Diagrams on Computer Networking security hacking DDOS attacks
- Sub Categories
-
 Cybersecurity Framework Against Email Phishing Icon
Cybersecurity Framework Against Email Phishing IconPresenting our set of slides with Cybersecurity Framework Against Email Phishing Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cybersecurity, Framework, Email.
-
 Cybersecurity Framework Model Audit Icon
Cybersecurity Framework Model Audit IconIntroducing our premium set of slides with Cybersecurity Framework Model Audit Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cybersecurity, Framework, Audit. So download instantly and tailor it with your information.
-
 Best Practices To Protect Data In Cloud Infra Security
Best Practices To Protect Data In Cloud Infra SecurityThe following slide illustrates practices to protect sensitive data in cloud infrastructure that comply with many standards, law and regulations. It presents information related to securing access to cloud, monitoring privileged users, etc. Increase audience engagement and knowledge by dispensing information using Best Practices To Protect Data In Cloud Infra Security. This template helps you present information on seven stages. You can also present information on Secure, Manage, Employee using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Icon For Infrastructure Protection
Cyber Security Icon For Infrastructure ProtectionIntroducing Cyber Security Icon For Infrastructure Protection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Security, Icon Infrastructure, Protection, using this template. Grab it now to reap its full benefits.
-
 Infra Security Icon For Eliminating Cyber Threats
Infra Security Icon For Eliminating Cyber ThreatsIncrease audience engagement and knowledge by dispensing information using Infra Security Icon For Eliminating Cyber Threats. This template helps you present information on four stages. You can also present information on Infra Security, Icon Eliminating, Cyber Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Lines Of Defense For Risk Management And Governance Icon
Lines Of Defense For Risk Management And Governance IconPresenting our set of slides with Lines Of Defense For Risk Management And Governance Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Lines Of Defense, Risk Management, Governance Icon.
-
 Three Lines Of Defense Model For Cyber Security
Three Lines Of Defense Model For Cyber SecurityThis slide represents the cyber security and governance lines of defense model. It includes functions of the three lines of defense such as policies, procedures and standards documentation, penetration testing, review policies and procedures, conduct cyber risk assessments etc. Presenting our set of slides with Three Lines Of Defense Model For Cyber Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Processes, Data Classification, Risk Assessments.
-
 Powerful Daily Quotes In Powerpoint And Google Slides Cpb
Powerful Daily Quotes In Powerpoint And Google Slides CpbPresenting our Powerful Daily Quotes In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Powerful Daily Quotes. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
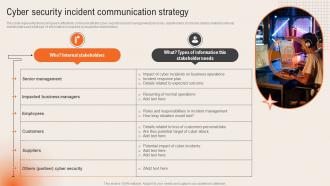 Cyber Security Incident Communication Strategy Deploying Computer Security Incident Management
Cyber Security Incident Communication Strategy Deploying Computer Security Incident ManagementThis slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders.Introducing Cyber Security Incident Communication Strategy Deploying Computer Security Incident Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Senior Management, Impacted Business, Incident Management, using this template. Grab it now to reap its full benefits.
-
 Cyber Threat Prevention Detection Correction Icon
Cyber Threat Prevention Detection Correction IconIntroducing our premium set of slides with Cyber Threat Prevention Detection Correction Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Threat Prevention, Detection Correction Icon. So download instantly and tailor it with your information.
-
 System Threat Prevention Detection Correction
System Threat Prevention Detection CorrectionPresenting our set of slides with System Threat Prevention Detection Correction. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on System Threat Prevention, Detection Correction.
-
 Remove Hybrid And Multi Cloud Solutions For Removing Complexity For Table Of Contents
Remove Hybrid And Multi Cloud Solutions For Removing Complexity For Table Of ContentsIntroducing Remove Hybrid And Multi Cloud Solutions For Removing Complexity For Table Of Contents to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Workload Placement Solution, Network Complexity Solution, Perimeter Defence Solution, using this template. Grab it now to reap its full benefits.
-
 Cyber Safety Ppt Powerpoint Presentation File Templates
Cyber Safety Ppt Powerpoint Presentation File TemplatesPresenting our set of slides with Cyber Safety Ppt Powerpoint Presentation File Templates. This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Safety.
-
 Multi Step Strategy To Implement Cyber Safety
Multi Step Strategy To Implement Cyber SafetyThe following slide provides a step by step strategy to monitor and reassess your organizations cybersecurity maturity which helps to strengthen the cyber safety. The process involves understand, assess, determine and document. Presenting our set of slides with Multi Step Strategy To Implement Cyber Safety. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Understand, Assess, Determine, Document.
-
 Two Factor Authentication Icon For Cyber Safety
Two Factor Authentication Icon For Cyber SafetyPresenting our set of slides with Two Factor Authentication Icon For Cyber Safety. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Two Factor Authentication, Icon For Cyber Safety.
-
 User Access Management Open Source Tools Icon
User Access Management Open Source Tools IconIntroducing our premium set of slides with User Access Management Open Source Tools Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like User Access Management, Open Source Tools, Icon. So download instantly and tailor it with your information.
-
 Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch
Step 4 And 5 Available Technology Review And Zero Trust Initiatives LaunchThis slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. Increase audience engagement and knowledge by dispensing information using Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch. This template helps you present information on two stages. You can also present information on Review Available Technology Review, Launch Key Zero Trust Initiatives using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Zero Trust Network Access User Flow Overview Ppt Outline Design Inspiration
Zero Trust Network Access User Flow Overview Ppt Outline Design InspirationThis slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Increase audience engagement and knowledge by dispensing information using Zero Trust Network Access User Flow Overview Ppt Outline Design Inspiration. This template helps you present information on four stages. You can also present information on Particular Network, Security, Device using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 ZTNA Estimated Cost Summary For ZTNA Implementation
ZTNA Estimated Cost Summary For ZTNA ImplementationThis slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. Introducing ZTNA Estimated Cost Summary For ZTNA Implementation to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Estimated Cost Summary, Ztna Implementation, using this template. Grab it now to reap its full benefits.
-
 ZTNA Key Characteristics Of Modern ZTNA Solution Ppt Model Layout Ideas
ZTNA Key Characteristics Of Modern ZTNA Solution Ppt Model Layout IdeasThis slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering. Introducing ZTNA Key Characteristics Of Modern ZTNA Solution Ppt Model Layout Ideas to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Scalable Performance, Data Loss Prevention, Service, using this template. Grab it now to reap its full benefits.
-
 ZTNA Other ZTNA Architecture Deployment Approaches
ZTNA Other ZTNA Architecture Deployment ApproachesThis slide represents the various deployment approaches for zero trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro segmentation, and ZTA with SDN perimeters. Increase audience engagement and knowledge by dispensing information using ZTNA Other ZTNA Architecture Deployment Approaches. This template helps you present information on three stages. You can also present information on Software Defined Network Perimeters, Micro Segmentation, Enhanced Identity Governance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 ZTNA Role Of ZTNA To Improve Business Operations And Security
ZTNA Role Of ZTNA To Improve Business Operations And SecurityThis slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Increase audience engagement and knowledge by dispensing information using ZTNA Role Of ZTNA To Improve Business Operations And Security. This template helps you present information on four stages. You can also present information on Traditional Method, Ztna Approach, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 ZTNA Table Of Contents Ppt Icon Layout Ideas Ppt Layout
ZTNA Table Of Contents Ppt Icon Layout Ideas Ppt LayoutIntroducing ZTNA Table Of Contents Ppt Icon Layout Ideas Ppt Layout to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Zero Trust Network Access , Zero Network Trust Access, Zero Trust Solution Categories, using this template. Grab it now to reap its full benefits.
-
 ZTNA Traditional Perimeter Based Network Security Overview And Limitations
ZTNA Traditional Perimeter Based Network Security Overview And LimitationsThis slide represents the overview of traditional perimeter based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter based security and how ZTNA can overcomethose challenges. Increase audience engagement and knowledge by dispensing information using ZTNA Traditional Perimeter Based Network Security Overview And Limitations. This template helps you present information on three stages. You can also present information on Overview, Limitations, Solution using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Launching Of Elevate With Worldwide Online Comprehensive Guide To KPMG Strategy SS
Launching Of Elevate With Worldwide Online Comprehensive Guide To KPMG Strategy SSThis slide covers online campaign launched by KPMG to explain the detailed explanation of different services provides and ways to avail them. The purpose of this template is to provide an overview on forms of media used, campaign type, campaign featuring and expected outcomes.Introducing Launching Of Elevate With Worldwide Online Comprehensive Guide To KPMG Strategy SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Campaign Featured, Service Global, Expected Outcome, using this template. Grab it now to reap its full benefits.
-
 Our Solution HashiCorp Investor Funding Elevator Pitch Deck
Our Solution HashiCorp Investor Funding Elevator Pitch DeckThis slide covers key solutions offered by company to enhance cloud security. It involves major solutions such infrastructure automation, effective application delivery and security and compliance. Increase audience engagement and knowledge by dispensing information using Our Solution HashiCorp Investor Funding Elevator Pitch Deck. This template helps you present information on three stages. You can also present information on Infrastructure Automation, Effective Application Delivery, Security And Compliance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security How To Develop Staff Handbook Ppt Ideas Background Images
Security How To Develop Staff Handbook Ppt Ideas Background ImagesIntroducing Security How To Develop Staff Handbook Ppt Ideas Background Images to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on IT Security, Malicious Programs And Code, Especially Vulnerable To Theft, using this template. Grab it now to reap its full benefits.
-
 Firewall As A Service Fwaas Comparison Between Fwaas And Cloud Firewalls
Firewall As A Service Fwaas Comparison Between Fwaas And Cloud FirewallsThis slide illustrates the concept of cloud firewalls and Firewall-as-a-Service. The purpose of this slide is to explain if cloud firewalls, and Firewall-as-Service are same or not. This slide also talks about the correlation of both the terms with each other. Increase audience engagement and knowledge by dispensing information using Firewall As A Service Fwaas Comparison Between Fwaas And Cloud Firewalls. This template helps you present information on one stages. You can also present information on Cloud Firewalls, Firewall As A Service, Risky Network Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall As A Service Fwaas For Table Of Contents Ppt Ideas Microsoft
Firewall As A Service Fwaas For Table Of Contents Ppt Ideas MicrosoftIntroducing Firewall As A Service Fwaas For Table Of Contents Ppt Ideas Microsoft to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Fwaas Solution Providers, Service Technology Solution, Firewall As A Service, Fwaas Requirements In Organization, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Compressive Planning Guide To Improve Cybersecurity
Table Of Contents For Compressive Planning Guide To Improve CybersecurityIntroducing Table Of Contents For Compressive Planning Guide To Improve Cybersecurity to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Attack Incidents, Cyber Attack Risk Levels, Cybersecurity Risk Assessment Program, Monetary Losses Incurred Due, using this template. Grab it now to reap its full benefits.
-
 Network Security Using Secure Web Gateway Table Of Contents
Network Security Using Secure Web Gateway Table Of ContentsIntroducing Network Security Using Secure Web Gateway Table Of Contents to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Organization, Implementation, Timeline using this template. Grab it now to reap its full benefits.
-
 Understanding Security Risk Related With Dark Data Dark Data And Its Utilization
Understanding Security Risk Related With Dark Data Dark Data And Its UtilizationThis slide focuses on the security risks associated with dark data. Some of the risks associated with dark data include vulnerability to hacking, negative impact on the business, and an increased workload for IT teams, etc. Introducing Understanding Security Risk Related With Dark Data Dark Data And Its Utilization to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability To Hacking, Negative Impact On Business, Increased Workload For IT Teams, using this template. Grab it now to reap its full benefits.
-
 Layered Defence Security Icon For Threat Detection
Layered Defence Security Icon For Threat DetectionPresenting our set of slides with Layered Defence Security Icon For Threat Detection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Layered Defence Security, Icon For Threat Detection.
-
 Unlocking The Impact Of Technology Current Cybersecurity Trends Followed By Organisations
Unlocking The Impact Of Technology Current Cybersecurity Trends Followed By OrganisationsThis slide showcases trends followed by organisations related to cybersecurity. This template focuses on improving detection and response capabilities and building more digitally immune identity ecosystems. It includes information related to Chrome, microphones, etc. Increase audience engagement and knowledge by dispensing information using Unlocking The Impact Of Technology Current Cybersecurity Trends Followed By Organisations. This template helps you present information on five stages. You can also present information on Current Cybersecurity Trends, Microphones, Digitally Immune, Identity Ecosystems using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Unlocking The Impact Of Technology On Business For Table Of Content
Unlocking The Impact Of Technology On Business For Table Of ContentIncrease audience engagement and knowledge by dispensing information using Unlocking The Impact Of Technology On Business For Table Of Content. This template helps you present information on one stages. You can also present information on Information Technology In Business, Best Practices Of Technology, Latest Statistics Associated using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Data Encryption Implementation Plan Table Of Contents
Cloud Data Encryption Implementation Plan Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Cloud Data Encryption Implementation Plan Table Of Contents. This template helps you present information on one stages. You can also present information on Key Challenges, Cloud Data Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Components Of Effective Enterprise Security System
Components Of Effective Enterprise Security SystemThis slide represents enterprise security system components for effectiveness. This further includes components such as security cameras, video monitoring, smartphone alerts, manage employee access. Presenting our set of slides with Components Of Effective Enterprise Security System. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Cameras, Video Monitoring, Smartphone Alerts.
-
 Confidential Computing V2 Critical Functions Of Confidential Computing Technology
Confidential Computing V2 Critical Functions Of Confidential Computing TechnologyThis slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Increase audience engagement and knowledge by dispensing information using Confidential Computing V2 Critical Functions Of Confidential Computing Technology. This template helps you present information on three stages. You can also present information on Code Integrity, Data Integrity, Data Confidentially, Confidential Computing Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing V2 For Table Of Contents Ppt Infographics Graphics Download
Confidential Computing V2 For Table Of Contents Ppt Infographics Graphics DownloadIntroducing Confidential Computing V2 For Table Of Contents Ppt Infographics Graphics Download to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Architecture And Realms Working, Trust Boundary Across Azure, Primary Approaches, Technologies Overview, using this template. Grab it now to reap its full benefits.
-
 Secops V2 For Table Of Contents Ppt Infographic Template Model
Secops V2 For Table Of Contents Ppt Infographic Template ModelIncrease audience engagement and knowledge by dispensing information using Secops V2 For Table Of Contents Ppt Infographic Template Model. This template helps you present information on one stages. You can also present information on Team Structure, Roles And Responsibilities, Critical Functional Areas, Key Outcomes Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies For Table Of Contents Ppt Ideas Templates
Encryption Implementation Strategies For Table Of Contents Ppt Ideas TemplatesIntroducing Encryption Implementation Strategies For Table Of Contents Ppt Ideas Templates to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Safeguard Network Communication, Encryption Key Management Software, Applications Of Encryption As A Service, using this template. Grab it now to reap its full benefits.
-
 Steps To Create Consortium Blockchain Network Technology Complete Guide To Understand BCT SS
Steps To Create Consortium Blockchain Network Technology Complete Guide To Understand BCT SSThis slide covers step-by-step process involved in creating a consortium blockchain network technology. It includes steps such as identifying participating companies, defining governance structure, establishing shared objectives, setting up private blockchains as nodes, etc. Introducing Steps To Create Consortium Blockchain Network Technology Complete Guide To Understand BCT SS to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Identify Participating Companies, Governance Structure, Between Blockchains using this template. Grab it now to reap its full benefits.
-
 Icon For Ensuring Cybersecurity In Automatic Control System
Icon For Ensuring Cybersecurity In Automatic Control SystemIntroducing our premium set of slides with Icon For Ensuring Cybersecurity In Automatic Control System. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon Ensuring Cybersecurity, Automatic Control System. So download instantly and tailor it with your information.
-
 Icon For Network Security Through Zero Trust Architecture
Icon For Network Security Through Zero Trust ArchitecturePresenting our set of slides with Icon For Network Security Through Zero Trust Architecture. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon Network Security, Zero Trust Architecture.
-
 Icon For Zero Trust Network Architecture
Icon For Zero Trust Network ArchitectureIntroducing our premium set of slides with Icon For Zero Trust Network Architecture. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon Zero Trust, Network Architecture. So download instantly and tailor it with your information.
-
 Network Security Management System Icon
Network Security Management System IconPresenting our set of slides with Network Security Management System Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Security Management, System Icon.
-
 Digital Transformation Icon For Information Security Management
Digital Transformation Icon For Information Security ManagementIntroducing our premium set of slides with Digital Transformation Icon For Information Security Management. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Digital Transformation Icon, Information Security Management. So download instantly and tailor it with your information.
-
 Information Security Management Icon For Consumer Data Privacy
Information Security Management Icon For Consumer Data PrivacyIntroducing our premium set of slides with Information Security Management Icon For Consumer Data Privacy. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Security Management Icon, Consumer Data Privacy. So download instantly and tailor it with your information.
-
 Information Security Management Icon For Data Protection
Information Security Management Icon For Data ProtectionPresenting our set of slides with Information Security Management Icon For Data Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Information Security Management Icon, Data Protection.
-
 Cryptography In Cybersecurity For Blockchain Icon
Cryptography In Cybersecurity For Blockchain IconPresenting our set of slides with Cryptography In Cybersecurity For Blockchain Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cryptography, Cybersecurity, Blockchain Icon.
-
 Cryptography In Cybersecurity For Business Icon
Cryptography In Cybersecurity For Business IconIntroducing our premium set of slides with Cryptography In Cybersecurity For Business Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Business Icon, Cybersecurity, Cryptography. So download instantly and tailor it with your information.
-
 Blockchain Technologies For Developing Metaverse Cryptocurrencies
Blockchain Technologies For Developing Metaverse CryptocurrenciesIntroducing our premium set of slides with Blockchain Technologies For Developing Metaverse Cryptocurrencies. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Blockchain, Technologies, Cryptocurrencies. So download instantly and tailor it with your information.
-
 Why Invest With Us Fundraising Pitch Deck For Project Management Software
Why Invest With Us Fundraising Pitch Deck For Project Management SoftwareFollowing slide showcases benefits that are offered by company to assure business safety. It include pointers such as consistent backups, development processes, encryption, code review etc. Increase audience engagement and knowledge by dispensing information using Why Invest With Us Fundraising Pitch Deck For Project Management Software. This template helps you present information on six stages. You can also present information on Consistent Backups, Separate Environments, Development Processes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Functional Testing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS V
Functional Testing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide showcases checklist for functional testing to ensure blockchain security. It includes elements such as size of blockchain, addition of blocks, data transmission, API, integration, performance and security testing, etc. Introducing Functional Testing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS V to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Size Of Blockchain, Addition Blocks, Data Transmission, using this template. Grab it now to reap its full benefits.
-
 Major Cybersecurity Challenges Securing Blockchain Transactions A Beginners Guide BCT SS V
Major Cybersecurity Challenges Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide illustrates various issues faced by blockchain users. It includes elements such as smart contract vulnerabilities, privacy, confidentiality, weak consensus mechanism, private key management, phishing, along with its impact, etc. Increase audience engagement and knowledge by dispensing information using Major Cybersecurity Challenges Securing Blockchain Transactions A Beginners Guide BCT SS V. This template helps you present information on one stages. You can also present information on Smart Contract Vulnerabilities, Weak Consensus Mechanism, Private Key Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview And Workflow Securing Blockchain Transactions A Beginners Guide BCT SS V
Overview And Workflow Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc. Introducing Overview And Workflow Securing Blockchain Transactions A Beginners Guide BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Transaction Requested, Node Validates Transaction, Transaction Completed, using this template. Grab it now to reap its full benefits.
-
 Overview And Working Process Securing Blockchain Transactions A Beginners Guide BCT SS V
Overview And Working Process Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide illustrates brief introduction of distributed denial of service DDoS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc. Increase audience engagement and knowledge by dispensing information using Overview And Working Process Securing Blockchain Transactions A Beginners Guide BCT SS V. This template helps you present information on four stages. You can also present information on Attacker Controls Website Hostage, Demands Hefty Amount, Companies Are Imposed using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloning In Cyber Security For Data Protection
Cloning In Cyber Security For Data ProtectionThis slide shows benefits of cloning for cyber protection. It aims to prevent cloning security risks to mitigate unauthorized access to technical assets. It covers four cyber security measures such as data protection, integrity, loss prevention and transfers. Presenting our set of slides with name Cloning In Cyber Security For Data Protection. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Protection, Data Integrity, Data Transfers.
-
 Cyber Security Icon Protecting Card Cloning Fraud
Cyber Security Icon Protecting Card Cloning FraudIntroducing our premium set of slides with name Cyber Security Icon Protecting Card Cloning Fraud. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security, Icon Protecting, Card Cloning Fraud. So download instantly and tailor it with your information.
-
 Disk Cloning Icon In Cyber Security
Disk Cloning Icon In Cyber SecurityPresenting our set of slides with name Disk Cloning Icon In Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Disk Cloning, Icon In Cyber Security.
-
Understandable and informative presentation.
-
Informative and engaging! I really like the design and quality of the slides.
-
The templates are easy to get, and the chat customer support is excellent.
-
Like always a great experience with you guys. Always there on the drop of hat to help.
-
Good research work and creative work done on every template.
-
I have just started downloading templates for my presentations and I must say this is a great design. It helped accelerate my presentation design process and made it more visually appealing.
-
If you are looking for satisfactory PowerPoint services, SlideTeam is your go-to place. I am fully contented with their research and development team.
-
Fantastic collection. Loved how we can personalize these templates as per the requirements.
-
The website is jam-packed with fantastic and creative templates for a variety of business concepts. They are easy to use and customize.
-
Thanks for all your great templates they have saved me lots of time and accelerate my presentations. Great product, keep them up!






