Powerpoint Templates and Google slides for Risks Cyber Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Icons Slide For Introducing A Risk Based Approach To Cyber Security
Icons Slide For Introducing A Risk Based Approach To Cyber SecurityPresenting our premium Icons Slide For Introducing A Risk Based Approach To Cyber Security set of slides with flexible icons. The icons are designed by our group of professionals. Add these Icons Slide For Introducing A Risk Based Approach To Cyber Security to your presentation to make it visually appealing. Also, edit them according to your requirement. Download it and captive your audience.
-
 Introducing New Incidents Logging Process Introducing A Risk Based Approach To Cyber Security
Introducing New Incidents Logging Process Introducing A Risk Based Approach To Cyber SecurityThis slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details.Present the topic in a bit more detail with this Introducing New Incidents Logging Process Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Category Selection, Assigned To Responsible, Provide An Interaction This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of New It Policy Framework Introducing A Risk Based Approach To Cyber Security
Overview Of New It Policy Framework Introducing A Risk Based Approach To Cyber SecurityThis slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies.Deliver an outstanding presentation on the topic using this Overview Of New It Policy Framework Introducing A Risk Based Approach To Cyber Security Dispense information and present a thorough explanation of Data Management Policy, Data Protection Policy, Externally Hosted Personal using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Governance Structure Introducing A Risk Based Approach To Cyber Security
Risk Governance Structure Introducing A Risk Based Approach To Cyber SecurityMentioned slide illustrates risk governance framework of the company. It include information about different governing committees along with their deliverables.Deliver an outstanding presentation on the topic using this Risk Governance Structure Introducing A Risk Based Approach To Cyber Security Dispense information and present a thorough explanation of Legal And Regulatory Risks, Annual Risk Assessment, Investment Risks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Setting Scenario For Cybersecurity Control Introducing A Risk Based Approach To Cyber Security
Setting Scenario For Cybersecurity Control Introducing A Risk Based Approach To Cyber SecurityFollowing slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description.Present the topic in a bit more detail with this Setting Scenario For Cybersecurity Control Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Technical Controls, Management Controls, Operational Controls This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents For Introducing A Risk Based Approach To Cyber Security
Table Of Contents For Introducing A Risk Based Approach To Cyber SecurityPresent the topic in a bit more detail with this Table Of Contents For Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Global Market Insights, Companies Digitization Levels, About Security Program This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat Drivers And Emerging Introducing A Risk Based Approach To Cyber Security
Threat Drivers And Emerging Introducing A Risk Based Approach To Cyber SecurityMentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security.Increase audience engagement and knowledge by dispensing information using Threat Drivers And Emerging Introducing A Risk Based Approach To Cyber Security This template helps you present information on one stage. You can also present information on Internet Of Things, Artificial Intelligence, Human Machine Interface using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Threat Vulnerability Asset Matrix Introducing A Risk Based Approach To Cyber Security
Threat Vulnerability Asset Matrix Introducing A Risk Based Approach To Cyber SecurityMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least.Present the topic in a bit more detail with this Threat Vulnerability Asset Matrix Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on System Redundancy, Incident Response Plan, Security Policy This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing cyber threats various industries cyber security risk management
Addressing cyber threats various industries cyber security risk managementThis slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. Introducing Addressing Cyber Threats Various Industries Cyber Security Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Industry, Healthcare, Manufacturing, Government, Energy, using this template. Grab it now to reap its full benefits.
-
 Addressing internal and external sources data cyber security risk management
Addressing internal and external sources data cyber security risk managementThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Deliver an outstanding presentation on the topic using this Addressing Internal And External Sources Data Cyber Security Risk Management. Dispense information and present a thorough explanation of Internal Sources, External Sources, Targeted Intelligence, Malware Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing several financial scenarios and signs cyber security risk management
Addressing several financial scenarios and signs cyber security risk managementThis slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Introducing Addressing Several Financial Scenarios And Signs Cyber Security Risk Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Liquidity, Profitability, Financial Performance, Employees, using this template. Grab it now to reap its full benefits.
-
 Addressing ways to handling financial threats cyber security risk management
Addressing ways to handling financial threats cyber security risk managementThis slide provides details regarding handling financial threats by safeguarding financial stability and protecting the firm from costly effects that financial threats can have. Introducing Addressing Ways To Handling Financial Threats Cyber Security Risk Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Abundant Cash Requirement, Key Financial Statements, Preparing Aged Debtors Trial Balance, using this template. Grab it now to reap its full benefits.
-
 Agenda of cyber security risk management ppt slides graphics
Agenda of cyber security risk management ppt slides graphicsThe purpose is to ensure management of various threats faced by firm and secure valuable assets associated to firm in terms of digital assets, people, financial assets, physical security, etc. Increase audience engagement and knowledge by dispensing information using Agenda Of Cyber Security Risk Management Ppt Slides Graphics. This template helps you present information on four stages. You can also present information on Management, Various Threats, Assets Associated, Digital Assets, People, Financial Assets using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Budget for effective threat management workplace cyber security risk management
Budget for effective threat management workplace cyber security risk managementFirm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Present the topic in a bit more detail with this Budget For Effective Threat Management Workplace Cyber Security Risk Management. Use it as a tool for discussion and navigation on Incident Management, Risk Management, Client Onboarding Process, Document Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management addressing asset security categorization
Cyber security risk management addressing asset security categorizationThis slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Introducing Cyber Security Risk Management Addressing Asset Security Categorization to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Position, Ownership, Location, Security Categorization, Integrity, Confidentiality, Availability, Value , using this template. Grab it now to reap its full benefits.
-
 Cyber security risk management addressing critical business functions recovery priorities
Cyber security risk management addressing critical business functions recovery prioritiesThis slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Addressing Critical Business Functions Recovery Priorities. This template helps you present information on two stages. You can also present information on Priorities, Department, Maximum Allowable Downtime, Contracts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security risk management addressing indicators associated to insider threats
Cyber security risk management addressing indicators associated to insider threatsThis slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Introducing Cyber Security Risk Management Addressing Indicators Associated To Insider Threats to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Demeanor, goals, Traits, Data Exfiltration, Financial Stress, using this template. Grab it now to reap its full benefits.
-
 Cyber security risk management addressing natural calamities posing threat organization
Cyber security risk management addressing natural calamities posing threat organizationThis slide provides details regarding natural calamities posing as threat to organization and threat management checklist during nature crisis. Deliver an outstanding presentation on the topic using this Cyber Security Risk Management Addressing Natural Calamities Posing Threat Organization. Dispense information and present a thorough explanation of Various Nature Threats, Hurricanes, Earthquake, Temporary Water Sources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber security risk management addressing threat management team training schedule
Cyber security risk management addressing threat management team training scheduleThe threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Present the topic in a bit more detail with this Cyber Security Risk Management Addressing Threat Management Team Training Schedule. Use it as a tool for discussion and navigation on Hypotheticals, Workshops, Field Exercises, Audience,Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management comparative assessment various threat agents
Cyber security risk management comparative assessment various threat agentsThis slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an outstanding presentation on the topic using this Cyber Security Risk Management Comparative Assessment Various Threat Agents. Dispense information and present a thorough explanation of Insider Threat, Social Engineering, Threat Agents, Cyber Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber security risk management contingency plan for cyber threat handling
Cyber security risk management contingency plan for cyber threat handlingThis slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Introducing Cyber Security Risk Management Contingency Plan For Cyber Threat Handling to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Contingency Solutions, Contingency Considerations, System Backups, Vendors Coordination, using this template. Grab it now to reap its full benefits.
-
 Cyber security risk management determine sequence phases for threat attack
Cyber security risk management determine sequence phases for threat attackThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Determine Sequence Phases For Threat Attack. This template helps you present information on four stages. You can also present information on Reconnaissance, Weaponization, Exploitation, Delivery using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security risk management determine several threat actors profile
Cyber security risk management determine several threat actors profileThis slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an outstanding presentation on the topic using this Cyber Security Risk Management Determine Several Threat Actors Profile. Dispense information and present a thorough explanation of Cyber Criminal, Targeted Asset, Objective using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber security risk management determine staff training schedule for skills
Cyber security risk management determine staff training schedule for skillsThe employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Determine Staff Training Schedule For Skills. This template helps you present information on three stages. You can also present information on Advanced Software Training, Advanced Skills Training, Training Module, Self Assessment Tools using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security risk management determine threat management team
Cyber security risk management determine threat management teamThe threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Introducing Cyber Security Risk Management Determine Threat Management Team to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Threat Management Head, Security Manager, Crisis Management Advisor, Medical Advisor, using this template. Grab it now to reap its full benefits.
-
 Cyber security risk management determine threat scenario analysis
Cyber security risk management determine threat scenario analysisThis slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Determine Threat Scenario Analysis. This template helps you present information on two stages. You can also present information on Threat Scenario, Threat Campaign, Exploitation, Command And Control, Actions And Objectives using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security risk management different kinds of insider digital threats
Cyber security risk management different kinds of insider digital threatsThis slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. Introducing Cyber Security Risk Management Different Kinds Of Insider Digital Threats to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Malicious Insider, Negligent Or Careless Insider, Third Party Insider, using this template. Grab it now to reap its full benefits.
-
 Cyber security risk management ensuring vital records maintenance
Cyber security risk management ensuring vital records maintenanceThis slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. Deliver an outstanding presentation on the topic using this Cyber Security Risk Management Ensuring Vital Records Maintenance. Dispense information and present a thorough explanation of Settlement Agreements, Litigation Files, Department File Cabinets, Department File Room using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber security risk management evaluating financial practices in firm
Cyber security risk management evaluating financial practices in firmThe firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Present the topic in a bit more detail with this Cyber Security Risk Management Evaluating Financial Practices In Firm. Use it as a tool for discussion and navigation on Needs Work, Not Applicable, Parameters, Cash Accounts Monthly. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management how financial risk can be controlled
Cyber security risk management how financial risk can be controlledThis slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Introducing Cyber Security Risk Management How Financial Risk Can Be Controlled to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Handling Liquidity Risk, Handling Foreign Exchange Risk, Handling Credit Exchange Risk, using this template. Grab it now to reap its full benefits.
-
 Cyber security risk management impact analysis of successful threat management
Cyber security risk management impact analysis of successful threat managementThis slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Impact Analysis Of Successful Threat Management. This template helps you present information on four stages. You can also present information on Focus Area, Past State, Present State, Benefit, Customer Satisfaction Rate using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security risk management incident reporting by different departments
Cyber security risk management incident reporting by different departmentsThis slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Introducing Cyber Security Risk Management Incident Reporting By Different Departments to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Number Incidents, Person Involved Incident, Average Cost Per Incident, using this template. Grab it now to reap its full benefits.
-
 Cyber security risk management key activities checklist associated to insider threat
Cyber security risk management key activities checklist associated to insider threatThis slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Deliver an outstanding presentation on the topic using this Cyber Security Risk Management Key Activities Checklist Associated To Insider Threat. Dispense information and present a thorough explanation of Plan And Collet, Review And Analyze, Develop Strategic Framework, Track Present Inventory using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber security risk management roles and responsibilities ensure work environment
Cyber security risk management roles and responsibilities ensure work environmentThis slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Roles And Responsibilities Ensure Work Enviro. This template helps you present information on four stages. You can also present information on Employee Responsibilities, Unit Supervisor, Manager Responsibilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security risk management selecting secured threat management software
Cyber security risk management selecting secured threat management softwareThis slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Present the topic in a bit more detail with this Cyber Security Risk Management Selecting Secured Threat Management Software. Use it as a tool for discussion and navigation on Centralized Platform, Security Incident Forms, Access Rights, API Integration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management statistics associated to workplace threats
Cyber security risk management statistics associated to workplace threatsThis slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Introducing Cyber Security Risk Management Statistics Associated To Workplace Threats to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Attacks Costs, Organizations Face, Data Records, Business, Financial, using this template. Grab it now to reap its full benefits.
-
 Cyber security risk management threat management action plan
Cyber security risk management threat management action planThe threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Introducing Cyber Security Risk Management Threat Management Action Plan to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Threat Identification, Threat Treatment, Plan, Threat Owner, using this template. Grab it now to reap its full benefits.
-
 Cyber security risk management various types of workplace violence and threats
Cyber security risk management various types of workplace violence and threatsThis slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. Introducing Cyber Security Risk Management Various Types Of Workplace Violence And Threats to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Threats Or Threatening Behavior, Physical Assault, Property Damage, using this template. Grab it now to reap its full benefits.
-
 Cyber security risk management workplace employee assistance program
Cyber security risk management workplace employee assistance programThe employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Workplace Employee Assistance Program. This template helps you present information on three stages. You can also present information on Clinical Services, Work And Life Services, Employer Services, Online Resources, Offline Resources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine sequence phases for threat attack contd cyber security risk management
Determine sequence phases for threat attack contd cyber security risk managementThis slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Introducing Determine Sequence Phases For Threat Attack Contd Cyber Security Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Installation, Command And Control, Actions And Objectives, Covering Tracks, using this template. Grab it now to reap its full benefits.
-
 Ensuring collaboration among various functional areas cyber security risk management
Ensuring collaboration among various functional areas cyber security risk managementThis slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Introducing Ensuring Collaboration Among Various Functional Areas Cyber Security Risk Management to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Legal, Compliance, Public Relations, Human Resources, Procurement, Board And Risk Committee, using this template. Grab it now to reap its full benefits.
-
 Icons slide for cyber security risk management
Icons slide for cyber security risk managementPresenting our premium Icons Slide For Cyber Security Risk Management set of slides with flexible icons. The icons are designed by our group of professionals. Add these Icons Slide For Cyber Security Risk Management to your presentation to make it visually appealing. Also, edit them according to your requirement. Download it and captive your audience.
-
 Impact analysis for effective threat management in cyber security risk management
Impact analysis for effective threat management in cyber security risk managementThis slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Introducing Impact Analysis For Effective Threat Management In Cyber Security Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Focus Areas, Actual Access Violations, Access Rights Authorized, using this template. Grab it now to reap its full benefits.
-
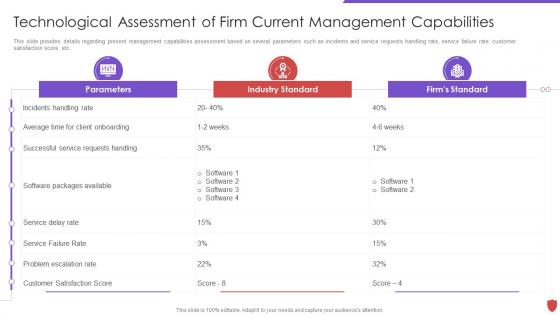 Technological assessment of firm current capabilities cyber security risk management
Technological assessment of firm current capabilities cyber security risk managementThis slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver an outstanding presentation on the topic using this Technological Assessment Of Firm Current Capabilities Cyber Security Risk Management. Dispense information and present a thorough explanation of Parameters, Industry Standard, Firms Standard, Service Delay Rate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat management action plan cyber security risk management
Threat management action plan cyber security risk managementThe threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Present the topic in a bit more detail with this Threat Management Action Plan Cyber Security Risk Management. Use it as a tool for discussion and navigation on Potential Risk, Risk Level, Action, Responsible Person, Risk Treated. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Workplace incident summary report cyber security risk management
Workplace incident summary report cyber security risk managementThis slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. Deliver an outstanding presentation on the topic using this Workplace Incident Summary Report Cyber Security Risk Management. Dispense information and present a thorough explanation of Type Incident, Employees Involved, Time Incident, Assets Money Lost, Damaged using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Assessment Matrix Of Cyber Risks
Information Technology Security Assessment Matrix Of Cyber RisksThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an outstanding presentation on the topic using this Information Technology Security Assessment Matrix Of Cyber Risks. Dispense information and present a thorough explanation of Assessment Matrix Of Cyber Risks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Strategies To Manage Cyber Risks
Information Technology Security Strategies To Manage Cyber RisksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Increase audience engagement and knowledge by dispensing information using Information Technology Security Strategies To Manage Cyber Risks. This template helps you present information on four stages. You can also present information on Strategic, Structures, Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Five Steps For Cyber Security Risk Analysis
Five Steps For Cyber Security Risk AnalysisThis slide covers the steps for analysis of risk occurring in cyber security to reduce errors and system hacks so that the information of clients remain safe. It includes finding assets, identifying consequences, threats and assessing risk. Presenting our set of slides with Five Steps For Cyber Security Risk Analysis. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Find Valuable Assets, Assess Risk, Identify Potential Consequences.
-
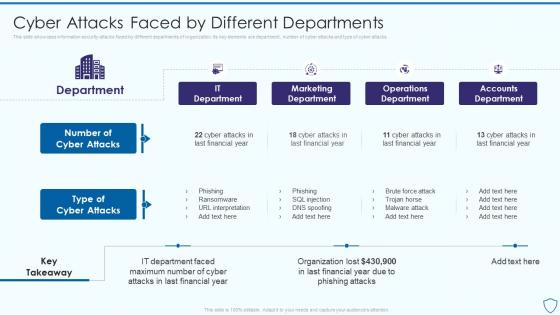 Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By Different
Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By DifferentThis slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks Deliver an outstanding presentation on the topic using this Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By Different. Dispense information and present a thorough explanation of Marketing Department, Operations Department, Accounts Department using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Project Risk Management Life Cycle
Cyber Security Project Risk Management Life CycleThis slide represents the lifecycle of project risk management. The process include Identification, Analyse, Prioritize and monitoring. Presenting our set of slides with Cyber Security Project Risk Management Life Cycle. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Monitoring, Identification, Prioritize.
-
 Cyber Security Risk Management Approach With Risk Priority And Control
Cyber Security Risk Management Approach With Risk Priority And ControlThe following slide highlights the cyber security risk management approach with risk priority and control it illustrates risk priority, mitigation, controls, automation, governance and risk culture, which helps organisation to train workforce for cyber awareness and define company policy for cyber security. Presenting our set of slides with name Cyber Security Risk Management Approach With Risk Priority And Control. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Governance, Risk Priority, Mitigation.
-
 Five Phase Of Risk Based Cyber Security
Five Phase Of Risk Based Cyber SecurityThe following slide highlights the five phase of risk based cyber security which includes business impact analysis, risk assessment, controls, report and monitor, it provides activity, value and outcome for each phase which helps company to develop a consistent incident response process. Presenting our set of slides with name Five Phase Of Risk Based Cyber Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Business Impact Analysis, Risk Assessment, Monitor.
-
 Vendor Selection Steps For Cyber Security Risk
Vendor Selection Steps For Cyber Security RiskThe following slide highlights the Vendor selection steps for cyber security risk depicting assessment methodology, tailor assessment, risk questions, risk threshold and cyber security assessment, it helps company to select cyber security framework and customize it to their requirements. Presenting our set of slides with name Vendor Selection Steps For Cyber Security Risk. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Assessment Methodology, Tailor Assessment, Risk Threshold, Cyber Security Assessment.
-
 Business Cyber Security Risk Assessment Process
Business Cyber Security Risk Assessment ProcessThe slide shows cyber threat detection and protection measures in order to eliminate the potential risks to the business. The steps include identifying, detecting, responding, protecting, and recovering. Presenting our set of slides with Business Cyber Security Risk Assessment Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Detect, Respond, Protect.
-
 Cyber Risk Security For Small Business
Cyber Risk Security For Small BusinessThis slide highlights the risk management strategy to detect and control cyber security threats for a small enterprise. The key strategies include a cyber security plan, password protection, e mail security, and protective software. Presenting our set of slides with Cyber Risk Security For Small Business. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Create Cyber Security Plan, Ensure Password Protection, Protective Software.
-
 Cyber Security Risk Review And Control Matrix
Cyber Security Risk Review And Control MatrixThe purpose of this slide is to define the level of hazards and their severity in cybersecurity management along with priority levels 1-5 to manage risks. This is categorized as certain, likely, possible, unlikely, and rare. Introducing our Cyber Security Risk Review And Control Matrix set of slides. The topics discussed in these slides are Risk Matrix, Minor, Priority Levels. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Risk Communication Process Framework
Cyber Security Risk Communication Process FrameworkThis slide showcases a model of risk communication process for cyber security. It includes identify issues, set goals, and objectives, community and constraints, stakeholder assessment, communication and engagement tools, implement strategy and evaluate and follow up. Introducing our premium set of slides with Cyber Security Risk Communication Process Framework. Ellicudate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify Issue, Implement Strategy, Identify Messages. So download instantly and tailor it with your information.
-
 IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation Plan
IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation PlanThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Increase audience engagement and knowledge by dispensing information using IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation Plan. This template helps you present information on one stages. You can also present information on Threat, Risk, Risk Priority, Risk Reduction Timeline using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enterprise Risk Management Prioritized Cyber Security Threats With Risk Mitigation Plan
Enterprise Risk Management Prioritized Cyber Security Threats With Risk Mitigation PlanThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Enterprise Risk Management Prioritized Cyber Security Threats With Risk Mitigation Plan. Use it as a tool for discussion and navigation on Threat, Risk, Risk Priority, Risk Reduction Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.





