Powerpoint Templates and Google slides for Attack Strategy
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Man In The Middle MITM Phishing Attack Diagram
Phishing Attacks And Strategies To Mitigate Them V2 Man In The Middle MITM Phishing Attack DiagramThis slide demonstrates the working flow of man-in-the-middle phishing attacks using MITM phishing toolkit cloud server. This slide also elaborates the various real-world examples of MITM attacks such as Equifaxs mobile application, superfish and DigiNotar. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Man In The Middle MITM Phishing Attack Diagram. Dispense information and present a thorough explanation of Phishing Attack Diagram, Equifaxs Mobile Application, Toolkit Cloud Server, Intended Website Server using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
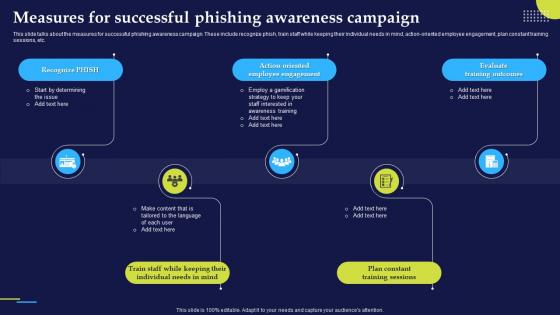 Phishing Attacks And Strategies To Mitigate Them V2 Measures For Successful Phishing Awareness Campaign
Phishing Attacks And Strategies To Mitigate Them V2 Measures For Successful Phishing Awareness CampaignThis slide talks about the measures for successful phishing awareness campaign. These include recognize phish, train staff while keeping their individual needs in mind, action-oriented employee engagement, plan constant training sessions, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Measures For Successful Phishing Awareness Campaign to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Action Oriented Employee Engagement, Evaluate Training Outcomes, Phishing Awareness Campaign, Plan Constant Training Sessions, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Multi Layered Approach To Phishing Defenses
Phishing Attacks And Strategies To Mitigate Them V2 Multi Layered Approach To Phishing DefensesThis slide represents the multi-layered approach to phishing defenses. These include create difficulty for attackers to reach users, guide users in identifying and reporting phishing emails, save your organization from unexpected phishing scams, etc. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Multi Layered Approach To Phishing Defenses. Use it as a tool for discussion and navigation on Multi Layered Approach, Reporting Phishing Emails, Unexpected Phishing Scams. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Pharming Phishing Types And Prevention Techniques
Phishing Attacks And Strategies To Mitigate Them V2 Pharming Phishing Types And Prevention TechniquesThis slide demonstrates the different types pf pharming phishing scams. The primary types include malware-based pharming and DNS pharming. This slide also outlines the ways which helps to prevent a pharming attack such as verify the URL, install VPN, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Pharming Phishing Types And Prevention Techniques. Dispense information and present a thorough explanation of Pharming Phishing Scams, Malware Based Pharming, Pharming Attack, Prevention Techniques using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Phishing Awareness Training Program For Employees
Phishing Attacks And Strategies To Mitigate Them V2 Phishing Awareness Training Program For EmployeesThis slide represents the training program for employees which will help them to prevent various cyber security scams in business. The purpose of this slide is to outline the mode, venue and schedule for the different training programs. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Phishing Awareness Training Program For Employees. This template helps you present information on one stages. You can also present information on Phishing Awareness Training, Program For Employees, Training Programs, Security Scams In Business using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Popular Man In The Middle Phishing Kits Used
Phishing Attacks And Strategies To Mitigate Them V2 Popular Man In The Middle Phishing Kits UsedThis slide outlines the various phishing kits used by attackers to conduct man-in-the-middle scams. The purpose of thus slide is to describe the reported year and use of different MITM kits such as Evilginx2, Modlishka, Muraena, EvilnoVNC and EvilProxy. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Popular Man In The Middle Phishing Kits Used. Use it as a tool for discussion and navigation on Creates Special Tokens, Uniform Resource Locator, Expose Phishing Content, Stolen Session Cookie. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Preventive Measures For Man In The Middle Cyber
Phishing Attacks And Strategies To Mitigate Them V2 Preventive Measures For Man In The Middle CyberThis slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Preventive Measures For Man In The Middle Cyber to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Secure Connections, Avoid Phishing Emails, Endpoint Security, Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Primary Techniques Employed In Phishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Primary Techniques Employed In Phishing AttacksThis slide demonstrates the ways utilized by phishers to attack victims. The purpose of this slide is to outline the different methods used by attackers to trick victims. The primary means of attacks are text messages, emails and phone calls from unknown sources. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Primary Techniques Employed In Phishing Attacks. This template helps you present information on three stages. You can also present information on Primary Techniques Employed, Phishing Attacks, Phishers To Attack Victims, Attackers To Trick Victims using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Real World Examples Of Smishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Real World Examples Of Smishing AttacksThis slide demonstrates the real-world example of smishing cyber attacks which targeted different individuals and organizations. The popular scams are early access apple iPhone 12 scam, USPS and FedEx scams and mandatory online COVID-19 test scam. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Real World Examples Of Smishing Attacks to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Real World Examples, Smishing Attacks, Smishing Cyber Attacks, Individuals And Organizations, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Resources And Training That Companies Can Provide
Phishing Attacks And Strategies To Mitigate Them V2 Resources And Training That Companies Can ProvideThis slide demonstrates the resources and training that can be provided by companies to their staff. These include employee training, check to see if you have already been breached, be aware of the various phishing attacks, invest in security education, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Resources And Training That Companies Can Provide. This template helps you present information on five stages. You can also present information on Employee Training, Security Education, Phishing Attacks, Resources And Training using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Roadmap To Secure Organizations From Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Roadmap To Secure Organizations From PhishingThis slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Roadmap To Secure Organizations From Phishing to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Implement Technical Controls, Establish Policies And Procedures, Employee Training, Baseline Security Assessment, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Steps To Identify Whaling Phishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Steps To Identify Whaling Phishing AttacksThis slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Steps To Identify Whaling Phishing Attacks. This template helps you present information on six stages. You can also present information on Flag Emails Received, Near Similar Email Domains, Spot Grammar, Cross Verify Sensitive Requests using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Steps To Take After Spear Phishing Scam
Phishing Attacks And Strategies To Mitigate Them V2 Steps To Take After Spear Phishing ScamIntroducing Phishing Attacks And Strategies To Mitigate Them V2 Steps To Take After Spear Phishing Scam to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing Scam, Change Your Passwords, Backup Your Files, Conduct A Hardware Scan, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Strategies To Identify Smishing Cyber Scams
Phishing Attacks And Strategies To Mitigate Them V2 Strategies To Identify Smishing Cyber ScamsThis slide talks about the various methods of identifying smishing cyber attacks. The purpose of this slide is to help users identify smishing scams. These include suspicious texts from unknown numbers, unrequested links and files, money transfer requests, etc. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Strategies To Identify Smishing Cyber Scams. Use it as a tool for discussion and navigation on Smishing Cyber Attacks, Smishing Scams, Unrequested Links And Files, Money Transfer Requests. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Techniques Used By Cybercriminals To Conduct
Phishing Attacks And Strategies To Mitigate Them V2 Techniques Used By Cybercriminals To ConductThis slide demonstrates the techniques used by scammers to conduct watering hole attacks. These methods are cross-site scripting, DMS cache poisoning, drive-by downloads, malvertising, etc. This slide also outlines common intelligence gathering methods. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Techniques Used By Cybercriminals To Conduct. Use it as a tool for discussion and navigation on Social Networking Sites, Demographic Information From Websites, Social Engineering, Keyloggers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Timeline To Secure Organizations From Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Timeline To Secure Organizations From PhishingThis slide shows the timeline to protect organizations from phishing for different organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Timeline To Secure Organizations From Phishing. This template helps you present information on five stages. You can also present information on Implement Technical Controls, Employee Training, Establish Policies And Procedures, Timely Evaluation And Updates using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Tools Provided By Google To Prevent Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Tools Provided By Google To Prevent PhishingThis slide demonstrates the different tools provided by Google to prevent and report cyber phishing scams. These include to spot phishing mails with the help of Gmail, utilize safe browsing in chrome, look for unsafe saved passwords, password alert for chrome, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Tools Provided By Google To Prevent Phishing. Dispense information and present a thorough explanation of Safe Browsing In Chrome, Phishing Mails Detection With Gmail, Two Step Verification, Password Alert For Chrome using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Tricks Employed By Malicious Websites To Scam
Phishing Attacks And Strategies To Mitigate Them V2 Tricks Employed By Malicious Websites To ScamThis slide talks about various tricks utilized by fraudulent websites to scam the visitors. The purpose of this slide is to make users aware of such different tricks such as free or discount offers, low interest rates or free credit cards, employment opportunities, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Tricks Employed By Malicious Websites To Scam to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Employment Opportunities, Emergency Warnings, Malicious Websites, Scam Victims, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Understanding The Process Of E Mail Based Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Understanding The Process Of E Mail Based PhishingThis slide demonstrates the procedure of email-based phishing attacks. The purpose of this slide is to explain how fake websites are used by attackers to get the sensitive data of the users. The key components include database, fake website, etc. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Understanding The Process Of E Mail Based Phishing. Use it as a tool for discussion and navigation on Email Based Phishing Attacks, Fake Website, Phishing Email, Original Website. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Prevention Email Signing And Code
Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Prevention Email Signing And CodeThis slide talks about the techniques which can help in protecting organizations from phishing and vishing attacks. The purpose of this slide is to explain two important methods of preventing cyber scams. These techniques are email signing and code signing. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Prevention Email Signing And Code. Dispense information and present a thorough explanation of Vishing Attacks Prevention, Email Signing And Code Signing, Preventing Cyber Scams using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Warning Signs Of Pop Up Phishing Scams
Phishing Attacks And Strategies To Mitigate Them V2 Warning Signs Of Pop Up Phishing ScamsThis slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Warning Signs Of Pop Up Phishing Scams to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Terrible Pop Up Advertisement, Pop Up Phishing Cyber Attacks, Install Their Malware, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Why Businesses Fall Victim To Phishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Why Businesses Fall Victim To Phishing AttacksThis slide outlines the various reasons responsible for businesses to fall victim to different phishing attacks. These include inadequate employee training, never evaluate the success of the training, careless browsing habits of the employees, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Why Businesses Fall Victim To Phishing Attacks. This template helps you present information on five stages. You can also present information on Inadequate Employee Training, Training Or Policy Improvement, Organizations Are Unaware, Changing Phishing Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Working Of Phishing Training Programs
Phishing Attacks And Strategies To Mitigate Them V2 Working Of Phishing Training ProgramsIntroducing Phishing Attacks And Strategies To Mitigate Them V2 Working Of Phishing Training Programs to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Start With Employee Training, Make Fictitious Phishing Campaigns, Track Progress And Upgrade, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Working Of Watering Hole Phishing Attack
Phishing Attacks And Strategies To Mitigate Them V2 Working Of Watering Hole Phishing AttackThis slide represents the working process of watering hole phishing attacks. The purpose of this slide is to illustrate the flow diagram of watering hole phishing scams. The key points include research and identification, analysis, preparation and execution. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Working Of Watering Hole Phishing Attack. This template helps you present information on four stages. You can also present information on Analysis, Research And Identification, Preparation, Execution, Phishing Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Working Procedure Of Spear Phishing Attack
Phishing Attacks And Strategies To Mitigate Them V2 Working Procedure Of Spear Phishing AttackThis slide illustrates the structure of spear phishing attack. The purpose of this slide is to explain the working flow of spear phishing attack. The key components include attacker, phishing email, targeted users, exploited system, internal network, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Working Procedure Of Spear Phishing Attack to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Email, Targeted Users, Exploited System, Internal Network, Attacker, using this template. Grab it now to reap its full benefits.
-
 Real World Examples Of Watering Hole Phishing Attacks And Strategies To Mitigate Them V2
Real World Examples Of Watering Hole Phishing Attacks And Strategies To Mitigate Them V2This slide describes the real-world examples of watering hole phishing scams. These include Facebook, Twitter, Microsoft, and Apple scam, LuckyMouse scam, International Civil Aviation Organization ICAO scam, Ccleaner scam and Holy Water scam. Increase audience engagement and knowledge by dispensing information using Real World Examples Of Watering Hole Phishing Attacks And Strategies To Mitigate Them V2. This template helps you present information on four stages. You can also present information on International Civil Aviation, Organization Scam, Watering Hole Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Content For Phishing Attacks And Strategies To Mitigate Them V2
Table Of Content For Phishing Attacks And Strategies To Mitigate Them V2Introducing Table Of Content For Phishing Attacks And Strategies To Mitigate Them V2 to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Attacks Prevention, Phishing Attacks Awareness Training, Phishing Attacks Introduction, using this template. Grab it now to reap its full benefits.
-
 Ransomware In Digital Age Effective Strategies For Ransomware Attack Negotiation
Ransomware In Digital Age Effective Strategies For Ransomware Attack NegotiationThis slide highlights the negotiation steps to take into consideration while paying a ransom, which includes a team-based approach to deal with ransom negation and having cybersecurity experts to make a better deal during negotiations. Deliver an outstanding presentation on the topic using this Ransomware In Digital Age Effective Strategies For Ransomware Attack Negotiation. Dispense information and present a thorough explanation of Professional Conduct, Time Extension, Innovative Negotiation Approaches, Team Based Approach using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ransomware In Digital Age RACI Matrix For Ransomware Attacks Prevention Strategy
Ransomware In Digital Age RACI Matrix For Ransomware Attacks Prevention StrategyThis slide showcases a RACI matrix for the ransomware prevention plan, outlining the appropriate roles and steps to be taken during a ransomware attack. It includes tasks such as incident registration, conduct initial triage, and classification assignment etc. Present the topic in a bit more detail with this Ransomware In Digital Age RACI Matrix For Ransomware Attacks Prevention Strategy. Use it as a tool for discussion and navigation on Ransomware Attacks, Prevention Strategy, Classification Assignment, Conduct Initial Triage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attacks Prevention Roadmap To Implement Social Engineering Prevention Strategies
Social Engineering Attacks Prevention Roadmap To Implement Social Engineering Prevention StrategiesThis slide represents the roadmap to prevent social engineering attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. Introducing Social Engineering Attacks Prevention Roadmap To Implement Social Engineering Prevention Strategies to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Establish Policies And Procedures, Implement Technical Controls, Social Engineering Prevention Strategies, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Attacks Prevention Social Engineering Prevention Strategies For Safe Network Use
Social Engineering Attacks Prevention Social Engineering Prevention Strategies For Safe Network UseThis slide represents the protective measures for users to practice safe networking. The best practices mentioned in this slide are restrict others from connecting to primary wi-fi network, use a VPN, security of network-connected devices, etc. Introducing Social Engineering Attacks Prevention Social Engineering Prevention Strategies For Safe Network Use to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Practice Safe Networking, Primary Wifi Network, Security Of Network Connected Devices, Social Engineering Prevention Strategies, using this template. Grab it now to reap its full benefits.
-
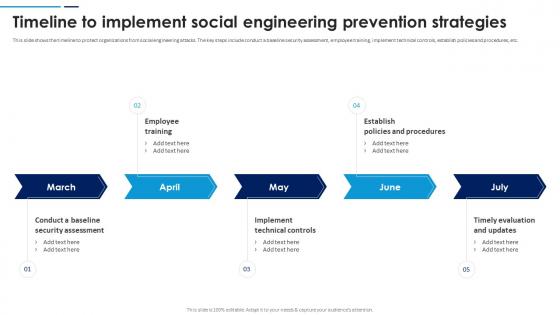 Social Engineering Attacks Prevention Timeline To Implement Social Engineering Prevention Strategies
Social Engineering Attacks Prevention Timeline To Implement Social Engineering Prevention StrategiesThis slide shows the timeline to protect organizations from social engineering attacks. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. Introducing Social Engineering Attacks Prevention Timeline To Implement Social Engineering Prevention Strategies to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Establish Policies And Procedures, Timely Evaluation And Updates, Implement Technical Controls, Employee Training, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Prevention Strategies For Safe Communication Social Engineering Attacks Prevention
Social Engineering Prevention Strategies For Safe Communication Social Engineering Attacks PreventionThis slide discusses several social engineering mitigation techniques. These include avoid clicking on links in emails and texts, use multi-factor authentication, select strong passwords, avoid sharing personal information, beware of internet friendships, etc. Introducing Social Engineering Prevention Strategies For Safe Communication Social Engineering Attacks Prevention to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering Prevention, Strategies For Safe Communication, Multi Factor Authentication, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Prevention Strategies For Safe Device Usage Social Engineering Attacks Prevention
Social Engineering Prevention Strategies For Safe Device Usage Social Engineering Attacks PreventionThe purpose of this slide is to represent the best practices for safe device usage. These safety measures include internet security software, never leave devices unsecured in public places, keep software updated and inspect all internet accounts. Increase audience engagement and knowledge by dispensing information using Social Engineering Prevention Strategies For Safe Device Usage Social Engineering Attacks Prevention. This template helps you present information on four stages. You can also present information on Internet Security Software, Keep Software Updated, Inspect All Internet Accounts, Devices Unsecured In Public using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Analyse Impact Of Cyber Attack On Valuable Implementing Strategies To Mitigate Cyber Security Threats
Analyse Impact Of Cyber Attack On Valuable Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the consequences of data breach threats to prevent information leakage. It mainly includes elements such as impact on revenue, protection cost, liability if lost, weightage criteria, asset importance etc. Deliver an outstanding presentation on the topic using this Analyse Impact Of Cyber Attack On Valuable Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Criteria, Impact On Revenue, Protection Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Prevent Cyber Attacks Implementing Strategies To Mitigate Cyber Security Threats
Best Practices To Prevent Cyber Attacks Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates some activities to minimize the probability of cybercrimes within the organization. It includes elements such as utilizing anti virus, preventing to open suspicious emails, keeping systems up to date etc. Introducing Best Practices To Prevent Cyber Attacks Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Leverage Firewalls, Prevent Opening Suspicious Emails using this template. Grab it now to reap its full benefits.
-
 Classify Assets Vulnerable To Cyber Attack Implementing Strategies To Mitigate Cyber Security Threats
Classify Assets Vulnerable To Cyber Attack Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts some major assets that are more prone to cyber attack. It mainly includes elements such as sales record, sales lead record, company internal database, customer and product information etc. Present the topic in a bit more detail with this Classify Assets Vulnerable To Cyber Attack Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Sales Record, Customer Database, Product Database This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security Threats
Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the negative impact of cyber crimes on business to build control actions and strategies. It includes key elements such as rising costs, reputational damage, operational disruption, loss of revenue etc. Introducing Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Rising Cost, Reputational Damage, Operational Disruption using this template. Grab it now to reap its full benefits.
-
 Types Of Cyber Attacks Encountered By Employees Implementing Strategies To Mitigate Cyber Security Threats
Types Of Cyber Attacks Encountered By Employees Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the various types of cyber attacks faced by staff to determine and formulate action plan. It includes elements such as malware, ransomware, man in the middle, phishing, denial of service tec. Introducing Types Of Cyber Attacks Encountered By Employees Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Malware, Ransomware, Phishing using this template. Grab it now to reap its full benefits.
-
 Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access Management
Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access ManagementThe following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Present the topic in a bit more detail with this Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access Management Use it as a tool for discussion and navigation on Access Request, Approval Rules, Session Proxy This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategies To Ensure Information Security From Ransomware Attacks
Strategies To Ensure Information Security From Ransomware AttacksThis slide highlights techniques for securing information against ransomware attacks. The purpose of this slide is to assist professionals in ensuring business continuity and minimizing downtime. It includes elements such as email security, patch updates, network segmentation, etc. Introducing our premium set of slides with Strategies To Ensure Information Security From Ransomware Attacks. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Control, Data Encryption, Awareness. So download instantly and tailor it with your information.
-
 Cloud Mitigation Strategies For DOS Attack Prevention
Cloud Mitigation Strategies For DOS Attack PreventionFollowing slide showcases DOS attack prevention cloud mitigation strategies for early threat detection and resolving it. It further covers paths for business as usual and when DOS attacks are detected. Introducing our premium set of slides with name Cloud Mitigation Strategies For DOS Attack Prevention. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Internet, Service Provider, Cloud Mitigation Strategies. So download instantly and tailor it with your information.
-
 Botnet Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Botnet Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases Botnet attack with mitigation strategies, key elements and example. It also includes mitigation strategies such as cyber security measures and network monitoring.Introducing Botnet Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Key Elements, Mitigation Strategies, Example, using this template. Grab it now to reap its full benefits.
-
 Cyber Attacks Detection In Iot Systems Strategic Guide To Implement Strategy SS
Cyber Attacks Detection In Iot Systems Strategic Guide To Implement Strategy SSPresent the topic in a bit more detail with this Cyber Attacks Detection In Iot Systems Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Social Media, Gamepad, Firewall, Storage, Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Espionage Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Cyber Espionage Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases Cyber Espionage attack with mitigation strategies and example. It includes mitigation strategies such as regular security audits and threat intelligence.Increase audience engagement and knowledge by dispensing information using Cyber Espionage Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS. This template helps you present information on three stages. You can also present information on Key Elements, Mitigation Strategies, Example using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 DNS Spoofing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
DNS Spoofing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the DNS spoofing attack with mitigation strategies and example. It also includes mitigation strategies such as use DNSSEC, use trusted DNS servers and frequent monitoring DNS software.Introducing DNS Spoofing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Description, Mitigation Strategies, Example, using this template. Grab it now to reap its full benefits.
-
 Eavesdropping Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Eavesdropping Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the Eavesdropping attack with mitigation strategies and example. It also includes mitigation strategies such as secure networks and endpoint security.Increase audience engagement and knowledge by dispensing information using Eavesdropping Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS. This template helps you present information on three stages. You can also present information on Description, Mitigation Strategies, Example using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Man In The Middle Mitm Attacks In Cyberterrorism Strategic Guide To Implement Strategy SS
Man In The Middle Mitm Attacks In Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the Man-in-the-Middle MITM Attacks in cyber terrorism. It includes mitigation startegies such as encryption, PKI, network security, 2FA and secure Wi-Fi.Introducing Man In The Middle Mitm Attacks In Cyberterrorism Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Mitigation Strategies, Account Security, Network Security, Encryption, using this template. Grab it now to reap its full benefits.
-
 Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the Phishing attack with mitigation strategies and its example. It also includes mitigation strategies such as user education, email filtering, MFA and incident reaction strategies.Introducing Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Mitigation Strategies, Example, Phishing Attack, Ideological Purposes, using this template. Grab it now to reap its full benefits.
-
 Ransomware Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Ransomware Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the Ransomware attack with mitigation strategies and example. It also includes mitigation strategies such as regular backups, email security and antivirus and anti-malware.Increase audience engagement and knowledge by dispensing information using Ransomware Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS. This template helps you present information on three stages. You can also present information on Description, Mitigation Strategies, Example, Encrypts Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Spear Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Spear Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the Spear phishing attack with mitigation strategies and its example. It also includes mitigation strategies such as email filtering, Multi-factor authentication MFA and network segmentation.Increase audience engagement and knowledge by dispensing information using Spear Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS. This template helps you present information on three stages. You can also present information on Description, Mitigation Strategies, Example, Presidential Election using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SQL Injection Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
SQL Injection Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the SQL injection attack with mitigation strategies and example. It also includes mitigation strategies such as parameterized SQL statements, install a WAF and restrict the database users privileges.Introducing SQL Injection Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Description, Mitigation Strategies, Example, Seize System Control, using this template. Grab it now to reap its full benefits.
-
 Train Employees On Cyber Attack Prevention Strategic Guide To Implement Strategy SS
Train Employees On Cyber Attack Prevention Strategic Guide To Implement Strategy SSThis slide showcases the Train employees on cyber attack prevention. It includes techniques such as email impersonation, vigilance in clicking links, verification of email addresses and use of common sense.Present the topic in a bit more detail with this Train Employees On Cyber Attack Prevention Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Threat Scenario, Description, Employee Awareness. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Trojan Horses Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Trojan Horses Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the Trojan horses attack with mitigation strategies and example. It includes mitigation strategies such as use updated version of antivirus and regular updates of operating systems.Introducing Trojan Horses Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Description, Mitigation Strategies, Example, using this template. Grab it now to reap its full benefits.
-
 Whale Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Whale Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases Whale phishing attack with mitigation strategies and its example. It includes mitigation strategies such as email filtering, Multi-factor authentication MFA and updates and patching.Increase audience engagement and knowledge by dispensing information using Whale Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS. This template helps you present information on three stages. You can also present information on Mitigation Strategies, Description, Example, Email Filtering using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 XSS Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
XSS Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the XSS attack with mitigation strategies and example. It includes mitigation strategies such as content security policy and web application firewalls.Increase audience engagement and knowledge by dispensing information using XSS Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS. This template helps you present information on three stages. You can also present information on Description, Mitigation Strategies, Example, Content Security Policy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategies To Enhance Protection Against Supply Chain Attacks
Strategies To Enhance Protection Against Supply Chain AttacksThis slide represents various strategies that help companies to effectively identify supply chain attacks and protect against them. It includes various strategies such as implementing zero trust, patching and vulnerability detection, and using malware prevention. Presenting our well structured Strategies To Enhance Protection Against Supply Chain Attacks. The topics discussed in this slide are Implement Zero Trust, Use Malware Prevention, Patching And Vulnerability Detection. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Training Plan For Detecting Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SS
Training Plan For Detecting Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SSThis slide provides details about the training plan designed to help employees detect phishing attacks. It covers training topics such as identifying general signs of phishing attacks, signs of phishing in email etc.Present the topic in a bit more detail with this Training Plan For Detecting Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SS. Use it as a tool for discussion and navigation on Training Sessions, Timeline, Trainer, Training Topic. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Training Plan For Preventing Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SS
Training Plan For Preventing Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines a training plan to help employees effectively prevent phishing attacks. It covers topics such as email communication, blocking popups and ads, report phishing attempts etc.Deliver an outstanding presentation on the topic using this Training Plan For Preventing Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Training Topics, Training Method, Expected Completion Date, Trainer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
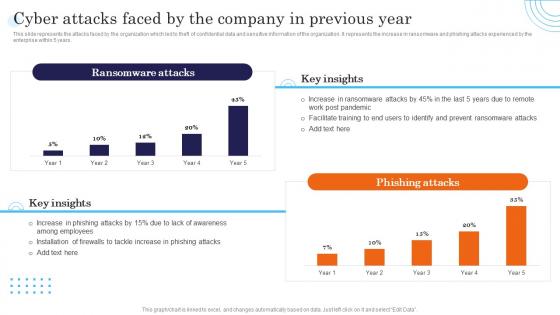 Cyber Attacks Faced By The Company In Previous Year Incident Response Strategies Deployment
Cyber Attacks Faced By The Company In Previous Year Incident Response Strategies DeploymentThis slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Deliver an outstanding presentation on the topic using this Cyber Attacks Faced By The Company In Previous Year Incident Response Strategies Deployment. Dispense information and present a thorough explanation of Ransomware, Phishing, Cyber using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





