Diagrams on Computer Networking security hacking DDOS attacks
- Sub Categories
-
 Shield icon with star sign
Shield icon with star signPresenting shield icon with star sign. This is a shield icon with star sign. This is a one stage process. The stages in this process are shield icon, protection icon, safety icon.
-
 Shield icon with tick mark
Shield icon with tick markPresenting shield icon with tick mark. This is a shield icon with tick mark. This is a one stage process. The stages in this process are shield icon, protection icon, safety icon.
-
 Shield with tick mark and ribbon icon
Shield with tick mark and ribbon iconPresenting shield with tick mark and ribbon icon. This is a shield with tick mark and ribbon icon. This is a one stage process. The stages in this process are shield icon, protection icon, safety icon.
-
 5 padlock and metal chain concept of protection
5 padlock and metal chain concept of protectionPresenting 5 padlock and metal chain concept of protection. This is a 5 padlock and metal chain concept of protection. This is a five stage process. The stages in this process are padlock, lock, locker.
-
 Five colored circle locked padlock text boxes
Five colored circle locked padlock text boxesPresenting five colored circle locked padlock text boxes. This is a five colored circle locked padlock text boxes. This is a eight stage process. The stages in this process are padlock, lock, locker.
-
 Five colored circle locked padlock text boxes1
Five colored circle locked padlock text boxes1Presenting five colored circle locked padlock text boxes1. This is a five colored circle locked padlock text boxes1. This is a five stage process. The stages in this process are padlock, lock, locker.
-
 Four unlocked locked padlock showcasing phases
Four unlocked locked padlock showcasing phasesPresenting four unlocked locked padlock showcasing phases. This is a four unlocked locked padlock showcasing phases. This is a four stage process. The stages in this process are padlock, lock, locker.
-
 Nine blue color locked padlock steps
Nine blue color locked padlock stepsPresenting nine blue color locked padlock steps. This is a nine blue color locked padlock steps. This is a one stage process. The stages in this process are padlock, lock, locker.
-
 Opening padlock with key doodlean showcasing protection
Opening padlock with key doodlean showcasing protectionPresenting opening padlock with key doodlean showcasing protection. This is a opening padlock with key doodlean showcasing protection. This is a four stage process. The stages in this process are padlock, lock, locker.
-
 Opening padlock with key doodlean showcasing protection1
Opening padlock with key doodlean showcasing protection1Presenting opening padlock with key doodlean showcasing protection1. This is a opening padlock with key doodlean showcasing protection1. This is a one stage process. The stages in this process are padlock, lock, locker.
-
 Padlock inside lighting bulb idea protection hand drawn
Padlock inside lighting bulb idea protection hand drawnPresenting padlock inside lighting bulb idea protection hand drawn. This is a padlock inside lighting bulb idea protection hand drawn. This is a one stage process. The stages in this process are padlock, lock, locker.
-
 Padlock security eye gear scissor question key globe design
Padlock security eye gear scissor question key globe designPresenting padlock security eye gear scissor question key globe design. This is a padlock security eye gear scissor question key globe design. This is a six stage process. The stages in this process are padlock, lock, locker.
-
 Padlock with seven icons and text holders in hexagonal shape
Padlock with seven icons and text holders in hexagonal shapePresenting padlock with seven icons and text holders in hexagonal shape. This is a padlock with seven icons and text holders in hexagonal shape. This is a seven stage process. The stages in this process are padlock, lock, locker.
-
 Six black locked padlock showcasing stages
Six black locked padlock showcasing stagesPresenting Six Black Locked Padlock Showcasing Stages slideshow which is completely editable. It is available in both 4:3 and 16:9 aspect ratio. It can be converted into various formats like PDF, JPG, and PNG. You can customize the color, font, font types, and font size of the slides as per your requirements. This template is adaptable with Google Slides which makes it easily accessible at once.
-
 Two locked unlocked grey color padlock
Two locked unlocked grey color padlockPresenting two locked unlocked grey color padlock. This is a two locked unlocked grey color padlock. This is a two stage process. The stages in this process are padlock, lock, locker.
-
 Padlock security eye gear scissor question key globe
Padlock security eye gear scissor question key globePresenting padlock security eye gear scissor question key globe. This is a padlock security eye gear scissor question key globe. This is a seven stage process. The stages in this process are padlock, lock, locker.
-
 Identify the change presentation visuals
Identify the change presentation visualsPresenting identify the change presentation visuals. This is a identify the change presentation visuals. This is a five stage process. The stages in this process are organization change readiness, gap analysis, types of change management, forces for change, vision for change.
-
 Fraud identity protection finger print chain icon
Fraud identity protection finger print chain iconPresenting fraud identity protection finger print chain icon. This is a fraud identity protection finger print chain icon. This is a one stage process. The stages in this process are fraud, cheater, stabber.
-
 Black lock with blue yellow shield icon
Black lock with blue yellow shield iconPresenting black lock with blue yellow shield icon. This is a black lock with blue yellow shield icon. This is a one stage process. The stages in this process are password, authentication, access approval.
-
 Blue person with green key icon
Blue person with green key iconPresenting blue person with green key icon. This is a blue person with green key icon. This is a two stage process. The stages in this process are password, authentication, access approval.
-
 Green lock icon with blue key
Green lock icon with blue keyPresenting green lock icon with blue key. This is a green lock icon with blue key. This is a one stage process. The stages in this process are password, authentication, access approval.
-
 Hotel safety and security icon 3
Hotel safety and security icon 3Presenting hotel safety and security icon 3. This is a hotel safety and security icon 3. This is a four stage process. The stages in this process are hotel safety and security, guest house safety, lodge safety.
-
 Hotel safety and security icon 4
Hotel safety and security icon 4Presenting hotel safety and security icon 4. This is a hotel safety and security icon 4. This is a one stage process. The stages in this process are hotel safety and security, guest house safety, lodge safety.
-
 Hotel safety and security icon1
Hotel safety and security icon1Presenting hotel safety and security icon1. This is a hotel safety and security icon1. This is a three stage process. The stages in this process are hotel safety and security, guest house safety, lodge safety.
-
 Hotel safety and security icons 2
Hotel safety and security icons 2Presenting hotel safety and security icons 2. This is a hotel safety and security icons 2. This is a one stage process. The stages in this process are hotel safety and security, guest house safety, lodge safety.
-
 Incentive policy chart icon powerpoint slide
Incentive policy chart icon powerpoint slidePresenting incentive policy chart icon powerpoint slide. This is a incentive policy chart icon powerpoint slide. This is a one stage process. The stages in this process are incentive policy chart, incentive structures, profit motive.
-
 Hand with unlock icon having key hole
Hand with unlock icon having key holePresenting hand with unlock icon having key hole. This is a hand with unlock icon having key hole. This is a two stage process. The stages in this process are unlock, padlock, open lock.
-
 Unlock black with three dots icon
Unlock black with three dots iconPresenting unlock black with three dots icon. This is a unlock black with three dots icon. This is a one stage process. The stages in this process are unlock, padlock, open lock.
-
 Unlock showing security numeric buttons icon
Unlock showing security numeric buttons iconPresenting Unlock Showing Security Numeric Buttons Icon template. This PPT template is available in both 4:3 and 16:9 aspect ratios. As this PowerPoint template is 100% editable, you can modify the color, font size, font type, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG
-
 Unlock the door with key and arrow icon
Unlock the door with key and arrow iconPresenting Unlock The Door With Key And Arrow slideshow. This PPT template is available in both 4:3 and 16:9 aspect ratios. As this PowerPoint template is 100% editable, you can modify the color, font size, font type, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG
-
 Unlock the folder document icon at bottom
Unlock the folder document icon at bottomPresenting unlock the folder document icon at bottom. This is a unlock the folder document icon at bottom. This is a one stage process. The stages in this process are unlock, padlock, open lock.
-
 Unlock the laptop with passcode icon
Unlock the laptop with passcode iconPresenting Unlock The Laptop With Passcode Icon template. This PPT template is available in both 4:3 and 16:9 aspect ratios. As this PowerPoint template is 100% editable, you can modify the color, font size, font type, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG
-
 Unlock the mobile with password icon
Unlock the mobile with password iconPresenting Unlock The Mobile With Password Icon. This slide can be downloaded into formats like PDF, JPG, and PNG with ease. You can edit the slide as per your requirements. It is adaptable with Google Slides which makes it accessible at once. This slide is available in both the standard and widescreen aspect ratio. High-quality graphics ensures that there is no room for deterioration.
-
 Unlock with the key icon
Unlock with the key iconPresenting Unlock With the Key Icon slideshow. This PPT template is available in both 4:3 and 16:9 aspect ratios. As this PowerPoint template is 100% editable, you can modify the color, font size, font type, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG
-
 Restricted sensitive and public data types levels
Restricted sensitive and public data types levelsPresenting Restricted Sensitive And Public Data Type Levels template. Easily modify various attributes such as font size, type, background color, diagram color, etc. The slideshow is totally editable in PowerPoint and other related software. You can include high-resolution graphics to the slide. It is having compatibility with Google Slides. Transform this layout to JPG, PDF, or other formats. High-quality graphics will ensure that distortion does not occur.
-
 Business insurance icon with briefcase and dollar shield
Business insurance icon with briefcase and dollar shieldPresenting this set of slides with name - Business Insurance Icon With Briefcase And Dollar Shield. This is a three stage process. The stages in this process are Security Icon, Surety Icon, Insurance Icon.
-
 Insurance icon with protecting hands and a shield
Insurance icon with protecting hands and a shieldPresenting this set of slides with name - Insurance Icon With Protecting Hands And A Shield. This is a four stage process. The stages in this process are Security Icon, Surety Icon, Insurance Icon.
-
 Travel insurance icon with plane and a shield
Travel insurance icon with plane and a shieldPresenting this set of slides with name - Travel Insurance Icon With Plane And A Shield. This is a two stage process. The stages in this process are Security Icon, Surety Icon, Insurance Icon.
-
 Red globe icon with lock sign
Red globe icon with lock signPresenting this set of slides with name - Red Globe Icon With Lock Sign. This is a two stage process. The stages in this process are Bank Fraud, Stolen Money, Reimburse Money.
-
 Key messages shown with four keys and text boxes
Key messages shown with four keys and text boxesPresenting this set of slides with name - Key Messages Shown With Four Keys And Text Boxes. This is a three stage process. The stages in this process are Key Messages, Key Notes, Comments.
-
 Login on with desktop and lock info graphics
Login on with desktop and lock info graphicsPresenting this set of slides with name - Login On With Desktop And Lock Info Graphics. This is a one stage process. The stages in this process are Security, Login, Authentication.
-
 Login page of account with user id and password
Login page of account with user id and passwordPresenting this set of slides with name - Login Page Of Account With User Id And Password. This is a one stage process. The stages in this process are Security, Login, Authentication.
-
 Login with application access with mailing address
Login with application access with mailing addressPresenting this set of slides with name - Login With Application Access With Mailing Address. This is a one stage process. The stages in this process are Security, Login, Authentication.
-
 Login with lock and silhouette profile
Login with lock and silhouette profilePresenting this set of slides with name - Login With Lock And Silhouette Profile. This is a one stage process. The stages in this process are Security, Login, Authentication.
-
 Login with the profile and identification with information
Login with the profile and identification with informationPresenting this set of slides with name - Login With The Profile And Identification With Information. This is a one stage process. The stages in this process are Security, Login, Authentication.
-
 Login with username and password and sign in
Login with username and password and sign inPresenting this set of slides with name - Login With Username And Password And Sign In. This is a one stage process. The stages in this process are Security, Login, Authentication.
-
 Member login vector illustrations
Member login vector illustrationsPresenting this set of slides with name - Member Login Vector Illustrations. This is a one stage process. The stages in this process are Security, Login, Authentication.
-
 Access rights key with five security access
Access rights key with five security accessPresenting this set of slides with name - Access Rights Key With Five Security Access. This is a one stage process. The stages in this process are Access Rights, Permission, Logins.
-
 Access rights showing key and the bricks
Access rights showing key and the bricksPresenting this set of slides with name - Access Rights Showing Key And The Bricks. This is a one stage process. The stages in this process are Access Rights, Permission, Logins.
-
 Access rights with protective shield and message box
Access rights with protective shield and message boxPresenting this set of slides with name - Access Rights With Protective Shield And Message Box. This is a one stage process. The stages in this process are Access Rights, Permission, Logins.
-
 Key with gear and six points access rights
Key with gear and six points access rightsPresenting this set of slides with name - Key With Gear And Six Points Access Rights. This is a one stage process. The stages in this process are Access Rights, Permission, Logins.
-
 Lock and key access rights icon
Lock and key access rights iconPresenting this set of slides with name - Lock And Key Access Rights Icon. This is a one stage process. The stages in this process are Access Rights, Permission, Logins.
-
 Physical storage network security layer lock shape
Physical storage network security layer lock shapePresenting this set of slides with name - Physical Storage Network Security Layer Lock Shape. This is a one stage process. The stages in this process are Security Layers, Safety Layers, Protection Layers.
-
 Security layer icon with boxes and lock in center
Security layer icon with boxes and lock in centerPresenting this set of slides with name - Security Layer Icon With Boxes And Lock In Center. This is a one stage process. The stages in this process are Security Layers, Safety Layers, Protection Layers.
-
 Security layer icon with three rows and lock icon
Security layer icon with three rows and lock iconPresenting this set of slides with name - Security Layer Icon With Three Rows And Lock Icon. This is a one stage process. The stages in this process are Security Layers, Safety Layers, Protection Layers.
-
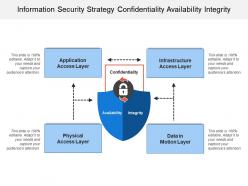 Information security strategy confidentiality availability integrity
Information security strategy confidentiality availability integrityPresenting this set of slides with name - Information Security Strategy Confidentiality Availability Integrity. This is a four stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
 Information security strategy icons
Information security strategy iconsPresenting this set of slides with name - Information Security Strategy Icons. This is a three stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
 Vulnerability management icon slide
Vulnerability management icon slidePresenting this set of slides with name - Vulnerability Management Icon Slide. This is a one stage process. The stages in this process are Vulnerability Management, Risk Management, Vulnerability Planning.
-
 Revenue assurance dollar sign on shield
Revenue assurance dollar sign on shieldPresenting this set of slides with name - Revenue Assurance Dollar Sign On Shield. This is a one stage process. The stages in this process are Revenue Assurance, Business Activity, Income Assurance.
-
 Company logo ppt file files
Company logo ppt file filesPresenting this set of slides with name - Company Logo Ppt File Files. This is a three stage process. The stages in this process are Person, Contact Details, Company Logo, Icons, Strategy.
-
Best Representation of topics, really appreciable.
-
Visually stunning presentation, love the content.
-
Innovative and attractive designs.
-
Presentation Design is very nice, good work with the content as well.
-
Best Representation of topics, really appreciable.
-
Good research work and creative work done on every template.
-
Designs have enough space to add content.
-
Easily Understandable slides.
-
Nice and innovative design.
-
Colors used are bright and distinctive.






