Powerpoint Templates and Google slides for Cybersecurity Attacks
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Blockchain And Cybersecurity Overview Of Blockchain 51 Percent Attack With Workflow BCT SS V
Blockchain And Cybersecurity Overview Of Blockchain 51 Percent Attack With Workflow BCT SS VThe following slide showcases brief introduction of 51percent attack to analyze hashing power of cryptocurrency users. It includes elements such at mining faster rate, malicious user, along with its workflow, etc. Present the topic in a bit more detail with this Blockchain And Cybersecurity Overview Of Blockchain 51 Percent Attack With Workflow BCT SS V Use it as a tool for discussion and navigation on Public Blockchain, Public Network, Maximum Miners This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Blockchain And Cybersecurity Overview Of Phishing Attack In Blockchain Technology BCT SS V
Blockchain And Cybersecurity Overview Of Phishing Attack In Blockchain Technology BCT SS VThe following slide illustrates brief introduction of phishing attacks impacting blockchian to minimize theft of user data. It includes elements such as sharing personal information, sending fake links through emails, stealing private keys, gaining access to account details, data breach, etc. Introducing Blockchain And Cybersecurity Overview Of Phishing Attack In Blockchain Technology BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Attached Fake Links, Investment Opportunities, Fake Website using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Techniques To Prevent Eclipse Attack And Secure Funds BCT SS V
Blockchain And Cybersecurity Techniques To Prevent Eclipse Attack And Secure Funds BCT SS VThe following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Techniques To Prevent Eclipse Attack And Secure Funds BCT SS V This template helps you present information on Four stages. You can also present information on Increased Node Connections, Deterministic Node Selection, New Node Restrictions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain And Cybersecurity Threats Imposed By Sybil Attack On Blockchain Network BCT SS V
Blockchain And Cybersecurity Threats Imposed By Sybil Attack On Blockchain Network BCT SS VThe following slide highlights major issues faced by users due to Sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51percent attack, etc. Introducing Blockchain And Cybersecurity Threats Imposed By Sybil Attack On Blockchain Network BCT SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Block Users From Network, Foster 51percent Attack, Breach Of Privacy using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Various Types Of Ddos Attacks Impacting Internet Traffic BCT SS V
Blockchain And Cybersecurity Various Types Of Ddos Attacks Impacting Internet Traffic BCT SS VThe following slide showcases various types of denial of service DDoS attack to reduce abnormal traffic and lessen the impact. It includes elements such as volumetric, applications, protocol, fragmentation attacks, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Various Types Of Ddos Attacks Impacting Internet Traffic BCT SS V This template helps you present information on Four stages. You can also present information on Volumetric Attacks, Protocol Attacks, Application Attacks, Fragmentation Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain And Cybersecurity Ways To Minimize 51 Percent Attacks And Optimize Hash Rate BCT SS V
Blockchain And Cybersecurity Ways To Minimize 51 Percent Attacks And Optimize Hash Rate BCT SS VThe following slide illustrates various methods to reduce the impact of 51percent attacks and optimize hash rate. It includes elements such as restriction on single user, constant updates, establishing strong network system, leveraging proof of stake, performing security audits, etc. Introducing Blockchain And Cybersecurity Ways To Minimize 51 Percent Attacks And Optimize Hash Rate BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Single User, Constant Updates, Network System using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Ways To Prevent Blockchain Routing Attacks BCT SS V
Blockchain And Cybersecurity Ways To Prevent Blockchain Routing Attacks BCT SS VThe following slide illustrates some methods to minimize blockchain routing attacks to safeguard network from wrong routing table. It includes elements such as strong passwords, updating firmware, managing access control lists, monitoring logs, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Ways To Prevent Blockchain Routing Attacks BCT SS V This template helps you present information on Four stages. You can also present information on Strong Passwords, Update Firmware, Manage Access Control List using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 5G Cybersecurity Icon For Preventing Digital Attacks
5G Cybersecurity Icon For Preventing Digital AttacksIntroducing our 5G Cybersecurity Icon For Preventing Digital Attacks set of slides. The topics discussed in these slides are Preventing, Digital, Cybersecurity. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cybersecurity Infrastructure Icon To Prevent Malware Attacks
Cybersecurity Infrastructure Icon To Prevent Malware AttacksIntroducing our premium set of slides with Cybersecurity Infrastructure Icon To Prevent Malware Attacks Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cybersecurity Infrastructure, Icon To Prevent, Malware Attacks So download instantly and tailor it with your information.
-
 Type Of Attack Cryptography In Cybersecurity
Type Of Attack Cryptography In CybersecurityThis slide covers various attacks on cybersecurity and provides details about to identity threads on organizations. It includes elements such as chosen plaintext, key, and algorithm, etc. Presenting our set of slides with Type Of Attack Cryptography In Cybersecurity. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Brute Force Attack, Key And Algorithm Attack, Known Plaintext Attack.
-
 Types Of Maritime Cybersecurity Attacks On Sensitive Data
Types Of Maritime Cybersecurity Attacks On Sensitive DataThis slide showcases various types of cybersecurity attacks on sensitive data. The main purpose of this template is to highlight various types of attacks, such as phishing attacks, supply chain attacks, data theft, and IoT device exploitation. Presenting our set of slides with Types Of Maritime Cybersecurity Attacks On Sensitive Data. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on IOT Device Exploitation, Supply Chain Attacks, Phishing Attacks.
-
 Navigating Cybersecurity Challenges On Maritime Attacks
Navigating Cybersecurity Challenges On Maritime AttacksThis slide represents maritime cybersecurity challenges for protecting human lives, securing assets, and maintaining overall stability of industry. It includes bases such as date, victim, location, incident type, and malware. Presenting our well structured Navigating Cybersecurity Challenges On Maritime Attacks The topics discussed in this slide are Victim, Location, Incident Type This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 CTI Cybersecurity Icon To Prevent Malware Infections And Attacks
CTI Cybersecurity Icon To Prevent Malware Infections And AttacksPresenting our set of slides with CTI Cybersecurity Icon To Prevent Malware Infections And Attacks This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on CTI Cybersecurity Icon, Prevent Malware Infections And Attacks
-
 Root Cause Analysis Of IoT Password Attacks Internet Of Things IoT Security Cybersecurity SS
Root Cause Analysis Of IoT Password Attacks Internet Of Things IoT Security Cybersecurity SSThis slide showcases root cause analysis of internet of things IoT password attacks, referable for related businesses. It provides details about cybercriminal, login page, IoT device, video recordings, etc. Increase audience engagement and knowledge by dispensing information using Root Cause Analysis Of IoT Password Attacks Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on two stages. You can also present information on Record Conversation, Password Attack, Cyber Criminal, Root Cause Analysis using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Biometric Authentication Trend Icon To Prevent Cybersecurity Attacks
Biometric Authentication Trend Icon To Prevent Cybersecurity AttacksIntroducing our premium set of slides with Biometric Authentication Trend Icon To Prevent Cybersecurity Attacks. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Biometric Authentication Trend, Icon To Prevent, Cybersecurity Attacks. So download instantly and tailor it with your information.
-
 Modern Trends Increasing Cybersecurity Attacks In Healthcare Industry
Modern Trends Increasing Cybersecurity Attacks In Healthcare IndustryThis slide represents various solutions that help healthcare industry to mitigate cybersecurity risks effectively due to emerging trends. It includes various trends such as rise of telemedicine, increasing adoption of IoT, and utilization of AI and ML systems. Introducing our Modern Trends Increasing Cybersecurity Attacks In Healthcare Industry set of slides. The topics discussed in these slides are Trends, Solutions, Rise Telemedicine. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Impact Of Cyber Attacks On Organizational Operations IT Security Awareness Training Cybersecurity SS
Impact Of Cyber Attacks On Organizational Operations IT Security Awareness Training Cybersecurity SSThis slide represents impact of attacks that are attempted to steal sensitive information in the form of user names, credit card numbers etc. on organizational operations. Increase audience engagement and knowledge by dispensing information using Impact Of Cyber Attacks On Organizational Operations IT Security Awareness Training Cybersecurity SS. This template helps you present information on four stages. You can also present information on Reputational Damage, Stolen Intellectual Property, Operational Disruption, Increased Costs using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Training Plan For Detecting Phishing Attacks IT Security Awareness Training Cybersecurity SS
Training Plan For Detecting Phishing Attacks IT Security Awareness Training Cybersecurity SSThis slide represents details related to training plan to assist employees in detecting phishing attacks. It includes details related to training topics such as general signs of phishing attacks etc. Present the topic in a bit more detail with this Training Plan For Detecting Phishing Attacks IT Security Awareness Training Cybersecurity SS. Use it as a tool for discussion and navigation on Manufactured Rapport Or History, Manufactured Urgency, Sensitive Questions As Standard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Training Plan For Detecting Ransomware Attacks IT Security Awareness Training Cybersecurity SS
Training Plan For Detecting Ransomware Attacks IT Security Awareness Training Cybersecurity SSThis slide represents training plan for detecting to malware that is designed to deny a user or organization access to files on their computer or networks. It includes details related to detection techniques etc. Deliver an outstanding presentation on the topic using this Training Plan For Detecting Ransomware Attacks IT Security Awareness Training Cybersecurity SS. Dispense information and present a thorough explanation of Signature Based Detection, Detection Based On Traffic, Detection By Data Behavior using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Training Plan For Mitigating Ransomware Attacks IT Security Awareness Training Cybersecurity SS
Training Plan For Mitigating Ransomware Attacks IT Security Awareness Training Cybersecurity SSThis slide represents training plan for mitigating malware that is designed to deny a user or organization access to files on their computer or networks. It includes details related to mitigation techniques etc. Introducing Training Plan For Mitigating Ransomware Attacks IT Security Awareness Training Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Managed Detection And Response, Extended Detection And Response, Endpoint Detection And Response, using this template. Grab it now to reap its full benefits.
-
 Training Plan For Preventing Phishing Attacks IT Security Awareness Training Cybersecurity SS
Training Plan For Preventing Phishing Attacks IT Security Awareness Training Cybersecurity SSThis slide represents training plan to assist employees in effectively preventing phishing attacks. It includes details related to training topics such as email communication and hyperlinks etc. Present the topic in a bit more detail with this Training Plan For Preventing Phishing Attacks IT Security Awareness Training Cybersecurity SS. Use it as a tool for discussion and navigation on Report Phishing Attempts, Email Communications And Hyperlinks, Best Practices For Handling Mails. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Intrusion Prevention Potential Attacks Detected And Prevented Cybersecurity SS
Implementing Intrusion Prevention Potential Attacks Detected And Prevented Cybersecurity SSThis slide represents cybersecurity attacks detected and prevented by a network security tool that monitors the network for malicious activities, including DDoS attacks, ARP spoofing, and IP fragmentation. Introducing Implementing Intrusion Prevention Potential Attacks Detected And Prevented Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Distributed Denial Of Service, Address Resolution Protocol ARP Spoofing, IP Fragmentation, using this template. Grab it now to reap its full benefits.
-
 AI Supply Chain Automation Icon To Prevent Cybersecurity Attacks
AI Supply Chain Automation Icon To Prevent Cybersecurity AttacksPresenting our well structured AI Supply Chain Automation Icon To Prevent Cybersecurity Attacks. The topics discussed in this slide are AI Supply Chain Automation Icon, Prevent Cybersecurity Attacks. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Steps To Prevent Supply Chain Cybersecurity Attacks By Companies
Steps To Prevent Supply Chain Cybersecurity Attacks By CompaniesThis slide represents steps that assist companies to prevent supply chain cybersecurity attacks by enhancing risk management systems. It includes steps such as prioritizing third-party risk management, identifying supply chain vulnerabilities, etc. Presenting our set of slides with name Steps To Prevent Supply Chain Cybersecurity Attacks By Companies. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Prioritize Third-Party Risk Management, Identify Supply Chain Vulnerabilities, Engage Suppliers.
-
 Training Plan For Detecting Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SS
Training Plan For Detecting Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SSThis slide provides details about the training plan designed to help employees detect phishing attacks. It covers training topics such as identifying general signs of phishing attacks, signs of phishing in email etc.Present the topic in a bit more detail with this Training Plan For Detecting Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SS. Use it as a tool for discussion and navigation on Training Sessions, Timeline, Trainer, Training Topic. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Training Plan For Preventing Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SS
Training Plan For Preventing Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines a training plan to help employees effectively prevent phishing attacks. It covers topics such as email communication, blocking popups and ads, report phishing attempts etc.Deliver an outstanding presentation on the topic using this Training Plan For Preventing Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Training Topics, Training Method, Expected Completion Date, Trainer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
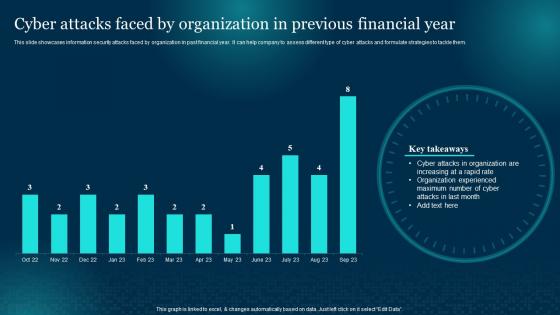 Cyber Attacks Faced By Organization Previous Cybersecurity Risk Analysis And Management Plan
Cyber Attacks Faced By Organization Previous Cybersecurity Risk Analysis And Management PlanThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Deliver an outstanding presentation on the topic using this Cyber Attacks Faced By Organization Previous Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Organization, Financial Year, Experienced using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
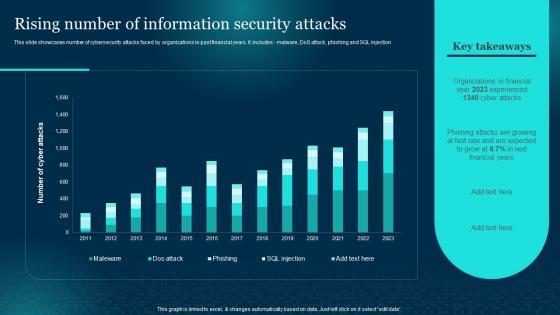 Rising Number Of Information Security Attacks Cybersecurity Risk Analysis And Management Plan
Rising Number Of Information Security Attacks Cybersecurity Risk Analysis And Management PlanThis slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection Present the topic in a bit more detail with this Rising Number Of Information Security Attacks Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Information, Security Attacks, Organizations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Faced By Organization In Previous Financial Year Formulating Cybersecurity Plan
Cyber Attacks Faced By Organization In Previous Financial Year Formulating Cybersecurity PlanThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Deliver an outstanding presentation on the topic using this Cyber Attacks Faced By Organization In Previous Financial Year Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Cyber Attacks, Organization, Financial Year using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Rising Number Of Information Security Attacks Formulating Cybersecurity Plan
Rising Number Of Information Security Attacks Formulating Cybersecurity PlanThis slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection. Deliver an outstanding presentation on the topic using this Rising Number Of Information Security Attacks Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Rising Number, Information Security, Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Assessment Program Cyber Attacks Faced By Organization
Cybersecurity Risk Assessment Program Cyber Attacks Faced By OrganizationThis slide provides information regarding the number of cyber attacks faced by the organization and its impact on IT operations and system downtime. It also provides details of percentage rise in such attacks since last month. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Cyber Attacks Faced By Organization. Use it as a tool for discussion and navigation on Cyber Attacks, IT Operations, System Downtime. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels
Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk LevelsThe slide represents the dashboard for tracking cyber attack risk levels. It includes information regarding the multiple threat agents, attack methods, preventive controls along with details of risk score and infected systems. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels. Dispense information and present a thorough explanation of Infrastructure Controls, Preventive Controls, Detective Controls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Assessment Program Dashboard To Monitor Cyber Attack Incidents
Cybersecurity Risk Assessment Program Dashboard To Monitor Cyber Attack IncidentsThis slide indicates the dashboard to monitor cyber attacks on IT assets of the firm. It includes information regarding the total cyber attack incidents both month and day wise along with the details of threat class, overall risk factor and top vulnerabilities. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Dashboard To Monitor Cyber Attack Incidents. Use it as a tool for discussion and navigation on Dashboard To Monitor, Cyber Attack Incidents, Vulnerabilities, Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Assessment Program Summary Of Key Cyber Attacks Occurred
Cybersecurity Risk Assessment Program Summary Of Key Cyber Attacks OccurredThis slide shows the summary of key of cybers attacks occurred in organization such as phishing, malware attack, denial of service, SQL injections, identity thefts. It also contains details of the cyber attacker origin such as inadvertent actors, malicious insiders. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Summary Of Key Cyber Attacks Occurred. Use it as a tool for discussion and navigation on Cyber Attacks Occurred, Financial Loss, Cyber Attack Origins. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ukraine and russia cyber warfare it how to protect yourself from ongoing cybersecurity attacks
Ukraine and russia cyber warfare it how to protect yourself from ongoing cybersecurity attacksThis slide talks about how to protect yourself from ongoing Russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Introducing Ukraine And Russia Cyber Warfare It How To Protect Yourself From Ongoing Cybersecurity Attacks to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Resources, Antivirus, Software, using this template. Grab it now to reap its full benefits.
-
 Cyber Attacks On Ukraine Cybersecurity Risks Of An Escalating Russia Ukraine Conflict
Cyber Attacks On Ukraine Cybersecurity Risks Of An Escalating Russia Ukraine ConflictThis slide represents the cybersecurity risks associated with Russia and Ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions. Introducing Cyber Attacks On Ukraine Cybersecurity Risks Of An Escalating Russia Ukraine Conflict to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Infrastructure, Cybersecurity, Potential, Cyberattacks, Financial, using this template. Grab it now to reap its full benefits.
-
 Cyber Attacks On Ukraine How To Protect Yourself From Ongoing Cybersecurity
Cyber Attacks On Ukraine How To Protect Yourself From Ongoing CybersecurityThis slide talks about how to protect yourself from ongoing Russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Increase audience engagement and knowledge by dispensing information using Cyber Attacks On Ukraine How To Protect Yourself From Ongoing Cybersecurity. This template helps you present information on six stages. You can also present information on Suspicious, Individuals, Adequately, Programmed using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Wiper Malware Attack Cybersecurity Risks Of An Escalating Russia
Wiper Malware Attack Cybersecurity Risks Of An Escalating RussiaThis slide represents the cybersecurity risks associated with Russia and Ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions. Introducing Wiper Malware Attack Cybersecurity Risks Of An Escalating Russia to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Risks Of An Escalating Russia Ukraine Conflict, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Risk Analysis And Management Plan Cyber Attacks Faced By Different Departments
Cybersecurity Risk Analysis And Management Plan Cyber Attacks Faced By Different DepartmentsThis slide showcases information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks Present the topic in a bit more detail with this Cybersecurity Risk Analysis And Management Plan Cyber Attacks Faced By Different Departments. Use it as a tool for discussion and navigation on Departments, Information, Cyber Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial Impact Of Information Security Attacks Cybersecurity Risk Analysis And Management Plan
Financial Impact Of Information Security Attacks Cybersecurity Risk Analysis And Management PlanThis slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type Present the topic in a bit more detail with this Financial Impact Of Information Security Attacks Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Financial, Information, Organizations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Attacks Faced By Organization Cybersecurity Risk Analysis And Management Plan
Information Security Attacks Faced By Organization Cybersecurity Risk Analysis And Management PlanThis slide showcases most common information attacks faced by organization. It includes - malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack Increase audience engagement and knowledge by dispensing information using Information Security Attacks Faced By Organization Cybersecurity Risk Analysis And Management Plan. This template helps you present information on six stages. You can also present information on Information, Organization, Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Risks Of An Escalating Russia Ukraine Conflict String Of Cyber Attacks Against
Cybersecurity Risks Of An Escalating Russia Ukraine Conflict String Of Cyber Attacks AgainstThis slide represents the cybersecurity risks associated with russia and ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions. Introducing Cybersecurity Risks Of An Escalating Russia Ukraine Conflict String Of Cyber Attacks Against to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Capabilities, Economic Warfare, Cybersecurity, using this template. Grab it now to reap its full benefits.
-
 How To Protect Yourself From Ongoing Cybersecurity Attacks String Of Cyber Attacks
How To Protect Yourself From Ongoing Cybersecurity Attacks String Of Cyber AttacksThis slide talks about how to protect yourself from ongoing russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Introducing How To Protect Yourself From Ongoing Cybersecurity Attacks String Of Cyber Attacks to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Choose A Strong Password, Check Your Credit, Unique Password, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Attack Vector Analysis For Effective Awareness Training
Cybersecurity Attack Vector Analysis For Effective Awareness TrainingThis slide covers cybersecurity attack vector analysis for effective awareness training. It involves malware, phishing, denial of service, poor encryption, device misconfiguration and cross site scripting. Introducing our premium set of slides with Cybersecurity Attack Vector Analysis For Effective Awareness Training. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Attack Vector, Examples, Objective, Problem Identifier. So download instantly and tailor it with your information.
-
 Cyber Attacks Faced By Different Departments Formulating Cybersecurity Plan
Cyber Attacks Faced By Different Departments Formulating Cybersecurity PlanThis slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Present the topic in a bit more detail with this Cyber Attacks Faced By Different Departments Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Marketing Department, Operations Department, Accounts Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial Impact Of Information Security Attacks Formulating Cybersecurity Plan
Financial Impact Of Information Security Attacks Formulating Cybersecurity PlanThis slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type. Present the topic in a bit more detail with this Financial Impact Of Information Security Attacks Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Financial Impact, Information, Security Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Attacks Faced By Organization Formulating Cybersecurity Plan
Information Security Attacks Faced By Organization Formulating Cybersecurity PlanThis slide showcases most common information attacks faced by organization. It includes malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack. Present the topic in a bit more detail with this Information Security Attacks Faced By Organization Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Malware, Phishing, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing The Various Security Incidents And Attacks Cybersecurity Incident And Vulnerability
Addressing The Various Security Incidents And Attacks Cybersecurity Incident And VulnerabilityPurpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques. Increase audience engagement and knowledge by dispensing information using Addressing The Various Security Incidents And Attacks Cybersecurity Incident And Vulnerability. This template helps you present information on three stages. You can also present information on Traditional IT Security Incidents, Cyber Security Attacks, Common Techniques using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Classifying Various Security Issues And Attacks Cybersecurity Incident And Vulnerability
Classifying Various Security Issues And Attacks Cybersecurity Incident And VulnerabilityPurpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks. Present the topic in a bit more detail with this Classifying Various Security Issues And Attacks Cybersecurity Incident And Vulnerability. Use it as a tool for discussion and navigation on Data Breaches, Data Loss, Risk Profiling. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Classifying Various Security Issues And Attacks Upgrading Cybersecurity With Incident Response Playbook
Classifying Various Security Issues And Attacks Upgrading Cybersecurity With Incident Response PlaybookPurpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks. Deliver an outstanding presentation on the topic using this Classifying Various Security Issues And Attacks Upgrading Cybersecurity With Incident Response Playbook. Dispense information and present a thorough explanation of Classifying, Steganography, Classification using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategy To Minimize Cyber Attacks Framework For Cybersecurity Risk Management
Strategy To Minimize Cyber Attacks Framework For Cybersecurity Risk ManagementThis slide indicates the framework for cybersecurity risk management. The major sub components of model are data sources, cyber intelligence and monitoring, threat and vulnerabilities, executive board and IT governance. Present the topic in a bit more detail with this Strategy To Minimize Cyber Attacks Framework For Cybersecurity Risk Management. Use it as a tool for discussion and navigation on Information Sharing, Components Of Framework, Framework For Cybersecurity, Risk Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategy To Minimize Cyber Attacks Multistep Approach To Conduct Cybersecurity Risk Assessment
Strategy To Minimize Cyber Attacks Multistep Approach To Conduct Cybersecurity Risk AssessmentThis slide indicates the multistep approach to conduct cybersecurity risk assessment in business organization. The major steps of process are risk identification, quantification, evaluation, mitigation and monitoring. Introducing Strategy To Minimize Cyber Attacks Multistep Approach To Conduct Cybersecurity Risk Assessment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Risk Identification, Risk Mapping, Risk Evaluation, Risk Mitigation And Monitoring, using this template. Grab it now to reap its full benefits.
-
 Strategy To Minimize Cyber Attacks Need Of Cybersecurity Program For Organization
Strategy To Minimize Cyber Attacks Need Of Cybersecurity Program For OrganizationThis slide depicts the value that a cybersecurity program with risk assessment module add to organization in terms of increased awareness of organization security landscape, identification of system vulnerabilities, actionable and prioritized list of cybersecurity risks and mitigation plan to tackle future threats. Increase audience engagement and knowledge by dispensing information using Strategy To Minimize Cyber Attacks Need Of Cybersecurity Program For Organization. This template helps you present information on four stages. You can also present information on Organization Security Landscape, Actionable And Prioritized, List Of Cybersecurity Risks, Identification Of System Vulnerabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategy To Minimize Cyber Attacks NIST Cybersecurity Framework With Subcategories
Strategy To Minimize Cyber Attacks NIST Cybersecurity Framework With SubcategoriesThis slide represents the NIST cybersecurity framework with subcategories. It also contains information regarding the software which fulfill multiple compliance requirements of NIST cybersecurity framework. Introducing Strategy To Minimize Cyber Attacks NIST Cybersecurity Framework With Subcategories to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on NIST Cybersecurity, Framework With Subcategories, Contains Information, Compliance Requirements, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Gap Analysis Representing Current Situation Of Cybersecurity Incident
Cyber Security Attacks Response Gap Analysis Representing Current Situation Of Cybersecurity IncidentThis slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Present the topic in a bit more detail with this Cyber Security Attacks Response Gap Analysis Representing Current Situation Of Cybersecurity Incident. Use it as a tool for discussion and navigation on Gap Analysis, Representing Current Situation, Cybersecurity Incident, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Best Practices For Cybersecurity Incident Management
Cyber Security Attacks Response Plan Best Practices For Cybersecurity Incident ManagementThis slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Introducing Cyber Security Attacks Response Plan Best Practices For Cybersecurity Incident Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Incident Management Process, Incident Management Plan, Responsibilities, Team Members, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Plan Five Phases Of Cybersecurity Incident Management
Cyber Security Attacks Response Plan Five Phases Of Cybersecurity Incident ManagementThis slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Introducing Cyber Security Attacks Response Plan Five Phases Of Cybersecurity Incident Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Plan And Prepare, Post Incident Activity, Assess And Design, Incident Management, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Plan Impact Of Cybersecurity Incidents On Organization
Cyber Security Attacks Response Plan Impact Of Cybersecurity Incidents On OrganizationThis slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Attacks Response Plan Impact Of Cybersecurity Incidents On Organization. This template helps you present information on six stages. You can also present information on Reputational Damage, Stolen Intellectual Property, Altered Business Practices, Operational Disruption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Risk Assessment Program Key Approaches To Minimize Cyber Attacks Risks
Cybersecurity Risk Assessment Program Key Approaches To Minimize Cyber Attacks RisksThis slide indicates the key approaches to minimize the risk associated with cyber attacks. The approaches discussed are update and upgrade outdated software, control accounts access, introduce signed software execution policies, regularly track network intrusions and use multifactor authentication. Increase audience engagement and knowledge by dispensing information using Cybersecurity Risk Assessment Program Key Approaches To Minimize Cyber Attacks Risks. This template helps you present information on five stages. You can also present information on Control Accounts Access, Multifactor Authentication, Track Network Intrusions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Risk Assessment Program Major Cyber Attacks Faced By Organization
Cybersecurity Risk Assessment Program Major Cyber Attacks Faced By OrganizationThis purpose of this slide is to showcase the major cyber attacks faced by business organization. The key attacks listed are phishing, malware attack, denial of service attacks, SQL injections, and ransomware. It also provides details regarding the major IT assets impacted and primary objective of each of the attacks. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Major Cyber Attacks Faced By Organization. Use it as a tool for discussion and navigation on Phishing, Malware Attack, Denial Of Service Attack, Ransomware. This template is free to edit as deemed fit for your organization. Therefore download it now.





