Powerpoint Templates and Google slides for Attack Strategy
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Phishing Attacks Tracking Dashboard Phishing Attacks And Strategies
Cyber Phishing Attacks Tracking Dashboard Phishing Attacks And StrategiesThis slide represents the dashboard to track cyber phishing attacks. The purpose of this slide is to provide a graphical representation of cyber attacks occurred in a specific time span. It also depicts the organizations health risk.Deliver an outstanding presentation on the topic using this Cyber Phishing Attacks Tracking Dashboard Phishing Attacks And Strategies. Dispense information and present a thorough explanation of Cyber Phishing Attacks, Tracking Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategy To Minimize Cyber Attacks Comprehensive Overview Of Organization IT Assets
Strategy To Minimize Cyber Attacks Comprehensive Overview Of Organization IT AssetsThe purpose this slide is to showcase the comprehensive overview of organization IT assets. The dashboards provide information regarding the IT devices count, distribution in terms of operating system, and location. It also contains details of endpoint by hardware, department and cyber attack visibility. Present the topic in a bit more detail with this Strategy To Minimize Cyber Attacks Comprehensive Overview Of Organization IT Assets. Use it as a tool for discussion and navigation on Operating System Distribution, Assets Distribution By Location, Endpoint By Department, Cyber Attack Visibility. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategy To Minimize Cyber Attacks Cyber Attacks Faced By Organization
Strategy To Minimize Cyber Attacks Cyber Attacks Faced By OrganizationThis slide provides information regarding the number of cyber attacks faced by the organization and its impact on IT operations and system downtime. It also provides details of percentage rise in such attacks since last month. Deliver an outstanding presentation on the topic using this Strategy To Minimize Cyber Attacks Cyber Attacks Faced By Organization. Dispense information and present a thorough explanation of Cyber Attacks, It Operations, System Downtime using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategy To Minimize Cyber Attacks Dashboard For Tracking Cyber Attack Risk Levels
Strategy To Minimize Cyber Attacks Dashboard For Tracking Cyber Attack Risk LevelsThe slide represents the dashboard for tracking cyber attack risk levels. It includes information regarding the multiple threat agents, attack methods, preventive controls along with details of risk score and infected systems. Present the topic in a bit more detail with this Strategy To Minimize Cyber Attacks Dashboard For Tracking Cyber Attack Risk Levels. Use it as a tool for discussion and navigation on Dashboard For Tracking, Cyber Attack Risk Levels, Infrastructure Controls, Preventive Controls, Detective Controls. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategy To Minimize Cyber Attacks Dashboard To Monitor Cyber Attack Incidents
Strategy To Minimize Cyber Attacks Dashboard To Monitor Cyber Attack IncidentsThis slide indicates the dashboard to monitor cyber attacks on IT assets of the firm. It includes information regarding the total cyber attack incidents both month and day wise along with the details of threat class, overall risk factor and top vulnerabilities. Deliver an outstanding presentation on the topic using this Strategy To Minimize Cyber Attacks Dashboard To Monitor Cyber Attack Incidents. Dispense information and present a thorough explanation of Dashboard To Monitor, Cyber Attack Incidents, Top Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategy To Minimize Cyber Attacks Monetary Losses Due To Cyber Crime Events
Strategy To Minimize Cyber Attacks Monetary Losses Due To Cyber Crime EventsThis slide tabulates the financial losses faced by the organization in multiple regions across the globe due to cyber crime incidents. The major losses highlighted are data, operational and revenue loss. It also contains details of solution, a cybersecurity program with risk assessment module. Deliver an outstanding presentation on the topic using this Strategy To Minimize Cyber Attacks Monetary Losses Due To Cyber Crime Events. Dispense information and present a thorough explanation of Monetary Losses, Recommended Solution, Cybersecurity Program, Risk Assessment Module using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategy To Minimize Cyber Attacks Summary Of Key Cyber Attacks Occurred
Strategy To Minimize Cyber Attacks Summary Of Key Cyber Attacks OccurredThis slide shows the summary of key of cybers attacks occurred in organization such as phishing, malware attack, denial of service, SQL injections, identity thefts. It also contains details of the cyber attacker origin such as inadvertent actors, malicious insiders. Present the topic in a bit more detail with this Strategy To Minimize Cyber Attacks Summary Of Key Cyber Attacks Occurred. Use it as a tool for discussion and navigation on Cybers Attacks Occurred, Phishing, Malware Attack, Denial Of Service, SQL Injections, Identity Thefts. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Analysis Of Phishing Attacks Impact On Business Phishing Attacks And Strategies
Analysis Of Phishing Attacks Impact On Business Phishing Attacks And StrategiesThis slide depicts the statistics of most vulnerable targets of phishing scams. The purpose of this slide is to represent the various impacts of cyber phishing attacks. These include compromised accounts, malware infections and loss of data.Present the topic in a bit more detail with this Analysis Of Phishing Attacks Impact On Business Phishing Attacks And Strategies. Use it as a tool for discussion and navigation on Phishing Impacts Experienced, Amounts Malware, Phishing Scams. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Phishing Cyber Scams On Phishing Attacks And Strategies
Impact Of Phishing Cyber Scams On Phishing Attacks And StrategiesThis slide talks about the damage caused by phishing attacks. The purpose of this slide is to explain the impact of phishing scams on organizations. The key points included are information loss, damaged credibility, direct financial loss and productivity loss.Increase audience engagement and knowledge by dispensing information using Impact Of Phishing Cyber Scams On Phishing Attacks And Strategies. This template helps you present information on six stages. You can also present information on Businesses Incur Reputational, Phishing Assault, Maintenance Reconfiguration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents Phishing Attacks And Strategies To Mitigate Them
Table Of Contents Phishing Attacks And Strategies To Mitigate ThemDeliver an outstanding presentation on the topic using this Table Of Contents Phishing Attacks And Strategies To Mitigate Them. Dispense information and present a thorough explanation of Phishing Attacks Overview, Types Phishing, Attacks Prevention using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Targeted Industries Of Cyber Phishing Attacks Phishing Attacks And Strategies
Targeted Industries Of Cyber Phishing Attacks Phishing Attacks And StrategiesThis slide represents the statistics of most targeted industries of phishing scams. The purpose of this slide is to outline the various sectors which are more prone to phishing attacks. These industries are retail, manufacturing, food and beverage, tech, etc.Present the topic in a bit more detail with this Targeted Industries Of Cyber Phishing Attacks Phishing Attacks And Strategies. Use it as a tool for discussion and navigation on Phishing Scams, Manufacturing Industry, Phishing Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Vishing Cyber Scams In Different Businesses Phishing Attacks And Strategies
Vishing Cyber Scams In Different Businesses Phishing Attacks And StrategiesThis slide demonstrates the various types of vishing scams. The purpose of this slide is to illustrate the ways in which attackers conduct scams in different businesses using vishing technique. These are banking vishing and internal revenue service vishing.Present the topic in a bit more detail with this Vishing Cyber Scams In Different Businesses Phishing Attacks And Strategies. Use it as a tool for discussion and navigation on Internal Revenue, Remote Application, Vishing Example. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Cyber Phishing Attacks With Key Strategies
Major Cyber Phishing Attacks With Key StrategiesMentioned slide showcases various cyber phishing attacks such as deceptive, spear, whaling and vishing. It provides detailed information about likelihood of attack, examples of attacks and strategies which can be implemented to overcome phishing attacks. Introducing our Major Cyber Phishing Attacks With Key Strategies set of slides. The topics discussed in these slides are Spear Phishing, Deceptive Phishing, Whaling. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Strategies To Keep Company Safe From Cyber Terrorism Attacks
Strategies To Keep Company Safe From Cyber Terrorism AttacksThis slide describes the checklist to deal with cyber terrorism threats and counter it such as go after the perpetrators and prosecute them. Introducing Strategies To Keep Company Safe From Cyber Terrorism Attacks to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Technology, Reduce, Implemented, Restoration, Organization, using this template. Grab it now to reap its full benefits.
-
 Attack And Defense Strategy Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Attack And Defense Strategy Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Attack and defense strategy colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Attack And Defense Strategy Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Attack And Defense Strategy Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Attack and defense strategy monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Cyber Attack Mitigation Strategies In Powerpoint And Google Slides Cpb
Cyber Attack Mitigation Strategies In Powerpoint And Google Slides CpbPresenting our er Attack Mitigation Strategies In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cyber Attack Mitigation Strategies This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Agenda For Strategy To Minimize Cyber Attacks Risks Ppt Icon Clipart Images
Agenda For Strategy To Minimize Cyber Attacks Risks Ppt Icon Clipart ImagesIntroducing Agenda For Strategy To Minimize Cyber Attacks Risks Ppt Icon Clipart Images to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Risk Assessment, Cyber Attacks Risks, Attacks Frequency, Cybersecurity Risk, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Strategy To Minimize Cyber Attacks Risks Ppt Icon Templates
Icons Slide For Strategy To Minimize Cyber Attacks Risks Ppt Icon TemplatesPresenting our premium Icons Slide For Strategy To Minimize Cyber Attacks Risks Ppt Icon Templates set of slides with flexible icons. The icons are designed by our group of professionals. Add these Icons Slide For Strategy To Minimize Cyber Attacks Risks Ppt Icon Templates to your presentation to make it visually appealing. Also, edit them according to your requirement. Download it and captive your audience.
-
 Strategy To Minimize Cyber Attacks Framework For Cybersecurity Risk Management
Strategy To Minimize Cyber Attacks Framework For Cybersecurity Risk ManagementThis slide indicates the framework for cybersecurity risk management. The major sub components of model are data sources, cyber intelligence and monitoring, threat and vulnerabilities, executive board and IT governance. Present the topic in a bit more detail with this Strategy To Minimize Cyber Attacks Framework For Cybersecurity Risk Management. Use it as a tool for discussion and navigation on Information Sharing, Components Of Framework, Framework For Cybersecurity, Risk Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategy To Minimize Cyber Attacks Key Approaches To Minimize Cyber Attacks Risks
Strategy To Minimize Cyber Attacks Key Approaches To Minimize Cyber Attacks RisksThis slide indicates the key approaches to minimize the risk associated with cyber attacks. The approaches discussed are update and upgrade outdated software, control accounts access, introduce signed software execution policies, regularly track network intrusions and use multifactor authentication. Increase audience engagement and knowledge by dispensing information using Strategy To Minimize Cyber Attacks Key Approaches To Minimize Cyber Attacks Risks. This template helps you present information on five stages. You can also present information on Control Accounts Access, Software Execution Policies, Multifactor Authentication, Regularly Track Network Intrusions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategy To Minimize Cyber Attacks Major Cyber Attacks Faced By Organization
Strategy To Minimize Cyber Attacks Major Cyber Attacks Faced By OrganizationThis purpose of this slide is to showcase the major cyber attacks faced by business organization. The key attacks listed are phishing, malware attack, denial of service attacks, SQL injections, and ransomware. It also provides details regarding the major IT assets impacted and primary objective of each of the attacks. Deliver an outstanding presentation on the topic using this Strategy To Minimize Cyber Attacks Major Cyber Attacks Faced By Organization. Dispense information and present a thorough explanation of Malware Attack, Denial Of Service Attack, Ransomware, Major Cyber Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategy To Minimize Cyber Attacks Mapping Of Multiple Cyber Attacks Using Risk Heat Map
Strategy To Minimize Cyber Attacks Mapping Of Multiple Cyber Attacks Using Risk Heat MapThis slide shows the mapping of cyber attacks based on the likelihood of risk occurrence and its impact. It also contains details of attacks segmentation and the control actions that must be taken such as track, monitor and mitigate against such cyber attacks. Present the topic in a bit more detail with this Strategy To Minimize Cyber Attacks Mapping Of Multiple Cyber Attacks Using Risk Heat Map. Use it as a tool for discussion and navigation on Random Malware Attack, Phishing Attack, Fraudulently Obtain, Sensitive Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategy To Minimize Cyber Attacks Multistep Approach To Conduct Cybersecurity Risk Assessment
Strategy To Minimize Cyber Attacks Multistep Approach To Conduct Cybersecurity Risk AssessmentThis slide indicates the multistep approach to conduct cybersecurity risk assessment in business organization. The major steps of process are risk identification, quantification, evaluation, mitigation and monitoring. Introducing Strategy To Minimize Cyber Attacks Multistep Approach To Conduct Cybersecurity Risk Assessment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Risk Identification, Risk Mapping, Risk Evaluation, Risk Mitigation And Monitoring, using this template. Grab it now to reap its full benefits.
-
 Strategy To Minimize Cyber Attacks Need Of Cybersecurity Program For Organization
Strategy To Minimize Cyber Attacks Need Of Cybersecurity Program For OrganizationThis slide depicts the value that a cybersecurity program with risk assessment module add to organization in terms of increased awareness of organization security landscape, identification of system vulnerabilities, actionable and prioritized list of cybersecurity risks and mitigation plan to tackle future threats. Increase audience engagement and knowledge by dispensing information using Strategy To Minimize Cyber Attacks Need Of Cybersecurity Program For Organization. This template helps you present information on four stages. You can also present information on Organization Security Landscape, Actionable And Prioritized, List Of Cybersecurity Risks, Identification Of System Vulnerabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategy To Minimize Cyber Attacks NIST Cybersecurity Framework With Subcategories
Strategy To Minimize Cyber Attacks NIST Cybersecurity Framework With SubcategoriesThis slide represents the NIST cybersecurity framework with subcategories. It also contains information regarding the software which fulfill multiple compliance requirements of NIST cybersecurity framework. Introducing Strategy To Minimize Cyber Attacks NIST Cybersecurity Framework With Subcategories to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on NIST Cybersecurity, Framework With Subcategories, Contains Information, Compliance Requirements, using this template. Grab it now to reap its full benefits.
-
 Strategy To Minimize Cyber Attacks Risk Register To Measure Cyber Attacks Vulnerabilities
Strategy To Minimize Cyber Attacks Risk Register To Measure Cyber Attacks VulnerabilitiesThis slide indicates the risk register to measure the cyber attack risk vulnerabilities faced by an organization. It includes information regarding the multiple risks in terms of vulnerability exploited, impact level, likelihood of occurrence and control recommended. Deliver an outstanding presentation on the topic using this Strategy To Minimize Cyber Attacks Risk Register To Measure Cyber Attacks Vulnerabilities. Dispense information and present a thorough explanation of Financial Transactions, Credentials Compromised, Cloud Network Compromised using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
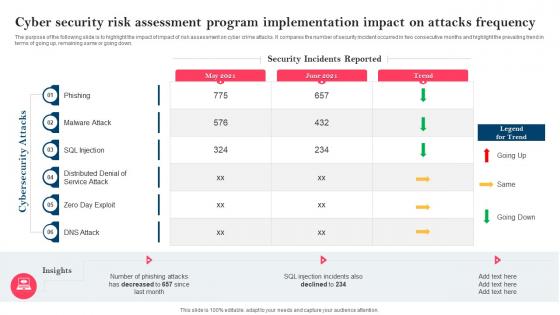 Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program Implementation
Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program ImplementationThe purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Present the topic in a bit more detail with this Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program Implementation. Use it as a tool for discussion and navigation on Cyber Security, Risk Assessment, Program Implementation, Impact On Attacks Frequency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategy To Minimize Cyber Attacks Risks For Table Of Content Ppt Icon Elements
Strategy To Minimize Cyber Attacks Risks For Table Of Content Ppt Icon ElementsIncrease audience engagement and knowledge by dispensing information using Strategy To Minimize Cyber Attacks Risks For Table Of Content Ppt Icon Elements. This template helps you present information on one stages. You can also present information on Cyber Attacks Risks, Cyber Attacks Risk Mitigation, Mitigation Plan using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategy To Minimize Cyber Attacks Strategic Plan To Mitigate Cyber Attacks
Strategy To Minimize Cyber Attacks Strategic Plan To Mitigate Cyber AttacksThe slide indicates the risk mitigation plan for the multiple cyber attacks. It also includes details of cost involved and implementation time required for each mitigation approach. Deliver an outstanding presentation on the topic using this Strategy To Minimize Cyber Attacks Strategic Plan To Mitigate Cyber Attacks. Dispense information and present a thorough explanation of Phishing Cybersecurity Attacks, Strategic Plan, Mitigate Cyber Attacks, Denial Of Service Attack using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents For Strategy To Minimize Cyber Attacks Risks
Table Of Contents For Strategy To Minimize Cyber Attacks RisksIntroducing Table Of Contents For Strategy To Minimize Cyber Attacks Risks to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Attacks Faced By Organization, Risk Heatmap, Risk Register, Mitigation Plan, Cybersecurity Risk Assessment Program, using this template. Grab it now to reap its full benefits.
-
 Adopting Strategies By Cyber Attack Type Cyber Attack Risks Mitigation
Adopting Strategies By Cyber Attack Type Cyber Attack Risks MitigationThe following slide depicts the various strategies to manage data control and breach. It includes elements such as attrition, malware, hacking, social tactic, improper usage, train and educate employees, automate identification, data management etc. Present the topic in a bit more detail with this Adopting Strategies By Cyber Attack Type Cyber Attack Risks Mitigation. Use it as a tool for discussion and navigation on Educate Employees, Data Management, Automate Attack Identification. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Multiple Strategic Cyber Security Approaches Cyber Attack Risks Mitigation
Multiple Strategic Cyber Security Approaches Cyber Attack Risks MitigationThe following slide depicts various cyber safety approaches to encrypt and back up key data to avoid information loss and improved accessibility. It includes elements such as data, application, infrastructure, network, devices, automation etc. Increase audience engagement and knowledge by dispensing information using Multiple Strategic Cyber Security Approaches Cyber Attack Risks Mitigation. This template helps you present information on one stage. You can also present information on Identities, Organization Policy, Threat Intelligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Passive Active And Offensive Cyber Security Strategies Cyber Attack Risks Mitigation
Passive Active And Offensive Cyber Security Strategies Cyber Attack Risks MitigationThe following slide showcases passive, active and offensive cyber safety techniques to ensure customer data safety. It includes elements such as inspecting vulnerabilities, penetration testing, deception technology, threat hunting etc. Increase audience engagement and knowledge by dispensing information using Passive Active And Offensive Cyber Security Strategies Cyber Attack Risks Mitigation. This template helps you present information on three stages. You can also present information on Passive Safety, Active Safety, Offensive Safety using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Stages Of Implementing Cyber Security Strategies Cyber Attack Risks Mitigation
Stages Of Implementing Cyber Security Strategies Cyber Attack Risks MitigationThe following slide highlights major stages of executing cyber security techniques to ensure effective implementation. It includes elements such as plan, analyze, upgrade, continuous improvement etc. Increase audience engagement and knowledge by dispensing information using Stages Of Implementing Cyber Security Strategies Cyber Attack Risks Mitigation. This template helps you present information on four stages. You can also present information on Plan Strategy, Implement Strategy, Analyse Strategy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Create Cyber Security Strategies Cyber Attack Risks Mitigation
Steps To Create Cyber Security Strategies Cyber Attack Risks MitigationThe following slide illustrates some steps to create and implement cybersecurity techniques. It includes elements such as determining threat type, selecting security framework, optimizing plan, implementing strategy etc. Introducing Steps To Create Cyber Security Strategies Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Comprehend Threat Landscape, Evaluate Cybersecurity Maturity, Optimize Cybersecurity Program, using this template. Grab it now to reap its full benefits.
-
 Strategic Cyber Security Action Plan Cyber Attack Risks Mitigation
Strategic Cyber Security Action Plan Cyber Attack Risks MitigationThe following slide depicts action plan to minimize impact of cyber attacks. It includes elements such as understand, develop, deliver, assess organizational principles, evaluate alternatives, examine possible alternatives, execute actions etc. Increase audience engagement and knowledge by dispensing information using Strategic Cyber Security Action Plan Cyber Attack Risks Mitigation. This template helps you present information on three stages. You can also present information on Understand, Develop, Deliver, Organizational Principles using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategic Framework For Cyber Attack Reduction Cyber Attack Risks Mitigation
Strategic Framework For Cyber Attack Reduction Cyber Attack Risks MitigationThe following slide showcases the framework to plan cyber-attack reduction actions and responsible heads. It includes elements such as strategic, tactical, operational, technical etc. Introducing Strategic Framework For Cyber Attack Reduction Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strategic, Tactical, Operational, Technical, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Cyber Attack Risks Mitigation Strategies Ppt Slides
Table Of Contents For Cyber Attack Risks Mitigation Strategies Ppt SlidesIntroducing Table Of Contents For Cyber Attack Risks Mitigation Strategies Ppt Slides to increase your presentation threshold. Encompassed with fifteen stages, this template is a great option to educate and entice your audience. Dispence information on Security Strategies, Strategic Framework, Password Management, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Plan Key Parameters To Select Cyber Security Containment Strategy
Cyber Security Attacks Response Plan Key Parameters To Select Cyber Security Containment StrategyThis slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Attacks Response Plan Key Parameters To Select Cyber Security Containment Strategy. This template helps you present information on five stages. You can also present information on Cyber Security, Containment Strategy, Incident Management Solutions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Attacks Response Plan Strategies To Analyze Cyber Security Incidents
Cyber Security Attacks Response Plan Strategies To Analyze Cyber Security IncidentsThis slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Introducing Cyber Security Attacks Response Plan Strategies To Analyze Cyber Security Incidents to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Profile Network And Systems, Understand Normal Behaviors, Perform Event Correlation, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Communication Strategy Cyber Security Attacks Response Plan
Cyber Security Incident Communication Strategy Cyber Security Attacks Response PlanThis slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. Introducing Cyber Security Incident Communication Strategy Cyber Security Attacks Response Plan to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Senior Management, Communication Strategy, Stakeholder Needs, Suppliers, using this template. Grab it now to reap its full benefits.
-
 Key Strategies To Mitigate Phishing Attack
Key Strategies To Mitigate Phishing AttackThis slide showcases protective measures against phishing attacks to save personal information from being stolen. It includes free anti phishing, analyzing phishing scams, password rotations, etc. Introducing our premium set of slides with Key Strategies To Mitigate Phishing Attack. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Scam Looks, Unsecured Site, Link. So download instantly and tailor it with your information.
-
 Cybersecurity Risk Assessment Program Strategic Plan To Mitigate Cyber Attacks
Cybersecurity Risk Assessment Program Strategic Plan To Mitigate Cyber AttacksThe slide indicates the risk mitigation plan for the multiple cyber attacks. It also includes details of cost involved and implementation time required for each mitigation approach. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Assessment Program Strategic Plan To Mitigate Cyber Attacks. Dispense information and present a thorough explanation of Strategic Plan, Mitigate Cyber Attacks, Malware Attack, Recommended Mitigation Strategy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them IT Illustration
Phishing Attacks And Strategies To Mitigate Them IT IllustrationThis coloured powerpoint Illustration provides a visual representation of phishing attacks and strategies to mitigate them. It includes a detailed overview of the different types of phishing attacks, the risks associated with them, and effective strategies to reduce the chances of becoming a victim. Ideal for IT professionals and security experts.
-
 Measures For Successful Phishing Awareness Phishing Attacks And Strategies
Measures For Successful Phishing Awareness Phishing Attacks And StrategiesThis slide talks about the measures for successful phishing awareness campaign. These include recognize phish, train staff while keeping their individual needs in mind, action oriented employee engagement, plan constant training sessions, etc.Increase audience engagement and knowledge by dispensing information using Measures For Successful Phishing Awareness Phishing Attacks And Strategies. This template helps you present information on six stages. You can also present information on Employee Engagement, Interested Awareness Training, Training Strategy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 30 60 90 Days Plan To Secure Organizations Phishing Attacks And Strategies
30 60 90 Days Plan To Secure Organizations Phishing Attacks And StrategiesThis slide represents 30 60 90 plan to protect companies and their employees from phishing attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.Introducing 30 60 90 Days Plan To Secure Organizations Phishing Attacks And Strategies to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Conduct Phishing, Deploy Anti Phishing, Implement Multi Factor, using this template. Grab it now to reap its full benefits.
-
 About Angler Phishing Working And Example Phishing Attacks And Strategies
About Angler Phishing Working And Example Phishing Attacks And StrategiesThis slide talks about the angler phishing attacks conducted on internet using social media platforms. The purpose of this slide is to illustrate how fraudulent tweets or texts containing malicious links and misleading information, can be used by scammers to trick individuals.Present the topic in a bit more detail with this About Angler Phishing Working And Example Phishing Attacks And Strategies. Use it as a tool for discussion and navigation on Sensitive Information, Fraudster Establishes, Working Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 About Email Phishing Overview And Impact Phishing Attacks And Strategies
About Email Phishing Overview And Impact Phishing Attacks And StrategiesThis slide talks about the email phishing cyber scams in which attacker sends fake mails to the target. The purpose of this slide to provide few examples of cyber phishing emails containing malicious links and attachments to target different organizations.Deliver an outstanding presentation on the topic using this About Email Phishing Overview And Impact Phishing Attacks And Strategies. Dispense information and present a thorough explanation of Compliance Issues, Productivity Loss, Data Breaches using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 About Evil Twin Phishing Overview And Example Phishing Attacks And Strategies
About Evil Twin Phishing Overview And Example Phishing Attacks And StrategiesThis slide talks about evil twin cyber attacks. The purpose of this slide is to outline the types of information that can be accessed by scammers of evil twin attacks. This slide also illustrates the flow of evil twin scams which include legitimate Wi Fi, fake access point, etc.Present the topic in a bit more detail with this About Evil Twin Phishing Overview And Example Phishing Attacks And Strategies. Use it as a tool for discussion and navigation on Personal Information, Enables Hacker, Managed Scammer. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 About Identity Theft Overview And Techniques Phishing Attacks And Strategies
About Identity Theft Overview And Techniques Phishing Attacks And StrategiesThis slide talks about the major crime committed by phishers named as identity theft. The purpose of this slide is to outline the ways of stealing information such as robbery, computer fraud, social networking sites, mail theft and dumpster diving.Deliver an outstanding presentation on the topic using this About Identity Theft Overview And Techniques Phishing Attacks And Strategies. Dispense information and present a thorough explanation of Personal Advantage, Romance Fraud, Social Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 About Man In The Middle Phishing Scams Phishing Attacks And Strategies
About Man In The Middle Phishing Scams Phishing Attacks And StrategiesThis slide demonstrates the idea behind man in the middle phishing attacks. The purpose of this slide is to illustrate the concept of MITM attack by comparing normal scenario and MITM attack which includes attacker, proxy server, real website, etc.Present the topic in a bit more detail with this About Man In The Middle Phishing Scams Phishing Attacks And Strategies. Use it as a tool for discussion and navigation on Safe Authentication, Manipulate Sensitive, Communicating Directly. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 About Pharming Phishing Identification And Phishing Attacks And Strategies
About Pharming Phishing Identification And Phishing Attacks And StrategiesThis slide talks about the pharming phishing cyber scams. The purpose of this slide is to illustrate the ways of recognizing pharming scams such as URL, design and HTTP vs HTTPS. This slide also illustrates the architecture of pharming phishing attack.Deliver an outstanding presentation on the topic using this About Pharming Phishing Identification And Phishing Attacks And Strategies. Dispense information and present a thorough explanation of Recognizing Pharming Scams, Architecture Pharming, Uniform Resource using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 About Phishing Attacks Overview And Impact Phishing Attacks And Strategies
About Phishing Attacks Overview And Impact Phishing Attacks And StrategiesThis slide demonstrates the overview of cyber phishing attacks. The purpose of this slide is to talk about the effectiveness of phishing scams. This slide also outlines the issues which can be caused by phishing attacks such as disclosure of private data, etc.Increase audience engagement and knowledge by dispensing information using About Phishing Attacks Overview And Impact Phishing Attacks And Strategies. This template helps you present information on one stage. You can also present information on Illicit Transactions, Executed Through, Illicit Transactions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 About Pop Up Phishing Overview And Examples Phishing Attacks And Strategies
About Pop Up Phishing Overview And Examples Phishing Attacks And StrategiesThis slide talks about the pop up phishing attacks conducted by sending pop up messages to the targets. The purpose of this slide is to illustrate how fraudulent and mis leading pop ups are displayed to the users which are clone of the original pop ups.Present the topic in a bit more detail with this About Pop Up Phishing Overview And Examples Phishing Attacks And Strategies. Use it as a tool for discussion and navigation on About Pop Up Phishing, Overview Examples. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 About Search Engine Phishing Overview Phishing Attacks And Strategies
About Search Engine Phishing Overview Phishing Attacks And StrategiesThis slide talks about search engine phishing scams. The purpose of this slide is to explain how phishers use their own built websites to trick victims. This slide also represents examples of search engine phishing websites which are indexed by reliable browsers.Introducing About Search Engine Phishing Overview Phishing Attacks And Strategies to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Victims Reputation, Account Information, Consumers Standard, using this template. Grab it now to reap its full benefits.
-
 About Smishing Attacks Working And Example Phishing Attacks And Strategies
About Smishing Attacks Working And Example Phishing Attacks And StrategiesThis slide talks about the smishing cyber attacks conducted by sending text messages to the targets. The purpose of this slide is to illustrate how fraudulent texts are sent to the users which contains malicious links and other mis leading information.Increase audience engagement and knowledge by dispensing information using About Smishing Attacks Working And Example Phishing Attacks And Strategies. This template helps you present information on three stages. You can also present information on Criminal Investigation, Arrest Warrant, Provide Personal using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 About Spear Phishing Overview And Example Phishing Attacks And Strategies
About Spear Phishing Overview And Example Phishing Attacks And StrategiesThis slide talks about spear phishing cyber attacks in which scammer targets a specific individual or specific group of persons. The purpose of this slide is to illustrate example of a mail used by phishers to conduct spear phishing cyber attacks.Deliver an outstanding presentation on the topic using this About Spear Phishing Overview And Example Phishing Attacks And Strategies. Dispense information and present a thorough explanation of Complaint Department, Businesses Everyone, Phisher Claims using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 About Vishing Attacks Overview And Identification Phishing Attacks And Strategies
About Vishing Attacks Overview And Identification Phishing Attacks And StrategiesThis slide talks about the vishing cyber attacks. The purpose of this slide is to explain the vishing technique used by phishers to scam victims. This slide also outlines the signs of vishing attack such as call from unknown number, act as an authority, etc.Introducing About Vishing Attacks Overview And Identification Phishing Attacks And Strategies to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Sensitive Information, Cybercriminal Calls, Pretend Conduct, using this template. Grab it now to reap its full benefits.
-
 About Whale Phishing Ceo Fraud Overview And Phishing Attacks And Strategies
About Whale Phishing Ceo Fraud Overview And Phishing Attacks And StrategiesThis slide talks about the whaling phishing attack which is also known as CEO fraud. The purpose of this slide is to explain how attackers target senior executives of organizations to conduct whale phishing cyber attacks by sending fraud mails to the employees.Present the topic in a bit more detail with this About Whale Phishing Ceo Fraud Overview And Phishing Attacks And Strategies. Use it as a tool for discussion and navigation on Beneficiary Account Details, Targeting Senior Executives, Pending Payment. This template is free to edit as deemed fit for your organization. Therefore download it now.





