Encryption Implementation Strategies Powerpoint Presentation Slides
In todays digital world, it is essential to ensure the security of your data, and thus the implementation of encryption is crucial. Check our meticulously crafted PowerPoint Presentation titled, Encryption Implementation Strategies which includes an analysis of various cyber-attacks experienced by the company due to a lack of encryption and security issues faced by the organization, such as unauthorized access, data breaches, insider threats, malware and ransomware, phishing attacks, etc. Additionally, this Data at Rest PPT demonstrates the working steps, architecture, benefits, limitations, and implementation of several encryption techniques. Furthermore, the Bring Your Own Encryption BYOE modules highlight the techniques and challenges of the various states of data that require encryption, named data-at-rest, data-in-transit, and data-in-use. Moreover, this Encryption as a Service EaaS Deck represents the different security protocols required according to the type of network and best practices to implement them. Lastly, this Transport Layer Security TLS module also contains sections about encryption implementation in organizations, including training, a timeline, a roadmap for encryption deployment, and a dashboard to track their performance. Download our 100 percent editable and customizable template, which is also compatible with Google Slides.
You must be logged in to download this presentation.
 Impress your
Impress your audience
Editable
of Time
PowerPoint presentation slides
This complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Encryption Implementation Strategies Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of one hundred eight slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide introduces Encryption Implementation Strategies. State Your Company Name and begin.
Slide 2: This slide is an Agenda slide. State your agendas here.
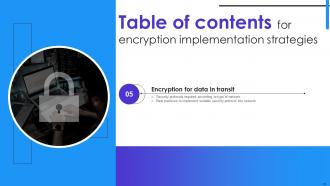
Slide 3: This slide shows a Table of Contents for the presentation.
Slide 4: This slide is in continuation with the previous slide.
Slide 5: This slide is an introductory slide.
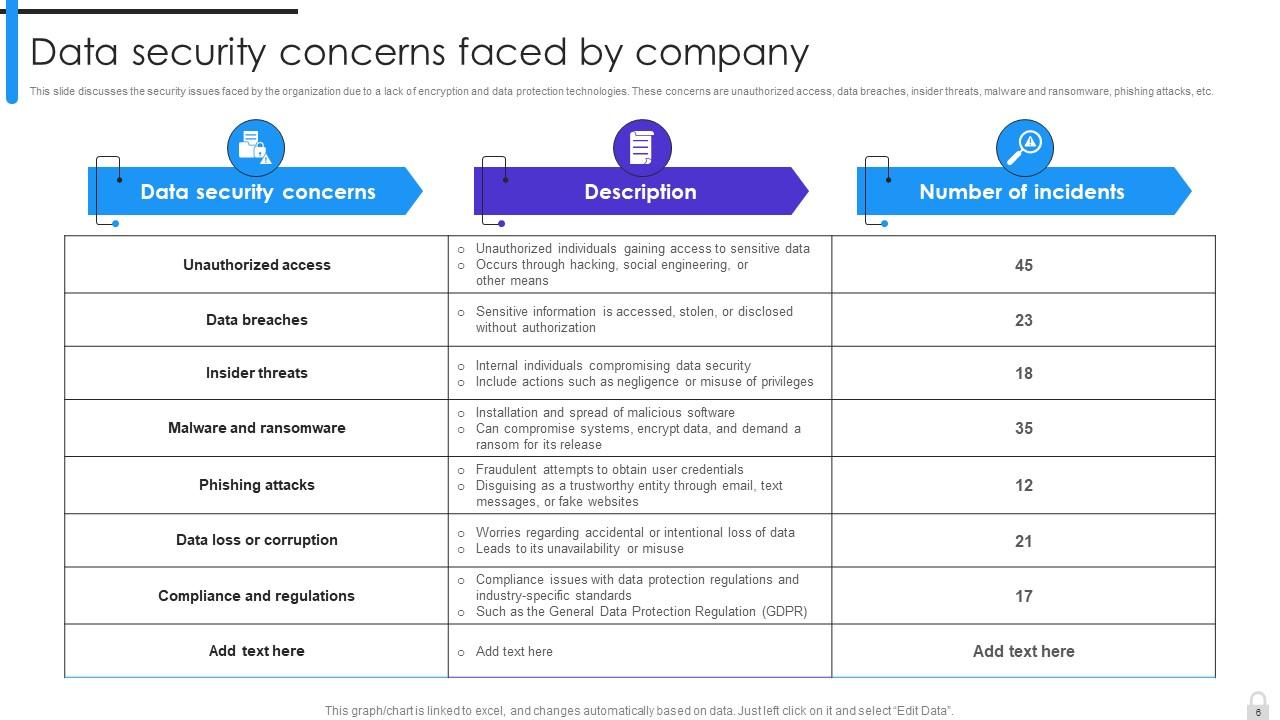
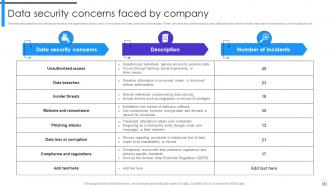
Slide 6: This slide discusses the security issues faced by the organization due to a lack of encryption and data protection technologies.
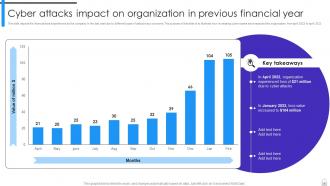
Slide 7: This slide depicts the financial loss experienced by the company in the last year due to different types of data privacy concerns.
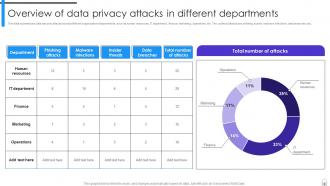
Slide 8: This slide summarizes data security attacks across different organizational departments.
Slide 9: This slide is an introductory slide.
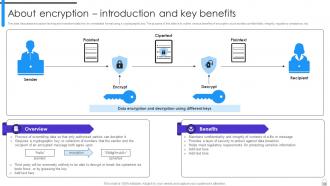
Slide 10: This slide discusses encryption technique to transform data into an unreadable format using a cryptographic key.
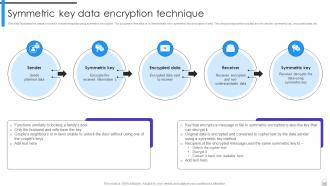
Slide 11: This slide illustrates the steps involved in transferring data using symmetric encryption.
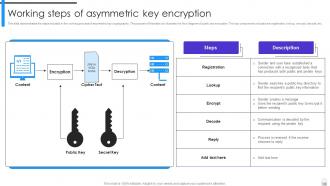
Slide 12: This slide demonstrates the steps included in the working process of asymmetric key cryptography.
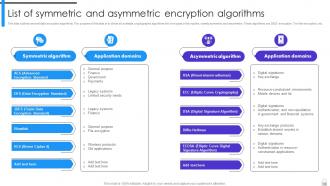
Slide 13: This slide outlines several data encryption algorithms.
Slide 14: This slide is an introductory slide.
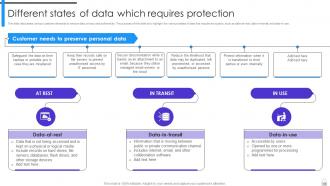
Slide 15: This slide discusses various customer demands to ensure data privacy and authenticity.
Slide 16: This slide is an introductory slide.
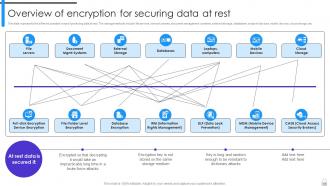
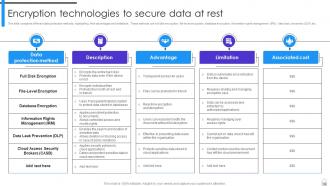
Slide 17: This slide represents the different possible ways of protecting data at rest.
Slide 18: This slide compares different data protection methods, highlighting their advantages and limitations.
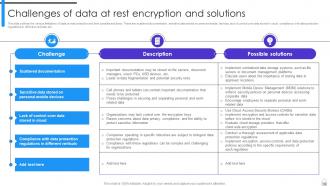
Slide 19: This slide outlines the various limitations of data at rest protection and their possible solutions.
Slide 20: This slide is an introductory slide.
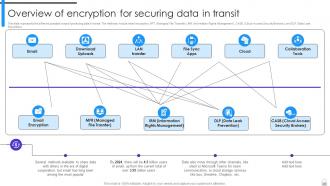
Slide 21: This slide represents the different possible ways of protecting data in transit.
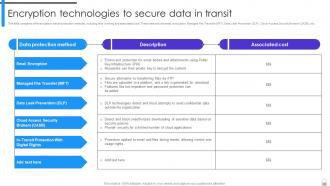
Slide 22: This slide entails different data in transit protection methods, including their working and associated cost.
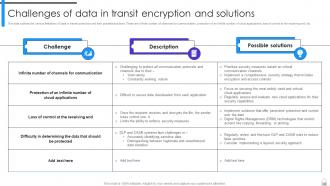
Slide 23: This slide outlines the various limitations of data in transit protection and their possible solutions.
Slide 24: This slide is an introductory slide.
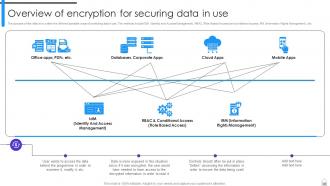
Slide 25: This slide puts the different possible ways of protecting data in use.
Slide 26: This slide compares different data in use protection methods, and their working and associated cost.
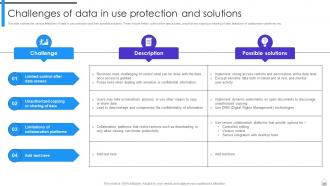
Slide 27: This slide outlines the various limitations of data in use protection and their possible solutions.
Slide 28: This slide is an introductory slide.
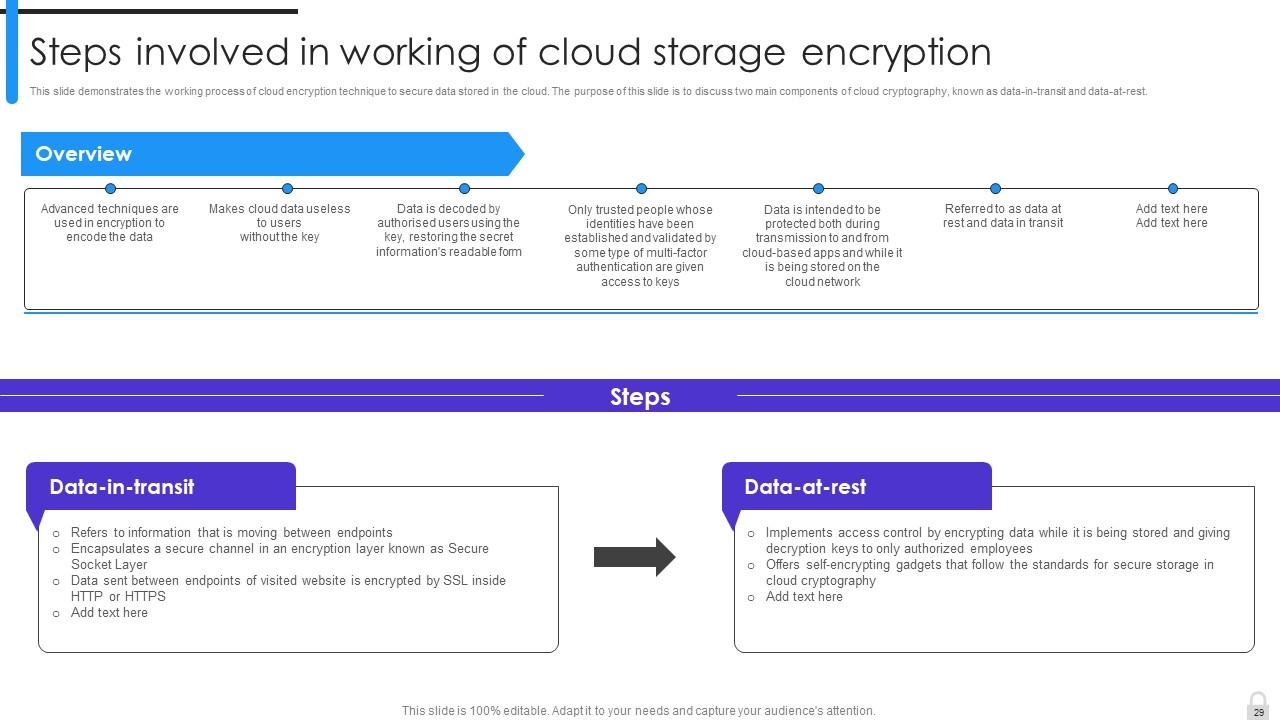
Slide 29: This slide demonstrates the working process of cloud encryption technique to secure data stored in the cloud.
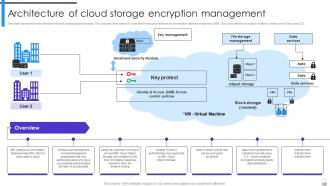
Slide 30: This slide represents the architecture of cloud cryptography technique.
Slide 31: This slide is an introductory slide.
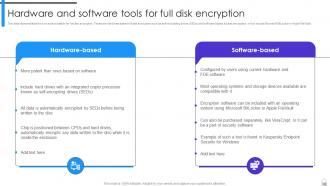
Slide 32: This slide demonstrates the two tools available for full disk encryption.
Slide 33: This slide discusses the full disk windows encryption technique provided by Microsoft, known as BitLocker.
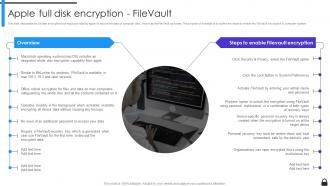
Slide 34: This slide discusses the full disk encryption technique provided by apple to secure the data of computer disk, known as the FileVault software.
Slide 35: This slide is an introductory slide.
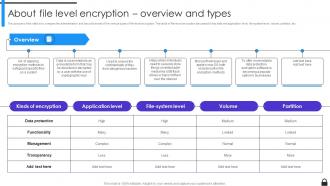
Slide 36: This slide compares the administration and security levels of the various types of file-level encryption.
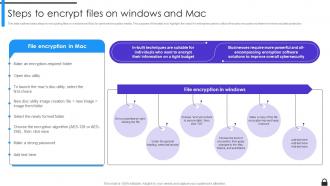
Slide 37: This slide outlines basic steps for encrypting files on windows and Mac for personal encryption needs.
Slide 38: This slide represents a guide for selecting a file encryption software based on several key factors.
Slide 39: This slide discusses the two main types of encryption used for computers, known as full-disk encryption (FDE) and file-level encryption (FLE).
Slide 40: This slide is an introductory slide.
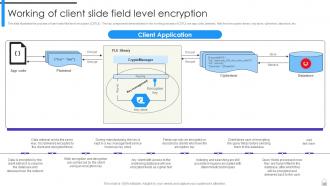
Slide 41: This slide illustrates the process of client-side field level encryption (CSFLE).
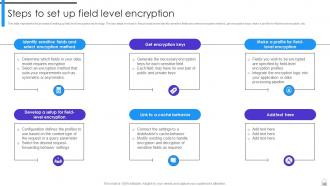
Slide 42: This slide presents the process of setting up field level encryption technology.
Slide 43: This slide is an introductory slide.
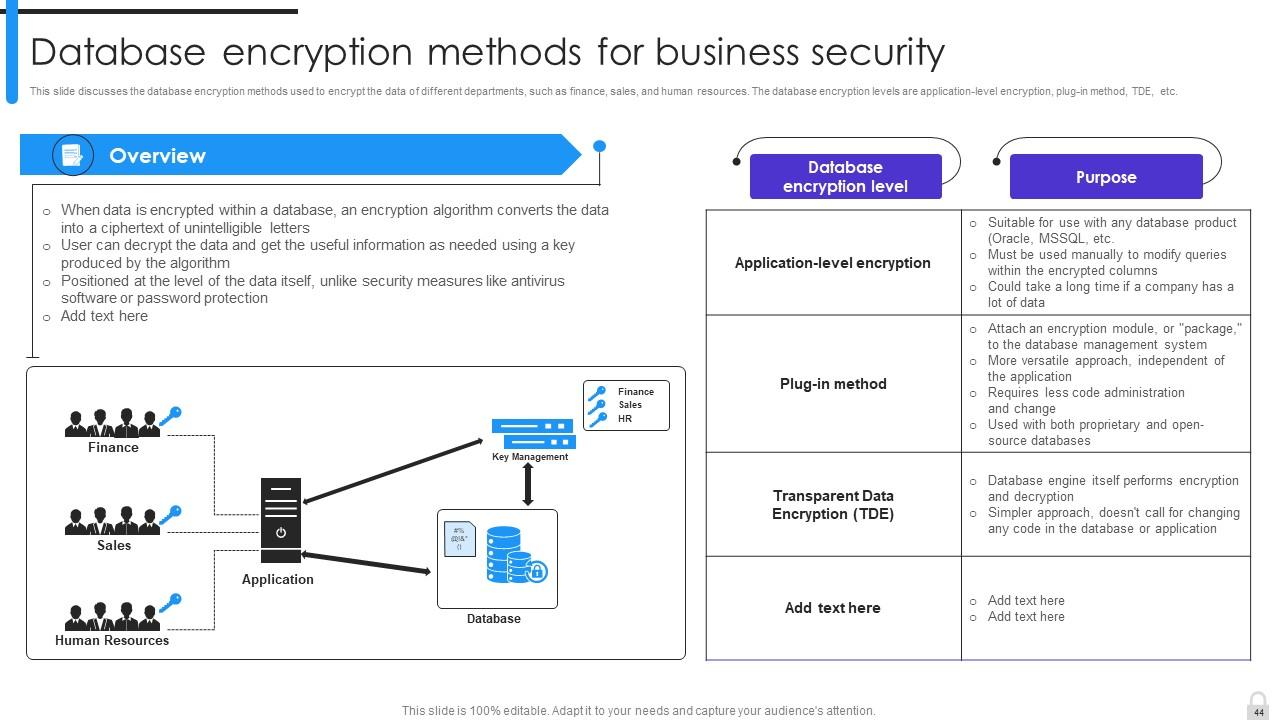
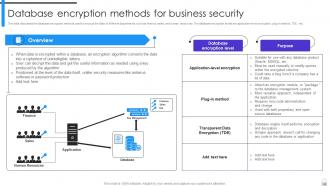
Slide 44: This slide marks the database encryption methods used to encrypt the data of different departments, such as finance, sales, and human resources.
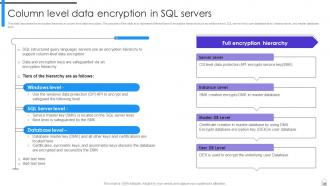
Slide 45: This slide discusses the encryption hierarchy in column level data encryption.
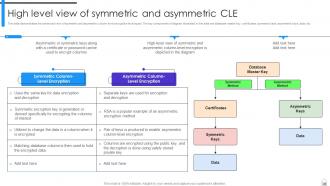
Slide 46: This slide demonstrates the enhanced view of symmetric and asymmetric column level encryption techniques.
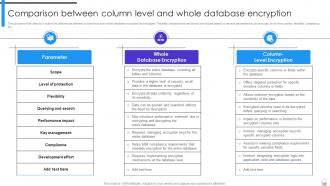
Slide 47: This slide outlines the differences between column level and whole database encryption technologies.
Slide 48: This slide is an introductory slide.
Slide 49: This slide presents a guide to analyze the need for data protection in an organization.
Slide 50: This slide is an introductory slide.
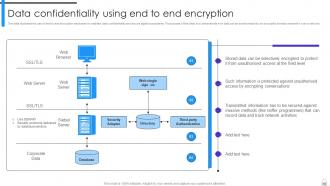
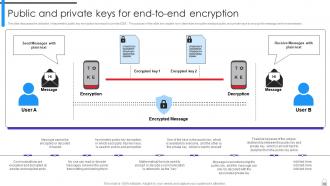
Slide 51: This slide illustrates the use of end-to-end encryption mechanism to maintain data confidentiality and secure digital ecosystems.
Slide 52: This slide discusses the utilization of asymmetric public key encryption technique to provide E2EE.
Slide 53: This slide is an introductory slide.
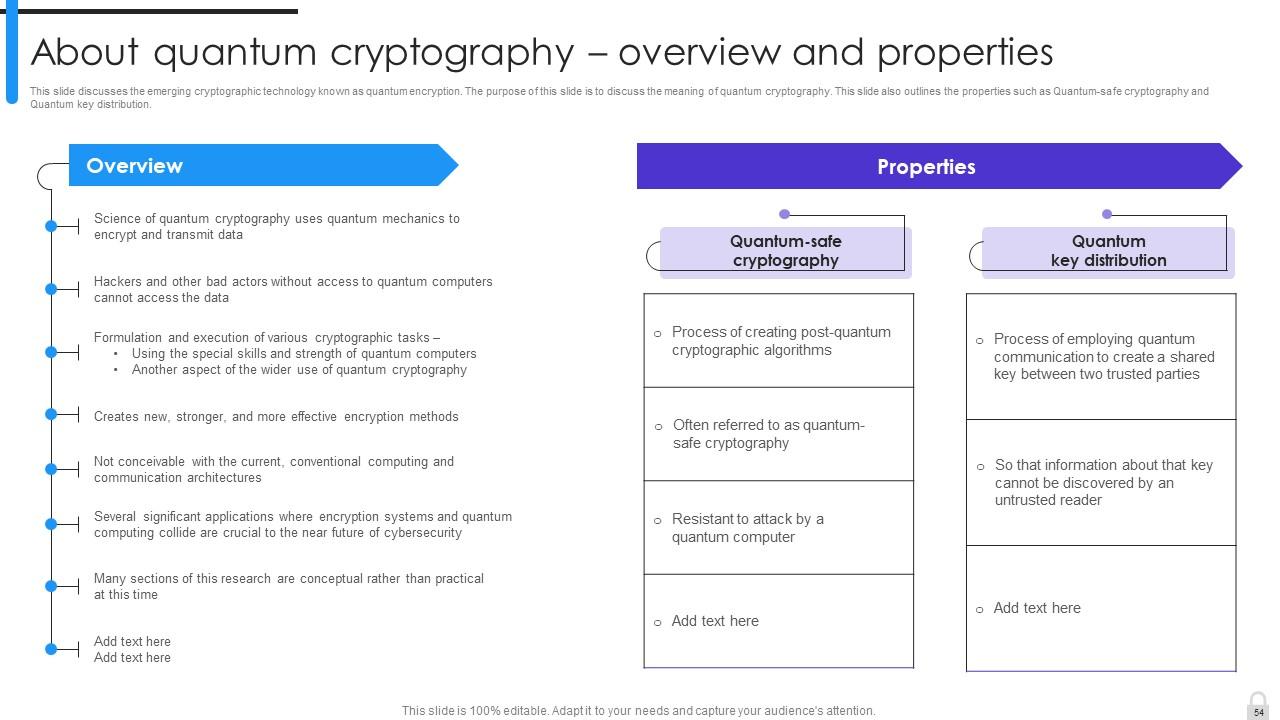
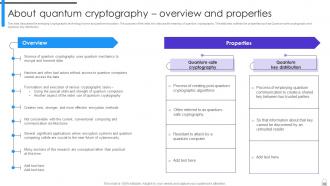
Slide 54: This slide discusses the emerging cryptographic technology known as quantum encryption.
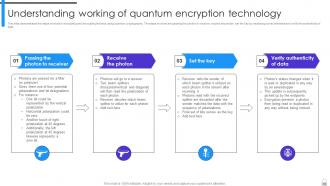
Slide 55: This slide demonstrates the steps involved in encrypting and decrypting the keys using quantum cryptography.
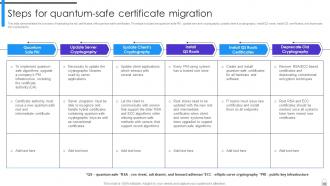
Slide 56: This slide delienates the process of replicating the old certificates with quantum-safe certificates.
Slide 57: This slide is an introductory slide.
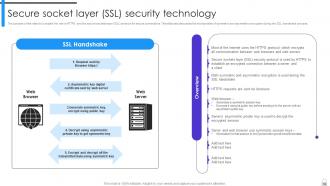
Slide 58: This slide explains the role of HTTPS and the secure sockets layer (SSL) protocol for secure connections.
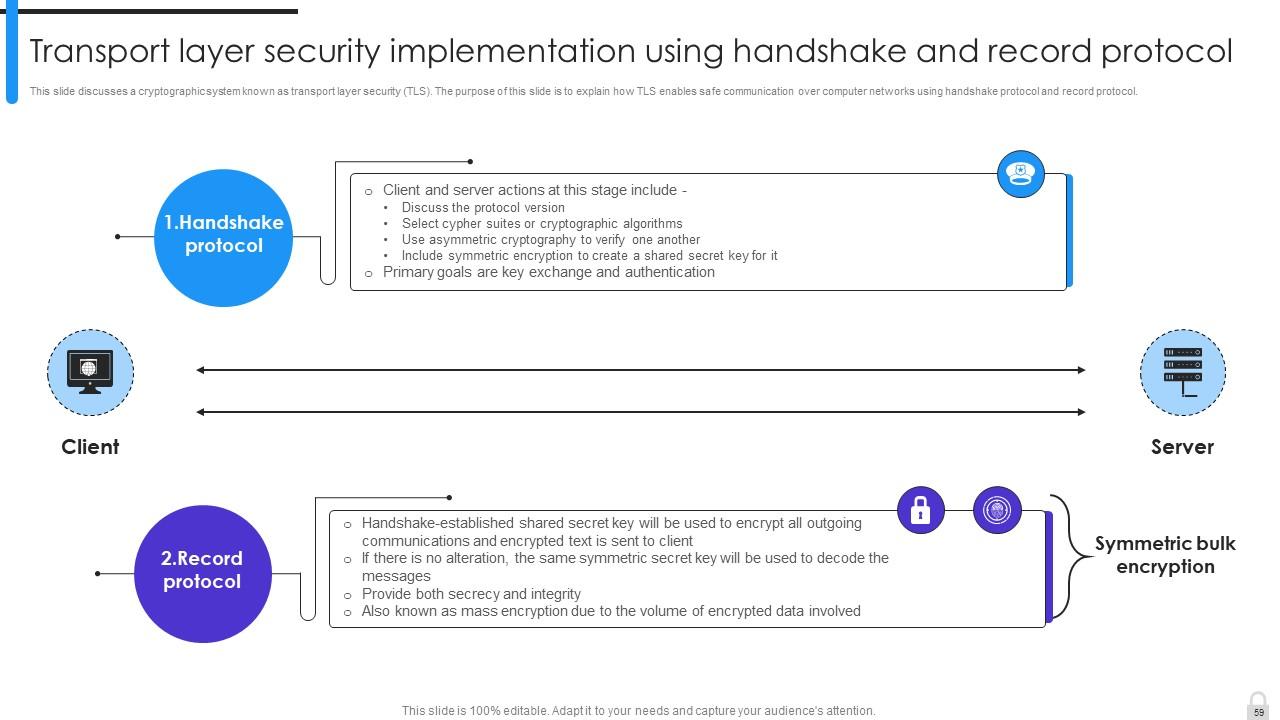
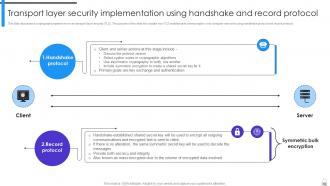
Slide 59: This slide discusses a cryptographic system known as transport layer security (TLS).
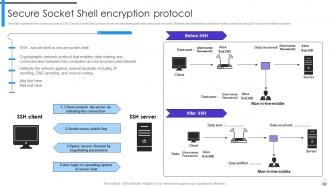
Slide 60: This slide represents the working process of SSH (Secure Socket Shell) protocol to secure data sharing between unsecured networks.
Slide 61: This slide is an introductory slide.
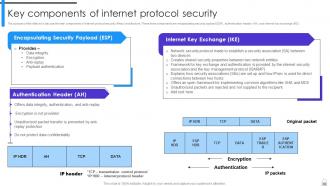
Slide 62: This slide discusses the main components of internet protocol security (IPsec) architecture.
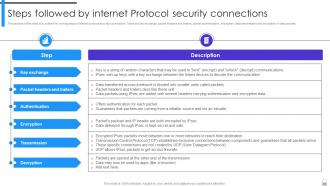
Slide 63: This slide outlines the working steps of internet protocol security connections.
Slide 64: This slide is an introductory slide.
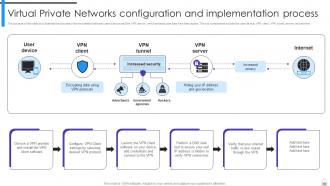
Slide 65: This slide discusses Virtual Private Network (VPN) to enable secure and private communication over public networks by creating an encrypted tunnel between user’s device and the VPN server.
Slide 66: This slide illustrates the process of tunnel creation between user’s device and the VPN server, which protects user data from interception.
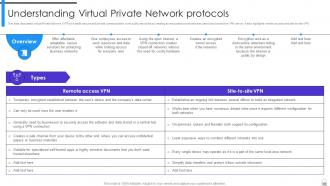
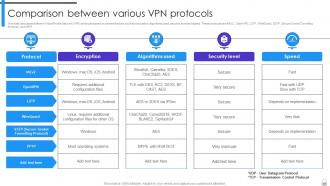
Slide 67: This slide discusses different Virtual Private Network (VPN) protocols based on several factors, such as encryption, algorithms used, security level and speed.
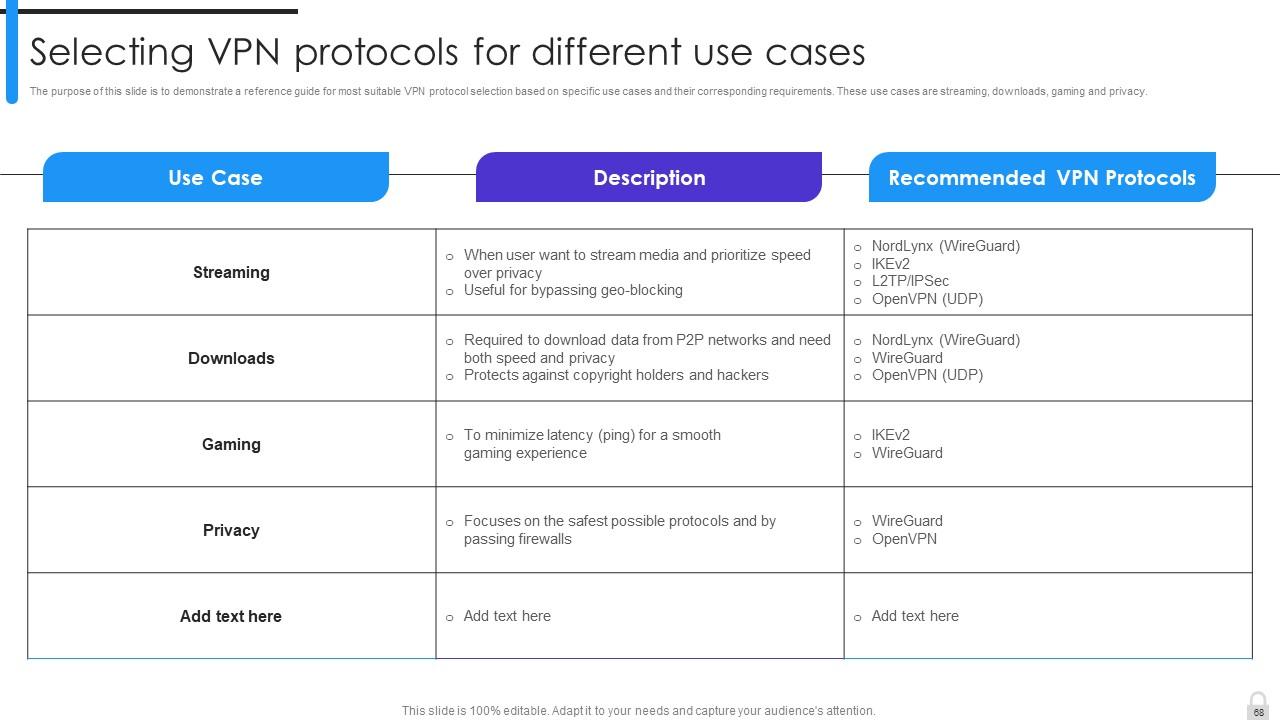
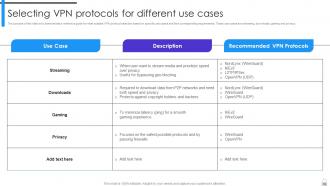
Slide 68: This slide demonstrates a reference guide for most suitable VPN protocol selection based on specific use cases and their corresponding requirements.
Slide 69: This slide is an introductory slide.
Slide 70: This slide outlines different security protocols used in various types of networks, and their specific applications.
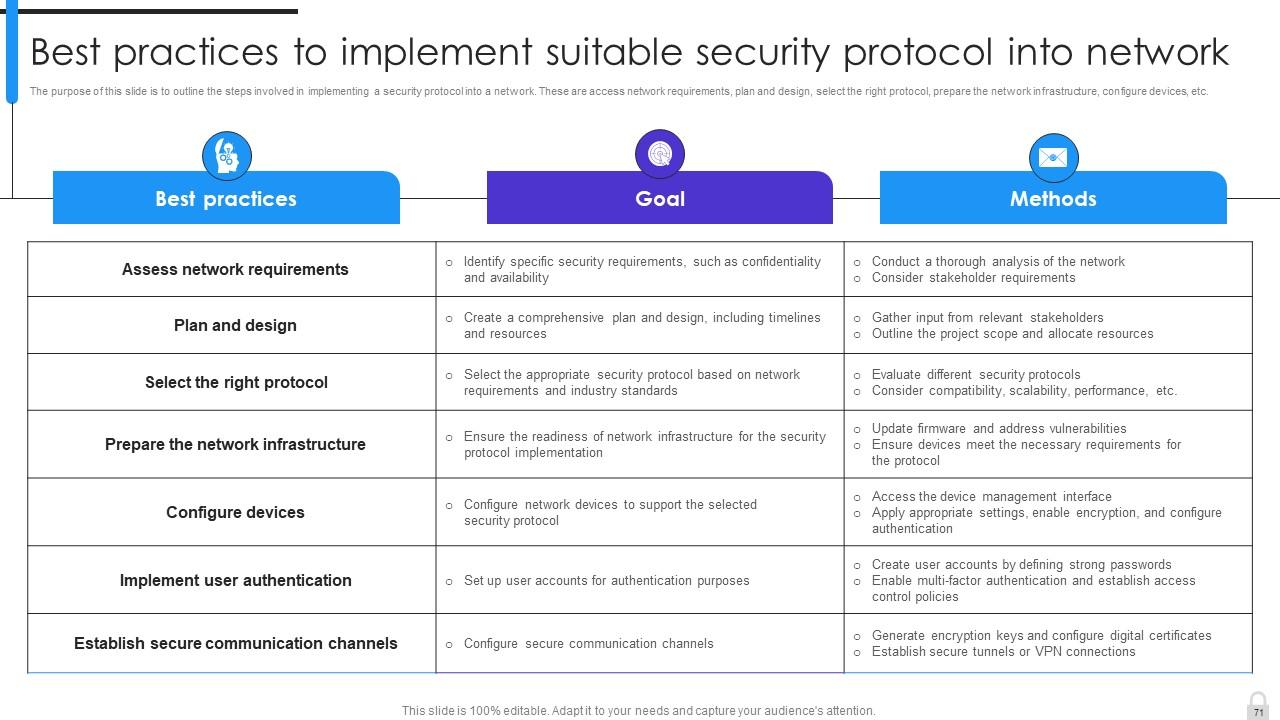
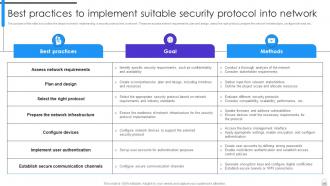
Slide 71: This slide puts the steps involved in implementing a security protocol into a network.
Slide 72: This slide is an introductory slide.
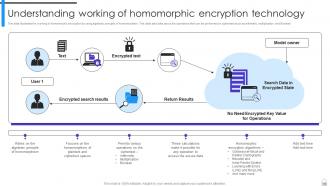
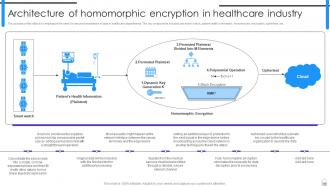
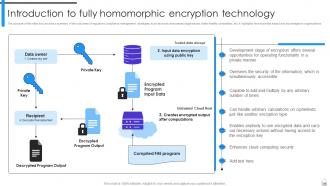
Slide 73: This slide illustrates the working of homomorphic encryption by using algebraic principle of homomorphism.
Slide 74: This slide entails the key uses of homomorphic encryption in different domains.
Slide 75: This slide emphasizes the need for secure transmission of data in healthcare departments.
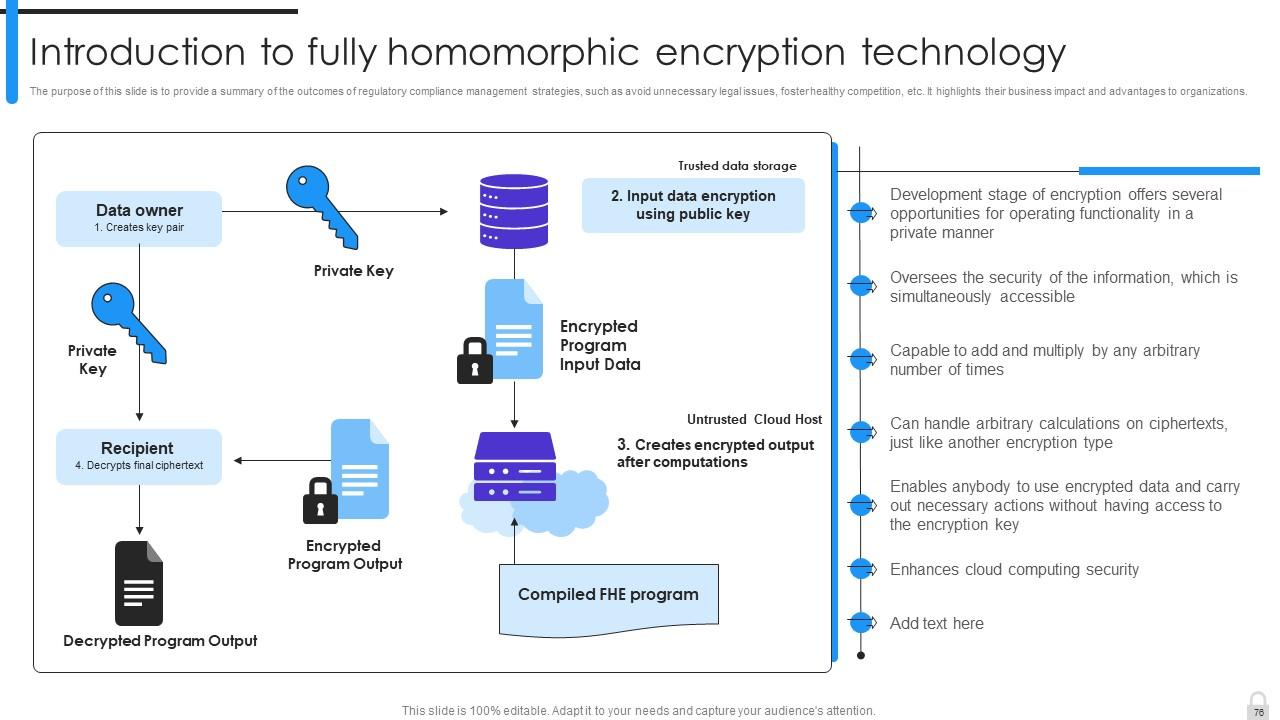
Slide 76: This slide provides a summary of the outcomes of regulatory compliance management strategies.
Slide 77: This slide is an introductory slide.
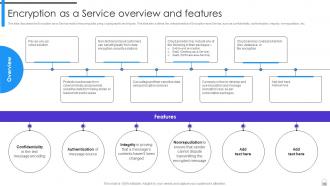
Slide 78: This slide discusses the Encryption-as-a-Service model of securing data using cryptographic techniques.
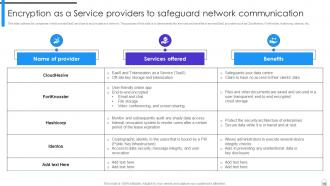
Slide 79: This slide outlines the companies which provide EaaS services to secure data in a network.
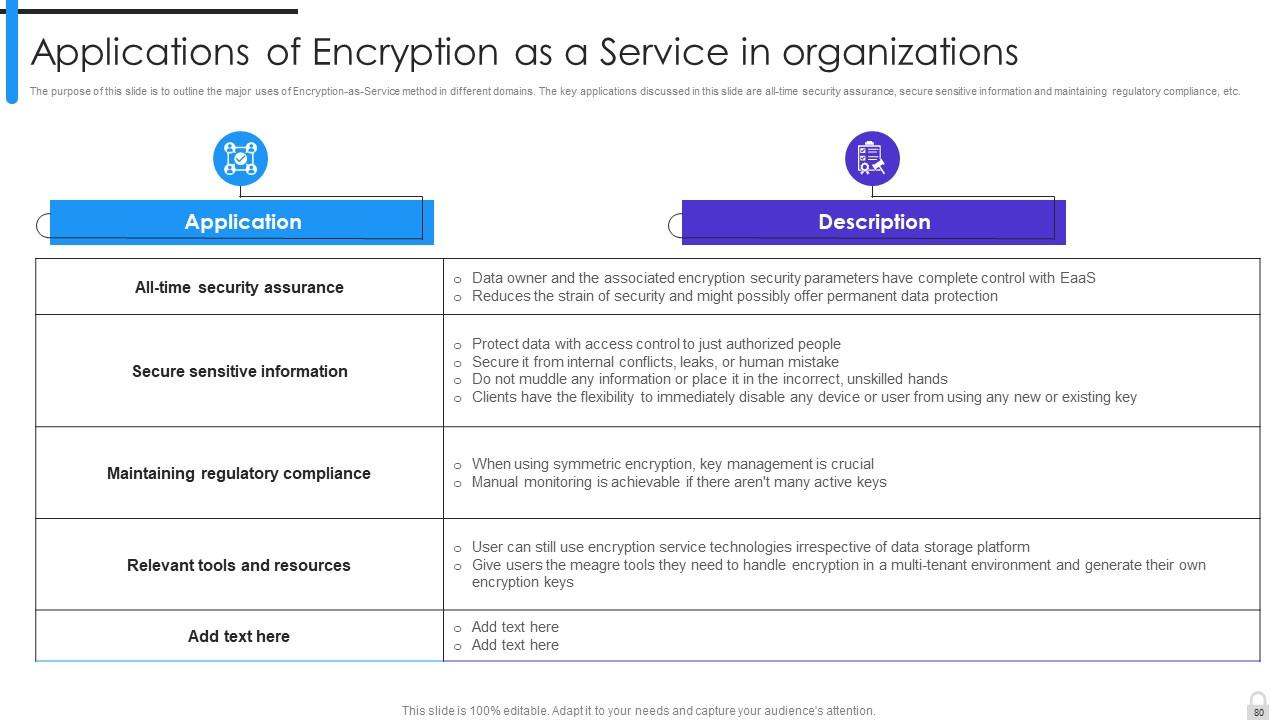
Slide 80: This slide marks the major uses of Encryption-as-Service method in different domains.
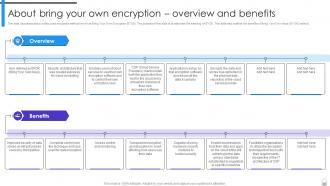
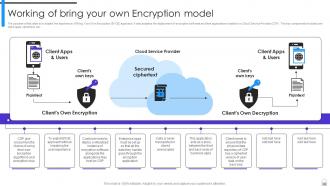
Slide 81: This slide discusses about widely used encryption method known as Bring Your Own Encryption (BYOE).
Slide 82: This slide explains the importance of Bring Your Own Encryption (BYOE) approach.
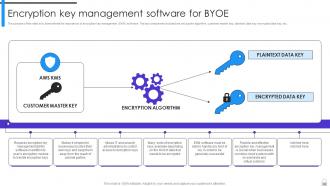
Slide 83: This slide shows the importance of encryption key management (EKM) software.
Slide 84: This slide is an introductory slide.
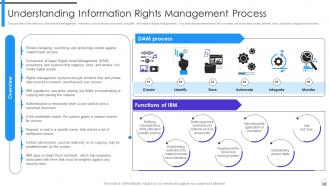
Slide 85: This slide highlights the differences between Information Rights Management (IRM) and Digital Rights Management (DRM).
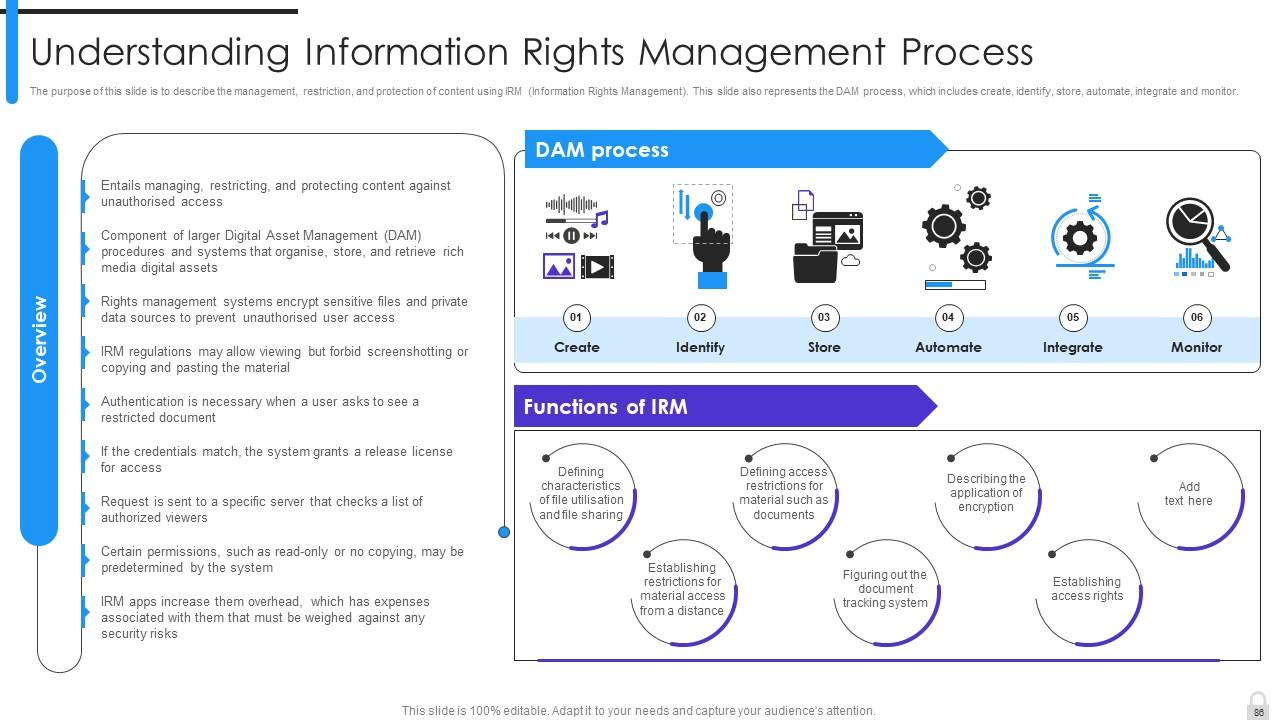
Slide 86: This slide describes the management, restriction, and protection of content using IRM (Information Rights Management).
Slide 87: This slide showcases the available Digital Rights Management (DRM) software for several industries.
Slide 88: This slide is an introductory slide.
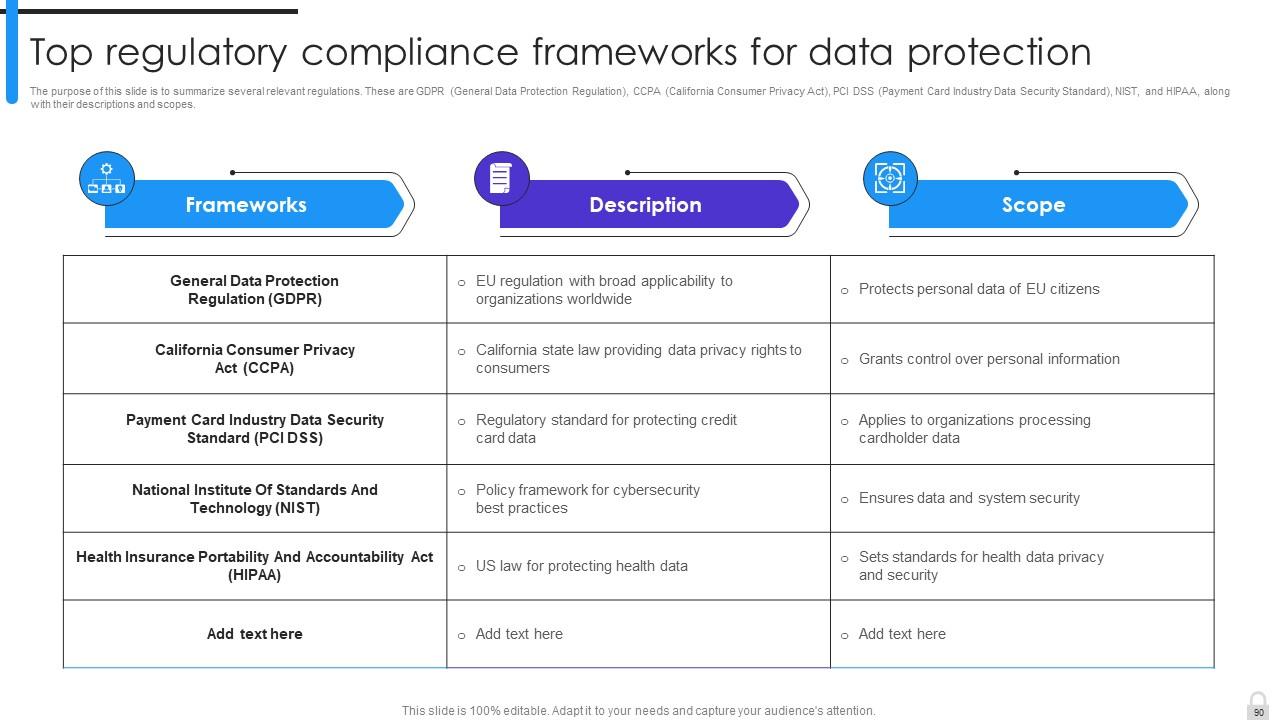
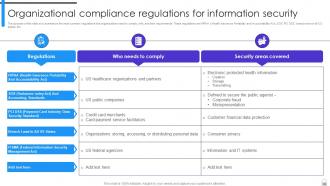
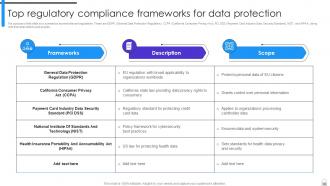
Slide 89: This slide summarizes the most common regulations that organizations need to comply with, and their requirements.
Slide 90: This slide puts several relevant regulations.
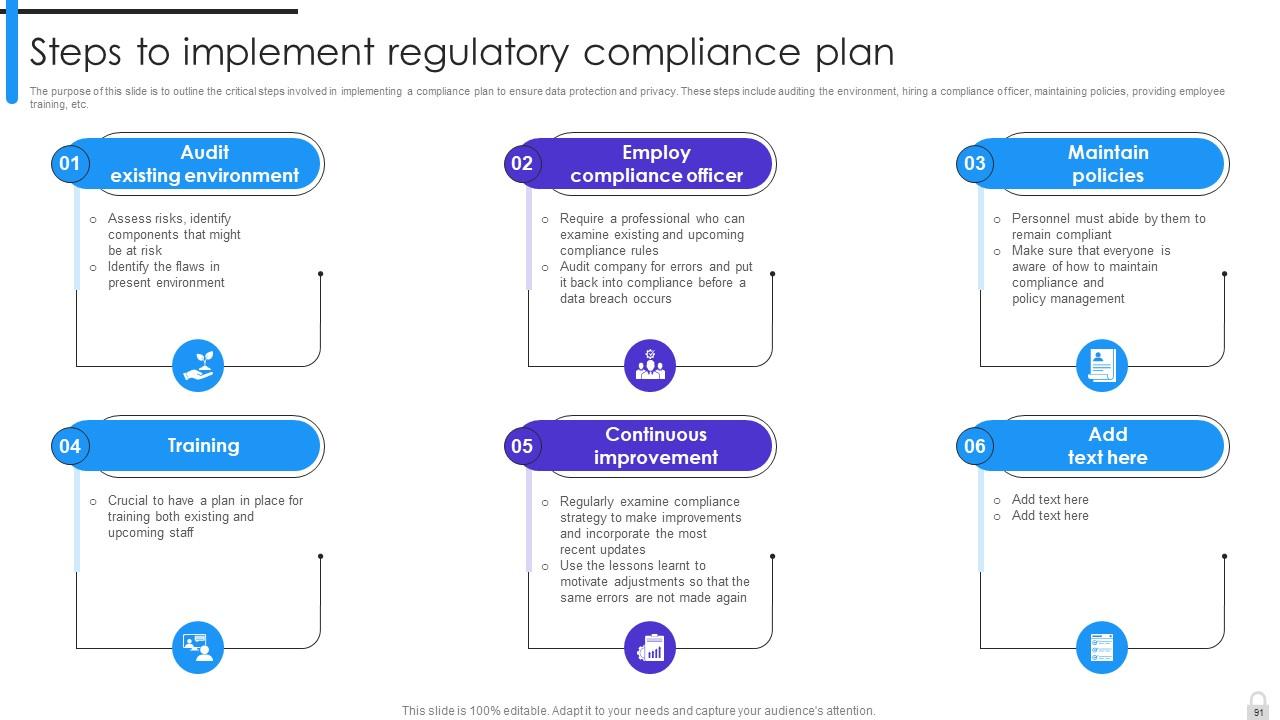
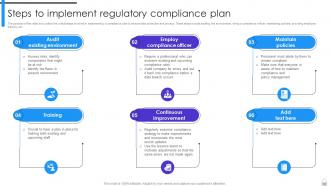
Slide 91: This slide outlines the critical steps involved in implementing a compliance plan to ensure data protection and privacy.
Slide 92: This slide provides a summary of the outcomes of regulatory compliance management strategies.
Slide 93: This slide is an introductory slide.
Slide 94: This slide discusses the procedure for implementing encryption in applications.
Slide 95: This slide describes the procedure for implementing encryption in applications.
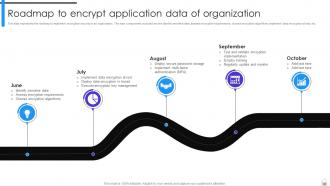
Slide 96: This slide mentions the roadmap to implement encryption security in an organization.
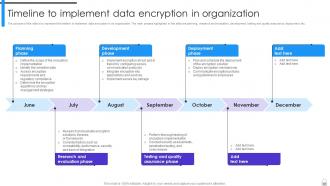
Slide 97: This slide represents the timeline to implement data encryption in an organization.
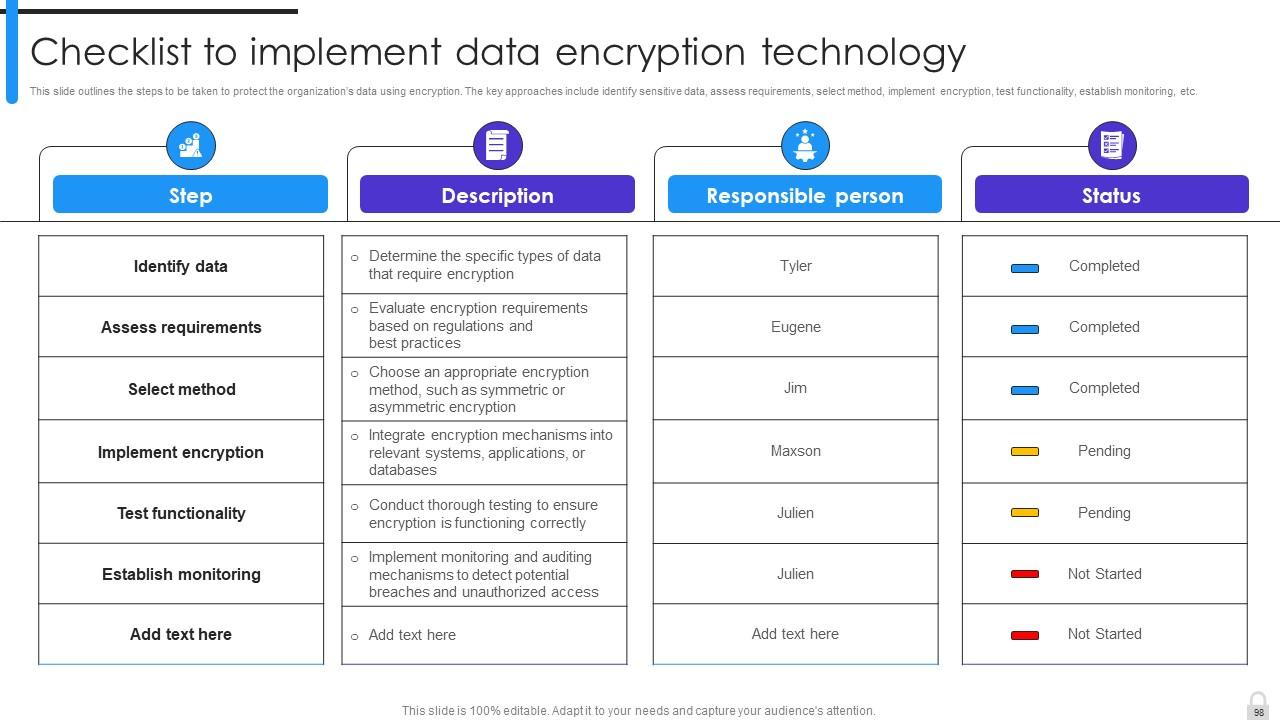
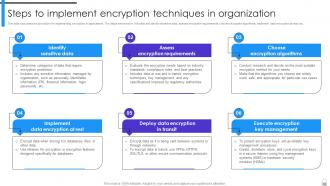
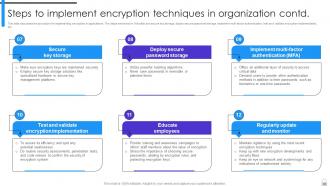
Slide 98: This slide outlines the steps to be taken to protect the organization’s data using encryption.
Slide 99: This slide is an introductory slide.
Slide 100: This slide presents the budget for securing data using encryption techniques.
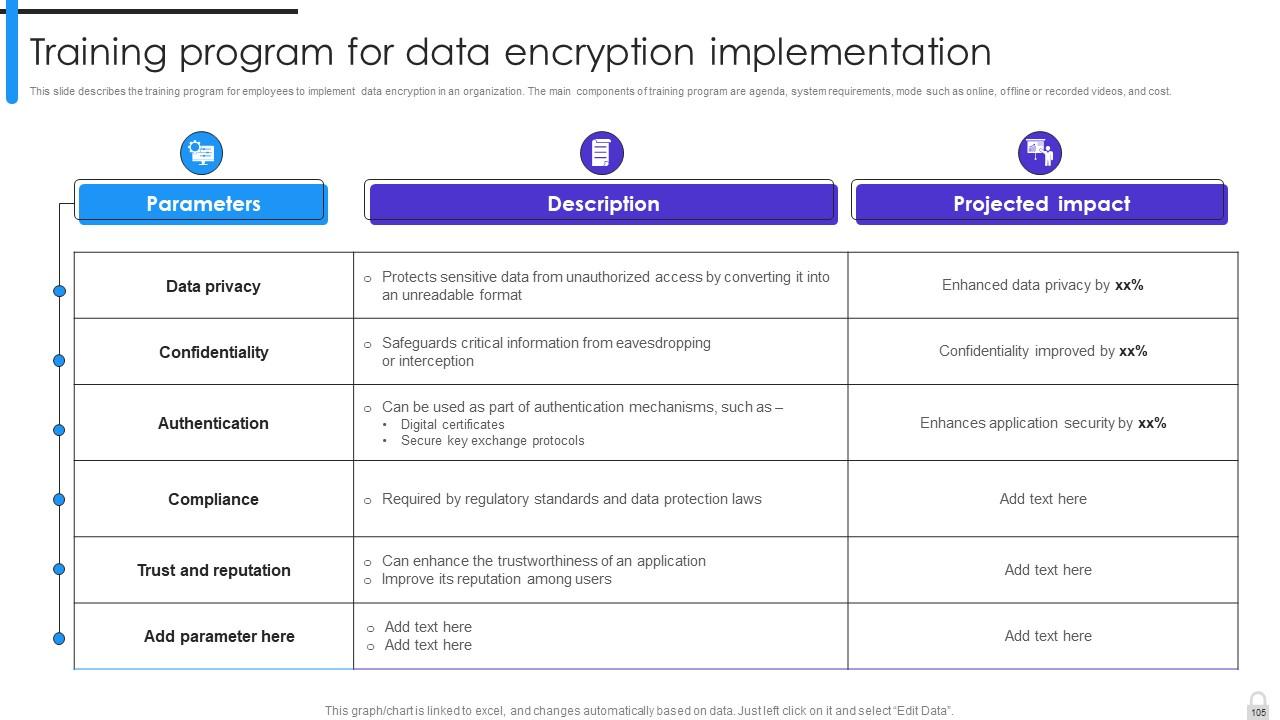
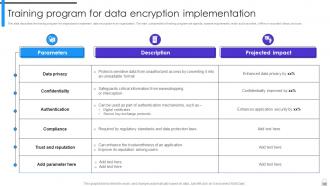
Slide 101: This slide describes the training program for employees to implement data encryption in an organization.
Slide 102: This slide is an introductory slide.
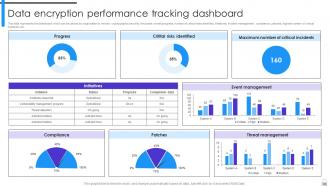
Slide 103: This slide showcases the dashboard which can be utilized by organization to monitor cryptographic security.
Slide 104: This slide is an introductory slide.
Slide 105: This slide marks the training program for employees to implement data encryption in an organization.
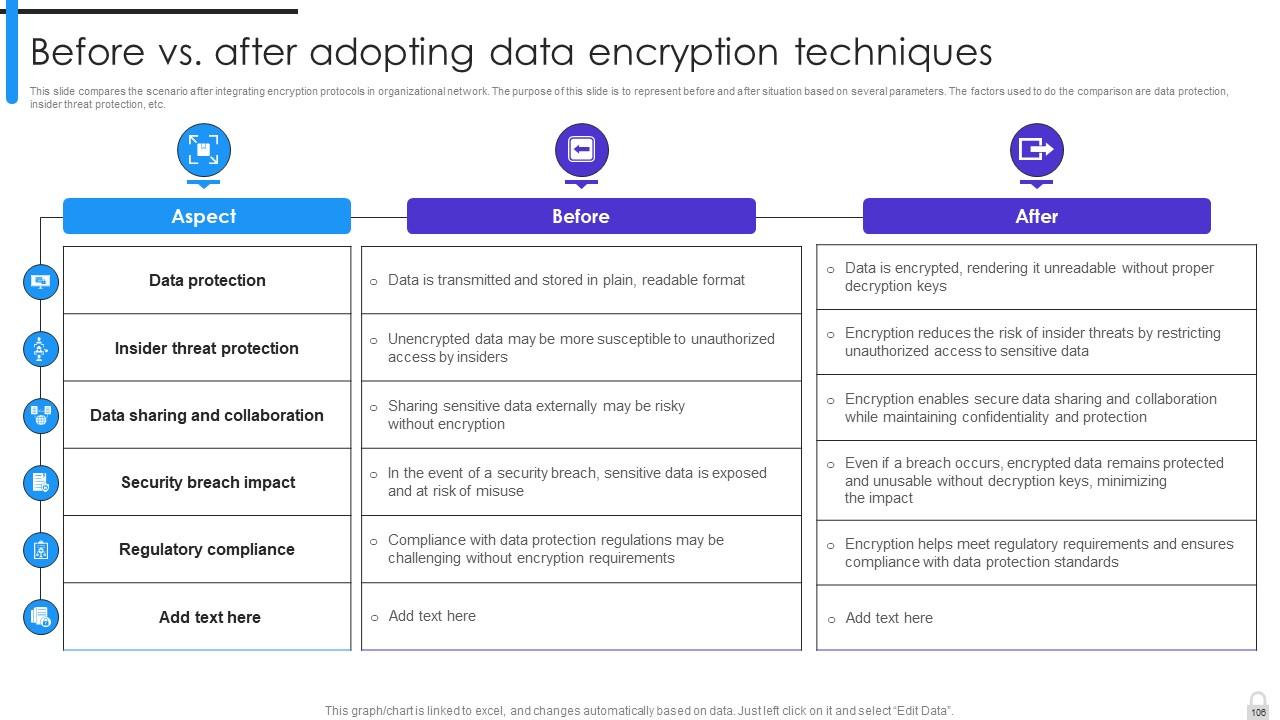
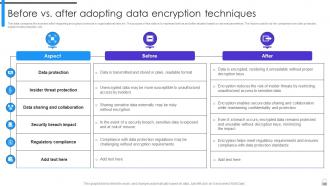
Slide 106: This slide compares the scenario after integrating encryption protocols in organizational network.
Slide 107: This slide shows all the icons included in the presentation.
Slide 108: This slide is a thank-you slide with address, contact numbers, and email address.
Encryption Implementation Strategies Powerpoint Presentation Slides with all 117 slides:
Use our Encryption Implementation Strategies Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Time saving slide with creative ideas. Help a lot in quick presentations..
-
Graphics are very appealing to eyes.