Powerpoint Templates and Google slides for Develop Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Developing Cyber Security Awareness Training Program For Staff Powerpoint Presentation Slides
Developing Cyber Security Awareness Training Program For Staff Powerpoint Presentation SlidesThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Developing Cyber Security Awareness Training Program For Staff Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of seventy two slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Development And Implementation Of Security Incident Management Powerpoint Presentation Slides V
Development And Implementation Of Security Incident Management Powerpoint Presentation Slides VEnthrall your audience with this Development And Implementation Of Security Incident Management Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising seventy slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Meta Data Organizational Securing Reporting Processing Development Monitoring
Meta Data Organizational Securing Reporting Processing Development MonitoringIf you require a professional template with great design, then this Meta Data Organizational Securing Reporting Processing Development Monitoring is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twelve slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Information security risk management development investment analytics framework
Information security risk management development investment analytics frameworkIf you require a professional template with great design, then this Information Security Risk Management Development Investment Analytics Framework is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twelve slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
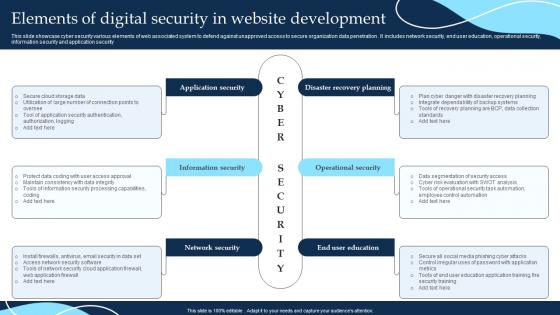 Elements Of Digital Security In Website Development
Elements Of Digital Security In Website DevelopmentThis slide showcase cyber security various elements of web associated system to defend against unapproved access to secure organization data penetration. It includes network security, end user education, operational security, information security and application security Presenting our set of slides with Elements Of Digital Security In Website Development. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security, Information, Network.
-
 Develop Checklist To Review KYC And AML Policy Security Token Offerings BCT SS
Develop Checklist To Review KYC And AML Policy Security Token Offerings BCT SSThe following slide depicts KYC and AML policy checklist to prevent money laundering and ensure customer due diligence. It includes elements such as collect users personal data, verifying details, specifying duration for checking, defining actions for unverified clients, checking taxation laws, etc. Deliver an outstanding presentation on the topic using this Develop Checklist To Review KYC And AML Policy Security Token Offerings BCT SS. Dispense information and present a thorough explanation of Develop Checklist, Determine Whether, Verify User Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Develop Security Token Offering Plan Security Token Offerings BCT SS
Develop Security Token Offering Plan Security Token Offerings BCT SSThe following slide depicts sample security token offering STO plan to enable fundraising and crowd funding activities. It includes elements such as number of tokens, percentage allocated to public, private investors, pre-sale participants, project teams, reserve funds, etc. Introducing Develop Security Token Offering Plan Security Token Offerings BCT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Elements, Completion Of Tokenization Process, Offering Plan, using this template. Grab it now to reap its full benefits.
-
 Develop Token Distribution And Allocation Plan Security Token Offerings BCT SS
Develop Token Distribution And Allocation Plan Security Token Offerings BCT SSThe following slide depicts sample security token distribution plan to enhance community participation and engagement. It includes components such as number of tokens allocated, vesting period, utility offered, distribution timeline, etc. Increase audience engagement and knowledge by dispensing information using Develop Token Distribution And Allocation Plan Security Token Offerings BCT SS. This template helps you present information on two stages. You can also present information on Token Allocation, Vesting Period, Distribution Timeline using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Major Challenges In Future Development Of Security Token Offerings Security Token Offerings BCT SS
Major Challenges In Future Development Of Security Token Offerings Security Token Offerings BCT SSThe following slide showcases the major issues in future development of security tokens to boost early stage adoption. It includes elements such as no uniformity, legal protection, regulations, manual processes, valuation, anti-money laundering, etc. Introducing Major Challenges In Future Development Of Security Token Offerings Security Token Offerings BCT SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Legal Protection, Manual Process, Valuation, Anti Money Laundering, using this template. Grab it now to reap its full benefits.
-
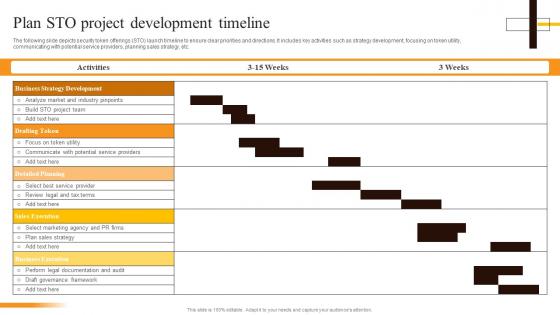 Plan STO Project Development Timeline Security Token Offerings BCT SS
Plan STO Project Development Timeline Security Token Offerings BCT SSThe following slide depicts security token offerings STO launch timeline to ensure clear priorities and directions. It includes key activities such as strategy development, focusing on token utility, communicating with potential service providers, planning sales strategy, etc. Present the topic in a bit more detail with this Plan STO Project Development Timeline Security Token Offerings BCT SS. Use it as a tool for discussion and navigation on Business Strategy Development, Drafting Token, Detailed Planning. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure Web Application Development Best Practices
Secure Web Application Development Best PracticesThis slide represents best practices of web application development in a secure way. It includes various practices such as maintain security, being paranoid, encrypt data, use exception management, apply access control, etc Presenting our set of slides with Secure Web Application Development Best Practices. This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Maintain Security, Encrypt Data, Use Exception Management.
-
 4 Step Development Process For Big Data Analytics Security
4 Step Development Process For Big Data Analytics SecurityThis slide depicts the 4 step developmental process for big data analytics. The purpose of this slide is to help the business establish big data security analytics in an appropriate manner for safeguarding sensitive and important business information. It includes steps such as classification, encryption, etc. Presenting our set of slides with 4 Step Development Process For Big Data Analytics Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Classification, Data Encryption.
-
 Sources For Securing Finance In Real Estate Development
Sources For Securing Finance In Real Estate DevelopmentThis slide highlights real estate finance for development. The purpose of this slide is to assist organizations in reducing the chances of losses by allocating investments among various financial instruments. It includes sources such as equity investment, bank loan, etc. Introducing our Sources For Securing Finance In Real Estate Development set of slides. The topics discussed in these slides are Equity Investment, Private Investors. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Critical Elements For Developing Information Security Management Plan
Critical Elements For Developing Information Security Management PlanThis slide shows the key elements for developing a successful information security management plan. This slide aims to help the company establish a robust and suitable security plan for protecting data against cyber threats and attacks. It includes components such as network security, physical measures, employee training, etc.Introducing our premium set of slides with Critical Elements For Developing Information Security Management Plan. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Security, Data Backup, Physical Security. So download instantly and tailor it with your information.
-
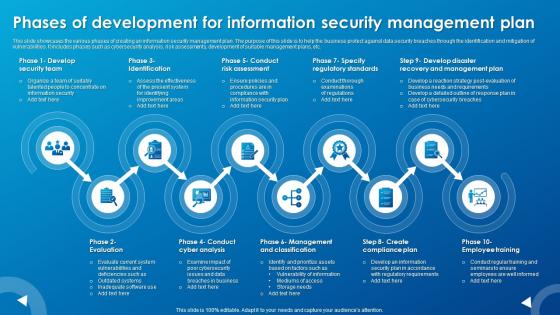 Phases Of Development For Information Security Management Plan
Phases Of Development For Information Security Management PlanThis slide showcases the various phases of creating an information security management plan. The purpose of this slide is to help the business protect against data security breaches through the identification and mitigation of vulnerabilities. It includes phases such as cybersecurity analysis, risk assessments, development of suitable management plans, etc.Presenting our set of slides with Phases Of Development For Information Security Management Plan. This exhibits information on ten stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Evaluate Current System, Outdated Systems, Inadequate Software.
-
 Cloud Development Security Use Cases
Cloud Development Security Use CasesThis slide mentions certain use cases of cloud development security to automate threat detection tools and reduce risk. It involves use cases such as cloud migration, cloud threat analysis, devsecops and cloud security compliance. Introducing our premium set of slides with Cloud Development Security Use Cases. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cloud Threat Analysis, Cloud Migration. So download instantly and tailor it with your information.
-
 Cloud Network Security Development Icon
Cloud Network Security Development IconIntroducing our premium set of slides with Cloud Network Security Development Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cloud Network Security Development. So download instantly and tailor it with your information.
-
 Information Security Plan Development Stages
Information Security Plan Development StagesThis slide covers steps for information system security plan creation to protect personal information and sensitive company data. It includes team creation, security risk evaluation, protective measures assessment, risk analysis, risk evaluation, data management, regulatory standards, compliance plan development, incident plan management and employees evaluation. Introducing our premium set of slides with Information Security Plan Development Stages. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Create Security Team, Develop Compliance Plan, Evaluate Employees. So download instantly and tailor it with your information.
-
 Data Security Best Practices To Developing Targeted Marketing Campaign MKT SS V
Data Security Best Practices To Developing Targeted Marketing Campaign MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Increase audience engagement and knowledge by dispensing information using Data Security Best Practices To Developing Targeted Marketing Campaign MKT SS V. This template helps you present information on four stages. You can also present information on Policy, Encryption, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Risk Trends For Security Policy Development
Cybersecurity Risk Trends For Security Policy DevelopmentThis slide highlights cybersecurity risk trends for enhancing organization security ensuring digital operations resilience. It includes developments such as attack surface expansion, identify system defense, digital supply chain risk, etc. Presenting our well structured Cybersecurity Risk Trends For Security Policy Development. The topics discussed in this slide are Attack Surface Expansion, Identify System Defense, Digital Supply Chain Risk. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Training And Development Plan Icon For IT Security Staff
Training And Development Plan Icon For IT Security StaffPresenting our set of slides with Training And Development Plan Icon For IT Security Staff. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Training, Development, Security.
-
 Strategic Website Development Website Security Management Action Plan
Strategic Website Development Website Security Management Action PlanMentioned slide provides insights into site security management tips which can be implemented by businesses to prevent website hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, SSL certification, etc. Present the topic in a bit more detail with this Strategic Website Development Website Security Management Action Plan. Use it as a tool for discussion and navigation on Criteria, Description, Priority Status. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Integrating Security Principle With Dynamic System Development Method
Integrating Security Principle With Dynamic System Development MethodThis slide showcases incorporation of software security principles in DSDM model which helps in improving degree of project agility. It provides information regarding execution, functional model iteration, security design and security functional modulation. Introducing our Integrating Security Principle With Dynamic System Development Method set of slides. The topics discussed in these slides are Business Study, Integrating Security, Dynamic System Development. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Secure Your Digital Assets Roadmap Of Development Of Cryptocurrency In Market
Secure Your Digital Assets Roadmap Of Development Of Cryptocurrency In MarketThis slide represents the roadmap for the development of cryptocurrency. The key steps include planning and research, design and development, testing and quality assurance, launch user acquisition, etc. Increase audience engagement and knowledge by dispensing information using Secure Your Digital Assets Roadmap Of Development Of Cryptocurrency In Market. This template helps you present information on six stages. You can also present information on Post Launch Maintenance And Growth, Testing And Quality Assurance, Planning And Research, Design And Development using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementing Byod Policy To Enhance Develop Security Policies For Data Protection
Implementing Byod Policy To Enhance Develop Security Policies For Data ProtectionThis slide shows major data protection policies for handling sensitive data of corporate. It include policies such as device security, network and data handling, etc. Introducing Implementing Byod Policy To Enhance Develop Security Policies For Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, Data Handling, Device Security, Data Protection, using this template. Grab it now to reap its full benefits.
-
 Budget Securing Tips For Public Relations Public Relations Marketing To Develop MKT SS V
Budget Securing Tips For Public Relations Public Relations Marketing To Develop MKT SS VThis slide shows various tips which can be used by organizations to while developing marketing budget. It includes aligning marketing outcome with organizational goals, strategic insights and highlight impacts. Increase audience engagement and knowledge by dispensing information using Budget Securing Tips For Public Relations Public Relations Marketing To Develop MKT SS V. This template helps you present information on three stages. You can also present information on Align Marketing Outcomes, Strategic Insights, Highlight Impacts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Devsecops Best Practices For Secure Devsecops Development Security And Operations
Devsecops Best Practices For Secure Devsecops Development Security And OperationsThis slide discusses the working process of development, security and operations in DevSecOps. The purpose of this slide is to highlight the process followed by DevSecOps for providing, monitoring and managing security at each level of the software system. Introducing Devsecops Best Practices For Secure Devsecops Development Security And Operations to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Development, Security, Operations, Code Expedites Development, using this template. Grab it now to reap its full benefits.
-
 Devsecops Best Practices For Secure Devsecops Pipeline Development Pre Commit Stage
Devsecops Best Practices For Secure Devsecops Pipeline Development Pre Commit StageThis slide discusses the development pre-commit stage of the DevSecOps pipeline. The purpose of this slide is to explain the pre-commit phase that includes initial defense on developer laptops, early security implementation, and Git pre-commit hooks for feedback. Increase audience engagement and knowledge by dispensing information using Devsecops Best Practices For Secure Devsecops Pipeline Development Pre Commit Stage. This template helps you present information on six stages. You can also present information on Static Analysis Scans, Security Engineer Peer Reviews, Lightweight Threat Modeling using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Devsecops Best Practices For Secure Software Development Security Importance And Drivers
Devsecops Best Practices For Secure Software Development Security Importance And DriversThis slide discusses the importance and driver of software development security. The purpose of this slide is to explain the importance of security in software development and its key drivers, which are cyber threat defense, data privacy, regulatory adherence, and so on. Increase audience engagement and knowledge by dispensing information using Devsecops Best Practices For Secure Software Development Security Importance And Drivers. This template helps you present information on three stages. You can also present information on Reputation Protection, Financial Risk Reduction, Data Privacy, Operational Risk Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Develop Raci Chart For Team Collaboration Creating Cyber Security Awareness
Develop Raci Chart For Team Collaboration Creating Cyber Security AwarenessThe following slide depicts the RACI accountable, consulted, responsible, informed plan to facilitate and ensure speedy communication during cyber issue management. It includes activities such as overall coordination, media messaging, internal communication, technical assistance etc. Deliver an outstanding presentation on the topic using this Develop Raci Chart For Team Collaboration Creating Cyber Security Awareness Dispense information and present a thorough explanation of Malware, Phishing, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Handling In Front End Development
Security Handling In Front End DevelopmentThis slide showcases security in front-end development which helps to protect user data and mitigate potential threats. It includes pointers such as data validation, sanitization, cross-site scripting, content security policies, secure communication and error handling. Presenting our set of slides with Development. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Validation And Sanitization, Content Security Policies, Secure Communication.
-
 Comparative Analysis Of Security Technology Stack For Software Development
Comparative Analysis Of Security Technology Stack For Software DevelopmentThis slide showcases the comparison between security technology stack used for software development which helps an organization to carefully analyze and reduce potential risks. It include details such as pricemonth, ratings, integrations, scalability, leverage cloud computing, etc. Introducing our Comparative Analysis Of Security Technology Stack For Software Development set of slides. The topics discussed in these slides are Scalability, Cost Effective, Manages Traffic. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Recent Developments In Healthcare Facility Security
Recent Developments In Healthcare Facility SecurityThe purpose of this slide is to focus on integrating advanced technologies to enhance overall safety and protect sensitive patient information via visitor management systems, social media monitoring, etc. Presenting our set of slides with name Recent Developments In Healthcare Facility Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Social Media Monitoring, Visitor Management Systems, Interactive Access Control, Turnstiles And Anti Tailgating Tech.
-
 Develop RACI Chart For Team Collaboration Implementing Strategies To Mitigate Cyber Security Threats
Develop RACI Chart For Team Collaboration Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the RACI accountable, consulted, responsible, informed plan to facilitate and ensure speedy communication during cyber issue management. It includes activities such as overall coordination, media messaging, internal communication, technical assistance etc. Present the topic in a bit more detail with this Develop RACI Chart For Team Collaboration Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Accountable, Consulted, Responsible This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Four Tips For Developing Strategic Retirement Planning To Build Secure Future Fin SS
Four Tips For Developing Strategic Retirement Planning To Build Secure Future Fin SSIntroducing Four Tips For Developing Strategic Retirement Planning To Build Secure Future Fin SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Four Tips, Developing Retirement Plan, using this template. Grab it now to reap its full benefits.
-
 Develop Checklist To Review Beginners Guide To Successfully Launch Security Token BCT SS V
Develop Checklist To Review Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide depicts KYC and AML policy checklist to prevent money laundering and ensure customer due diligence. It includes elements such as collect users personal data, verifying details, specifying duration for checking, defining actions for unverified clients, checking taxation laws, etc. Present the topic in a bit more detail with this Develop Checklist To Review Beginners Guide To Successfully Launch Security Token BCT SS V. Use it as a tool for discussion and navigation on Develop Checklist, Review KYC, AML Policy. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Develop Security Token Beginners Guide To Successfully Launch Security Token BCT SS V
Develop Security Token Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide depicts sample security token offering STO plan to enable fundraising and crowd funding activities. It includes elements such as number of tokens, percentage allocated to public, private investors, pre-sale participants, project teams, reserve funds, etc. Deliver an outstanding presentation on the topic using this Develop Security Token Beginners Guide To Successfully Launch Security Token BCT SS V. Dispense information and present a thorough explanation of Develop Security Token, Offering Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Develop Token Distribution Beginners Guide To Successfully Launch Security Token BCT SS V
Develop Token Distribution Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide depicts sample security token distribution plan to enhance community participation and engagement. It includes components such as number of tokens allocated, vesting period, utility offered, distribution timeline, etc. Present the topic in a bit more detail with this Develop Token Distribution Beginners Guide To Successfully Launch Security Token BCT SS V. Use it as a tool for discussion and navigation on Token Allocation, Vesting Period, Utility Offered. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Developing Holistic Approach Using Mobile Security Framework
Developing Holistic Approach Using Mobile Security FrameworkThis slide represents mobile security framework approaches and includes secure devices, safeguard applications, and content protection. Presenting our set of slides with name Developing Holistic Approach Using Mobile Security Framework. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secure Devices, Safeguard Applications, Content Protection.
-
 Security Improvement In Mobile Application Development
Security Improvement In Mobile Application DevelopmentThis slide highlights the different ways to improve security in mobile application development which includes enforce updates, enable two factor authentication, etc. Introducing our premium set of slides with name Security Improvement In Mobile Application Development. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Improvement, Mobile Application Development, Handle Sensitive Data Carefully. So download instantly and tailor it with your information.
-
 Security Features Of Cryptocurrency Exchange Development Services
Security Features Of Cryptocurrency Exchange Development ServicesThis slide highlights the security features integral to cryptocurrency exchange development services, ensuring a resilient and secure platform for users and their assets. Presenting our set of slides with Security Features Of Cryptocurrency Exchange Development Services This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Authentication, Data Encryption, Jail Login
-
 Web Security Principles For Software Development Companies
Web Security Principles For Software Development CompaniesThis template covers four principles of web security followed by well established software development businesses. The purpose of this slide is to streamline business operations by preventing hackers from data manipulation. It includes principles such as authentication, confidentiality, integrity and availability. Introducing our premium set of slides with Web Security Principles For Software Development Companies Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Confidentiality, Authentication, Integrity So download instantly and tailor it with your information.
-
 Smart Contracts Security Due Diligence Checklist Step By Step Process To Develop Blockchain BCT SS
Smart Contracts Security Due Diligence Checklist Step By Step Process To Develop Blockchain BCT SSThe following slide depicts smart contract security checklist to minimize data breaches. It includes elements such as audit, token approval, interface, restrict potential risk, hardware wallets, etc. Deliver an outstanding presentation on the topic using this Smart Contracts Security Due Diligence Checklist Step By Step Process To Develop Blockchain BCT SS. Dispense information and present a thorough explanation of Token Approval, Restrict Potential Risk, Hardware Wallets using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices For Fintech Application Development Security
Best Practices For Fintech Application Development SecurityThe purpose of this slide is to protect users personal and financial data from vulnerabilities, including best practices such as security code, multi factor authentication, encryption, etc. Presenting our set of slides with Best Practices For Fintech Application Development Security This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Code, Quality Assurance, Multi Factor Authentication
-
 Compliance Failure In Secure Coding Practices Software Development Training Program DTE SS
Compliance Failure In Secure Coding Practices Software Development Training Program DTE SSThis slide represents challenge an organization faces i.e. compliance failure due to inadequate awareness of secure coding practices leading to non compliance fines, loss of customer trust and damage to brand reputation. Increase audience engagement and knowledge by dispensing information using Compliance Failure In Secure Coding Practices Software Development Training Program DTE SS This template helps you present information on three stages. You can also present information on Customer Attrition, Competitive Advantage, Coding Practices using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ineffective Utilization Of Security Tools By Employees Software Development Training Program DTE SS
Ineffective Utilization Of Security Tools By Employees Software Development Training Program DTE SSThis slide represents challenge employee faces i.e. ineffective utilization of security tools due to inadequate awareness of secure coding practices leading to non identification of security vulnerabilities, delay response to security threats, etc. Increase audience engagement and knowledge by dispensing information using Ineffective Utilization Of Security Tools By Employees Software Development Training Program DTE SS This template helps you present information on three stages. You can also present information on Security Threats, Security Vulnerabilities, Security Team using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Checklist To Develop Secure Embedded Systems Mastering Embedded Systems Technology
Checklist To Develop Secure Embedded Systems Mastering Embedded Systems TechnologyThis slide outlines the checklist for building secure embedded systems. The purpose of this slide is to showcase the various tasks that need to be performed to develop secure embedded systems, required actions, responsible person, and status. Present the topic in a bit more detail with this Checklist To Develop Secure Embedded Systems Mastering Embedded Systems Technology. Use it as a tool for discussion and navigation on Operating System Selection, Processor And Peripherals, Prototype Development, System Architecture Design. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Applications For Secure Mobile OS Development
Applications For Secure Mobile OS DevelopmentFollowing slide represents secure mobile operating system apps development for device security management. It further covers methods such as source code encryption, data security provision, latest cryptology, etc. Presenting our set of slides with Applications For Secure Mobile OS Development This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Code Encryption, Security Provision, Cryptography Techniques
-
 Chatbot Security Measures For Different Development Stages
Chatbot Security Measures For Different Development StagesThis slide shows information regarding various security measures that organizations should adopt for different stages of chatbot development. These measures include deploying anti-virus, conducting threat modelling, performing static analysis, etc. Presenting our set of slides with Chatbot Security Measures For Different Development Stages. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Intial Phase, Design And Architecture, Development And Coding.
-
 Organizational Physical Security Development Techniques
Organizational Physical Security Development TechniquesThis slide highlights various techniques to enhance physical security environment by providing real-time tracking and monitoring of activities. The different measures are access control systems, surveillance cameras, detection systems, etc. Introducing our premium set of slides with Organizational Physical Security Development Techniques. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Control Systems, Surveillance Cameras, Detection Systems, Security Personnel. So download instantly and tailor it with your information.
-
 Employee Development Training Icon To Enhance On Site Security
Employee Development Training Icon To Enhance On Site SecurityIntroducing our premium set of slides with Employee Development Training Icon To Enhance On Site Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Employee Development Training, Icon, Enhance Site Security. So download instantly and tailor it with your information.
-
 Develop Security Token Offering Plan Ultimate Guide Smart BCT SS V
Develop Security Token Offering Plan Ultimate Guide Smart BCT SS VThe following slide depicts sample security token offering STO plan to enable fundraising and crowd funding activities. It includes elements such as number of tokens, percentage allocated to public, private investors, pre-sale participants, project teams, reserve funds, etc. Introducing Develop Security Token Offering Plan Ultimate Guide Smart BCT SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Key Elements, Completion Tokenization Process, Token Allocation, using this template. Grab it now to reap its full benefits.
-
 Major Challenges In Future Development Of Security Token Ultimate Guide Smart BCT SS V
Major Challenges In Future Development Of Security Token Ultimate Guide Smart BCT SS VThe following slide showcases the major issues in future development of security tokens to boost early stage adoption. It includes elements such as no uniformity, legal protection, regulations, manual processes, valuation, anti-money laundering, etc. Introducing Major Challenges In Future Development Of Security Token Ultimate Guide Smart BCT SS V to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Manual Process, Valuation, Anti Money Laundering, using this template. Grab it now to reap its full benefits.
-
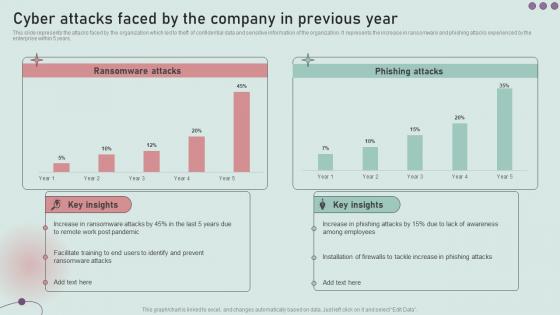 Cyber Attacks Faced By The Company In Previous Year Development And Implementation Of Security
Cyber Attacks Faced By The Company In Previous Year Development And Implementation Of SecurityThis slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Present the topic in a bit more detail with this Cyber Attacks Faced By The Company In Previous Year Development And Implementation Of Security. Use it as a tool for discussion and navigation on Ransomware Attacks, Phishing Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure agile development diagram presentation images
Secure agile development diagram presentation imagesPresenting secure agile development diagram presentation images. This is a secure agile development diagram presentation images. This is a six stage process. The stages in this process are testing, architecture, quality assurance, synthesis, design, analysis.
-
 Conducting Cyber Security Gap Analysis Of Organization Developing Cyber Security Awareness Training
Conducting Cyber Security Gap Analysis Of Organization Developing Cyber Security Awareness TrainingThe purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Present the topic in a bit more detail with this Conducting Cyber Security Gap Analysis Of Organization Developing Cyber Security Awareness Training. Use it as a tool for discussion and navigation on Conducting Cyber, Security Gap, Analysis Of Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determining The Actors Behind Most Significant Cyber Attack Developing Cyber Security Awareness
Determining The Actors Behind Most Significant Cyber Attack Developing Cyber Security AwarenessThe purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present the topic in a bit more detail with this Determining The Actors Behind Most Significant Cyber Attack Developing Cyber Security Awareness. Use it as a tool for discussion and navigation on Determining The Actors, Behind Most Significant, Cyber Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 How To Overcome The Security Awareness Training Program Challenges Developing Cyber Security Awareness
How To Overcome The Security Awareness Training Program Challenges Developing Cyber Security AwarenessThe purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. Deliver an outstanding presentation on the topic using this How To Overcome The Security Awareness Training Program Challenges Developing Cyber Security Awareness. Dispense information and present a thorough explanation of Security Awareness, Training Program, Challenges using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Statistics Showing The Impact Of Security Awareness Training Software Developing Cyber Security
Key Statistics Showing The Impact Of Security Awareness Training Software Developing Cyber SecurityDeliver an outstanding presentation on the topic using this Key Statistics Showing The Impact Of Security Awareness Training Software Developing Cyber Security. Dispense information and present a thorough explanation of Key Statistics, Showing The Impact, Security Awareness, Training Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPI Dashboard To Monitor Cyber Security Performance Management Developing Cyber Security Awareness
KPI Dashboard To Monitor Cyber Security Performance Management Developing Cyber Security AwarenessThe purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. Deliver an outstanding presentation on the topic using this KPI Dashboard To Monitor Cyber Security Performance Management Developing Cyber Security Awareness. Dispense information and present a thorough explanation of KPI Dashboard, Monitor Cyber Security, Performance Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.




