Powerpoint Templates and Google slides for Vulnerability Management Risks
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
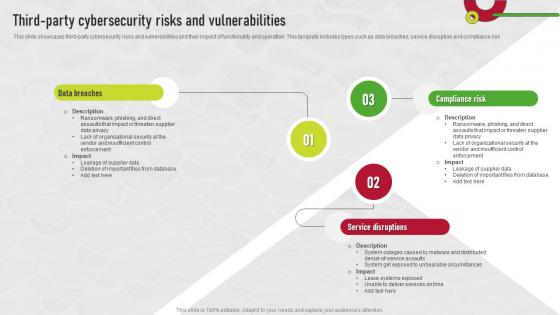 Third Party Cybersecurity Risks And Vulnerabilities Supplier Risk Management
Third Party Cybersecurity Risks And Vulnerabilities Supplier Risk ManagementThis slide showcases third party cybersecurity risks and vulnerabilities and their impact of functionality and operation. This template includes types such as data breaches, service disruption and compliance risk. Increase audience engagement and knowledge by dispensing information using Third Party Cybersecurity Risks And Vulnerabilities Supplier Risk Management. This template helps you present information on three stages. You can also present information on Data Breaches, Service Disruptions, Compliance Risk using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Classify Assets Vulnerable To Cyber Attack Implementing Cyber Risk Management Process
Classify Assets Vulnerable To Cyber Attack Implementing Cyber Risk Management ProcessThe following slide depicts some major assets that are more prone to cyber-attack. It mainly includes elements such as sales record, sales lead record, company internal database, customer and product information etc. Present the topic in a bit more detail with this Classify Assets Vulnerable To Cyber Attack Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Assets, Details, Comments. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identify Threat And Vulnerabilities Within Information Implementing Cyber Risk Management Process
Identify Threat And Vulnerabilities Within Information Implementing Cyber Risk Management ProcessThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Present the topic in a bit more detail with this Identify Threat And Vulnerabilities Within Information Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Vulnerability, Threat, Threat Source. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk And Vulnerability Management Dashboard Introduction
Risk And Vulnerability Management Dashboard IntroductionThe slide highlights the risk and vulnerability management dashboard introduction representing risk exposure, number of impacted resources and weekly trend, recent risk exposure, risk exposure by resource proportion and type. Presenting our well structured Risk And Vulnerability Management Dashboard Introduction. The topics discussed in this slide are Impacted Resource, Risk Exposure By Resource Proportion, Risk Exposure By Resource Type, Recent Risk Exposure. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Risk Management Framework For Information Security Threat And Vulnerability
Risk Management Framework For Information Security Threat And VulnerabilityFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Risk Management Framework For Information Security Threat And Vulnerability. Use it as a tool for discussion and navigation on Exposure Score, Top Vulnerable Software, Severity Distribution, Active Remediation, Configuration Score. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
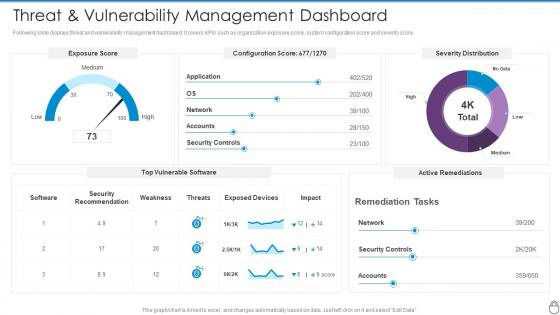 Cybersecurity Risk Management Framework Threat And Vulnerability Management Dashboard
Cybersecurity Risk Management Framework Threat And Vulnerability Management DashboardFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Cybersecurity Risk Management Framework Threat And Vulnerability Management Dashboard. Use it as a tool for discussion and navigation on Exposure Score, Configuration Score, Severity Distribution, Weakness, Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Defining vulnerability rating effective information security risk management process
Defining vulnerability rating effective information security risk management processFollowing slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description.Present the topic in a bit more detail with this Defining Vulnerability Rating Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Occurrence Of Attack, Organization Is Reasonably, Organization Is Capable Enough. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 How financial risk can be controlled managing critical threat vulnerabilities and security threats
How financial risk can be controlled managing critical threat vulnerabilities and security threatsThis slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Increase audience engagement and knowledge by dispensing information using How Financial Risk Can Be Controlled Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on three stages. You can also present information on Liquidity Risk, Exchange Risk, Credit Exchange Risk using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Threat vulnerability asset matrix managing cyber risk in a digital age
Threat vulnerability asset matrix managing cyber risk in a digital ageMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Present the topic in a bit more detail with this Threat Vulnerability Asset Matrix Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Threat Vulnerability Asset Matrix. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Framework For Information Security Defining Vulnerability Rating With Criteria
Risk Management Framework For Information Security Defining Vulnerability Rating With CriteriaFollowing slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Present the topic in a bit more detail with this Risk Management Framework For Information Security Defining Vulnerability Rating With Criteria. Use it as a tool for discussion and navigation on Vulnerability Ranking, Organization, High, Low, Medium. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Management Framework Defining Vulnerability Rating
Cybersecurity Risk Management Framework Defining Vulnerability RatingFollowing slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Management Framework Defining Vulnerability Rating. Dispense information and present a thorough explanation of Occurrence Attack, Asset Moderately Susceptible, Asset Highly Susceptible using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
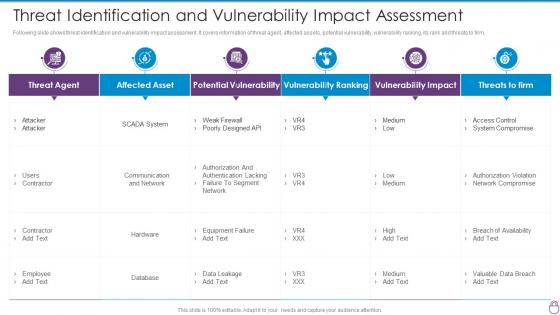 Cybersecurity Risk Management Framework Threat Identification And Vulnerability Impact
Cybersecurity Risk Management Framework Threat Identification And Vulnerability ImpactFollowing slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Management Framework Threat Identification And Vulnerability Impact. Dispense information and present a thorough explanation of Threat Agent, Affected Asset, Potential Vulnerability, Vulnerability Ranking, Vulnerability Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
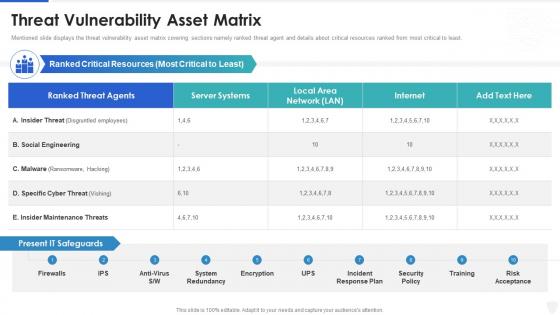 Cybersecurity and digital business risk management threat vulnerability asset matrix
Cybersecurity and digital business risk management threat vulnerability asset matrixMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an outstanding presentation on the topic using this Cybersecurity And Digital Business Risk Management Threat Vulnerability Asset Matrix. Dispense information and present a thorough explanation of Threat Vulnerability Asset Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Acceptance Checklist With Vulnerability Management
Risk Acceptance Checklist With Vulnerability ManagementThis slide showcases risk acceptance checklist which can be referred by IT management to accept or mitigate vulnerabilities with least amount of loss. It includes information about risks, date of occurrence, vulnerability level, next follow up, etc. Introducing our Risk Acceptance Checklist With Vulnerability Management set of slides. The topics discussed in these slides are Risk Acceptance, Checklist, Vulnerability Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Risk Assessment Matrix With Vulnerability Risk Assessment And Management Plan For Information Security
Risk Assessment Matrix With Vulnerability Risk Assessment And Management Plan For Information SecurityThis slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level Present the topic in a bit more detail with this Risk Assessment Matrix With Vulnerability Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Assessment, Vulnerability, Associated. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Vulnerability Rating For Risk Identification Risk Assessment And Management Plan For Information Security
Vulnerability Rating For Risk Identification Risk Assessment And Management Plan For Information SecurityThis slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description Present the topic in a bit more detail with this Vulnerability Rating For Risk Identification Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Identification, Information, Vulnerability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Risk Management Strategies IT Vulnerabilities With Threat Source And Action
IT Risk Management Strategies IT Vulnerabilities With Threat Source And ActionThe following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Present the topic in a bit more detail with this IT Risk Management Strategies IT Vulnerabilities With Threat Source And Action. Use it as a tool for discussion and navigation on Vulnerabilities, Threat Source, Threat Action. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise Risk Management IT Vulnerabilities With Threat Source And Action
Enterprise Risk Management IT Vulnerabilities With Threat Source And ActionThe following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Present the topic in a bit more detail with this Enterprise Risk Management IT Vulnerabilities With Threat Source And Action. Use it as a tool for discussion and navigation on Vulnerabilities, Threat Source, Threat Action. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Vulnerabilities With Threat Source Risk Management Guide For Information Technology Systems
IT Vulnerabilities With Threat Source Risk Management Guide For Information Technology SystemsThe following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Present the topic in a bit more detail with this IT Vulnerabilities With Threat Source Risk Management Guide For Information Technology Systems. Use it as a tool for discussion and navigation on Vulnerabilities, Threat Source, Threat Action. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Management
Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk ManagementThis slide showcases assessment matrix to identify risk associate with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level. Deliver an outstanding presentation on the topic using this Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Management. Dispense information and present a thorough explanation of Risk Assessment Matrix, Vulnerability Level, Threat Level using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat Identification And Vulnerability Assessment Information Security Risk Management
Threat Identification And Vulnerability Assessment Information Security Risk ManagementThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Present the topic in a bit more detail with this Threat Identification And Vulnerability Assessment Information Security Risk Management. Use it as a tool for discussion and navigation on Threat Identification, Vulnerability Assessment, Risk Identification. This template is free to edit as deemed fit for your organization. Therefore download it now
-
 Vulnerability Rating For Risk Identification Information Security Risk Management
Vulnerability Rating For Risk Identification Information Security Risk ManagementThis slide showcases table for allocating vulnerability rating to different class of information assets. Its shows information about severity, vulnerability score and description. Present the topic in a bit more detail with this Vulnerability Rating For Risk Identification Information Security Risk Management. Use it as a tool for discussion and navigation on Vulnerability Score, Risk Identification, Severity. This template is free to edit as deemed fit for your organization. Therefore download it now
-
 Cybersecurity Risk Analysis And Management Plan Risk Assessment Matrix With Vulnerability And Threat
Cybersecurity Risk Analysis And Management Plan Risk Assessment Matrix With Vulnerability And ThreatThis slide showcases assessment matrix to identify risk associated with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level Deliver an outstanding presentation on the topic using this Cybersecurity Risk Analysis And Management Plan Risk Assessment Matrix With Vulnerability And Threat. Dispense information and present a thorough explanation of Assessment, Vulnerability, Threat Level using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management Plan
Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management PlanThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating Deliver an outstanding presentation on the topic using this Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Identification, Assessment, Vulnerability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Vulnerability Rating For Risk Identification Cybersecurity Risk Analysis And Management Plan
Vulnerability Rating For Risk Identification Cybersecurity Risk Analysis And Management PlanThis slide showcases table for allocating vulnerability rating to different class of information assets. Its shows information about severity, vulnerability score and description Deliver an outstanding presentation on the topic using this Vulnerability Rating For Risk Identification Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Vulnerability, Identification, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Based Vulnerability Management Software In Powerpoint And Google Slides Cpb
Risk Based Vulnerability Management Software In Powerpoint And Google Slides CpbPresenting Risk Based Vulnerability Management Software In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Risk Based Vulnerability Management Software. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Project management cycle evaluating risk and vulnerabilities at different stages of project cycle
Project management cycle evaluating risk and vulnerabilities at different stages of project cyclePresenting this set of slides with name - Project Management Cycle Evaluating Risk And Vulnerabilities At Different Stages Of Project Cycle. This is a four stage process. The stages in this process are Project Management Cycle, Project Management Process, Project Management.
-
 Vulnerability management lifecycle risk security reporting monitoring
Vulnerability management lifecycle risk security reporting monitoringPresenting this set of slides with name - Vulnerability Management Lifecycle Risk Security Reporting Monitoring. This is a six stage process. The stages in this process are Vulnerability Management, Risk Management, Vulnerability Planning.
-
 Vulnerability management risks discovery risk management drivers performance cpb
Vulnerability management risks discovery risk management drivers performance cpbPresenting this set of slides with name - Vulnerability Management Risks Discovery Risk Management Drivers Performance Cpb. This is an editable five stages graphic that deals with topics like Vulnerability Management Risks, Discovery Risk Management, Drivers Performance to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Affiliate marketing operational risk resilience personalisation marketing vulnerability management cpb
Affiliate marketing operational risk resilience personalisation marketing vulnerability management cpbPresenting this set of slides with name - Affiliate Marketing Operational Risk Resilience Personalisation Marketing Vulnerability Management Cpb. This is an editable three stages graphic that deals with topics like Affiliate Marketing, Operational Risk Resilience, Personalisation Marketing, Vulnerability Management to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Bi fold risk assessment in vulnerability management document report pdf ppt template
Bi fold risk assessment in vulnerability management document report pdf ppt templateStrengthen your customer engagement with this Bi Fold Risk Assessment In Vulnerability Management Document Report PDF PPT Template. Put together with 4 pages crafted in PowerPoint, this bi-fold document reflects everything your company stands for. Featuring editable and customizable design elements, this A4 size layout is a great communication and visual reporting tool. Fully compatible with Google Slides, this bi-fold design can be used to fulfill any industrial requirement. The choice is yours and the options are endless.
-
 Vulnerability management risk management ppt powerpoint presentation show cpb
Vulnerability management risk management ppt powerpoint presentation show cpbPresenting this set of slides with name Vulnerability Management Risk Management Ppt Powerpoint Presentation Show Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Vulnerability Management Risk Management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 One page risk assessment in vulnerability management presentation report infographic ppt pdf document
One page risk assessment in vulnerability management presentation report infographic ppt pdf documentHere we present One Page Risk Assessment In Vulnerability Management Presentation Report Infographic PPT PDF Document one pager PowerPoint template. Vulnerability means the inability of a group or an individual to cope up or withstand the impact of hostile environment. Vulnerability management thus helps in identifying, classifying, evaluating and mitigating the vulnerabilities in software. To assist you in mitigating the risks we have come up with risk assessment in vulnerability management PowerPoint slide design one pager. This vulnerability assessment PowerPoint template one pager covers details about risk assessment in vulnerability management with executive summary where you can present the aim of vulnerability scan. It gives you a column to jot down your findings and severity of vulnerability. Manage your network security using vulnerability management approach and safeguard data assets of your organization. The slide being completely customizable and readily available saves a lot of time of the presenter in explaining and showcasing the concepts. You can add or remove any element on this vulnerability scanner one pager template. Incorporate this amazingly curated PowerPoint template to deal with vulnerabilities and make sure that your organization focuses on efficient tactics. Grab this One Page Risk Assessment In Vulnerability Management Presentation Report Infographic PPT PDF Document one pager template now.
-
 Organization risk probability management categorize and prioritize vulnerabilities ppt grid
Organization risk probability management categorize and prioritize vulnerabilities ppt gridIncrease audience engagement and knowledge by dispensing information using Organization Risk Probability Management Categorize And Prioritize Vulnerabilities Ppt Grid. This template helps you present information on three stages. You can also present information on Relevance, Responsibility, Prioritize, Categorize using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Organization risk probability management define a vulnerability analysis and resolution strategy ppt layouts
Organization risk probability management define a vulnerability analysis and resolution strategy ppt layoutsIntroducing Organization Risk Probability Management Define A Vulnerability Analysis And Resolution Strategy Ppt Layouts to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability, Resolution, Management, Activities, using this template. Grab it now to reap its full benefits.
-
 Organization risk probability management determine approved methods of vulnerability assessment ppt display
Organization risk probability management determine approved methods of vulnerability assessment ppt displayIntroducing Organization Risk Probability Management Determine Approved Methods Of Vulnerability Assessment Ppt Display to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Determine, Required, Requirements, Legal, Candidate, using this template. Grab it now to reap its full benefits.
-
 Organization risk probability management determine effectiveness of vulnerability dispositions ppt designs
Organization risk probability management determine effectiveness of vulnerability dispositions ppt designsIncrease audience engagement and knowledge by dispensing information using Organization Risk Probability Management Determine Effectiveness Of Vulnerability Dispositions Ppt Designs. This template helps you present information on three stages. You can also present information on Vulnerability, Necessary, Organization, Determine using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Organization risk probability management determine the scope of vulnerability management ppt themes
Organization risk probability management determine the scope of vulnerability management ppt themesIntroducing Organization Risk Probability Management Determine The Scope Of Vulnerability Management Ppt Themes to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Management, Environment, Monitoring, Services, Assets, using this template. Grab it now to reap its full benefits.
-
 Organization risk probability management identify sources of vulnerability information ppt grid
Organization risk probability management identify sources of vulnerability information ppt gridIncrease audience engagement and knowledge by dispensing information using Organization Risk Probability Management Identify Sources Of Vulnerability Information Ppt Grid. This template helps you present information on six stages. You can also present information on Identify, Sources, Assets, Department, Groups using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Organization risk probability management implement the vulnerability analysis ppt good
Organization risk probability management implement the vulnerability analysis ppt goodIntroducing Organization Risk Probability Management Implement The Vulnerability Analysis Ppt Good to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability, Resolution, Training, Manage, Assessment, using this template. Grab it now to reap its full benefits.
-
 Organization risk probability management manage exposure to discovered vulnerabilities ppt template
Organization risk probability management manage exposure to discovered vulnerabilities ppt templateIncrease audience engagement and knowledge by dispensing information using Organization Risk Probability Management Manage Exposure To Discovered Vulnerabilities Ppt Template. This template helps you present information on four stages. You can also present information on Manage, Determine, Disposition, Resolution, Vulnerabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Organization risk probability management need for vulnerability management ppt slideshow
Organization risk probability management need for vulnerability management ppt slideshowIntroducing Organization Risk Probability Management Need For Vulnerability Management Ppt Slideshow to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Management, Vulnerability, Need, Reduction, using this template. Grab it now to reap its full benefits.
-
 Organization risk probability management overview vulnerability ppt portfolio
Organization risk probability management overview vulnerability ppt portfolioPresent the topic in a bit more detail with this Organization Risk Probability Management Overview Vulnerability Ppt Portfolio. Use it as a tool for discussion and navigation on Guidance, Management, Improvement, Monitoring, Input. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organization risk probability management record discovered vulnerabilities ppt samples
Organization risk probability management record discovered vulnerabilities ppt samplesIncrease audience engagement and knowledge by dispensing information using Organization Risk Probability Management Record Discovered Vulnerabilities Ppt Samples. This template helps you present information on five stages. You can also present information on Vulnerabilities, Repository, Assets, Categorization, Priority using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Organization risk probability management vulnerability management model ppt powerpoint ideas
Organization risk probability management vulnerability management model ppt powerpoint ideasIntroducing Organization Risk Probability Management Vulnerability Management Model Ppt Powerpoint Ideas to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Scanning, Compliance, Prioritization, Management, Business, using this template. Grab it now to reap its full benefits.
-
 Defining vulnerability rating information security risk management program
Defining vulnerability rating information security risk management programFollowing slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver an outstanding presentation on the topic using this Defining Vulnerability Rating Information Security Risk Management Program. Dispense information and present a thorough explanation of Organization, Occurrence, Asset using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat vulnerability dashboard information security risk management program
Threat vulnerability dashboard information security risk management programFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Threat Vulnerability Dashboard Information Security Risk Management Program. Use it as a tool for discussion and navigation on Exposure Score, Vulnerable Software, Security Recommendation. This template is free to edit as deemed fit for your organization. Therefore download it now.



