Powerpoint Templates and Google slides for Cyber Security Process
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Improving Cyber Security Risks Management Process Powerpoint PPT Template Bundles DK MD
Improving Cyber Security Risks Management Process Powerpoint PPT Template Bundles DK MDIf you require a professional template with great design, then this Improving Cyber Security Risks Management Process Powerpoint PPT Template Bundles DK MD is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twenty one slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Fintech Cyber Security Tool Investment By Process
Fintech Cyber Security Tool Investment By ProcessThis slide showcases the investment in tools to protect against cyber security. Its aim is to monitor and invest in best tools for securing fintech. This slide includes monitoring, policy, hiring, software, firewall, authentication and encryption. Introducing our Fintech Cyber Security Tool Investment By Process set of slides. The topics discussed in these slides are Fintech, Cyber Security Tool, Investment By Process. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Risk Analysis Process In Cyber Security
Risk Analysis Process In Cyber SecurityThis slide outlines the risk analysis process for cyber security to effectively and efficiently protect their department assets. It includes key steps such as conduct risk assessment survey, identify risks, analyse risks, develop a risk management plan, implement risk management plan and monitor risks.Introducing our premium set of slides with Risk Analysis Process In Cyber Security. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Assessment Survey, Identify Risks, Analyze Risks. So download instantly and tailor it with your information.
-
 Cyber Security Risk Audit Process Flowchart Improving Cyber Security Risks Management
Cyber Security Risk Audit Process Flowchart Improving Cyber Security Risks ManagementThe following slide depicts the cyber security review flowchart to manage risk and minimize its impact. It includes elements such as request access, grantor, authorizer, tools, auditor, follow up, alert to end user etc. Present the topic in a bit more detail with this Cyber Security Risk Audit Process Flowchart Improving Cyber Security Risks Management. Use it as a tool for discussion and navigation on Request Access, Validate User Identity, Dismiss Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents For Improving Cyber Security Risk Management Process
Table Of Contents For Improving Cyber Security Risk Management ProcessIntroducing Table Of Contents For Improving Cyber Security Risk Management Process to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Risks And Attacks, Management Solutions, Program Courses, using this template. Grab it now to reap its full benefits.
-
 Enhancing Cyber Security With Patch Management Process
Enhancing Cyber Security With Patch Management ProcessFollowing slide showcases the process for improving cybersecurity with patch management process. The purpose of this slide is to help organizations strengthen their action plan against cyber threats to ensure a secure computing environment. It includes elements such as well trained staff, communication plan, etc.Presenting our set of slides with Enhancing Cyber Security With Patch Management Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Communication Plan, Regularly Test Patches, Production Systems.
-
 Cyber Security Audit Process For Digital Ecosystem
Cyber Security Audit Process For Digital EcosystemThis slide elaborates on cybersecurity audit process and provides details about how to implement protection in a digital ecosystem. It includes elements such as build blueprint, audit frequently, etc. Presenting our set of slides with Cyber Security Audit Process For Digital Ecosystem. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Define Audit Purpose, Build Blueprint, Identify Evaluate Risk Management.
-
 Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS V
Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS V Dispense information and present a thorough explanation of Consensus Mechanism, Smart Contract Security, Data Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Build Cyber Security Team Structure Implementing Cyber Risk Management Process
Build Cyber Security Team Structure Implementing Cyber Risk Management ProcessThe following slide showcases the organizational cyber security team hierarchy to prevent sensitive data loss and damage. It mainly includes elements such as security manager, engineer, analyst, chief information security officer etc. Deliver an outstanding presentation on the topic using this Build Cyber Security Team Structure Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Security Analyst, Security Manager, Chief Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management Process
Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management ProcessThe following slide showcases some facts and figures to generate awareness about cyber-crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc. Introducing Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering, Data Breaches, Mobile Malware Attacks, using this template. Grab it now to reap its full benefits.
-
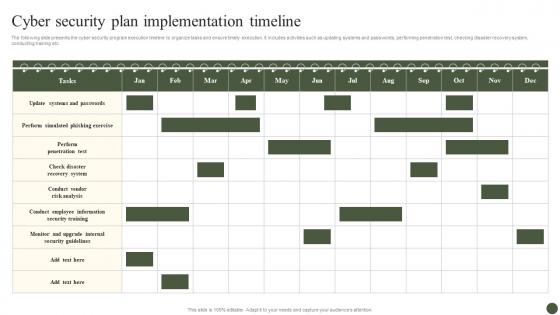 Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management Process
Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management ProcessThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Present the topic in a bit more detail with this Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Cyber Security Plan, Implementation Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management Process
Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management ProcessThe following slide depicts some figures to analyse the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Increase audience engagement and knowledge by dispensing information using Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management Process. This template helps you present information on five stages. You can also present information on Malware Infection, Systems With Passwords, Employees Feels, Allow Official Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process
Determine Cyber Security Risks And Threats Implementing Cyber Risk Management ProcessThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Present the topic in a bit more detail with this Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Objectives, Issue Identifier. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Global Cyber Security Trend Analysis Implementing Cyber Risk Management Process
Global Cyber Security Trend Analysis Implementing Cyber Risk Management ProcessThe following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber-attacks etc. Introducing Global Cyber Security Trend Analysis Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Businesses Targeted, Ransomware Attack, Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management Process
Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management ProcessThe following slide depicts the projected consequences of implementing cyber security preventive measures. It includes data about number of cyber attracts pre and post adopting latest strategies. Present the topic in a bit more detail with this Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Cyber Attack Type, Remarks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process
Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management ProcessThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions. Deliver an outstanding presentation on the topic using this Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Inadequate Security Guidelines, Inappropriate Privacy Policies, Insufficient Background Check using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management Process
KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management ProcessThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Before, After. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management Process
Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management ProcessThe following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Present the topic in a bit more detail with this Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Target Audience, Trainer Name, Mode. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management Process
Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management ProcessThe following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Present the topic in a bit more detail with this Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Rare, Unlikely, Possible. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management Process
Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management ProcessThe following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy, disaster recovery, password encryption, tasks, reviews etc. Present the topic in a bit more detail with this Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Parameters, Tasks, Status, Reviews. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process
Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management ProcessThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Deliver an outstanding presentation on the topic using this Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Features, Free Trial, Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps For Effective Triage Cyber Security Process
Steps For Effective Triage Cyber Security ProcessThis slide represents steps for effective triage process which assists security teams to focus on critical threats and allocate resources effectively., It includes steps for effective triage cyber security process such as identify, map and eradicate Introducing our premium set of slides with name Steps For Effective Triage Cyber Security Process Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify Artifacts, Draw Event Timelines, System From Backup. So download instantly and tailor it with your information.
-
 Triage Process For Cyber Security Icon
Triage Process For Cyber Security IconPresenting our set of slides with name Triage Process For Cyber Security Icon This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Triage Process, Cyber Security Icon
-
 Utilization Of Triage Cyber Security Process In It
Utilization Of Triage Cyber Security Process In ItThis slide represents utilization of triage cyber security process in IT which assists to handle large number of tickets and increases help desk efficiency. It includes utilization of triage cyber security process in IT such as IT operations, email, etc Presenting our set of slides with name Utilization Of Triage Cyber Security Process In It This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Software Testing, Agile Software Development, IT Operations
-
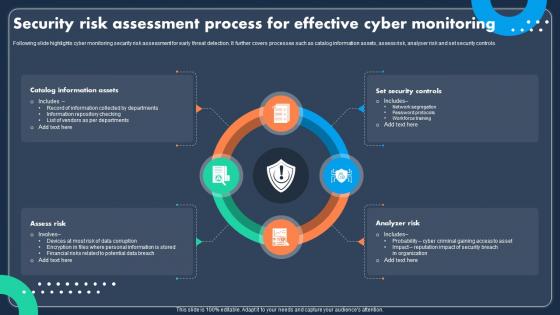 Security Risk Assessment Process For Effective Cyber Monitoring
Security Risk Assessment Process For Effective Cyber MonitoringFollowing slide highlights cyber monitoring security risk assessment for early threat detection. It further covers processes such as catalog information assets, assess risk, analyser risk and set security controls. Introducing our premium set of slides with Security Risk Assessment Process For Effective Cyber Monitoring Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Assets, Security Controls, Analyzer Risk. So download instantly and tailor it with your information.
-
 Process To Create Cyber Security Policy
Process To Create Cyber Security PolicyIntroducing our premium set of slides with Process To Create Cyber Security Policy Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Risk Assessment, Legal Compliance Review, Stakeholder Collaboration. So download instantly and tailor it with your information.
-
 ATP Cyber Security Attack Process
ATP Cyber Security Attack ProcessThis slide depicts the ATP cyber security attack process. Its aim is to monitor the cyber security attack and prevent them. This slide includes brute force attacker, unfamiliar location, lateral movement, sensitive data, etc. Presenting our set of slides with name ATP Cyber Security Attack Process. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Integrate Security, Measures In The System, Prevents Attack Automatically, Access Of Sensitive Data.
-
 ATP Cyber Security System Process
ATP Cyber Security System ProcessThis slide showcases the ATP cyber security process. Its aim is to help define the target and identify the anomalies. This slide includes researching target, acquiring tools, detection of virus, strengthening the system, remove virus, etc. Presenting our set of slides with name ATP Cyber Security System Process. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Plan, Intrusion, Getting Out, Sub Zero.
-
 Cyber Security Gap Analysis Process
Cyber Security Gap Analysis ProcessThis slide covers procedure for cyber security gap analysis such as establishing security goal, assembling skilled team, and gathering documentation to identify and address vulnerabilities and shortcomings in an organizations security measures to enhance overall resilience against cyber threats. Presenting our set of slides with name Cyber Security Gap Analysis Process. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Establish Security Goal, Assemble Skilled Team, Gather Necessary Documentation.
-
 Process To Determine Adequate Cyber Security Control
Process To Determine Adequate Cyber Security ControlThis slide represents the process to identifying adequate cyber security control for business to prevent online threats and implement necessary steps. It includes various steps such as evaluate size of the company, identify scope of IT infrastructure, etc. Presenting our set of slides with Process To Determine Adequate Cyber Security Control This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify Scope Of It Infrastructure, Evaluate Size Of Company, Investment In Cyber Security
-
 IP Security For Cyber Protocol Icon
IP Security For Cyber Protocol IconPresenting our set of slides with name IP Security For Cyber Protocol Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on IP Security, Cyber Protocol Icon.
-
 Effective Cyber Security Management Process
Effective Cyber Security Management ProcessFollowing slide showcases process that can help businesses in mitigating cyber security threats. It includes steps such as pinpoint cyber security risks, evaluate cybersecurity risks, mitigation measures, monitoring, etc. Presenting our well structured Effective Cyber Security Management Process. The topics discussed in this slide are Identify The Cybersecurity Risks, Identify Cybersecurity Risks, Mitigation Measures. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Process To Implement Gamified Cyber Security Training
Process To Implement Gamified Cyber Security TrainingThe purpose of this slide is to create a gamified cybersecurity training program that captures attention of users also achieves specific, measurable improvements in cybersecurity awareness and skills including steps such as identifying learning objectives, structuring activities and challenges, etc. Introducing our premium set of slides with name Process To Implement Gamified Cyber Security Training. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify Learning Objectives, Structure Activities And Challenges, Cyber Security Training. So download instantly and tailor it with your information.
-
 Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security Threat
Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about system patch management to determine vulnerabilities after cyber attack. It includes key process of automated patch management and best practices such as schedule patching, prioritization, and patch testing. Deliver an outstanding presentation on the topic using this Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Management, Process, Vulnerability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comanagement Of SIEM Cyber Security Process
Comanagement Of SIEM Cyber Security ProcessThis slide showcases the co management of SIEM cyber security process. Its aim is to list monitoring activities and manage services. This slide includes onboarding, build out, baseline, tune and monitor. Introducing our premium set of slides with name Comanagement Of SIEM Cyber Security Process. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Onboard, Build Out, Baseline. So download instantly and tailor it with your information.
-
 Cyber Security Process In Industry 4 0 Icon
Cyber Security Process In Industry 4 0 IconPresenting our set of slides with Cyber Security Process In Industry 4 0 Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Process, Industry 4 0, Icon.
-
 Fintech Cyber Security KYC Process
Fintech Cyber Security KYC ProcessThis slide showcases the fintech cyber security KYC process. Its aim is to identify the problems and verify the right customer to protect the data. This slide includes document verification, customer authentication, assess risk, enrolment facilitation, etc. Presenting our set of slides with name Fintech Cyber Security KYC Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Enrolment, Risk Assessment, Identity Verification Report.
-
 Growing cyber security issues intelligent service analytics ppt rules
Growing cyber security issues intelligent service analytics ppt rulesThe slide provides the major cyber security issues Unprecedented Attacks, Cyber Espionage, and Data Theft along with the split of total information security incidents by the type of incident. Present the topic in a bit more detail with this Growing Cyber Security Issues Intelligent Service Analytics Ppt Rules. Use it as a tool for discussion and navigation on Unprecedented Attacks, Cyber Espionage, Data Theft. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Before And After Results Of Cyber Security Process Changes
Before And After Results Of Cyber Security Process ChangesThis slide shows reduction in threats percentage after adopting cyber security. It includes computer virus, data breach, DOS and phishing. Introducing our Before And After Results Of Cyber Security Process Changes set of slides. The topics discussed in these slides are Computer Virus, Data Breach, DOS. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Eliminating manual security processes managing cyber risk in a digital age
Eliminating manual security processes managing cyber risk in a digital ageMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Present the topic in a bit more detail with this Eliminating Manual Security Processes Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Vulnerability, Scanning, Resolution, Team. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber threat security planning process with risk tolerance and threats
Cyber threat security planning process with risk tolerance and threatsThis following slide illustrates the cyber security threat program planning which include steps like identify key personnel, risk tolerance strategy and developing frequency. Presenting our set of slides with Cyber Threat Security Planning Process With Risk Tolerance And Threats. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Built Risk Tolerance, Identify And Document, Establish Governance.
-
 Eliminating Manual Security Processes Through Automation Risk Based Methodology To Cyber
Eliminating Manual Security Processes Through Automation Risk Based Methodology To CyberMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools.Present the topic in a bit more detail with this Eliminating Manual Security Processes Through Automation Risk Based Methodology To Cyber Use it as a tool for discussion and navigation on Manual Vulnerability, Scanning And Resolution, Vulnerability Scanning This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Flow Diagram Of Incident Response Process Introducing A Risk Based Approach To Cyber Security
Flow Diagram Of Incident Response Process Introducing A Risk Based Approach To Cyber SecurityMentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down.Present the topic in a bit more detail with this Flow Diagram Of Incident Response Process Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Remediate Eradicate, Contain Mitigate, Consider The Potential This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Introducing New Incidents Logging Process Introducing A Risk Based Approach To Cyber Security
Introducing New Incidents Logging Process Introducing A Risk Based Approach To Cyber SecurityThis slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details.Present the topic in a bit more detail with this Introducing New Incidents Logging Process Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Category Selection, Assigned To Responsible, Provide An Interaction This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Technical Assessment Process
Cyber Security Technical Assessment ProcessThis slide signifies the technical assessment process of cyber security. It include stages like identify, planning, execution, monitor and closure. Presenting our set of slides with Cyber Security Technical Assessment Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Execution, Closure, Planning, Monitor.
-
 Cyber Security Roadmap With Process And Tasks
Cyber Security Roadmap With Process And TasksThis slide represent roadmap for various cyber security task and process like response planning ,risk assessment progress in an organization with timeline. It includes hours per week ,owner and start date introducing our Cyber Security Roadmap With Process And Tasks set of slides. The topics discussed in these slides are Roadmap, Process, Assessment. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Data Security Protocols Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Data Security Protocols Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Cyber data security protocols colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Cyber Data Security Protocols Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Data Security Protocols Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Cyber data security protocols monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Security Strategic Planning Process For CPS Cyber Physical Systems In Powerpoint And Google Slides
Security Strategic Planning Process For CPS Cyber Physical Systems In Powerpoint And Google SlidesThis slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Deliver an outstanding presentation on the topic using this Security Strategic Planning Process For CPS Cyber Physical Systems In Powerpoint And Google Slides. Dispense information and present a thorough explanation of Gap Analysis, Prioritization, Environmental Trends using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Process For Cloud Services
Cyber Security Process For Cloud ServicesThe following slide highlights the cyber security process for cloud computing, cloud storage and cloud analytics storage. It depict identification, network security, data safety, application safety, monitoring and policy control to govern, protect and control the cloud services. Introducing our premium set of slides with name Cyber Security Process For Cloud Services. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Security, Policy Control, Monitoring. So download instantly and tailor it with your information.
-
 Process Of Cyber Security Asset Management
Process Of Cyber Security Asset ManagementThe following slide highlights the process of cyber security asset management depicting four steps which include asset inventory, synchronization, security gaps and response to save assets and mitigate the risk in minimum time. Introducing our premium set of slides with name Process Of Cyber Security Asset Management. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Asset Inventory, Synchronization, Response, Security Gaps. So download instantly and tailor it with your information.
-
 Three Layers Of Cyber Security Management Process
Three Layers Of Cyber Security Management ProcessThe following slide highlights the three layers of cyber security management process which are dependent on people, process and technology, it helps company to manage cyber risks such as phishing attacks, data loss and exposed vulnerabilities. Presenting our set of slides with name Three Layers Of Cyber Security Management Process. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on People, Process, Technology.
-
 Business Cyber Security Risk Assessment Process
Business Cyber Security Risk Assessment ProcessThe slide shows cyber threat detection and protection measures in order to eliminate the potential risks to the business. The steps include identifying, detecting, responding, protecting, and recovering. Presenting our set of slides with Business Cyber Security Risk Assessment Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Detect, Respond, Protect.
-
 Cyber Security Risk Communication Process Framework
Cyber Security Risk Communication Process FrameworkThis slide showcases a model of risk communication process for cyber security. It includes identify issues, set goals, and objectives, community and constraints, stakeholder assessment, communication and engagement tools, implement strategy and evaluate and follow up. Introducing our premium set of slides with Cyber Security Risk Communication Process Framework. Ellicudate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify Issue, Implement Strategy, Identify Messages. So download instantly and tailor it with your information.
-
 Cyber Security Protocols In Powerpoint And Google Slides Cpb
Cyber Security Protocols In Powerpoint And Google Slides CpbPresenting our Cyber Security Protocols In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases nine stages. It is useful to share insightful information on Cyber Security Protocols This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Problem Management Process For Enhancing Cyber Security
Problem Management Process For Enhancing Cyber SecurityThis slide signifies increasing cyber security and IT through problem management process. It includes stages like detection, define, investigate, identify resolutions, implement and follow up Introducing our premium set of slides with Problem Management Process For Enhancing Cyber Security. Elucidate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Problem Detection, Define, Investigate, Identify Resolutions, Implement. So download instantly and tailor it with your information.
-
 Security Incident Response Playbook Addressing The Cyber Incident Logging Process
Security Incident Response Playbook Addressing The Cyber Incident Logging ProcessThis slide displays logging process for a cyber incident logging. It covers information about process ID, procedure, its description and owner details. Deliver an outstanding presentation on the topic using this Security Incident Response Playbook Addressing The Cyber Incident Logging Process. Dispense information and present a thorough explanation of Process, Information, Procedure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Bank Frauds Prevention Process With Cyber Security Program
Bank Frauds Prevention Process With Cyber Security ProgramThe slide illustrates a banking frauds mitigation process for client to reduce and prevent issues. Its key steps are establish governance structure, define culture shift, introduce staff training, improve payment process, implement technology controls and harden human firewall. Introducing our premium set of slides with Bank Frauds Prevention Process With Cyber Security Program. Elucidate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Introduce Staff Training, Implement Technology Controls, Improve Payment Process, Harden Human Firewall. So download instantly and tailor it with your information.
-
 Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations
Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security OperationsThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Present the topic in a bit more detail with this Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Automation, Integrates, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Processes That Cant Be Automated Enabling Automation In Cyber Security Operations
Security Processes That Cant Be Automated Enabling Automation In Cyber Security OperationsThe following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Increase audience engagement and knowledge by dispensing information using Security Processes That Cant Be Automated Enabling Automation In Cyber Security Operations. This template helps you present information on three stages. You can also present information on Threat Modeling, Penetration Testing, Bug Bounty using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.




