Powerpoint Templates and Google slides for Cyber strategy
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Incident Handling Checklist Incident Response Strategies Deployment
Cyber Security Incident Handling Checklist Incident Response Strategies DeploymentThis slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post incident activity. Introducing Cyber Security Incident Handling Checklist Incident Response Strategies Deployment to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Parameters, Analysis, Containment, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Management Checklist After An Incident Response Strategies Deployment
Cyber Security Incident Management Checklist After An Incident Response Strategies DeploymentThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Checklist After An Incident Response Strategies Deployment. This template helps you present information on ten stages. You can also present information on Management, Security, Review using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Management Checklist Before Incident Response Strategies Deployment
Cyber Security Incident Management Checklist Before Incident Response Strategies DeploymentThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident Management before the occurrence of the incident. Introducing Cyber Security Incident Management Checklist Before Incident Response Strategies Deployment to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Parameters, Security, Management, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Management Checklist During Incident Response Strategies Deployment
Cyber Security Incident Management Checklist During Incident Response Strategies DeploymentThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident Management during the occurrence of the incident. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Checklist During Incident Response Strategies Deployment. This template helps you present information on nine stages. You can also present information on Record, Convene, Meeting using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Management Team Roles Incident Response Strategies Deployment
Cyber Security Incident Management Team Roles Incident Response Strategies DeploymentThis slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. Introducing Cyber Security Incident Management Team Roles Incident Response Strategies Deployment to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Responsibilities, Roles, Management, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Management Team Structure Incident Response Strategies Deployment
Cyber Security Incident Management Team Structure Incident Response Strategies DeploymentThis slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Team Structure Incident Response Strategies Deployment. This template helps you present information on one stages. You can also present information on Legal, System, Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Response Lifecycle Incident Response Strategies Deployment
Cyber Security Incident Response Lifecycle Incident Response Strategies DeploymentThis slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Present the topic in a bit more detail with this Cyber Security Incident Response Lifecycle Incident Response Strategies Deployment. Use it as a tool for discussion and navigation on Preparation, Activity, DetectionThis template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Response Plan Timeline Incident Response Strategies Deployment
Cyber Security Incident Response Plan Timeline Incident Response Strategies DeploymentThis slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Introducing Cyber Security Incident Response Plan Timeline Incident Response Strategies Deployment to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Verification, Detection, Response, using this template. Grab it now to reap its full benefits.
-
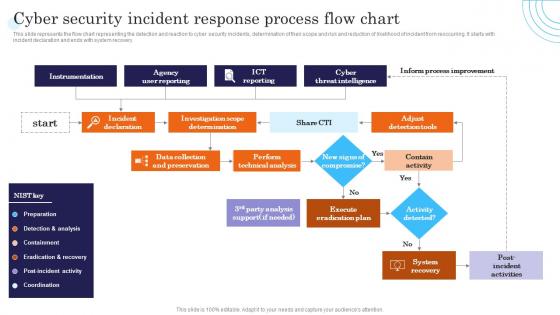 Cyber Security Incident Response Process Flow Chart Incident Response Strategies Deployment
Cyber Security Incident Response Process Flow Chart Incident Response Strategies DeploymentThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Response Process Flow Chart Incident Response Strategies Deployment. This template helps you present information on one stages. You can also present information on Instrumentation, Agency, Intelligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incidents Follow Up Report Incident Response Strategies Deployment
Cyber Security Incidents Follow Up Report Incident Response Strategies DeploymentThis slide represents the follow up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. Deliver an outstanding presentation on the topic using this Cyber Security Incidents Follow Up Report Incident Response Strategies Deployment. Dispense information and present a thorough explanation of Security, Incident, Cyber using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Assessment And Management Matrix Incident Response Strategies Deployment
Cyber Security Risk Assessment And Management Matrix Incident Response Strategies DeploymentThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Matrix Incident Response Strategies Deployment. Dispense information and present a thorough explanation of Vulnerability, Consequences, Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Threats Detection Techniques Incident Response Strategies Deployment
Cyber Security Threats Detection Techniques Incident Response Strategies DeploymentThis slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Introducing Cyber Security Threats Detection Techniques Incident Response Strategies Deployment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Threat, Analytics, Intruder, using this template. Grab it now to reap its full benefits.
-
 Impact Of Implementing Cyber Security Management Incident Response Strategies Deployment
Impact Of Implementing Cyber Security Management Incident Response Strategies DeploymentThis slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Present the topic in a bit more detail with this Impact Of Implementing Cyber Security Management Incident Response Strategies Deployment. Use it as a tool for discussion and navigation on Implementing, Security, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Issues Faced By Organization Due To Cyber Security Incidents Response Strategies Deployment
Key Issues Faced By Organization Due To Cyber Security Incidents Response Strategies DeploymentThis slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Increase audience engagement and knowledge by dispensing information using Key Issues Faced By Organization Due To Cyber Security Incidents Response Strategies Deployment. This template helps you present information on five stages. You can also present information on Compliance, Information, Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Parameters To Select Cyber Security Containment Strategy Incident Response Strategies Deployment
Key Parameters To Select Cyber Security Containment Strategy Incident Response Strategies DeploymentThis slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Increase audience engagement and knowledge by dispensing information using Key Parameters To Select Cyber Security Containment Strategy Incident Response Strategies Deployment. This template helps you present information on five stages. You can also present information on Organizational, Evidence, Duration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
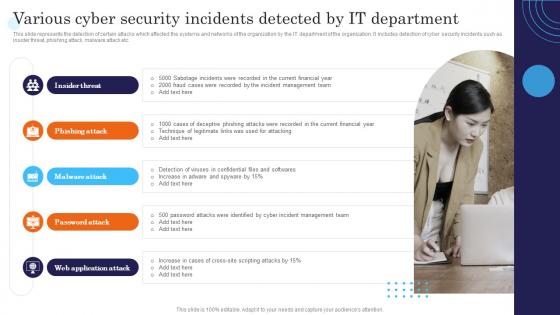 Various Cyber Security Incidents Detected By IT Department Incident Response Strategies Deployment
Various Cyber Security Incidents Detected By IT Department Incident Response Strategies DeploymentThis slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Introducing Various Cyber Security Incidents Detected By IT Department Incident Response Strategies Deployment to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Insider, Phishing, Application, using this template. Grab it now to reap its full benefits.
-
 Ways To Detect Cyber Security Incidents Incident Response Strategies Deployment
Ways To Detect Cyber Security Incidents Incident Response Strategies DeploymentThis slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Increase audience engagement and knowledge by dispensing information using Ways To Detect Cyber Security Incidents Incident Response Strategies Deployment. This template helps you present information on four stages. You can also present information on Accounts, Network, Locations using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Incident Response Strategies Deployment Key Lessons Learned By Organization From Cyber Security
Incident Response Strategies Deployment Key Lessons Learned By Organization From Cyber SecurityThis slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. Introducing Incident Response Strategies Deployment Key Lessons Learned By Organization From Cyber Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Ransomware, Authentication, Cloud, using this template. Grab it now to reap its full benefits.
-
 Incidents Response Strategies Deployment User Awareness Training Program To Prevent Cyber Security
Incidents Response Strategies Deployment User Awareness Training Program To Prevent Cyber SecurityThis slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Deliver an outstanding presentation on the topic using this Incidents Response Strategies Deployment User Awareness Training Program To Prevent Cyber Security. Dispense information and present a thorough explanation of Trainer, Budget, Method using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Initiatives Playbook Risk Management Plan To Manage Cyber Threats
Strategic Initiatives Playbook Risk Management Plan To Manage Cyber ThreatsThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Deliver an outstanding presentation on the topic using this Strategic Initiatives Playbook Risk Management Plan To Manage Cyber Threats. Dispense information and present a thorough explanation of Risk Management Plan, Manage Cyber Threats, Firewall Configurations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Plan To Manage Cyber Threats IT Cost Optimization And Management Strategy SS
Risk Management Plan To Manage Cyber Threats IT Cost Optimization And Management Strategy SSThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Deliver an outstanding presentation on the topic using this Risk Management Plan To Manage Cyber Threats IT Cost Optimization And Management Strategy SS. Dispense information and present a thorough explanation of Threat, Vulnerability, Cyber Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incident Communication Strategy Development And Implementation Of Security
Cyber Security Incident Communication Strategy Development And Implementation Of SecurityThis slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. Deliver an outstanding presentation on the topic using this Cyber Security Incident Communication Strategy Development And Implementation Of Security. Dispense information and present a thorough explanation of Senior Management, Impacted Business Managers, Employees using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Parameters To Select Cyber Security Containment Strategy Development And Implementation Of Security
Key Parameters To Select Cyber Security Containment Strategy Development And Implementation Of SecurityThis slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Introducing Key Parameters To Select Cyber Security Containment Strategy Development And Implementation Of Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Organizational Resources, Potential Damages, Strategy, using this template. Grab it now to reap its full benefits.
-
 Strategies To Analyze Cyber Security Incidents Development And Implementation Of Security Incident Management
Strategies To Analyze Cyber Security Incidents Development And Implementation Of Security Incident ManagementThis slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Increase audience engagement and knowledge by dispensing information using Strategies To Analyze Cyber Security Incidents Development And Implementation Of Security Incident Management. This template helps you present information on two stages. You can also present information on Profile Network And Systems, Understand Normal Behaviors, Perform Event Correlation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategic Cyber Assessment And Assurance Framework
Strategic Cyber Assessment And Assurance FrameworkThe following slide illustrates cyber assessment framework aimed at analysing the extent to which cyber risks from functions are being managed by organisations. It covers roles and responsibilities under NIS objectives and principles.Introducing our Strategic Cyber Assessment And Assurance Framework set of slides. The topics discussed in these slides are Security Risk Management, Against Cyber Attacks, Identification Cyber. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Risk Management Plan To Manage Cyber Threats Develop Business Aligned IT Strategy
Risk Management Plan To Manage Cyber Threats Develop Business Aligned IT StrategyThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Deliver an outstanding presentation on the topic using this Risk Management Plan To Manage Cyber Threats Develop Business Aligned IT Strategy. Dispense information and present a thorough explanation of Vulnerability, Likelihood, Control Initiative, Natural Disaster using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Key Parameters To Select Cyber Security Containment Strategy
Cyber Security Attacks Response Plan Key Parameters To Select Cyber Security Containment StrategyThis slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Attacks Response Plan Key Parameters To Select Cyber Security Containment Strategy. This template helps you present information on five stages. You can also present information on Cyber Security, Containment Strategy, Incident Management Solutions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Attacks Response Plan Strategies To Analyze Cyber Security Incidents
Cyber Security Attacks Response Plan Strategies To Analyze Cyber Security IncidentsThis slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Introducing Cyber Security Attacks Response Plan Strategies To Analyze Cyber Security Incidents to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Profile Network And Systems, Understand Normal Behaviors, Perform Event Correlation, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Communication Strategy Cyber Security Attacks Response Plan
Cyber Security Incident Communication Strategy Cyber Security Attacks Response PlanThis slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. Introducing Cyber Security Incident Communication Strategy Cyber Security Attacks Response Plan to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Senior Management, Communication Strategy, Stakeholder Needs, Suppliers, using this template. Grab it now to reap its full benefits.
-
 Strategic Framework To Manage IT Risk Management Plan To Manage Cyber Threats Strategy SS
Strategic Framework To Manage IT Risk Management Plan To Manage Cyber Threats Strategy SSThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Present the topic in a bit more detail with this Strategic Framework To Manage IT Risk Management Plan To Manage Cyber Threats Strategy SS. Use it as a tool for discussion and navigation on Risk Management Plan, Manage Cyber Threats, Vulnerability, Control Initiative. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Communication Strategy Deploying Computer Security Incident Management
Cyber Security Incident Communication Strategy Deploying Computer Security Incident ManagementThis slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders.Introducing Cyber Security Incident Communication Strategy Deploying Computer Security Incident Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Senior Management, Impacted Business, Incident Management, using this template. Grab it now to reap its full benefits.
-
 Key Parameters To Select Cyber Security Containment Strategy Deploying Computer Security Incident
Key Parameters To Select Cyber Security Containment Strategy Deploying Computer Security IncidentThis slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc.Introducing Key Parameters To Select Cyber Security Containment Strategy Deploying Computer Security Incident to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Potential Damages, Organizational Resources, Containment Strategy, using this template. Grab it now to reap its full benefits.
-
 Strategies We Will Implement To Make Security Raising Cyber Security Awareness In Organizations
Strategies We Will Implement To Make Security Raising Cyber Security Awareness In OrganizationsThe purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high quality content and variety. Introducing Strategies We Will Implement To Make Security Raising Cyber Security Awareness In Organizations to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Gamification, Personalization, High Quality Content, using this template. Grab it now to reap its full benefits.
-
 IT Strategy Planning Guide Risk Management Plan To Manage Cyber Threats Strategy SS V
IT Strategy Planning Guide Risk Management Plan To Manage Cyber Threats Strategy SS VThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Present the topic in a bit more detail with this IT Strategy Planning Guide Risk Management Plan To Manage Cyber Threats Strategy SS V. Use it as a tool for discussion and navigation on Risk Management Plan, Manage Cyber Threats, Natural Disaster, Website Resources Unavailability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Plan To Manage Cyber Threats Blueprint Develop Information It Roadmap Strategy Ss
Risk Management Plan To Manage Cyber Threats Blueprint Develop Information It Roadmap Strategy SsThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Present the topic in a bit more detail with this Risk Management Plan To Manage Cyber Threats Blueprint Develop Information It Roadmap Strategy Ss. Use it as a tool for discussion and navigation on Management, Information, Vulnerability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Privileged IAM Strategy For Cyber Defense
Privileged IAM Strategy For Cyber DefenseThis slide shows privileged access management for IAM model or organization. The purpose of this strategy is to highlight all phases for implementing IAM strategy against cyber crimes. It include phases such as pre work operations and monitoring Introducing our Privileged IAM Strategy For Cyber Defense set of slides. The topics discussed in these slides are Privileged, Strategy, Cyber. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cybersecurity Risk Assessment Program Strategic Plan To Mitigate Cyber Attacks
Cybersecurity Risk Assessment Program Strategic Plan To Mitigate Cyber AttacksThe slide indicates the risk mitigation plan for the multiple cyber attacks. It also includes details of cost involved and implementation time required for each mitigation approach. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Assessment Program Strategic Plan To Mitigate Cyber Attacks. Dispense information and present a thorough explanation of Strategic Plan, Mitigate Cyber Attacks, Malware Attack, Recommended Mitigation Strategy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategies To Reduce Cyber Security Threats
Strategies To Reduce Cyber Security ThreatsThis slide highlights major strategies as used by business organizations to reduce cyber security threats which hamper the functioning of business processes. The various strategies are to encrypt data, update software, monitor physical security, use strong passwords and install firewalls Introducing our premium set of slides with Strategies To Reduce Cyber Security Threats. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Encrypt Data, Install Firewalls. So download instantly and tailor it with your information.
-
 Risk Management Plan To Manage Cyber Threats Strategic Initiatives To Boost IT Strategy SS V
Risk Management Plan To Manage Cyber Threats Strategic Initiatives To Boost IT Strategy SS VThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Increase audience engagement and knowledge by dispensing information using Risk Management Plan To Manage Cyber Threats Strategic Initiatives To Boost IT Strategy SS V. This template helps you present information on seven stages. You can also present information on Plan, Management, Risk using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Strategy Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Security Strategy Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Cyber security strategy colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Cyber Security Strategy Management Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Security Strategy Management Colored Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Cyber security strategy management colored icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Cyber Security Strategy Management Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Security Strategy Management Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Cyber security strategy management monotone icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Cyber Security Strategy Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Security Strategy Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Cyber security strategy monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Cyber Security Strategy Network Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Security Strategy Network Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Cyber security strategy network colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Cyber Security Strategy Network Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Security Strategy Network Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Cyber security strategy network monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Strategies To Develop Effective Cyber Security Plan Ppt Professional Infographics
Strategies To Develop Effective Cyber Security Plan Ppt Professional InfographicsThis slide represents the techniques to be adopted by administration to effectively manage cyber security incidents in order to reduce their impact on business operations. It includes strategies to develop cyber security plan such as establish IR team, conduct threat analysis etc.Introducing Strategies To Develop Effective Cyber Security Plan Ppt Professional Infographics to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Response Guidelines, External Communication, Develop Procedures, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Communication Strategy Plan
Cyber Security Communication Strategy PlanThis slide shows communication strategy plan used to spread awareness regarding cyber security among employees. It includes communication objectives, activity, mode of communication and accountable person etc. Presenting our well structured Cyber Security Communication Strategy Plan. The topics discussed in this slide are Communication Objective, Accountable Person, Activity. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
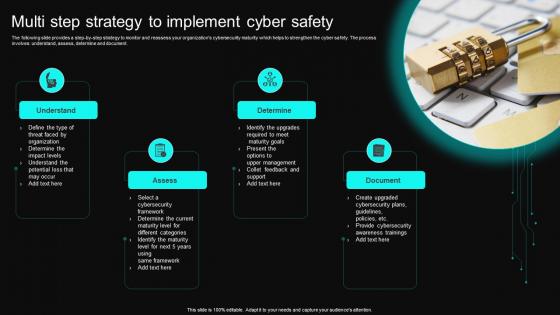 Multi Step Strategy To Implement Cyber Safety
Multi Step Strategy To Implement Cyber SafetyThe following slide provides a step by step strategy to monitor and reassess your organizations cybersecurity maturity which helps to strengthen the cyber safety. The process involves understand, assess, determine and document. Presenting our set of slides with Multi Step Strategy To Implement Cyber Safety. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Understand, Assess, Determine, Document.
-
 Risk Management Plan To Manage Cyber Threats Definitive Guide To Manage Strategy SS V
Risk Management Plan To Manage Cyber Threats Definitive Guide To Manage Strategy SS VThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Deliver an outstanding presentation on the topic using this Risk Management Plan To Manage Cyber Threats Definitive Guide To Manage Strategy SS V. Dispense information and present a thorough explanation of Management, Threat, Asset using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Communication Plan Development Strategy Icon
Cyber Security Communication Plan Development Strategy IconIntroducing our premium set of slides with Cyber Security Communication Plan Development Strategy Icon Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security Communication Plan, Development Strategy Icon So download instantly and tailor it with your information.
-
 Cyber Strategies For KPMG For Client Data Comprehensive Guide To KPMG Strategy SS
Cyber Strategies For KPMG For Client Data Comprehensive Guide To KPMG Strategy SSThis slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data And technology and regulatory.Deliver an outstanding presentation on the topic using this Cyber Strategies For KPMG For Client Data Comprehensive Guide To KPMG Strategy SS. Dispense information and present a thorough explanation of Security Processes, Broad Visibility, Explore Automating using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Other Cyber Strategies Of KPMG For Client Data Comprehensive Guide To KPMG Strategy SS
Other Cyber Strategies Of KPMG For Client Data Comprehensive Guide To KPMG Strategy SSThis slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc.Introducing Other Cyber Strategies Of KPMG For Client Data Comprehensive Guide To KPMG Strategy SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Comprehensive Understanding, Establishing Robust Security, Security Vendors, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Program Risk Management Strategy
Cyber Security Program Risk Management StrategyThis slide provides a strategy for cybersecurity risk management which helps business and organizations to secure the data and information. Key elements are understand, assess, determine and document.Introducing our premium set of slides with Cyber Security Program Risk Management Strategy. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Determine Maturity, Different Categories, Policies Guidelines. So download instantly and tailor it with your information.
-
 Comprehensive Strategy To Improve Cyber Resilience
Comprehensive Strategy To Improve Cyber ResilienceThe slide showcases the steps for building efficient cyber resiliency across organization. It covers steps like secure remote working enablement, develop a comprehensive response plan, build a cyber security improvement roadmap, build detection and response capability and educating users on escalating threats. Introducing our Comprehensive Strategy To Improve Cyber Resilience set of slides. The topics discussed in these slides are Working Enablement, Comprehensive Response Plan, Improvement Roadmap. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Resilience Action Plan Strategy Icon
Cyber Resilience Action Plan Strategy IconPresenting our set of slides with Cyber Resilience Action Plan Strategy Icon This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Resilience, Action Plan Strategy Icon
-
 Cyber Resilience Strategy For Manufacturing Sector Icon
Cyber Resilience Strategy For Manufacturing Sector IconPresenting our well structured Cyber Resilience Strategy For Manufacturing Sector Icon The topics discussed in this slide are Cyber Resilience, Strategy For Manufacturing, Sector Icon. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Developing A Long Term Cyber Resilience Strategy
Developing A Long Term Cyber Resilience StrategyThe slide showcases a multistage strategy that promotes cyber resilience long term adaptability and response. It covers stages like baseline assessment, objectives, plan, execute, report and manage. Introducing our premium set of slides with Developing A Long Term Cyber Resilience Strategy Ellicudate the Six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Objectives, Baseline Assessment, Manage. So download instantly and tailor it with your information.
-
 Essential Components Of Cyber Resilience Strategy
Essential Components Of Cyber Resilience StrategyThe slide showcases the crucial components of cyber resilience which enables business acceleration by preparing, responding and recovering from cyber threats and aims to secure the whole organization dynamically. It covers aspects like protect, detect and evolve. Presenting our set of slides with Essential Components Of Cyber Resilience Strategy This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Protect, Detect, Evolve.
-
 Risk Management Plan To Manage Cyber Threats Strategic Plan To Secure It Infrastructure Strategy SS V
Risk Management Plan To Manage Cyber Threats Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Present the topic in a bit more detail with this Risk Management Plan To Manage Cyber Threats Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Risk Management, Initiatives, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Plan To Manage Cyber Threats Cios Guide For It Strategy Strategy SS V
Risk Management Plan To Manage Cyber Threats Cios Guide For It Strategy Strategy SS VThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Present the topic in a bit more detail with this Risk Management Plan To Manage Cyber Threats Cios Guide For It Strategy Strategy SS V. Use it as a tool for discussion and navigation on Risk Management, Vulnerability, Likelihood . This template is free to edit as deemed fit for your organization. Therefore download it now.





