mobile Device Management Ensuring Checklist For Mobile Security DeploymentThis slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Present the topic in a bit more detail with this Effective Mobile Device Management Ensuring Checklist For Mobile Security Deployment. Use it as a tool for discussion and navigation on Ensuring Checklist For Mobile Security Deployment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Steps Enable Data Security Crm Software Deployment Guide
Implementation Steps Enable Data Security Crm Software Deployment GuideThis slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Present the topic in a bit more detail with this Implementation Steps Enable Data Security Crm Software Deployment Guide. Use it as a tool for discussion and navigation on Implementation, Authentication, Restrictions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Security Considerations For 5g For Threat Handling Deployment Of 5g Wireless System
Key Security Considerations For 5g For Threat Handling Deployment Of 5g Wireless SystemThis slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Present the topic in a bit more detail with this Key Security Considerations For 5g For Threat Handling Deployment Of 5g Wireless System. Use it as a tool for discussion and navigation on Considerations, Service, Unauthorized. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Steps To Deploy People Centric Security
Steps To Deploy People Centric SecurityThe following slide showcases steps to enforce human centric security system to empower employees in handling useful information. It includes elements such as establishing environment for people centric security PCS, promoting culture of cyber security, etc. Introducing our premium set of slides with name Steps To Deploy People Centric Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Promote Culture Of Cybersecurity, Make Cyber Security An Obligation, Establish An Environment For PCS. So download instantly and tailor it with your information.
-
 Implementation Add Roles And Enable Security Customer Relationship Management Deployment Strategy
Implementation Add Roles And Enable Security Customer Relationship Management Deployment StrategyThis slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an outstanding presentation on the topic using this Implementation Add Roles And Enable Security Customer Relationship Management Deployment Strategy Dispense information and present a thorough explanation of Restrictions Enabling, Double Authentication, Prevent Unauthorized using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Securing Our Data With CRM Customer Relationship Management Deployment Strategy
Securing Our Data With CRM Customer Relationship Management Deployment StrategyThis slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security.Increase audience engagement and knowledge by dispensing information using Securing Our Data With CRM Customer Relationship Management Deployment Strategy This template helps you present information on three stages. You can also present information on Factor Authentication, Storage And Failover, Communication Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Security Considerations For 5G For Threat Handling Proactive Approach For 5G Deployment
Key Security Considerations For 5G For Threat Handling Proactive Approach For 5G DeploymentThis slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Present the topic in a bit more detail with this Key Security Considerations For 5G For Threat Handling Proactive Approach For 5G Deployment. Use it as a tool for discussion and navigation on Virtualization Threats, Information Interception, Unauthorized Activities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Steps Involved In Mobile Device Deployment Enterprise Mobile Security For On Device
Key Steps Involved In Mobile Device Deployment Enterprise Mobile Security For On DeviceThis slide provides information regarding key steps involved in deploying mobile device management system.Increase audience engagement and knowledge by dispensing information using Key Steps Involved In Mobile Device Deployment Enterprise Mobile Security For On Device. This template helps you present information on four stages. You can also present information on Associated Device, Profile Configuration, Device Purchase using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





