Powerpoint Templates and Google slides for Cybersecurity Attacks
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Overview Of Active And Passive Attacks In Cybersecurity Training PPT
Overview Of Active And Passive Attacks In Cybersecurity Training PPTPresenting Active and Passive Attacks in Cybersecurity. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Denial Of Service Attack In Cybersecurity Training Ppt
Denial Of Service Attack In Cybersecurity Training PptPresenting Denial of Service Attack in Cybersecurity. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
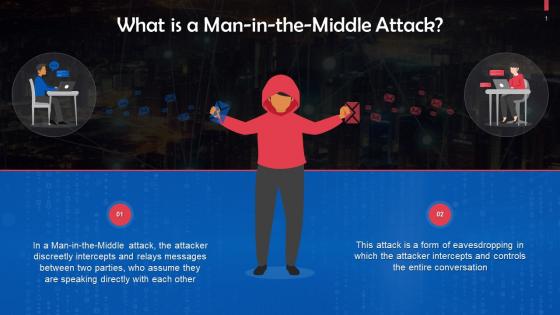 Man In The Middle Attacks In Cybersecurity Training Ppt
Man In The Middle Attacks In Cybersecurity Training PptPresenting Man in the Middle Attacks in Cybersecurity. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
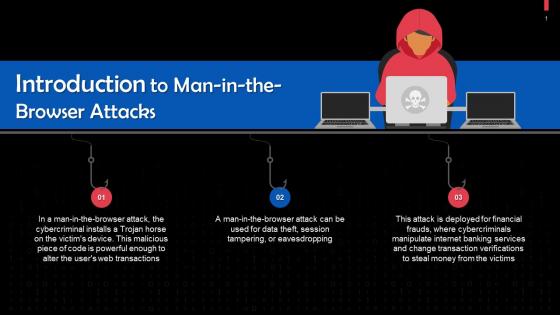 Man In The Browser Attacks In Cybersecurity Training Ppt
Man In The Browser Attacks In Cybersecurity Training PptPresenting Man in the Browser Attacks in Cybersecurity. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Spyware Cyber Attack In Cybersecurity Training Ppt
Spyware Cyber Attack In Cybersecurity Training PptPresenting Spyware Cyber Attack in Cybersecurity. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Social Engineering Attacks In Cybersecurity Training Ppt
Social Engineering Attacks In Cybersecurity Training PptPresenting Social Engineering Attacks in Cybersecurity. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Ransomware Attacks In Cybersecurity Training Ppt
Ransomware Attacks In Cybersecurity Training PptPresenting Ransomware Attacks in Cybersecurity. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Malvertising Cyber Attacks In Cybersecurity Training Ppt
Malvertising Cyber Attacks In Cybersecurity Training PptPresenting Malvertising Cyber Attacks in Cybersecurity. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Cyber Attack In Cybersecurity Training Ppt
Cyber Attack In Cybersecurity Training PptPresenting Cyber Attack in Cybersecurity. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Password Spraying Attacks In Cybersecurity Training Ppt
Password Spraying Attacks In Cybersecurity Training PptPresenting Password Spraying Attacks in Cybersecurity. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Active And Passive Attacks In Cybersecurity Training Ppt
Active And Passive Attacks In Cybersecurity Training PptPresenting Active and Passive Attacks in Cybersecurity This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 IoT Password Attack Prevention Strategies Improving IoT Device Cybersecurity IoT SS
IoT Password Attack Prevention Strategies Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to highlight Internet of Things IoT password attack prevention measures. The techniques outlined in slide are limit public information, verifying the source, and no sharing of password. Deliver an outstanding presentation on the topic using this IoT Password Attack Prevention Strategies Improving IoT Device Cybersecurity IoT SS. Dispense information and present a thorough explanation of Information, Verify, Password using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Most Common Types Of IoT Botnet Attacks Improving IoT Device Cybersecurity IoT SS
Most Common Types Of IoT Botnet Attacks Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase various types of Internet of Things IoT botnet attacks. Bruce force attack, Phishing, Device Bricking, and Cryptocurrency Mining are the most common types which are outlined in slide. Present the topic in a bit more detail with this Most Common Types Of IoT Botnet Attacks Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Phishing, Bricking, Mining. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Most Common Types Of Ransomware Attack Improving IoT Device Cybersecurity IoT SS
Most Common Types Of Ransomware Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline various types of ransomware attack which can cause financial loss to company. It covers information about Scareware, Screen Lockers, DDoS Distributed Denial of Service Extortion, Encrypting Ransomware, etc. Deliver an outstanding presentation on the topic using this Most Common Types Of Ransomware Attack Improving IoT Device Cybersecurity IoT SS. Dispense information and present a thorough explanation of Scareware, Lockers, Mobile using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ransomware Attack Volume Across Globe Improving IoT Device Cybersecurity IoT SS
Ransomware Attack Volume Across Globe Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to display graphical representation of ransomware attack volume worldwide. Information covered in this slide is related to number of attack from 2015 2022 along with key intakes. Deliver an outstanding presentation on the topic using this Ransomware Attack Volume Across Globe Improving IoT Device Cybersecurity IoT SS. Dispense information and present a thorough explanation of Globe, Attacks, Developing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Statistics Highlighting IoT Attacks Faced Improving IoT Device Cybersecurity IoT SS
Statistics Highlighting IoT Attacks Faced Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to display graphical representation of various IoT attacks faced by companies. The slide covers information about cyber attacks such as network scan, remote code execution, command injection, buffer overflow, worm, ransomware, botnet, password, phishing, etc. Present the topic in a bit more detail with this Statistics Highlighting IoT Attacks Faced Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Statistics, Injection, Execution. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Various Types Of Dos Attack Improving IoT Device Cybersecurity IoT SS
Various Types Of Dos Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline multiple types of Denial of Service Dos attack. It covers information about application layer, buffer overflow, DNS Domain Name Server amplification, and ping of death. Deliver an outstanding presentation on the topic using this Various Types Of Dos Attack Improving IoT Device Cybersecurity IoT SS. Dispense information and present a thorough explanation of Application, Layer, Death using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Various Types Of IoT Password Attack Improving IoT Device Cybersecurity IoT SS
Various Types Of IoT Password Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to delineate multiple types of Internet of Things IoT password attack. Phishing, Dictionary Attack, Credential Stuffing, and Keyloggers are the major attacks which are mentioned in slide. Present the topic in a bit more detail with this Various Types Of IoT Password Attack Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Phishing, Dictionary, Credential. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Blockchain And Cybersecurity Various Types Of Crypto Phishing Attacks BCT SS V
Blockchain And Cybersecurity Various Types Of Crypto Phishing Attacks BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Introducing Blockchain And Cybersecurity Various Types Of Crypto Phishing Attacks BCT SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing, Whaling Phishing, Clone Phishing using this template. Grab it now to reap its full benefits.
-
 Types Of Cybersecurity Attacks In Education
Types Of Cybersecurity Attacks In EducationThis slide depicts the types of cybersecurity attacks in education. This slide aims to help education businesses adopt suitable measures to prevent cyberattacks. It includes a graphical analysis and key insights Introducing our Types Of Cybersecurity Attacks In Education set of slides. The topics discussed in these slides are Cyberattacks In Education, Education Is Phishing. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Financial Impact Of Endpoint Security Attacks Building Next Generation Endpoint Security Cybersecurity SS
Financial Impact Of Endpoint Security Attacks Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases financial impact of endpoint attacks, which can help organizations assess their costs and plan recovery strategies of system downtime, information assets, etc.Deliver an outstanding presentation on the topic using this Financial Impact Of Endpoint Security Attacks Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Zero Day, Polymorphic Malware, Malicious Code using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Attacks On Employee Mobile Devices Mobile Device Security Cybersecurity SS
Cyber Attacks On Employee Mobile Devices Mobile Device Security Cybersecurity SSThis slide showcases cyber threats faced by workforce on mobile devices. It highlights data regarding malware, phishing attacks, ransomware etc. Present the topic in a bit more detail with this Cyber Attacks On Employee Mobile Devices Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Awareness Training, Weak Security Measures This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Decrease In Cyber Attacks On Different Mobile Devices Mobile Device Security Cybersecurity SS
Decrease In Cyber Attacks On Different Mobile Devices Mobile Device Security Cybersecurity SSThis slide showcases decline in cyber attacks after implementation of mobile security techniques. It highlights decrease in cyber attacks on android and iOS devices Deliver an outstanding presentation on the topic using this Decrease In Cyber Attacks On Different Mobile Devices Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Security Attacks, Mobile Devices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mobile Cyber Attacks Occurrence Globally Mobile Device Security Cybersecurity SS
Mobile Cyber Attacks Occurrence Globally Mobile Device Security Cybersecurity SSThis slide showcases number of cyber attacks faced by mobile users around the world. It highlights data regarding attacks faced in last three years Deliver an outstanding presentation on the topic using this Mobile Cyber Attacks Occurrence Globally Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Fingerprint Scanner, Facial Recognition, Voice Recognition using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mobile Malware Attacks By Country Share Mobile Device Security Cybersecurity SS
Mobile Malware Attacks By Country Share Mobile Device Security Cybersecurity SSThis slide showcases percentage share of mobile malware attacks faced in different countries. It highlights share of China, Iran, Yemen, Switzerland, Kenya etc. Present the topic in a bit more detail with this Mobile Malware Attacks By Country Share Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Purpose, Scope, Loss And Theft This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Password Authentication For Protection Against Brute Force Attacks Cybersecurity SS
Password Authentication For Protection Against Brute Force Attacks Cybersecurity SSThis slide outlines strategies for protecting networks from brute-force attacks, including password authentication methods such as limiting the number of login attempts and password requests etc.Deliver an outstanding presentation on the topic using this Password Authentication For Protection Against Brute Force Attacks Cybersecurity SS. Dispense information and present a thorough explanation of Password Authentication, Solutions, Login Attempts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Potential Impact Of Mitigating Network Vulnerabilities On Cyber Attacks Cybersecurity SS
Potential Impact Of Mitigating Network Vulnerabilities On Cyber Attacks Cybersecurity SSThis slide shows the impact of strategies implemented by IT and security professionals to prevent and mitigate network vulnerabilities, including phishing attacks, malware attacks, insider attacks and software vulnerabilities.Deliver an outstanding presentation on the topic using this Potential Impact Of Mitigating Network Vulnerabilities On Cyber Attacks Cybersecurity SS. Dispense information and present a thorough explanation of Cyber Attacks, Secure Passwords, Compliant Monitoring And Auditing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tools To Address Supply Chain Cybersecurity Attacks For Data Protection
Tools To Address Supply Chain Cybersecurity Attacks For Data ProtectionThis slide graphically represents use of various tools and approaches that assist companies in addressing various supply chain cybersecurity attacks and optimizing data protection. It includes tools such as IT vendor risk management tools, supply chain risk management tools, etc. Presenting our well structured Tools To Address Supply Chain Cybersecurity Attacks For Data Protection. The topics discussed in this slide are Audits Of Suppliers, Manufacturers, Logistics Partners. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Types Of Cyber Attacks Faced By How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS
Types Of Cyber Attacks Faced By How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SSThis slide showcases various types of cyber attacks that significantly damage the organization resources and reputation. Different types of attacks faced are Malware, Phishing, Man in middle attack, SQL injection etc. Introducing Types Of Cyber Attacks Faced By How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Software, Financial, Results, using this template. Grab it now to reap its full benefits.
-
 Healthcare Cybersecurity Icon For Protection Against Phishing Attacks
Healthcare Cybersecurity Icon For Protection Against Phishing AttacksIntroducing our Healthcare Cybersecurity Icon For Protection Against Phishing Attacks set of slides. The topics discussed in these slides are Healthcare Cybersecurity Icon, Protection Against Phishing Attacks. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Healthcare Cybersecurity Plan For Phishing Attacks
Healthcare Cybersecurity Plan For Phishing AttacksThis slide presents healthcare cybersecurity plan for phishing attacks, helpful in making employees and department vigilant against threats at early stage. It includes strategies such as identifying phishing email attacks, investing in cybersecurity trainings and implementing technical safeguards Presenting our set of slides with Healthcare Cybersecurity Plan For Phishing Attacks. This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Phishing Email Tricks, Cybersecurity Trainings, Technical Safeguards.
-
 How Does Dos Attack Work Improving IoT Device Cybersecurity IoT SS
How Does Dos Attack Work Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase working of Denial of Service DoS attack working. It covers information about target identification, exploiting weaknesses, target flooding, exhausting system capabilities Introducing How Does Dos Attack Work Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Target, Exploiting, Flooding, using this template. Grab it now to reap its full benefits.
-
 How Does IoT Botnet Attack Work Improving IoT Device Cybersecurity IoT SS
How Does IoT Botnet Attack Work Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase working of Internet of Things IoT botnet attack. The botnet attack begins with scanning vulnerable IoT devices, gaining access to IoT devices, malware installation, botnet expansion, and conducting malicious activities. Increase audience engagement and knowledge by dispensing information using How Does IoT Botnet Attack Work Improving IoT Device Cybersecurity IoT SS. This template helps you present information on five stages. You can also present information on Devices, Gaining, Installation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Does IoT Password Attack Work Improving IoT Device Cybersecurity IoT SS
How Does IoT Password Attack Work Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase working of Internet of Things IoT password attack. It covers information about gaining control of IoT device, records conversation, collects private video recordings, sends sensitive data to malicious user, etc. Present the topic in a bit more detail with this How Does IoT Password Attack Work Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Cybercriminal, Server, Default. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 How Does Ransomware Attack Work Improving IoT Device Cybersecurity IoT SS
How Does Ransomware Attack Work Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase the working of ransomware attack. The attack begins with installing malware in IoT devices, identifying files stored on local devices, establishing key exchange with control server, covering instruction files, etc. Increase audience engagement and knowledge by dispensing information using How Does Ransomware Attack Work Improving IoT Device Cybersecurity IoT SS. This template helps you present information on seven stages. You can also present information on Devices, Exchange, Covers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Introduction To Denial Of Service Dos Attack Improving IoT Device Cybersecurity IoT SS
Introduction To Denial Of Service Dos Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to provide glimpse of Denial of Service DoS attack. It also covers information about signs of DoS attack such as poor network performance of IoT devices, specific website doesnt opened, increasing volume of email spam, etc. Increase audience engagement and knowledge by dispensing information using Introduction To Denial Of Service Dos Attack Improving IoT Device Cybersecurity IoT SS. This template helps you present information on four stages. You can also present information on Accessing, Website, Increasing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Introduction To IoT Botnet Attack And Its Improving IoT Device Cybersecurity IoT SS
Introduction To IoT Botnet Attack And Its Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to provide glimpse of Internet of Things IoT botnet attack along with its features. The features mentioned in slide are related to taking advantages of security vulnerabilities, issuing instructions through centralized command, etc. Increase audience engagement and knowledge by dispensing information using Introduction To IoT Botnet Attack And Its Improving IoT Device Cybersecurity IoT SS. This template helps you present information on five stages. You can also present information on Vulnerabilities, Compromised, Centralized using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Introduction To IoT Password Attack And Improving IoT Device Cybersecurity IoT SS
Introduction To IoT Password Attack And Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to provide glimpse of Internet of Things IoT attack and its major characteristics. It covers information about using multiple software, using pre built default wordlist, using compromised login credentials, scanning for open port, etc. Increase audience engagement and knowledge by dispensing information using Introduction To IoT Password Attack And Improving IoT Device Cybersecurity IoT SS. This template helps you present information on seven stages. You can also present information on Software, Credentials, Technique using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Introduction To Ransomware Attack And Improving IoT Device Cybersecurity IoT SS
Introduction To Ransomware Attack And Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to provide glimpse of ransomware attack which can cause deny user to access to files on their system. It also covers information abut ransomware attack features such as focusing on industrial control system, smart home devices, etc. Present the topic in a bit more detail with this Introduction To Ransomware Attack And Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Industrial, Software, Functionalities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Access Points To Malicious Attackers Improving IoT Device Cybersecurity IoT SS
IoT Access Points To Malicious Attackers Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to delineate various Internet of Things IoT access points that can be accessed by hackers. The slide covers information about edge computing, communication network, and cloud computing. Increase audience engagement and knowledge by dispensing information using IoT Access Points To Malicious Attackers Improving IoT Device Cybersecurity IoT SS. This template helps you present information on four stages. You can also present information on Devices, Hardware, Commonly using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IoT Cyber Attack Scenario In Self Automated Improving IoT Device Cybersecurity IoT SS
IoT Cyber Attack Scenario In Self Automated Improving IoT Device Cybersecurity IoT SSPresent the topic in a bit more detail with this IoT Cyber Attack Scenario In Self Automated Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Systems, Updates, Connectivity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Cyber Attack Scenario In Smart Home Improving IoT Device Cybersecurity IoT SS
IoT Cyber Attack Scenario In Smart Home Improving IoT Device Cybersecurity IoT SSDeliver an outstanding presentation on the topic using this IoT Cyber Attack Scenario In Smart Home Improving IoT Device Cybersecurity IoT SS. Dispense information and present a thorough explanation of Identification, Temperature, Identity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mirai Botnet Attack Caused By IoT Improving IoT Device Cybersecurity IoT SS
Mirai Botnet Attack Caused By IoT Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline the most common example of IoT cybersecurity attack. The slide covers information about attack type, attack description, impact of Mirai Botnet attack, and key intakes for business leaders. Introducing Mirai Botnet Attack Caused By IoT Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Distributed, Various, Credentials, using this template. Grab it now to reap its full benefits.
-
 Real Life Example Of Ransomware Attack Improving IoT Device Cybersecurity IoT SS
Real Life Example Of Ransomware Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline illustration of ransomware attack. WannaCry, Crypto Locker, and Fake Flash Player are some of the major attacks which are mentioned in slide along with their impact. Introducing Real Life Example Of Ransomware Attack Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Running, Locker, Player, using this template. Grab it now to reap its full benefits.
-
 Real Life Examples Of Botnet Attack Improving IoT Device Cybersecurity IoT SS
Real Life Examples Of Botnet Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline real life example of Internet of Things IoT botnet attack. The attacks mentioned in slide are Kneber Botnet, Avalanche Botnet, and Sality Botnet along with potential impact of each attack. Increase audience engagement and knowledge by dispensing information using Real Life Examples Of Botnet Attack Improving IoT Device Cybersecurity IoT SS. This template helps you present information on three stages. You can also present information on Botnet, Avalanche, Attachment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Real Life Examples Of Dos Attack Improving IoT Device Cybersecurity IoT SS
Real Life Examples Of Dos Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase real life illustration of Denial of Service DoS attack. It covers information about attacks such as GitHub attack, PlayStation Network Attack, and Dyn attack along with potential impact of each attack. Introducing Real Life Examples Of Dos Attack Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Attack, Network, Managing, using this template. Grab it now to reap its full benefits.
-
 Real Life Examples Of IoT Password Attack Improving IoT Device Cybersecurity IoT SS
Real Life Examples Of IoT Password Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline real life illustrations of Internet of Things IoT password attack. Information covered in this slide attack description, various strategies used to conduct password attack, and potential impact. Increase audience engagement and knowledge by dispensing information using Real Life Examples Of IoT Password Attack Improving IoT Device Cybersecurity IoT SS. This template helps you present information on two stages. You can also present information on Conduct, Techniques, Potential using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Stuxnet Attack Caused By IoT Security Improving IoT Device Cybersecurity IoT SS
Stuxnet Attack Caused By IoT Security Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to highlight overview of Stuxnet attack caused by Internet of Things IoT security vulnerability. The slide covers information about attack occurred date, its overview, impact of Stuxnet attack, and key takeaways for companies. Introducing Stuxnet Attack Caused By IoT Security Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Efficiency, Reduction, Damage, using this template. Grab it now to reap its full benefits.
-
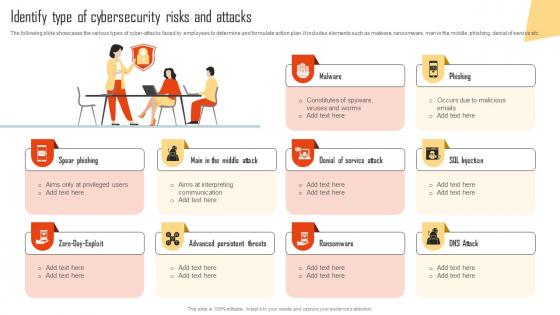 Identify Type Of Cybersecurity Risks And Attacks Improving Cyber Security Risks Management
Identify Type Of Cybersecurity Risks And Attacks Improving Cyber Security Risks ManagementThe following slide showcases the various types of cyber-attacks faced by employees to determine and formulate action plan. It includes elements such as malware, ransomware, man in the middle, phishing, denial of service etc. Introducing Identify Type Of Cybersecurity Risks And Attacks Improving Cyber Security Risks Management to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing, Advanced Persistent Threats, Ransomware, Phishing, using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity How Does Phishing Attack Works On Blockchain Network BCT SS V
Blockchain And Cybersecurity How Does Phishing Attack Works On Blockchain Network BCT SS VThe following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity How Does Phishing Attack Works On Blockchain Network BCT SS V This template helps you present information on Seven stages. You can also present information on Phishing Email, Internet Network, Dispense Email using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain And Cybersecurity How Hackers Attack Blockchain Technology BCT SS V
Blockchain And Cybersecurity How Hackers Attack Blockchain Technology BCT SS VThe following slide showcases how hackers attacks blockchain technology to protect key information and mange threats. It includes elements such as false transactions, private keys, hampering network nodes, fake cryptocurrencies, personal information, etc. Introducing Blockchain And Cybersecurity How Hackers Attack Blockchain Technology BCT SS V to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Blockchain Technology, Modify Data, Swindles Private Keys using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Impact Of 51 Percent Attack On Bitcoin And Blockchain Transactions BCT SS V
Blockchain And Cybersecurity Impact Of 51 Percent Attack On Bitcoin And Blockchain Transactions BCT SS VThe following slide depicts the key effect of 51percent attack on bitcoin and blockchain technology to plan actions and minimize its impact. It includes element such as delayed transactions, network disruption, low miner rewards, market volatility, reputation, credibility, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Impact Of 51 Percent Attack On Bitcoin And Blockchain Transactions BCT SS V This template helps you present information on Five stages. You can also present information on Network Disruption, Low Miner Rewards, Market Volatility using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain And Cybersecurity Impact Of Ddos Attack On Targeted Servers BCT SS V
Blockchain And Cybersecurity Impact Of Ddos Attack On Targeted Servers BCT SS VThe following slide depicts the adverse impact of denial of service DDoS attack to determine malicious attempt to hamper targeted server. It includes elements such as software crashes, node failure, network congestion, bloated ledger, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Impact Of Ddos Attack On Targeted Servers BCT SS V This template helps you present information on Four stages. You can also present information on Software Crashes, Network Congestion, Bloated Ledger using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain And Cybersecurity Impact Of Eclipse Attack On Peer To Peer Network BCT SS V
Blockchain And Cybersecurity Impact Of Eclipse Attack On Peer To Peer Network BCT SS VThe following slide illustrates the impact of eclipse attack on functioning of blockchain network to plan strategies and action steps. It includes elements such as leading to double spending, centralization, disrupting mining power, network instability, monetary loss, etc. Introducing Blockchain And Cybersecurity Impact Of Eclipse Attack On Peer To Peer Network BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Leads To Double Spending, Centralization, Disrupts Mining Power using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Key Scenarios Of Sybil Attack On Blockchain Network BCT SS V
Blockchain And Cybersecurity Key Scenarios Of Sybil Attack On Blockchain Network BCT SS VThe following slide showcases major scenarios of Sybil attack to minimize the impact and manage operations. It includes elements such as attack on bitcoin network, tor network, peer-to-peer model, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Key Scenarios Of Sybil Attack On Blockchain Network BCT SS V This template helps you present information on Two stages. You can also present information on Bitcoin Network, Attack On Tor Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain And Cybersecurity Methods To Avoid Sybil Attack For Protecting Tokens BCT SS V
Blockchain And Cybersecurity Methods To Avoid Sybil Attack For Protecting Tokens BCT SS VThe following slide illustrates various ways to minimize and prevent Sybil attacks and ensure safe blockchain transactions. It includes elements such as identity validation, hierarchical, defense system, cost of new nodes, social trust graphs, etc. Introducing Blockchain And Cybersecurity Methods To Avoid Sybil Attack For Protecting Tokens BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Identity Validation, Establishing Hierarchical System, Defense System using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Overview And Categories Of Sybil Attack On Blockchain Network BCT SS V
Blockchain And Cybersecurity Overview And Categories Of Sybil Attack On Blockchain Network BCT SS VThe following slide illustrates brief introduction of Sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Overview And Categories Of Sybil Attack On Blockchain Network BCT SS V This template helps you present information on Four stages. You can also present information on Direct Sybil Attack, Indirect Sybil Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain And Cybersecurity Overview And Impact Of Blockchain Routing Attacks BCT SS V
Blockchain And Cybersecurity Overview And Impact Of Blockchain Routing Attacks BCT SS VThe following slide illustrates the brief introduction of routing attacks to reduce leakage of information. It includes elements such as interrupting communication between nodes, delaying blockchain delivery, breaking network into two or more parts, etc. Introducing Blockchain And Cybersecurity Overview And Impact Of Blockchain Routing Attacks BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Internet Service Providers, Partial Proceedings, Impact Of Routing Attack using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Overview And Workflow Process Of Eclipse Attack BCT SS V
Blockchain And Cybersecurity Overview And Workflow Process Of Eclipse Attack BCT SS VThe following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer-to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc. Present the topic in a bit more detail with this Blockchain And Cybersecurity Overview And Workflow Process Of Eclipse Attack BCT SS V Use it as a tool for discussion and navigation on Blockchain And Cybersecurity Overview And Workflow Process Of Eclipse Attack BCT SS V This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Blockchain And Cybersecurity Overview And Working Process Of Ddos Attack BCT SS V
Blockchain And Cybersecurity Overview And Working Process Of Ddos Attack BCT SS VThe following slide illustrates brief introduction of distributed denial of service DDoS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Overview And Working Process Of Ddos Attack BCT SS V This template helps you present information on Four stages. You can also present information on Attacker Controls Website Hostage, Perform Operations using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.




