Powerpoint Templates and Google slides for Cyber strategy
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Different Types Of Smishing Cyber Scams Phishing Attacks And Strategies
Different Types Of Smishing Cyber Scams Phishing Attacks And StrategiesThis slide talks about the various types of smishing cyber attacks. The purpose of this slide is to briefly explain different techniques of smishing scams used by the attackers to scam users. These are covid 19 smishing, financial services smishing, etc.Increase audience engagement and knowledge by dispensing information using Different Types Of Smishing Cyber Scams Phishing Attacks And Strategies. This template helps you present information on five stages. You can also present information on Confirmation Smishing, Services Smishing, Smishing Scams using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Different Types Of Vishing Cyber Attacks Phishing Attacks And Strategies
Different Types Of Vishing Cyber Attacks Phishing Attacks And StrategiesThis slide talks about the various types of vishing cyber attacks. The purpose of this slide is to briefly explain different techniques of vishing scams used by the attackers to scam users. These are caller ID spoofing, dumpster diving, wardialing, etc.Introducing Different Types Of Vishing Cyber Attacks Phishing Attacks And Strategies to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Protocol Transmission, Achieved Automatically, Phishing Attack Victims, using this template. Grab it now to reap its full benefits.
-
 Examples Of Clone Phishing Cyber Scams Phishing Attacks And Strategies
Examples Of Clone Phishing Cyber Scams Phishing Attacks And StrategiesThis slide demonstrates the various examples of clone phishing cyber scams. The purpose of this slide is to illustrate different types of clone phishing emails targeting different individuals. These include customer support scams, fake virus scams and refund scams.Increase audience engagement and knowledge by dispensing information using Examples Of Clone Phishing Cyber Scams Phishing Attacks And Strategies. This template helps you present information on three stages. You can also present information on Detected Suspicious, Support Scams, Virus Scams using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Execution Of Man In The Middle Cyber S Phishing Attacks And Strategies
Execution Of Man In The Middle Cyber S Phishing Attacks And StrategiesThis slide illustrates the process of executing man in the middle cyber attacks. The purpose of this slide is to outline the two stages of execution of MITM scams. These stages are interception and decryption which include HTTPS spoofing, SSL BEAST, hijacking, etc.Deliver an outstanding presentation on the topic using this Execution Of Man In The Middle Cyber S Phishing Attacks And Strategies. Dispense information and present a thorough explanation of Data Transfer, Direct Interception, Password Protected using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Introduction To Clone Phishing Cyber Attacks Phishing Attacks And Strategies
Introduction To Clone Phishing Cyber Attacks Phishing Attacks And StrategiesThis slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information.Present the topic in a bit more detail with this Introduction To Clone Phishing Cyber Attacks Phishing Attacks And Strategies. Use it as a tool for discussion and navigation on Personal Information, Sensitive Information, Abnormal Timings Unexpected. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategies To Identify Smishing Cyber Scams Phishing Attacks And Strategies
Strategies To Identify Smishing Cyber Scams Phishing Attacks And StrategiesThis slide talks about the various methods of identifying smishing cyber attacks. The purpose of this slide is to help users identify smishing scams. These include suspicious texts from unknown numbers, unrequested links and files, money transfer requests, etc.Present the topic in a bit more detail with this Strategies To Identify Smishing Cyber Scams Phishing Attacks And Strategies. Use it as a tool for discussion and navigation on Requests Asking, Transfer Requests, Notifications Stating. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Process Of Cyber Phishing Attacks Phishing Attacks And Strategies
Working Process Of Cyber Phishing Attacks Phishing Attacks And StrategiesThis slide talks about the implementation and working of phishing attacks. The purpose of this slide is to explain how are cyber phishing scams conducted. The components include hacker, phishing mail, target, phishing website and original website.Introducing Working Process Of Cyber Phishing Attacks Phishing Attacks And Strategies to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Information Website, Hacker Access Private, Credentials Victim, using this template. Grab it now to reap its full benefits.
-
 Cyber security strategy powerpoint slide background designs
Cyber security strategy powerpoint slide background designsPresenting cyber security strategy powerpoint slide background designs. This is a cyber security strategy powerpoint slide background designs. This is a one stage process. The stages in this process are firewall, antivirus, passwords, email scans.
-
 Cyber security strategy financial retail services migration work cpb
Cyber security strategy financial retail services migration work cpbPresenting this set of slides with name - Cyber Security Strategy Financial Retail Services Migration Work Cpb. This is an editable four graphic that deals with topics like Cyber Security Strategy, Financial Retail Services, Migration Work to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber security strategies small business ppt powerpoint presentation demonstration cpb
Cyber security strategies small business ppt powerpoint presentation demonstration cpbPresenting this set of slides with name Cyber Security Strategies Small Business Ppt Powerpoint Presentation Demonstration Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Cyber Security Strategies Small Business to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Corporate rebranding strategy cyber security ppt powerpoint presentation gallery layout cpb
Corporate rebranding strategy cyber security ppt powerpoint presentation gallery layout cpbPresenting this set of slides with name Corporate Rebranding Strategy Cyber Security Ppt Powerpoint Presentation Gallery Layout Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Corporate Rebranding Strategy Cyber Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber security strategy ppt powerpoint presentation infographic template portfolio cpb
Cyber security strategy ppt powerpoint presentation infographic template portfolio cpbPresenting this set of slides with name Cyber Security Strategy Ppt Powerpoint Presentation Infographic Template Portfolio Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Cyber Security Strategy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber security strategy requirements ppt powerpoint presentation sample cpb
Cyber security strategy requirements ppt powerpoint presentation sample cpbPresenting this set of slides with name Cyber Security Strategy Requirements Ppt Powerpoint Presentation Sample Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Cyber Security Strategy Requirements to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
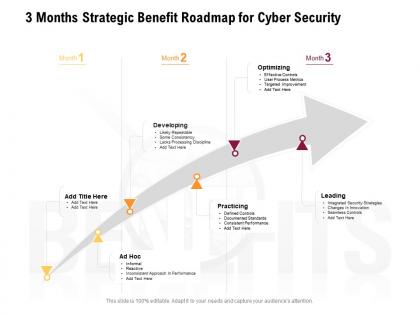 3 months strategic benefit roadmap for cyber security
3 months strategic benefit roadmap for cyber securityPresenting 3 Months Strategic Benefit Roadmap For Cyber Security PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 5 year strategic benefit roadmap for cyber security
5 year strategic benefit roadmap for cyber securityPresenting 5 Year Strategic Benefit Roadmap For Cyber Security PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 6 months strategic benefit roadmap for cyber security
6 months strategic benefit roadmap for cyber securityPresenting 6 Months Strategic Benefit Roadmap For Cyber Security PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
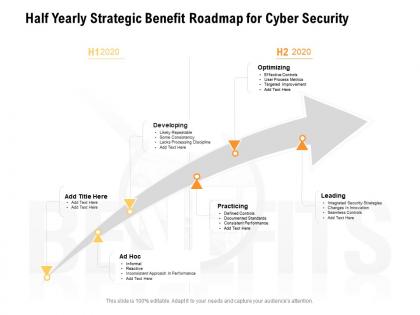 Half yearly strategic benefit roadmap for cyber security
Half yearly strategic benefit roadmap for cyber securityPresenting Half Yearly Strategic Benefit Roadmap For Cyber Security PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
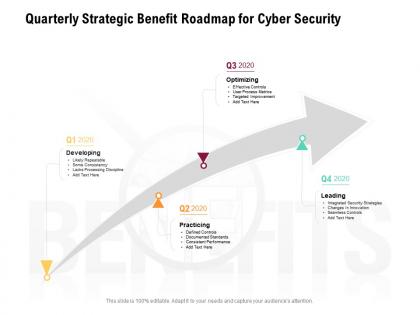 Quarterly strategic benefit roadmap for cyber security
Quarterly strategic benefit roadmap for cyber securityPresenting Quarterly Strategic Benefit Roadmap For Cyber Security PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
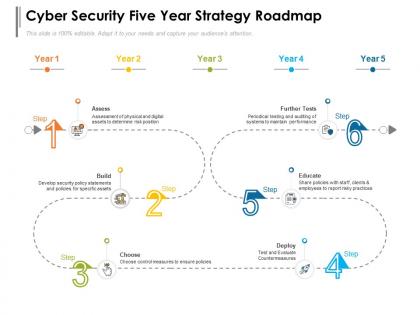 Cyber security five year strategy roadmap
Cyber security five year strategy roadmapPresenting Cyber Security Five Year Strategy Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Cyber security half yearly strategy roadmap
Cyber security half yearly strategy roadmapPresenting Cyber Security Half Yearly Strategy Roadmap PowerPoint Template. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements.
-
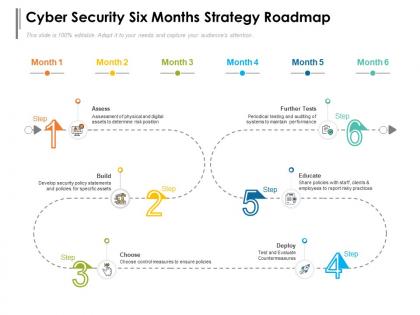 Cyber security six months strategy roadmap
Cyber security six months strategy roadmapPresenting Cyber Security Six Months Strategy Roadmap PowerPoint slide which is percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
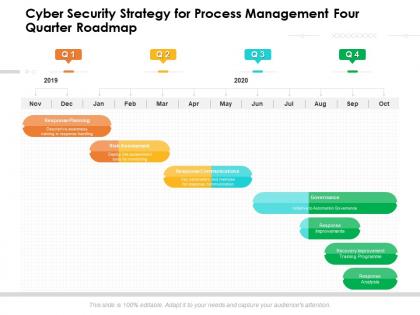 Cyber security strategy for process management four quarter roadmap
Cyber security strategy for process management four quarter roadmapPresenting Cyber Security Strategy For Process Management Four Quarter Roadmap PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
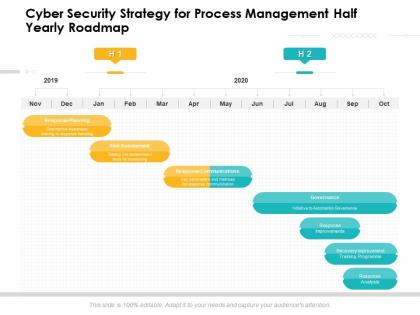 Cyber security strategy for process management half yearly roadmap
Cyber security strategy for process management half yearly roadmapPresenting Cyber Security Strategy For Process Management Half Yearly Roadmap PowerPoint slide. This PPT slide is available at 4,3 and 16,9 aspect ratios. You can download this PPT theme in various formats like PDF, PNG, and JPG. This PowerPoint template is completely editable and you can modify the font size, font type, and shapes as per your requirements. Our PPT layout is compatible with Google Slides.
-
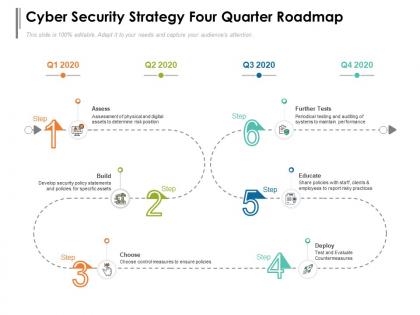 Cyber security strategy four quarter roadmap
Cyber security strategy four quarter roadmapPresenting Cyber Security Strategy Four Quarter Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
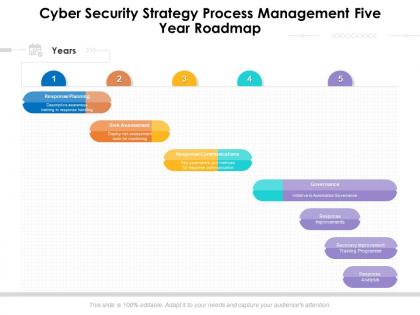 Cyber security strategy process management five year roadmap
Cyber security strategy process management five year roadmapPresenting Cyber Security Strategy Process Management Five Year Roadmap PowerPoint Template. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements.
-
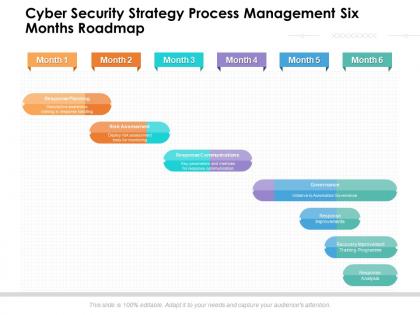 Cyber security strategy process management six months roadmap
Cyber security strategy process management six months roadmapPresenting Cyber Security Strategy Process Management Six Months Roadmap PowerPoint slide which is percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
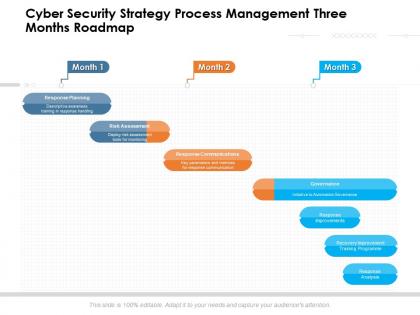 Cyber security strategy process management three months roadmap
Cyber security strategy process management three months roadmapPresenting Cyber Security Strategy Process Management Three Months Roadmap PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
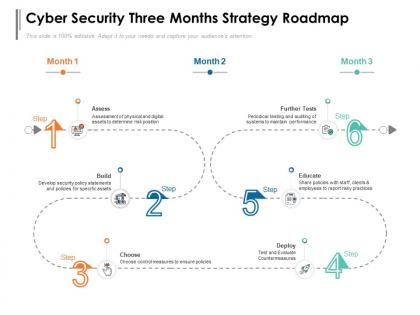 Cyber security three months strategy roadmap
Cyber security three months strategy roadmapPresenting Cyber Security Three Months Strategy Roadmap PowerPoint slide. This PPT slide is available at 4,3 and 16,9 aspect ratios. You can download this PPT theme in various formats like PDF, PNG, and JPG. This PowerPoint template is completely editable and you can modify the font size, font type, and shapes as per your requirements. Our PPT layout is compatible with Google Slides.
-
 Cyber security governance strategy ppt file brochure
Cyber security governance strategy ppt file brochureThis slide portrays information about how firm will assess different alternate sites on certain parameters such as implementation cost hardware and telecommunication connection requirement setup time location. Presenting this set of slides with name Cyber Security Governance Strategy Ppt File Brochure. The topics discussed in these slides are Senior Management, Business Strategy, Security Requirements, Security Programmes, Implementation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
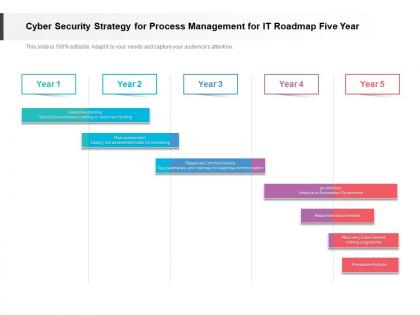 Cyber security strategy for process management for it roadmap five year
Cyber security strategy for process management for it roadmap five yearPresenting Cyber Security Strategy For Process Management For IT Roadmap Five Year PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Cyber security strategy for process management for it roadmap four quarter
Cyber security strategy for process management for it roadmap four quarterPresenting Cyber Security Strategy For Process Management For IT Roadmap Four Quarter PowerPoint Template. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements.
-
 Cyber security strategy for process management for it roadmap half yearly
Cyber security strategy for process management for it roadmap half yearlyPresenting Cyber Security Strategy For Process Management For IT Roadmap Half Yearly PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
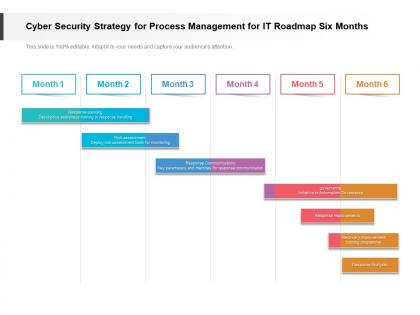 Cyber security strategy for process management for it roadmap six months
Cyber security strategy for process management for it roadmap six monthsPresenting Cyber Security Strategy For Process Management For IT Roadmap Six Months PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Cyber security strategy for process management for it roadmap three months
Cyber security strategy for process management for it roadmap three monthsPresenting Cyber Security Strategy For Process Management For IT Roadmap Three Months PowerPoint slide. This PPT slide is available at 4,3 and 16,9 aspect ratios. You can download this PPT theme in various formats like PDF, PNG, and JPG. This PowerPoint template is completely editable and you can modify the font size, font type, and shapes as per your requirements. Our PPT layout is compatible with Google Slides.
-
 Key strategies for minimizing cyber risks in supply chain management
Key strategies for minimizing cyber risks in supply chain managementIntroducing our premium set of slides with Key Strategies For Minimizing Cyber Risks In Supply Chain Management. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Estalish Supply Chain Context, Evaluate Product Life Cycle, Control. So download instantly and tailor it with your information.
-
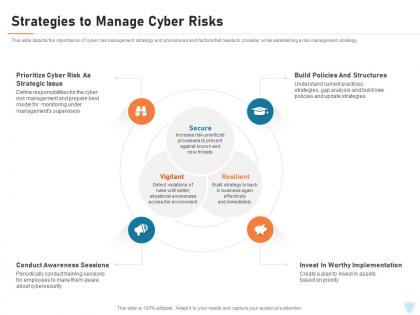 Cyber security it strategies to manage cyber risks ppt powerpoint presentation show
Cyber security it strategies to manage cyber risks ppt powerpoint presentation showThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Increase audience engagement and knowledge by dispensing information using Cyber Security IT Strategies To Manage Cyber Risks Ppt Powerpoint Presentation Show. This template helps you present information on four stages. You can also present information on Conduct Awareness, Implementation, Build Policies And Structures, Strategic Issue using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security it impact on organization after implementing cyber security strategy and training
Cyber security it impact on organization after implementing cyber security strategy and trainingThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Present the topic in a bit more detail with this Cyber Security IT Impact On Organization After Implementing Cyber Security Strategy And Training. Use it as a tool for discussion and navigation on Phishing, Network Intrusion, Inadvertent Disclosure, Stolen Or Lost Devises Or Records, System Misconfiguration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
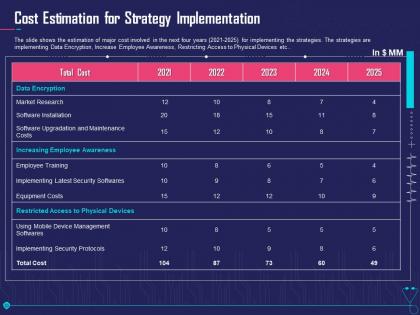 Cost estimation for strategy implementation overcome challenge cyber security healthcare
Cost estimation for strategy implementation overcome challenge cyber security healthcareThe slide shows the estimation of major cost involved in the next four years 2021 to 2025 for implementing the strategies. The strategies are implementing Data Encryption, Increase Employee Awareness, Restricting Access to Physical Devices etc. Present the topic in a bit more detail with this Cost Estimation For Strategy Implementation Overcome Challenge Cyber Security Healthcare. Use it as a tool for discussion and navigation on Software, Implementing, Security, Costs. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
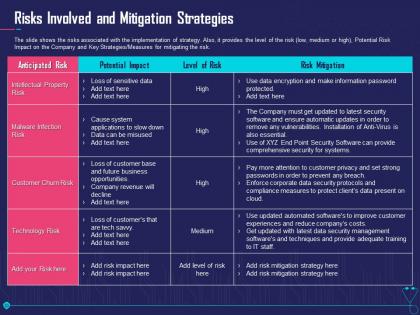 Risks involved and mitigation strategies overcome challenge cyber security healthcare ppt ideas
Risks involved and mitigation strategies overcome challenge cyber security healthcare ppt ideasThe slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, Potential Risk Impact on the Company and Key Strategies or Measures for mitigating the risk. Present the topic in a bit more detail with this Risks Involved And Mitigation Strategies Overcome Challenge Cyber Security Healthcare Ppt Ideas. Use it as a tool for discussion and navigation on Revenue, Opportunities, Management, Security, Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategies for reducing overcome challenge cyber security healthcare ppt summary
Strategies for reducing overcome challenge cyber security healthcare ppt summaryThis slide shows strategies that can be adopted by the company in order to minimize the cybersecurity risks and increasing malware attacks. Some strategies are data encryption, proper employee training, protection of physical devices, use df latest and updated softwares etc. Introducing Strategies For Reducing Overcome Challenge Cyber Security Healthcare Ppt Summary to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Management, Software, Security, Procedures, Financial, using this template. Grab it now to reap its full benefits.
-
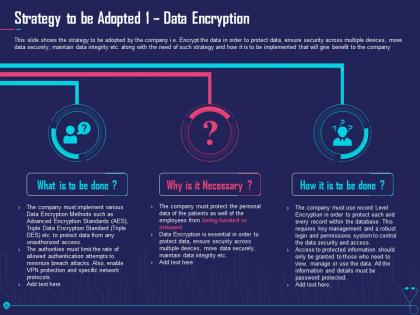 Strategy to be adopted 1 data encryption overcome challenge cyber security healthcare ppt tips
Strategy to be adopted 1 data encryption overcome challenge cyber security healthcare ppt tipsThis slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Increase audience engagement and knowledge by dispensing information using Strategy To Be Adopted 1 Data Encryption Overcome Challenge Cyber Security Healthcare Ppt Tips. This template helps you present information on three stages. You can also present information on Implement, Security, Patients, System, Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
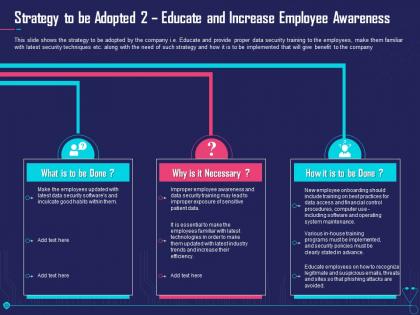 Strategy to be adopted overcome challenge cyber security healthcare ppt model smartart
Strategy to be adopted overcome challenge cyber security healthcare ppt model smartartThis slide shows the strategy to be adopted by the company i.e. Educate and provide proper data security training to the employees, make them familiar with latest security techniques etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Increase audience engagement and knowledge by dispensing information using Strategy To Be Adopted Overcome Challenge Cyber Security Healthcare Ppt Model Smartart. This template helps you present information on three stages. You can also present information on Security, Awareness, Patient, Procedures, Software using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security strategy example ppt powerpoint presentation image cpb
Cyber security strategy example ppt powerpoint presentation image cpbPresenting this set of slides with name Cyber Security Strategy Example Ppt Powerpoint Presentation Image Cpb. This is an editable Powerpoint six stages graphic that deals with topics like Cyber Security Strategy Example to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Organization impact metrics strategic enterprise cyber security ppt demonstration
Organization impact metrics strategic enterprise cyber security ppt demonstrationThis slides the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission.Deliver an outstanding presentation on the topic using this Organization Impact Metrics Strategic Enterprise Cyber Security Ppt Demonstration. Dispense information and present a thorough explanation of Tracking Procedures, Human Resources Or Security, Computers Currently using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Organization impact metrics strategic cyber security phishing awareness training ppt slides
Organization impact metrics strategic cyber security phishing awareness training ppt slidesThis slide the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver an outstanding presentation on the topic using this Organization Impact Metrics Strategic Cyber Security Phishing Awareness Training Ppt Slides. Dispense information and present a thorough explanation of Policy Violations, Data Loss Incidents, Infected Computers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Complete Guide To KPMG Overview Of Key KPMG Cyber Security Considerations Strategy SS V
Complete Guide To KPMG Overview Of Key KPMG Cyber Security Considerations Strategy SS VThis slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less and data centric future, etc. with description and insights. Deliver an outstanding presentation on the topic using this Complete Guide To KPMG Overview Of Key KPMG Cyber Security Considerations Strategy SS V Dispense information and present a thorough explanation of Shared Responsibility, Secure Behaviors, New Models using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Complete Guide To KPMG Cyber Strategies For KPMG For Client Data Protection Strategy SS V
Complete Guide To KPMG Cyber Strategies For KPMG For Client Data Protection Strategy SS VThis slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. Introducing Complete Guide To KPMG Cyber Strategies For KPMG For Client Data Protection Strategy SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on People, Process, Data And Technology using this template. Grab it now to reap its full benefits.
-
 Complete Guide To KPMG Other Cyber Strategies Of KPMG For Client Data Protection Strategy SS V
Complete Guide To KPMG Other Cyber Strategies Of KPMG For Client Data Protection Strategy SS VThis slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies Introducing Complete Guide To KPMG Other Cyber Strategies Of KPMG For Client Data Protection Strategy SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Security Governance Framework, Cyber Security, Cyber Threat Landscape using this template. Grab it now to reap its full benefits.
-
 Firewall Implementation For Cyber Security Firewall Architecture Implementation Strategy Selection
Firewall Implementation For Cyber Security Firewall Architecture Implementation Strategy SelectionThis slide represents the comparative analysis of various firewall implementation architecture strategies. The purpose of this slide is to compare the three firewall architecture implementation strategies, such as packet filtering routers, screened host firewalls, and screened subset firewalls. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Firewall Architecture Implementation Strategy Selection. Dispense information and present a thorough explanation of Firewall Architecture, Strategy Selection, Screened Host Firewalls, Screened Subset Firewalls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation Preventive Strategies For Baiting Cyber Attacks
Social Engineering Methods And Mitigation Preventive Strategies For Baiting Cyber AttacksThis slide outlines the methods to prevent baiting attacks. These are employee training, dont follow links blindly, use anti-virus and anti-malware software, avoid use of external devices without scanning and hold organized simulated attacks. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation Preventive Strategies For Baiting Cyber Attacks. Dispense information and present a thorough explanation of Vulnerability Scanning, Security Patches, Input Vulnerability, Bug Bounty Programs using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation Strategies To Identify Smishing Cyber Scams
Social Engineering Methods And Mitigation Strategies To Identify Smishing Cyber ScamsThis slide talks about the various methods of identifying smishing cyber attacks. The purpose of this slide is to help users identify smishing scams. These include suspicious texts from unknown numbers, unrequested links and files, money transfer requests, etc. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation Strategies To Identify Smishing Cyber Scams. Dispense information and present a thorough explanation of Smishing Cyber Scams, Money Transfer Requests, Unrequested Links And Files using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.




