Powerpoint Templates and Google slides for Cyber Security Process
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Why To Automate The It Security Process Enabling Automation In Cyber Security Operations
Why To Automate The It Security Process Enabling Automation In Cyber Security OperationsThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Increase audience engagement and knowledge by dispensing information using Why To Automate The It Security Process Enabling Automation In Cyber Security Operations. This template helps you present information on five stages. You can also present information on Better Threat Detection, Faster Containment, Improve Productivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Response Process Flowchart
Cyber Security Incident Response Process FlowchartThis slide covers cyber security incident response process flowchart. It involves relationship between technical actions coordinator, incident manager, supporting actions coordinator and business owner. Introducing our Cyber Security Incident Response Process Flowchart set of slides. The topics discussed in these slides are Technical Actions Coordinator, Supporting Actions Coordinator, Business Owner. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Incident Management Process In Cyber Security
Incident Management Process In Cyber SecurityThis slide covers incident management process in cyber security. It involves steps such as engage team, identify incidents, assessment, investigation and documentation. Presenting our set of slides with name Incident Management Process In Cyber Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Incident Response Team, Monitoring And Evaluation, Investigation Or Resolving.
-
 Key Steps Cyber Security Incident Response Plan Process
Key Steps Cyber Security Incident Response Plan ProcessThis slide covers key steps cyber incident response plan process. It involves six stages such as preparation, detection, analysis, containment, eradication and recovery. Presenting our set of slides with name Key Steps Cyber Security Incident Response Plan Process. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Preparation, Detection, Containment, Eradication.
-
 6 Stage Process For Implementation Of Risk Management In Cyber Security Project
6 Stage Process For Implementation Of Risk Management In Cyber Security ProjectThis This slide signifies the six step process for successful implementation of risk assessment in cyber security project. It covers information about stages like identify, analyse, evaluate, prioritize, treat and monitor. Presenting our set of slides with name 6 Stage Process For Implementation Of Risk Management In Cyber Security Project. This exhibits information on six stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Analyse, Evaluate, Prioritize, Treat.
-
 Cyber Data Security Risk Management Response Process
Cyber Data Security Risk Management Response ProcessThis slide covers process to respond towards cyber data security risk. It includes steps such as preparation of incident response plan, detection of data compromises, analyse use of malicious tools, eradicate network threats, data recovery as the final step. Presenting our set of slides with name Cyber Data Security Risk Management Response Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Threats, Compromised Data, Data Compromises.
-
 Four Steps Of Cyber Security Data Breach Risk Process
Four Steps Of Cyber Security Data Breach Risk ProcessThis slide covers steps utilised to breach data. It includes stages such as probing, performing initial attack, expansion of attacks and data lifting. Introducing our premium set of slides with name Four Steps Of Cyber Security Data Breach Risk Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Initial Attack, Expanded Attack, Breach Risk Process. So download instantly and tailor it with your information.
-
 Cyber Security Incident Response Process Flow Chart Ppt Powerpoint Presentation Model File Formats
Cyber Security Incident Response Process Flow Chart Ppt Powerpoint Presentation Model File FormatsThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Deliver an outstanding presentation on the topic using this Cyber Security Incident Response Process Flow Chart Ppt Powerpoint Presentation Model File Formats. Dispense information and present a thorough explanation of Instrumentation, Agency User Reporting, Cyber Threat Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threat Prevention And Security Process
Cyber Threat Prevention And Security ProcessThis slide shows four steps to provide and assure protection against cyber threats. It includes steps secure perimeter, protect users, network segmentation, determine and control risks. Introducing our premium set of slides with name Cyber Threat Prevention And Security Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Secure Perimeter, Smart Network Segmentation, Determine And Control. So download instantly and tailor it with your information.
-
 Threat Modelling Process Of Cyber Security Program
Threat Modelling Process Of Cyber Security ProgramThis slide shows threat modelling process to identify gaps and improve efficiency of cyber security program. It contains five steps select digital asset, identify attack scenarios, evaluate existing controls, assess residual risks and construct business case. Presenting our set of slides with name Threat Modelling Process Of Cyber Security Program. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Threat Modelling, Cyber Security, Assess Residual Risk .
-
 Cyber Security Transformation Process Flow
Cyber Security Transformation Process FlowThis slide provides a cyber security process for transformation of business operations which can be used by managers for risk mitigation by resolving security issues. The steps relate to assessment of current cyber security posture, set objectives, implement strategies, train employees etc. Introducing our premium set of slides with Cyber Security Transformation Process Flow. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Set Objectives, Implement Strategies, Train Employees. So download instantly and tailor it with your information.
-
 Cyber Security Incident Response Process
Cyber Security Incident Response ProcessThis slide covers procedure of cyber security incident response. The purpose of this process is to examine the cyber threat and try to find the ways to mitigate the risk. It includes four steps such as identification and detection, containment, eradication and recovery and post recovery.Introducing our premium set of slides with Cyber Security Incident Response Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identification Detection, Eradication Recovery, Incident Manager. So download instantly and tailor it with your information.
-
 Six Step Process For Risk Management In Cyber Security Project
Six Step Process For Risk Management In Cyber Security ProjectThis slide signifies the six step process for risk assessment in cyber security project. It covers information about stages like identify, analyse, evaluate, prioritize, treat and monitor Presenting our set of slides with name Six Step Process For Risk Management In Cyber Security Project. This exhibits information on six stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Management, Process, Computing Software.
-
 Cyber Security Policy Byod Procedure Device Protocols For Workers
Cyber Security Policy Byod Procedure Device Protocols For WorkersThis slide represents the device protocols that are the first step in the BYOD procedure. It also includes the software information that should be installed on the employees personal devices. Increase audience engagement and knowledge by dispensing information using Cyber Security Policy Byod Procedure Device Protocols For Workers. This template helps you present information on four stages. You can also present information on Software, Business, Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
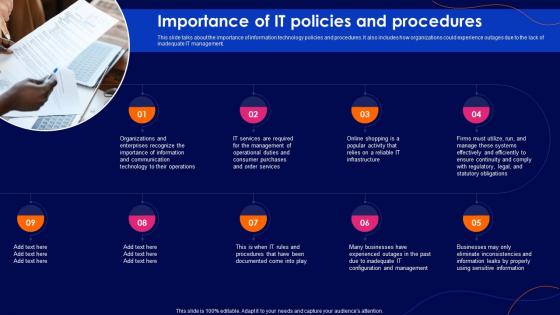 Cyber Security Policy Importance Of It Policies And Procedures
Cyber Security Policy Importance Of It Policies And ProceduresThis slide talks about the importance of information technology policies and procedures. It also includes how organizations could experience outages due to the lack of inadequate IT management. Increase audience engagement and knowledge by dispensing information using Cyber Security Policy Importance Of It Policies And Procedures. This template helps you present information on nine stages. You can also present information on Services, Operational, Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
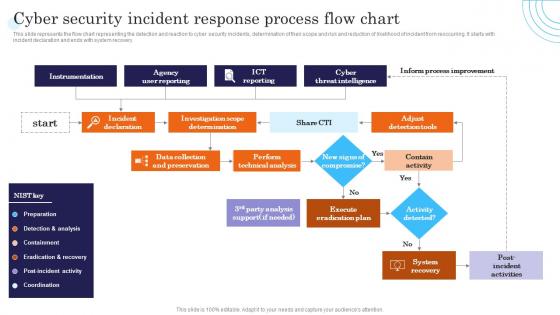 Cyber Security Incident Response Process Flow Chart Incident Response Strategies Deployment
Cyber Security Incident Response Process Flow Chart Incident Response Strategies DeploymentThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Response Process Flow Chart Incident Response Strategies Deployment. This template helps you present information on one stages. You can also present information on Instrumentation, Agency, Intelligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Policy What Happens In The Absence Of It Policies And Procedures
Cyber Security Policy What Happens In The Absence Of It Policies And ProceduresThis slide represents the consequences of not having IT policies and procedures. Effects include disrupted and inconsistent operational duties, communication gaps between staff and employees, etc. Introducing Cyber Security Policy What Happens In The Absence Of It Policies And Procedures to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Procedures, Information, Corporations, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Response Process Flow Chart Development And Implementation Of Security
Cyber Security Incident Response Process Flow Chart Development And Implementation Of SecurityThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Deliver an outstanding presentation on the topic using this Cyber Security Incident Response Process Flow Chart Development And Implementation Of Security. Dispense information and present a thorough explanation of Data Collection And Preservation, Perform Technical Analysis, Incident Declaration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incident Response Process Flow Chart Cyber Security Attacks Response Plan
Cyber Security Incident Response Process Flow Chart Cyber Security Attacks Response PlanThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Present the topic in a bit more detail with this Cyber Security Incident Response Process Flow Chart Cyber Security Attacks Response Plan. Use it as a tool for discussion and navigation on Cyber Threat Intelligence, Agency User Reporting, Instrumentation, Cyber Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Response Process Flow Chart Deploying Computer Security Incident Management
Cyber Security Incident Response Process Flow Chart Deploying Computer Security Incident ManagementThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery.Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Response Process Flow Chart Deploying Computer Security Incident Management. This template helps you present information on Two stages. You can also present information on Agency Reporting, Investigation Scope Determination, Collection Preservation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Five Step Process To Create Cyber Security Raising Cyber Security Awareness In Organizations
Five Step Process To Create Cyber Security Raising Cyber Security Awareness In OrganizationsThe purpose of this slide is to outline a multistep process that can assist IT managers in drafting a cyber security awareness roadmap. The various steps are assessing, building, choosing, deploying, educating employees and retesting. Increase audience engagement and knowledge by dispensing information using Five Step Process To Create Cyber Security Raising Cyber Security Awareness In Organizations. This template helps you present information on six stages. You can also present information on Assess, Build, Choose, Deploy, Educate, Retest using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Four Stage Cyclic Process Of Building Cyber Security
Four Stage Cyclic Process Of Building Cyber SecurityThis slide showcases four cyclic stages of cyber security process of creating and maintaining a secure . It includes security assess , detecting , identifying , recording attacks , bringing safety measures , strengthening protection etc. Introducing our premium set of slides with Four Stage Cyclic Process Of Building Cyber Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Safe State, Strengthen Protection, Remediation. So download instantly and tailor it with your information.
-
 Cyber Security Risk Management Process In Powerpoint And Google Slides Cpb
Cyber Security Risk Management Process In Powerpoint And Google Slides CpbPresenting our Cyber Security Risk Management Process In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Cyber Security Risk Management Process This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Process To Formulate Cyber Security Communication Plan
Process To Formulate Cyber Security Communication PlanThis slide provides information to develop a cyber security communication plan effectively and efficiently. It includes elements such as formulate committee, identify scenarios, draft statement, rehearse plan and regulatory compliance. Introducing our premium set of slides with Process To Formulate Cyber Security Communication Plan Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Formulate Committee, Draft Statement, Rehearse, Plan, Regulatory Compliance So download instantly and tailor it with your information.
-
 Cyber Security Action Plan Process
Cyber Security Action Plan ProcessThis slide illustrates action plan process of cyber security. It further consists steps such as system hygiene, plan development, create risk profile, evaluate and measure, minimize risk, cyber insurance, etc Introducing our premium set of slides with Cyber Security Action Plan Process. Ellicudate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Action, Security, Process. So download instantly and tailor it with your information.
-
 Latest cyber security technology ppt powerpoint presentation gallery rules cpb
Latest cyber security technology ppt powerpoint presentation gallery rules cpbPresenting this set of slides with name Latest Cyber Security Technology Ppt Powerpoint Presentation Gallery Rules Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Latest Cyber Security Technology to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber security essentials ppt powerpoint presentation model rules cpb
Cyber security essentials ppt powerpoint presentation model rules cpbPresenting this set of slides with name Cyber Security Essentials Ppt Powerpoint Presentation Model Rules Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Cyber Security Essentials to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber security audit procedures ppt powerpoint presentation infographics slides cpb
Cyber security audit procedures ppt powerpoint presentation infographics slides cpbPresenting this set of slides with name Cyber Security Audit Procedures Ppt Powerpoint Presentation Infographics Slides Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Cyber Security Audit Procedures to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber security people process technology ppt powerpoint presentation file graphics template cpb
Cyber security people process technology ppt powerpoint presentation file graphics template cpbPresenting this set of slides with name Cyber Security People Process Technology Ppt Powerpoint Presentation File Graphics Template Cpb. This is an editable Powerpoint six stages graphic that deals with topics like Cyber Security People Process Technology to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber security people process technology framework
Cyber security people process technology frameworkPresenting this set of slides with name Cyber Security People Process Technology Framework. This is a six stage process. The stages in this process are Information Risk Management, Incident Response And Forensic Investigation, Architecture, Applications And Network Security, Threat And Vulnerability Assessment, Compliance And Awareness, Security Management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
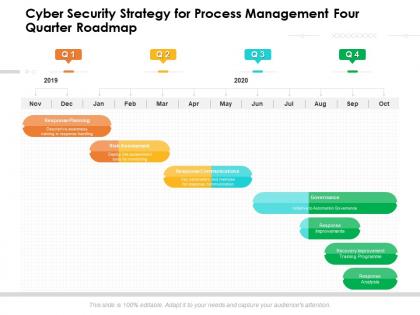 Cyber security strategy for process management four quarter roadmap
Cyber security strategy for process management four quarter roadmapPresenting Cyber Security Strategy For Process Management Four Quarter Roadmap PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
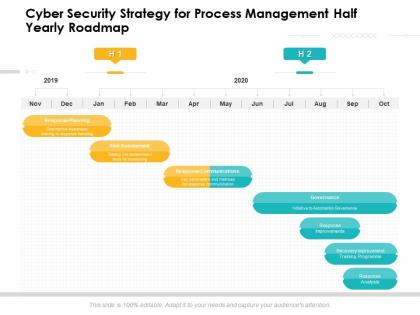 Cyber security strategy for process management half yearly roadmap
Cyber security strategy for process management half yearly roadmapPresenting Cyber Security Strategy For Process Management Half Yearly Roadmap PowerPoint slide. This PPT slide is available at 4,3 and 16,9 aspect ratios. You can download this PPT theme in various formats like PDF, PNG, and JPG. This PowerPoint template is completely editable and you can modify the font size, font type, and shapes as per your requirements. Our PPT layout is compatible with Google Slides.
-
 Cyber security strategy process management five year roadmap
Cyber security strategy process management five year roadmapPresenting Cyber Security Strategy Process Management Five Year Roadmap PowerPoint Template. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements.
-
 Cyber security strategy process management six months roadmap
Cyber security strategy process management six months roadmapPresenting Cyber Security Strategy Process Management Six Months Roadmap PowerPoint slide which is percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
 Cyber security strategy process management three months roadmap
Cyber security strategy process management three months roadmapPresenting Cyber Security Strategy Process Management Three Months Roadmap PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Process flow for cyber security service ppt powerpoint presentation files
Process flow for cyber security service ppt powerpoint presentation filesPresenting this set of slides with name Process Flow For Cyber Security Service Ppt Powerpoint Presentation Files. This is a three stage process. The stages in this process are Project Kickoff, Planning, Development And Implementation, Maintain And Train. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Cyber security process with identify and react
Cyber security process with identify and reactPresenting this set of slides with name Cyber Security Process With Identify And React. This is a four stage process. The stages in this process are Identify, Protect, Detect, React. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Process flow for enterprise cyber safety and security services ppt gallery
Process flow for enterprise cyber safety and security services ppt galleryPresenting this set of slides with name Process Flow For Enterprise Cyber Safety And Security Services Ppt Gallery. This is a four stage process. The stages in this process are Project Kickoff, Planning, Development And Implementation, Maintain And Train. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Incident management process cyber security ppt powerpoint presentation infographics show cpb
Incident management process cyber security ppt powerpoint presentation infographics show cpbPresenting this set of slides with name Incident Management Process Cyber Security Ppt Powerpoint Presentation Infographics Show Cpb. This is an editable Powerpoint six stages graphic that deals with topics like Incident Management Process Cyber Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber security strategy for process management for it roadmap five year
Cyber security strategy for process management for it roadmap five yearPresenting Cyber Security Strategy For Process Management For IT Roadmap Five Year PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Cyber security strategy for process management for it roadmap four quarter
Cyber security strategy for process management for it roadmap four quarterPresenting Cyber Security Strategy For Process Management For IT Roadmap Four Quarter PowerPoint Template. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements.
-
 Cyber security strategy for process management for it roadmap half yearly
Cyber security strategy for process management for it roadmap half yearlyPresenting Cyber Security Strategy For Process Management For IT Roadmap Half Yearly PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
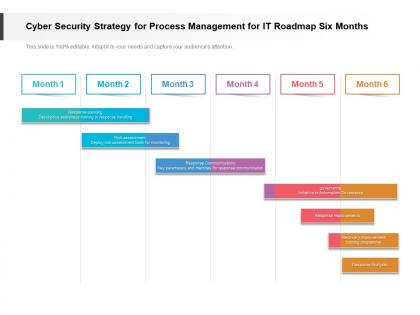 Cyber security strategy for process management for it roadmap six months
Cyber security strategy for process management for it roadmap six monthsPresenting Cyber Security Strategy For Process Management For IT Roadmap Six Months PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Cyber security strategy for process management for it roadmap three months
Cyber security strategy for process management for it roadmap three monthsPresenting Cyber Security Strategy For Process Management For IT Roadmap Three Months PowerPoint slide. This PPT slide is available at 4,3 and 16,9 aspect ratios. You can download this PPT theme in various formats like PDF, PNG, and JPG. This PowerPoint template is completely editable and you can modify the font size, font type, and shapes as per your requirements. Our PPT layout is compatible with Google Slides.
-
 Analysts discussing cyber security protocols against crime
Analysts discussing cyber security protocols against crimePresenting this set of slides with name Analysts Discussing Cyber Security Protocols Against Crime. This is a three stage process. The stages in this process are Analysts Discussing Cyber Security Protocols Against Crime. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Computer security cyber security quotes ppt powerpoint presentation show rules cpb
Computer security cyber security quotes ppt powerpoint presentation show rules cpbPresenting our Computer Security Cyber Security Quotes Ppt Powerpoint Presentation Show Rules Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Computer Security Cyber Security Quotes This PPT slide can be easily accessed in standard screen 4.3 and widescreen 16.9 aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cyber Security Risk Management Process With Data Sharing
Cyber Security Risk Management Process With Data SharingIntroducing our Cyber Security Risk Management Process With Data Sharing set of slides. The topics discussed in these slides are Assess Data Sources, Cyber Intelligence, Continuous Monitoring. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Process of disaster recovery planning cyber security it ppt powerpoint presentation styles
Process of disaster recovery planning cyber security it ppt powerpoint presentation stylesThis slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Introducing Process Of Disaster Recovery Planning Cyber Security IT Ppt Powerpoint Presentation Styles to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Approval, Plan Testing, Data Collection, Recovery Plans, Perform Risk Analysis, using this template. Grab it now to reap its full benefits.
-
 Costs incurred to process overcome challenge cyber security healthcare ppt grid
Costs incurred to process overcome challenge cyber security healthcare ppt gridThis slide shows the amount of costs that is incurred by the company to process and rectify faulty cybersecurity transactions for the past 5 years. Deliver an outstanding presentation on the topic using this Costs Incurred To Process Overcome Challenge Cyber Security Healthcare Ppt Grid. Dispense information and present a thorough explanation of Costs Incurred To Process Faulty Cybersecurity Transactions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber security econometric system process ppt powerpoint presentation deck cpb
Cyber security econometric system process ppt powerpoint presentation deck cpbPresenting this set of slides with name Cyber Security Econometric System Process Ppt Powerpoint Presentation Deck Cpb. This is an editable Powerpoint ten stages graphic that deals with topics like Cyber Security Econometric System Process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Idea generation enterprise cyber security ppt rules
Idea generation enterprise cyber security ppt rulesIntroducing Idea Generation Enterprise Cyber Security Ppt Rules to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Idea Generation, using this template. Grab it now to reap its full benefits.
-
 Automated security awareness platform and cost cyber security phishing awareness training ppt rules
Automated security awareness platform and cost cyber security phishing awareness training ppt rulesThis slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks. Present the topic in a bit more detail with this Automated Security Awareness Platform And Cost Cyber Security Phishing Awareness Training Ppt Rules. Use it as a tool for discussion and navigation on Platform, Functioning, Benefits. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Employee security awareness training budget cyber security phishing awareness training ppt rules
Employee security awareness training budget cyber security phishing awareness training ppt rulesThis slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Present the topic in a bit more detail with this Employee Security Awareness Training Budget Cyber Security Phishing Awareness Training Ppt Rules. Use it as a tool for discussion and navigation on Employee Security Awareness Training Budget. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact of security awareness training cyber security phishing awareness training ppt rules
Impact of security awareness training cyber security phishing awareness training ppt rulesThis slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen lost devices or records and system misconfiguration. Present the topic in a bit more detail with this Impact Of Security Awareness Training Cyber Security Phishing Awareness Training Ppt Rules. Use it as a tool for discussion and navigation on Phishing, Network Intrusion, Inadvertent Disclosure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security awareness program timeline cyber security phishing awareness training ppt rules
Security awareness program timeline cyber security phishing awareness training ppt rulesThis slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Introducing Security Awareness Program Timeline Cyber Security Phishing Awareness Training Ppt Rules to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Security Awareness Program Timeline, using this template. Grab it now to reap its full benefits.
-
 Cyber security threat landscape evaluation process
Cyber security threat landscape evaluation processIntroducing our Cyber Security Threat Landscape Evaluation Process set of slides. The topics discussed in these slides are Inspect, Preliminary Assessment, Prioritize. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.




