Powerpoint Templates and Google slides for Develop Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Incident Response Process Flow Chart Development And Implementation Of Security
Cyber Security Incident Response Process Flow Chart Development And Implementation Of SecurityThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Deliver an outstanding presentation on the topic using this Cyber Security Incident Response Process Flow Chart Development And Implementation Of Security. Dispense information and present a thorough explanation of Data Collection And Preservation, Perform Technical Analysis, Incident Declaration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incidents Follow Up Report Development And Implementation Of Security Incident Management
Cyber Security Incidents Follow Up Report Development And Implementation Of Security Incident ManagementThis slide represents the follow up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. Present the topic in a bit more detail with this Cyber Security Incidents Follow Up Report Development And Implementation Of Security Incident Management. Use it as a tool for discussion and navigation on Confidential Information Customers, Theft Confidential Information, Organizational Projects. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security Incident
Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security IncidentThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security Incident. Use it as a tool for discussion and navigation on Consequences, Vulnerability, Risk. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Threats Detection Techniques Development And Implementation Of Security Incident Management
Cyber Security Threats Detection Techniques Development And Implementation Of Security Incident ManagementThis slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Present the topic in a bit more detail with this Cyber Security Threats Detection Techniques Development And Implementation Of Security Incident Management. Use it as a tool for discussion and navigation on Intruder Traps, Attacker And User Behavior Analytics, Threat Intelligence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Development And Implementation Of Security Incident Management Table Of Contents
Development And Implementation Of Security Incident Management Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Development And Implementation Of Security Incident Management Table Of Contents. This template helps you present information on one stages. You can also present information on Best Practices, Cybersecurity Incident Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Five Phases Of Cybersecurity Incident Management Development And Implementation Of Security Incident
Five Phases Of Cybersecurity Incident Management Development And Implementation Of Security IncidentThis slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Introducing Five Phases Of Cybersecurity Incident Management Development And Implementation Of Security Incident to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Assess And Design, Detect And Report, Plan And Prepare, using this template. Grab it now to reap its full benefits.
-
 Gap Analysis Representing Current Situation Of Cybersecurity Development And Implementation Of Security
Gap Analysis Representing Current Situation Of Cybersecurity Development And Implementation Of SecurityThis slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Deliver an outstanding presentation on the topic using this Gap Analysis Representing Current Situation Of Cybersecurity Development And Implementation Of Security. Dispense information and present a thorough explanation of Report Cyber Security Incidents, Relevant Authority using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Icons Slide For Development And Implementation Of Security Incident Management
Icons Slide For Development And Implementation Of Security Incident ManagementIntroducing our well researched set of slides titled Icons Slide For Development And Implementation Of Security Incident Management. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Impact Of Cybersecurity Incidents On Organization Development And Implementation Of Security Incident
Impact Of Cybersecurity Incidents On Organization Development And Implementation Of Security IncidentThis slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Increase audience engagement and knowledge by dispensing information using Impact Of Cybersecurity Incidents On Organization Development And Implementation Of Security Incident. This template helps you present information on five stages. You can also present information on Increased Costs, Operational Disruption, Reputational Damage using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Impact Of Implementing Cyber Security Incident Management Development And Implementation Of Security
Impact Of Implementing Cyber Security Incident Management Development And Implementation Of SecurityThis slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Present the topic in a bit more detail with this Impact Of Implementing Cyber Security Incident Management Development And Implementation Of Security. Use it as a tool for discussion and navigation on Results, Post Implementation, Pre Implementation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Parameters To Select Cyber Security Containment Strategy Development And Implementation Of Security
Key Parameters To Select Cyber Security Containment Strategy Development And Implementation Of SecurityThis slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Introducing Key Parameters To Select Cyber Security Containment Strategy Development And Implementation Of Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Organizational Resources, Potential Damages, Strategy, using this template. Grab it now to reap its full benefits.
-
 Strategies To Analyze Cyber Security Incidents Development And Implementation Of Security Incident Management
Strategies To Analyze Cyber Security Incidents Development And Implementation Of Security Incident ManagementThis slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Increase audience engagement and knowledge by dispensing information using Strategies To Analyze Cyber Security Incidents Development And Implementation Of Security Incident Management. This template helps you present information on two stages. You can also present information on Profile Network And Systems, Understand Normal Behaviors, Perform Event Correlation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents For Development And Implementation Of Security Incident Management
Table Of Contents For Development And Implementation Of Security Incident ManagementIntroducing Table Of Contents For Development And Implementation Of Security Incident Management to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Security Incident Response Management, Cyber Security Incident Response Lifecycle, Cyber Security Incident Management, using this template. Grab it now to reap its full benefits.
-
 Various Cyber Security Incidents Detected By It Department Development And Implementation Of Security
Various Cyber Security Incidents Detected By It Department Development And Implementation Of SecurityThis slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Increase audience engagement and knowledge by dispensing information using Various Cyber Security Incidents Detected By It Department Development And Implementation Of Security. This template helps you present information on five stages. You can also present information on Insider Threat, Phishing Attack, Malware Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ways To Detect Cyber Security Incidents Development And Implementation Of Security Incident Management
Ways To Detect Cyber Security Incidents Development And Implementation Of Security Incident ManagementThis slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Introducing Ways To Detect Cyber Security Incidents Development And Implementation Of Security Incident Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Privileged User Accounts, Unusual Behavior, Network Traffic, using this template. Grab it now to reap its full benefits.
-
 Steps To Develop Security Communication Plan For Large Events
Steps To Develop Security Communication Plan For Large EventsThe following slide brings forth major steps to develop security communication plan for large events which will assist event managers to take actions accordingly. The steps are to identify key stakeholders, create security teams, assess best communication platforms, etc.Presenting our set of slides with Steps To Develop Security Communication Plan For Large Events. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify Key Stakeholders, Create Security Teams, Communication Platforms.
-
 Dashboard To Track IT Security Incidents Prevailing Develop Business Aligned IT Strategy
Dashboard To Track IT Security Incidents Prevailing Develop Business Aligned IT StrategyThis slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Deliver an outstanding presentation on the topic using this Dashboard To Track IT Security Incidents Prevailing Develop Business Aligned IT Strategy. Dispense information and present a thorough explanation of Application Whitelisting, Application Hardening, Patch Operating Systems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 How Management Enables Effective Corporate Security Develop Business Aligned IT Strategy
How Management Enables Effective Corporate Security Develop Business Aligned IT StrategyThis slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Deliver an outstanding presentation on the topic using this How Management Enables Effective Corporate Security Develop Business Aligned IT Strategy. Dispense information and present a thorough explanation of Senior Executives, Steering Committees, Chief Security Officer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Governance Management Develop Business Aligned IT Strategy
Information Security And Governance Management Develop Business Aligned IT StrategyThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Present the topic in a bit more detail with this Information Security And Governance Management Develop Business Aligned IT Strategy. Use it as a tool for discussion and navigation on Infrastructure Security, Response And Recovery, Security Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Risk Management Framework To Manage Security Threats Develop Business Aligned IT Strategy
IT Risk Management Framework To Manage Security Threats Develop Business Aligned IT StrategyThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Increase audience engagement and knowledge by dispensing information using IT Risk Management Framework To Manage Security Threats Develop Business Aligned IT Strategy. This template helps you present information on three stages. You can also present information on Enterprise Security Program, Control Environment, Security Processes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Development And Implementation Of Security Key Issues Faced By Organization Due To Cybersecurity Incidents
Development And Implementation Of Security Key Issues Faced By Organization Due To Cybersecurity IncidentsThis slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Introducing Development And Implementation Of Security Key Issues Faced By Organization Due To Cybersecurity Incidents to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Employees, Privacy, Compliance, Security, using this template. Grab it now to reap its full benefits.
-
 Development And Implementation Of Security Key Lessons Learned By Organization From Cyber Security Incident
Development And Implementation Of Security Key Lessons Learned By Organization From Cyber Security IncidentThis slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. Increase audience engagement and knowledge by dispensing information using Development And Implementation Of Security Key Lessons Learned By Organization From Cyber Security Incident. This template helps you present information on three stages. You can also present information on Active, Probably Stay, No Signs Reduction Ransomware Activities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Development And Implementation User Awareness Training Program To Prevent Cyber Security Incidents
Development And Implementation User Awareness Training Program To Prevent Cyber Security IncidentsThis slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Deliver an outstanding presentation on the topic using this Development And Implementation User Awareness Training Program To Prevent Cyber Security Incidents. Dispense information and present a thorough explanation of Password Security, Cloud And Internet Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
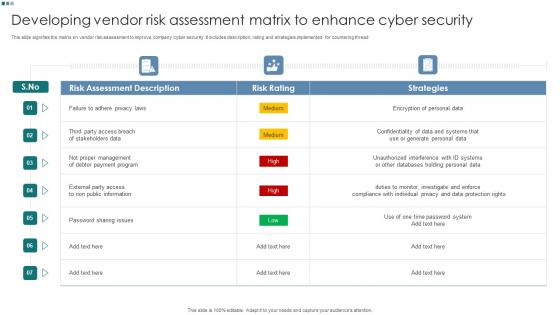 Developing Vendor Risk Assessment Matrix To Enhance Cyber Security
Developing Vendor Risk Assessment Matrix To Enhance Cyber SecurityThis slide signifies the matrix on vendor risk assessment to improve company cyber security. It includes description, rating and strategies implemented for countering thread. Introducing our Developing Vendor Risk Assessment Matrix To Enhance Cyber Security set of slides. The topics discussed in these slides are Strategies, Risk Assessment, Risk Rating. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Dashboard To Track It Security Incidents Prevailing Blueprint Develop Information It Roadmap Strategy Ss
Dashboard To Track It Security Incidents Prevailing Blueprint Develop Information It Roadmap Strategy SsThis slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Deliver an outstanding presentation on the topic using this Dashboard To Track It Security Incidents Prevailing Blueprint Develop Information It Roadmap Strategy Ss. Dispense information and present a thorough explanation of Dashboard, Information, Authentification using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Governance Management Blueprint Develop Information It Roadmap Strategy Ss
Information Security And Governance Management Blueprint Develop Information It Roadmap Strategy SsThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Present the topic in a bit more detail with this Information Security And Governance Management Blueprint Develop Information It Roadmap Strategy Ss. Use it as a tool for discussion and navigation on Evaluation And Direction, Identify Security, Infrastructure Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 It Risk Management Framework To Manage Security Blueprint Develop Information It Roadmap Strategy Ss
It Risk Management Framework To Manage Security Blueprint Develop Information It Roadmap Strategy SsThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Present the topic in a bit more detail with this It Risk Management Framework To Manage Security Blueprint Develop Information It Roadmap Strategy Ss. Use it as a tool for discussion and navigation on Management, Framework, Environment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SDN Security IT Methodologies For Developing SDN 4d Approach
SDN Security IT Methodologies For Developing SDN 4d ApproachThis slide represents the 4D methodology of SDN development and includes the architecture and principles of the 4D approach. It also caters to the four planes that handle decision, distribution, discovery, and information. Deliver an outstanding presentation on the topic using this SDN Security IT Methodologies For Developing SDN 4d Approach. Dispense information and present a thorough explanation of Developing, Methodologies, Approach using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 W20 SDN Security IT Methodologies For Developing SDN Ethane
W20 SDN Security IT Methodologies For Developing SDN EthaneThis slide depicts the ethane methodology of SDN development by covering its overview and principles. It also caters to ethane architecture consisting of policies, registration, topology, bindings, flow entities, network devices, and an ethane controller. Deliver an outstanding presentation on the topic using this W20 SDN Security IT Methodologies For Developing SDN Ethane. Dispense information and present a thorough explanation of Developing, Methodologies, Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 W21 SDN Security IT Methodologies For Developing SDN Forces
W21 SDN Security IT Methodologies For Developing SDN ForcesThis slide depicts the forwarding and control element separation methodology of SDN development and caters to the overview and deployment methods. It also includes the FORCES architecture, consisting of control and forwarding elements. Present the topic in a bit more detail with this W21 SDN Security IT Methodologies For Developing SDN Forces. Use it as a tool for discussion and navigation on Methodologies, Developing, Overview. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategies To Develop Effective Cyber Security Plan Ppt Professional Infographics
Strategies To Develop Effective Cyber Security Plan Ppt Professional InfographicsThis slide represents the techniques to be adopted by administration to effectively manage cyber security incidents in order to reduce their impact on business operations. It includes strategies to develop cyber security plan such as establish IR team, conduct threat analysis etc.Introducing Strategies To Develop Effective Cyber Security Plan Ppt Professional Infographics to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Response Guidelines, External Communication, Develop Procedures, using this template. Grab it now to reap its full benefits.
-
 Develop Raci Chart Generating Security Awareness Among Employees To Reduce
Develop Raci Chart Generating Security Awareness Among Employees To ReduceThe following slide depicts the RACI accountable, consulted, responsible, informed plan to facilitate and ensure speedy communication during cyber issue management. It includes activities such as overall coordination, media messaging, internal communication, technical assistance etc. Deliver an outstanding presentation on the topic using this Develop Raci Chart Generating Security Awareness Among Employees To Reduce Dispense information and present a thorough explanation of Incident Management, Team Coordinator using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Analyzing Multiple Sales Tactics For Securing New Leads Developing Actionable Sales Plan Tactics
Analyzing Multiple Sales Tactics For Securing New Leads Developing Actionable Sales Plan TacticsThis slide provides glimpse about employing different techniques that can help the business in new lead generation. It includes techniques such as social media marketing, cold calling, email marketing, their impact, etc. Introducing Analyzing Multiple Sales Tactics For Securing New Leads Developing Actionable Sales Plan Tactics to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Social Media Marketing, Cold Calling, Email Marketing , using this template. Grab it now to reap its full benefits.
-
 Best Practices To Develop Cyber Security Communication Plan
Best Practices To Develop Cyber Security Communication PlanThis slide illustrates various best practices for developing an effective Cyber security communication plan. It includes best practices such as make plan flexible, provide visibility to audience and keep relevant and engaging content. Presenting our set of slides with Best Practices To Develop Cyber Security Communication Plan This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Make Plan Flexible, Visibility To Audience, Relevant And Engaging Content
-
 Cyber Security Communication Plan Development Icon
Cyber Security Communication Plan Development IconPresenting our set of slides with Cyber Security Communication Plan Development Icon This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Communication, Plan Development Icon
-
 Cyber Security Communication Plan Development Strategy Icon
Cyber Security Communication Plan Development Strategy IconIntroducing our premium set of slides with Cyber Security Communication Plan Development Strategy Icon Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security Communication Plan, Development Strategy Icon So download instantly and tailor it with your information.
-
 Cyber Security Incident Response Communication Plan Development
Cyber Security Incident Response Communication Plan DevelopmentThis slide illustrates steps to develop a cyber security incident response communication plan to minimize impact level. It includes steps such as formulate team activation process, designate person, create criteria for law involvement etc. Presenting our set of slides with Cyber Security Incident Response Communication Plan Development This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Formulate Team Activation Process, Designate, Person, Formulate, Communication Template
-
 Ways To Develop Cyber Security Communication Plan For Employees
Ways To Develop Cyber Security Communication Plan For EmployeesThis slide showcase ways to formulate a cyber security communication plan for employees to respond proactive during a cyber incident. It include ways such as formulate internal communication strategy, tell a story and implement training session. Presenting our set of slides with Ways To Develop Cyber Security Communication Plan For Employees This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Formulate Internal Communication Strategy, Tell A Story, Implement Training Session
-
 SDN Development Approaches What Role Does SDN Play In Customer Security
SDN Development Approaches What Role Does SDN Play In Customer SecurityThis slide represents the role of software defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low security public facing network for regular information. Increase audience engagement and knowledge by dispensing information using SDN Development Approaches What Role Does SDN Play In Customer Security . This template helps you present information on five stages. You can also present information on Customer, Security, Connection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 W66 SDN Development Approaches Software Defined Networking And Security
W66 SDN Development Approaches Software Defined Networking And SecurityThis slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and ddos. It also includes security components for SDN such as infrastructure, controller, API, and application security. Present the topic in a bit more detail with this W66 SDN Development Approaches Software Defined Networking And Security. Use it as a tool for discussion and navigation on Networking, Security, Secure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Web Development Technique Web Designing And Development
Security Web Development Technique Web Designing And DevelopmentThis slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.Increase audience engagement and knowledge by dispensing information using Security Web Development Technique Web Designing And Development. This template helps you present information on three stages. You can also present information on Intrusion Detection, Application Firewall, Database Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 What Is The Cyber Security Web Designing And Development
What Is The Cyber Security Web Designing And DevelopmentThis slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.Increase audience engagement and knowledge by dispensing information using What Is The Cyber Security Web Designing And Development. This template helps you present information on four stages. You can also present information on Deletion Cybercriminals, Protect Information, Resources Manipulation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data interchange security management development integration financial management
Data interchange security management development integration financial managementPresenting this set of slides with name - Data Interchange Security Management Development Integration Financial Management. This is an editable seven graphic that deals with topics like Data Interchange, Security Management, Development Integration, Financial Management to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Application environment security controls application development security information accuracy
Application environment security controls application development security information accuracyPresenting this set of slides with name - Application Environment Security Controls Application Development Security Information Accuracy. This is an editable seven stages graphic that deals with topics like Application Environment Security Controls, Application Development Security, Information Accuracy to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Data stewardship application development product delivery data security
Data stewardship application development product delivery data securityPresenting this set of slides with name - Data Stewardship Application Development Product Delivery Data Security. This is an editable five stages graphic that deals with topics like Data Stewardship, Application Development, Product Delivery, Data Security to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Inability farmers increase food security training material developed
Inability farmers increase food security training material developedPresenting this set of slides with name - Inability Farmers Increase Food Security Training Material Developed. This is an editable four stages graphic that deals with topics like Inability Farmers, Increase Food Security, Training Material Developed to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Risk factors defining service delivery system development data security and management
Risk factors defining service delivery system development data security and managementPresenting this set of slides with name - Risk Factors Defining Service Delivery System Development Data Security And Management. This is a six stage process. The stages in this process are Risk Factors, Risk Management, Risk Variable.
-
 Application development security software protection mechanism financial modeling
Application development security software protection mechanism financial modelingPresenting this set of slides with name - Application Development Security Software Protection Mechanism Financial Modeling. This is an editable five stages graphic that deals with topics like Application Development Security, Software Protection Mechanism, Financial Modeling to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Brand development management working teams effectively iot security cpb
Brand development management working teams effectively iot security cpbPresenting this set of slides with name - Brand Development Management Working Teams Effectively Iot Security Cpb. This is an editable three graphic that deals with topics like Brand Development Management, Working Teams Effectively, Iot Security to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
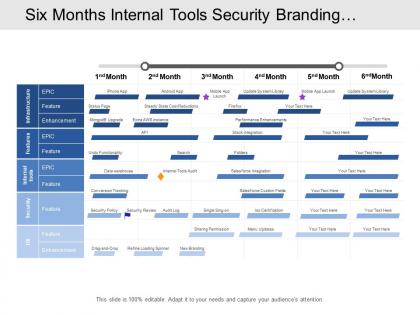 Six months internal tools security branding integration development timeline
Six months internal tools security branding integration development timelinePresenting this set of slides with name - Six Months Internal Tools Security Branding Integration Development Timeline. This is a six stage process. The stages in this process are Development Timeline, Development Roadmap, Production Timeline.
-
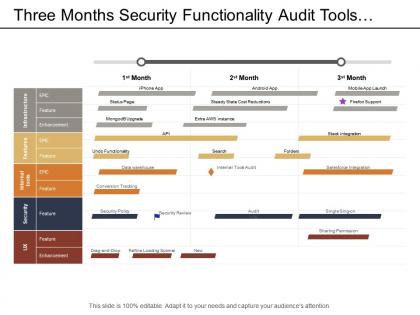 Three months security functionality audit tools development timeline
Three months security functionality audit tools development timelinePresenting this set of slides with name - Three Months Security Functionality Audit Tools Development Timeline. This is a three stage process. The stages in this process are Development Timeline, Development Roadmap, Production Timeline.
-
 Yearly feature enhancement security audit infrastructure development timeline
Yearly feature enhancement security audit infrastructure development timelinePresenting this set of slides with name - Yearly Feature Enhancement Security Audit Infrastructure Development Timeline. This is a five stage process. The stages in this process are Development Timeline, Development Roadmap, Production Timeline.
-
 Identify development needs personal growth job security
Identify development needs personal growth job securityPresenting this set of slides with name - Identify Development Needs Personal Growth Job Security. This is a five stage process. The stages in this process are Physiological, Job Security, Belonging, Self Esteem, Personal Growth.
-
 Identify development needs physiological job security personal growth
Identify development needs physiological job security personal growthPresenting this set of slides with name - Identify Development Needs Physiological Job Security Personal Growth. This is a five stage process. The stages in this process are Physiological, Job Security, Belonging, Self Esteem, Personal Growth.
-
 Business strategy continuity management network security product development cpb
Business strategy continuity management network security product development cpbPresenting this set of slides with name - Business Strategy Continuity Management Network Security Product Development Cpb. This is an editable four stages graphic that deals with topics like Business, Strategy, Continuity, Management, Network, Security, Product, Development to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Big data development big data security market ppt powerpoint presentation infographics infographic template cpb
Big data development big data security market ppt powerpoint presentation infographics infographic template cpbPresenting this set of slides with name Big Data Development Big Data Security Market Ppt Powerpoint Presentation Infographics Infographic Template Cpb. This is an editable Powerpoint six stages graphic that deals with topics like Big Data Development Big Data Security Market to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Business development strategy template templates chain security teamwork ppt powerpoint
Business development strategy template templates chain security teamwork ppt powerpointWe are proud to present our business development strategy template templates chain security teamwork ppt powerpoint. This PowerPoint Template Targets the Security in Life, Business as shown above. This Template points to the Chain Security which signifies Team Work.
-
 Business strategy development powerpoint templates mind key security ppt process
Business strategy development powerpoint templates mind key security ppt processWe are proud to present our business strategy development powerpoint templates mind key security ppt process. This template with keys in mind on it will be the great choice for presentations on security, symbol, shapes, and business.
-
 Payment security and fraud management solutions development ppt powerpoint presentation gallery
Payment security and fraud management solutions development ppt powerpoint presentation galleryPresenting this set of slides with name Payment Security And Fraud Management Solutions Development Ppt Powerpoint Presentation Gallery. This is a six process. The stages in this process are Development, Behavioural Analytics, Operational Costs, Location, Payments Process. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Secure development life cycle ppt powerpoint presentation professional vector cpb
Secure development life cycle ppt powerpoint presentation professional vector cpbPresenting this set of slides with name Secure Development Life Cycle Ppt Powerpoint Presentation Professional Vector Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Secure Development Life Cycle to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.





