Powerpoint Templates and Google slides for Risks Cyber Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber security risk management current potential implications faced by firm threats
Cyber security risk management current potential implications faced by firm threatsThis slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Present the topic in a bit more detail with this Cyber Security Risk Management Current Potential Implications Faced By Firm Threats. Use it as a tool for discussion and navigation on Issues Related, Employees, Data Breaches, Records Exposed, Reported Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management cyber threats management dashboard
Cyber security risk management cyber threats management dashboardThis slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver an outstanding presentation on the topic using this Cyber Security Risk Management Cyber Threats Management Dashboard. Dispense information and present a thorough explanation of Risk Rating Breakdown, Risk Heat Map, Action Plan Breakdown, Risks, Threshold Top 5 Entities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber security risk management financial performance tracking dashboard
Cyber security risk management financial performance tracking dashboardThis slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver an outstanding presentation on the topic using this Cyber Security Risk Management Financial Performance Tracking Dashboard. Dispense information and present a thorough explanation of Receivables Analysis, Revenue And Expense Trends, Central County Deal using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
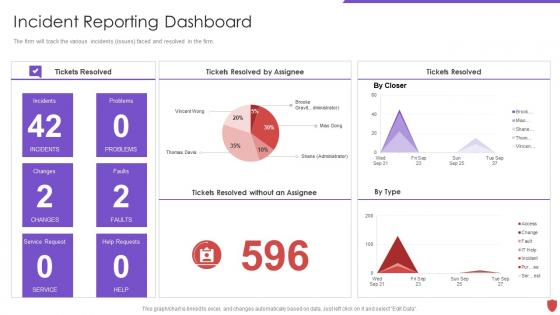 Cyber security risk management incident reporting dashboard
Cyber security risk management incident reporting dashboardThe firm will track the various incidents issues faced and resolved in the firm. Present the topic in a bit more detail with this Cyber Security Risk Management Incident Reporting Dashboard. Use it as a tool for discussion and navigation on Tickets Resolved, Tickets Resolved By Assignee, Tickets Resolved, Tickets Resolved Assignee. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Risk Management Dashboard With Geographical Distribution
Cyber Security Risk Management Dashboard With Geographical DistributionThe following slide highlights the cyber security risk management dashboard with dashboard with geographical distribution depicting incident volume by severity, open incidents, root cause details, divisional details and geographical distribution of risks. Introducing our Cyber Security Risk Management Dashboard With Geographical Distribution set of slides. The topics discussed in these slides are Geographical Distribution, Information Technology, Research And Development. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security KPI Dashboard With Risk Analysis
Cyber Security KPI Dashboard With Risk AnalysisThis slide covers the multiple types of risks under the cyber security that could hinder the process and break the security. It also includes the critical risk events with the weighted index percentage for three months and the value of risks involved or occurred during these months. Introducing our Cyber Security KPI Dashboard With Risk Analysis set of slides. The topics discussed in these slides are Cyber Security, Dashboard, Risk Analysis. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Attacks Faced By Organization In Previous Information Security Risk Management
Cyber Attacks Faced By Organization In Previous Information Security Risk ManagementThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different types of cyber attacks and formulate strategies to tackle them. Deliver an outstanding presentation on the topic using this Cyber Attacks Faced By Organization In Previous Information Security Risk Management. Dispense information and present a thorough explanation of Cyber Attacks Faced, Organization, Previous Financial Year using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Dashboard Snapshot With KPI Metrics
Cyber Security Risk Dashboard Snapshot With KPI MetricsThis slide depicts global cyber security and risk trends providing information about every aspect of threat. It includes overall progression, critical risk identified, initiatives, incident and vulnerabilities management, compliance and patches. Introducing our Cyber Security Risk Dashboard Snapshot With KPI Metrics set of slides. The topics discussed in these slides are Incident Management, Global, Cybersecurity, Vulnerabilities Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Risk Landscape Dashboard For Cyber Security Program Management
Risk Landscape Dashboard For Cyber Security Program ManagementThis slide shows risk landscape dashboard for cyber security program management which contains threat level by month, current threat posture, threats by source, threats by owner, risks by threat and threat register. This can help businesses in effective management of risks and counter measures. Introducing our Risk Landscape Dashboard For Cyber Security Program Management set of slides. The topics discussed in these slides are Risk Landscape, Cyber Security, Program Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
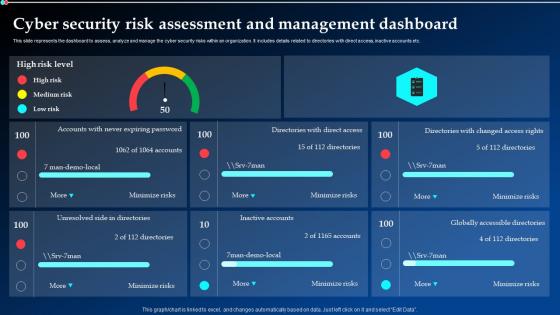 Cyber Security Risk Assessment And Management Dashboard Ppt Portrait
Cyber Security Risk Assessment And Management Dashboard Ppt PortraitThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Dashboard Ppt Portrait. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Cyber Risk Management Dashboard Implementing Cyber Security Ppt Demonstration
Enterprise Cyber Risk Management Dashboard Implementing Cyber Security Ppt DemonstrationThis slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Deliver an outstanding presentation on the topic using this Enterprise Cyber Risk Management Dashboard Implementing Cyber Security Ppt Demonstration. Dispense information and present a thorough explanation of Enterprise Cyber, Risk Management, Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incidents Risk Tracking Dashboard For Response
Cyber Security Incidents Risk Tracking Dashboard For ResponseThis slide highlights dashboard to identify and track security threats occurred in the company. The purpose of this template is to provide information to the management about severities of the incidents along with risk rating in form of heat map.Introducing our Cyber Security Incidents Risk Tracking Dashboard For Response set of slides. The topics discussed in these slides are Action Plan Breakdown, Risk Rating, Analysis Progress. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Kpi Dashboard To Manage Cyber Security Risk
Kpi Dashboard To Manage Cyber Security RiskThis slide shows dashboard which can be used by organizations to track cyber risk. It includes metrics such as overall progress, risk identified, number of critical incidents, initiatives, incident and threat management etc. Presenting our well structured Kpi Dashboard To Manage Cyber Security Risk. The topics discussed in this slide are Dashboard, Organizations, Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Risk Assessment And Management Dashboard Incident Response Strategies Deployment
Cyber Security Risk Assessment And Management Dashboard Incident Response Strategies DeploymentThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Dashboard Incident Response Strategies Deployment. Use it as a tool for discussion and navigation on Accounts, Globally, Unresolved. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Risk Assessment And Management Dashboard Development And Implementation Of Security
Cyber Security Risk Assessment And Management Dashboard Development And Implementation Of SecurityThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Dashboard Development And Implementation Of Security. Dispense information and present a thorough explanation of Medium Risk, Unresolved Side, Inactive Accounts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
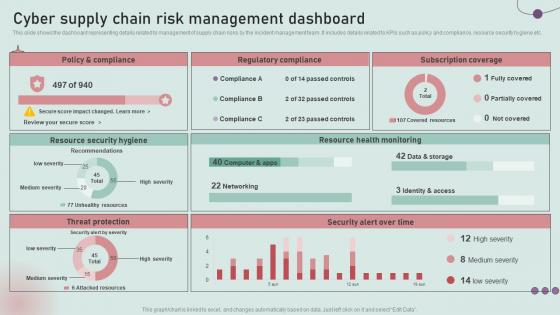 Cyber Supply Chain Risk Management Dashboard Development And Implementation Of Security Incident
Cyber Supply Chain Risk Management Dashboard Development And Implementation Of Security IncidentThis slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Deliver an outstanding presentation on the topic using this Cyber Supply Chain Risk Management Dashboard Development And Implementation Of Security Incident. Dispense information and present a thorough explanation of Regulatory Compliance, Subscription Coverage, Resource Health using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
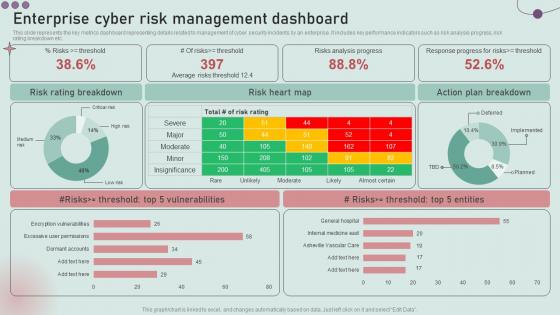 Enterprise Cyber Risk Management Dashboard Development And Implementation Of Security Incident
Enterprise Cyber Risk Management Dashboard Development And Implementation Of Security IncidentThis slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Present the topic in a bit more detail with this Enterprise Cyber Risk Management Dashboard Development And Implementation Of Security Incident. Use it as a tool for discussion and navigation on Risk Rating Breakdown, Risk Heart Map, Action Plan Breakdown. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management Dashboard
Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management DashboardThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management Dashboard. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Cyber Supply Chain Risk Management Dashboard
Cyber Security Attacks Response Plan Cyber Supply Chain Risk Management DashboardThis slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Cyber Supply Chain Risk Management Dashboard. Use it as a tool for discussion and navigation on Cyber Supply Chain, Risk Management, Dashboard, Regulatory Compliance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Enterprise Cyber Risk Management Dashboard
Cyber Security Attacks Response Plan Enterprise Cyber Risk Management DashboardThis slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Enterprise Cyber Risk Management Dashboard. Dispense information and present a thorough explanation of Enterprise Cyber, Risk Management, Dashboard, Action Plan Breakdown using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Assessment And Management Dashboard Deploying Computer Security Incident
Cyber Security Risk Assessment And Management Dashboard Deploying Computer Security IncidentThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc.Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Dashboard Deploying Computer Security Incident. Use it as a tool for discussion and navigation on Expiring Password, Accessible Directories, Directories Direct Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Supply Chain Risk Management Dashboard Deploying Computer Security Incident Management
Cyber Supply Chain Risk Management Dashboard Deploying Computer Security Incident ManagementThis slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc.Present the topic in a bit more detail with this Cyber Supply Chain Risk Management Dashboard Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Resource Security Hygiene, Subscription Coverage, Resource Health Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
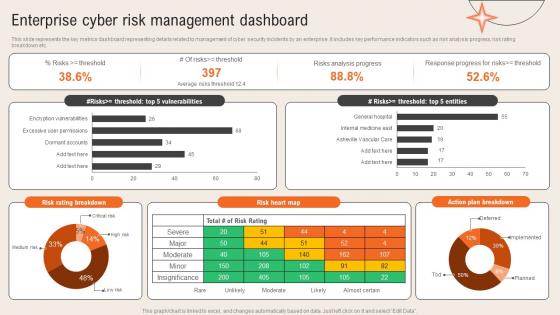 Enterprise Cyber Risk Management Dashboard Deploying Computer Security Incident Management
Enterprise Cyber Risk Management Dashboard Deploying Computer Security Incident ManagementThis slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc.Present the topic in a bit more detail with this Enterprise Cyber Risk Management Dashboard Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Risks Analysis Progress, Response Progress, Action Plan Breakdown. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
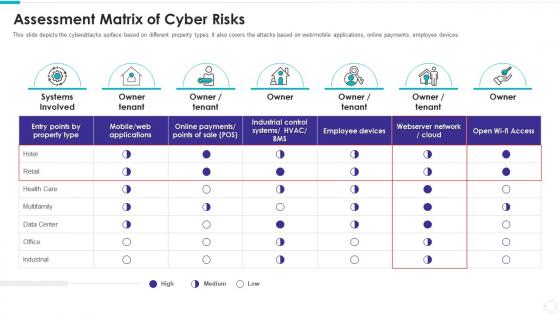 Electronic information security assessment matrix of cyber risks
Electronic information security assessment matrix of cyber risksThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Present the topic in a bit more detail with this Electronic Information Security Assessment Matrix Of Cyber Risks. Use it as a tool for discussion and navigation on Systems Involved, Owner Tenant, Data Center, Industrial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Electronic information security strategies to manage cyber risks
Electronic information security strategies to manage cyber risksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Increase audience engagement and knowledge by dispensing information using Electronic Information Security Strategies To Manage Cyber Risks. This template helps you present information on four stages. You can also present information on Prioritize Cyber Risk Strategic Issue, Build Policies And Structures, Invest Worthy Implementation, Conduct Awareness Sessions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 5 practices of information and cyber security risk management
5 practices of information and cyber security risk managementMentioned slide delineates best practices for information security risk management. Knowledge of IT environment and assets, developing risk management strategy, embedding risk management into organization culture, continuous risk assessment and security protocols are the practices covered in this slide. Presenting our set of slides with 5 Practices Of Information And Cyber Security Risk Management. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Management, Organization, Risk.
-
 Cyber and information security risk management framework
Cyber and information security risk management frameworkMentioned slide exhibits information security risk management framework which can be used to enhance cybersecurity of organization. The various components covered in this framework are service design, transition and operationalization, penetration testing etc. Introducing our Cyber And Information Security Risk Management Framework set of slides. The topics discussed in these slides are Development, Service Transition, Service Operationalization. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Icon for information and cyber security risk management
Icon for information and cyber security risk managementIntroducing our premium set of slides with Icon For Information And Cyber Security Risk Management. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon For Information And Cyber Security Risk Management. So download instantly and tailor it with your information.
-
 Information and cyber security risk management maturity levels
Information and cyber security risk management maturity levelsMentioned slide showcase maturity stages of information security risk management, which will assist company to develop comprehensive cybersecurity strategy. The maturity stages could be Partial informed repetitive and adaptive. Introducing our premium set of slides with Information And Cyber Security Risk Management Maturity Levels. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Partial, Informed, Repetitive. So download instantly and tailor it with your information.
-
 Information and cyber security risk management plan
Information and cyber security risk management planMentioned slide showcase information security risk management plan. The template provides information about various risks such as DDoS, crypto jacking, malware and password theft and with other details like degree of risk involved, impact, strategies to be deployed. Introducing our Information And Cyber Security Risk Management Plan set of slides. The topics discussed in these slides are Degree Of Risk, Strategies, Devices. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Eliminating manual security processes managing cyber risk in a digital age
Eliminating manual security processes managing cyber risk in a digital ageMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Present the topic in a bit more detail with this Eliminating Manual Security Processes Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Vulnerability, Scanning, Resolution, Team. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information security program framework managing cyber risk in a digital age
Information security program framework managing cyber risk in a digital ageMentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver an outstanding presentation on the topic using this Information Security Program Framework Managing Cyber Risk In A Digital Age. Dispense information and present a thorough explanation of Information Security Program Framework Key Components using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Managing cyber risk in a digital age information security program values to business
Managing cyber risk in a digital age information security program values to businessFollowing slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Introducing Managing Cyber Risk In A Digital Age Information Security Program Values To Business to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Response, Management, Vulnerabilities, using this template. Grab it now to reap its full benefits.
-
 Security lifecycle managing cyber risk in a digital age
Security lifecycle managing cyber risk in a digital ageIncrease audience engagement and knowledge by dispensing information using Security Lifecycle Managing Cyber Risk In A Digital Age. This template helps you present information on one stages. You can also present information on Security Lifecycle using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Summary existing security managing cyber risk in a digital age
Summary existing security managing cyber risk in a digital ageFollowing slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Present the topic in a bit more detail with this Summary Existing Security Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Summary Existing Security Management Capabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management framework for threat protection
Cyber security risk management framework for threat protectionThis slide highlights the cyber security risk management framework which include third party risk management, IT risk assessment and security center operations. Presenting our set of slides with Cyber Security Risk Management Framework For Threat Protection. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Governance, Security Assessment, Independent Audit.
-
 Cyber threat security planning process with risk tolerance and threats
Cyber threat security planning process with risk tolerance and threatsThis following slide illustrates the cyber security threat program planning which include steps like identify key personnel, risk tolerance strategy and developing frequency. Presenting our set of slides with Cyber Threat Security Planning Process With Risk Tolerance And Threats. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Built Risk Tolerance, Identify And Document, Establish Governance.
-
 Risk Based Methodology To Cyber And Information Security Table Of Contents
Risk Based Methodology To Cyber And Information Security Table Of ContentsDeliver an outstanding presentation on the topic using this Risk Based Methodology To Cyber And Information Security Table Of Contents Dispense information and present a thorough explanation of Threat Matrix, Identified Assets, Impact Assessment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Based Methodology To Cyber Information Security Program Framework Key Components
Risk Based Methodology To Cyber Information Security Program Framework Key ComponentsMentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc.Introducing Risk Based Methodology To Cyber Information Security Program Framework Key Components to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Culture And Awareness, Security Risk Management, Data Security And Privacy, using this template. Grab it now to reap its full benefits.
-
 Information Security Assessment Matrix Of Cyber Risks
Information Security Assessment Matrix Of Cyber RisksThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Present the topic in a bit more detail with this Information Security Assessment Matrix Of Cyber Risks. Use it as a tool for discussion and navigation on Assessment Matrix Of Cyber Risks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Strategies To Manage Cyber Risks
Information Security Strategies To Manage Cyber RisksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Introducing Information Security Strategies To Manage Cyber Risks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strategies To Manage Cyber Risks, using this template. Grab it now to reap its full benefits.
-
 Solution Recommendation For Common Business Cyber Security Risks
Solution Recommendation For Common Business Cyber Security RisksThis slide covers the major IT support skills that could potentially help organizations to solve the most common IT problems. It includes solutions for common cyber risks such as poor network security, data backup issues, etc. Introducing our premium set of slides with Solution Recommendation For Common Business Cyber Security Risks. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Risks, Solution Recommendation, Network Security. So download instantly and tailor it with your information.
-
 Checklist For Effectively Managing Asset Security Risk Based Methodology To Cyber
Checklist For Effectively Managing Asset Security Risk Based Methodology To CyberFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them.Increase audience engagement and knowledge by dispensing information using Checklist For Effectively Managing Asset Security Risk Based Methodology To Cyber This template helps you present information on one stage. You can also present information on System Monitoring, Data Backup, Security Patches using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Defining Business Priorities To Ensure Information Security Risk Based Methodology To Cyber
Defining Business Priorities To Ensure Information Security Risk Based Methodology To CyberThis slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security.Increase audience engagement and knowledge by dispensing information using Defining Business Priorities To Ensure Information Security Risk Based Methodology To Cyber This template helps you present information on three stages. You can also present information on Efficient Risk Management, Transparent Communication, Standardized Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Eliminating Manual Security Processes Through Automation Risk Based Methodology To Cyber
Eliminating Manual Security Processes Through Automation Risk Based Methodology To CyberMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools.Present the topic in a bit more detail with this Eliminating Manual Security Processes Through Automation Risk Based Methodology To Cyber Use it as a tool for discussion and navigation on Manual Vulnerability, Scanning And Resolution, Vulnerability Scanning This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons Slide For Risk Based Methodology To Cyber and Information Security
Icons Slide For Risk Based Methodology To Cyber and Information SecurityPresenting our well crafted Icons Slide For Risk Based Methodology To Cyber and Information Security set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly
-
 Information Security Program Framework Key Components Risk Based Methodology To Cyber
Information Security Program Framework Key Components Risk Based Methodology To CyberMentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc.Introducing Information Security Program Framework Key Components Risk Based Methodology To Cyber to increase your presentation threshold. Encompassed with one stage this template is a great option to educate and entice your audience. Dispence information on Culture And Awareness, Security Risk Management, Data Security And Privacy using this template. Grab it now to reap its full benefits.
-
 Information Security Program Values To Business Risk Based Methodology To Cyber
Information Security Program Values To Business Risk Based Methodology To CyberFollowing slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management.Increase audience engagement and knowledge by dispensing information using Information Security Program Values To Business Risk Based Methodology To Cyber This template helps you present information on two stages. You can also present information on Undetectable By Current, Vulnerabilities In The Current, Threats To The Companys Environment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Summary Existing Security Management Capabilities Risk Based Methodology To Cyber
Summary Existing Security Management Capabilities Risk Based Methodology To CyberFollowing slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating.Deliver an outstanding presentation on the topic using this Summary Existing Security Management Capabilities Risk Based Methodology To Cyber Dispense information and present a thorough explanation of Information From Breaching, Occurrence Identification, Information Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents For Risk Based Methodology To Cyber and Information Security
Table Of Contents For Risk Based Methodology To Cyber and Information SecurityPresent the topic in a bit more detail with this Table Of Contents For Risk Based Methodology To Cyber and Information Security Use it as a tool for discussion and navigation on Defining Business Priorities, Global Market Insights, Companies Digitization Levels This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Action Plan In Case Of Breaches Introducing A Risk Based Approach To Cyber Security
Action Plan In Case Of Breaches Introducing A Risk Based Approach To Cyber SecurityMentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time.Present the topic in a bit more detail with this Action Plan In Case Of Breaches Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Expected Resolution Time, Responsible Person, Communication Mode This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agenda Of Introducing A Risk Based Approach To Cyber Security
Agenda Of Introducing A Risk Based Approach To Cyber SecurityIntroducing Agenda Of Introducing A Risk Based Approach To Cyber Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Agenda using this template. Grab it now to reap its full benefits.
-
 Communication Plan For Cyber Breaches Introducing A Risk Based Approach To Cyber Security
Communication Plan For Cyber Breaches Introducing A Risk Based Approach To Cyber SecurityMentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible.Present the topic in a bit more detail with this Communication Plan For Cyber Breaches Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Evaluate Sprint Status, Quality Standards, Project Coordinator This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Criticality Assessment Of Identified Assets Introducing A Risk Based Approach To Cyber Security
Criticality Assessment Of Identified Assets Introducing A Risk Based Approach To Cyber SecurityFollowing slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost.Deliver an outstanding presentation on the topic using this Criticality Assessment Of Identified Assets Introducing A Risk Based Approach To Cyber Security Dispense information and present a thorough explanation of Infrastructure Hardware, Routers And Switches, Server Computers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Defining Business Security Introducing A Risk Based Approach To Cyber Security
Defining Business Security Introducing A Risk Based Approach To Cyber SecurityThis slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security.Introducing Defining Business Security Introducing A Risk Based Approach To Cyber Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Efficient Risk Management, Standardized Incident, Management Process using this template. Grab it now to reap its full benefits.
-
 Defining Risk Events Based On Introducing A Risk Based Approach To Cyber Security
Defining Risk Events Based On Introducing A Risk Based Approach To Cyber SecurityThis slide provides information about risk based events that company will use to define the risks based on impact size and likelihood of occurrence.Present the topic in a bit more detail with this Defining Risk Events Based On Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Defining Risk Events Based On Impact Size And Likelihood Of Occurrence This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Eliminating Manual Security Introducing A Risk Based Approach To Cyber Security
Eliminating Manual Security Introducing A Risk Based Approach To Cyber SecurityMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools.Present the topic in a bit more detail with this Eliminating Manual Security Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Manual Vulnerability, Scanning And Resolution, Automation Vulnerability This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Embedding Risk Based Approach Into Introducing A Risk Based Approach To Cyber Security
Embedding Risk Based Approach Into Introducing A Risk Based Approach To Cyber SecurityPurpose of this slide is to highlight the risK based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models.Introducing Embedding Risk Based Approach Into Introducing A Risk Based Approach To Cyber Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Cyberrisk Management, Security Organization, Information Security Processes using this template. Grab it now to reap its full benefits.
-
 Employee Upskilling Training Program Introducing A Risk Based Approach To Cyber Security
Employee Upskilling Training Program Introducing A Risk Based Approach To Cyber SecurityMentioned slide displays a five day employee upskilling training program that company will use to provide an in dept details about information security program activities and deliverables.Present the topic in a bit more detail with this Employee Upskilling Training Program Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Assess Security Requirements, Perform A Gap Analysis, Develop Gap Initiatives This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Flow Diagram Of Incident Response Process Introducing A Risk Based Approach To Cyber Security
Flow Diagram Of Incident Response Process Introducing A Risk Based Approach To Cyber SecurityMentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down.Present the topic in a bit more detail with this Flow Diagram Of Incident Response Process Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Remediate Eradicate, Contain Mitigate, Consider The Potential This template is free to edit as deemed fit for your organization. Therefore download it now.





